Navigation
- Change Log
- Overview
- Prerequisites
- AAA Groups
- Session Policy/Profile
- Citrix Gateway Plug-in (i.e. VPN Client)
- Other VPN Objects
- StoreFront in Gateway Clientless Access Portal
- Quarantine Group
💡 = Recently Updated
Change Log
- 2021 May 5 – Upgrade Gateway Plug-in on ADC
- 2021 Feb 5 – VPN Client – added SecureDNS info from 13.0-71.44 release notes
- 2021 Jan 9 – Bind Session Policy – added info from CTX289931 AAA group session policies are not applying based on priority
- 2019 Mar 6 – VPN Session Profile – added link to AlwaysOn service for Windows at Citrix Docs.
- 2018 Oct 6 – updated some screenshots for Gateway 12.1
- Gateway Plug-in – 12.1 supports nFactor authentication
- 2018 Apr 3 – in the Create Session Profile section, added Clientless Access removal instructions from CTP Sam Jacobs at NetScaler Gateway Client Choices – hide/remove Virtual Apps and Desktops at Citrix Discussions
- 2018 Mar 18 – in the NetScaler Gateway Virtual Server section, added info from Julien Mooren NetScaler – Native OTP is breaking SSL VPN.
- 2018 Feb 8 – in Authorization Policies section, added info from CTX232237 NetScaler Unified Gateway Advanced Authorization Policy Support for UDP/ICMP/DNS Traffic
Overview
Here’s an overview of the Citrix Gateway connection process:
- Users use SSL/TLS to connect to a Citrix Gateway Virtual Server (VIP).
- Citrix Gateway prompts the user for authentication.
- Once the user is authenticated, Citrix Gateway uses Session Policies/Profiles to determine what happens next.
Citrix Gateway supports six different connection methods:
- ICA Proxy to Citrix Virtual Apps and Desktops (CVAD) (aka XenApp/XenDesktop) and StoreFront – the client is built into Citrix Workspace app (aka Citrix Receiver)
- SSL VPN – requires installation of Citrix Gateway plug-in (VPN client)
- Clientless – browser only, no VPN client, uses rewrite
- Secure Browse – from MDX-wrapped mobile applications (Citrix Endpoint Management aka XenMobile), uses rewrite
- RDP Proxy – only RDP client is needed
- PCoIP Proxy – only VMware Horizon Client is needed
You can configure Citrix Gateway Session Policies/Profiles to only use one of the connection methods. Or Citrix Gateway can be configured to let users choose between ICA Proxy, Clientless, and SSL VPN connection methods. Here’s a sample Client Choices screen using the RfWebUI theme:
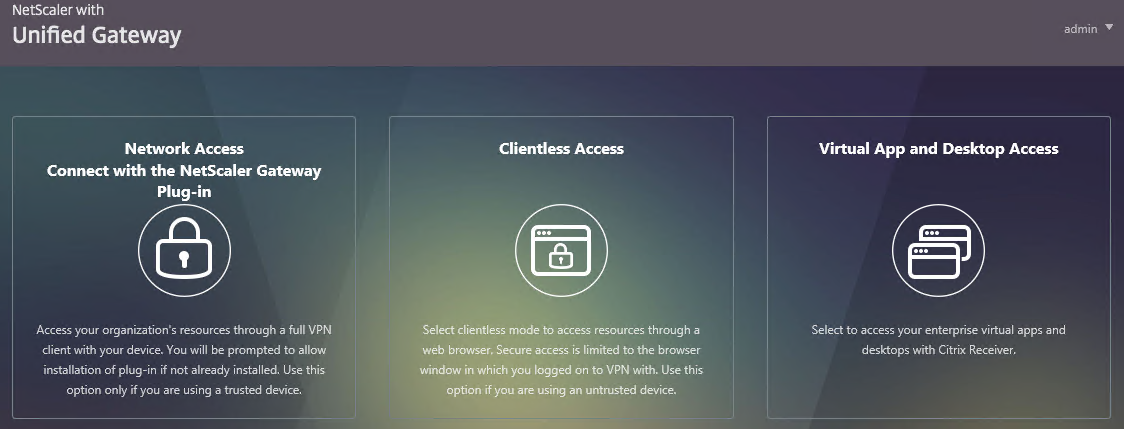
- The Clientless Access option opens a portal page that has icons from Citrix StoreFront (ICA Proxy), icons for RDP Proxy, icons for PCoIP Proxy, and links to websites.
- The website links can be proxied through Citrix Gateway. Proxy methods include: clientless rewrite, SSL VPN, and traditional load balancing.
- Citrix Gateway can optionally Single Sign-on to the websites.
- The Virtual App and Desktop Access option only displays icons from Citrix StoreFront (ICA Proxy). For other types of icons, you’ll need Clientless Access.
- The Connect with Citrix Gateway Plug-in option launches the VPN tunnel. After the tunnel is established, a portal page is displayed. This can be the Clientless Access portal, or a user defined website URL (e.g. intranet).
Session Policies/Profiles have several settings that control the behavior seen after authentication:
- ICA Proxy – ON or OFF
- If ON, then ICA Proxy is the only connection method allowed, overriding the other connection methods.
- ICA Proxy does not launch the VPN client. It only needs Citrix Workspace app.
- ICA Proxy shows the Webpage that’s configured in the Web Interface Address field of the Session Profile. This is typically the StoreFront Receiver for Web page, but technically it can be any internal website.
- If OFF, that doesn’t mean ICA Proxy doesn’t work. You can still send ICA traffic to the Citrix Gateway Virtual Server, and the Citrix Gateway Virtual Server will still proxy it to internal VDAs.
- Setting it to OFF allows the other connection methods to function. For example, Clientless Access can show both Citrix Gateway Bookmarks and StoreFront published apps. If VPN is launched, then the portal page shown to the user after the tunnel is established can contain the StoreFront published applications.
- Clientless Access – On, Off, Disabled
- If On, then Clientless is the only connection method allowed, assuming ICA Proxy is not set to ON. After the user logs in, the user is presented with a portal page that contains a list of Gateway bookmarks and/or StoreFront published icons. The VPN Client is not launched.
- The Home Page setting in the Session Profile allows you to display an internal website instead of displaying the Citrix Gateway Portal Page.
- Bookmarks are configured at Citrix Gateway > Resources > Bookmarks. You can bind the Bookmarks (Urls) to the Citrix Gateway Virtual Server, or to AAA Groups.
- Only Bookmarks configured for Clientless Access will work without a VPN. The internal websites are rewritten so they are proxied through Citrix Gateway. For example, if the internal website is http://intranet.corp.local, then Gateway rewrites them to https://gateway.corp.com/cvpn/http/internal.corp.local. This causes the web browser to send the HTTP Request to Citrix Gateway, which then forwards the HTTP Request to the internal web server. No VPN needed.
- Plug-in Type – Windows/MAC OS X
- If both Clientless and ICA Proxy are set to Off, then the VPN Client will be downloaded and launched.
- Once the VPN tunnel is established, the webpage configured in the Home Page setting is displayed. Or the Citrix Gateway Portal Page (Clientless Access) is displayed if no Home Page is configured. The Bookmarks in the Portal Page can link to internal websites that are only accessible through a VPN tunnel. Or Bookmarks can be configured for Clientless Access.
- Additional Gateway objects control VPN behavior including: DNS Suffix, Intranet Applications, Intranet IPs, and Authorization Policies.
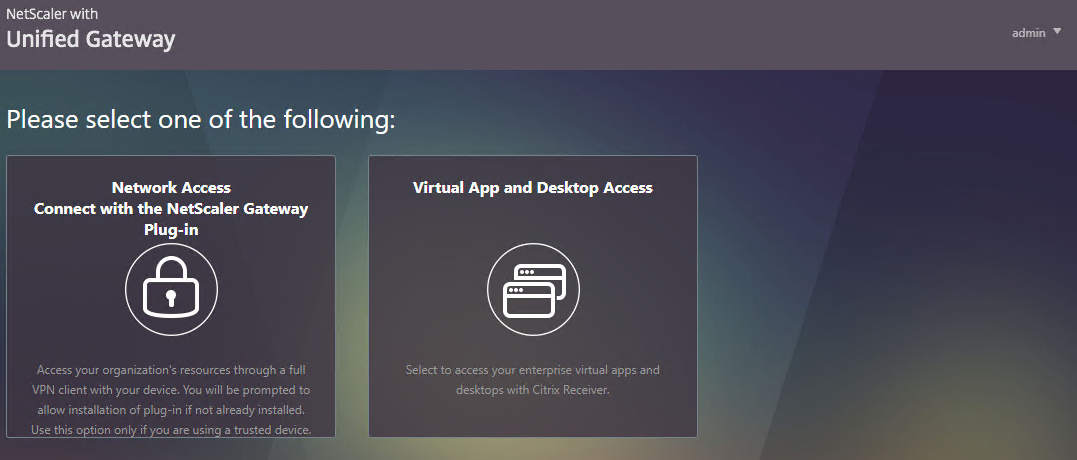
- Client Choices – checked or unchecked
- If Client Choices is checked, then it displays a page containing up to three buttons allowing the user to choose between VPN, Clientless, or StoreFront. The Network Access with the Citrix Gateway Plug-in (VPN) button is always displayed. The Clientless Access button is displayed if Clientless Access is set to On or Off (not Disabled). The Virtual App and Desktop Access button is displayed if a Web Interface Address is configured.
Here are some characteristics of Session Policies:
- Citrix Gateway > Global Settings > Change Global Settings has the same settings as a Session Profile. However, all Session Policies/Profiles override the settings configured in Global Settings. That’s the whole point of the Override Global checkboxes in the Session Profiles.
- Session Policy Expression – If the Session Policy Expression is true, then the settings contained in the Session Profile are applied.
- Action = Session Profile – The Session Profile is also sometimes called the Action. That’s because all Citrix ADC policies follow a standard structure – if the expression evaluates to True, then perform the Action. For Session Policies in particular, the policy Action = Session Profile.
- EPA – The Session Policy Expression in Classic Syntax could include an Endpoint Analysis (EPA) expression.
- Default Syntax Expressions vs Classic Syntax Policy Expressions – Citrix ADC 12 and newer supports Default (Advanced) Syntax Expressions on Session Policies, in addition to the older Classic Syntax.
- No syntax mixing – All Session Policies bound anywhere must be either Default or Classic. You cannot mix the two types.
- EPA is Classic only – EPA Scans are only supported in Classic Expressions.
- AD Group in Default Syntax – Default Syntax allows expressions for AD Group Membership like
HTTP.REQ.USER.IS_MEMBER_OF("MyADGroup"). This could eliminate AAA Groups in some circumstances.
- Policy Bind Points – Session Policies can be bound to three different bind points – Citrix Gateway Virtual Server, AAA Groups, and AAA User.
- When bound to a Citrix Gateway Virtual Server, the Session policy/profile applies to all users that log into that Virtual Server.
- When bound to a AAA Group, the Session policy/profile only applies to members of the AAA group (Active Directory group or local group)
- When bound to a AAA User, the Session policy/profile only applies to the AAA user (Active Directory user or local user)
- Profile Conflicts – Multiple Session Policies/Profiles could apply to a single session. In this case, the Profile settings are merged. But if there’s a conflict (e.g. one Session Profile enables Clientless access, but another Session Profile disables Clientless access), then which one wins?
- Priority number – When you bind a Session Policy to a bind point, you specify a priority number. This priority number usually defaults to 100.
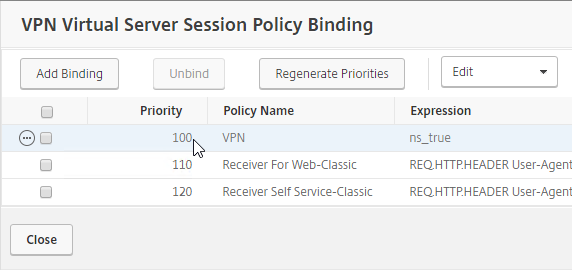
- Lowest priority number wins – The Session Policy binding that has the lowest priority number, wins. Session Policies bound with a priority of 80 will win over Session Policies bound with a priority of 100. Remember, for settings that don’t conflict, the two Profiles merge, but for settings that do conflict, the lower priority number policy/profile settings win.
- Classic Policy Priority and multiple bind points – for Classic Session Policies the bind point location doesn’t matter. If you bind a Session Policy to a AAA Group with a priority of 100, and you also bind a Session Policy to the Citrix Gateway Virtual Server with a priority of 80, then the conflicting settings in the Session Policy bound to the Citrix Gateway Virtual Server will win because it has the lower priority number. You might think that AAA-bound policies always override Virtual Server-bound policies, but that is not the case.
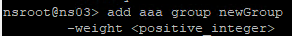
- Advanced Policy Priority and multiple AAA Groups – see CTX289931 AAA group session policies are not applying based on priority. The first created AAA Group overrides AAA Groups created later unless you specify the weight parameter when creating the AAA Group from the CLI.
- Priority number – When you bind a Session Policy to a bind point, you specify a priority number. This priority number usually defaults to 100.
- Global Settings vs Virtual Server Settings – When you bind a Session Policy to a Citrix Gateway Virtual Server, the settings in the Session Profile only apply to connections through that particular Citrix Gateway Virtual Server.
- Settings in Citrix Gateway > Global Settings > Change Global Settings apply to every Gateway Virtual Server.
- Settings in AAA Group > Policies > Session Policy/Profile apply to every Gateway Virtual Server.
- If you want a particular Gateway Virtual Server to override AAA or Global, your only choice is to bind a Session Policy to the Gateway Virtual Server with a lower priority number than the AAA Bind Points.
AAA Groups are a critical component of Citrix Gateway VPN configuration:
- Group extraction – Make sure the LDAP Policy/Server is configured to extract to the user’s Active Directory Groups.
- Create AAA Groups on the Citrix ADC that match exactly (case sensitive) with the user’s Active Directory Group Name.
- Default Syntax and AD Groups – An alternative to AAA Groups is to use
HTTP.REQ.USER.IS_MEMBER_OF("MyADGroup")Default Syntax expressions. However, Default Syntax does not support Endpoint Analysis. And Default Syntax only applies to Session Policies and Authorization Policies, so you might still need AAA Groups for Bookmarks, Intranet Applications, and Intranet IPs.
- Default Syntax and AD Groups – An alternative to AAA Groups is to use
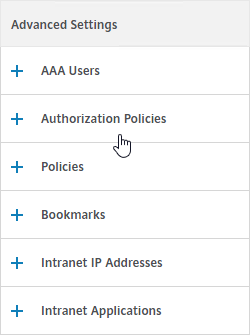
- You can bind policies and other Gateway objects to the AAA Group, and these bindings only affect that particular AAA Group. These bindings include:
- Session Policies
- Bookmarks
- Intranet IPs (aka IP Pool)
- Intranet Applications (for split tunnel)
- Authorization Policies (what’s allowed across the VPN tunnel)
- Note: these objects can also be bound to the Gateway Virtual Server, which means they apply to all users that connect to that Gateway Virtual Server.
- If the user belongs to multiple AAA Groups, then policies are applied as follows:
- Session Policies – the settings are merged, unless there’s a conflict. If a conflict, then the policy with the lowest priority number wins.
- Bookmarks, Intranet Applications, and Authorization Policies are merged.
- Intranet IPs (IP Pool) are probably random allocation. It’s probably best to make sure a user only belongs to one AAA Group that assigns Intranet IPs.
- You can also create local AAA Groups that are unrelated to Active Directory groups. There are several ways of getting users into these local AAA groups:
- Create local AAA Users and assign them to the AAA Group
- Configure Session Policy/Profile with a Client Security Check String (EPA Scan). If the scan succeeds, users are placed into local Authorization AAA Groups. If the scan fails, then users are placed into a local Quarantine AAA Group, and removed from all other AAA Groups.
- When users are authenticated with a particular authentication server, the authentication server can be configured to place users into a Default Authentication Group. This lets you apply different Session Policy/Profiles (and other Gateway objects) depending on how the user authenticated.
Citrix Gateway supports Client Security Expressions (Endpoint Analysis expressions) at four different locations:
- nFactor (Authentication Virtual Server) Advanced EPA Policy and EPA Action – this is the preferred method in ADC 13 and newer since Classic EPA is supposed to be removed in ADC 13.1 and newer. See nFactor EPA for details.
- Classic Preauthentication Policy Expression
- If the EPA Scan succeeds, then the user is allowed to login.
