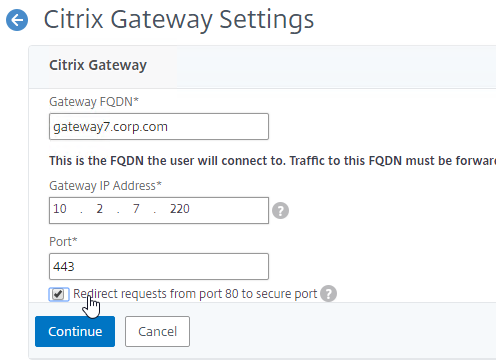
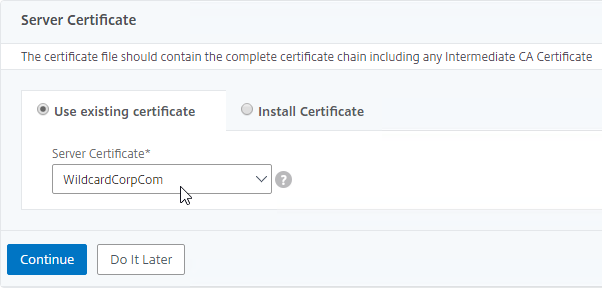
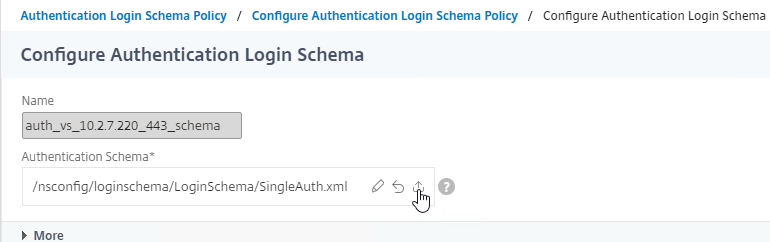
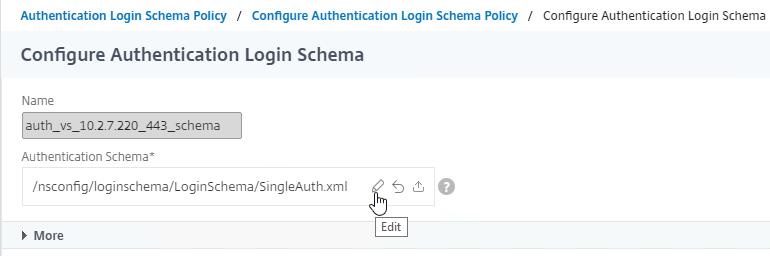
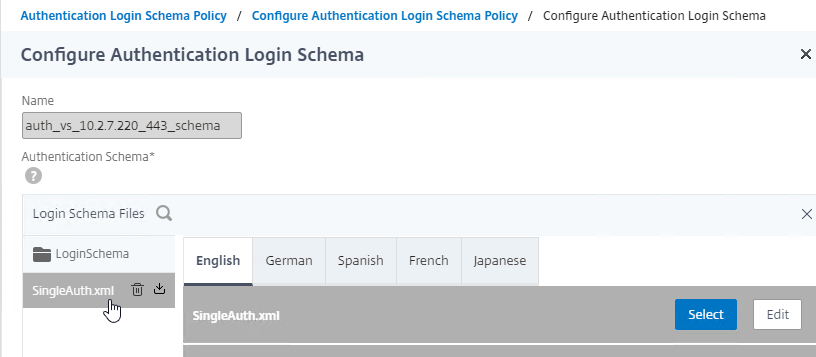
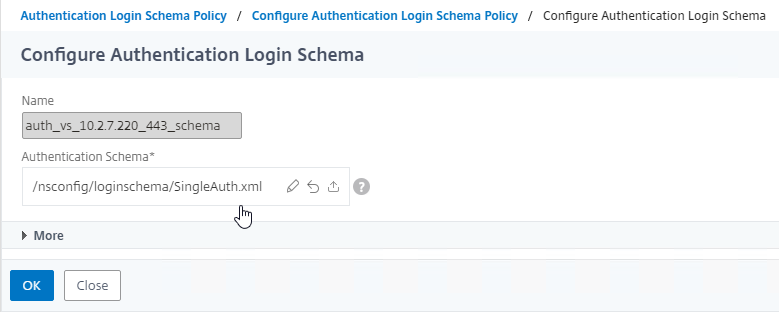
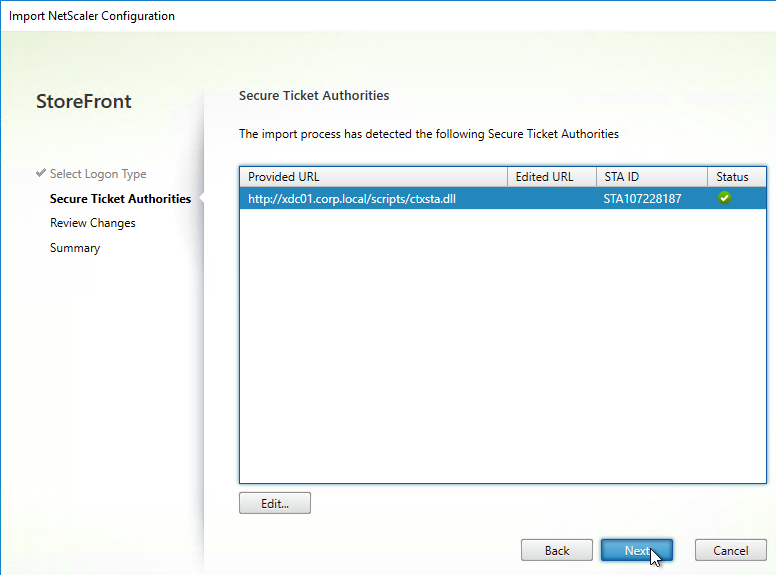
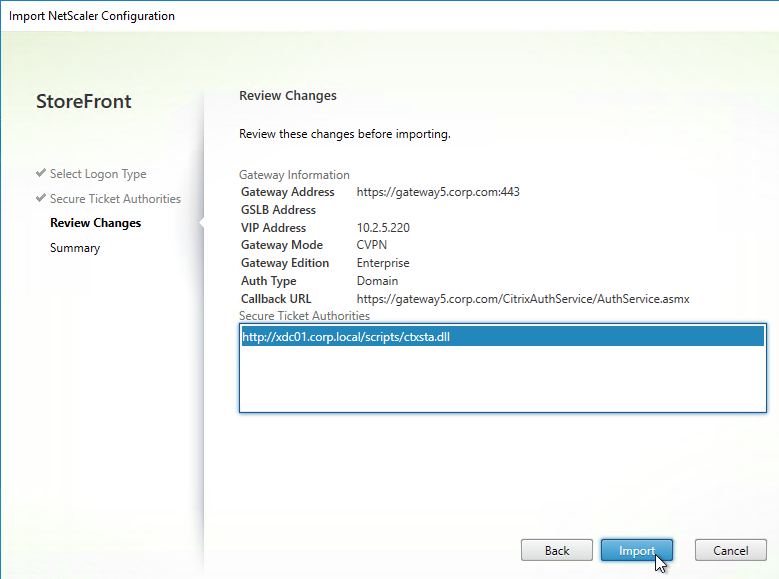
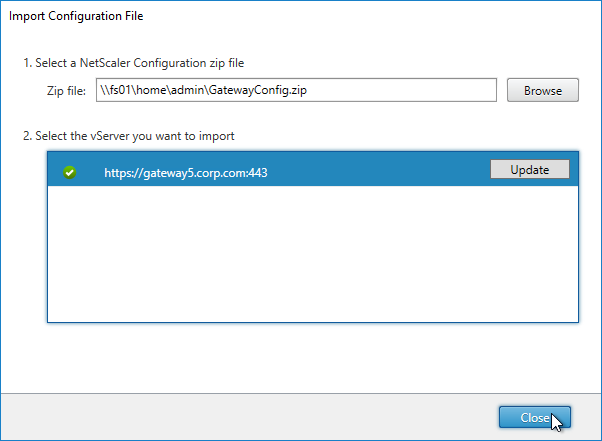
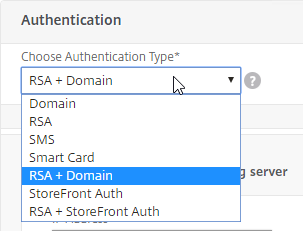
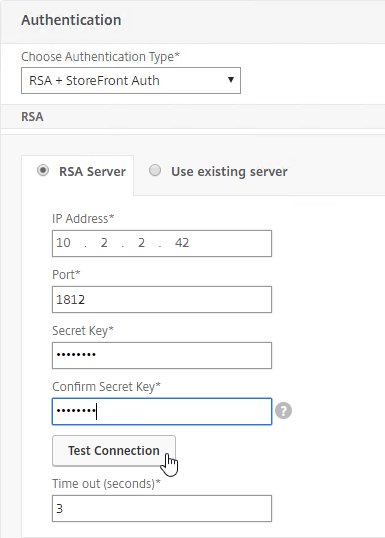
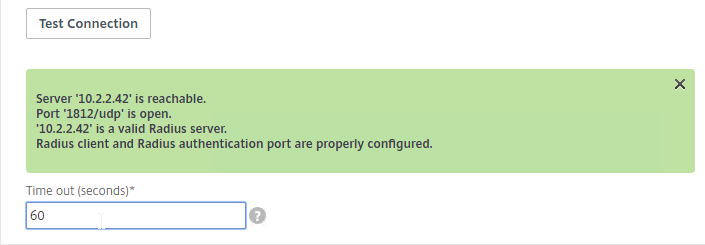
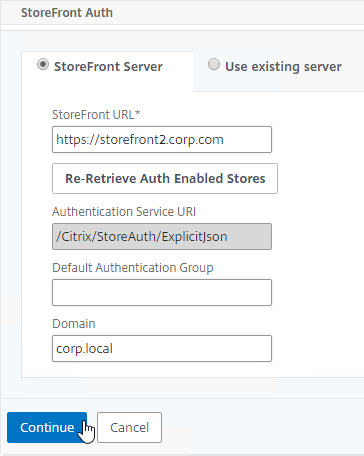
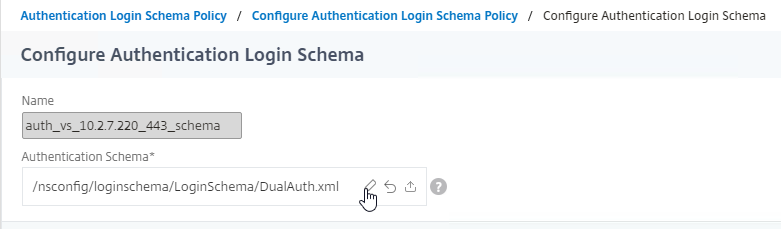
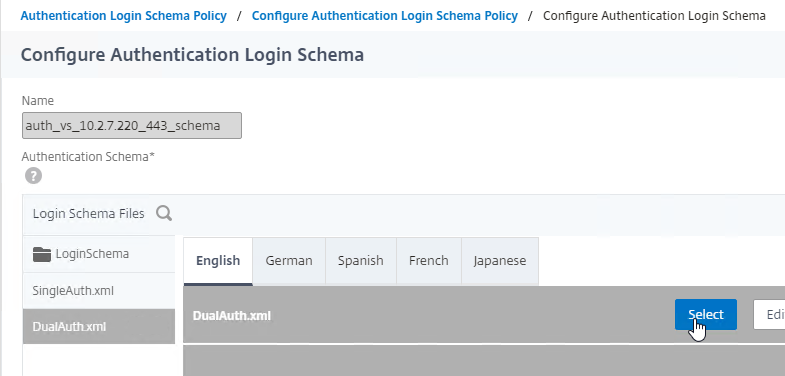
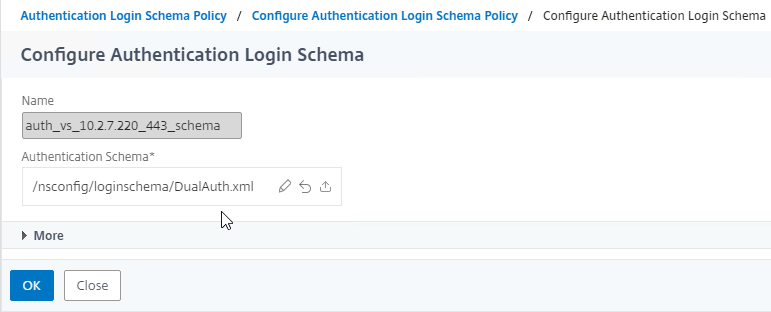
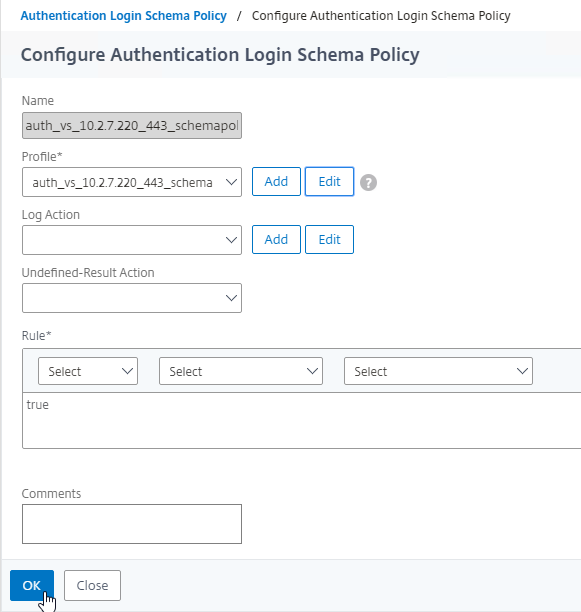
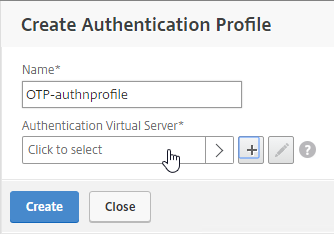
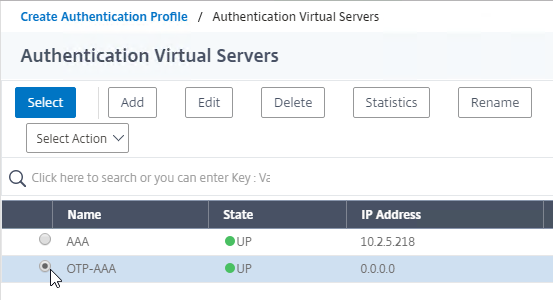
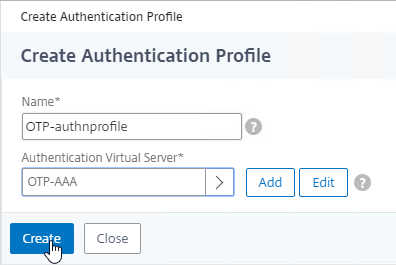
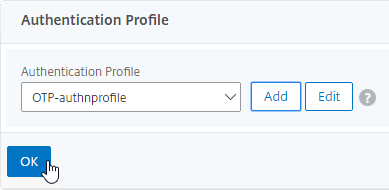
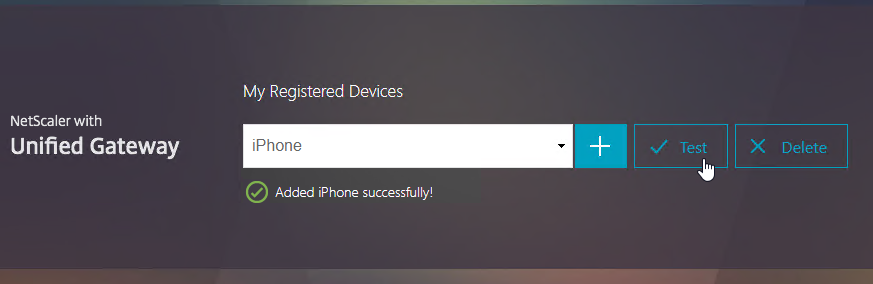
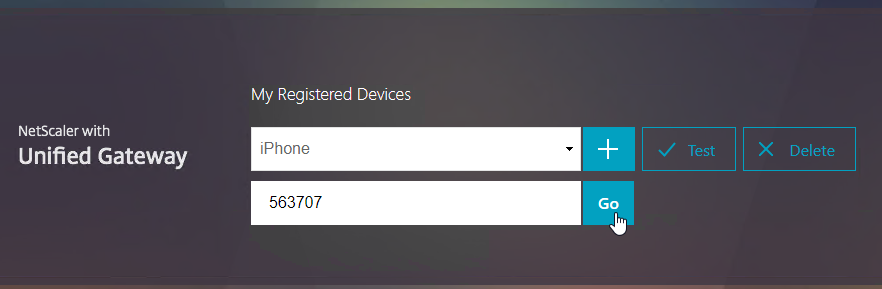
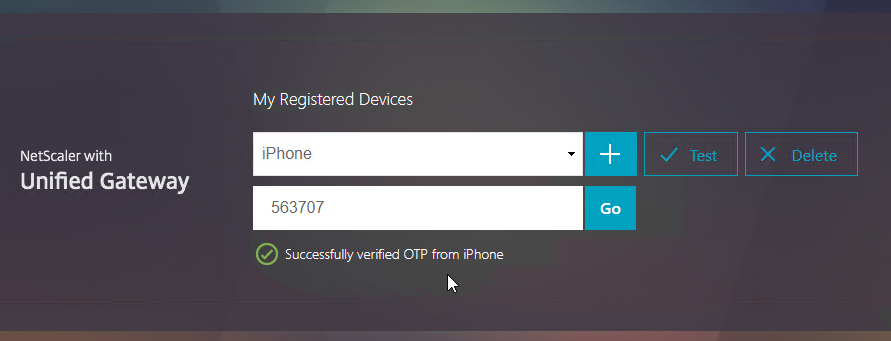
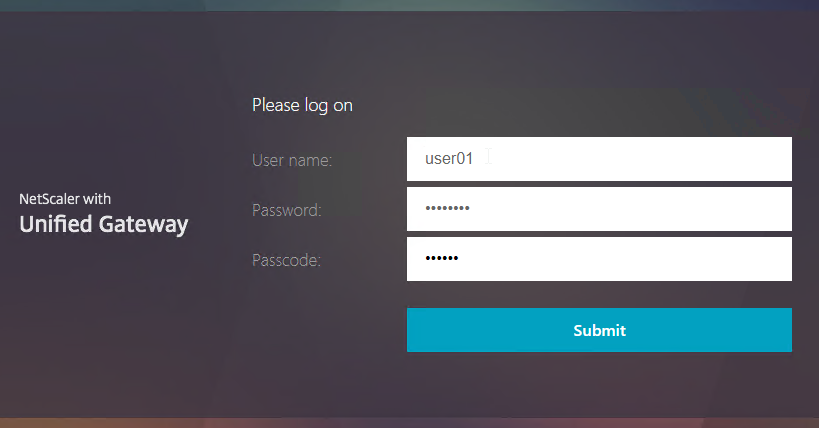
Navigation
- Change Log
- Overview
- Prerequisites
- AAA Groups
- Session Policy/Profile
- Citrix Gateway Plug-in (i.e. VPN Client)
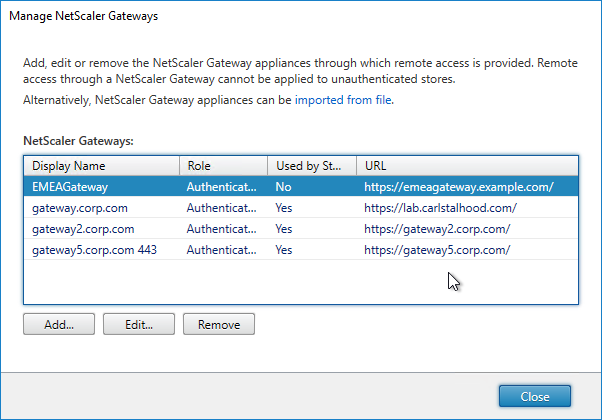
- Other VPN Objects
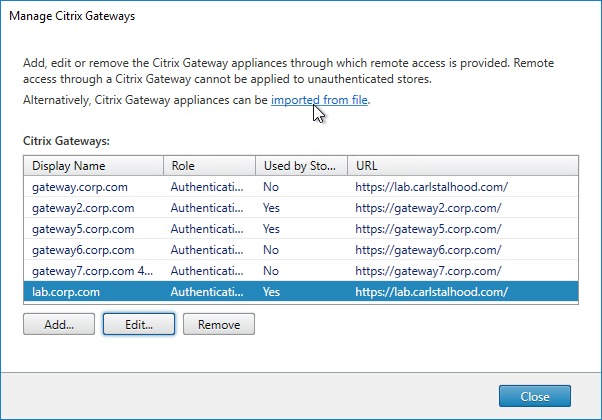
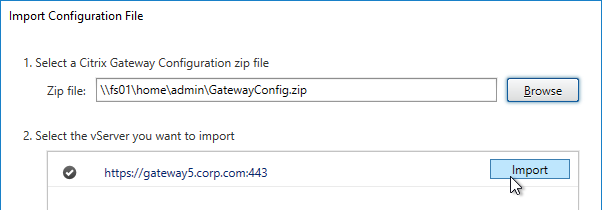
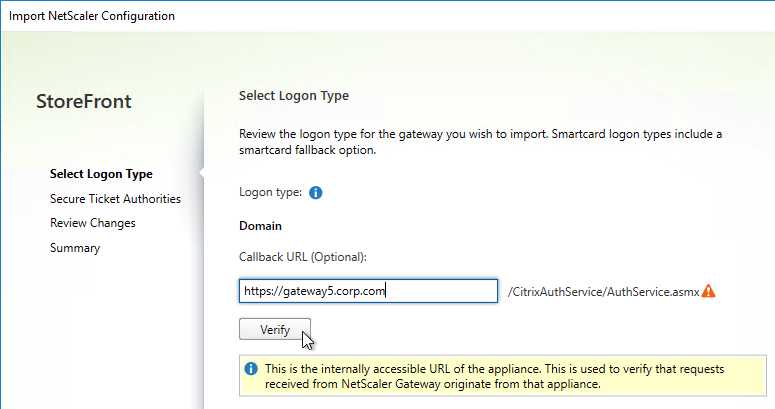
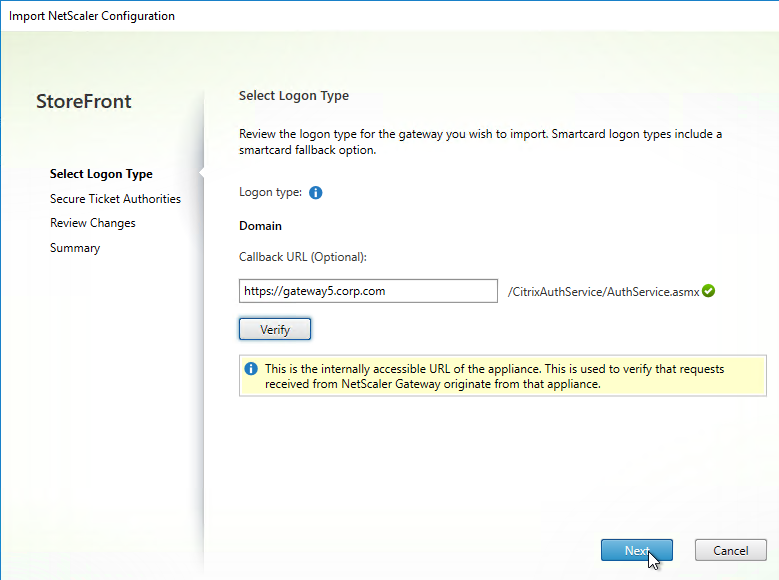
- StoreFront in Gateway Clientless Access Portal
- Quarantine Group
💡 = Recently Updated
Change Log
- 2021 May 5 – Upgrade Gateway Plug-in on ADC
- 2021 Feb 5 – VPN Client – added SecureDNS info from 13.0-71.44 release notes
- 2021 Jan 9 – Bind Session Policy – added info from CTX289931 AAA group session policies are not applying based on priority
- 2019 Mar 6 – VPN Session Profile – added link to AlwaysOn service for Windows at Citrix Docs.
- 2018 Oct 6 – updated some screenshots for Gateway 12.1
- Gateway Plug-in – 12.1 supports nFactor authentication
- 2018 Apr 3 – in the Create Session Profile section, added Clientless Access removal instructions from CTP Sam Jacobs at NetScaler Gateway Client Choices – hide/remove Virtual Apps and Desktops at Citrix Discussions
- 2018 Mar 18 – in the NetScaler Gateway Virtual Server section, added info from Julien Mooren NetScaler – Native OTP is breaking SSL VPN.
- 2018 Feb 8 – in Authorization Policies section, added info from CTX232237 NetScaler Unified Gateway Advanced Authorization Policy Support for UDP/ICMP/DNS Traffic
Overview
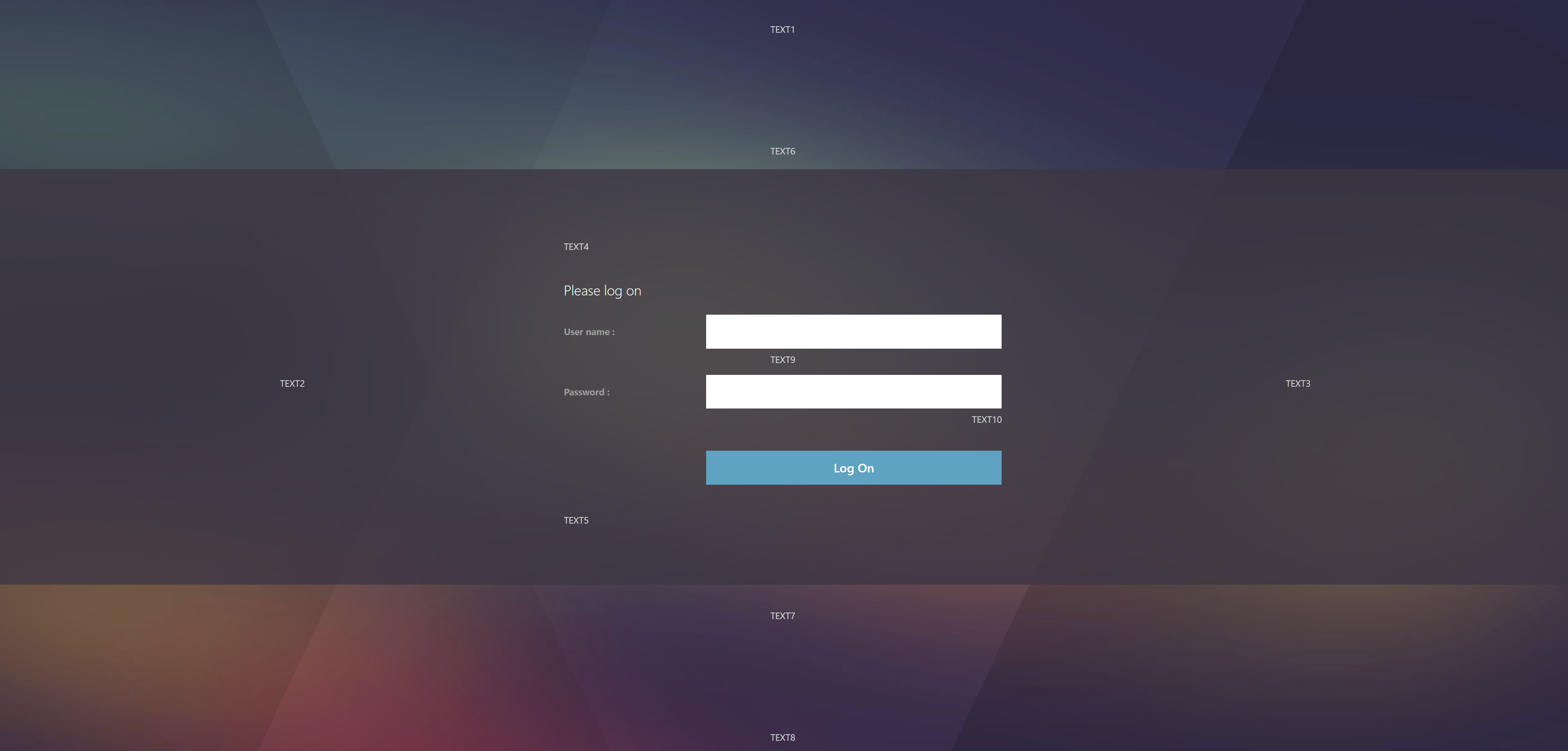
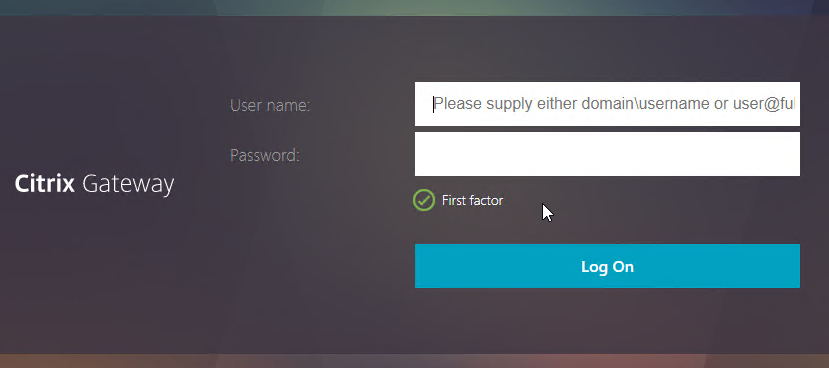
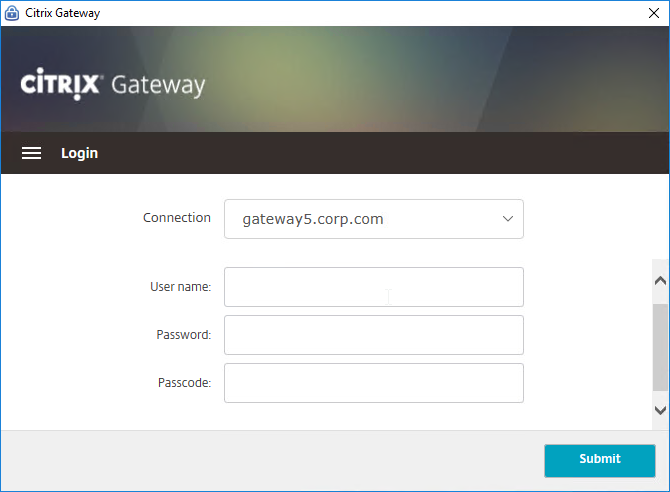
Here’s an overview of the Citrix Gateway connection process:
- Users use SSL/TLS to connect to a Citrix Gateway Virtual Server (VIP).
- Citrix Gateway prompts the user for authentication.
- Once the user is authenticated, Citrix Gateway uses Session Policies/Profiles to determine what happens next.
Citrix Gateway supports six different connection methods:
- ICA Proxy to Citrix Virtual Apps and Desktops (CVAD) (aka XenApp/XenDesktop) and StoreFront – the client is built into Citrix Workspace app (aka Citrix Receiver)
- SSL VPN – requires installation of Citrix Gateway plug-in (VPN client)
- Clientless – browser only, no VPN client, uses rewrite
- Secure Browse – from MDX-wrapped mobile applications (Citrix Endpoint Management aka XenMobile), uses rewrite
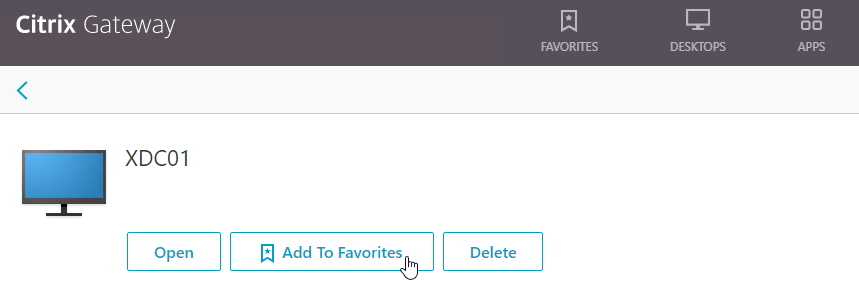
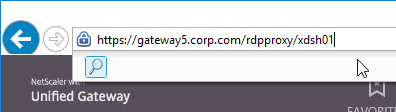
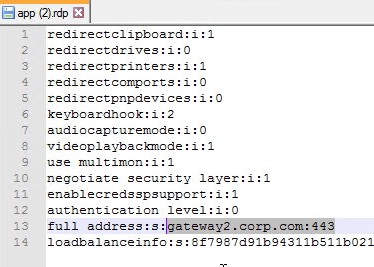
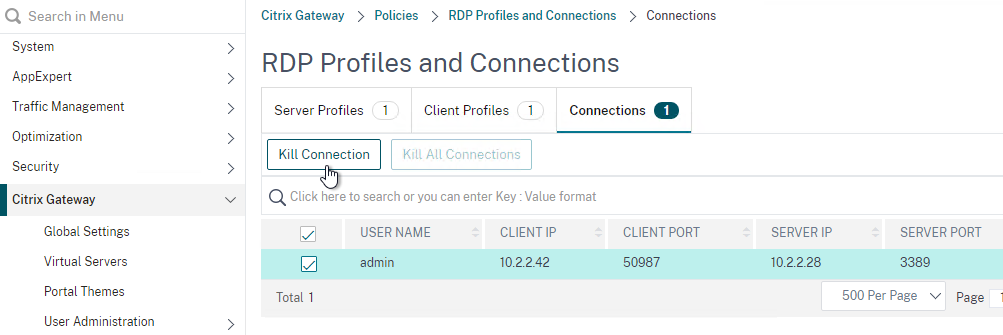
- RDP Proxy – only RDP client is needed
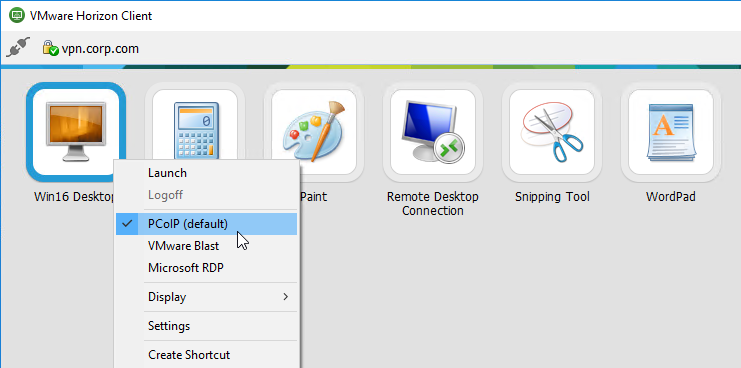
- PCoIP Proxy – only VMware Horizon Client is needed
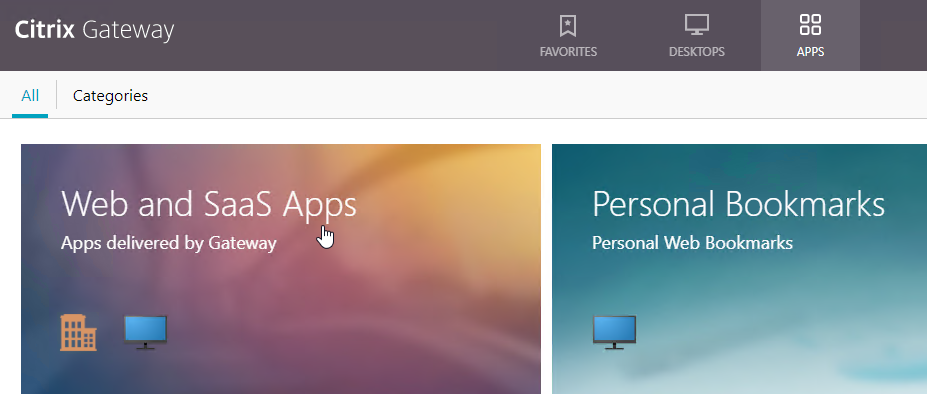
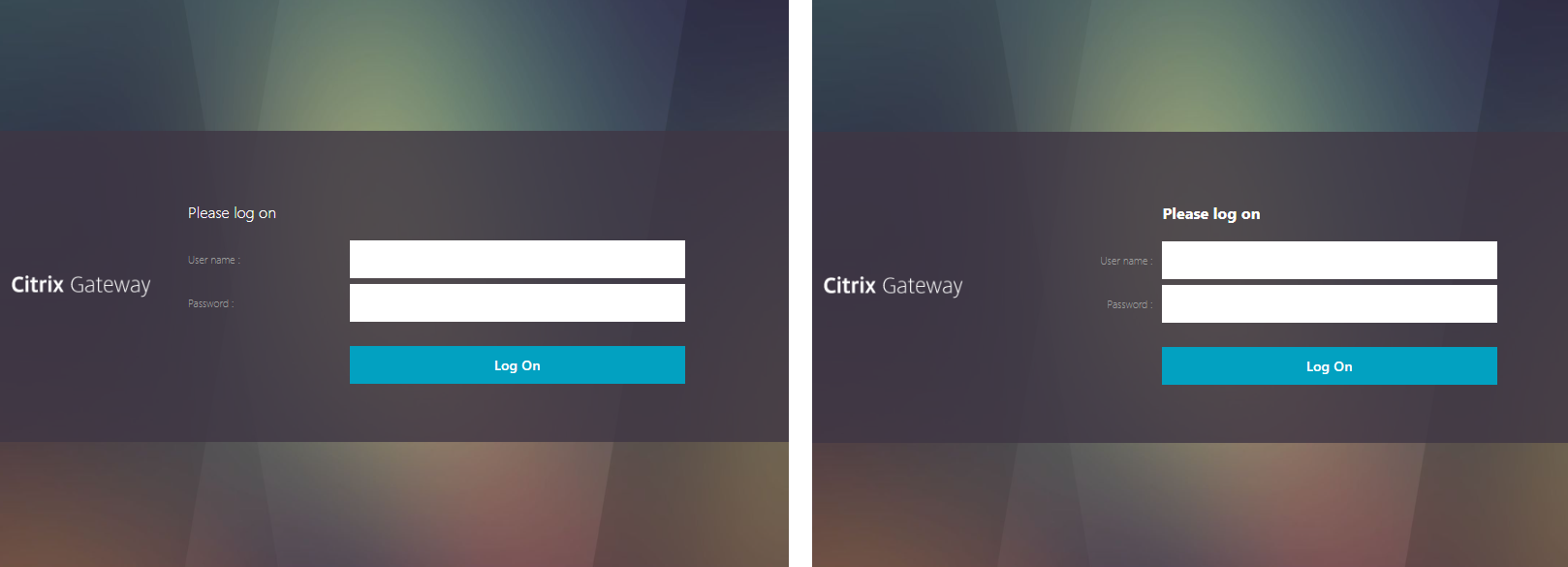
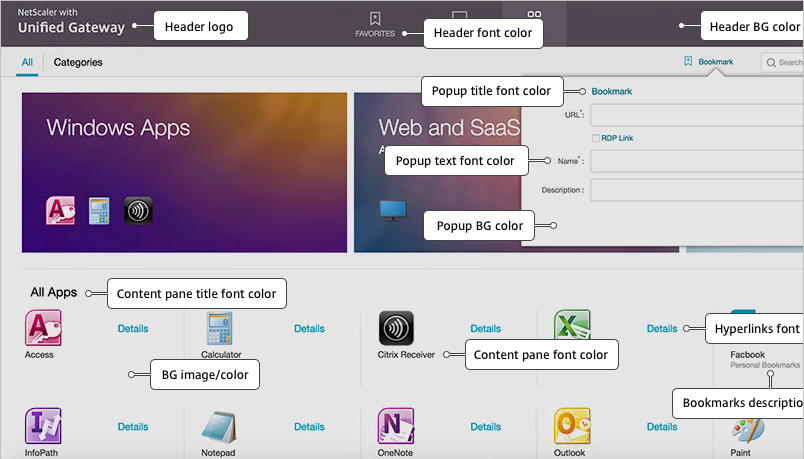
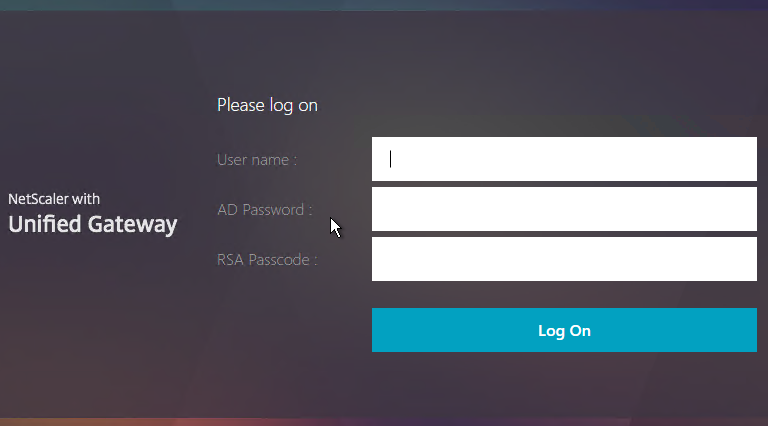
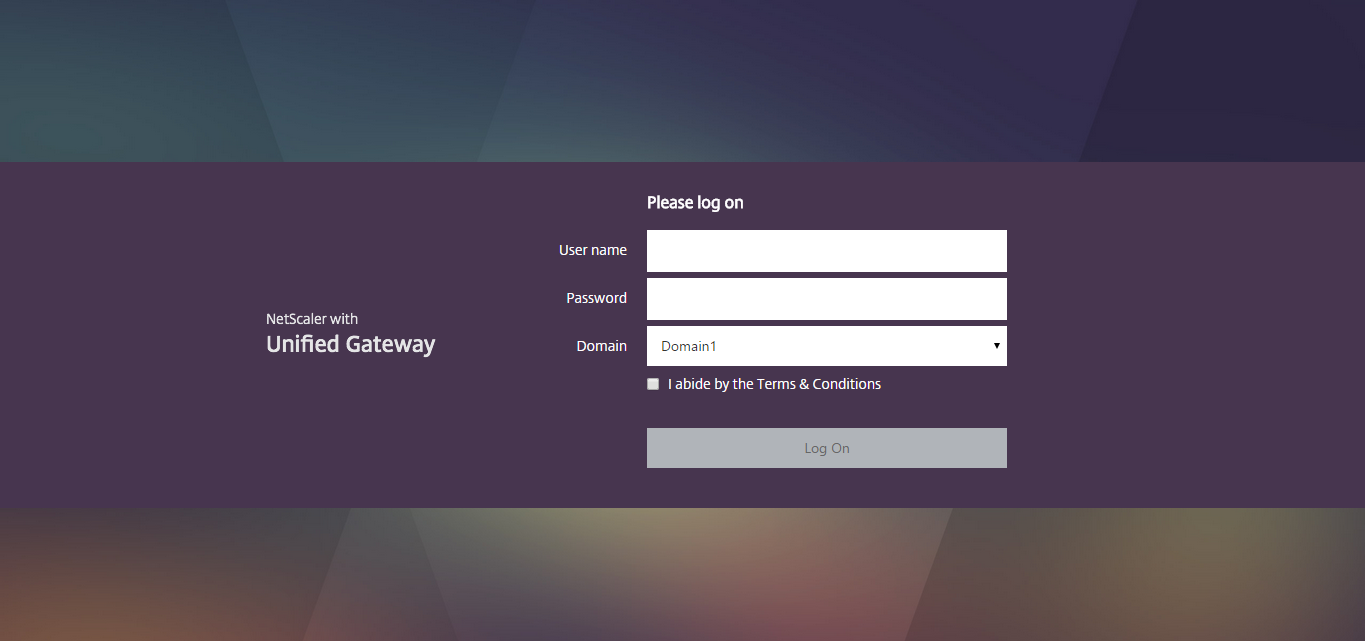
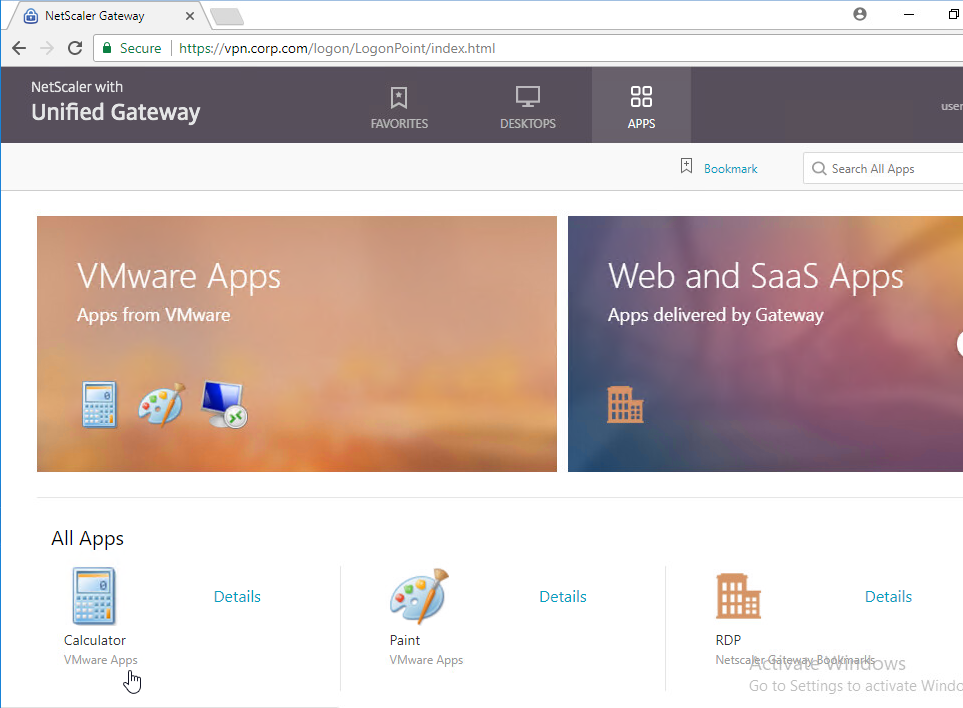
You can configure Citrix Gateway Session Policies/Profiles to only use one of the connection methods. Or Citrix Gateway can be configured to let users choose between ICA Proxy, Clientless, and SSL VPN connection methods. Here’s a sample Client Choices screen using the RfWebUI theme:
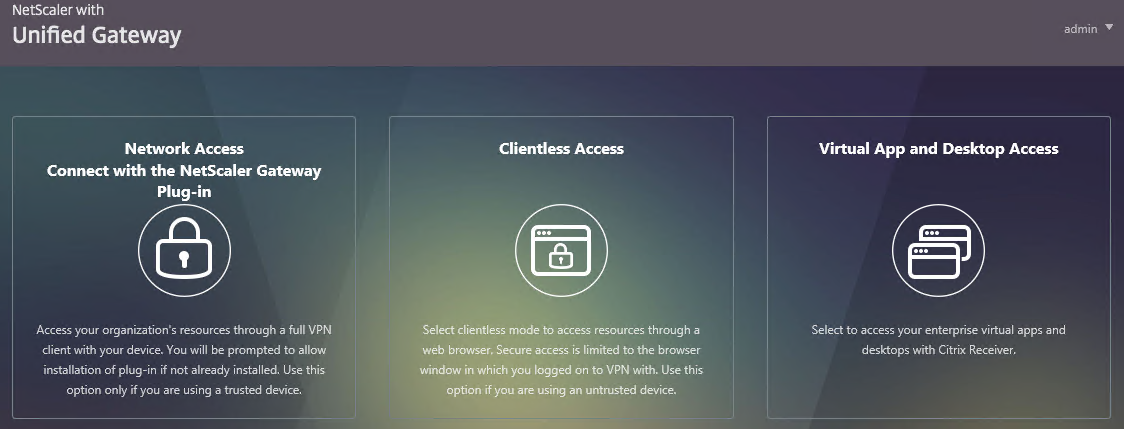
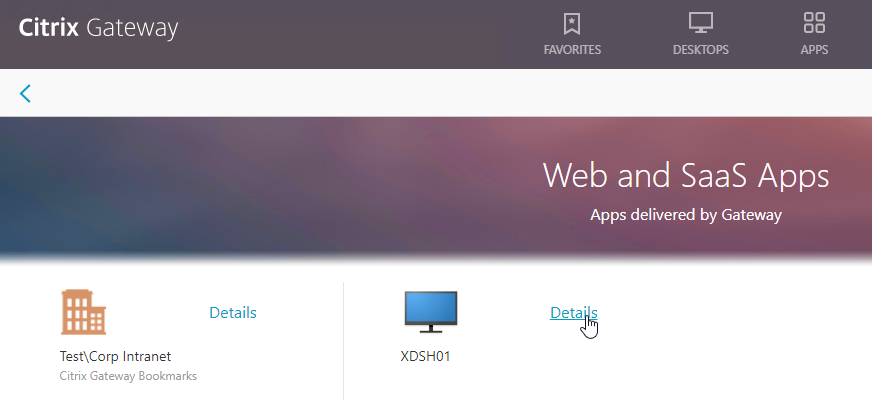
- The Clientless Access option opens a portal page that has icons from Citrix StoreFront (ICA Proxy), icons for RDP Proxy, icons for PCoIP Proxy, and links to websites.
- The website links can be proxied through Citrix Gateway. Proxy methods include: clientless rewrite, SSL VPN, and traditional load balancing.
- Citrix Gateway can optionally Single Sign-on to the websites.
- The Virtual App and Desktop Access option only displays icons from Citrix StoreFront (ICA Proxy). For other types of icons, you’ll need Clientless Access.
- The Connect with Citrix Gateway Plug-in option launches the VPN tunnel. After the tunnel is established, a portal page is displayed. This can be the Clientless Access portal, or a user defined website URL (e.g. intranet).
Session Policies/Profiles have several settings that control the behavior seen after authentication:
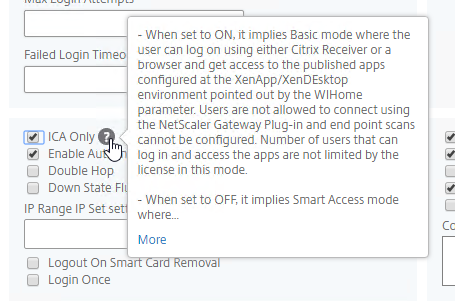
- ICA Proxy – ON or OFF
- If ON, then ICA Proxy is the only connection method allowed, overriding the other connection methods.
- ICA Proxy does not launch the VPN client. It only needs Citrix Workspace app.
- ICA Proxy shows the Webpage that’s configured in the Web Interface Address field of the Session Profile. This is typically the StoreFront Receiver for Web page, but technically it can be any internal website.
- If OFF, that doesn’t mean ICA Proxy doesn’t work. You can still send ICA traffic to the Citrix Gateway Virtual Server, and the Citrix Gateway Virtual Server will still proxy it to internal VDAs.
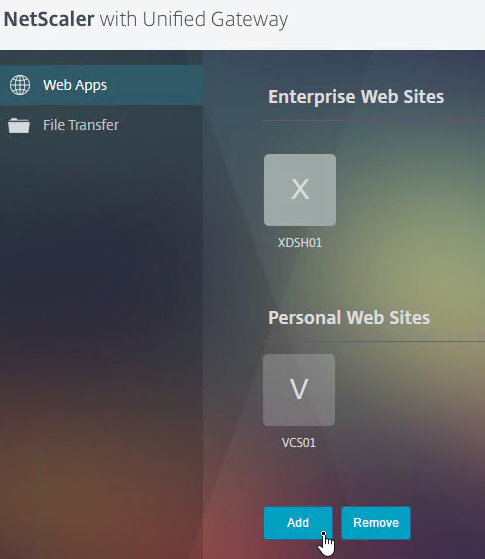
- Setting it to OFF allows the other connection methods to function. For example, Clientless Access can show both Citrix Gateway Bookmarks and StoreFront published apps. If VPN is launched, then the portal page shown to the user after the tunnel is established can contain the StoreFront published applications.
- Clientless Access – On, Off, Disabled
- If On, then Clientless is the only connection method allowed, assuming ICA Proxy is not set to ON. After the user logs in, the user is presented with a portal page that contains a list of Gateway bookmarks and/or StoreFront published icons. The VPN Client is not launched.
- The Home Page setting in the Session Profile allows you to display an internal website instead of displaying the Citrix Gateway Portal Page.
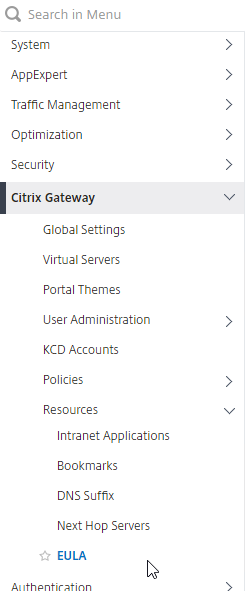
- Bookmarks are configured at Citrix Gateway > Resources > Bookmarks. You can bind the Bookmarks (Urls) to the Citrix Gateway Virtual Server, or to AAA Groups.
- Only Bookmarks configured for Clientless Access will work without a VPN. The internal websites are rewritten so they are proxied through Citrix Gateway. For example, if the internal website is http://intranet.corp.local, then Gateway rewrites them to https://gateway.corp.com/cvpn/http/internal.corp.local. This causes the web browser to send the HTTP Request to Citrix Gateway, which then forwards the HTTP Request to the internal web server. No VPN needed.
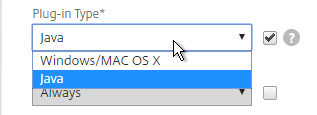
- Plug-in Type – Windows/MAC OS X
- If both Clientless and ICA Proxy are set to Off, then the VPN Client will be downloaded and launched.
- Once the VPN tunnel is established, the webpage configured in the Home Page setting is displayed. Or the Citrix Gateway Portal Page (Clientless Access) is displayed if no Home Page is configured. The Bookmarks in the Portal Page can link to internal websites that are only accessible through a VPN tunnel. Or Bookmarks can be configured for Clientless Access.
- Additional Gateway objects control VPN behavior including: DNS Suffix, Intranet Applications, Intranet IPs, and Authorization Policies.
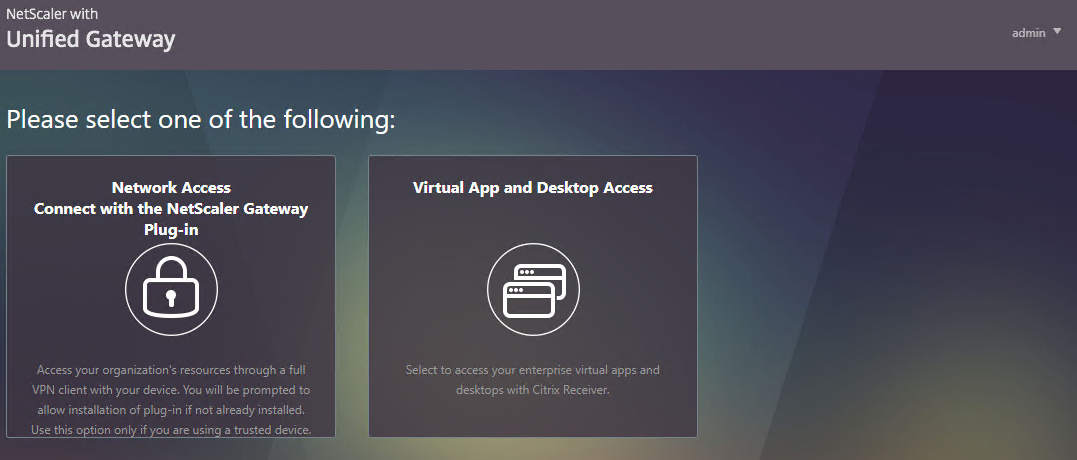
- Client Choices – checked or unchecked
- If Client Choices is checked, then it displays a page containing up to three buttons allowing the user to choose between VPN, Clientless, or StoreFront. The Network Access with the Citrix Gateway Plug-in (VPN) button is always displayed. The Clientless Access button is displayed if Clientless Access is set to On or Off (not Disabled). The Virtual App and Desktop Access button is displayed if a Web Interface Address is configured.
Here are some characteristics of Session Policies:
- Citrix Gateway > Global Settings > Change Global Settings has the same settings as a Session Profile. However, all Session Policies/Profiles override the settings configured in Global Settings. That’s the whole point of the Override Global checkboxes in the Session Profiles.
- Session Policy Expression – If the Session Policy Expression is true, then the settings contained in the Session Profile are applied.
- Action = Session Profile – The Session Profile is also sometimes called the Action. That’s because all Citrix ADC policies follow a standard structure – if the expression evaluates to True, then perform the Action. For Session Policies in particular, the policy Action = Session Profile.
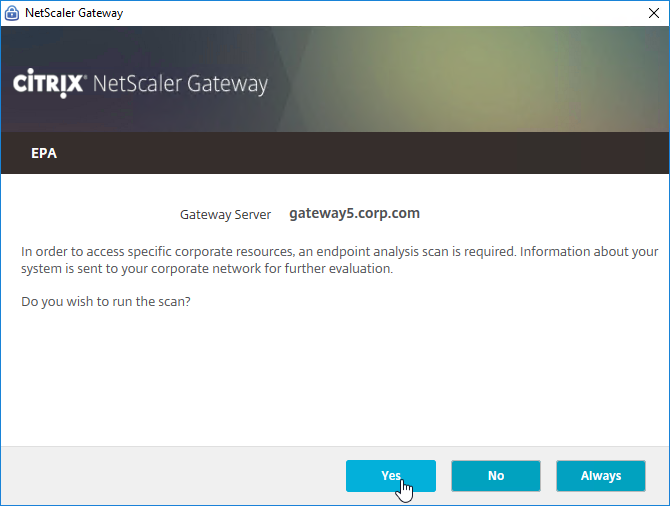
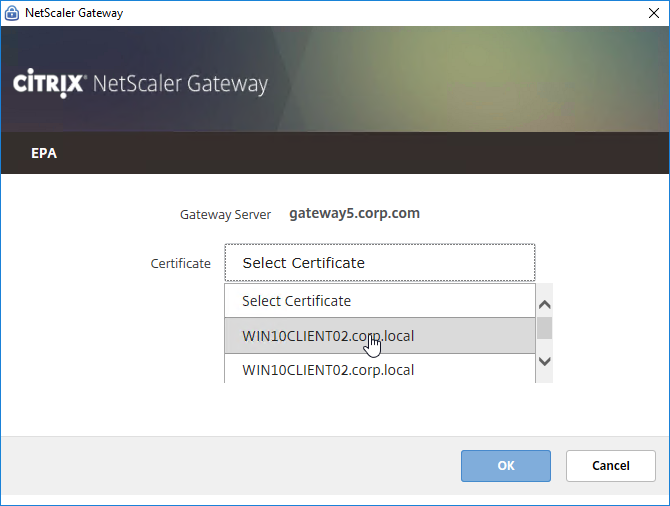
- EPA – The Session Policy Expression in Classic Syntax could include an Endpoint Analysis (EPA) expression.
- Default Syntax Expressions vs Classic Syntax Policy Expressions – Citrix ADC 12 and newer supports Default (Advanced) Syntax Expressions on Session Policies, in addition to the older Classic Syntax.
- No syntax mixing – All Session Policies bound anywhere must be either Default or Classic. You cannot mix the two types.
- EPA is Classic only – EPA Scans are only supported in Classic Expressions.
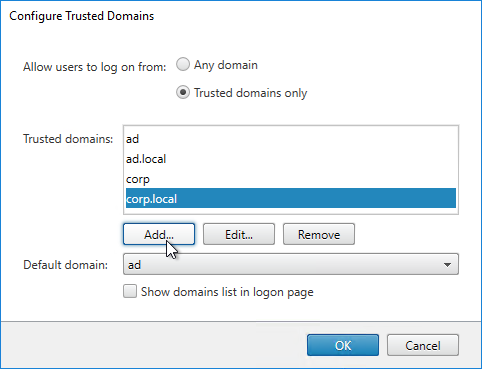
- AD Group in Default Syntax – Default Syntax allows expressions for AD Group Membership like
HTTP.REQ.USER.IS_MEMBER_OF("MyADGroup"). This could eliminate AAA Groups in some circumstances.
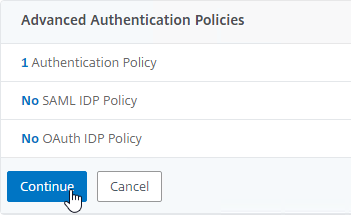
- Policy Bind Points – Session Policies can be bound to three different bind points – Citrix Gateway Virtual Server, AAA Groups, and AAA User.
- When bound to a Citrix Gateway Virtual Server, the Session policy/profile applies to all users that log into that Virtual Server.
- When bound to a AAA Group, the Session policy/profile only applies to members of the AAA group (Active Directory group or local group)
- When bound to a AAA User, the Session policy/profile only applies to the AAA user (Active Directory user or local user)
- Profile Conflicts – Multiple Session Policies/Profiles could apply to a single session. In this case, the Profile settings are merged. But if there’s a conflict (e.g. one Session Profile enables Clientless access, but another Session Profile disables Clientless access), then which one wins?
- Priority number – When you bind a Session Policy to a bind point, you specify a priority number. This priority number usually defaults to 100.
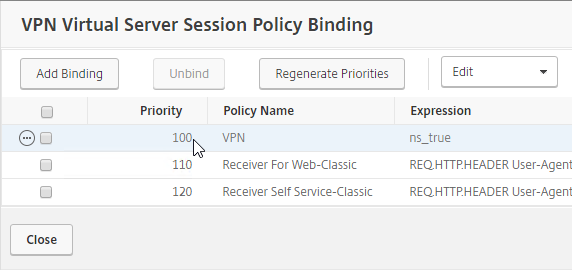
- Lowest priority number wins – The Session Policy binding that has the lowest priority number, wins. Session Policies bound with a priority of 80 will win over Session Policies bound with a priority of 100. Remember, for settings that don’t conflict, the two Profiles merge, but for settings that do conflict, the lower priority number policy/profile settings win.
- Classic Policy Priority and multiple bind points – for Classic Session Policies the bind point location doesn’t matter. If you bind a Session Policy to a AAA Group with a priority of 100, and you also bind a Session Policy to the Citrix Gateway Virtual Server with a priority of 80, then the conflicting settings in the Session Policy bound to the Citrix Gateway Virtual Server will win because it has the lower priority number. You might think that AAA-bound policies always override Virtual Server-bound policies, but that is not the case.
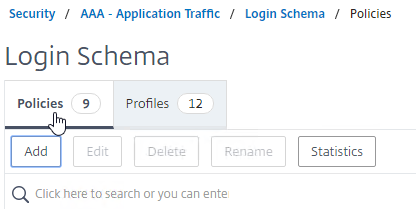
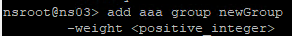
- Advanced Policy Priority and multiple AAA Groups – see CTX289931 AAA group session policies are not applying based on priority. The first created AAA Group overrides AAA Groups created later unless you specify the weight parameter when creating the AAA Group from the CLI.
- Priority number – When you bind a Session Policy to a bind point, you specify a priority number. This priority number usually defaults to 100.
- Global Settings vs Virtual Server Settings – When you bind a Session Policy to a Citrix Gateway Virtual Server, the settings in the Session Profile only apply to connections through that particular Citrix Gateway Virtual Server.
- Settings in Citrix Gateway > Global Settings > Change Global Settings apply to every Gateway Virtual Server.
- Settings in AAA Group > Policies > Session Policy/Profile apply to every Gateway Virtual Server.
- If you want a particular Gateway Virtual Server to override AAA or Global, your only choice is to bind a Session Policy to the Gateway Virtual Server with a lower priority number than the AAA Bind Points.