- If the EPA Scan fails, then the user is not allowed to login.
- Preauthentication Policies are bound to Citrix Gateway Virtual Servers only, and thus applies to all users of that Virtual Server.
- Classic Session Policy Expression – Note: Advanced Session Policies do not support EPA expressions. Use nFactor instead.
- This type of EPA Scan is configured in the Session Policy Expression, not the Session Profile.
- If the EPA Scan succeeds, then the settings in the Session Profile are applied to the session.
- If the EPA Scan fails, then the Session Profile is ignored. Other Session Policies expressions are still evaluated. Remember, Session Policy/Profiles merge, so all applicable Session Policies must be considered.
- A limitation of this EPA method is that nothing negative happens. Instead, you typically design higher priority number (lower priority) Session Policies with restrictive settings so that if the EPA Scans fail, then users still get something. For example, you can configure your highest priority number Session Policy/Profile with StoreFront (ICA Proxy) only. In the lower priority number Session Policies/Profiles, VPN might be enabled, but only if the EPA scan succeeds. More restrictive Session Profiles usually uncheck Client Choices, and enable Clientless Access or ICA Proxy.
- This method of EPA Scans is used in SmartAccess and SmartControl configurations.
- EPA expressions are not supported in Default Syntax, so you’ll need to use Classic Syntax instead.
- Session Profile > Security tab > Advanced Settings > Client Security Check String
- If the EPA Scan succeeds, add the user to the listed Authorization AAA Groups.
- If the EPA Scan fails, add the user to the selected Quarantine Group, and remove the user from all other AAA Groups.
- If Quarantine Group is not defined, then prevent SSL VPN. Other methods of connecting (Clientless, StoreFront), still work.
- Assigning EPA scans to Session Policies and Session Profiles is also known as Post-Authentication EPA Scans.
- If Endpoint Analysis is configured anywhere, then an Endpoint Analysis plug-in is downloaded to the Windows or Mac client.
Prerequisites
Gateway Universal Licenses
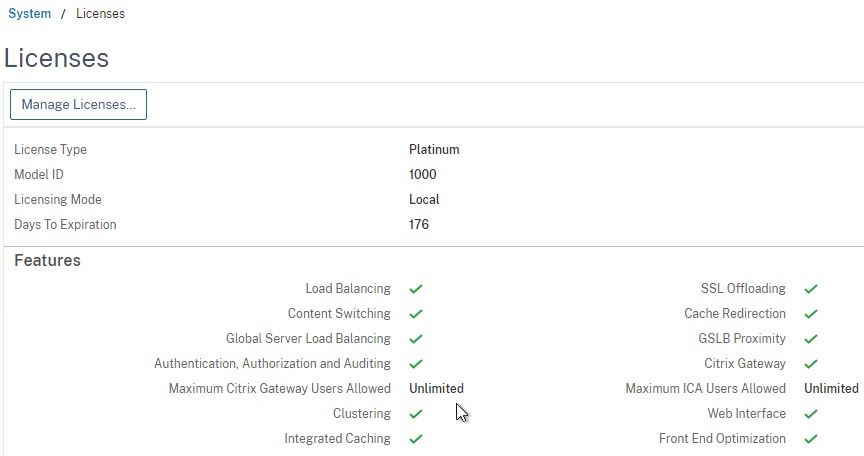
Except for ICA Proxy, all Citrix Gateway connection methods require a Citrix Gateway Universal License for each concurrent session. Go to System > Licenses.
On the right, make sure Maximum Citrix Gateway User licenses are installed. Most Citrix ADC Editions come with built-in licenses. For example, Citrix ADC Premium Edition comes with Unlimited Gateway licenses.
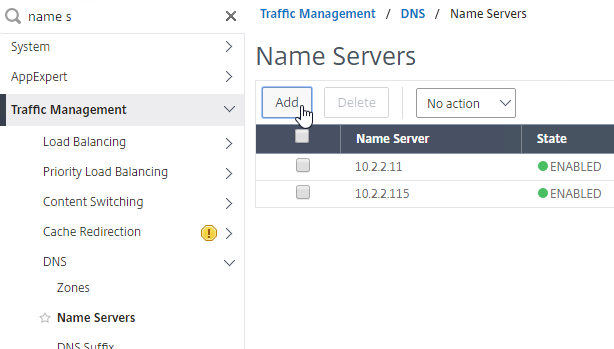
DNS Name Servers
DNS usually needs to function across the VPN tunnel. Go to Traffic Management > DNS > Name Servers to add DNS servers.
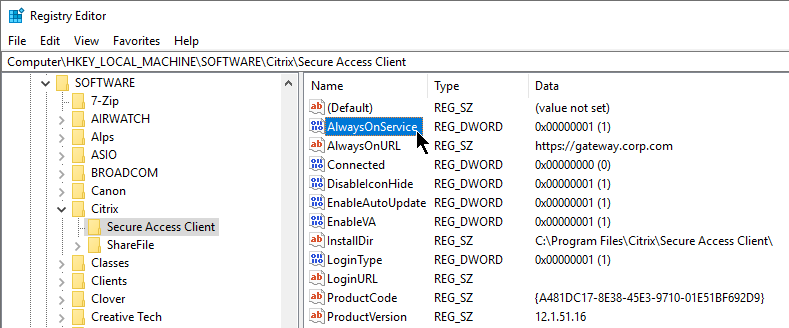
In ADC 13.0 build 71.44 and newer, VPN plug-in for Windows supports Secure DNS update. This feature is disabled by default. To enable it, create the following on the client device: (source = 13.0-71.44 release notes) 💡
- HKEY_LOCAL_MACHINE\SOFTWARE\Citrix\Secure Access Client\secureDNSUpdate value of type REG_DWORD and set it to 1.
- When you set the value to 1, the VPN plug-in tries the unsecure DNS update first. If the unsecure DNS update fails, the VPN plug-in tries the secure DNS update.
- To try only the secure DNS update, you can set the value to 2.
AAA Groups
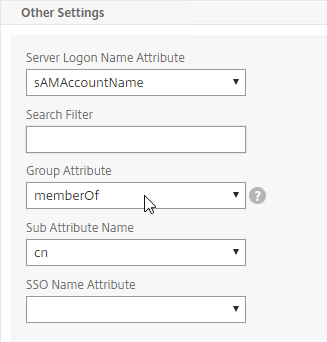
- Edit your LDAP Policy/Server, and make sure Group Extraction is configured. Configure the Group Attribute and the Sub Attribute Name. This causes Citrix ADC to extract the user’s AD groups when the user logs in using LDAP.
- Go to Citrix Gateway > User Administration > AAA Groups.
- On the right, click Add.
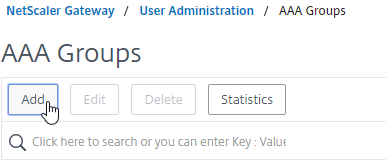
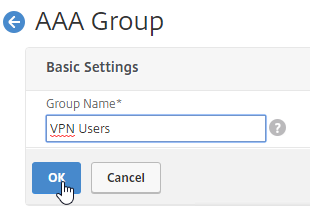
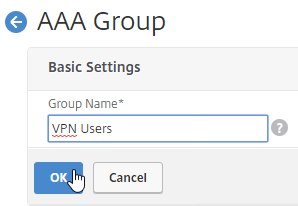
- Enter a case sensitive group name that matches the group name in Active Directory. Click OK.
- On the right, in the Advanced Settings column, you can see the types of objects that can be bound to AAA Groups. These objects are detailed later in this post.
Create Session Profile
To enable SSL VPN: first create the Session Profile. Then create a Session Policy.
You can create multiple Session Policies/Profiles with different settings. Then you can bind these Session Policies to AAA groups and/or Citrix Gateway Virtual Servers. The Session Profiles are merged, and if conflicts, lower priority bind points win.
To enable SSL VPN in a Session Profile:
- On the left, expand Citrix Gateway, expand Policies, and click Session.
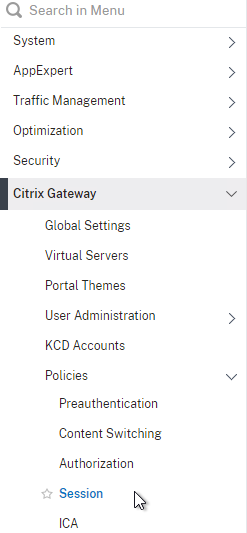
- On the right, switch to the Session Profiles tab, and click Add.
- Name the profile VPN or similar.
- In Session Profiles, every field has an Override Global checkbox to the right of it. If you check this box next to a particular field, then you can configure that field, and the field in this session profile will override settings configured globally (Citrix Gateway > Global Settings > Change Global Settings), or in a lower priority (higher priority number) session policy.
Network Configuration tab
- In the Session Profile, switch to the Network Configuration tab.
- You will find a setting that lets you select a DNS Virtual Server. Or if you don’t select anything, then the tunnel will use the DNS servers configured under Traffic Management > DNS > Name Servers.
Client Experience Tab
- In the Session Profile, switch to the Client Experience tab. This tab contains most of the Citrix Gateway VPN settings.
- Override Plug-in Type, and set it to Windows/Mac OS X.
- On the Client Experience tab, override Split Tunnel and make your choice. Setting it to OFF will force all traffic to use the tunnel. Setting it to ON will require you to create Intranet Applications so the Citrix Gateway Plug-in will know which traffic goes through the tunnel, and which traffic goes directly out the client NIC (e.g. to the Internet). REVERSE means all traffic goes through the tunnel except for the addresses defined in Intranet Applications.
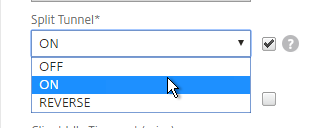
- On the Client Experience tab, there are timers that can be configured. Global Settings contains default timers, so you might want to configure this Session Profile to override the defaults and increase the timeouts. See Configuring Time-Out Settings at Citrix Docs for details.
- Client Idle Time-out is a Citrix Gateway Plug-in timer that disconnects the session if there is no user activity (mouse, keyboard) on the client machine.
- Session Time-out is a Citrix Gateway timer that disconnects the session if there is no network activity for this duration.
- In addition to these two timers, on the Network Configuration tab, under Advanced Settings…
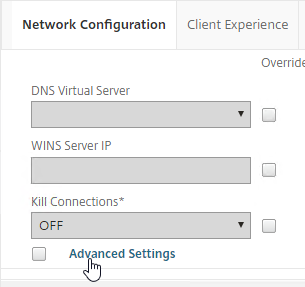
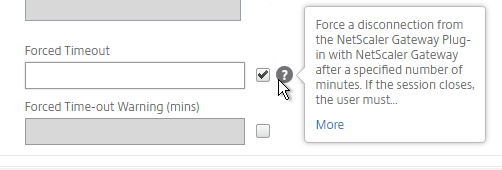
- There’s a Forced Timeout setting.
- By default, once the VPN tunnel is established, a portal page appears containing Gateway Bookmarks, and StoreFront published icons. An example of the portal page in the RfWebUI theme is shown below:
- The X1 theme is shown below:
- The X1 theme is shown below:
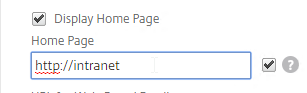
- On the Client Experience tab, the Home Page field lets you override the the default portal page, and instead display a different webpage (e.g. Intranet). This homepage is displayed after the VPN tunnel is established (or immediately if connecting using Clientless Access).
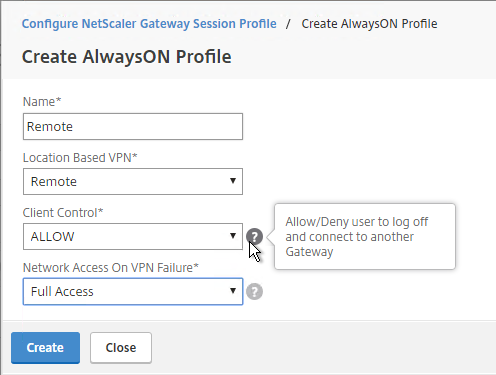
- Citrix Gateway can automatically start the VPN tunnel whenever the user is remote. This method only starts the VPN Tunnel after the user is logged into Windows.
- On the Client Experience tab, click the plus icon next to AlwaysON Profile Name.
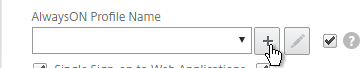
- Give the profile name. Hover over the question marks to see what each of them does.
- Then click Create.
- More info at AlwaysON at Citrix Docs.
- On the Client Experience tab, click the plus icon next to AlwaysON Profile Name.
- Citrix Gateway 12.1 build 51 and newer also support the VPN Client establishing a tunnel before the user logs into Windows. The pre-logon AlwaysOn Service feature requires certificate-based authentication and registry keys on the client device. See AlwaysOn service for Windows at Citrix Docs. 💡
- Additional VPN settings can be found by clicking Advanced Settings near the bottom of the Client Experience tab.
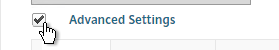
- Under Client Experience > Advanced Settings, on the General tab, there are settings to run a login script at login, enable/disable Split DNS, and enable Local LAN Access. Use the question marks to see what they do.
- Note: if Split Tunnel is OFF, and if Split DNS is set to REMOTE, Citrix Gateway only returns one IP address to DNS queries. This behavior can be changed by following Citrix CTX200243 DNS Query Responds with Only One IP to Client PC When Connected Through NetScaler Gateway Full VPN.
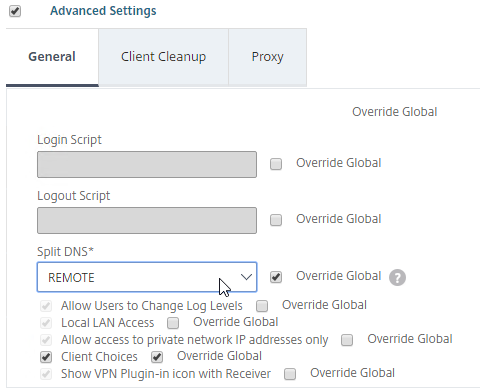
- Under Client Experience > Advanced Settings, on the General tab, is a checkbox for Client Choices. This lets the user decide if they want VPN, Clientless, or ICA Proxy (StoreFront). Without Client Choices, one of the connection methods will occur automatically, depending on what’s enabled.
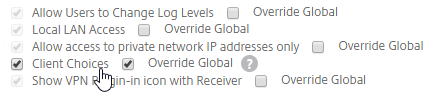
- An example of Client Choices is shown below:

- On the main Client Experience tab, if you enabled Client Choices, you can set Clientless Access to Off to add Clientless to the list of available connection methods in the Client Choices screen.
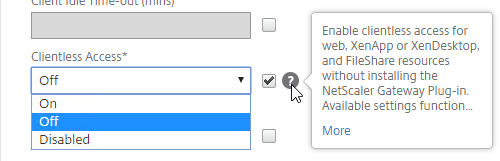
- Clientless Access is difficult to remove from the Client Choices page since you need Clientless Access for StoreFront integration. The following removal instructions were confirmed on a custom Portal Theme based on RfWebUI:
- WinSCP to the Citrix ADC.
- Navigate to
/var/netscaler/logon/themes/<yourThemeName>/css. - Edit the file theme.css.
- At the bottom of the file, add the following code: (source = CTP Sam Jacobs at NetScaler Gateway Client Choices – hide/remove Virtual Apps and Desktops at Citrix Discussions.
div.box:nth-child(2) { display:none; } - When you refresh the Client Choices page, the Clientless box should be hidden.
- On the main Client Experience tab, if you enabled Client Choices, you can set Clientless Access to Off to add Clientless to the list of available connection methods in the Client Choices screen.
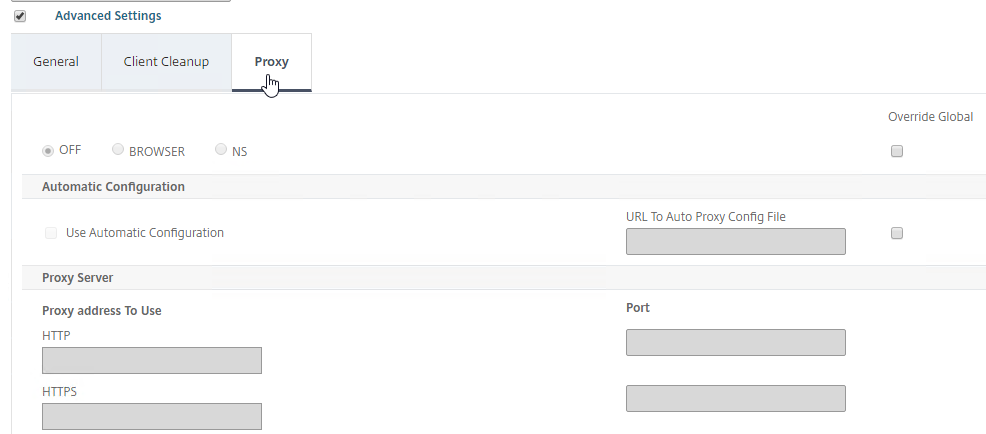
- The Client Experience > Advanced Settings section has additional tabs. A commonly configured tab is Proxy, which allows you to enable a proxy server for VPN users.