AAA Groups are a critical component of Citrix Gateway VPN configuration:
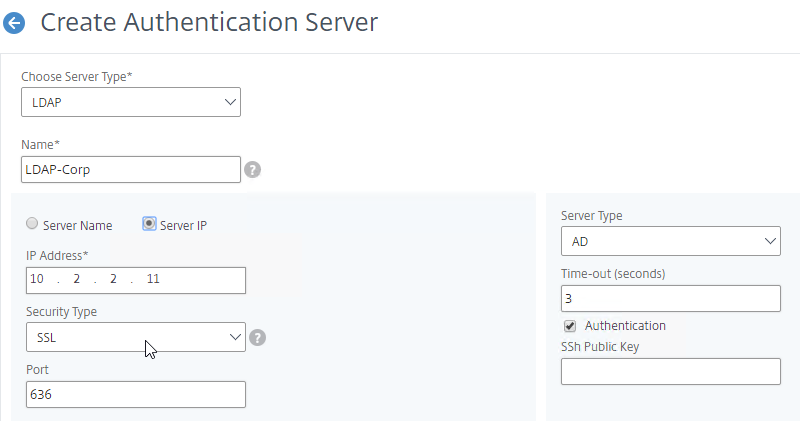
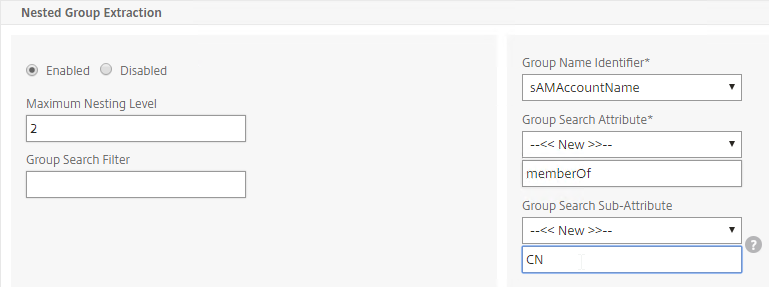
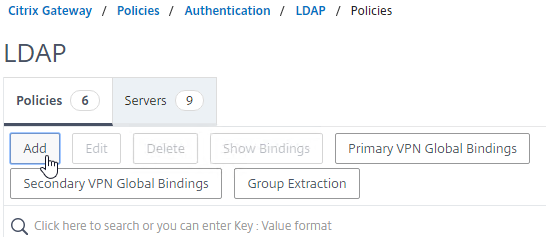
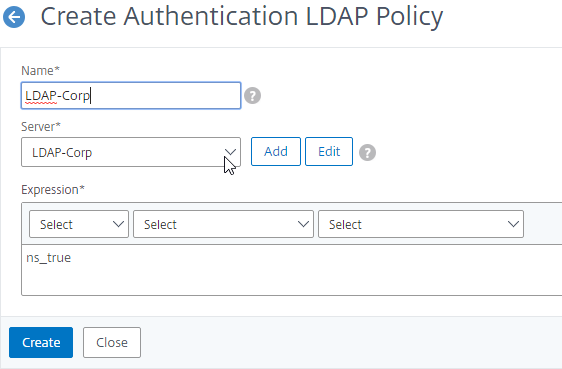
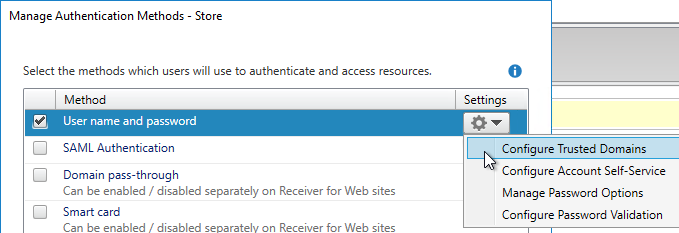
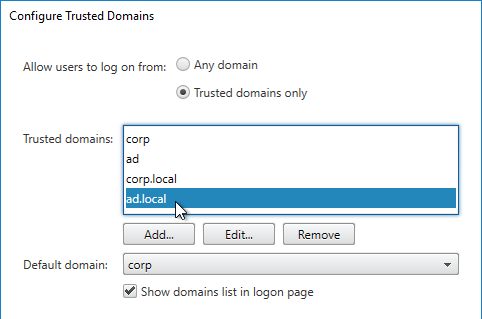
- Group extraction – Make sure the LDAP Policy/Server is configured to extract to the user’s Active Directory Groups.
- Create AAA Groups on the Citrix ADC that match exactly (case sensitive) with the user’s Active Directory Group Name.
- Default Syntax and AD Groups – An alternative to AAA Groups is to use
HTTP.REQ.USER.IS_MEMBER_OF("MyADGroup")Default Syntax expressions. However, Default Syntax does not support Endpoint Analysis. And Default Syntax only applies to Session Policies and Authorization Policies, so you might still need AAA Groups for Bookmarks, Intranet Applications, and Intranet IPs.
- Default Syntax and AD Groups – An alternative to AAA Groups is to use
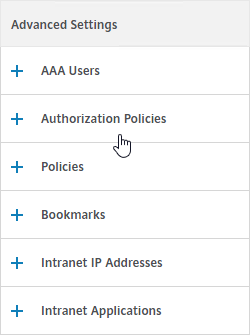
- You can bind policies and other Gateway objects to the AAA Group, and these bindings only affect that particular AAA Group. These bindings include:
- Session Policies
- Bookmarks
- Intranet IPs (aka IP Pool)
- Intranet Applications (for split tunnel)
- Authorization Policies (what’s allowed across the VPN tunnel)
- Note: these objects can also be bound to the Gateway Virtual Server, which means they apply to all users that connect to that Gateway Virtual Server.
- If the user belongs to multiple AAA Groups, then policies are applied as follows:
- Session Policies – the settings are merged, unless there’s a conflict. If a conflict, then the policy with the lowest priority number wins.
- Bookmarks, Intranet Applications, and Authorization Policies are merged.
- Intranet IPs (IP Pool) are probably random allocation. It’s probably best to make sure a user only belongs to one AAA Group that assigns Intranet IPs.
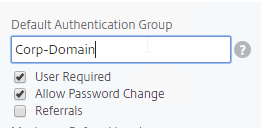
- You can also create local AAA Groups that are unrelated to Active Directory groups. There are several ways of getting users into these local AAA groups:
- Create local AAA Users and assign them to the AAA Group
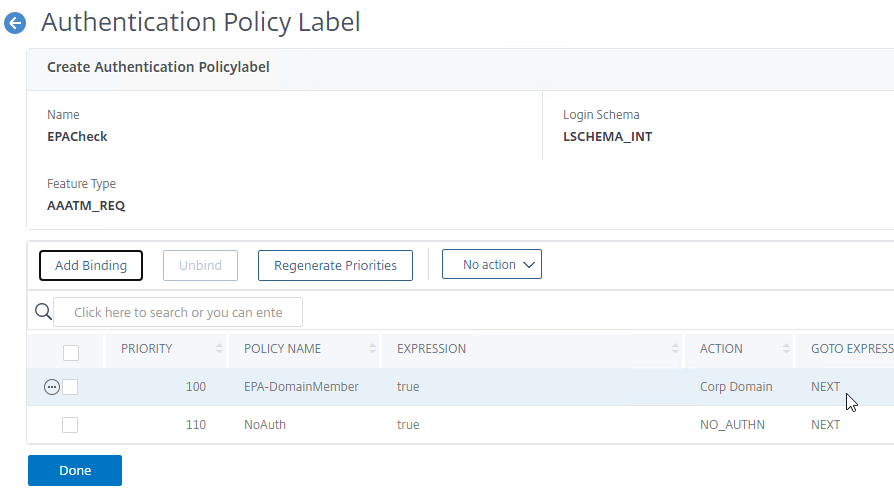
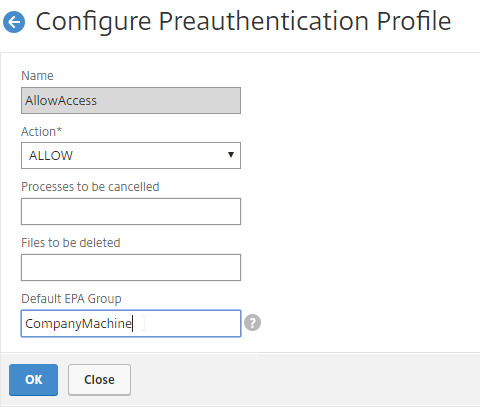
- Configure Session Policy/Profile with a Client Security Check String (EPA Scan). If the scan succeeds, users are placed into local Authorization AAA Groups. If the scan fails, then users are placed into a local Quarantine AAA Group, and removed from all other AAA Groups.
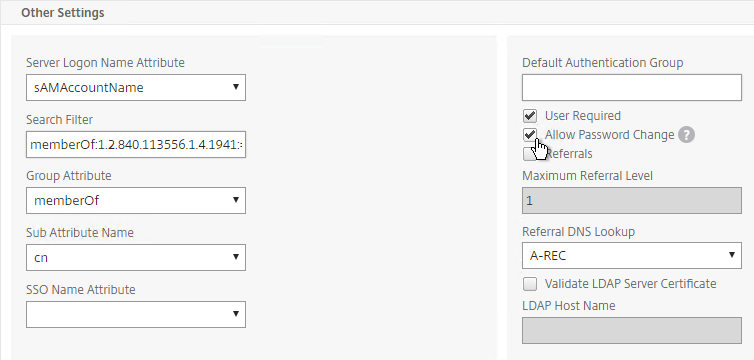
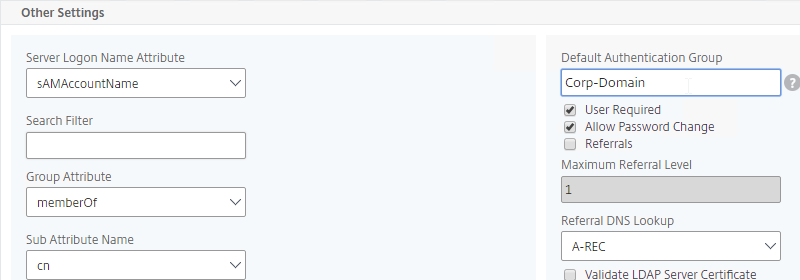
- When users are authenticated with a particular authentication server, the authentication server can be configured to place users into a Default Authentication Group. This lets you apply different Session Policy/Profiles (and other Gateway objects) depending on how the user authenticated.
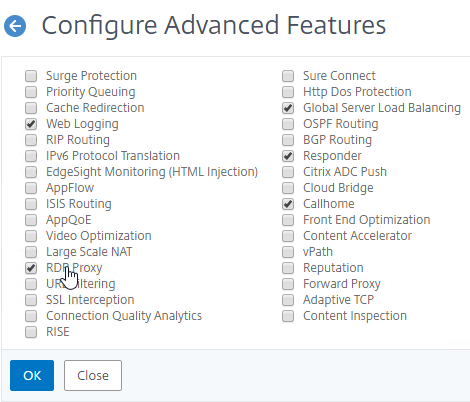
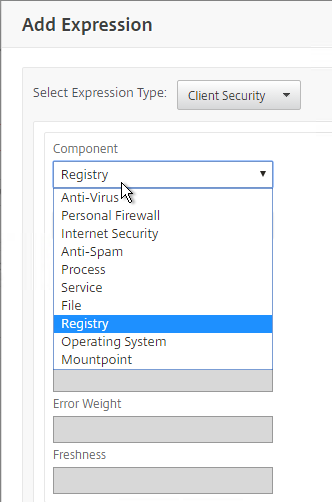
Citrix Gateway supports Client Security Expressions (Endpoint Analysis expressions) at four different locations:
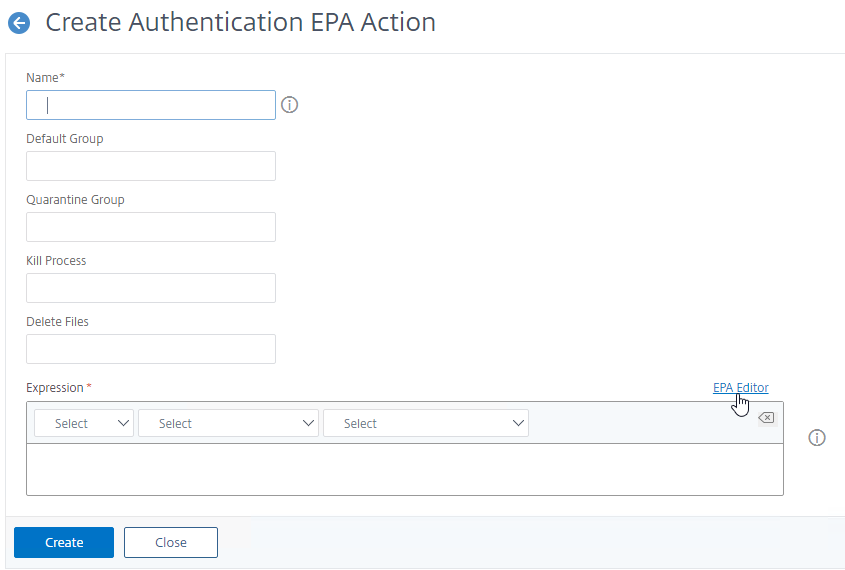
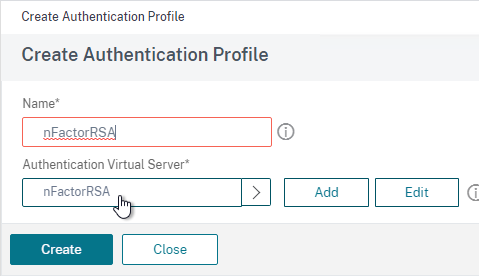
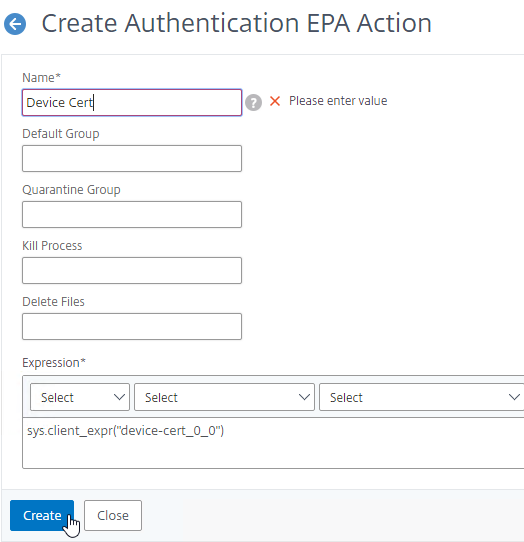
- nFactor (Authentication Virtual Server) Advanced EPA Policy and EPA Action – this is the preferred method in ADC 13 and newer since Classic EPA is supposed to be removed in ADC 13.1 and newer. See nFactor EPA for details.
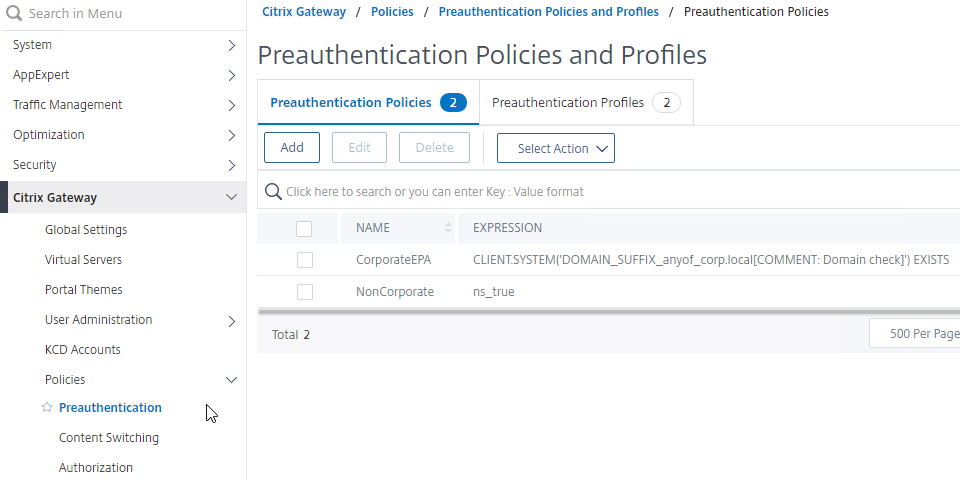
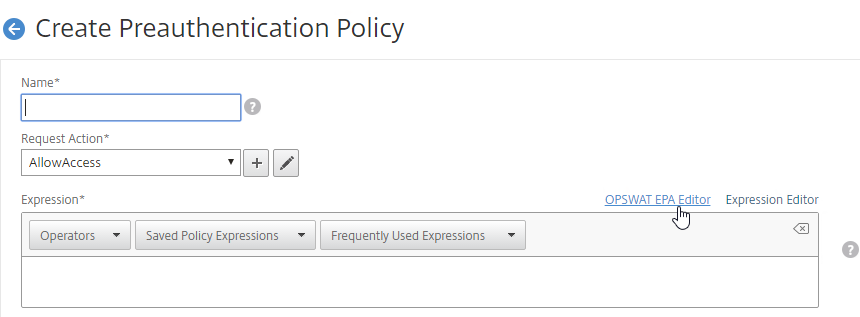
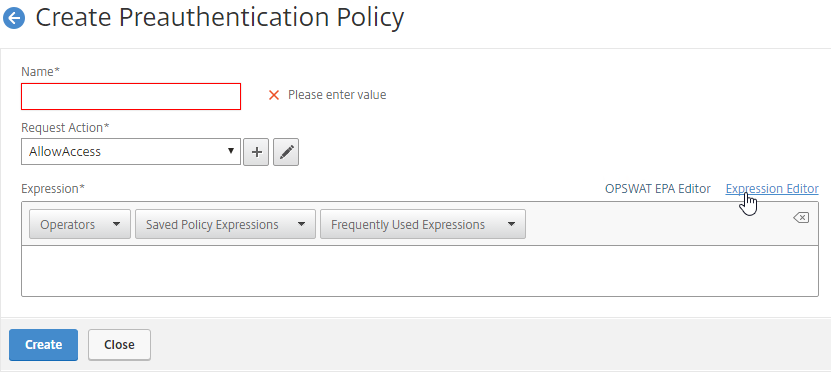
- Classic Preauthentication Policy Expression
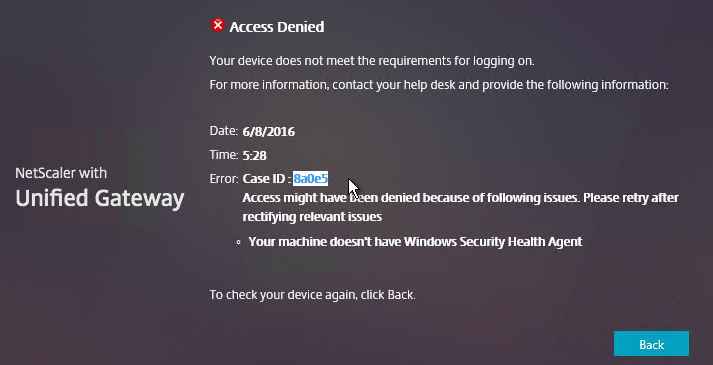
- If the EPA Scan succeeds, then the user is allowed to login.
- If the EPA Scan fails, then the user is not allowed to login.
- Preauthentication Policies are bound to Citrix Gateway Virtual Servers only, and thus applies to all users of that Virtual Server.
- Classic Session Policy Expression – Note: Advanced Session Policies do not support EPA expressions. Use nFactor instead.
- This type of EPA Scan is configured in the Session Policy Expression, not the Session Profile.
- If the EPA Scan succeeds, then the settings in the Session Profile are applied to the session.
- If the EPA Scan fails, then the Session Profile is ignored. Other Session Policies expressions are still evaluated. Remember, Session Policy/Profiles merge, so all applicable Session Policies must be considered.
- A limitation of this EPA method is that nothing negative happens. Instead, you typically design higher priority number (lower priority) Session Policies with restrictive settings so that if the EPA Scans fail, then users still get something. For example, you can configure your highest priority number Session Policy/Profile with StoreFront (ICA Proxy) only. In the lower priority number Session Policies/Profiles, VPN might be enabled, but only if the EPA scan succeeds. More restrictive Session Profiles usually uncheck Client Choices, and enable Clientless Access or ICA Proxy.
- This method of EPA Scans is used in SmartAccess and SmartControl configurations.
- EPA expressions are not supported in Default Syntax, so you’ll need to use Classic Syntax instead.
- Session Profile > Security tab > Advanced Settings > Client Security Check String
- If the EPA Scan succeeds, add the user to the listed Authorization AAA Groups.
- If the EPA Scan fails, add the user to the selected Quarantine Group, and remove the user from all other AAA Groups.
- If Quarantine Group is not defined, then prevent SSL VPN. Other methods of connecting (Clientless, StoreFront), still work.
- Assigning EPA scans to Session Policies and Session Profiles is also known as Post-Authentication EPA Scans.
- If Endpoint Analysis is configured anywhere, then an Endpoint Analysis plug-in is downloaded to the Windows or Mac client.
Prerequisites
Gateway Universal Licenses
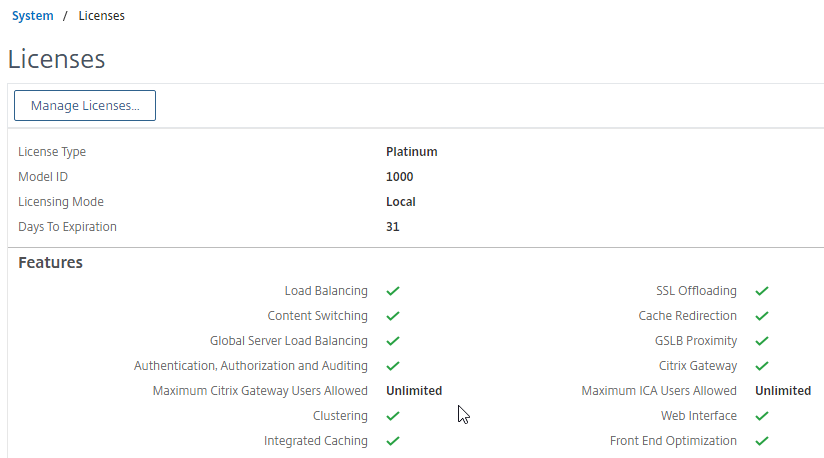
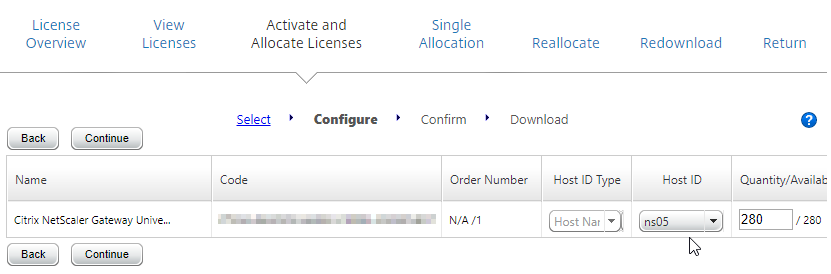
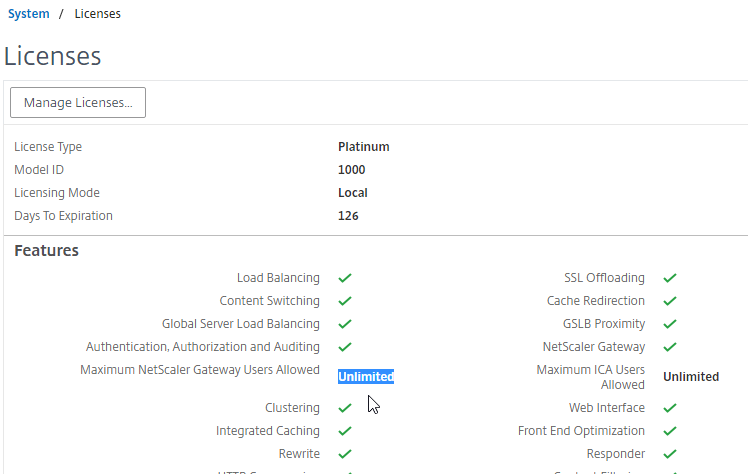
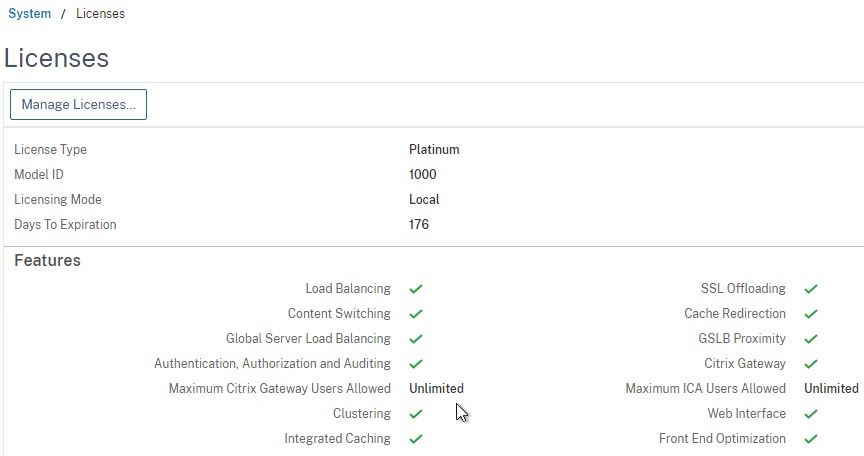
Except for ICA Proxy, all Citrix Gateway connection methods require a Citrix Gateway Universal License for each concurrent session. Go to System > Licenses.
On the right, make sure Maximum Citrix Gateway User licenses are installed. Most Citrix ADC Editions come with built-in licenses. For example, Citrix ADC Premium Edition comes with Unlimited Gateway licenses.
DNS Name Servers
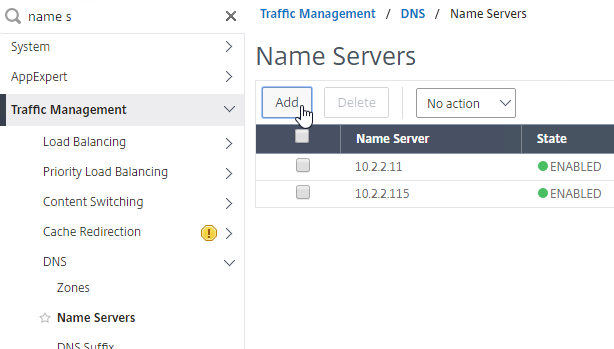
DNS usually needs to function across the VPN tunnel. Go to Traffic Management > DNS > Name Servers to add DNS servers.
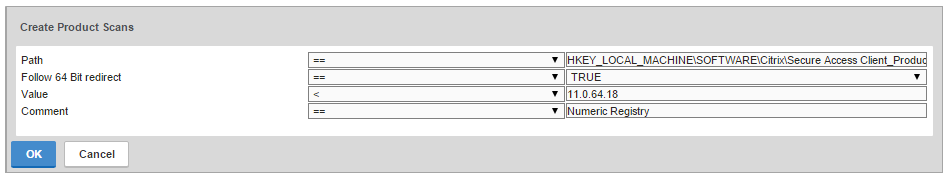
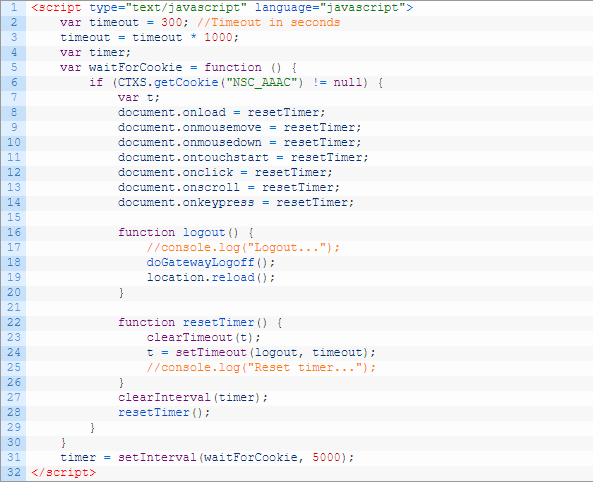
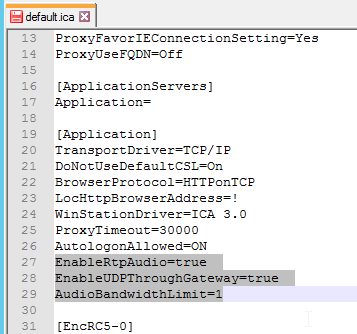
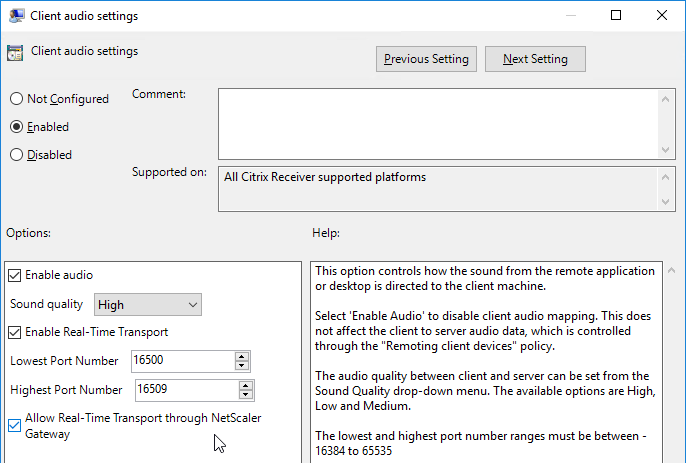
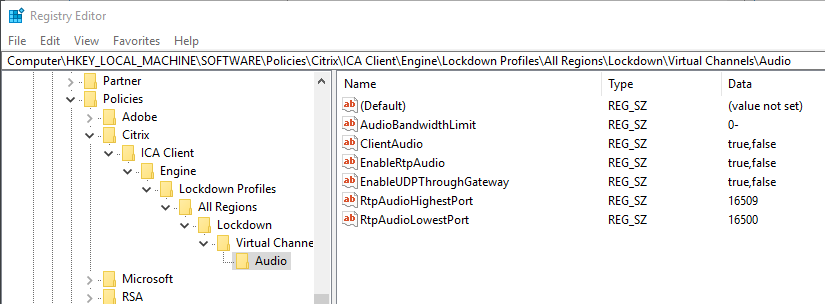
In ADC 13.0 build 71.44 and newer, VPN plug-in for Windows supports Secure DNS update. This feature is disabled by default. To enable it, create the following on the client device: (source = 13.0-71.44 release notes) 💡
- HKEY_LOCAL_MACHINE\SOFTWARE\Citrix\Secure Access Client\secureDNSUpdate value of type REG_DWORD and set it to 1.
- When you set the value to 1, the VPN plug-in tries the unsecure DNS update first. If the unsecure DNS update fails, the VPN plug-in tries the secure DNS update.
- To try only the secure DNS update, you can set the value to 2.
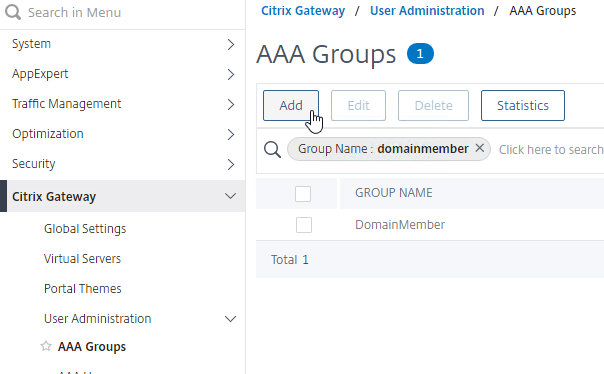
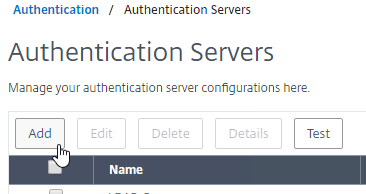
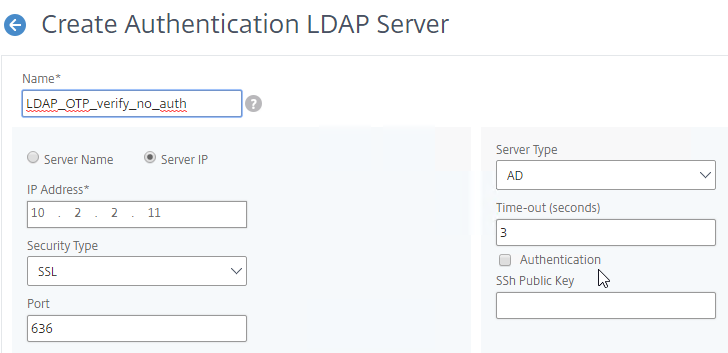
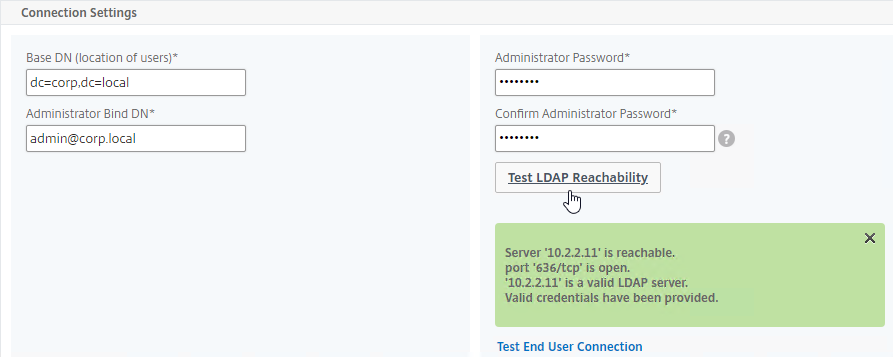
AAA Groups
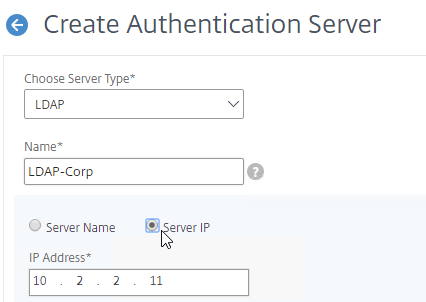
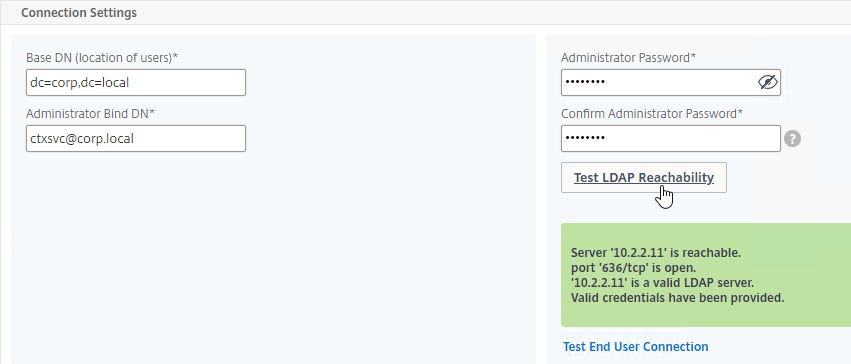
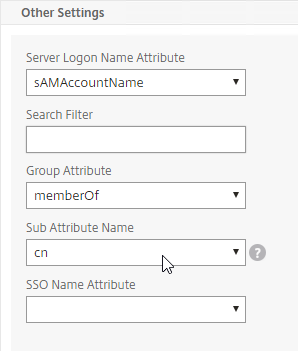
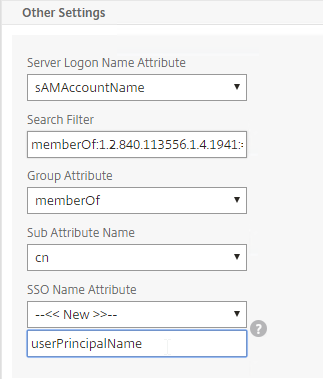
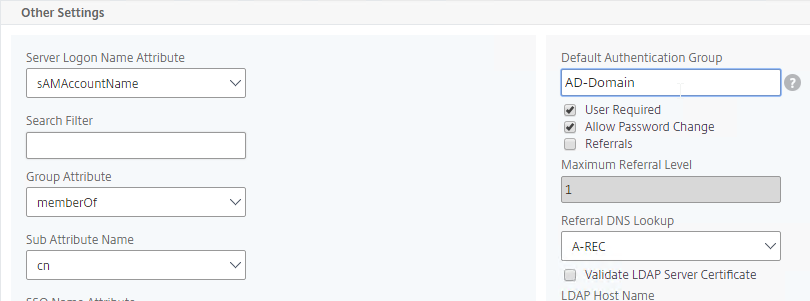
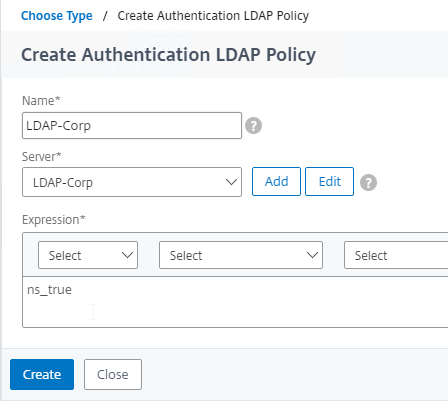
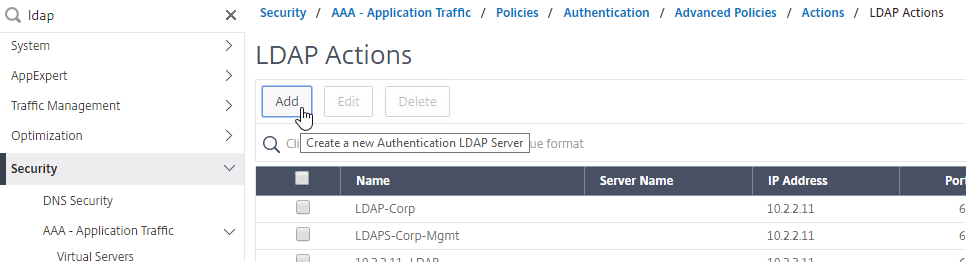
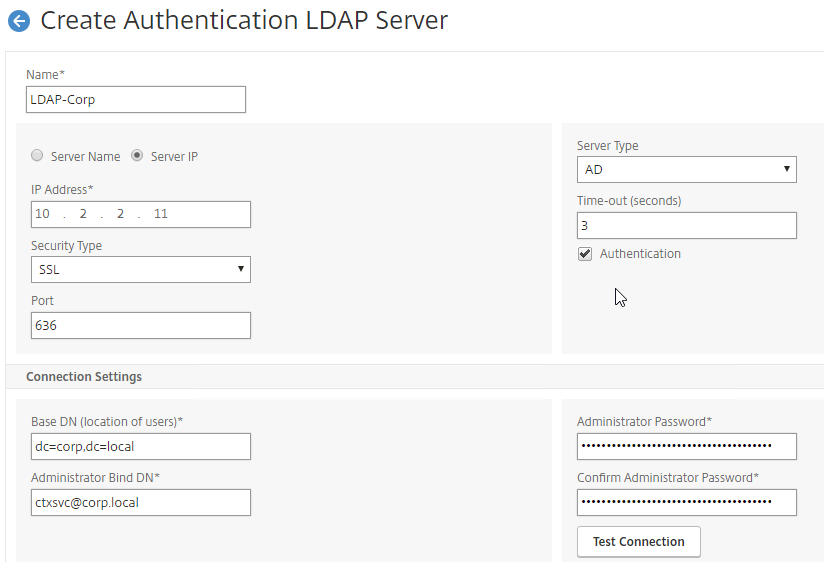
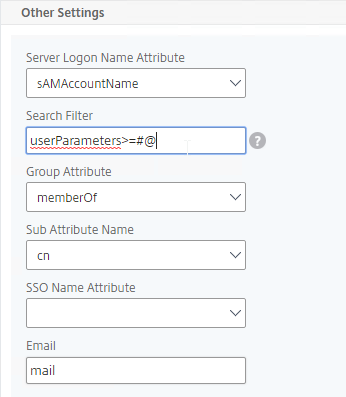
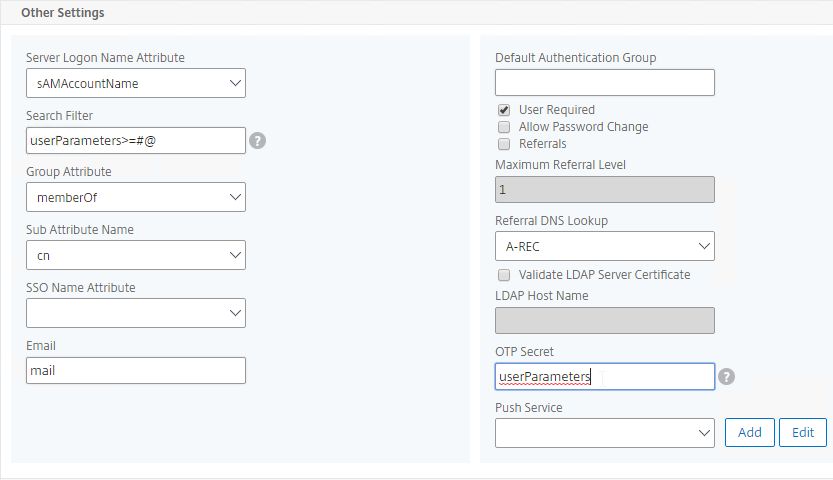
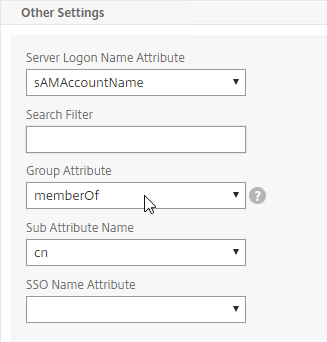
- Edit your LDAP Policy/Server, and make sure Group Extraction is configured. Configure the Group Attribute and the Sub Attribute Name. This causes Citrix ADC to extract the user’s AD groups when the user logs in using LDAP.
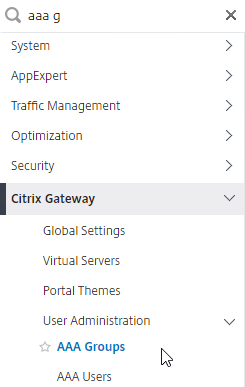
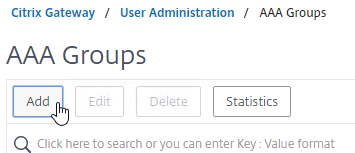
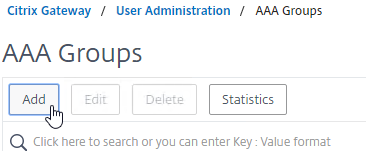
- Go to Citrix Gateway > User Administration > AAA Groups.
- On the right, click Add.
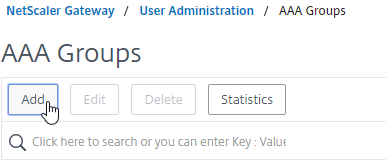
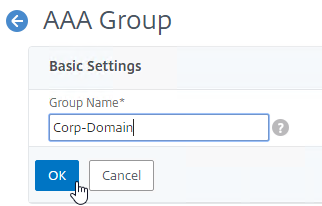
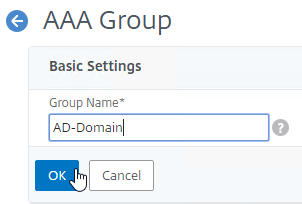
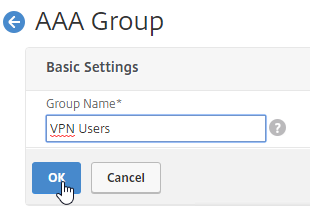
- Enter a case sensitive group name that matches the group name in Active Directory. Click OK.
- On the right, in the Advanced Settings column, you can see the types of objects that can be bound to AAA Groups. These objects are detailed later in this post.
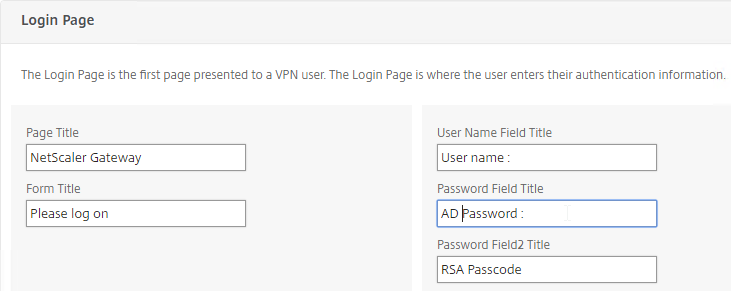
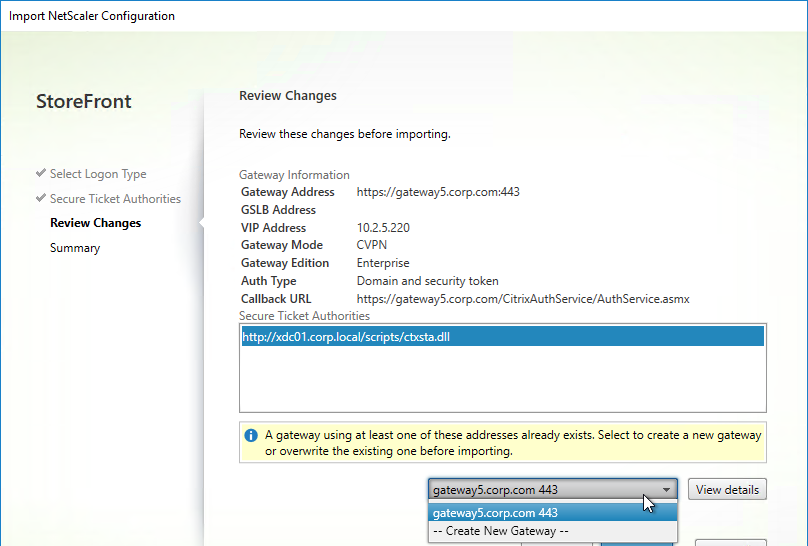
Create Session Profile
To enable SSL VPN: first create the Session Profile. Then create a Session Policy.
You can create multiple Session Policies/Profiles with different settings. Then you can bind these Session Policies to AAA groups and/or Citrix Gateway Virtual Servers. The Session Profiles are merged, and if conflicts, lower priority bind points win.
To enable SSL VPN in a Session Profile:
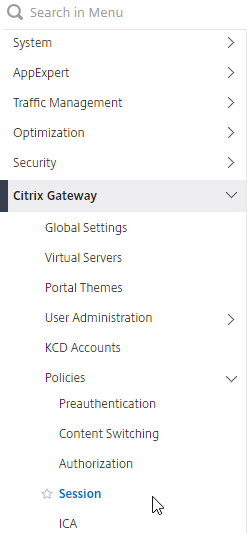
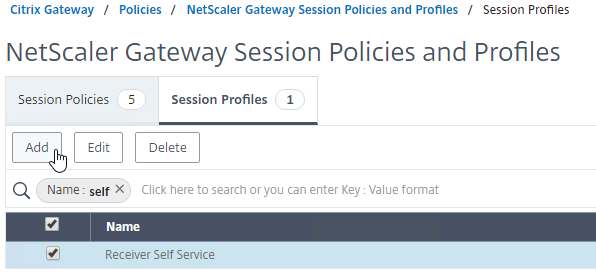
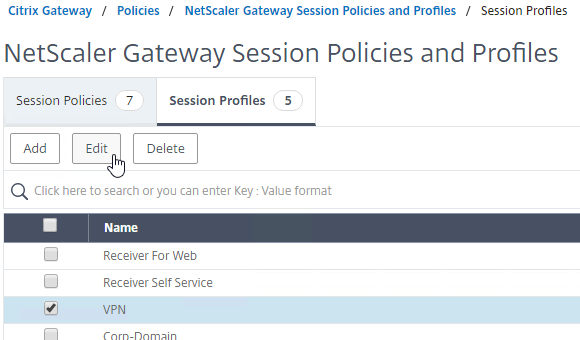
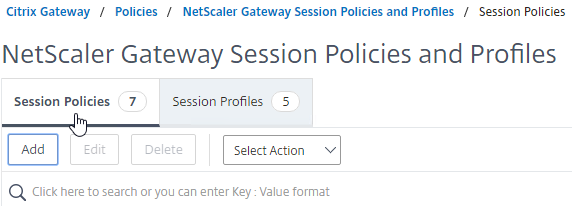
- On the left, expand Citrix Gateway, expand Policies, and click Session.
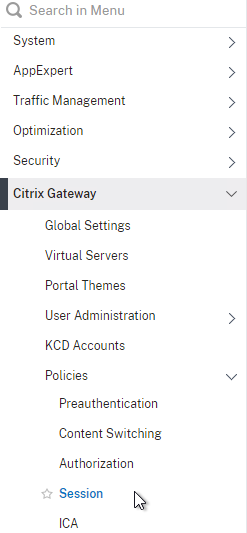
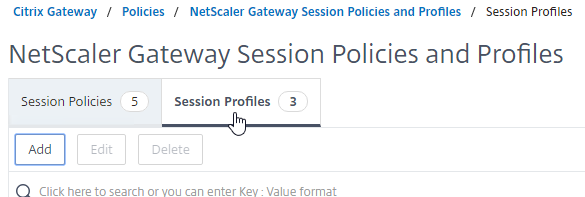
- On the right, switch to the Session Profiles tab, and click Add.
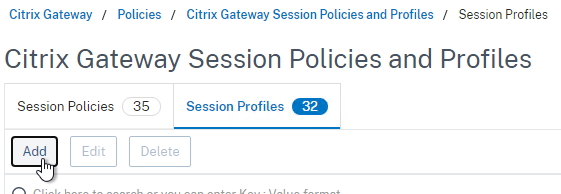
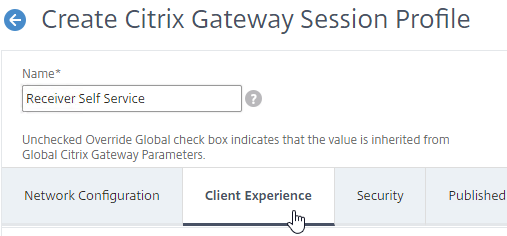
- Name the profile VPN or similar.
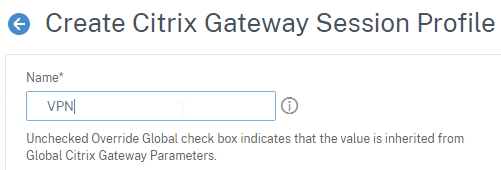
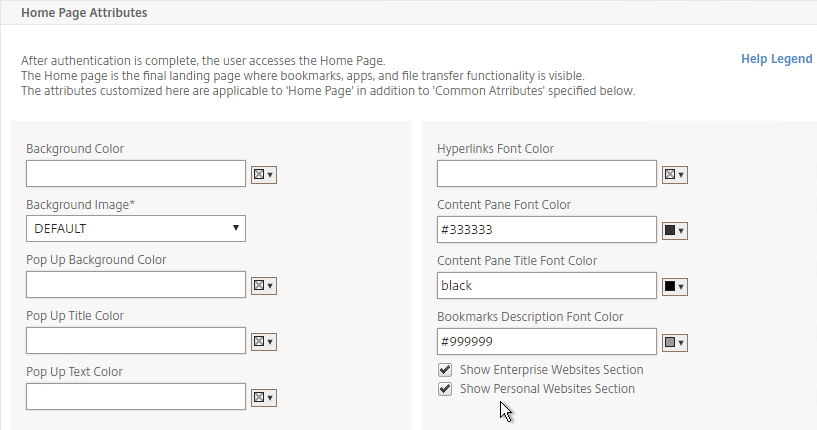
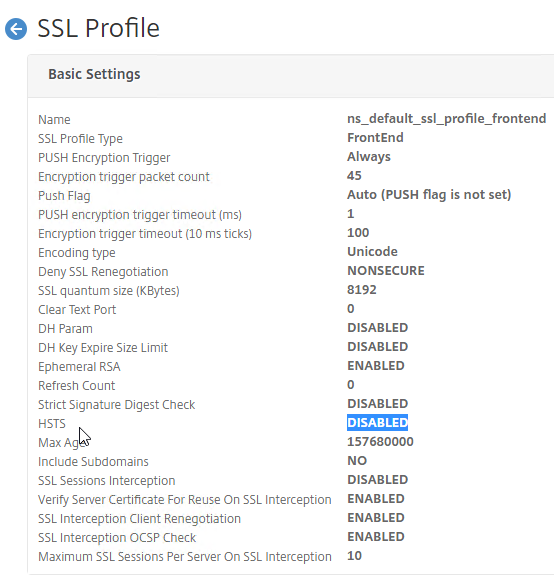
- In Session Profiles, every field has an Override Global checkbox to the right of it. If you check this box next to a particular field, then you can configure that field, and the field in this session profile will override settings configured globally (Citrix Gateway > Global Settings > Change Global Settings), or in a lower priority (higher priority number) session policy.
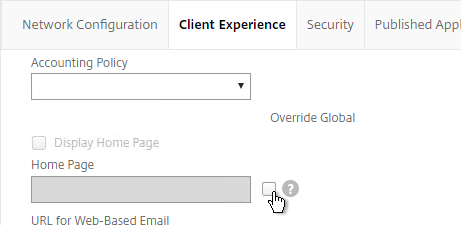
Network Configuration tab
- In the Session Profile, switch to the Network Configuration tab.
- You will find a setting that lets you select a DNS Virtual Server. Or if you don’t select anything, then the tunnel will use the DNS servers configured under Traffic Management > DNS > Name Servers.
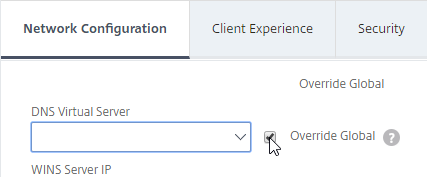
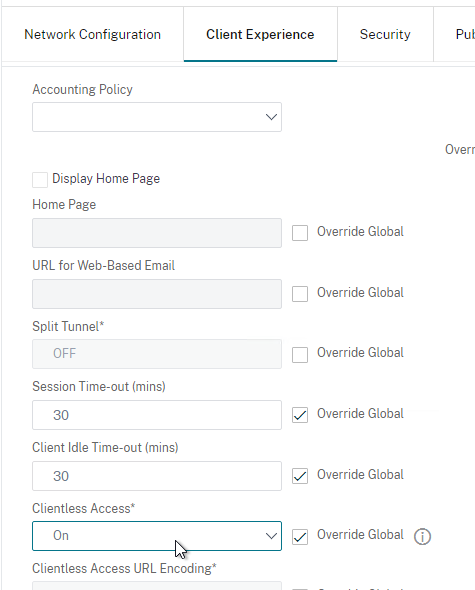
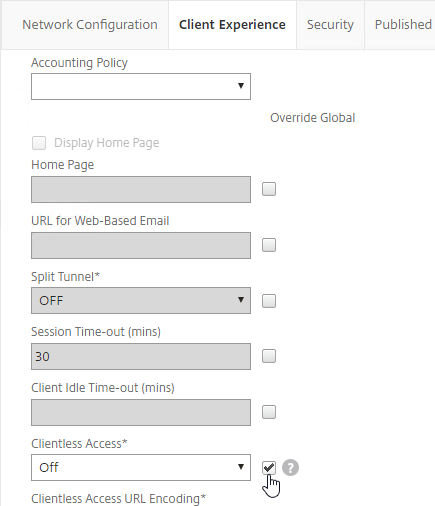
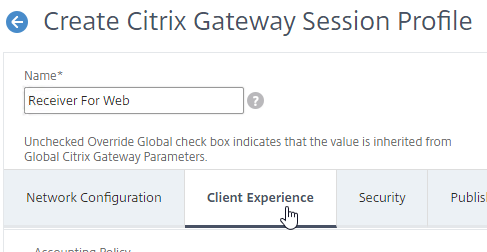
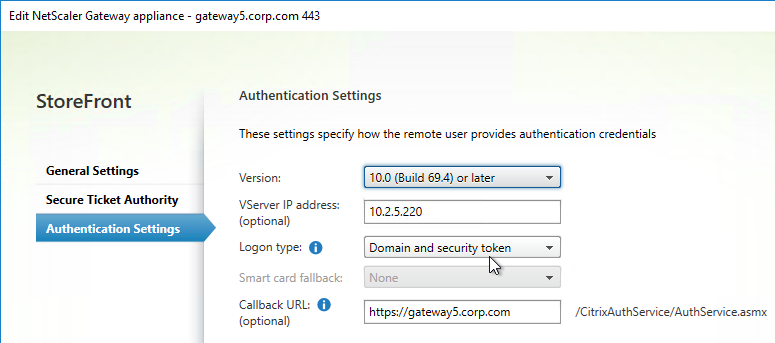
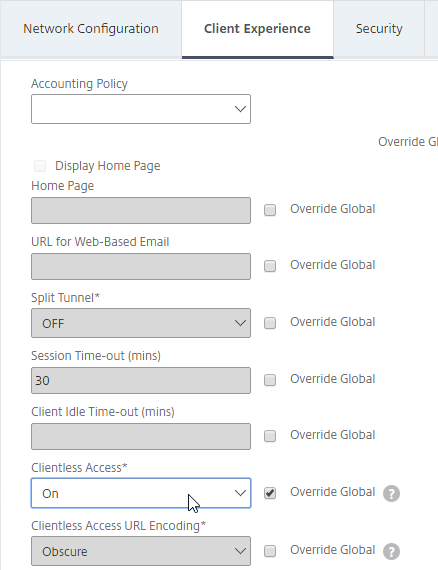
Client Experience Tab
- In the Session Profile, switch to the Client Experience tab. This tab contains most of the Citrix Gateway VPN settings.
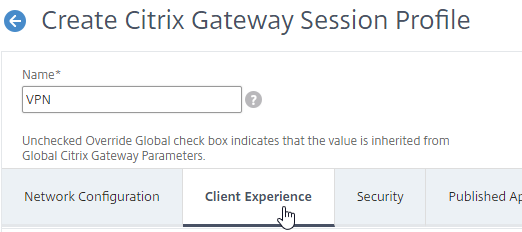
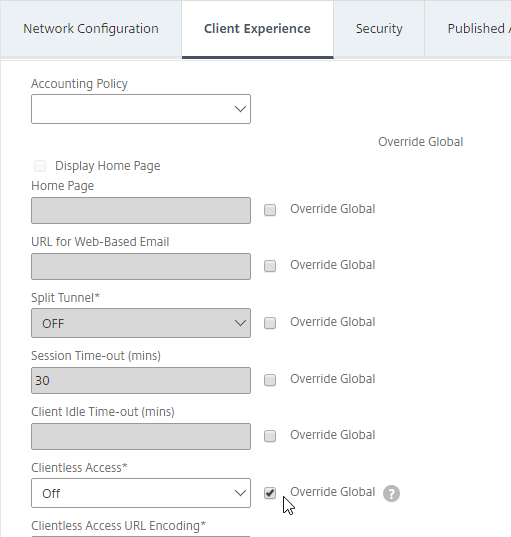
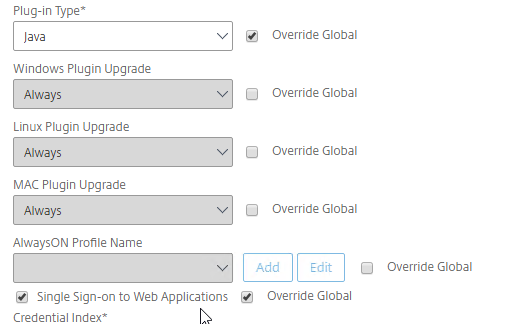
- Override Plug-in Type, and set it to Windows/Mac OS X.
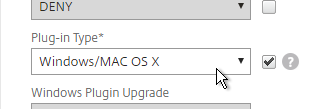
- On the Client Experience tab, override Split Tunnel and make your choice. Setting it to OFF will force all traffic to use the tunnel. Setting it to ON will require you to create Intranet Applications so the Citrix Gateway Plug-in will know which traffic goes through the tunnel, and which traffic goes directly out the client NIC (e.g. to the Internet). REVERSE means all traffic goes through the tunnel except for the addresses defined in Intranet Applications.
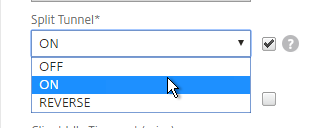
- On the Client Experience tab, there are timers that can be configured. Global Settings contains default timers, so you might want to configure this Session Profile to override the defaults and increase the timeouts. See Configuring Time-Out Settings at Citrix Docs for details.
- Client Idle Time-out is a Citrix Gateway Plug-in timer that disconnects the session if there is no user activity (mouse, keyboard) on the client machine.
- Session Time-out is a Citrix Gateway timer that disconnects the session if there is no network activity for this duration.
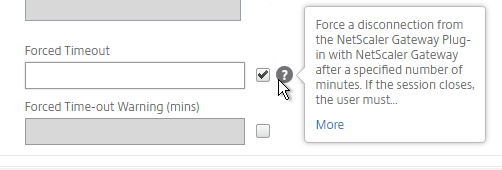
- In addition to these two timers, on the Network Configuration tab, under Advanced Settings…
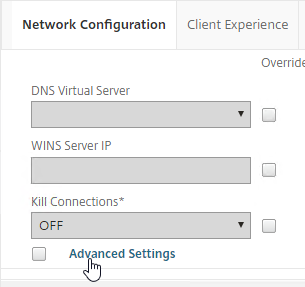
- There’s a Forced Timeout setting.