Security Tab
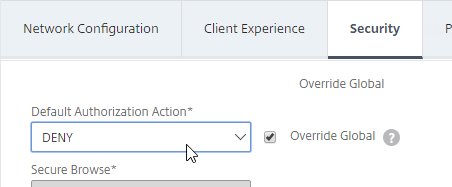
- Back in the main Session Profile, switch to the Security tab.
- Set the default authorization to Allow or Deny. If Deny (recommended), you will need to create authorization policies to allow traffic across the tunnel. You can later create different authorization policies for different groups of users.
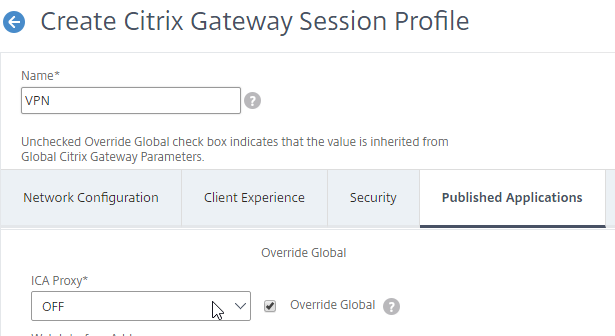
Published Applications Tab
- On the Published Applications tab, set ICA Proxy to Off. This ensures VPN is used instead of ICA Proxy.
- Configure the Web Interface Address to embed StoreFront into the default Clientless Access portal page.
- Note: for X1 theme, additional iFrame configuration is required on the StoreFront side as detailed below. RfWebUI theme does not need any StoreFront changes.
- From Michael Krasnove: if you configured the Session Policy to direct users to StoreFront, but aren’t using RfWebUI, then placing the following code in c:\inetpub\wwwroot\Citrix\StoreWeb\custom\script.js will cause StoreFront to end the VPN tunnel when the user logs off of StoreFront.
var LOGOFF_REDIRECT_URL = 'https://YourGatewayFQDN.com/cgi/logout'; // Prevent the default "logoff" screen from being displayed CTXS.Controllers.LogoffController.prototype._handleLogoffResult = $.noop; CTXS.Extensions.afterWebLogoffComplete = function () { window.location.href = LOGOFF_REDIRECT_URL; };
- See the ICA Proxy post for more information on integrating StoreFront with Citrix Gateway.
Other Tabs
- The Remote Desktop tab is detailed in the RDP Proxy post.
- The PCoIP tab is detailed in the PCoIP Proxy post.
- Click Create when you’re done creating the Session Profile.
Create Session Policy
Once the Session Profile is created, you need a Session Policy linked to it. The Session Policy contains an expression, where if true, then the Session Profile is applied.
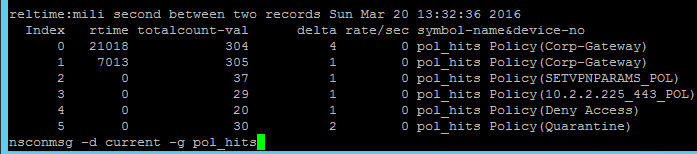
If multiple Session Policies apply to a particular connection, then the settings in the policies are merged. For conflicting settings, the Session Policy with the highest priority (lowest priority number) wins. Session Policies bound to AAA groups only override Session Policies bound to Citrix Gateway Virtual Servers if the AAA group bind point has a lower priority number. In other words, priority numbers are evaluated globally no matter where the Session Policy is bound. You can run the command nsconmsg –d current –g pol_hits to see which Session Policies are applying to a particular connection. See CTX214588 Understanding Session Policy Priority on Different Bind Points.
You can also include Endpoint Analysis expressions in a Session Policy, so that the Session Policy only applies to machines that pass the Endpoint Analysis scan. However, EPA Scans are only supported with Classic Syntax policy expressions, and not with Default Syntax.
To create a Session Policy that is linked to a Session Profile:
- On the left, go to Citrix Gateway > Policies > Session.
- In the right pane, switch to the Session Policies tab, and click Add.
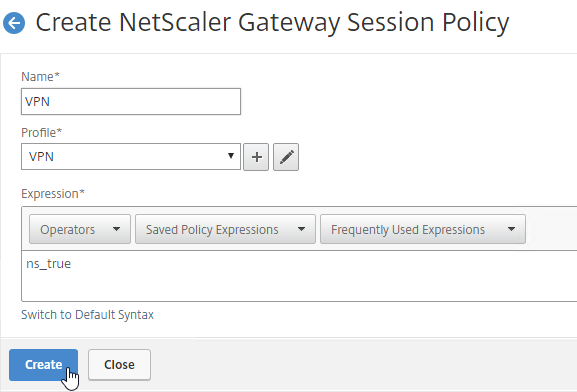
- Give the policy a descriptive name.
- Change the Profile drop-down to the VPN Profile you just created.
- The Expression box has an option for switching to Default Syntax.
- If Default Syntax, enter true in the Expression box so it always evaluates to true. If Classic Syntax, it would be ns_true instead of true.
- If Default Syntax, you can enter
HTTP.REQ.USER.IS_MEMBER_OF("MyADGroup")to restrict the Session Profile to members of a specific AD group. In Classic Syntax, this isn’t possible in an expression, and instead you must assign the Session Policy to a AAA Group.
- If Classic Syntax, you can add Endpoint Analysis scans to the Expression box. If the Endpoint Analysis scan succeeds, then the session policy is applied. If the Endpoint Analysis scan fails, then this session policy is skipped, and the next one is evaluated. This is how you can allow VPN if EPA scan succeeds, but all failed EPA scans will get a different session policy that only has ICA Proxy enabled.
- To add an Endpoint Analysis scan, use one of the Editor links on the right.
- Configure OPSWAT scans in the OPSWAT EPA Editor.
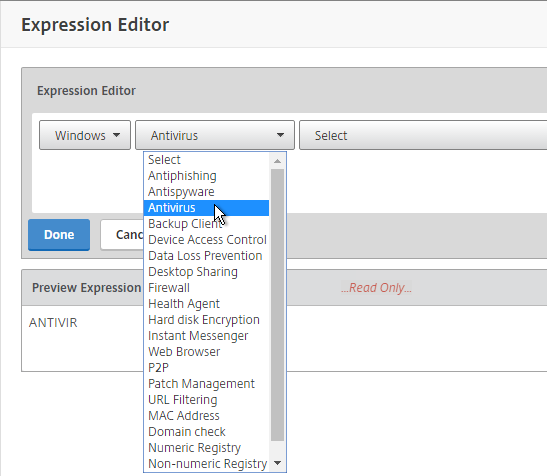
- Configure Client Security Expressions in the Expression Editor.
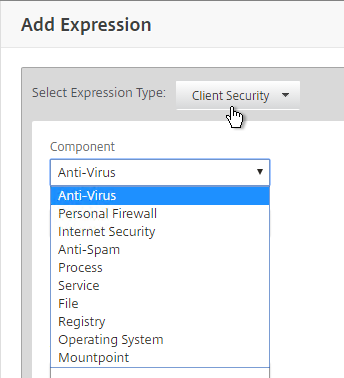
- You can combine multiple Endpoint Analysis scan expressions using Booleans (&&, ||, !).
- To add an Endpoint Analysis scan, use one of the Editor links on the right.
- Click Create when done.
Bind Session Policy
Most of the Citrix Gateway configuration objects can be bound to a Citrix Gateway Virtual Server, AAA Groups, or both. This section details binding of Session Policies, but the other Citrix Gateway objects (e.g. Authorization Policies) can be bound using similar instructions.
- Objects bound directly to the Citrix Gateway Virtual Server are evaluated for every user of that Gateway Virtual Server.
- Objects bound to a AAA Group are only evaluated for members of that AAA Group.
- Polices bound to AAA Groups usually have lower priority numbers than policies bound to Gateway Virtual Servers, so the AAA binding can override the Gateway binding.
- However, objects/policies bound to a AAA Group are applied to every Gateway Virtual Server on the same appliance. To override AAA bindings at a specific Gateway, you can bind lower priority number policies to the Gateway Virtual Server.
Bind the new Session Policy to a Citrix Gateway Virtual Server, or a AAA group.
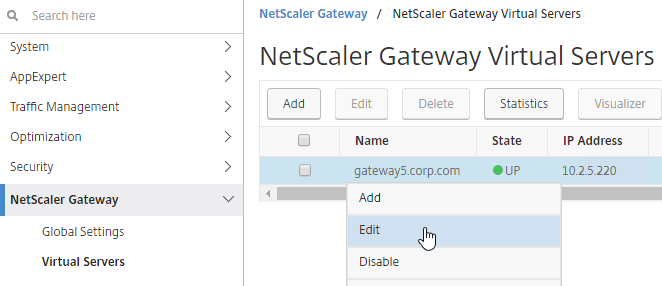
To bind to a Citrix Gateway Virtual Server
- Edit a Citrix Gateway Virtual Server (or create a new one).
- To make sure ICA Only is unchecked:
- Click the pencil icon for the Basic Settings section.
- Click More.
- Make sure ICA Only is unchecked, and click OK to close the Basic Settings section.
- Note: with this box unchecked, Gateway Universal licenses are now required for all users connecting through this Gateway Virtual Server.
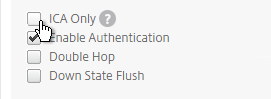
- Click the pencil icon for the Basic Settings section.
- While editing the Gateway Virtual Server, consider changing the Portal Theme to RfWebUI. This changes the default portal page to look identical to StoreFront.
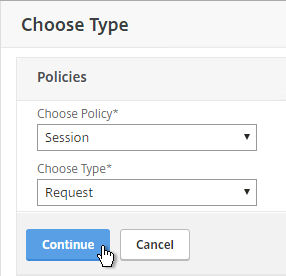
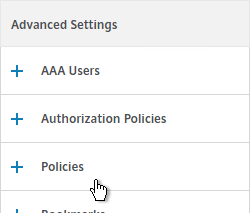
- Scroll down to the Policies section, and click the Plus icon.

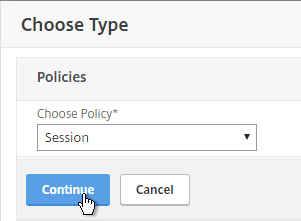
- In the Choose Type page, ensure the Choose Policy drop-down is set to Session.
- Ensure the Choose Type drop-down is set to Request, and click Continue.
- Click where it says Click to select.
- If you already have Session Policies bound to this Gateway Virtual Server, then you might have to click Add Binding first.
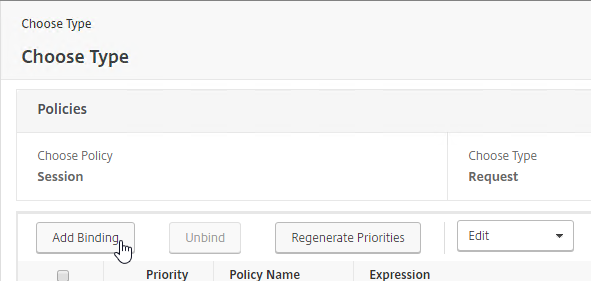
- If you already have Session Policies bound to this Gateway Virtual Server, then you might have to click Add Binding first.
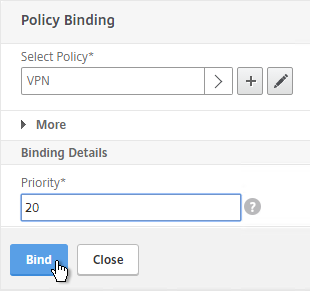
- Click the radio button next to the previously created Session Policy, and click Select.
- Note: you cannot mix Classic Syntax Policies and Default Syntax Policies.
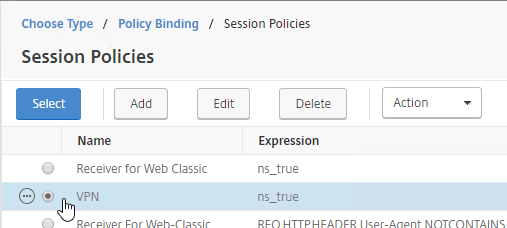
- In the Priority field, adjust the priority number. If you want this Session Policy to override other Session Policies, then set the priority number to a low value. See CTX214588 Understanding Session Policy Priority on Different Bind Points.
- Click Bind.
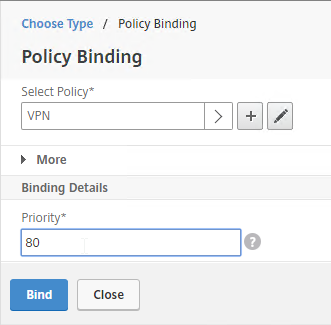
- If you already have Session Policies bound to the Gateway Virtual Server, then the list of Policies is displayed. If you don’t see this list, on the left, in the Policies section, click the line that says Session Policies.
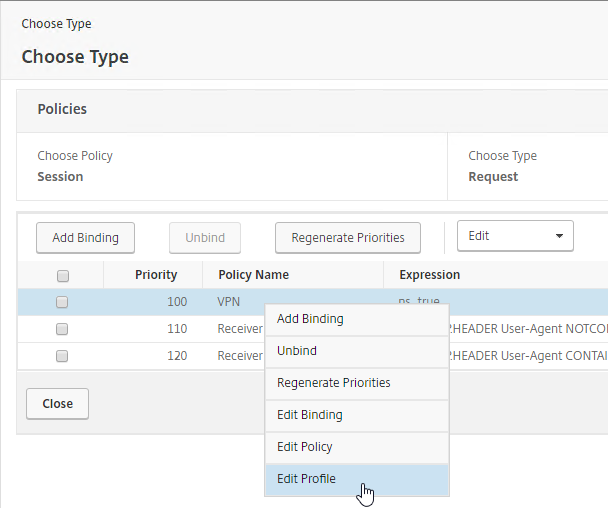
- From this list, you can right-click the policies to Edit Binding (priority number), or Edit Profile.
- If your Citrix Gateway Virtual Server is configured with a Traffic Policy for Native OTP (One Time Passwords), change the Traffic Policy expression to the following. Source = Julien Mooren at NetScaler – Native OTP is breaking SSL VPN.
http.req.method.eq(post)||http.req.method.eq(get) && false
Bind to AAA Group
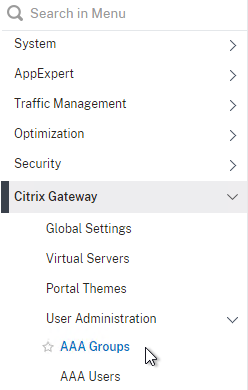
- To bind to a AAA Group, go to Citrix Gateway > User Administration > AAA Groups.
- On the right, add a AAA group with the same name (case sensitive) as the Active Directory group name. This assumes your LDAP policies/server are configured for group extraction (Group Attribute, and Sub Attribute).
- Edit the AAA Group.
- On the right, in the Advanced Settings column, add the Policies section.
- Click the plus icon to bind one or more Session Policies.
- If you want these Session Policies to override the Session Policies bound to the Citrix Gateway Virtual Server, then make sure the Session Policies bound to the AAA Group have lower priority numbers. See CTX214588 Understanding Session Policy Priority on Different Bind Points.

- If a user belongs to multiple groups, then for Advanced Session Policies, see CTX289931 AAA group session policies are not applying based on priority. Classic Policies in multiple AAA Groups are lumped together and evaluated based on bind point priority number. Advanced Policies are no longer lumped together and instead each AAA Group is evaluated separately. The first AAA Group created has higher priority than later created AAA Groups unless you specify the weight when creating the AAA Group from the CLI. 💡
Citrix Gateway Plug-in
Upgrade Citrix Gateway Plug-in
Citrix ADC pushes the Gateway Plug-in (aka VPN client) to client machines. In newer builds of Citrix ADC 13.0, you can upgrade the VPN plugin on the ADC without upgrading the ADC firmware.
- Download the latest plugin .tgz file from https://www.citrix.com/downloads/citrix-gateway/plug-ins/citrix-gateway-windows-plug-in-clients.html.
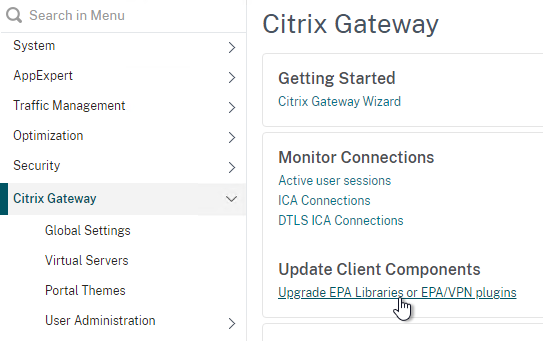
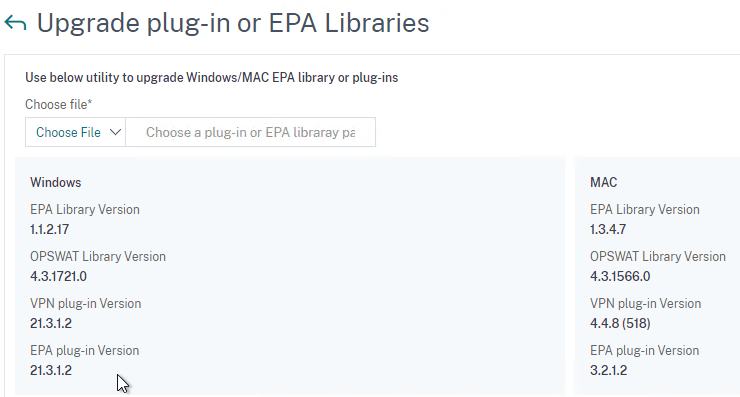
- In Citrix ADC, on the left click the Citrix Gateway node. On the right, click Upgrade EPA Libraries or EPA/VPN plugins.
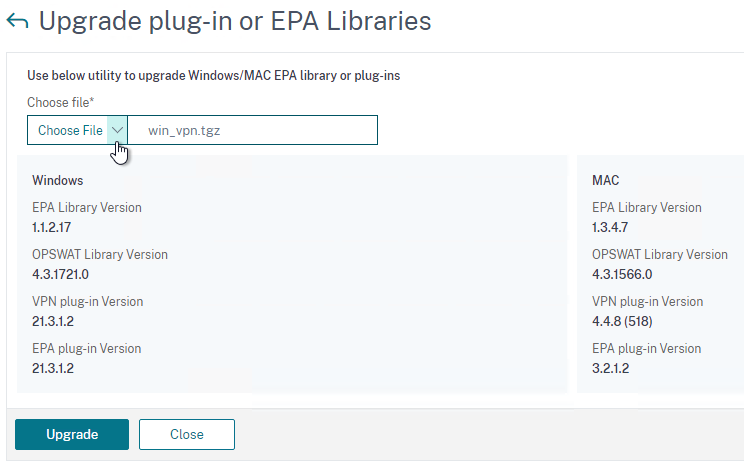
- This page shows you the versions of the currently installed plugins.
- Click Choose File and select the win_vpn.tgz file. Click Upgrade.
- Click OK when prompted that the upgrade completed successfully.
- Go back to the Upgrade plug-in or EPA Libraries page to see the new versions.
Citrix Gateway Plug-in Installation
Here is what the user sees when launching the VPN session for the first time. This assumes the user is an administrator of the local machine.
- Wait for 10 seconds for the webpage to not detect Gateway Plug-in, and then click the Download button.
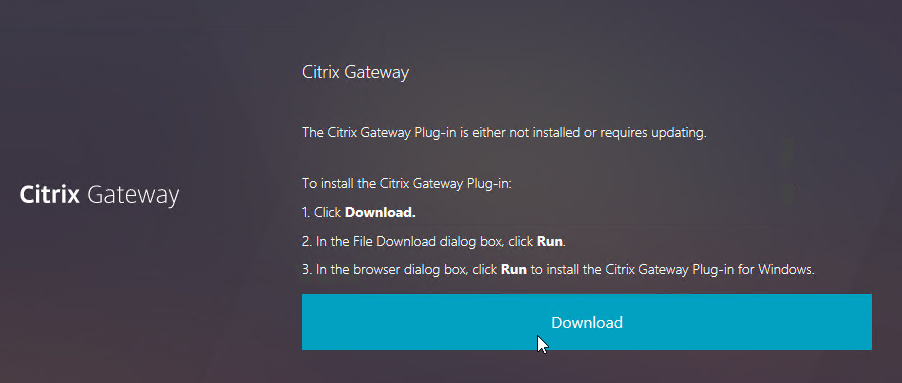
- Run the downloaded AGEE_setup.exe.
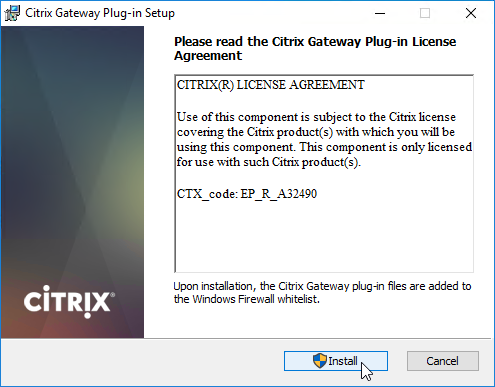
- In the Please read the Citrix Gateway Plug-in License Agreement page, click Install.
- In the Complete the Citrix Gateway Plug-in Setup Wizard page, click Finish.
- Click Yes to restart your system.
- In ADC 13.0 build 71.44 and newer, VPN plug-in for Windows supports Secure DNS update. This feature is disabled by default. To enable it, create the following on the client device: (source = 13.0-71.44 release notes) 💡
- HKEY_LOCAL_MACHINE\SOFTWARE\Citrix\Secure Access Client\secureDNSUpdate value of type REG_DWORD and set it to 1.
- When you set the value to 1, the VPN plug-in tries the unsecure DNS update first. If the unsecure DNS update fails, the VPN plug-in tries the secure DNS update.
- To try only the secure DNS update, you can set the value to 2.
- HKEY_LOCAL_MACHINE\SOFTWARE\Citrix\Secure Access Client\secureDNSUpdate value of type REG_DWORD and set it to 1.
Only administrators can install the Citrix Gateway Plug-in. You can download the Gateway plug-in from the NetScaler appliance at /var/netscaler/gui/vpns/scripts/vista and push it to corporate-managed machines. Or you can download VPN clients from Citrix.com. The VPN client version must match the Citrix ADC firmware version.
To deploy the Gateway Plug-in using Group Policy, see CTX124649 How to Deploy NetScaler Gateway Plug-in and Endpoint Analysis Installer Packages for Windows by Using Active Directory Group Policy.
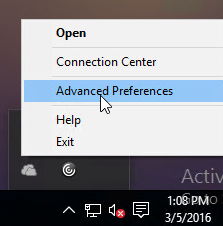
While a VPN tunnel is established, you can open the Gateway Plug-in to see status. If the Gateway Plug-in is merged with Workspace app, right-click Workspace app, click Advanced Preferences, click Citrix Gateway Settings, and click Open.
Or, if the Gateway Plug-in icon is separated from Workspace app, then right-click the Gateway Plug-in icon, and click Open.
The hamburger menu on the left lets you see more info about the VPN tunnel.
If the Gateway VPN session isn’t established, you can open the Gateway plug-in, and login. No browser needed.
- Gateway Plug-in 12.1 build 49 with Citrix ADC 12 build 49 support nFactor authentication (e.g. Native OTP) in the Gateway Plug-in. Older versions do not support nFactor. 💡
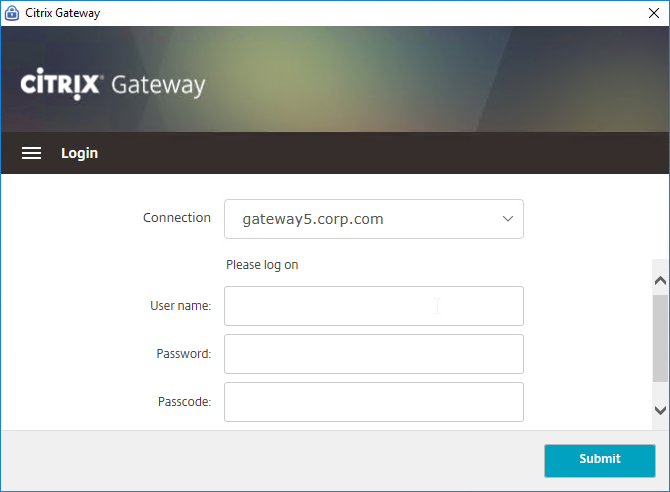
The Configuration page lets you enable Logging. Then the Logging page lets you collect the logs. See Citrix CTX138155 How to Collect Client VPN Logs for NetScaler Gateway.
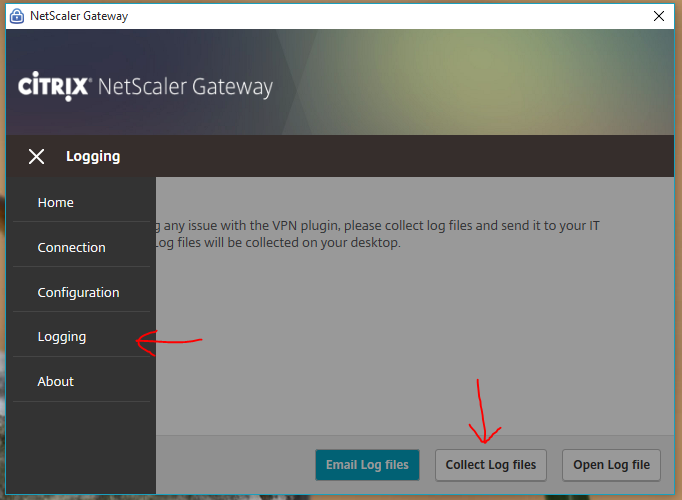
VPN Client (Citrix Gateway Plug-in) Session Profile Settings
Separate Icons for Workspace app and Gateway
- By default, if Workspace app, and Citrix Gateway Plug-in, are installed on the same machine, then the icons are merged. To see the Citrix Gateway Plug-in Settings, you right-click Workspace app, open Advanced Preferences, and then click Citrix Gateway Settings. This makes it difficult to log off.
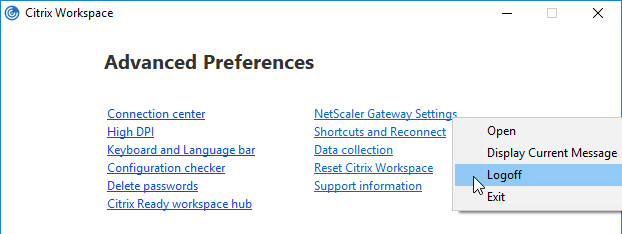
- You can configure the Session Profile to prevent the Citrix Gateway Plug-in from merging with Workspace app. Edit your VPN Session Policy/Profile. On the Client Experience tab…
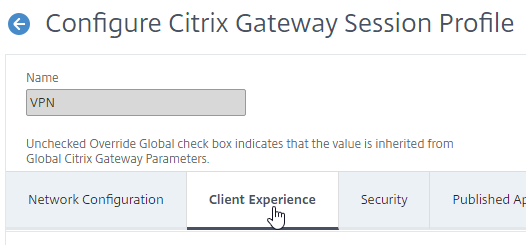
- Scroll down, and check the box next to Advanced Settings.

- At the bottom of the General tab, check the box next to Show VPN Plugin-in icon with Receiver.
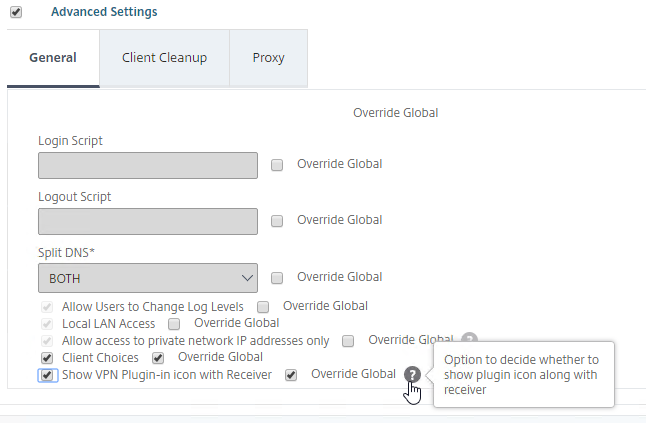
- This setting causes the two icons to be displayed separately thus making it easier to access the Citrix Gateway Plug-in settings, including Logoff.
Cleanup
- When the user logs off of VPN, a Cleanup page is displayed. This can be enabled or disabled in a Session Profile on the Client Experience tab.
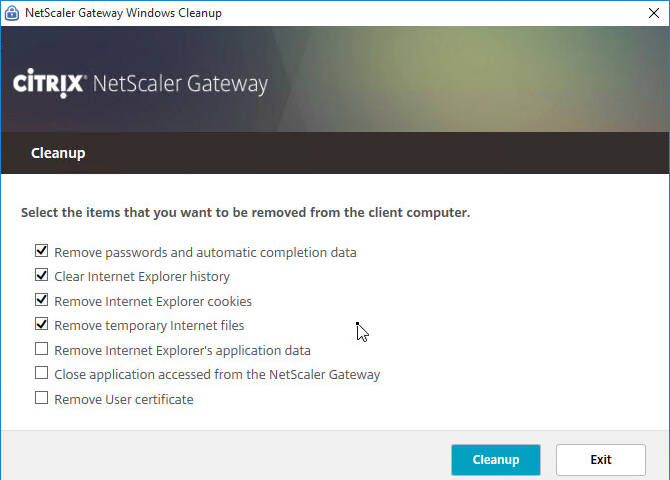
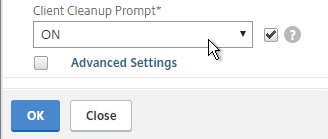
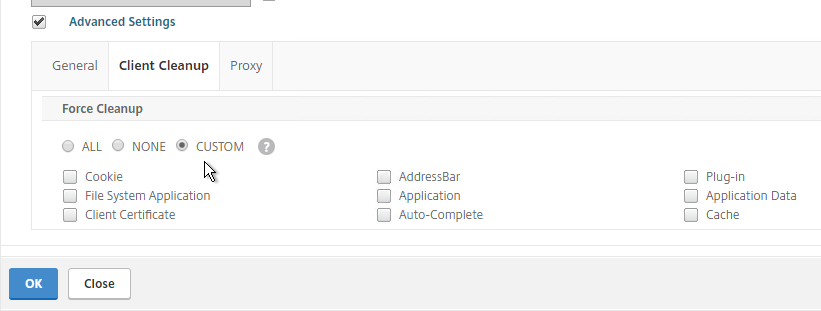
- The cleanup options can be forced in a Session Profile on the Client Experience tab…
- Under Advanced Settings > Client Cleanup.
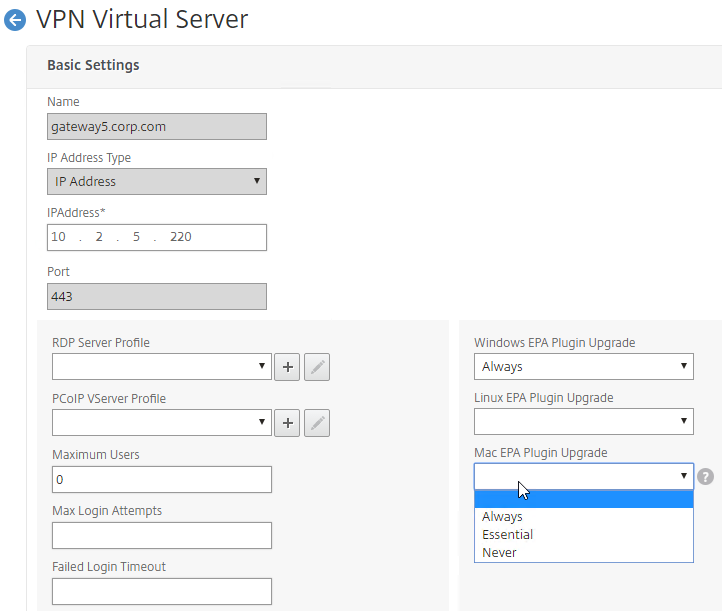
VPN Client Upgrades
- Whenever Citrix ADC firmware is upgraded, all users will be prompted to upgrade their VPN clients. You can edit a Session Policy/Profile, and on the Client Experience tab…
- Use the Upgrade drop-downs to disable the automatic upgrade.