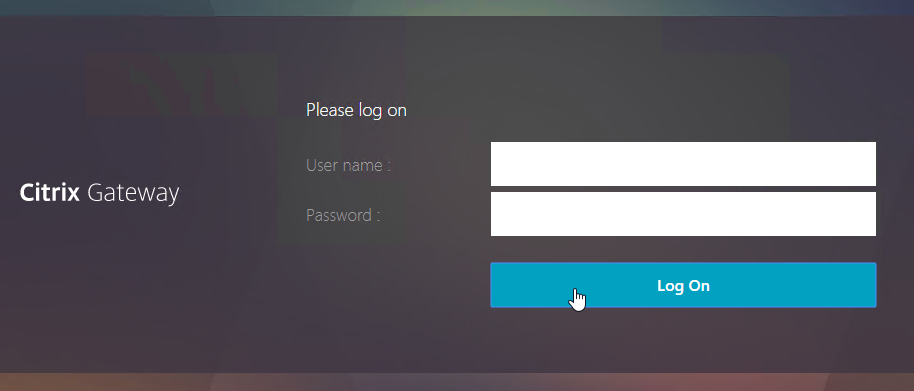
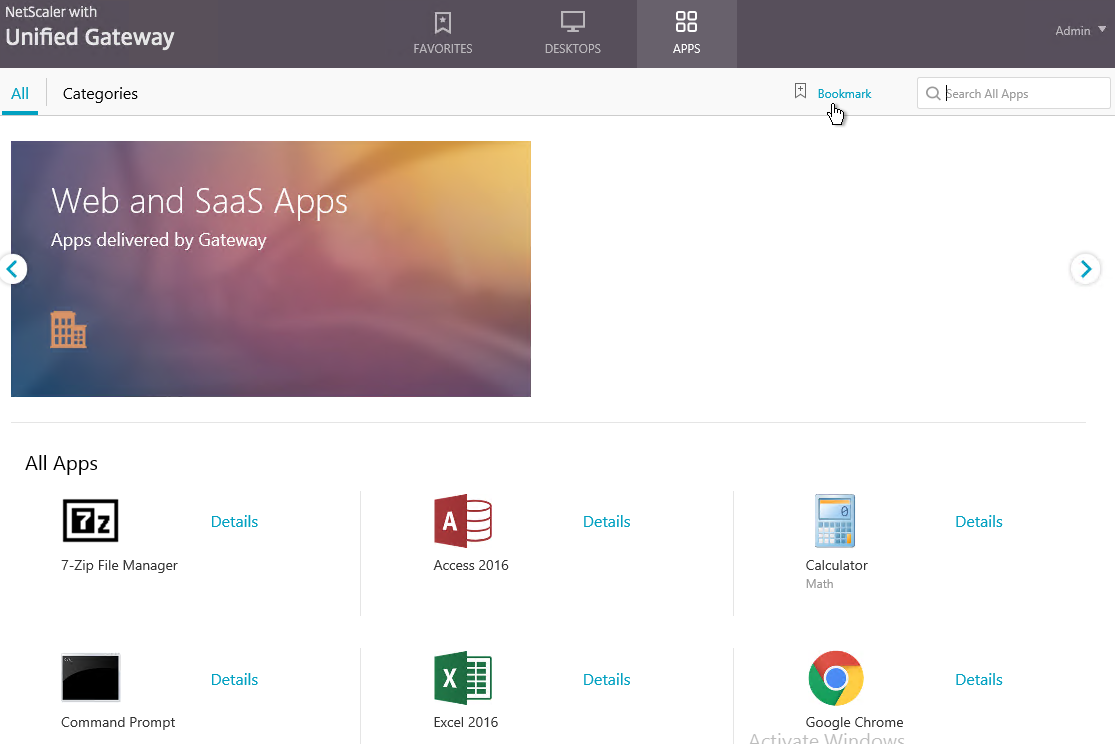
- By default, once the VPN tunnel is established, a portal page appears containing Gateway Bookmarks, and StoreFront published icons. An example of the portal page in the RfWebUI theme is shown below:
- The X1 theme is shown below:
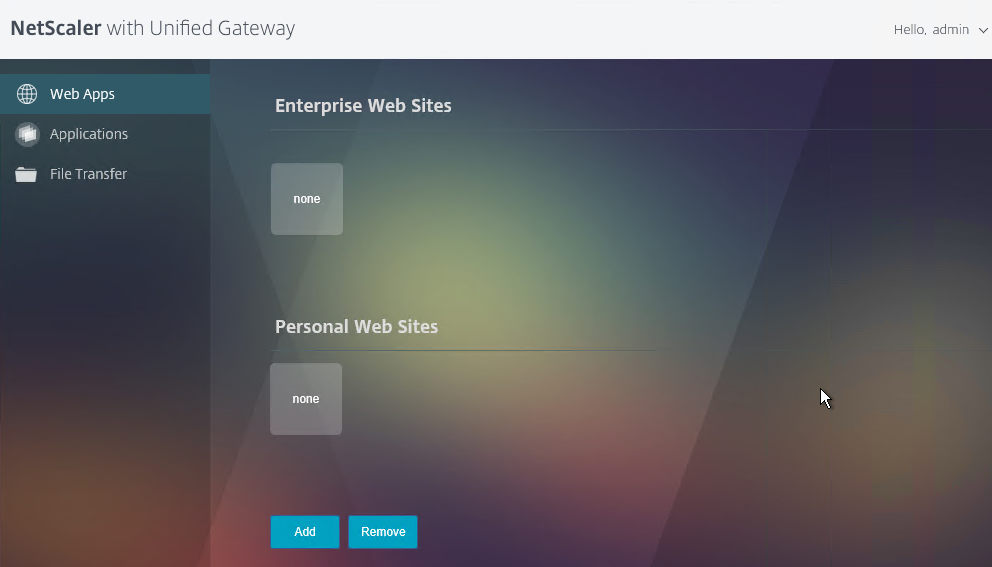
- The X1 theme is shown below:
- On the Client Experience tab, the Home Page field lets you override the the default portal page, and instead display a different webpage (e.g. Intranet). This homepage is displayed after the VPN tunnel is established (or immediately if connecting using Clientless Access).
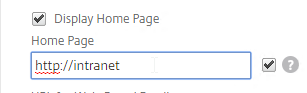
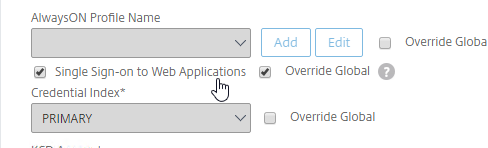
- Citrix Gateway can automatically start the VPN tunnel whenever the user is remote. This method only starts the VPN Tunnel after the user is logged into Windows.
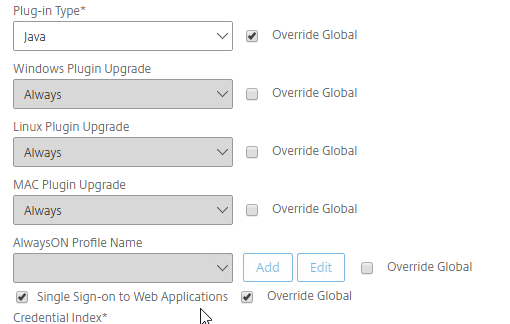
- On the Client Experience tab, click the plus icon next to AlwaysON Profile Name.
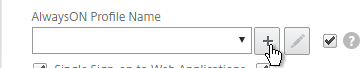
- Give the profile name. Hover over the question marks to see what each of them does.
- Then click Create.
- More info at AlwaysON at Citrix Docs.
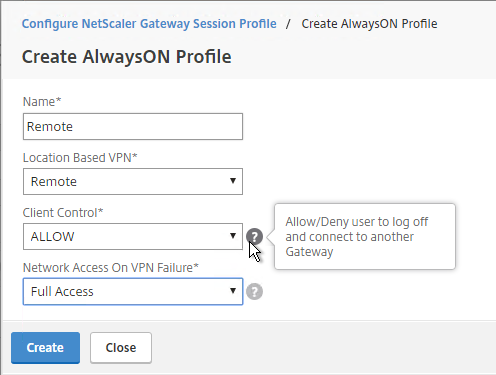
- On the Client Experience tab, click the plus icon next to AlwaysON Profile Name.
- Citrix Gateway 12.1 build 51 and newer also support the VPN Client establishing a tunnel before the user logs into Windows. The pre-logon AlwaysOn Service feature requires certificate-based authentication and registry keys on the client device. See AlwaysOn service for Windows at Citrix Docs. 💡
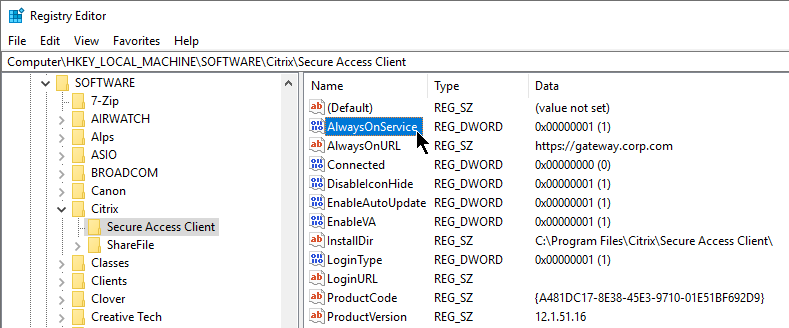
- Additional VPN settings can be found by clicking Advanced Settings near the bottom of the Client Experience tab.
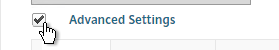
- Under Client Experience > Advanced Settings, on the General tab, there are settings to run a login script at login, enable/disable Split DNS, and enable Local LAN Access. Use the question marks to see what they do.
- Note: if Split Tunnel is OFF, and if Split DNS is set to REMOTE, Citrix Gateway only returns one IP address to DNS queries. This behavior can be changed by following Citrix CTX200243 DNS Query Responds with Only One IP to Client PC When Connected Through NetScaler Gateway Full VPN.
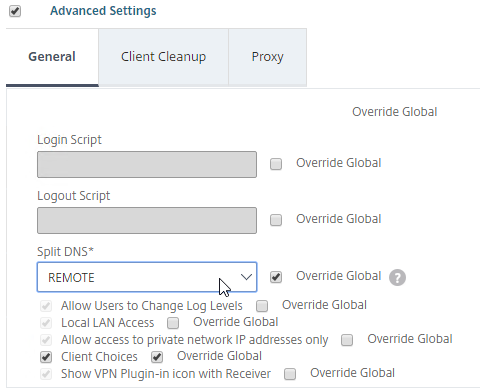
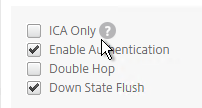
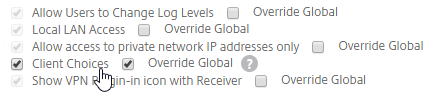
- Under Client Experience > Advanced Settings, on the General tab, is a checkbox for Client Choices. This lets the user decide if they want VPN, Clientless, or ICA Proxy (StoreFront). Without Client Choices, one of the connection methods will occur automatically, depending on what’s enabled.
- An example of Client Choices is shown below:

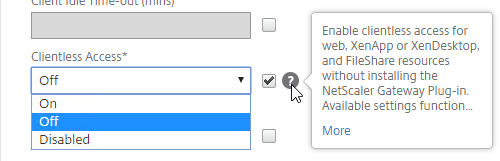
- On the main Client Experience tab, if you enabled Client Choices, you can set Clientless Access to Off to add Clientless to the list of available connection methods in the Client Choices screen.
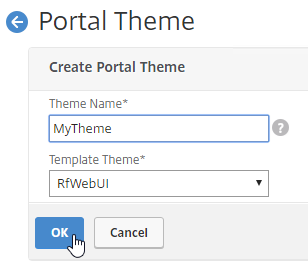
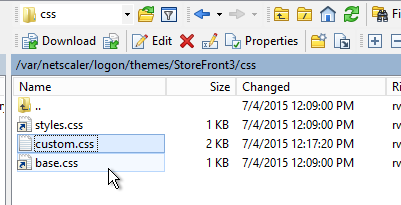
- Clientless Access is difficult to remove from the Client Choices page since you need Clientless Access for StoreFront integration. The following removal instructions were confirmed on a custom Portal Theme based on RfWebUI:
- WinSCP to the Citrix ADC.
- Navigate to
/var/netscaler/logon/themes/<yourThemeName>/css. - Edit the file theme.css.
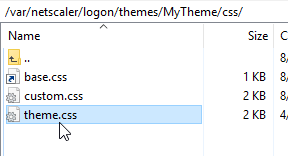
- At the bottom of the file, add the following code: (source = CTP Sam Jacobs at NetScaler Gateway Client Choices – hide/remove Virtual Apps and Desktops at Citrix Discussions.
div.box:nth-child(2) { display:none; } - When you refresh the Client Choices page, the Clientless box should be hidden.
- On the main Client Experience tab, if you enabled Client Choices, you can set Clientless Access to Off to add Clientless to the list of available connection methods in the Client Choices screen.
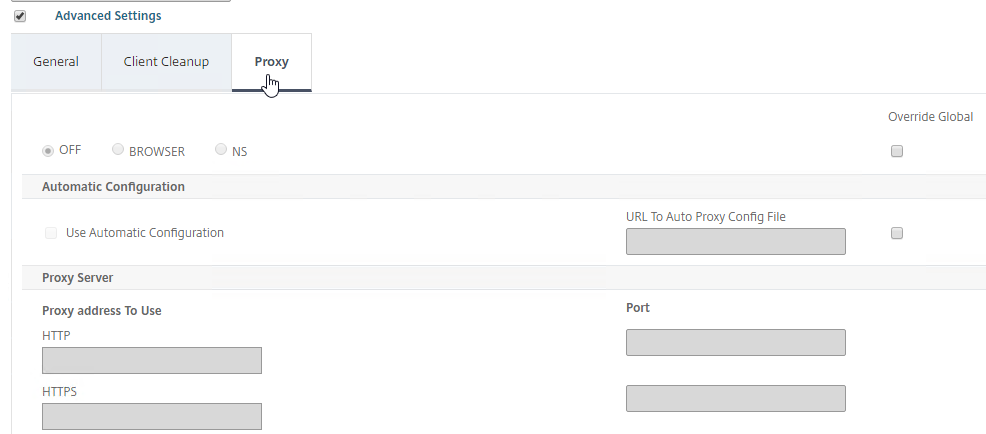
- The Client Experience > Advanced Settings section has additional tabs. A commonly configured tab is Proxy, which allows you to enable a proxy server for VPN users.
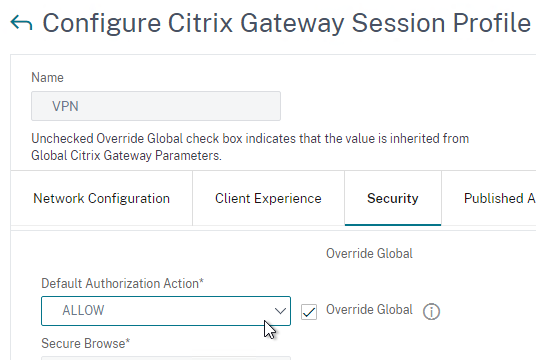
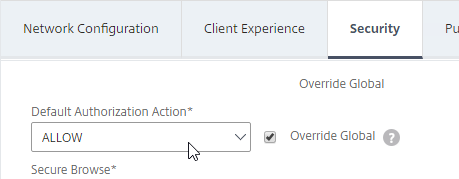
Security Tab
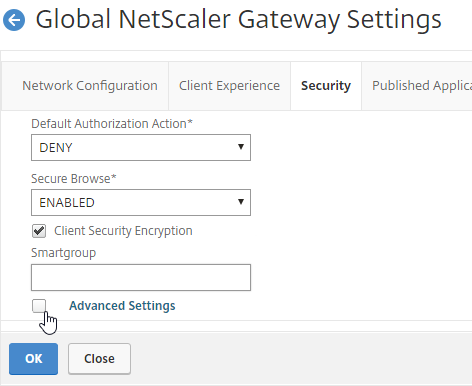
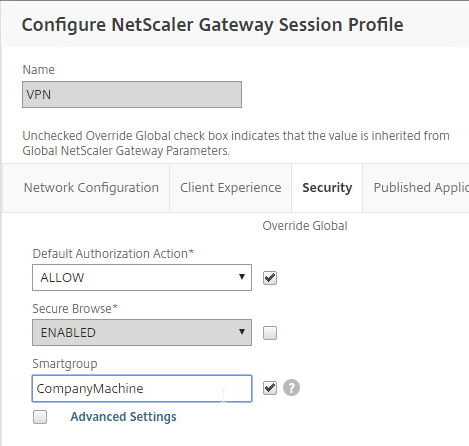
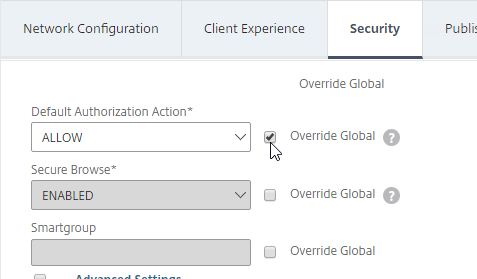
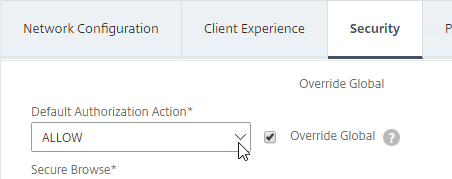
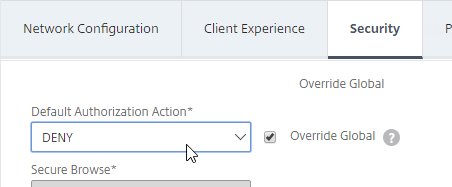
- Back in the main Session Profile, switch to the Security tab.
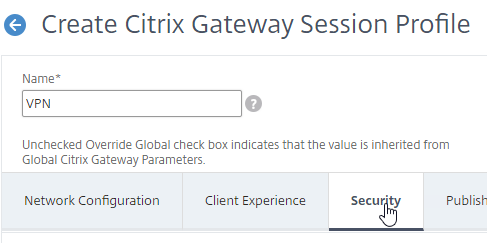
- Set the default authorization to Allow or Deny. If Deny (recommended), you will need to create authorization policies to allow traffic across the tunnel. You can later create different authorization policies for different groups of users.
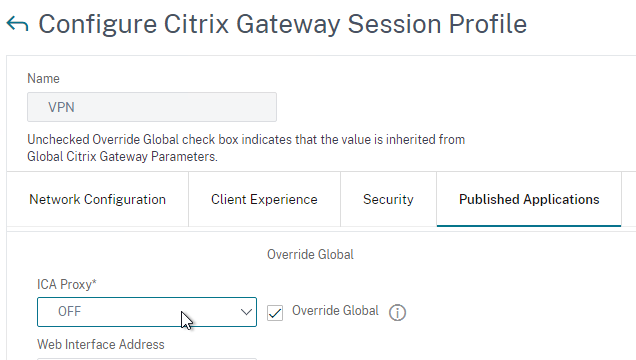
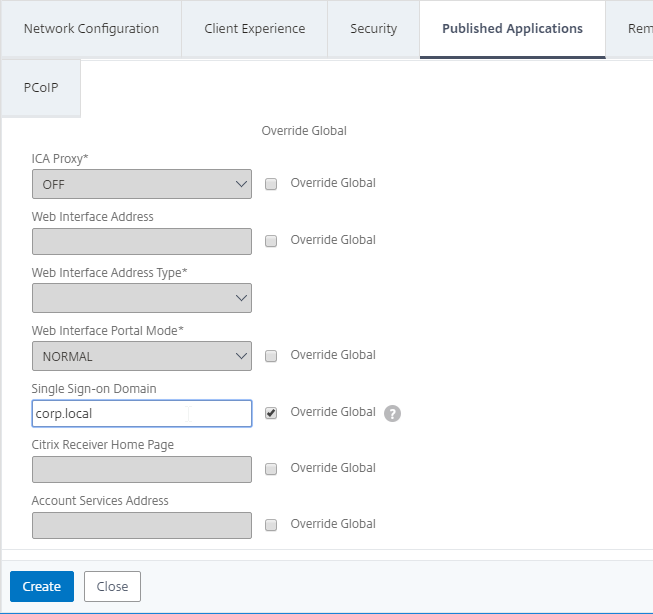
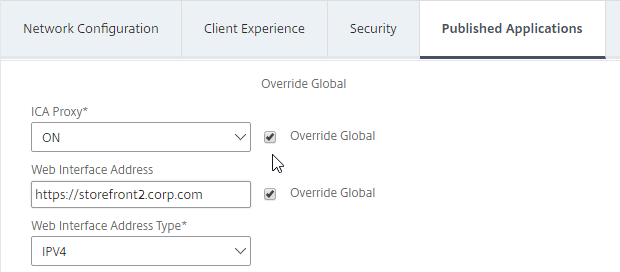
Published Applications Tab
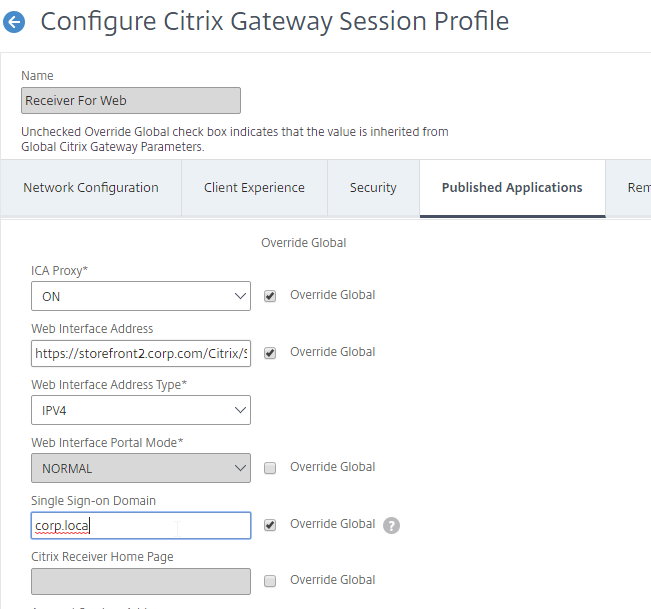
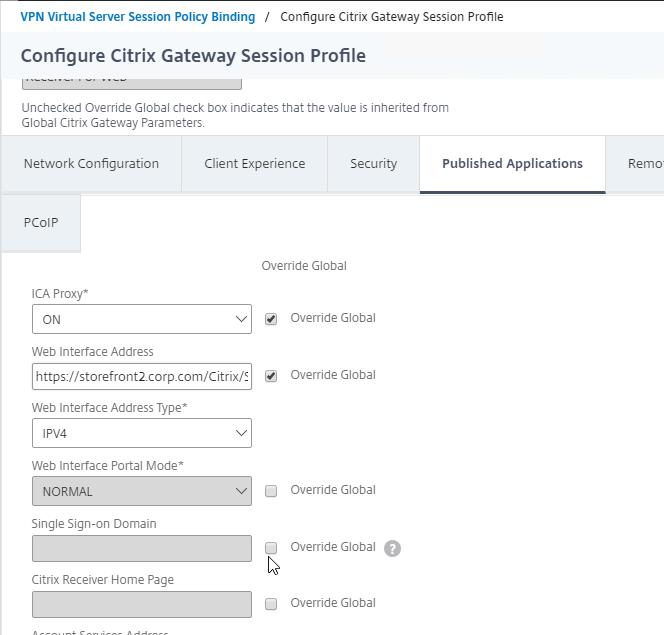
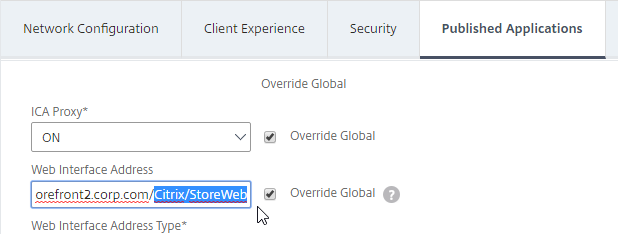
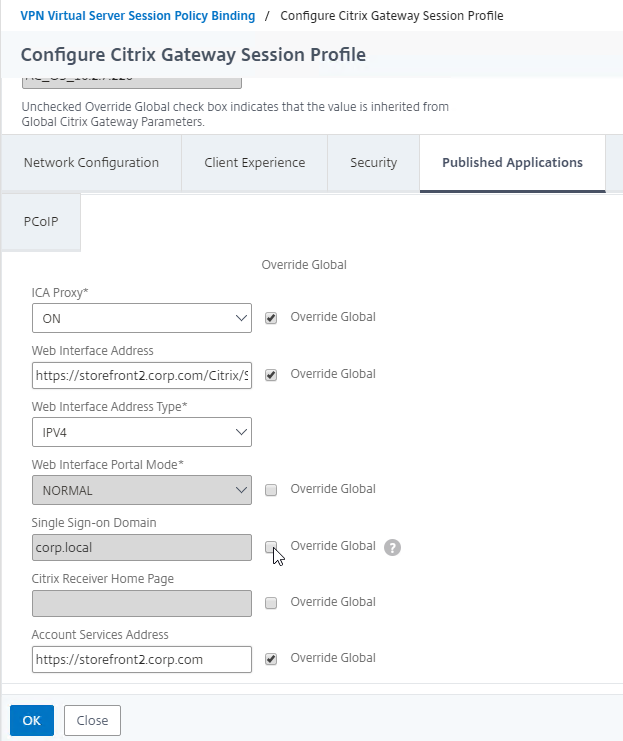
- On the Published Applications tab, set ICA Proxy to Off. This ensures VPN is used instead of ICA Proxy.
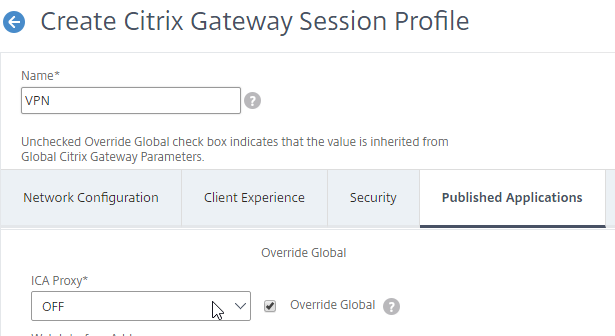
- Configure the Web Interface Address to embed StoreFront into the default Clientless Access portal page.
- Note: for X1 theme, additional iFrame configuration is required on the StoreFront side as detailed below. RfWebUI theme does not need any StoreFront changes.
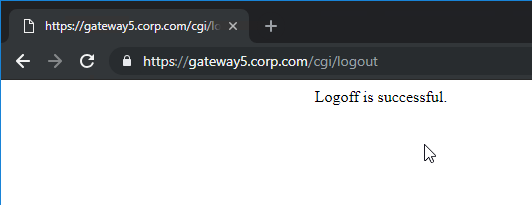
- From Michael Krasnove: if you configured the Session Policy to direct users to StoreFront, but aren’t using RfWebUI, then placing the following code in c:\inetpub\wwwroot\Citrix\StoreWeb\custom\script.js will cause StoreFront to end the VPN tunnel when the user logs off of StoreFront.
var LOGOFF_REDIRECT_URL = 'https://YourGatewayFQDN.com/cgi/logout'; // Prevent the default "logoff" screen from being displayed CTXS.Controllers.LogoffController.prototype._handleLogoffResult = $.noop; CTXS.Extensions.afterWebLogoffComplete = function () { window.location.href = LOGOFF_REDIRECT_URL; };
- See the ICA Proxy post for more information on integrating StoreFront with Citrix Gateway.
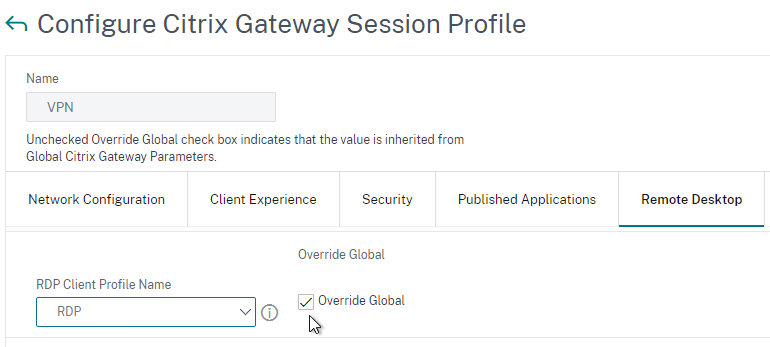
Other Tabs
- The Remote Desktop tab is detailed in the RDP Proxy post.
- The PCoIP tab is detailed in the PCoIP Proxy post.
- Click Create when you’re done creating the Session Profile.
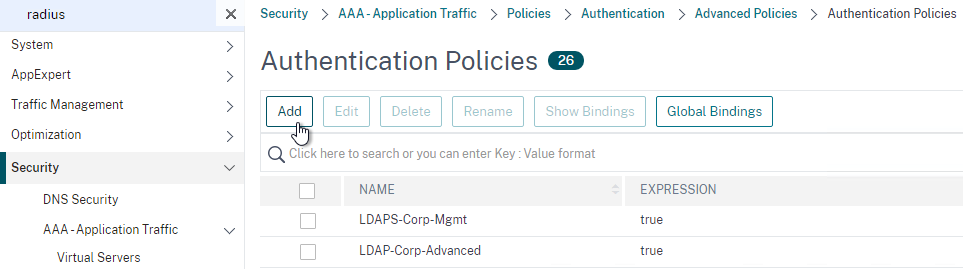
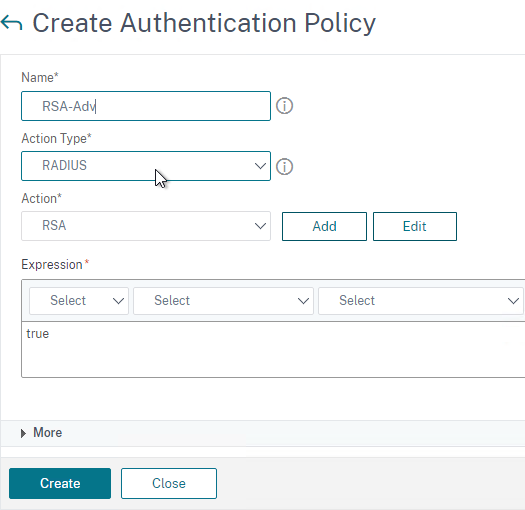
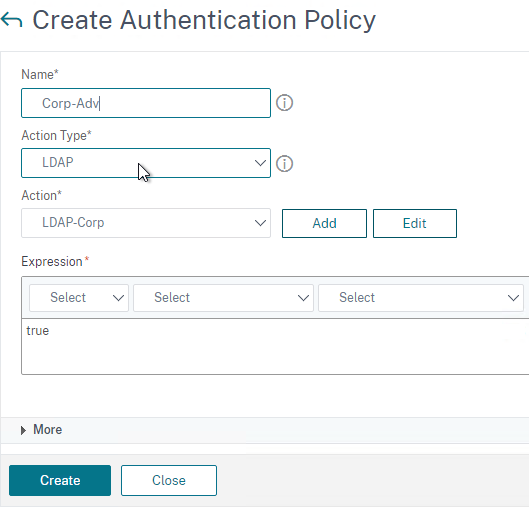
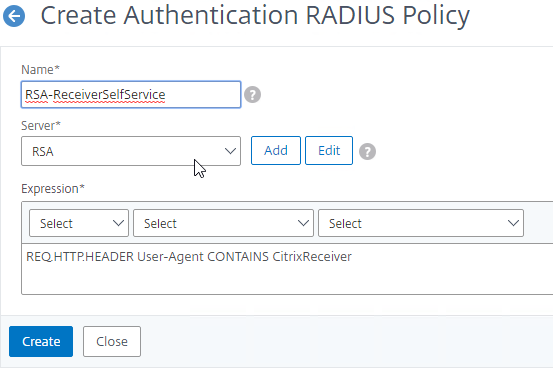
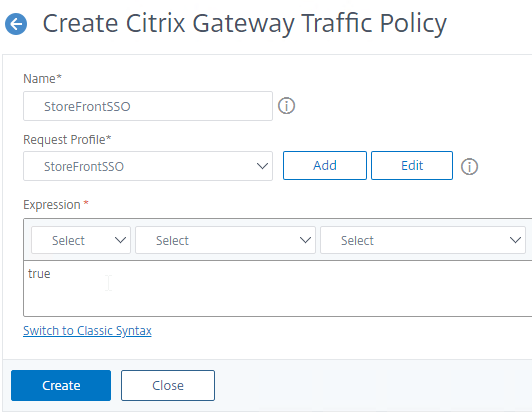
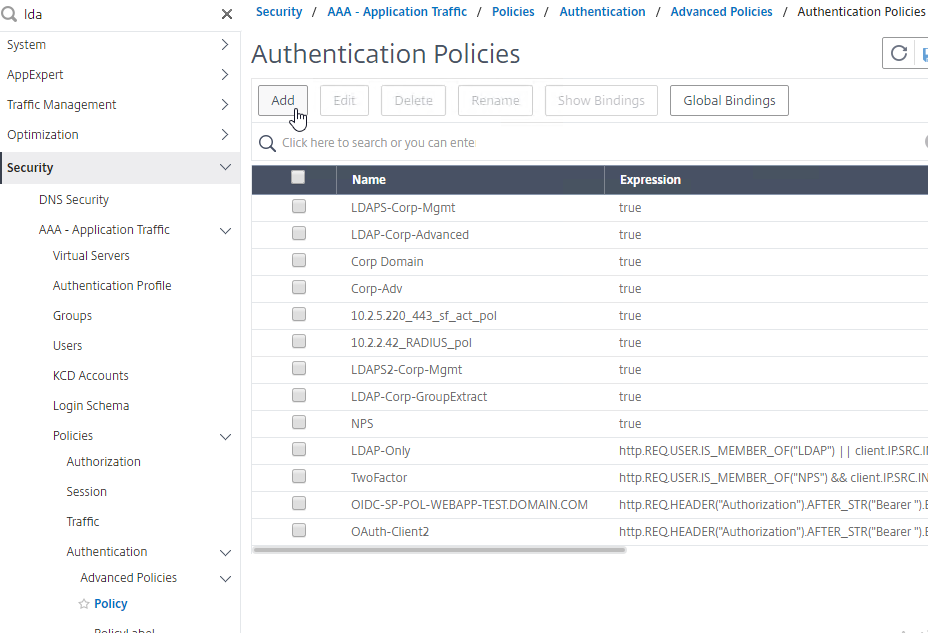
Create Session Policy
Once the Session Profile is created, you need a Session Policy linked to it. The Session Policy contains an expression, where if true, then the Session Profile is applied.