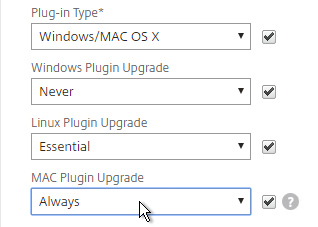
- The Plugin Upgrade settings are also configurable in the Gateway Virtual Server…
- In the Basic Settings > More section.
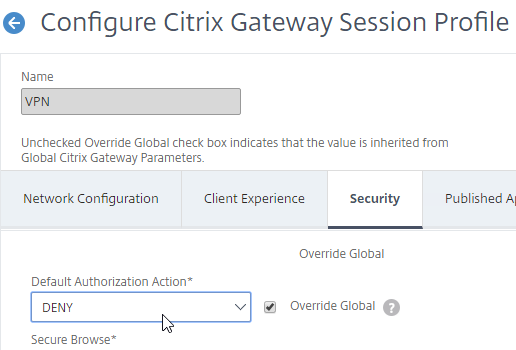
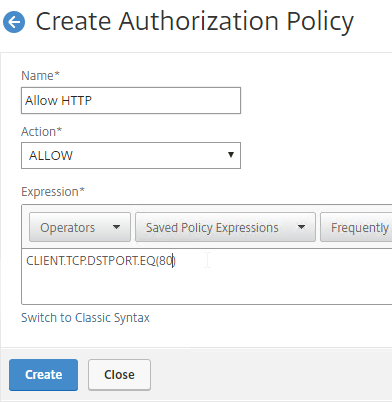
Authorization Policies
If your Session Profile has Security tab > Default Authorization Action set to Deny (recommended), then create Authorization Policies to allow access across the tunnel.
- On the left, under Citrix Gateway, expand Policies, and click Authorization.
- On the right, click Add.
- Name the Authorization Policy.
- Select Allow or Deny.
- For the Expression, Citrix Gateway supports both Classic Syntax and Default Syntax.
- Default Syntax gives you much greater flexibility in matching the traffic that should be allowed or denied. Hit Control+Space on your keyboard to begin building a Default Syntax expression. You typically want to identify traffic based on Destination IP Address, Destination Port Number, HTTP Request URL, HTTP Host Header, etc. Common expressions include:
CLIENT.IP.DST.IN_SUBNET()CLIENT.TCP.DSTPORT.EQ()- You can also use
HTTP.REQ.USER.IS_MEMBER_OF("MyADGroup")in your expressions.
- CTX232237 NetScaler Unified Gateway Advanced Authorization Policy Support for UDP/ICMP/DNS Traffic explains new types of Authorization Policies in NetScaler 12.0 build 56 and newer.
CLIENT.UDP.DSTPORT.EQ(2080)CLIENT.IP.PROTOCOL.EQ(ICMP)CLIENT.UDP.DNS.DOMAIN.CONTAINS("citrix")
- Note: you cannot mix both Classic Syntax and Default Syntax. You must unbind every Classic Syntax Authorization Policy before you can bind Default Syntax Authorization Policies.
- Default Syntax gives you much greater flexibility in matching the traffic that should be allowed or denied. Hit Control+Space on your keyboard to begin building a Default Syntax expression. You typically want to identify traffic based on Destination IP Address, Destination Port Number, HTTP Request URL, HTTP Host Header, etc. Common expressions include:
- Click Create when done.
- Authorization Policies are usually bound to AAA groups. This allows different groups to have different access across the tunnel.
- Or, you can use
HTTP.REQ.USER.IS_MEMBER_OF("MyADGroup")in your Default Syntax expressions.
- Or, you can use
- Edit a AAA Group at Citrix Gateway > User Administration > AAA Groups.
- On the right, in the Advanced Settings column, add the Authorization Policies section.
- Then click where it says No Authorization Policy to bind policies.
- CTX232237 NetScaler Unified Gateway Advanced Authorization Policy Support for UDP/ICMP/DNS Traffic explains new types of Authorization Policies in NetScaler 12.0 build 56 and newer.
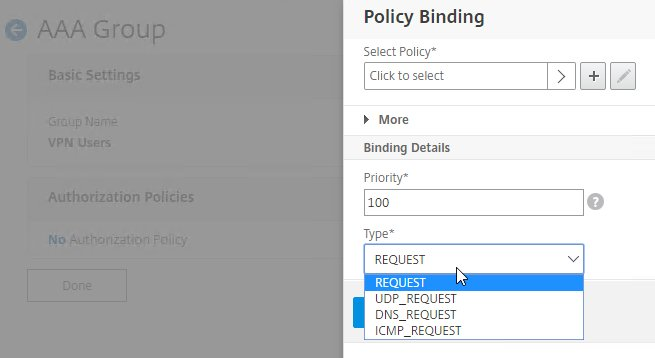
- CTX232237 NetScaler Unified Gateway Advanced Authorization Policy Support for UDP/ICMP/DNS Traffic explains new types of Authorization Policies in NetScaler 12.0 build 56 and newer.
Intranet Applications
If you enabled Split Tunnel, then you’ll need to create Intranet Applications to specify which traffic goes through the tunnel.
- On the left, under Citrix Gateway, expand Resources, and click Intranet Applications.
- On the right, click Add.
- Enter a name for the Internal subnet.
- Change the Interception Mode to TRANSPARENT.
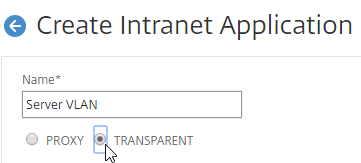
- Enter an IP subnet. Only packets destined for this network go across the tunnel.
- You typically specify a summary address for all internal subnets (e.g. 10.0.0.0/8).
- Alternatively, you can define minimal Intranet Application destinations as a security mechanism (assuming Split Tunnel is enabled), but Authorization Policies are more appropriate for that task.
- Click Create.
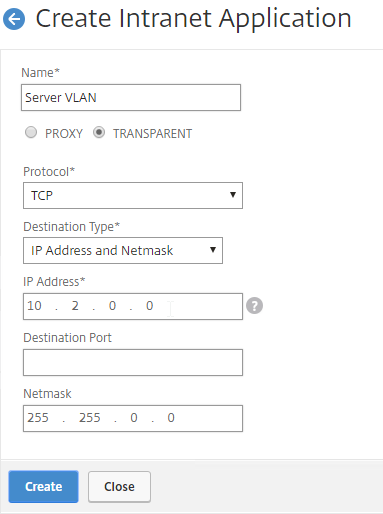
- Create additional Intranet applications for each internal subnet.
- Intranet Applications are usually bound to the Gateway Virtual Server, but you can also bind them to AAA Groups.
- On the right, in the Advanced Settings column, add the Intranet Applications section.
- On the left, click No Intranet Application to bind Intranet Applications.
DNS Suffix
Specify a DNS Suffix for Split DNS to function with single label DNS names. Citrix Gateway adds these DNS suffixes to DNS queries across the VPN tunnel.
- On the left, under Citrix Gateway, expand Resources, and click DNS Suffix.
- On the right, click Add.
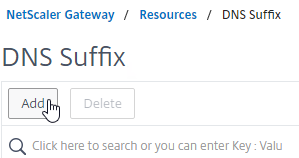
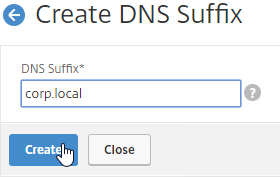
- Enter the DNS Suffix, and click Create. You can add multiple suffixes.
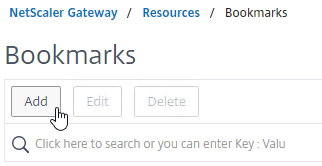
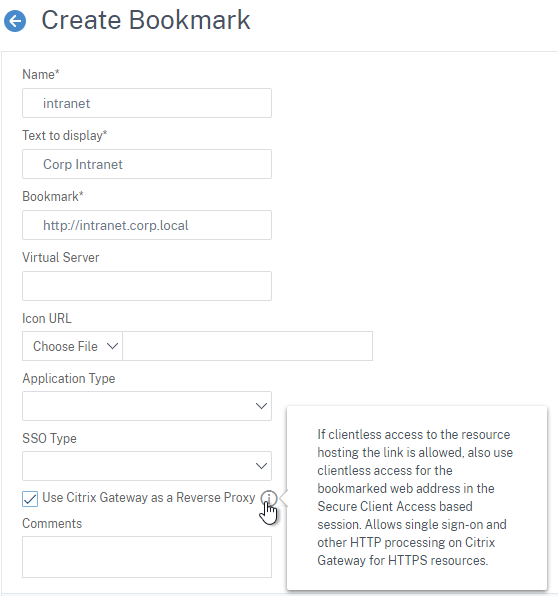
Bookmarks
Bookmarks are the links that are displayed in the default portal interface. They can point to websites, or RDP addresses. PCoIP bookmarks come from VMware Horizon Connection Server. ICA bookmarks come from Citrix StoreFront.
- Under Citrix Gateway, expand Resources, and click Bookmarks.
- On the right, click Add.
- Give the bookmark a name, and display text.
- Enter a website or RDP address.
- Optionally browse to an Icon file.
- You typically need to check Use Citrix Gateway As a Reverse Proxy, especially for Clientless Access (rewrite without VPN) to an internal website.
- The other fields are for Single Sign-on through Unified Gateway.
- Click Create.
- Bookmarks (aka Published Applications > Url) are usually bound to AAA groups so different groups can have different bookmarks. But it’s also possible to bind Bookmarks to Citrix Gateway Virtual Servers.
- If Citrix Gateway Virtual Server, add the Published Applications section to bind Bookmarks (Url).

- For AAA Group, it’s the Bookmarks section.
- On the left, find the Published Applications section, and click No Url to bind Bookmarks.
VPN Client IP Pools (Intranet IPs)
By default, Citrix Gateway VPN clients use Citrix ADC SNIP as their source IP when communicating with internal resources. To support IP Phones or endpoint management, you must instead assign IP addresses to VPN clients.
Any IP pool you add to Citrix Gateway must be reachable from the internal network. Configure a static route on the upstream router. The reply traffic to VPN Client IPs should be routed through a Citrix ADC SNIP. Or the Citrix ADC can participate in OSPF.
When a client is assigned a client IP, this IP address persists across multiple sessions until the appliance reboots, or until the appliance runs out of IPs in the pool.
- Edit a Citrix Gateway Virtual Server, or a AAA group.
- On the right, in the Advanced Settings section, click the plus icon next to Intranet IP Addresses.
- On the left, click where it says No Intranet IP.
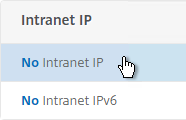
- Enter a subnet and netmask. Click Bind.
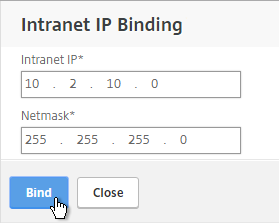
- In a Session Profile, on the Network Configuration tab, check the box next to Advanced Settings.
- Use the Intranet IP drop-down to configure the behavior when there are more VPN clients than available IPs in the address pool.
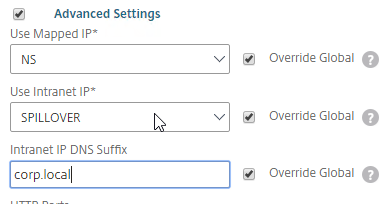
- If you set it to NOSPILLOVER, then users can only have one VPN session, as described in CTX218066 How to Limit One Session Per User on NetScaler Gateway?.
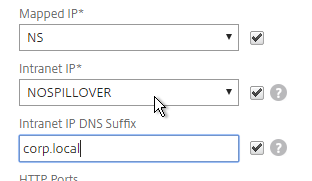
- If you set it to NOSPILLOVER, then users can only have one VPN session, as described in CTX218066 How to Limit One Session Per User on NetScaler Gateway?.
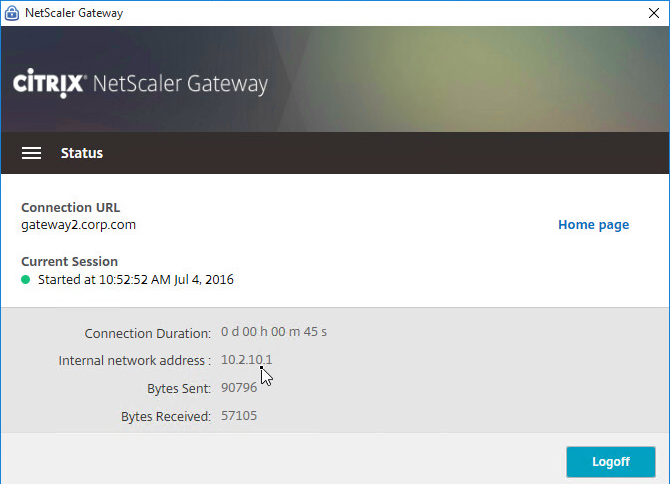
- To see the Client IP address, on the client side, after the tunnel is established, right-click the Citrix Gateway Plug-in, and click Open.
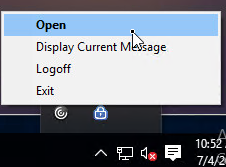
- See the Internal network address.
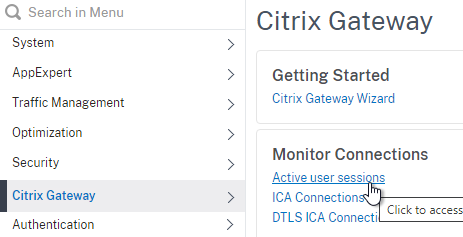
- To see the client IP on the Citrix ADC, go to Citrix Gateway, and on the right is Active user sessions.
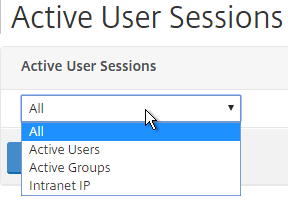
- Select one of the views, and click Continue.
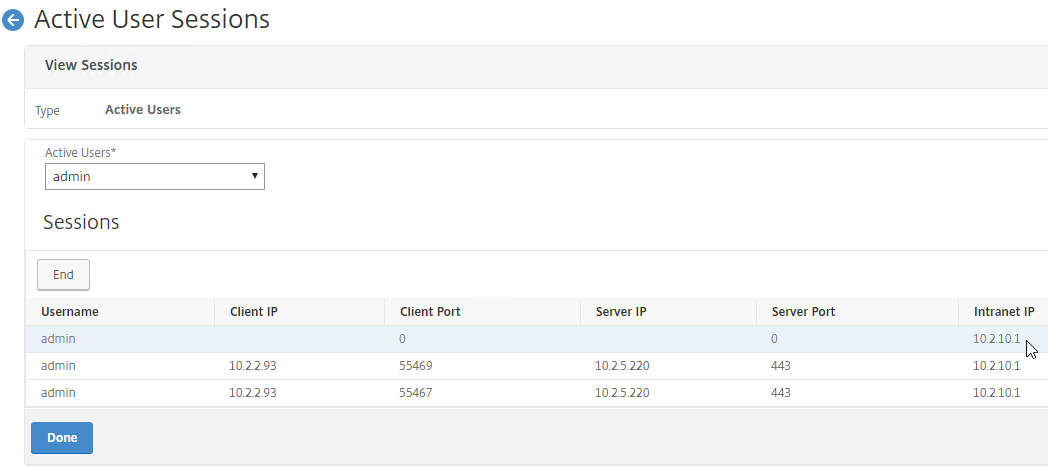
- The right column contains the Intranet IP.
StoreFront in Gateway Clientless Access Portal
If you enabled the RfWebUI theme, then no StoreFront configuration is necessary.
But if you want to embed StoreFront in the other Gateway themes (X1, Default, Green Bubble), then follow these instructions.
- On StoreFront, edit the file C:\Inetpub\wwwroot\Citrix\StoreWeb\web.config.
- On the bottom, there are three sections containing X-Frame-Options. Change all three of them from deny to allow.
- Also change frame-ancestors from none to self.
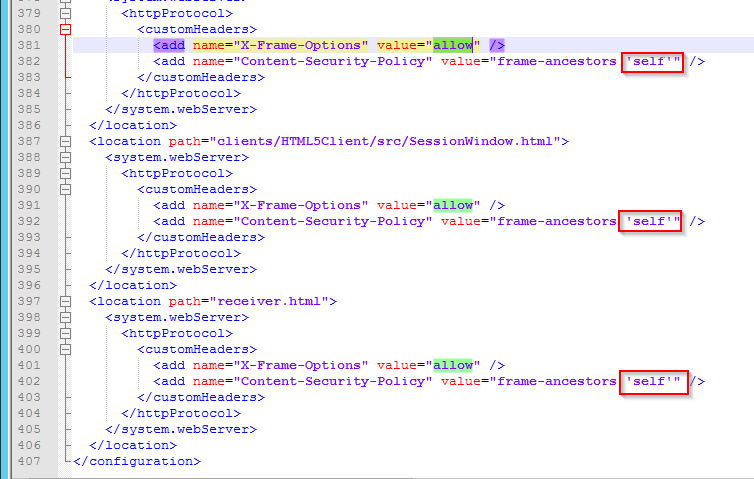
- In Citrix ADC, go to Citrix Gateway > Global Settings, and click Configure Domains for Clientless Access.
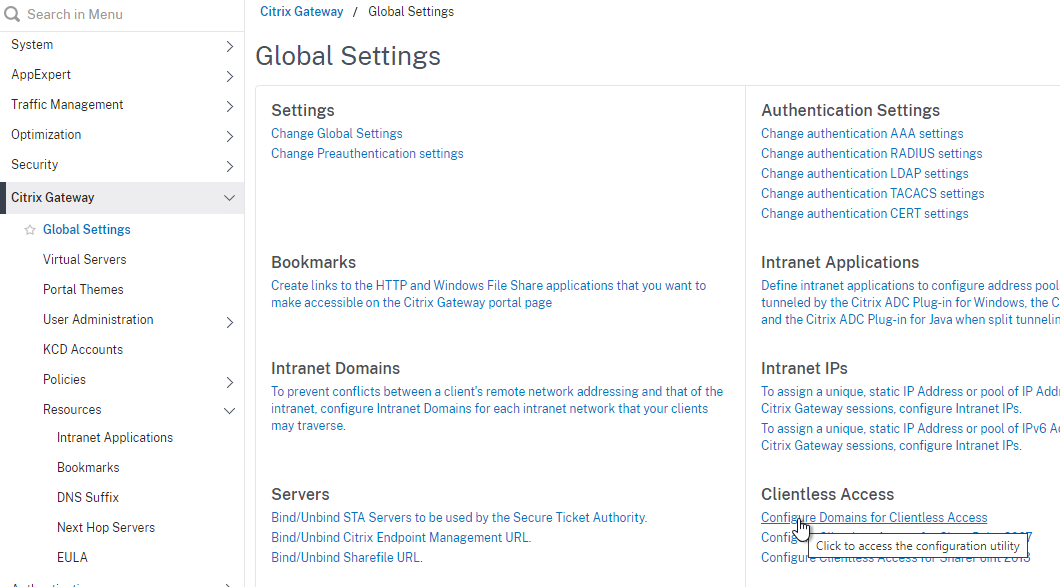
- Change the selection to Allow Domains, enter your StoreFront FQDN, and click the plus icon.
- Click OK.
- In a Session Policy/Profile:
- On the Client Experience tab, make sure Single Sign-on to Web Applications is enabled.
- On the Published Applications tab, configure the Web Interface Address to point to the StoreFront Receiver for Web page.
- Configure the Single Sign-on domain to match what’s configured in StoreFront.
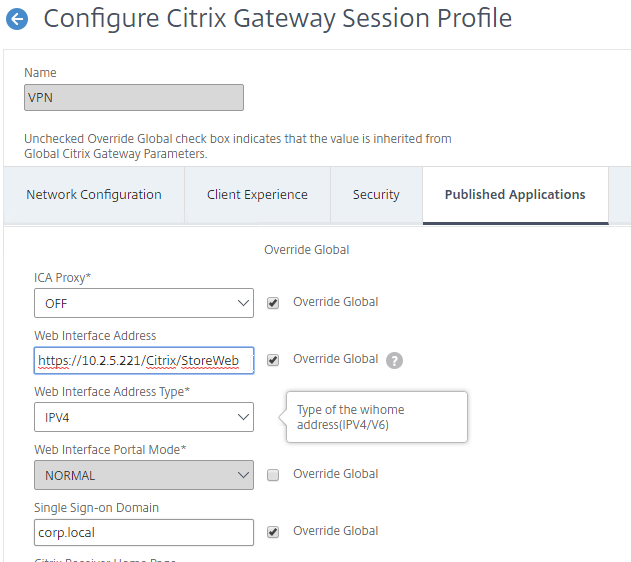
- You might have to override the Web Interface Portal Mode.
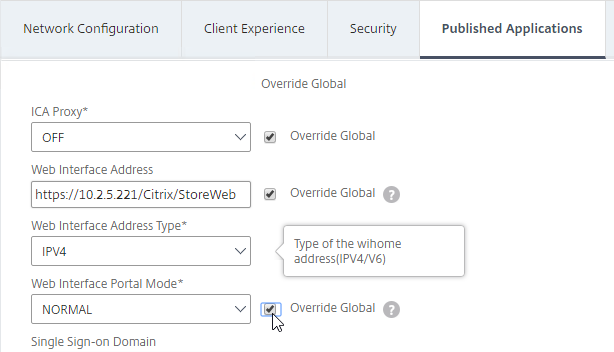
- On the Client Experience tab, make sure Single Sign-on to Web Applications is enabled.
- The Applications page of the 3-page portal (e.g. X1 theme) should automatically show the StoreFront published icons.
Quarantine Group
Citrix Gateway can be configured so that if Endpoint Analysis scans fail, then the user is placed into a Quarantine Group. You can bind session policies, authorization policies, etc. to this quarantine group. Policies bound to other AAA groups are ignored.
- Go to Citrix Gateway > User Administration > AAA Groups.
- Add a new local group for your Quarantined Users. This group is local, and does not need to exist in Active Directory.
- Bind session policies, authorization policies, etc. to your quarantine AAA group. These policies typically allow limited access to the internal network so users can remediate. Or, it might simply display a webpage telling users how to become compliant.
- The Session Policy bound to the Quarantine Group is usually different than the Session Policies bound to other AAA groups. You can use the variation in Session Policy names for SmartAccess.
- One option is to configure the Delivery Groups > Access Policy so that icons are shown for Session Policies bound to non-quarantine AAA Groups, but not for the Session Policy that is bound to the Quarantine Group.
- Another option is to configure Citrix Policies > Access Control to disable functionality for the Quarantine Group Session Policy, but not for other AAA Group Session Policies.
- Add a new local group for your Quarantined Users. This group is local, and does not need to exist in Active Directory.
- Create or edit a Session Profile to include a Client Security Expression that checks for compliance.
- In the Session Profile, on the Security tab, check the box next to Advanced Settings.
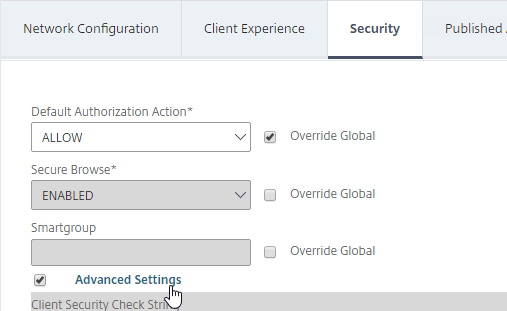
- Scroll down, and check the box to the right of Client Security Check String.
- Use the Editor links to add an Endpoint Analysis expression.
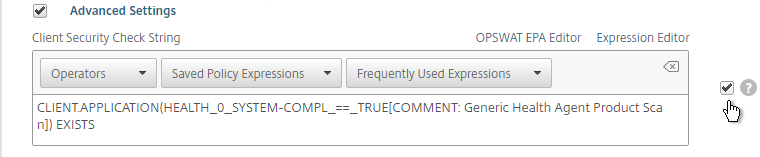
- Just below the Client Security Check String, select the previously created Quarantine Group. If the Client Security Check String EPA Scan fails, then the failed users are added to the Quarantine Group and removed from all other AAA Groups.
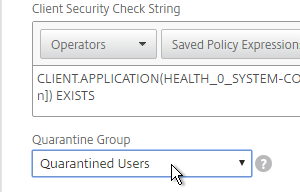
- In the Session Profile, on the Security tab, check the box next to Advanced Settings.
- Click Create when done creating or editing the Session Profile.
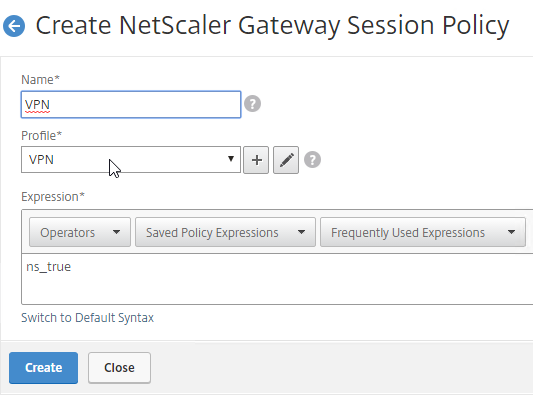
- Create a Session Policy for the Session Profile that contains the Client Security Check String.
- Enter ns_true as the expression.
- Then click Create.
- Edit your Gateway Virtual Server, and bind the Session Policy/Profile that has the Client Security Check String configured.

- To troubleshoot Quarantine policies, use the command
nsconmsg –d current –g pol_hits.
- Citrix ADM Gateway Insight shows users that failed EPA scans, and their quarantine status.
Carl – Im using a ADC 13 sslvpn with a couple hundred users. Security really wants to disable split tunneling. When I do, our TCP connection count climbs to about 7000 and plateaus and the VPN is completely non-functional at that point for everyone.
Citrix has recommended we play around with tcp buffer size.
Any tips for what tcp profile settings we might look at for good cpn performance for a large number of users. I see various tips from different places but nothing that sounds tried and true.
Implement reverse split tunnel for Microsoft 365.
Here are Citrix’s recommendations – https://support.citrix.com/article/CTX232321/recommended-tcp-profile-settings-for-full-tunnel-vpnicaproxy-from-netscaler-gateway-111-onwards
If anyone is currently using the Secure Access Client plugin for Windows versions >21.x.x.x and if you installed it with the WFP option (instead of default DNE) you need to be aware that there is a significant bug with that combination.
Here’s my story so far:
I opened a case back on the second week of August this year regarding this issue that was discovered during pre-production testing. As usual, support is dragging and it has been escalated to Engineering a little over a week ago, and now it has been finally admitted that there is a “bug” with what I would assume pretty much any version of Citrix Secure Access plug-in for Windows when it is installed with the WFP option (instead of the default DNE filter) because I personally tested close to half a dozen releases which yielded the same results (22.x.x.x through 23.x.x.x).
What we discovered was that any iteration of the plugin that offers a WFP option exhibits a concerning symptom with regards to the Windows Firewall Profile assignment when a VPN tunnel session is established. If a machine is domain-joined and has multiple firewall policies (Domain, Public, Private), and when a VPN session is established ( and when the plugin uses WFP), the Windows OS will deactivate the Public Profile from the physical adapter and only apply the Domain Profile. This occurs regardless if your gateway is configured with a full or split tunnel option in the session profile. This profile application also remains until the machine is rebooted or network adapters are manually reset. I tested the same plugins without WFP (Default DNE), and the symptom doesn’t occur.
Why should anyone be concerned? Well there could be enterprises that have Domain Firewall profiles with more lax rule sets compared to the Public or Private Profiles, which leads to a broader attack surface and in general… EXPOSURE of an endpoint system.
This is a serious issue, and we should all not be endlessly waiting for the next release cycle. If anyone here is experiencing the same, open a case with Citrix if you have a support agreement so their development of a fix is expedited.
If anyone else is having the same issue and would like to reference my open support case, please reach out to me. If you are wondering why we need to use the WFP option not just settle for the DNE option: Citrix support advised to used that because of known certificate issues related to DNE filter drivers (discovered after kernel-level analysis by Microsoft support). Long story short, it was a lingering issue we limped by on for close to two years.
On the use of the VPN plugin (AKA Citrix Secure Access Client)… It’s nice that we can connect without a browser and we have been doing this for years, with first factor LDAP and second factor RSA (RADIUS), but what about using SAML as an authentication factor. Is this possible or does SAML require a “real” browser because it is, in effect, a redirect? Context: We would like to migrate RSA to Cloud Authentiction Services (RSA SecurID CAS).
Anyone using the VPN Plugin directly against SAML?
Yes, if you configure nFactor authentication.
Good to know.
Thanks for the quick response.
Hello Carl,
at the moment we update our NetScaler to version 13.1 and we convert all policies to advanced. Our issue is, when we use advanced authorization policies the user do not have access via vpn to the internal recources. If we use our classic policies all is working. At the moment I do not found the misstake. Do you have any ideas? We have used diffrent firmware versions but the problem was the same.
THX
Where did you bind the authorization policies? If you did it at the Gateway vServer, and if they reference AAA Groups, then you must also add the AAA Group even if you don’t bind anything to the AAA Group.
We have bound the authorization policies to a local aaaGroup and all users will be added after they are succesful authenticated at the aaa auth server (nFactor – LDAP). It is the same configuration only diffrent is we use advanced authorization policies instead of classic ones. Additional we saw that nslookup only work if no Advanved authorization policy is bound, with classic it is working. I do not have any ideas at the moment. We have open a case but we received no comments from suppurt.
When we migrated our policies to advanced, we found that we had to add a new policy to explicitly allow DNS requests, i.e.,
add authorization policy Allow_All_UDP_DNS CLIENT.UDP.DNS.IS_AREC ALLOW
bind aaa group [groupname] -policy Allow_All_UDP_DNS -priority 100 -type DNS_REQUEST -gotoPriorityExpression END
Hi Phil,
thx for your support. Yes thats right and now it looks like that all is working.
Great article as always.
We recently started migrating users to the VPN on our VPX version 13.1. Users are now complaining that Zoom is slow and choppy and kicking them out at times. We want to do web filtering, so a split tunnel is not the way we wanted to go. We started to look into reverse split tunneling and adding the zoom IPs as intranet applications. From what I have seen, with reverse split tunneling we need to add the Zoom IPs and cannot use the FQDN. Zoom uses probably close to 100 IP ranges.
Is there a limit to how many intranet applications I can add? Will this slow down processing if I have that many??
Has anyone else seen this issue and potentially have another idea.
Thanks,
Rob
According to https://docs.citrix.com/en-us/citrix-gateway/citrix-gateway-clients/windows-plug-in-release-notes.html, FQDN is supported.
FQDN is supported… sort of. I believe the client will do a DNS lookup and add first entry it finds, which is useless for something with more than IP to be resolved. Reverse split tunnel works by altering local routing table so I don’t know how it could do otherwise. Worth testing. Add the entry as FQDN, login, then test by doing “route print” from workstation CLI.
FQDN is not supported and it’s by design, when I last checked with citrix there is no plan to get it working.
We have been doing reverse-split tunnel for years – back to firmware 11.1 – with hundreds of entries. We have never had issues.
Hello
First, Carl thank you for all your articles and posts…
It would be nice if there were Session Profile examples for platforms and common scenarios so we can at least get ideas and mix and match:
Full VPN + ICA Proxy on Windows
Full VPN + ICA Proxy on modern mobile devices
ICA Proxy on Windows
Full VPN on iOS
Full VPN on Android
etc…
There arent any decent examples of this anywhere.
Thank you
Hi Carl
I need to enable password reset functionality for the end users via clientless VPN from outside and inside the office and it needs to get sync with the AD
I have used SSPR its working but password is not getting sync ,
How can i achieve this ?
Note:- I want functionality also wherein even if user forgets password still they can login and change the password:- This is strange ask but how can we overcome this ?
StoreFront has a SSPR feature. Gateway has a SSPR feature. These two SSPR features are unrelated to each other.
I recommend buying something to do SSPR instead of using Citrix’s SSPR features. Most SAML IdPs (e.g., Azure Active Directory) have a SSPR feature.
Hi Carl,
Great sharing.