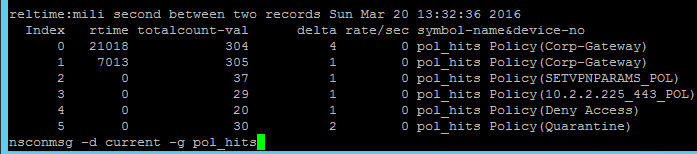
If multiple Session Policies apply to a particular connection, then the settings in the policies are merged. For conflicting settings, the Session Policy with the highest priority (lowest priority number) wins. Session Policies bound to AAA groups only override Session Policies bound to Citrix Gateway Virtual Servers if the AAA group bind point has a lower priority number. In other words, priority numbers are evaluated globally no matter where the Session Policy is bound. You can run the command nsconmsg –d current –g pol_hits to see which Session Policies are applying to a particular connection. See CTX214588 Understanding Session Policy Priority on Different Bind Points.
You can also include Endpoint Analysis expressions in a Session Policy, so that the Session Policy only applies to machines that pass the Endpoint Analysis scan. However, EPA Scans are only supported with Classic Syntax policy expressions, and not with Default Syntax.
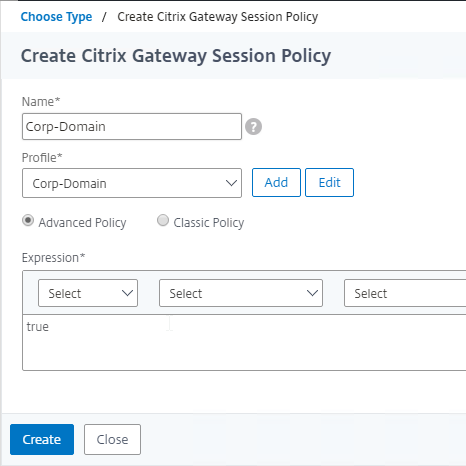
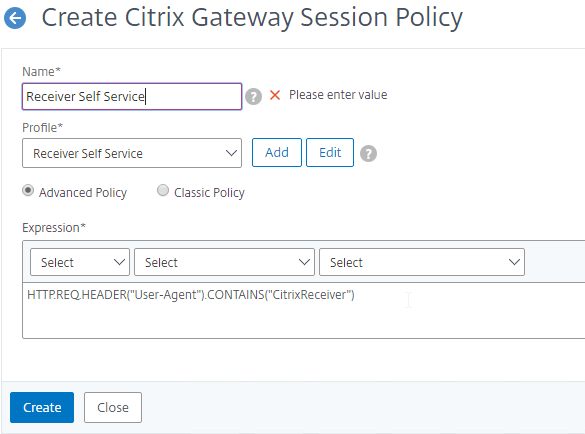
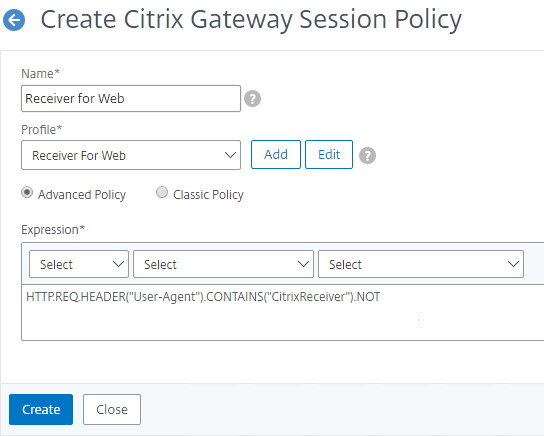
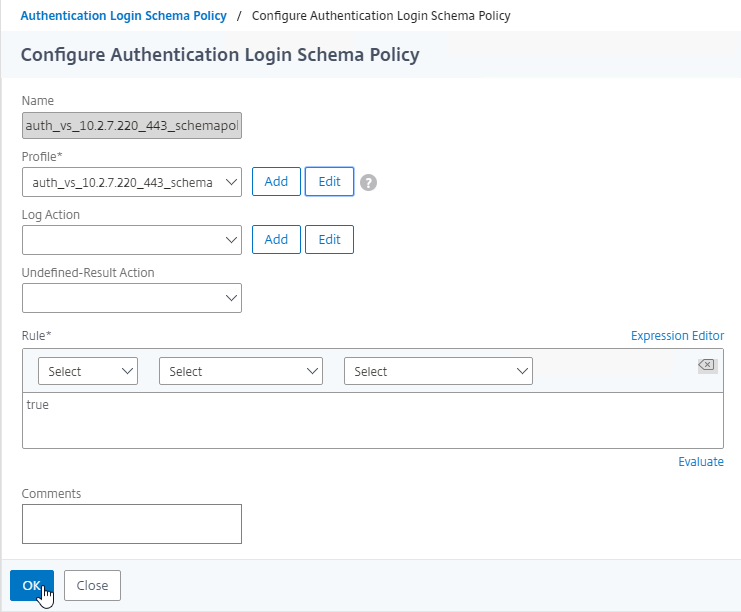
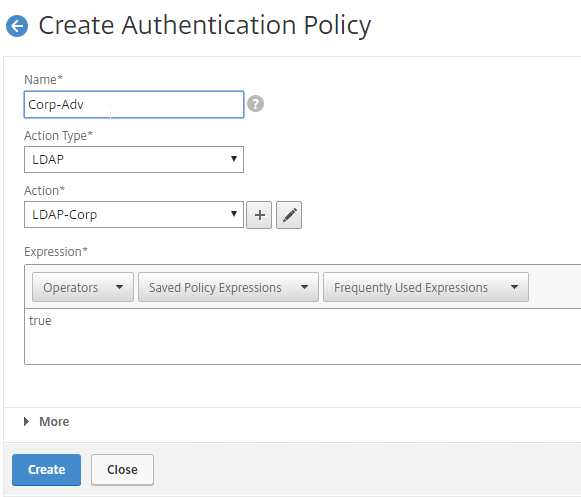
To create a Session Policy that is linked to a Session Profile:
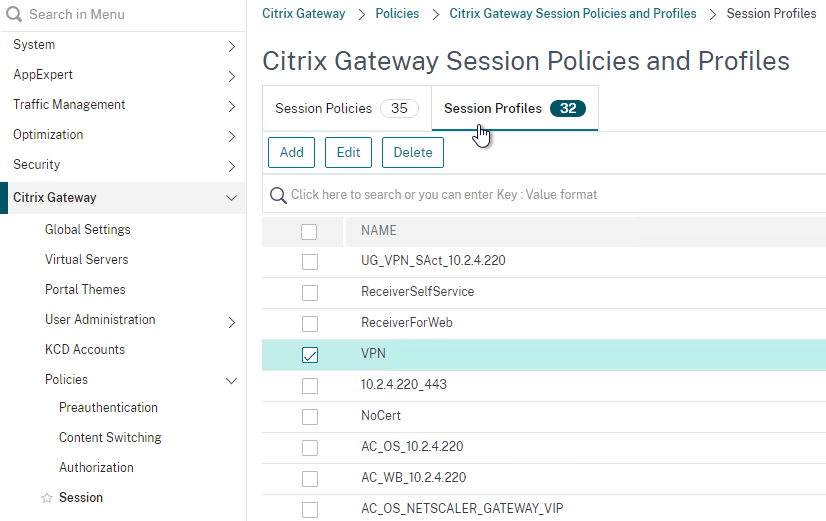
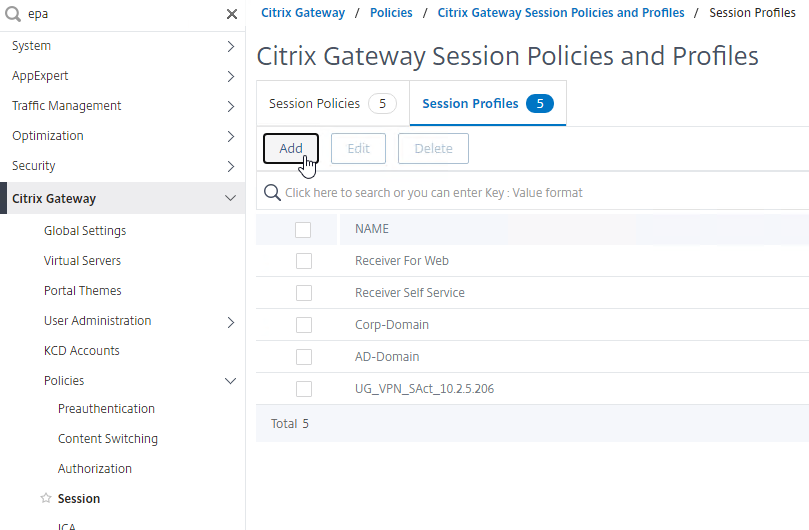
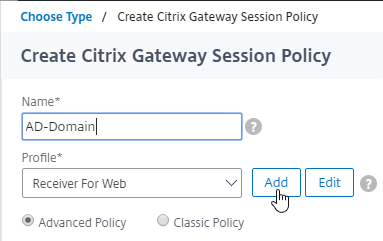
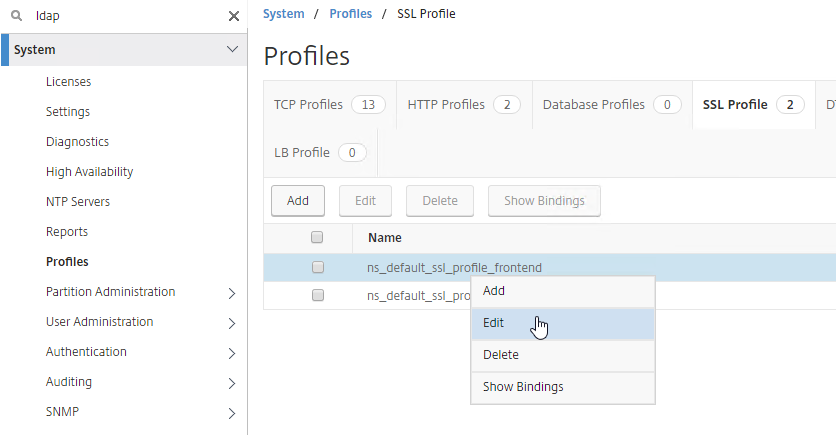
- On the left, go to Citrix Gateway > Policies > Session.
- In the right pane, switch to the Session Policies tab, and click Add.
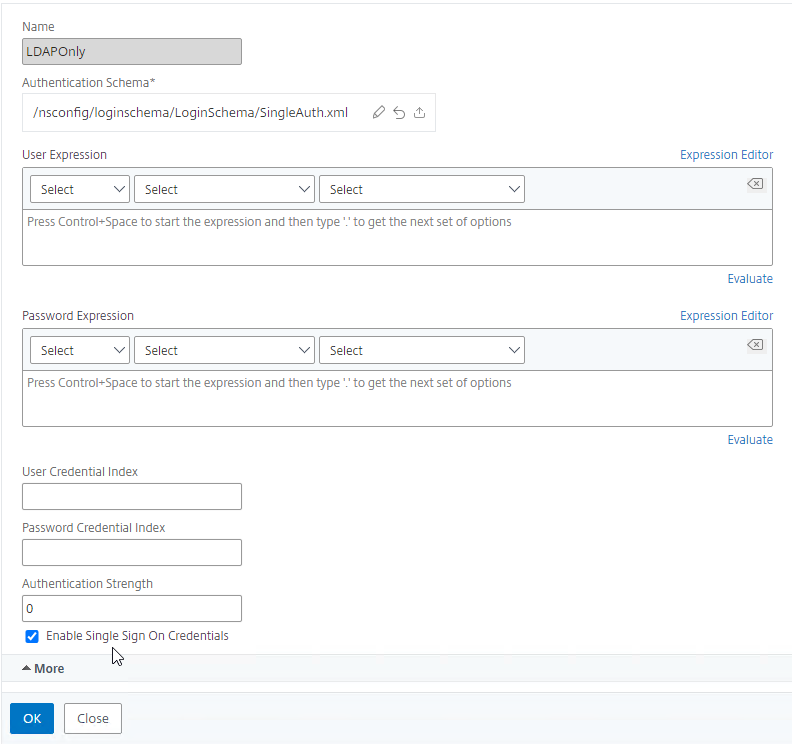
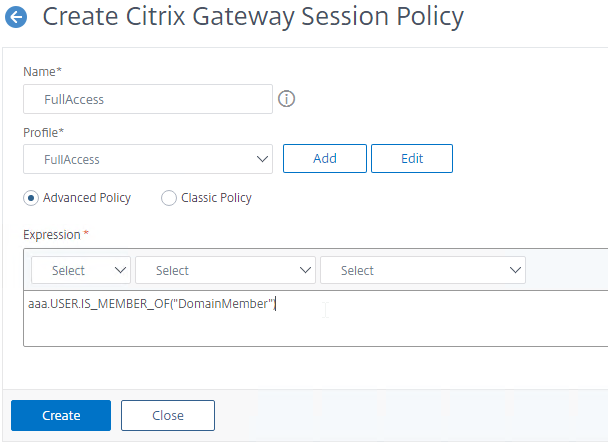
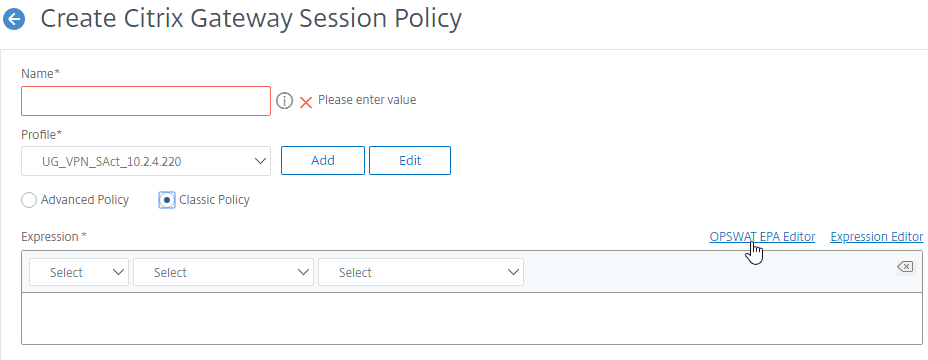
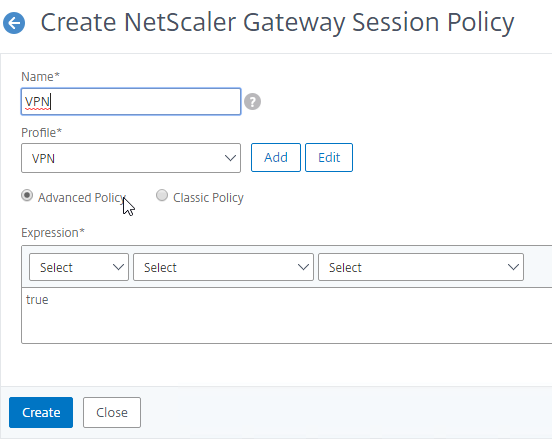
- Give the policy a descriptive name.
- Change the Profile drop-down to the VPN Profile you just created.
- The Expression box has an option for switching to Default Syntax.
- If Default Syntax, enter true in the Expression box so it always evaluates to true. If Classic Syntax, it would be ns_true instead of true.
- If Default Syntax, you can enter
HTTP.REQ.USER.IS_MEMBER_OF("MyADGroup")to restrict the Session Profile to members of a specific AD group. In Classic Syntax, this isn’t possible in an expression, and instead you must assign the Session Policy to a AAA Group.
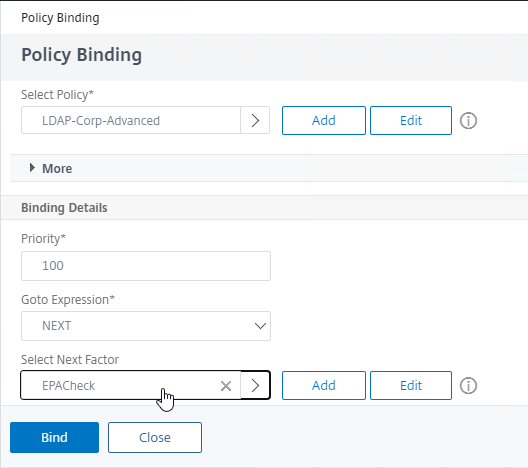
- If Classic Syntax, you can add Endpoint Analysis scans to the Expression box. If the Endpoint Analysis scan succeeds, then the session policy is applied. If the Endpoint Analysis scan fails, then this session policy is skipped, and the next one is evaluated. This is how you can allow VPN if EPA scan succeeds, but all failed EPA scans will get a different session policy that only has ICA Proxy enabled.
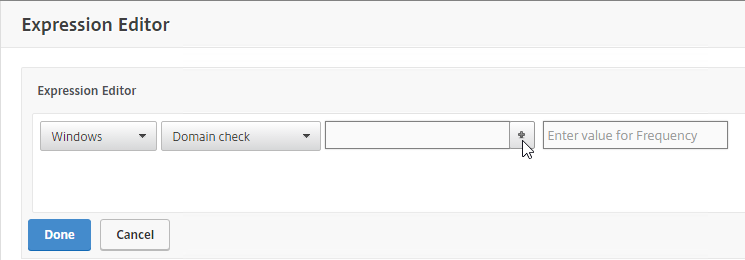
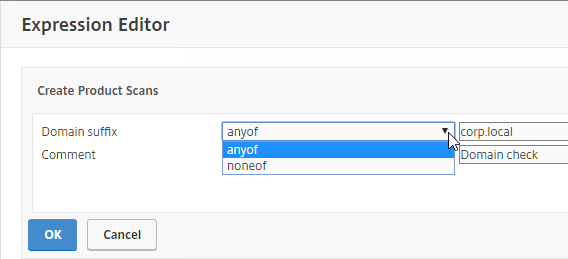
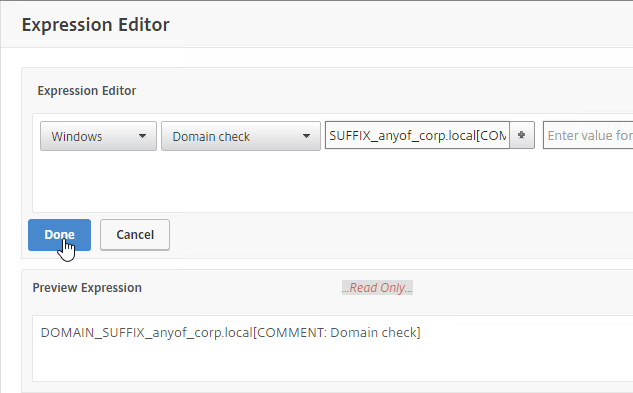
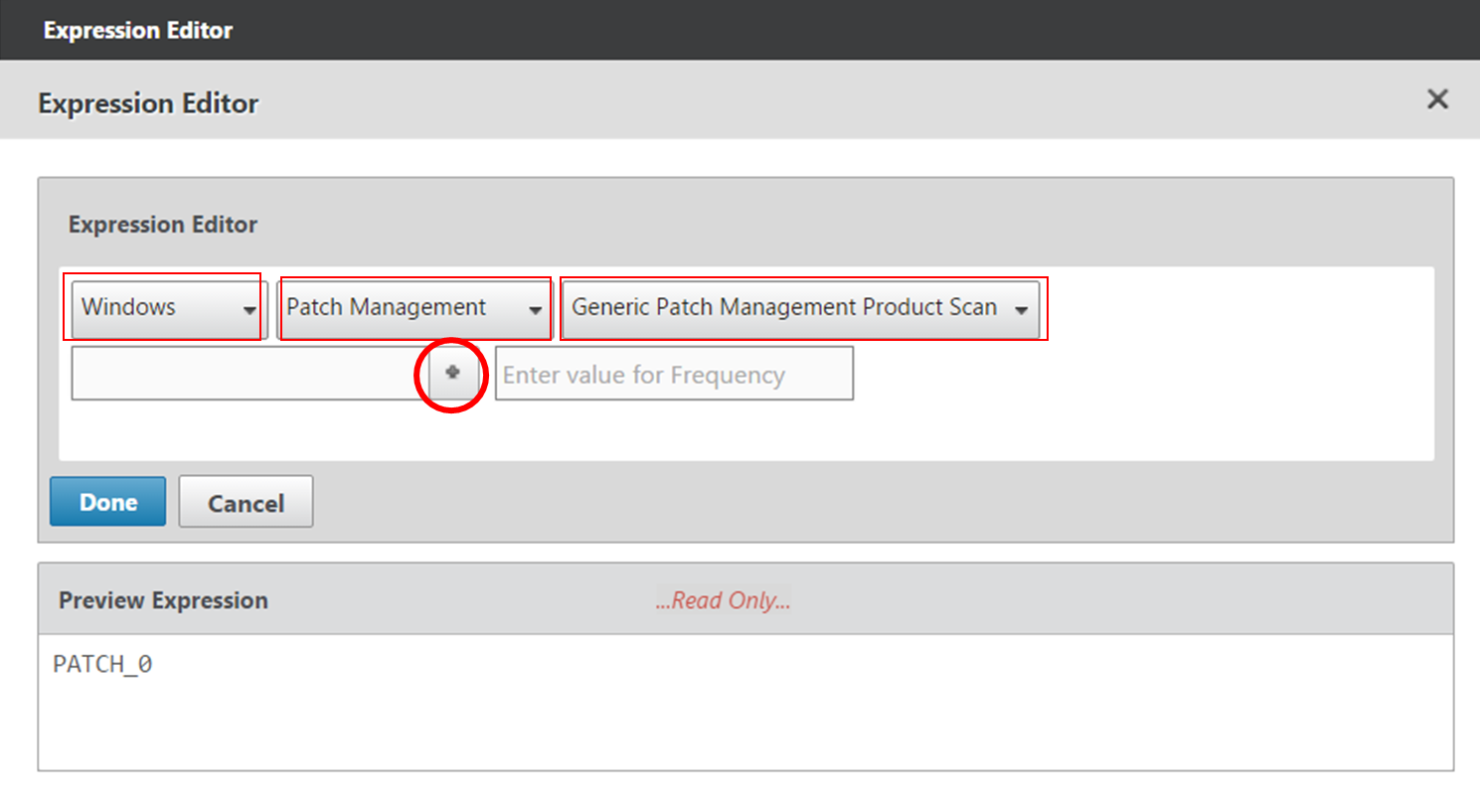
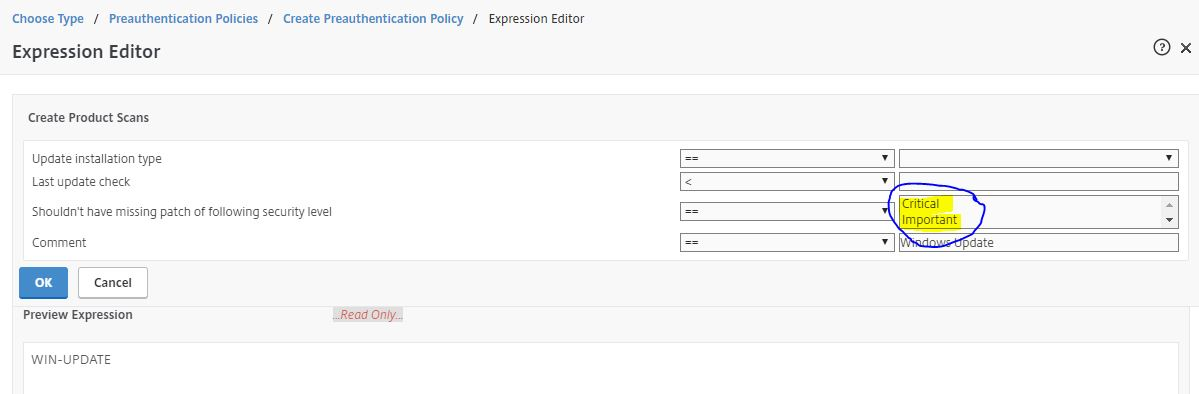
- To add an Endpoint Analysis scan, use one of the Editor links on the right.
- Configure OPSWAT scans in the OPSWAT EPA Editor.
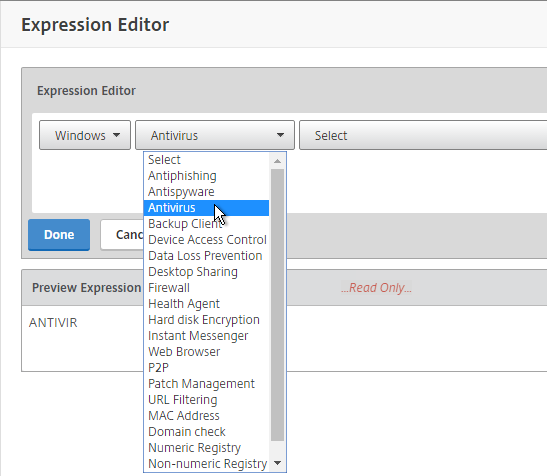
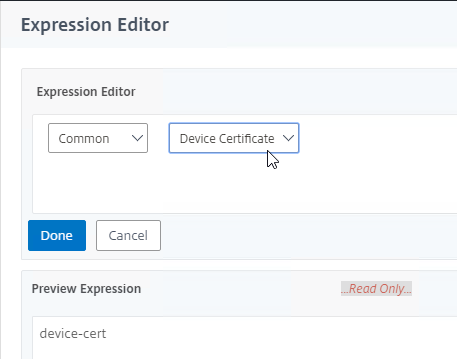
- Configure Client Security Expressions in the Expression Editor.
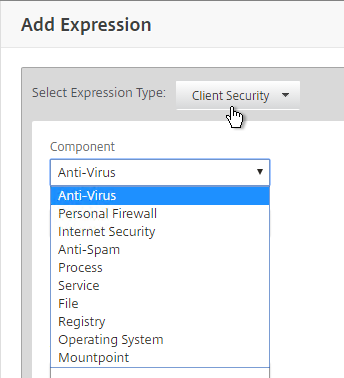
- You can combine multiple Endpoint Analysis scan expressions using Booleans (&&, ||, !).
- To add an Endpoint Analysis scan, use one of the Editor links on the right.
- Click Create when done.
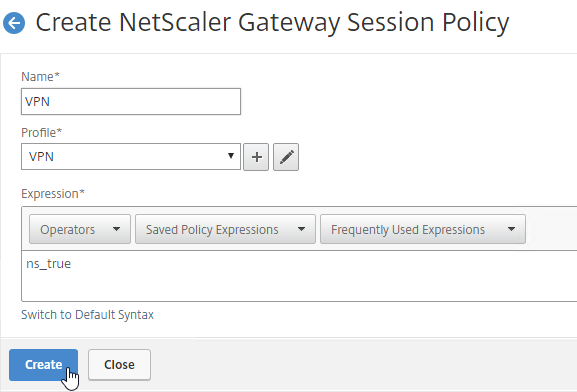
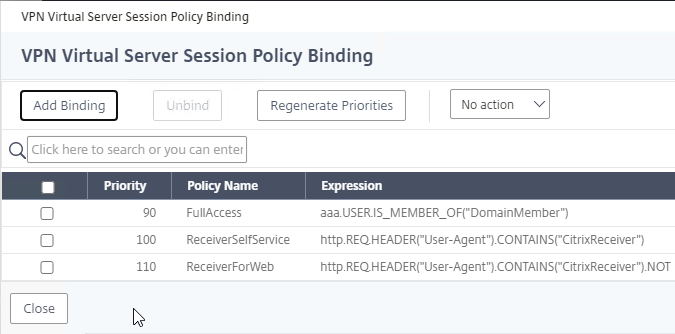
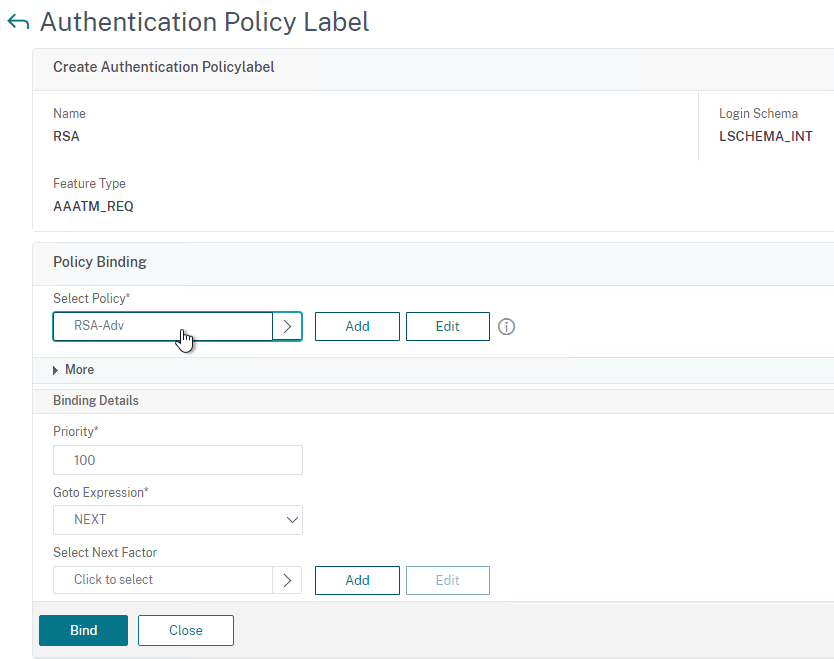
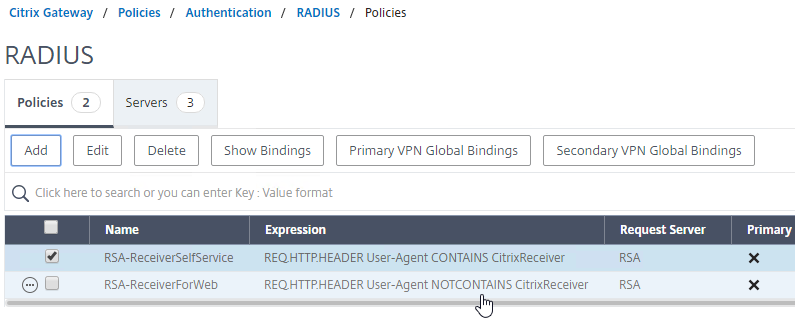
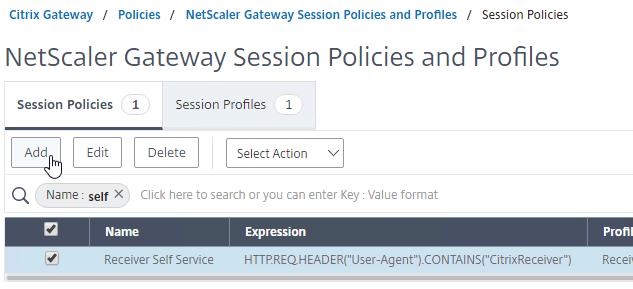
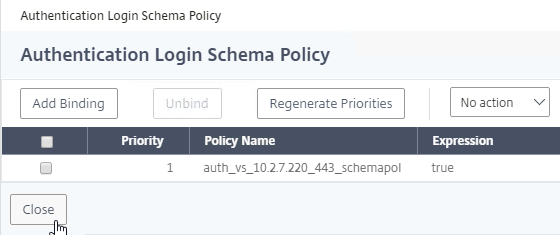
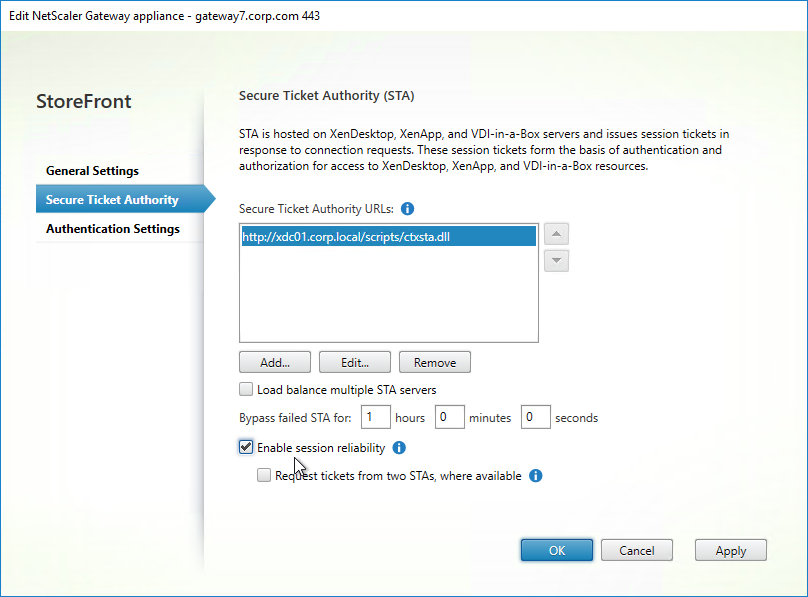
Bind Session Policy
Most of the Citrix Gateway configuration objects can be bound to a Citrix Gateway Virtual Server, AAA Groups, or both. This section details binding of Session Policies, but the other Citrix Gateway objects (e.g. Authorization Policies) can be bound using similar instructions.