I have a question relating to whitelisting MAC addresses. I’m configuring whitelist MAC for VPN. With number of MAC addresses less than 1900, classic EPA pre-authentication can work. But if number of MAC addresses more than 1900, EPA function can’t work. In my environment, VPN users only authenticate with username and password, there’s no 2-factor authentication. Please advise
Thank you
ADC 13.1 supports using a pattern set for MAC addresses – https://docs.citrix.com/en-us/citrix-gateway/current-release/vpn-user-config/advanced-endpoint-analysis-policies/epa-scan-for-whitelisted-mac-addresses.html
Hey Carl – is there a way to “auto” favorite a bookmark (e.g. KEYWORDS: MANDATORY for XenApp)?
There are bookmarks files in /var/vpn/bookmark. I wonder if you can pre-create them for users.
Hello Carl, thank you for providing such a great blog with many helpful information.
I wanted to ask you if you could help me out regarding a VPN configuration (Full VPN) which should also provide internet access using a proxy.
At the moment I have a running VPN gateway configuration which initionally only provides access to internal ressources. Of course this works without any problems for HTTP and HTTPS traffic, as designed.
Now I have to change the configuration to also allow internet access (http, https) passing through a proxy. I have tried to configure this following the solution for Citrix Secure Web (Secure Browse) Proxy solution using traffic policies.
Unfortunately for the full VPN configuration (Citrix Gateway Plug-in, Citrix SSO App on iOS) this only works for HTTP traffic. HTTPS traffic is forwarded by IP-Adress (i.e. proxy sees tcp://….:443) instead of the URL (i.e. proxy sees https://google.com). Thus the proxy won’t allow internet access due to the fact that there is no IP whitelisting.
It doesn’t seem to be DNS related, because I can see the DNS entries on the netscaler as proxied entries.
Do you have any hints that points me to the right direction on how to get this working?
Thank you very much.
Best regards,
Sebastian
Hi Carl,
We recently switched from Classic Expressions to Advanced. VPN users are still able to connect but their devices are not showing as Domain Joined and are missing the mapped network drives. Everything else seems to work just fine. Switching back to Classic Expressions Policies “fixes” the issue.
We are using Reverse Split Tunneling, and AAA Group with Auth, Session and Intranet defined Apps. All traffic should be allowed – we allow all traffic, not only certain ports
Any idea where to focus the investigation? Thank you
For secure DNS registration, you need a few things in place:
1. Latest 13.0 client which supports secure DNS registration, i.e., 21.3.1.2
On workstation: HKEY_LOCAL_MACHINE\SOFTWARE\Citrix\Secure Access Client\secureDNSUpdate type REG_DWORD and value of 1 or 2. (Secure First or Secure always)
2. On appliance: nsapimgr -ys enable_vpn_dns_override=0
For non-secure DNS update see: https://docs.citrix.com/en-us/citrix-gateway/current-release/vpn-user-config/configure-plugin-connections/configure-address-pools.html#intranet-ip-dns-registration
Hi Carl, Many thanks for all your work. I’ve been following you for years and the contribution you give is priceless.
One question please, is there any way to use Address name space with Slipt Tunnel? I mean, having the posibility for example to route some *.examen domain outside off vpn, and all the other traffic inside the vpn.
Many thanks for your time in done these tutorials.
Christian.
I don’t think so. Even Citrix’s Office 365 article is based on IP addresses. https://docs.citrix.com/en-us/citrix-gateway/current-release/optimizing-citrix-gateway-vpn-split-tunnel-for-office365.html
Host name based intranet application works only when you have split tunneling set to ON. You are looking for this in reverse split tunneling, which is not supported. See: https://docs.citrix.com/en-us/citrix-gateway/current-release/vpn-user-config/configure-plugin-connections/configure-client-interception.html#to-create-an-intranet-application-for-a-host-name
Hey Carl,
Thank you for the article. It is very detailed and excellent reading. I enjoyed it.
What I could not find in this article is a way to disable the auto-reconnect. When the users connect to the VPN, reboot their laptops, it automatically tries to reconnect. I turned off “Single sign-on with Windows”, but it did not help. Also tried removing the Citrix client from start-up, but that also did not help. This is causing issues on their side.
How do I turn off this auto-reconnect “feature”, so the VPN client does not try to auto-reconnect upon a reboot? Any information would be a massive help.
Does your Session Profile have an AlwaysOn configuration?
There is currently no AlwaysOn profile setup on both the VPN vserver or on the Global Settings.
Try to exclude always on from the VPN client package
Hi Carl, as usual this is a great article, I just can’t find this information : our managed PCs (domain joined) receive their updates and software via SCCM. While being connected through VPN (Netscaler plugin), is it possible to upgrade the client (14.9 to 1912 CU3 LTSR) without losing the connection ? SCCM caches its installation package before starting.
Thanks !
I don’t see any reason why not. I don’t think that upgrading Workspace app affects the VPN connection. If they do a pull, then you probably don’t need Intranet IPs. If you do push then you’ll probably need Intranet IPs.
Thanks Carl and Davey for your swift feedbacks, that’s compliant with what I thought I understood about the relationship between the Receiver and the NS plugin. Have a great day 🙂
I can also reply: we work this way for quite some time now and for us the connection also remains available. Of course any published apps will be disconnected. For that reason a colleague built a special script in SCCM to show a pop-up before installing the software.
Is there a best practises to be followed for MS Teams while working on Citrix Gateway Full VPN tunnel. We are getting Audio/Video performance issues
Enable Split tunnel
Hi Carl,
A security audit ask us to secure Netscaler cookies for the VPN virtual server, add http-cookie-http-only-flag and http-cookie-secure-flag
I don’t find where I can set rewrite policy. Can you help me ?
Thanks in advance
I think that will break client-side Javascript. See https://support.citrix.com/article/CTX219479
Hello @Carl,
Do we have any policy that can be used to sync time on VPN clients from internal NTP system ?
There is no such policy. If clients are not domain-joined, rely on default NTP config from Windows.
Hi Carl,
I have configured ssl vpn with split tunnel on and I have added intranet applications which are hostname based and they resolved to private ip-addresses.
Once the connection is up, when accessing my intranet app using its url, I can see traffic in the Tunneled Application and after a minute I get err_timed_out on the browser.
I took a capture on ADC and I only see a TCP handshake between SNIP and the Host and nothing else. I cannot understand why there is no further traffic after the TCP handshake.
Kindly suggest what could cause such a behavior.
Thanks
Mohammed
Hi Carl,
In one of our customers environment we have users that just close their browsers when working from home and put their laptop into sleep mode.
We have setup a time-out setting in the Session Policies to close the session after some timeout (1day) but the Netscaler Gateway Plug-in remains active. When they come to the office, the netscaler plugin is still active which led to having issues to open an application inside the network. After a reboot they can solve this issue offcourse.
But is there a way that you can automatically log off the plugin on the client computer as well?
I’ve read something about it in one of your other blogs (https://www.carlstalhood.com/category/netscaler/netscaler-12/netscaler-gateway-12/) :
——————–
From Michael Krasnove: if you configured the Session Policy to direct users to StoreFront, but aren’t using RfWebUI, then placing the following code in c:\inetpub\wwwroot\Citrix\StoreWeb\custom\script.js will cause StoreFront to end the VPN tunnel when the user logs off of StoreFront.
var LOGOFF_REDIRECT_URL = ‘https://YourGatewayFQDN.com/cgi/logout’;
// Prevent the default “logoff” screen from being displayed
CTXS.Controllers.LogoffController.prototype._handleLogoffResult = $.noop;
CTXS.Extensions.afterWebLogoffComplete = function () {
window.location.href = LOGOFF_REDIRECT_URL;
};
———————
But not sure if this is the case in our setup.
I assume that “direct users to storefront” means that in the defined “Session Profile” on the tab “Published Applications” you direct to one of the storefront servers?
Just want to be 100% sure before I make this change in a large production environment 🙂
Thanks in advance!
Kenneth
Hi Carl,
I still have a question from a customer I can’t really reply on at the moment.
When building up the VPN over the Netscaler plugin, everything works fine.
But is there like some sort of idle timer that disconnects the vpn when user is not active (or pc goes into sleep mode?)
Session Profile > Client Experience tab has some timers.
Hi Carl,
Thanks for the quick answer.
Some users don’t use a citrix appliation just the client vpn to provide support on a machine with RDP.
I assume that timeout is also on affect on those users?
Maybe another small question that goes a bit hand in hand with this.
Is there any reporting or help that Netcaler Gateway or Netscaler plugin gives in orde to see when a user his VPN is connected and when the user is disconnected? So we can have an overview of who logs in when and for how long.
The timers in Session Profile apply to VPN clients.
Syslog has entries for logons. Ideally you should be sending Syslog to a Syslog server. If not, there’s /var/log/ns.log on the appliance but it only has limited history.
I am a little bit confused: is it possible to have full SSLVPN and start ICA apps (what ist usually doing a ICA Proxy) using one vServer?
Yes. One way is to connect to StoreFront after VPN is started. E.g. you can set the Session Policy > Home Page to your StoreFront URL.
Or you can enable Client Choices and let the user choose between ICA Proxy or VPN.
OK, thank you. In the first case: when the user clicks on an app in storefront, the ICA traffic flows through the gateway just like it would flow through an ICA Proxy? What about AppFlow data? Is this supported too?
IF you open StoreFront through VPN, then it’s like being internal. If you want AppFlow, then you can configure HDX Optimal Routing on StoreFront to force the ICA traffic through a Gateway.
Thank you. 🙂 To complete the picture: if I set up a complete SSLVPN with no split tunneling, how is the HDX gateway reached? Through the SSL tunnel? That would mean I need an additional HDX gateway on the inside and the traffic ist encrypted twice (1: SSLVPN, 2: HDX Proxy)?
You could do Reverse Split Tunneling if the Gateway is reachable externally.
Hello Carl
vpn access is possible.
but the private ip (192.168.0.2) of the gateway cannot be accessed while vpn is running.
The public ip of the gateway is accessible.
Is there a way to access the gateway’s private ip?
I don’t speak English well. Sorry.
thank you.
I have configured AlwaysON before logon, without user persona, using Advanced Authentication Policy, but when im opening the gateway URL, am getting error “No active policy to begin EPA”. I have both, a user certificate and device certificate, yet it’s not working.
I followed Citrix Docs, any idea why EPA is not kick in?
Thank you
Hi Carl,
Have a quick question, could we configure a FULLVPN profile and CITRIXICA/PublishedApps Profile on the same gateway. And if so what would be the best way to separate them out, I’m thinking a policy on each referencing the Type of Client connecting ?
Thanks,
Jason
The typical method is AAA Groups. Assign different Session Policies to different AAA Groups. You can enable Client Choices for the VPN people.
Citrix Gateway (VPN):
Can the installation bundle add the CheckMark for Local LAN Access in installs. Is there the ability to add this condition to the installation script?
Hi Carl,
Hope you are safe and Good. I have a situation in my environment. We are renewing our SSL certificate which is going get expired . Can you please help me with the below details.
1.Do we have any command to fetch all the bindings of a particular certificate.
2. And the command to bind the new certificate to many groups at a time
3.Command to fetch ip address of a LB server.
expecting you reply . Thanks in advance
Thanks,
Azifkhan.N
Go to System > Diagnostics > Running Configuration. Download the file. Open it in Notepad++ or any advanced text editing tool. Search for the certificate name. In Notepad++, you can “Mark” lines and then copy Bookmarked lines to a new file and then do search/replace. Once you have new lines, run them from the CLI. To replace a cert, simply bind the new one (no need to unbind).
You can also search the file for vServer VIPs.
Hey Carl, just wondering if you have any advice around increasing capacity for Gateways (VPX running on SDX) for if we reach 100% CPU – which I calculate is where we will top out first if we get around 13,200 concurrent split tunnel full SSLVPN users, going by my baselining of existing sessions we are getting. We’re running VPXs in 2 data centres (both HA paired) using GSLB Active/Active but need to increase our SSLVPN capacity to 40,000 concurrent. And potentially out to 60,000 concurrent. If we’re adding more VPXs we’d like to add 1 more per data centre to keep the load spread consistently.
I was reading up on Spillover based on Health where I assume I’d create additional VPXs and Spillover to them when metrics are triggered, but then it speaks about a redirect URL and all of our clients currently use a single URL (maybe that doesn’t matter and the client will just flick them to the Spillover URL?). Not sure if I’m going down the right path. Also I see you can bind Spillover settings at GSLB Service level, Content Switch level and Virtual Server level and I’m not sure where I’d want to do that in my case if it even is the right path to take.
I know this is a bit of a curly one but things are getting a bit hectic with planning for the possible event of our entire customer base working remotely very soon. Any direction you could point me in would be amazing. Thank you in advance.
Hi, Carl,
We would like to push the gateway and epa plug-ins to the users before upgrading the firmware (msi eventually). Can you please let me know where I can find these files?
There is not trace of them on the Citrix download page and we don’t have a test environment.
Thank you
Hey: the installs live on the appliance as separate components in case EPA might be used separately. If you plan to install both, download latest from Citrix website and deploy using your normal software deployment. The package contains both client an EPA. We just finished a deployment for about 50k users. All good.
Hi, Phil,
Can you please be more specific where to find the package on the Citrix website?
Thank you
Hi:
Under downloads > Citrix Gateway. Oddly, no 12.1 clients available for download. Something must be up. I am running 13.0 47.22 against every firmware from 10.5 through 13. Works great.
Also see https://support.citrix.com/article/CTX124649#Acquiring%20the%20Access%20Gateway%20Plug-in%20for%20Windows%20Installation%20Package
Unzip the .the build file. The installers are in there. 😉
great article, I’ve run into an issue with my clients configuration, running windows 10 – 1803 build (fully patched) and using netscaler plugin version 12.1.52.15; machines performs normally when plugged into LAN, however once connected via VPN, browser speed deteriorates to a point where the machine is not usable, issues is consistent in both Internet Explorer and Google Chrome, our Citrix support consultant has investigated the Citrix infrastructure and and analyzed network traffic etc and can’t seem to find any issues at that layer, they of the opinion it’s something on the client?
Problem from a client perspective, besides the monthly M$ patches, no changes made, we’ve rolled back patches for several months in an attempt to locate the fault, no avail. I understand that the issue first surfaced in October, 2019, I cant wholeheartedly confirm that is the case, we’ve rolled back patches as far as September 2019, issue still present, cant’ find any information out there where customers facing a similar issue, and advise/help will be warmly received.
Maybe this? https://support.citrix.com/article/CTX264377
much appreciated Carl, we’ve checked everything at a client layer (Windows 10 Os), the registry keys are set as per the articles, from Citrix Pov, I don’t know what’s been configured/tweaked as it’s managed be a 3rd party, who assured us that that there is no issues from the Citrix end, they adamant it’s a client issue, or something in our Windows 10 build, it’s abit of a needle in haystack job trying to find the solution,
Do you know when the issue with EMS will be address by Citrix? We are having exactly the same issue with VPN SSL connection failing for randomly for users and ADC consuming 100% CPU.
Hi Carl, I’m trying to use ssl vpn to acces an internal web application but when I try to access the links of the page I have this error message “Http/1.1 Object Not Found”.
For example, the root page is displayed fine and this is the url https://portal.mydomain.com/cvpn/https/web.mydomain.com/ but when I try to access the welcome page I have the error and this is the URL https://portal.mydomain.com/welcome.php
I appresiate your guide.
Best regards.
Are you trying to do Clientless VPN instead of Full VPN? If Clientless, then you need to rewrite the web server responses so the links are under https://portal.mydomain.com/cvpn/https/web.mydomain.com/.
Another option is Unified Gateway, where you can content switch your website instead of proxying through Citrix Gateway.
Hi Carl,
I created a Citrix Gateway for SSL VPN.
The LAN-Access ist limited by AAA Groups an Authorization Policies (IP-based and UDP-Port-based, as explained in this article: https://support.citrix.com/article/CTX232237).
I need to do more troubleshooting. So I would like to see which packets will be blocked because of my authorization policies. With the cli commands “nsconmsg -d current -g pcb_hits” and “nsconmsg -d current -g pol_hits” i see the policies i created hits.
But how can I see which packets are blocked?
Thanks and Regards
Sascha
HI Carl:
With regards to “Citrix Gateway 12.1 build 51 and newer also support the VPN Client establishing a tunnel before the user logs into Windows…” Do you know anyone who is actually doing this? I’m trying to get support from Citrix and remarkably, I have to force feed them the article on their site, which you link to. The SME is telling me that the only acceptable form of authentication is LDAP + User Cert per the base documentation and that Machine Cert can only be used for EPA. The issue for me is that I’m wanting to implement pre-login AlwaysOn for a customer and the article is sparse on details. I.e., is set up for authentication done per https://support.citrix.com/article/CTX200290.
I’m actually looking for the same thing. Problem seems to me that Windows can never authenticate pre login as it doesn’t know which user attempts logon. Therefore it doesn’t make sense to use a user based certificate in the pre logon stage for always on VPN.
It’s not a user certificate in use but a Machine cert. This can be deciphered from instruction #2, “Install certificate used for Citrix Gateway authentication to machine store (computer account)”
I did get a response from Citrix SME today. They spoke to the Product Management team and confirmed that yes, NetScaler will actually do this, despite the base document which says, only support for LDAP + User Cert. They will be updating the document soon, to be slightly less foggy. Specifically that, “Step 2 is referring to Computer Certificate that is issued by corporate PKI (internal CA) which is usually deployed by AD GPO to domain joined computers”. I suspect that that there will be reference to .https://support.citrix.com/article/CTX200290. Ultimately, status quo. Most Citrix how-tos don’t come from Citrix. Thus the need for great folks like Carl and George Spiers.
Hello
Did you ever get this working, am struggling to get the VPN before Windows Logon working?
Regards
Farouk
Hi Carl, I have one question: how can I use the real IP of the Client on xendesktop?
I think the Client IP is at HKEY_LOCAL_MACHINE\SOFTWARE\Citrix\Ica\Session\1\Connection on the VDA machine.
Hi Carl, do you know a way to update AlwaysOn URL from remote users so they point to a new gateway on the next connection? I tried pushing a reg change but it reverts back to the old URL
same here.. wondering if there is any config file with AGEE folder that holds the gateway URL information that we add or modify. Please let me know if you manage to find a solution. Will share if I manage to find one.
Carl,
When a NS Plugin (always on) intercepts the enterprise it automatically tears down the tunnel and disconnect. (great), however if my mistake a user clicks on the icon, it reestablished the connection disregarding its location and only a reboot, end task or disconnect from NS can kill the connection causing some users to be in a tunnel while in the LAN.
IS there a way to disallow this from happening?
thanks
Hi Carl,
I have an Intranet IP pool configured with SpillOver so that a user can establish more than one VPN session. However the first VPN session for a given user gets an Intranet IP, but the second session for the same user gets no IP assigned and uses the SNIP. When there are multiple sessions from unique users they do get Intranet IPs assigned.
Any ideas?
Cheers, Dan
Maybe assign an IP pool to the user instead of to a group – https://support.citrix.com/article/CTX229843
Thanks – that’s the first bit of doco I’ve seen that explains the restrictions. Binding per user isn’t practical in our scenario, so we’ll figure something else out.
Hi Carl.
If I have a pool of 10 IPs and spillover method is chosen. Can I have concurrent more than 10 Users? Where do I set the SNIP oder so called mapped IPs and bind to my VPN Server?
Try creating a Net Profile and bind it to the VPN vServer.
We would like StoreFront Published Apps to work in the normal way with no Client Choices but VPN to also work on the same vServer and URL – will the following achieve this?
ICA Proxy: Off
Clientless Access: Disabled
Client Choices: unchecked
VPN users can access purely using the Gateway plugin.
You can add AAA Groups and assign different Session Policies to different AAA Groups. This lets you enable VPN for members of a VPN AD Group and ICA Proxy for everybody else. Is that what you’re asking?
No quite, the scenario would be:
Most users would log in via the browser and see Storefront Published apps and not use a VPN
Other users would not use the browser and login via the Gateway Plugin to use VPN, this users would also use StoreFront published apps at times, when they log in via the browser this is what they would see, not the client choices screen.
Essentially, what I am saying is that VPN is only apparent through the plugin, any browser based logons would go straight to published apps no matter who you are.
Hello Carl,
Happy New Year.
Can you assist with the below?
We have a NetScaler setup with NS 11.1.58.13, for which I have configured a portals, behind a content switch. I have enabled cvpn bookmarks that work fine. However it seems NetScaler is allowing any internal URL to be accessed with the proper url formulation. That is to say our portal is at
https://myname.mycompany.com
When you click one of the bookmarks say myinternalapp.mycompany.com NetScaler CVPN renders this to
https://myname.mycompany.com/cvpn/https/myinternalapp.mycompany.com which takes you to the bookmark with no problem as expected.
However it seems any internal address can now be accessed this way including the NetScaler IP.
So https://myname.mycompany.com/cvpn/https/%5BNetScaler NSIP] takes you to the login page of the NetScaler. This is obviously a huge threat and I saw here in your page you say only the bookmarks should work:
“Only Bookmarks configured for Clientless Access will work without a VPN. The internal websites are rewritten so they are proxied through NetScaler Gateway. For example, if the internal website is http://intranet.corp.local, then Gateway rewrites them to https://gateway.corp.com/cvpn/http/internal.corp.local. This causes the web browser to send the HTTP Request to NetScaler Gateway, which then forwards the HTTP Request to the internal web server. No VPN needed.”
In the session policy for this VS clientless access is ON obviously and I have tried obscure and encrypt and neither of them stop this behaviour.
Do you know whats wrong? Or is this a bug?
Do Authorization policies have any effect on this?
Also check the clientless domains configuration at Gateway > Global Settings on the bottom right.
I need your help,
I now need to configure the access limit of the Netscaler gateway, based on the client MAC address.
Can you tell me what to do?
Info:
Platform NSMPX-5500
License type Standard
Software 12.0 53.13
I’m not sure if the OPSwat scans include MAC Address. But here’s an alternative method using registry – https://support.citrix.com/article/CTX118871
I have been read this docs, and configure it as same this docs. But it not working when I test it. I am looking for some information about the EPA analysis settings. Can you recommend it?
My SmartAccess article has some info on EPA scans – https://www.carlstalhood.com/smartaccess-smartcontrol-netscaler-gateway-12/
You can use also use EPA scans during nFactor authentication.
Thank you very much for having deployed the EPA strategy and it has taken effect. I now have a new question 1: Can the Preauthentication Policy be bound to a user or user group?
2: Configure multiple Preauthentication Policies to be bound to the same VS at the same time. You can check each Policy in turn. As long as one Policy is met, the Client can log in normally.
1. Preauth means before it knows who the groups are. nFactor can get the groups first and then ask for EPA scan.
2. Yes, I think you can do multiple.
Please tell me How configure multiple Preauth Policy with vs .I no fond any docs about this
Note: Just multiple Preauth Policy not useed nFactor .
Hi Carl,
I am trying to use VDA over SSL. This works fine if connecting through StoreFront (I can even block the ports 1494 and 2598), but this connection does not work if I am using a NetScaler.
I receive the error “Cannot connect to the Citrix XenApp server. The Citrix SSL server you have selected is not accepting connections.” The NetScaler has the CA installed and Intermediate certificate and they are linked.
What am I forgetting for it feels asif the certificate is not being accepted by the NetScaler.
And is there a log file that has more detailed info on this? nstcpdump.sh did not give any detailed info on this.
Thanks for your help and wisdom
TCP 443 is open from the SNIP to the VDAs?
If you do a network trace, you can see SSL Handshake. Any errors? NetScaler 12.0 build 59 added TLS 1.2 ciphers to the default backend cipher group.
Thank you for your swift reply. I have performed a telnet from the Netscaler to the vda on port 443. I can see the snip address on the session host and that the traffic has been accepted. I now started a nstrace, but need to check the file later on when I am at a machine with wireshark.
I will keep you posted.
Thanks again.
Wireshark shows one red line:
“133”,”0.411609548″,”192.168.82.50″,”192.168.82.24″,”TCP”,”89″,”443 → 8021 [RST, ACK] Seq=1 Ack=2 Win=0 Len=0″ (exported summary in csv)
Expanding the line shows me:
Frame 133: 89 bytes on wire (712 bits), 89 bytes captured (712 bits)
Encapsulation type: NetScaler Encapsulation 3.5 of Ethernet (176)
Arrival Time: Sep 27, 2018 11:41:53.411630464 West-Europa (zomertijd)
[Time shift for this packet: 0.000000000 seconds]
Epoch Time: 1538041313.411630464 seconds
[Time delta from previous captured frame: 0.000315884 seconds]
[Time delta from previous displayed frame: 0.000315884 seconds]
[Time since reference or first frame: 0.411609548 seconds]
Frame Number: 133
Frame Length: 89 bytes (712 bits)
Capture Length: 89 bytes (712 bits)
[Frame is marked: False]
[Frame is ignored: False]
[Protocols in frame: ns:eth:ethertype:ip:tcp]
[Coloring Rule Name: TCP RST]
[Coloring Rule String: tcp.flags.reset eq 1]
NetScaler Packet Trace
Operation: NEW_RX (0xaf)
Nic No: 0
Activity Flags: 0x00000000
…. …. …. …. …. …. …. …0 = Perf Collection: False
…. …. …. …. …. …. …. ..0. = PCB Zombie: False
…. …. …. …. …. …. …. .0.. = NATPCB Zombie: False
…. …. …. …. …. …. …. 0… = LB Stats Sync: False
…. …. …. …. …. …. …0 …. = Stats Req: False
Capture Flags: 0x00000000
…. …. …. ..0. …. …. …. …. = debug packet: False
…. …. …. .0.. …. …. …. …. = internal packet: False
…. …. …. 0… …. …. …. …. = skip headers: False
Errorcode: No Error (0x00)
App: IP (0x01)
Core Id: 0
Vlan: 1
PcbDevNo: 0x000183c9
Linked PcbDevNo: 0x00000000
Ethernet II, Src: Vmware_b0:d4:3b (00:50:56:b0:d4:3b), Dst: Vmware_b0:4e:28 (00:50:56:b0:4e:28)
Destination: Vmware_b0:4e:28 (00:50:56:b0:4e:28)
Address: Vmware_b0:4e:28 (00:50:56:b0:4e:28)
…. ..0. …. …. …. …. = LG bit: Globally unique address (factory default)
…. …0 …. …. …. …. = IG bit: Individual address (unicast)
Source: Vmware_b0:d4:3b (00:50:56:b0:d4:3b)
Address: Vmware_b0:d4:3b (00:50:56:b0:d4:3b)
…. ..0. …. …. …. …. = LG bit: Globally unique address (factory default)
…. …0 …. …. …. …. = IG bit: Individual address (unicast)
Type: IPv4 (0x0800)
Internet Protocol Version 4, Src: 192.168.82.50, Dst: 192.168.82.24
0100 …. = Version: 4
…. 0101 = Header Length: 20 bytes (5)
Differentiated Services Field: 0x00 (DSCP: CS0, ECN: Not-ECT)
0000 00.. = Differentiated Services Codepoint: Default (0)
…. ..00 = Explicit Congestion Notification: Not ECN-Capable Transport (0)
Total Length: 40
Identification: 0x3a23 (14883)
Flags: 0x4000, Don’t fragment
0… …. …. …. = Reserved bit: Not set
.1.. …. …. …. = Don’t fragment: Set
..0. …. …. …. = More fragments: Not set
…0 0000 0000 0000 = Fragment offset: 0
Time to live: 128
Protocol: TCP (6)
Header checksum: 0x9b11 [validation disabled]
[Header checksum status: Unverified]
Source: 192.168.82.50
Destination: 192.168.82.24
Transmission Control Protocol, Src Port: 443, Dst Port: 8021, Seq: 1, Ack: 2, Len: 0
Source Port: 443
Destination Port: 8021
[Stream index: 4]
[TCP Segment Len: 0]
Sequence number: 1 (relative sequence number)
[Next sequence number: 1 (relative sequence number)]
Acknowledgment number: 2 (relative ack number)
0101 …. = Header Length: 20 bytes (5)
Flags: 0x014 (RST, ACK)
000. …. …. = Reserved: Not set
…0 …. …. = Nonce: Not set
…. 0… …. = Congestion Window Reduced (CWR): Not set
…. .0.. …. = ECN-Echo: Not set
…. ..0. …. = Urgent: Not set
…. …1 …. = Acknowledgment: Set
…. …. 0… = Push: Not set
…. …. .1.. = Reset: Set
[Expert Info (Warning/Sequence): Connection reset (RST)]
[Connection reset (RST)]
[Severity level: Warning]
[Group: Sequence]
Window size value: 0
[Calculated window size: 0]
[Window size scaling factor: -2 (no window scaling used)]
Checksum: 0xfdce [unverified]
[Checksum Status: Unverified]
Urgent pointer: 0
[SEQ/ACK analysis]
[This is an ACK to the segment in frame: 132]
[The RTT to ACK the segment was: 0.000315884 seconds]
[iRTT: 0.000415128 seconds]
[Timestamps]
[Time since first frame in this TCP stream: 0.000731012 seconds]
[Time since previous frame in this TCP stream: 0.000315884 seconds]
Do you see SSL Handshake packets?
The only Handshake packets are for all other resources like STA server and StoreFront, but not for the VDA.
To the VDA it shows that it wants to contact using 1494. And this off course fails.
ICA only is not configured on the Virtual Server.
Hi Carl, Do you know if you can set which Tab will be the default on the NetScaler Unified Gateway Clientless Access Page? For example the Web Apps tab shows by default. Can you change this to the Applications tab in the X1 theme? Thanks, Daniel
Hi Carl,
Do you know if it is possible to skip EPA analysis (preauthentication policies) if a user belongs to a particular AD security group? Or only is possible to do that with post-authentication policies?
Thanks in advance and kind regards!
Can I use customized port for SSL-VPN? In my lab, netscaler was assigned 49200, but it stuck at starting tunneling.
Hi Carl
Is it possible to configure Full VPN without the AAA licensing?
I want to configure it for mobile devices using certificate based authentication.
Thanks
Felipe
Yes. VPN only needs NetScaler Gateway licensing.
Hi Carl,
Great Article,
Quick question if you know, Can be EPA scans be configured conditionally to allow 2 different authentication methods, based on pass or fail.
IF pass User gets VPN Always-ON
If fail User gets VPN MFA,LDAP and RSA.
Thanks in Advance,
Jason
You should be able to do that with nFactor – https://www.carlstalhood.com/nfactor-authentication-for-netscaler-gateway-12/
Dear Carl,
We are using XenMobile as IDP for our ShareFile single sign on.
Can we use Netscaler native OTP for the XenMobile Appcontroller server(netscaler gateway) to enable two factor also for our sharefile.
Please share me your valuable suggestions.
If you are using native OTP authentication on your SSL VPN gateway you need to change the expression of the OTP traffic policy.
https://citrixguyblog.com/2018/03/16/netscaler-otp-is-breaking-ssl-vpn/
Thanks. I added a note about this to the Native OTP article. I also added it to the SSL VPN Virtual Server binding section.
Hi Carl, thank’s for this great article. I have got two little questions.
Question 1 (NS Plugin compatibility): You discribed that the NS Plugin Version should match the NS Firmware Version. Do my users have to update their NS Plugin after I updated my NS to a newer Firmware? Or is it also working, because of downward compatibility?
Question 2 (VPN Client IP Pools): Is it possible that my NS does not spread IP addresses to my connected Clients? For example if I want to use my DHCP Server for IP releases of my VPN Subnet?
Thanks and Regards
Julian
1. Depends on your Session Policy configuration for plug-in upgrades. Minor firmware upgrades might not require a plug-in upgrade. But major upgrades (e.g. 11.0 – 11.1) always require an upgrade.
2. I don’t think DHCP is supported.
Been a great help but stuck on one item and out of ideas, we have SSL VPN and plugin configured fine, can rdp, ping servers on remote end no problem. Cannot create a mapped drive however , can connect to ports on telnet but unable to create a mapped drive to the windows 2016 file server. Any hints would be great
hello
On my windows 7 i have issue with vpn access through citrix netscaler plugin
When I go on netwokk my citrix virtual adaptater says network cable unplugged
so I cannot ping any or access any servers in my internals network
Could be a DNS issue, or a DNE issue – https://support.citrix.com/article/CTX215320
hi normally the citrix virtual adaptater must be connected ?
If all is ok normally I can run a cmd and ping internals servers
tks
Can i send you some sreenshot ‘
Hi Carl, great article. I have one question: what needs to be configured so a VPN Client can register itself in DNS? We need this, so we can remotely manager these clients. We use latest Netscaler version.
Thanks!
You need to allow dynamic dns updates on your dns and allow domain joined machines to update the dns records.