- Objects bound directly to the Citrix Gateway Virtual Server are evaluated for every user of that Gateway Virtual Server.
- Objects bound to a AAA Group are only evaluated for members of that AAA Group.
- Polices bound to AAA Groups usually have lower priority numbers than policies bound to Gateway Virtual Servers, so the AAA binding can override the Gateway binding.
- However, objects/policies bound to a AAA Group are applied to every Gateway Virtual Server on the same appliance. To override AAA bindings at a specific Gateway, you can bind lower priority number policies to the Gateway Virtual Server.
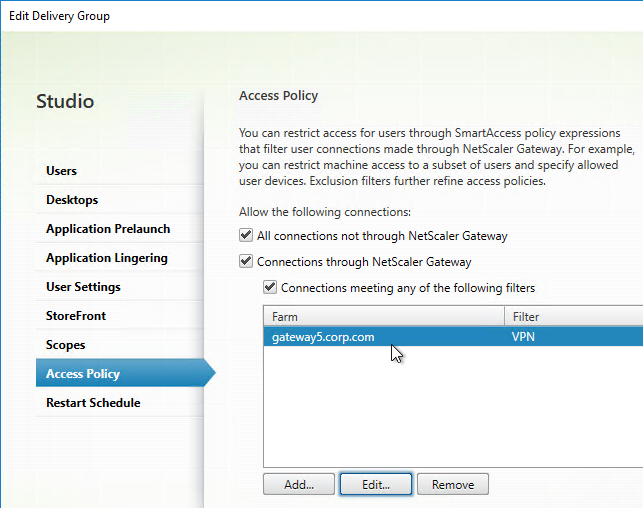
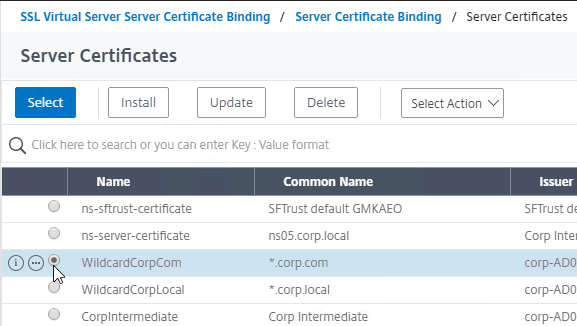
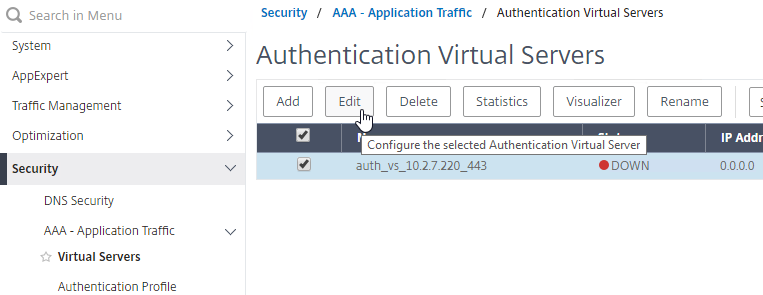
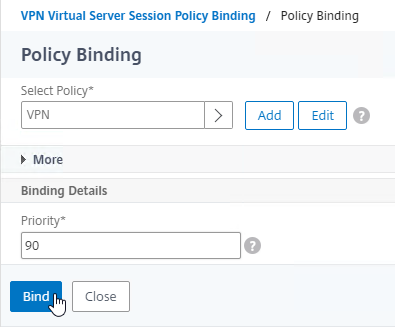
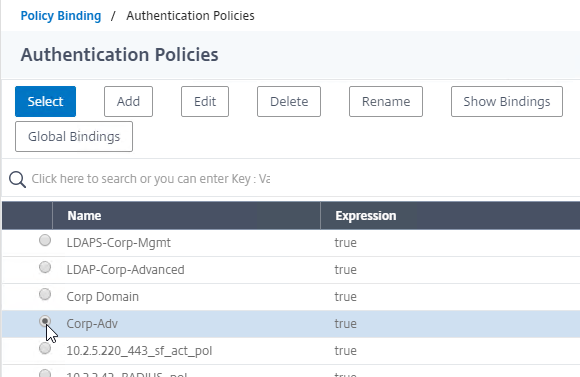
Bind the new Session Policy to a Citrix Gateway Virtual Server, or a AAA group.
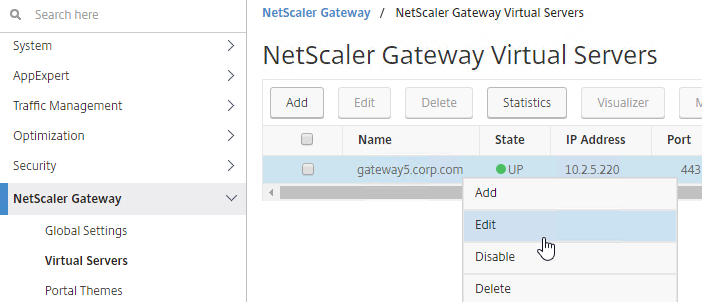
To bind to a Citrix Gateway Virtual Server
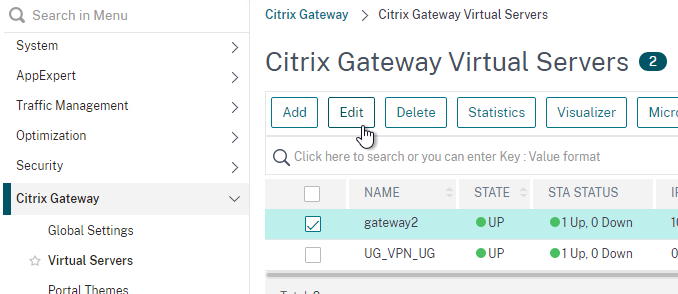
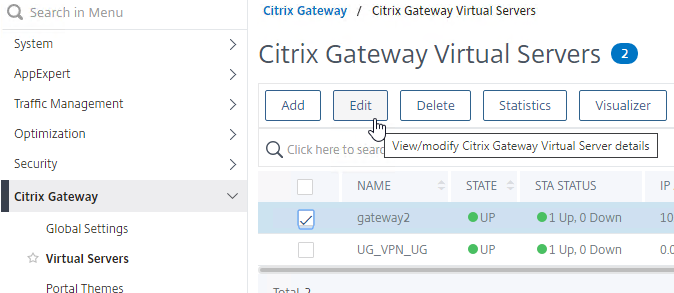
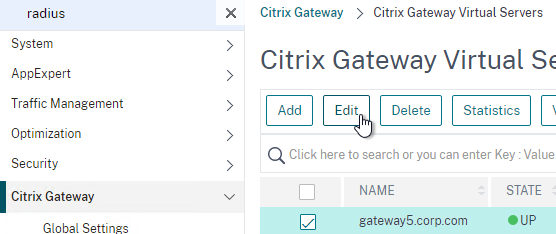
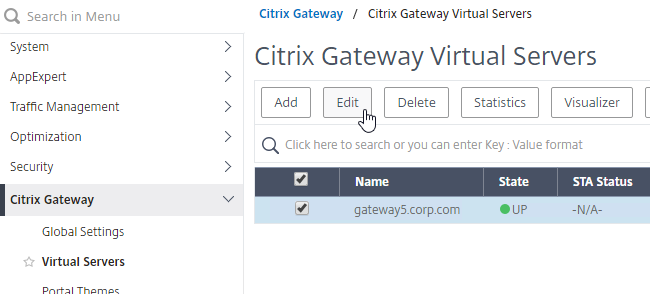
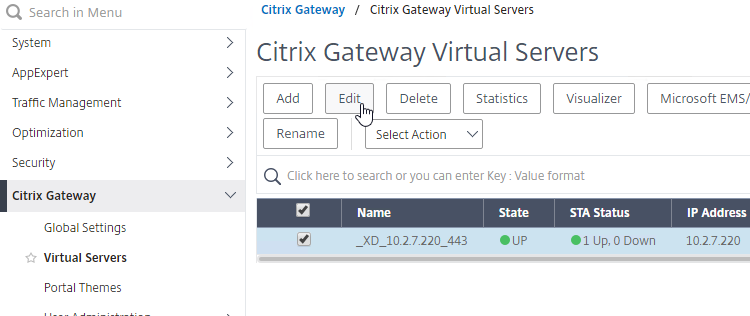
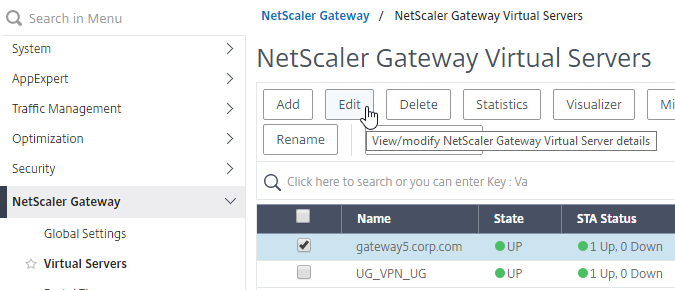
- Edit a Citrix Gateway Virtual Server (or create a new one).
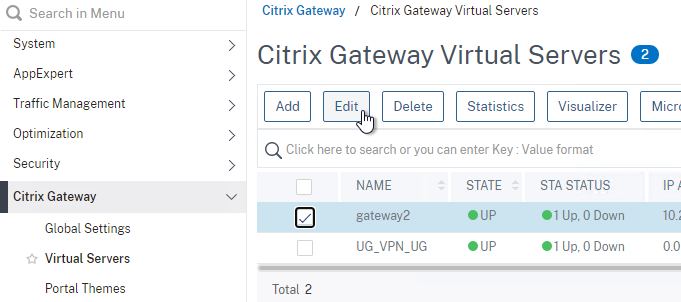
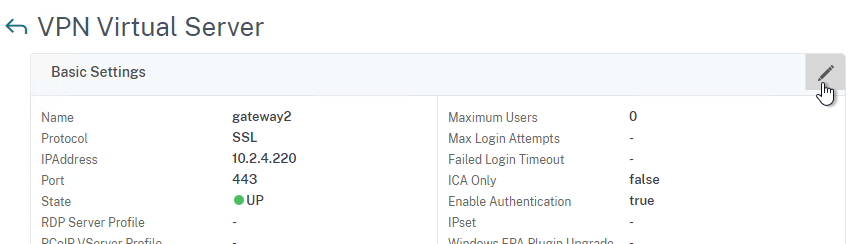
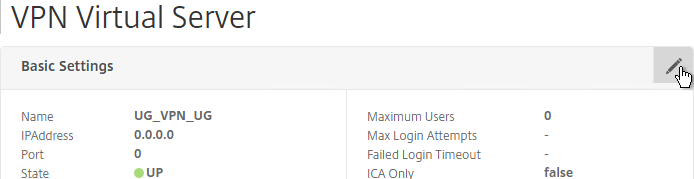
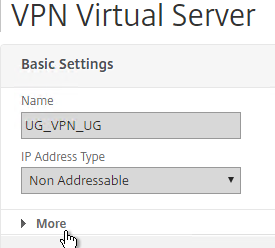
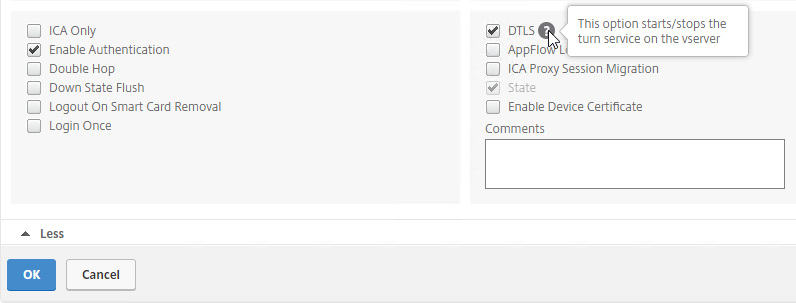
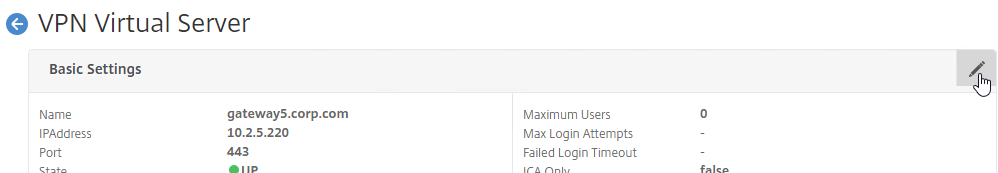
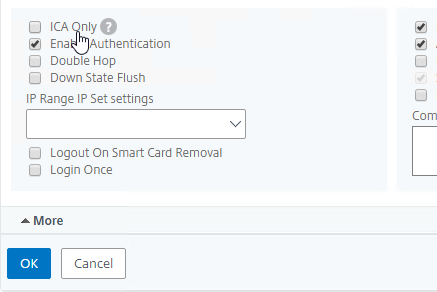
- To make sure ICA Only is unchecked:
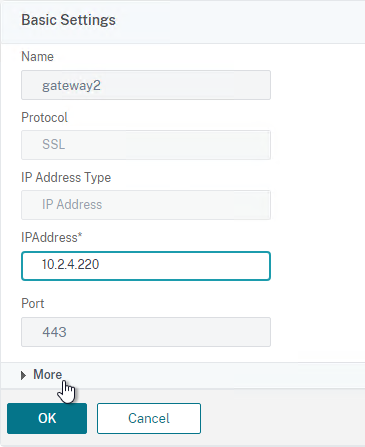
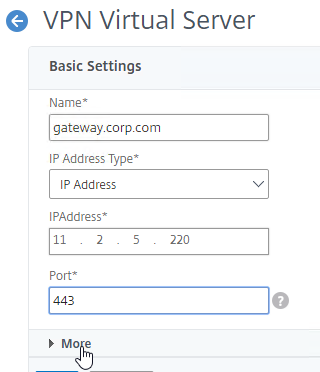
- Click the pencil icon for the Basic Settings section.
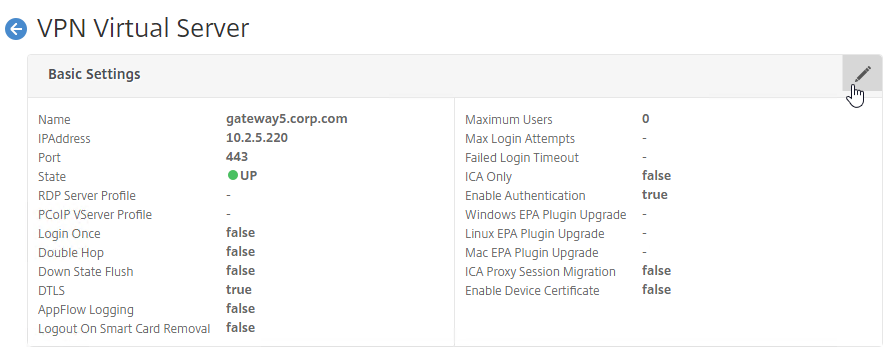
- Click More.
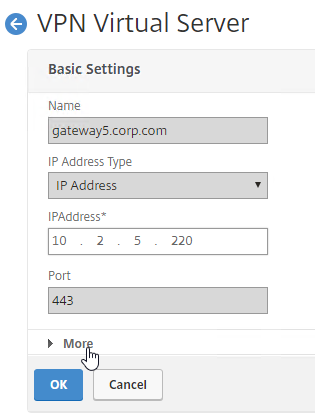
- Make sure ICA Only is unchecked, and click OK to close the Basic Settings section.
- Note: with this box unchecked, Gateway Universal licenses are now required for all users connecting through this Gateway Virtual Server.
- Click the pencil icon for the Basic Settings section.
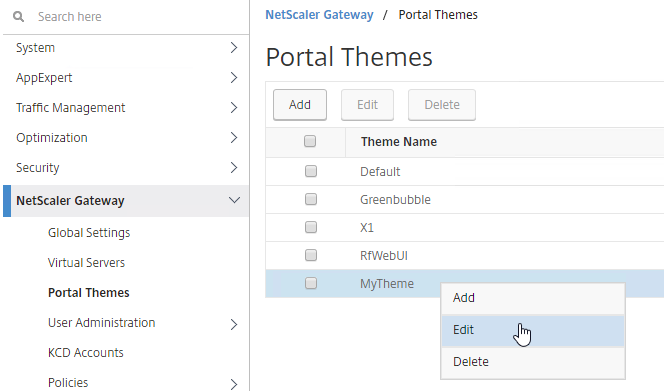
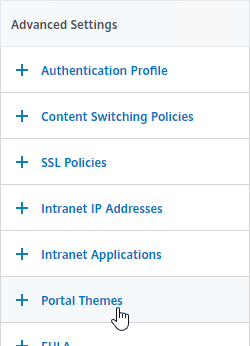
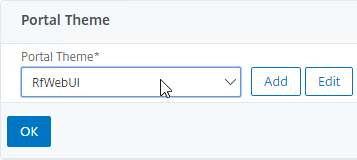
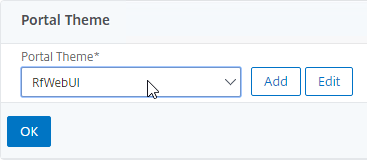
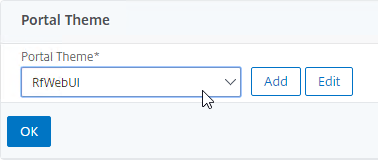
- While editing the Gateway Virtual Server, consider changing the Portal Theme to RfWebUI. This changes the default portal page to look identical to StoreFront.
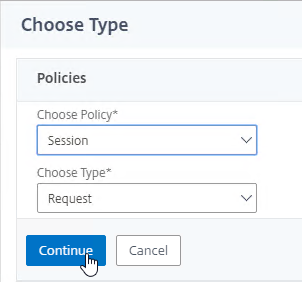
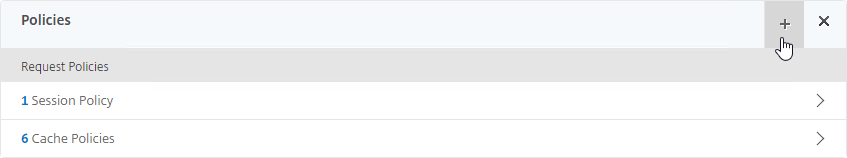
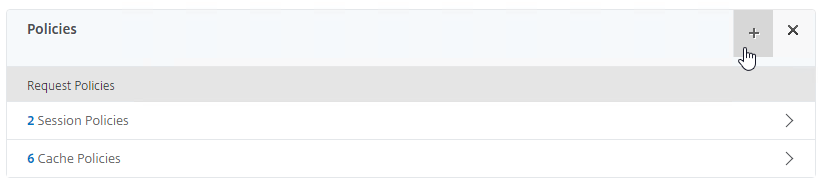
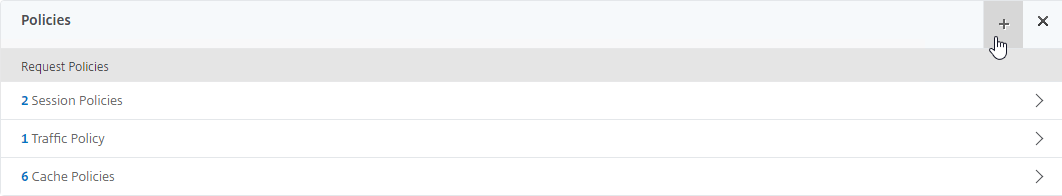
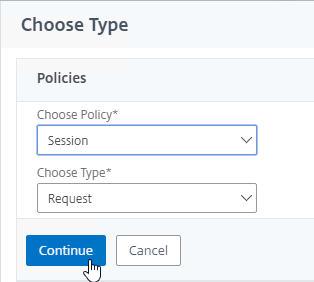
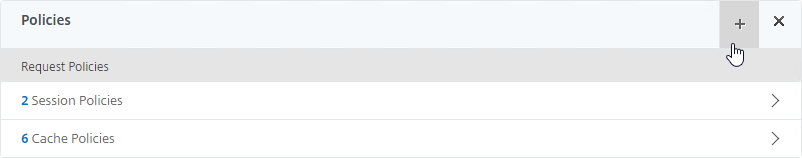
- Scroll down to the Policies section, and click the Plus icon.

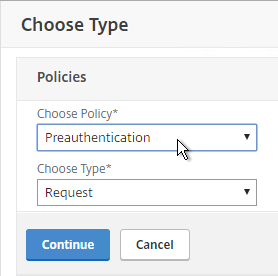
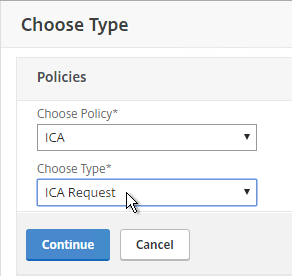
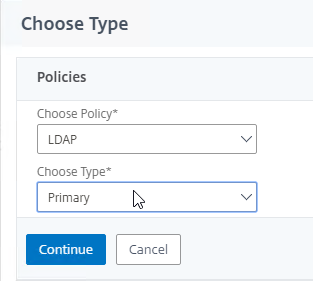
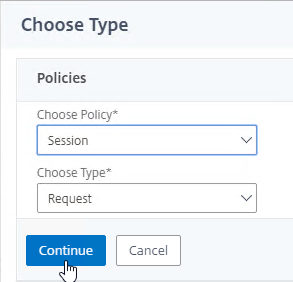
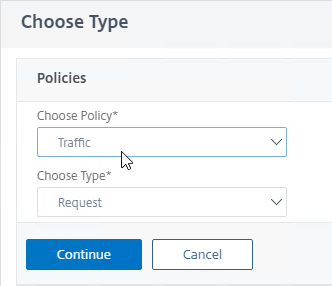
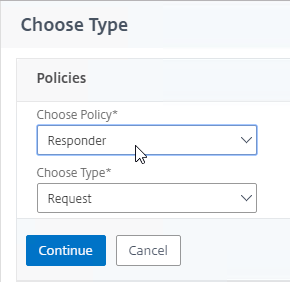
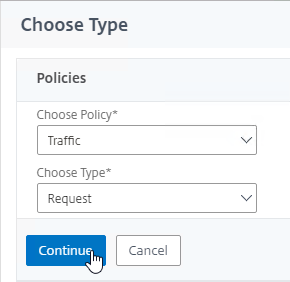
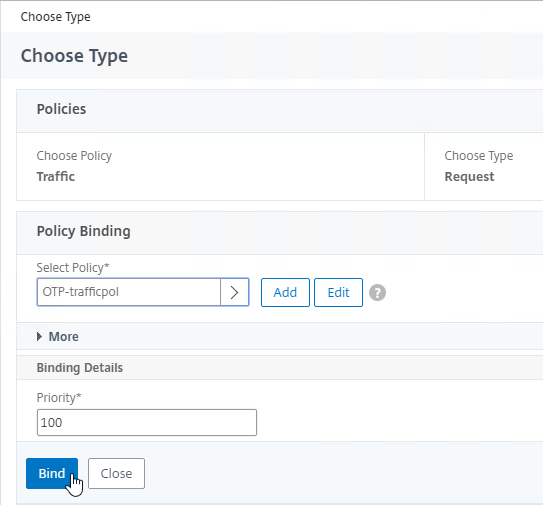
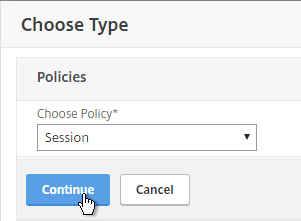
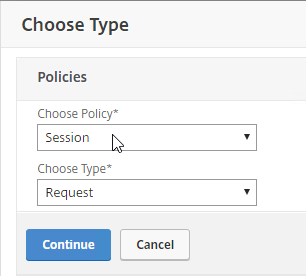
- In the Choose Type page, ensure the Choose Policy drop-down is set to Session.
- Ensure the Choose Type drop-down is set to Request, and click Continue.
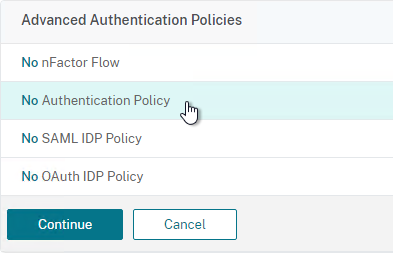
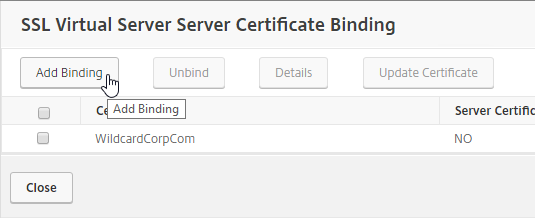
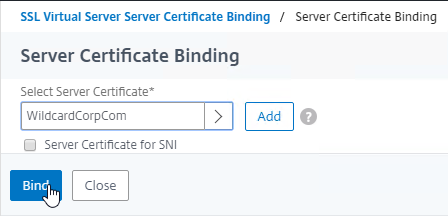
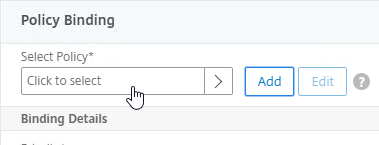
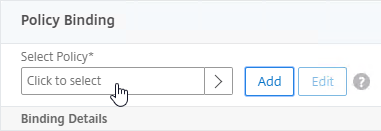
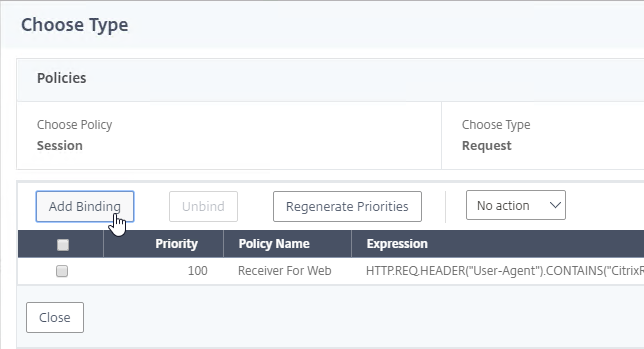
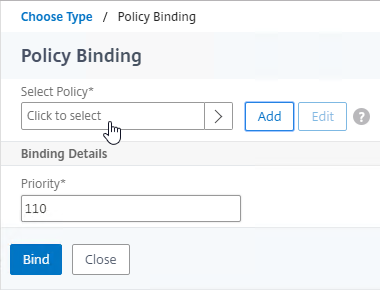
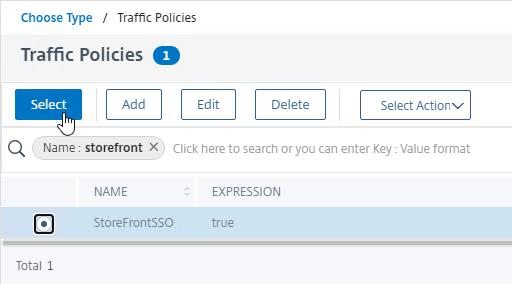
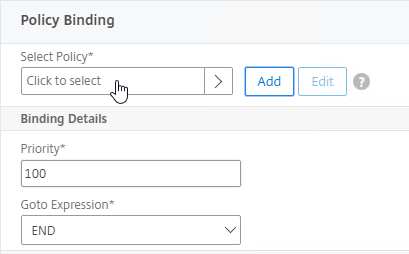
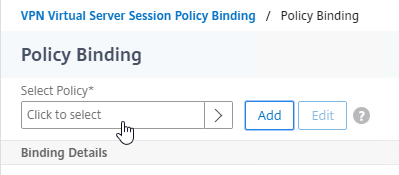
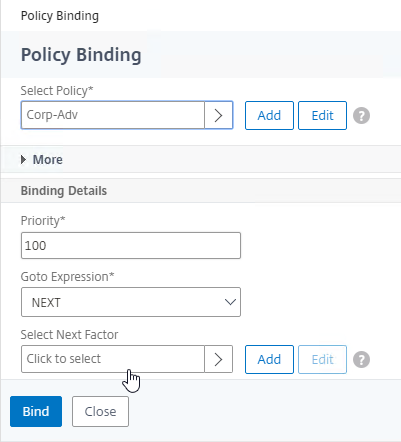
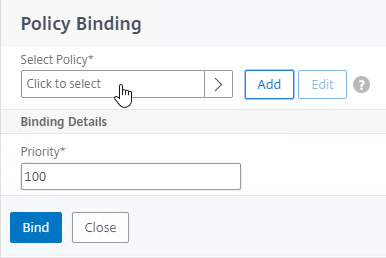
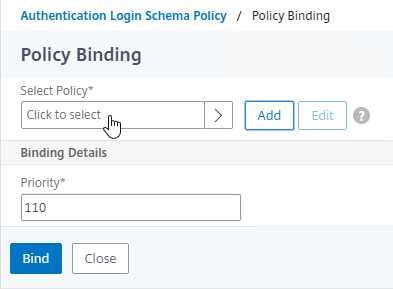
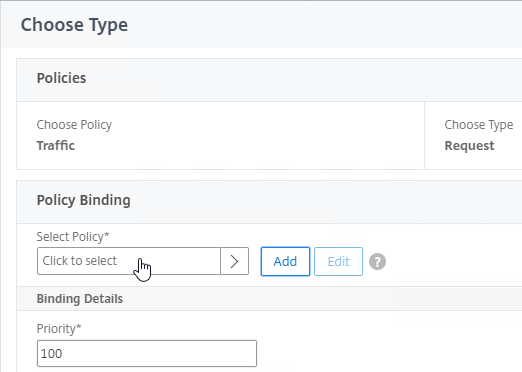
- Click where it says Click to select.
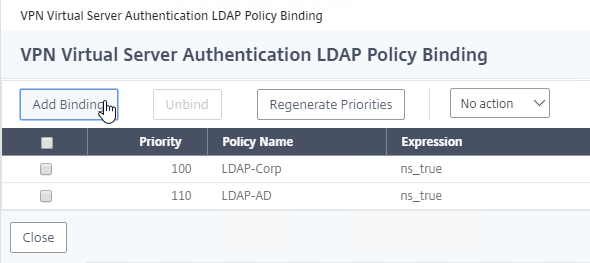
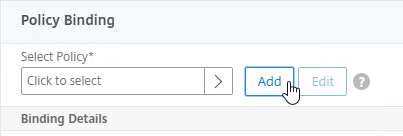
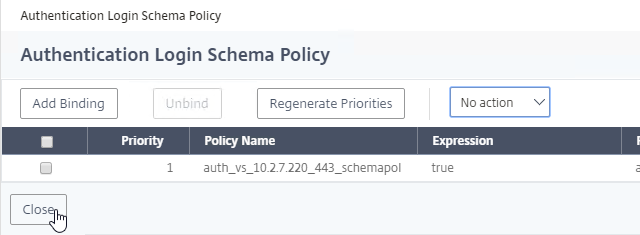
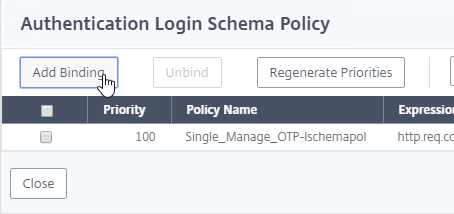
- If you already have Session Policies bound to this Gateway Virtual Server, then you might have to click Add Binding first.
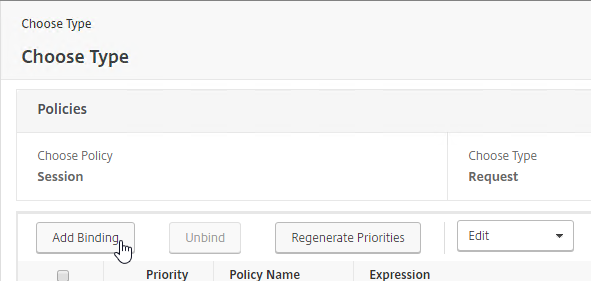
- If you already have Session Policies bound to this Gateway Virtual Server, then you might have to click Add Binding first.
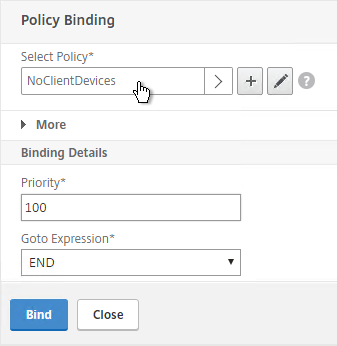
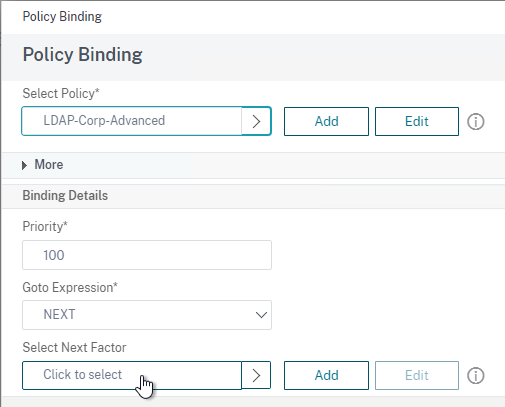
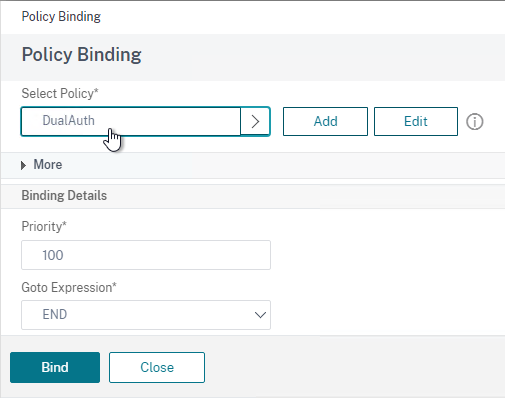
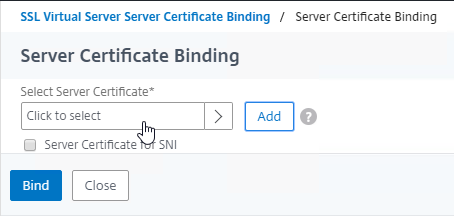
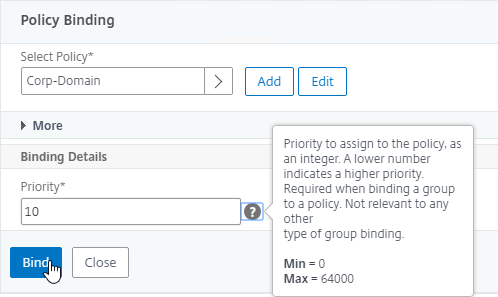
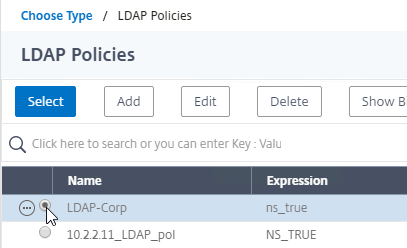
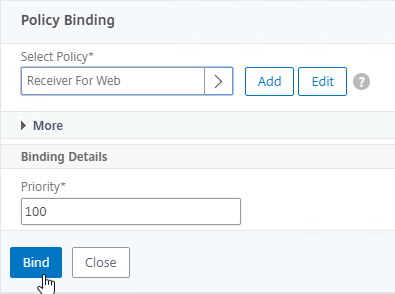
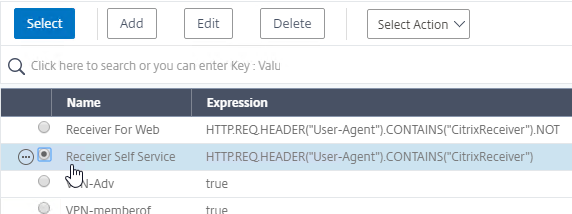
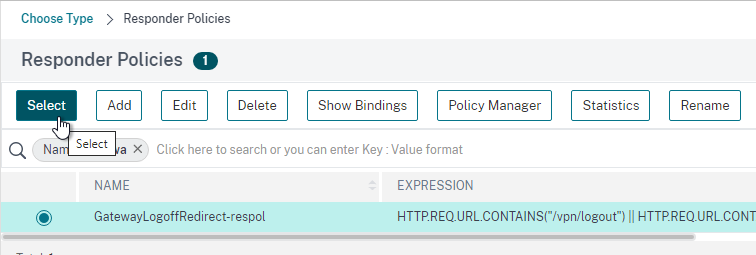
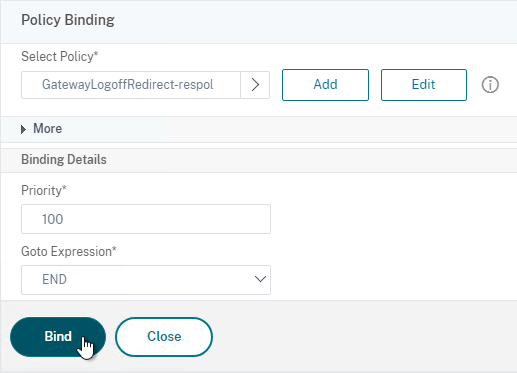
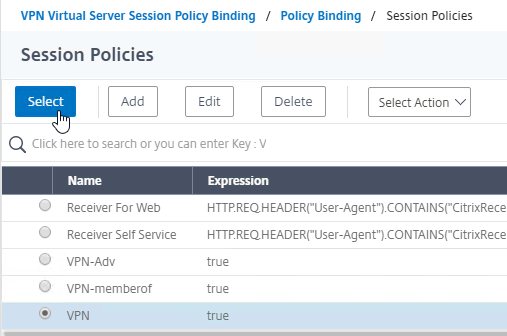
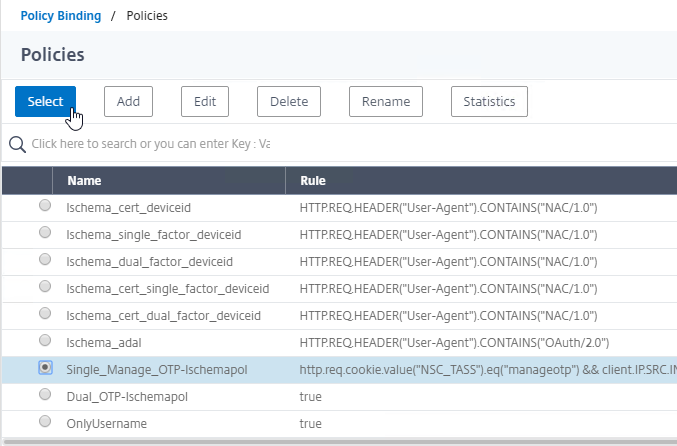
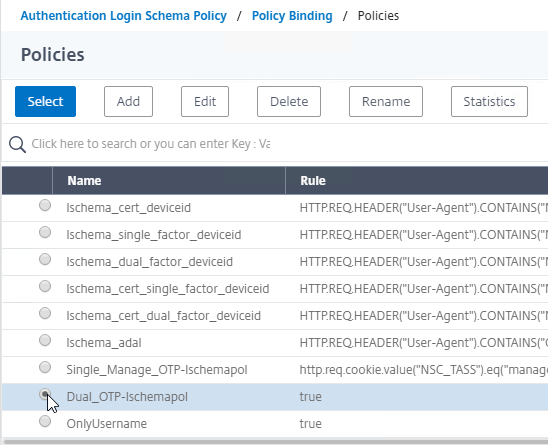
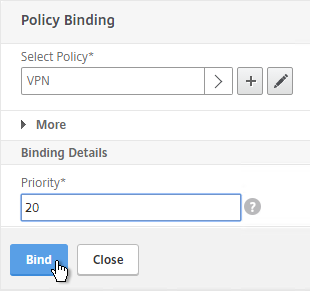
- Click the radio button next to the previously created Session Policy, and click Select.
- Note: you cannot mix Classic Syntax Policies and Default Syntax Policies.
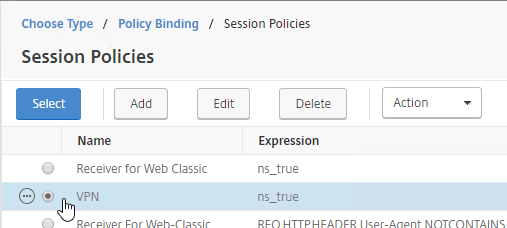
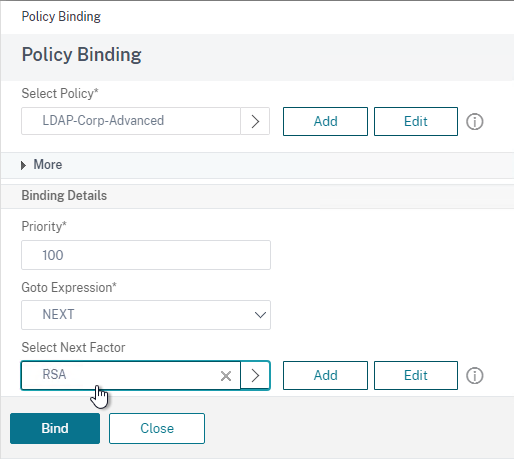
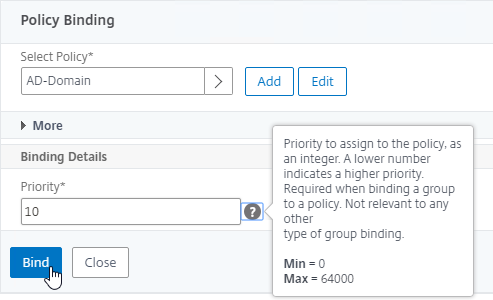
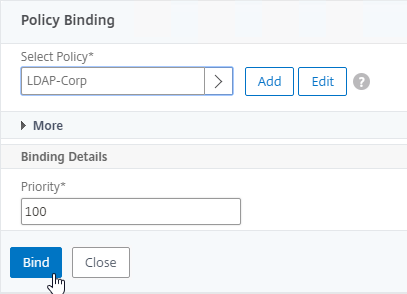
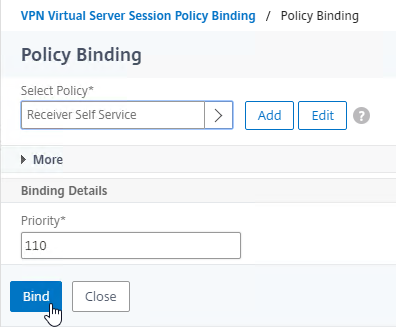
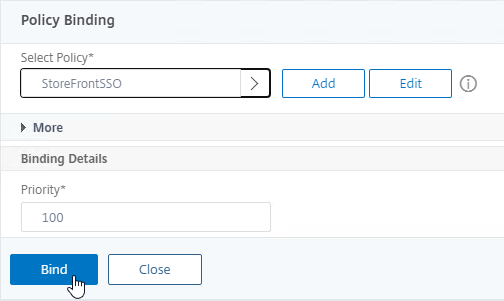
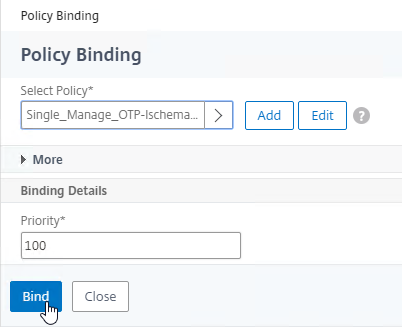
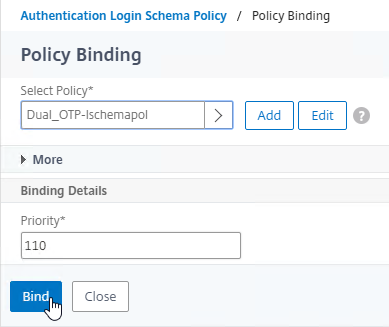
- In the Priority field, adjust the priority number. If you want this Session Policy to override other Session Policies, then set the priority number to a low value. See CTX214588 Understanding Session Policy Priority on Different Bind Points.
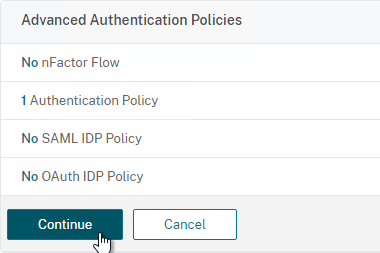
- Click Bind.
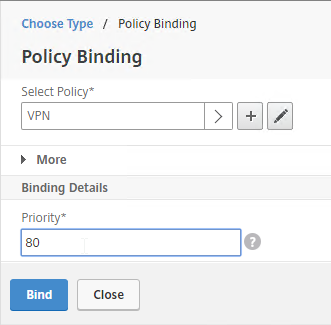
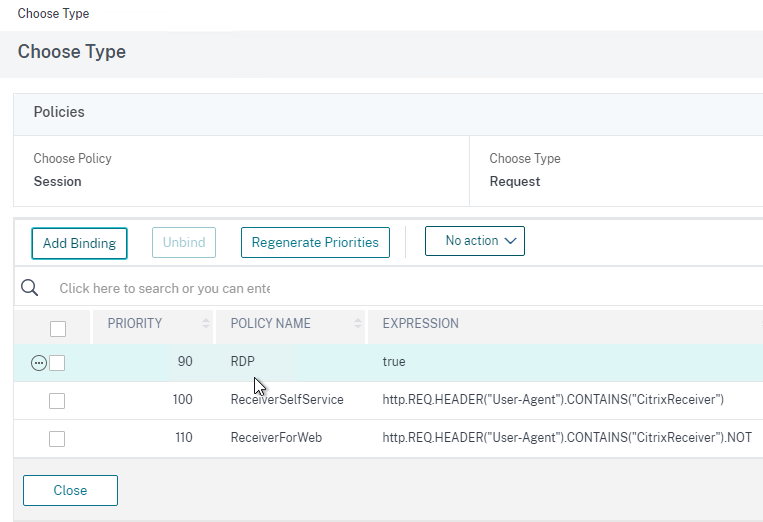
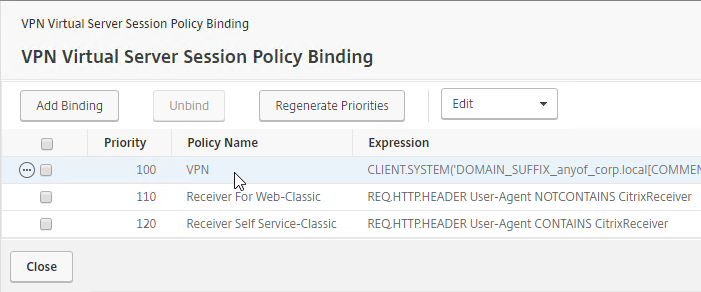
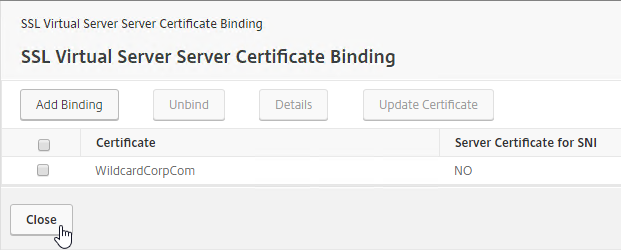
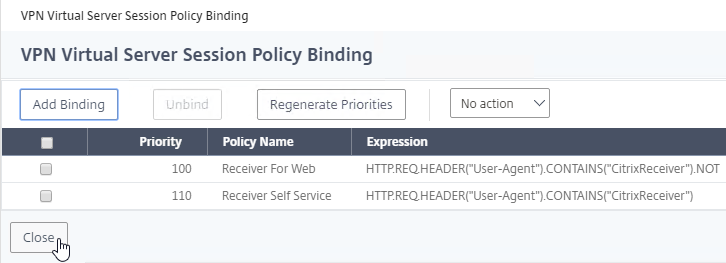
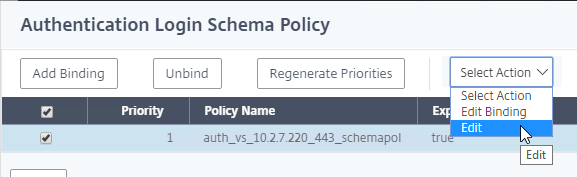
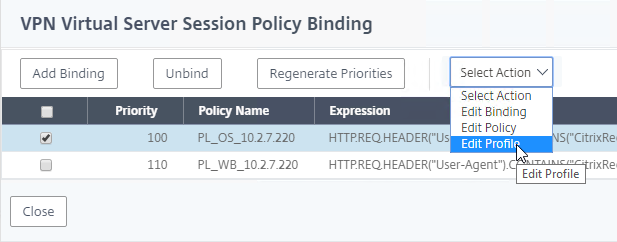
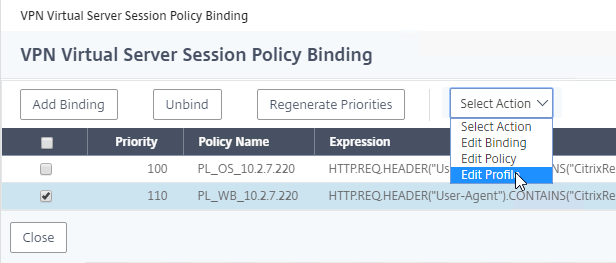
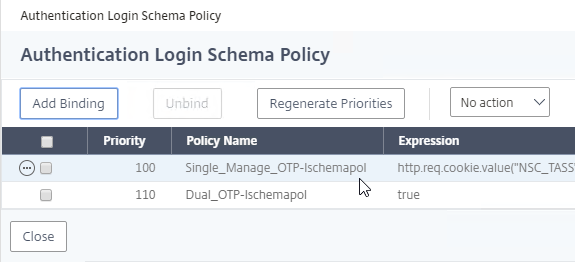
- If you already have Session Policies bound to the Gateway Virtual Server, then the list of Policies is displayed. If you don’t see this list, on the left, in the Policies section, click the line that says Session Policies.
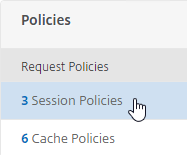
- From this list, you can right-click the policies to Edit Binding (priority number), or Edit Profile.
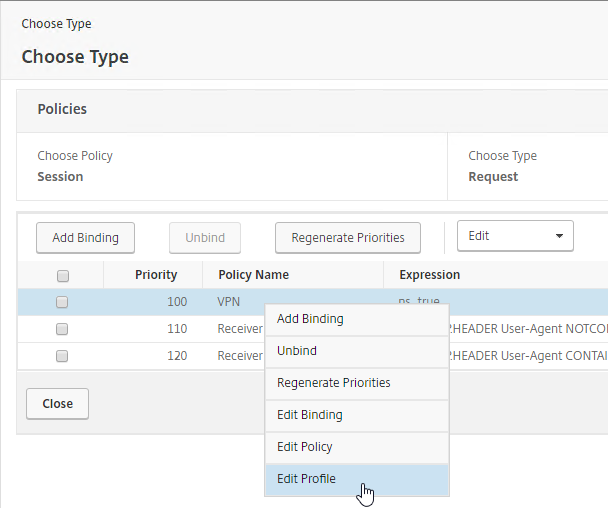
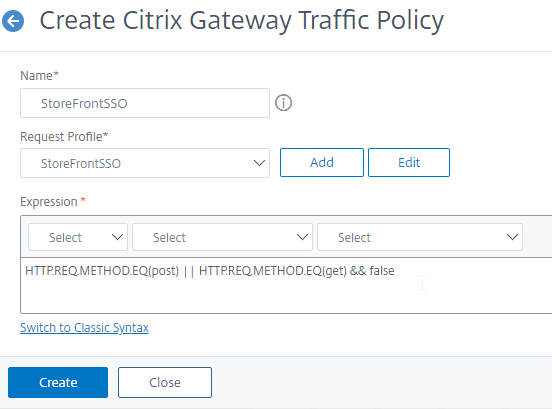
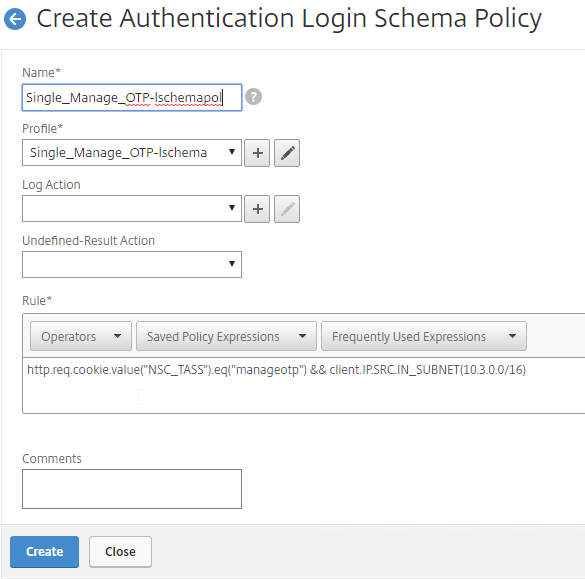
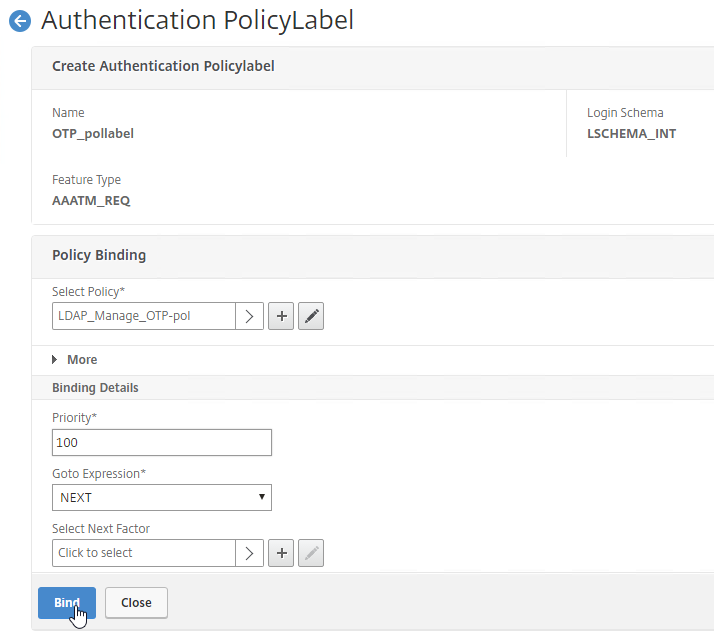
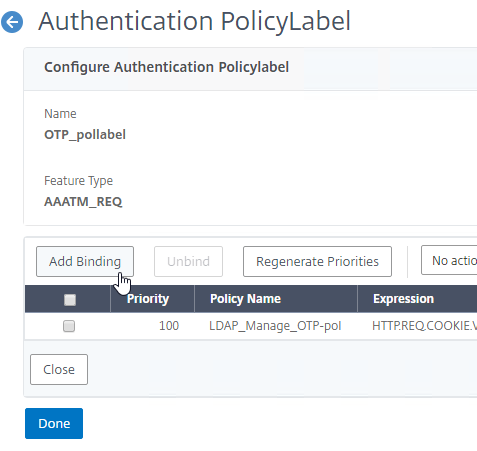
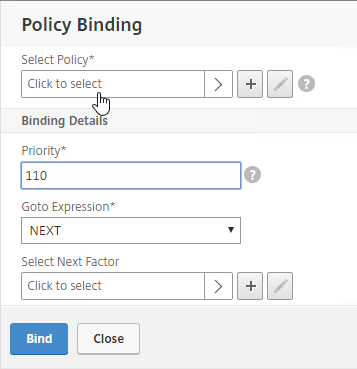
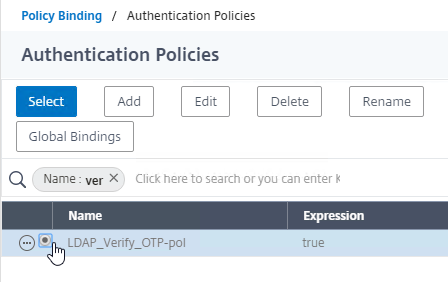
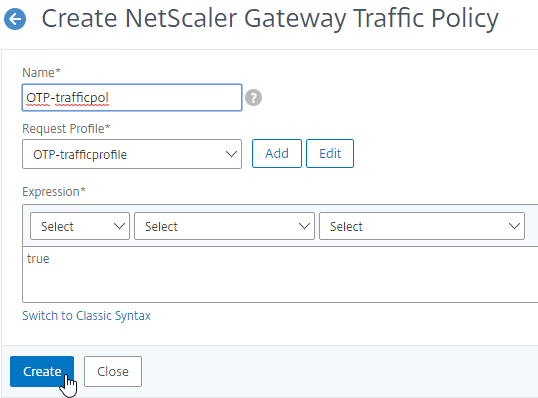
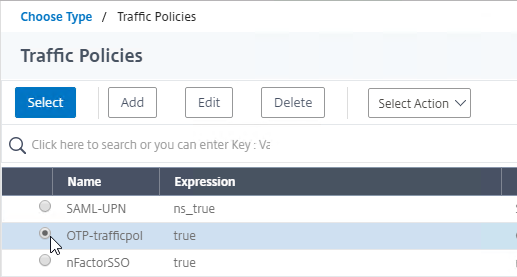
- If your Citrix Gateway Virtual Server is configured with a Traffic Policy for Native OTP (One Time Passwords), change the Traffic Policy expression to the following. Source = Julien Mooren at NetScaler – Native OTP is breaking SSL VPN.
http.req.method.eq(post)||http.req.method.eq(get) && false
Bind to AAA Group
- To bind to a AAA Group, go to Citrix Gateway > User Administration > AAA Groups.
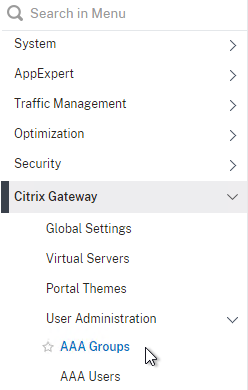
- On the right, add a AAA group with the same name (case sensitive) as the Active Directory group name. This assumes your LDAP policies/server are configured for group extraction (Group Attribute, and Sub Attribute).
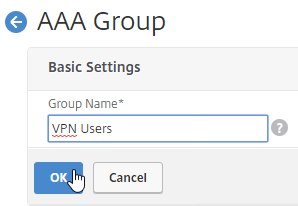
- Edit the AAA Group.
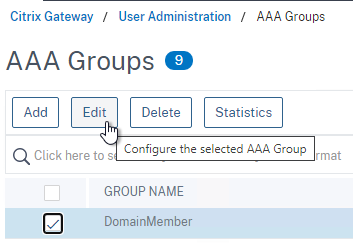
- On the right, in the Advanced Settings column, add the Policies section.
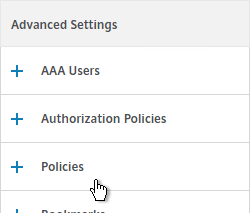
- Click the plus icon to bind one or more Session Policies.
- If you want these Session Policies to override the Session Policies bound to the Citrix Gateway Virtual Server, then make sure the Session Policies bound to the AAA Group have lower priority numbers. See CTX214588 Understanding Session Policy Priority on Different Bind Points.

- If a user belongs to multiple groups, then for Advanced Session Policies, see CTX289931 AAA group session policies are not applying based on priority. Classic Policies in multiple AAA Groups are lumped together and evaluated based on bind point priority number. Advanced Policies are no longer lumped together and instead each AAA Group is evaluated separately. The first AAA Group created has higher priority than later created AAA Groups unless you specify the weight when creating the AAA Group from the CLI. 💡
Citrix Gateway Plug-in
Upgrade Citrix Gateway Plug-in
Citrix ADC pushes the Gateway Plug-in (aka VPN client) to client machines. In newer builds of Citrix ADC 13.0, you can upgrade the VPN plugin on the ADC without upgrading the ADC firmware.
- Download the latest plugin .tgz file from https://www.citrix.com/downloads/citrix-gateway/plug-ins/citrix-gateway-windows-plug-in-clients.html.
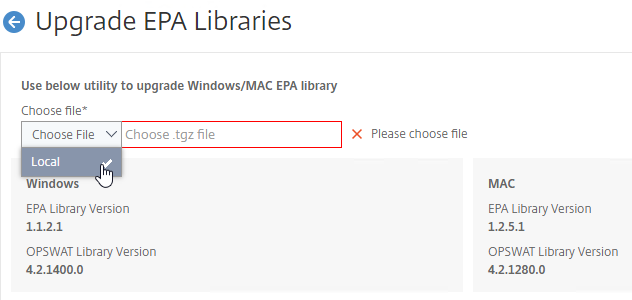
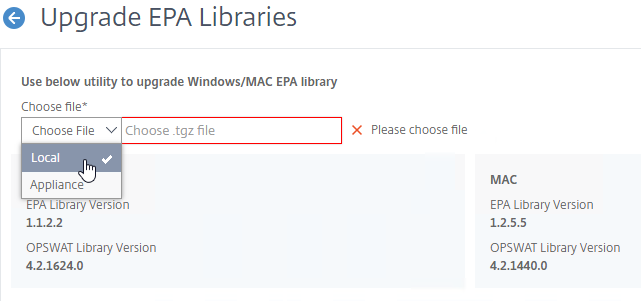
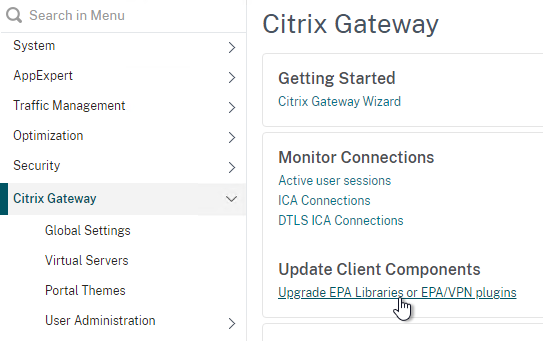
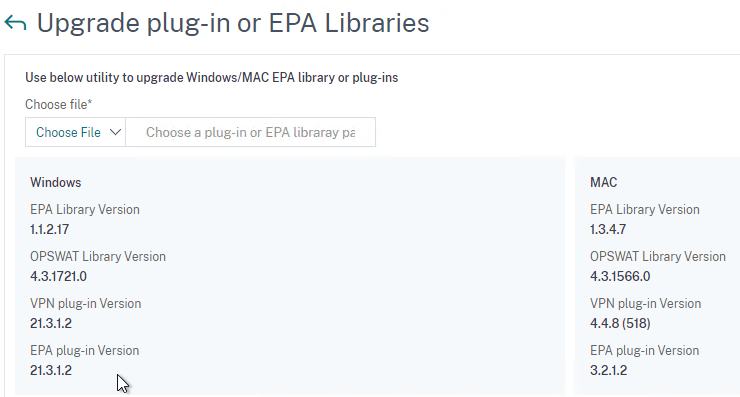
- In Citrix ADC, on the left click the Citrix Gateway node. On the right, click Upgrade EPA Libraries or EPA/VPN plugins.
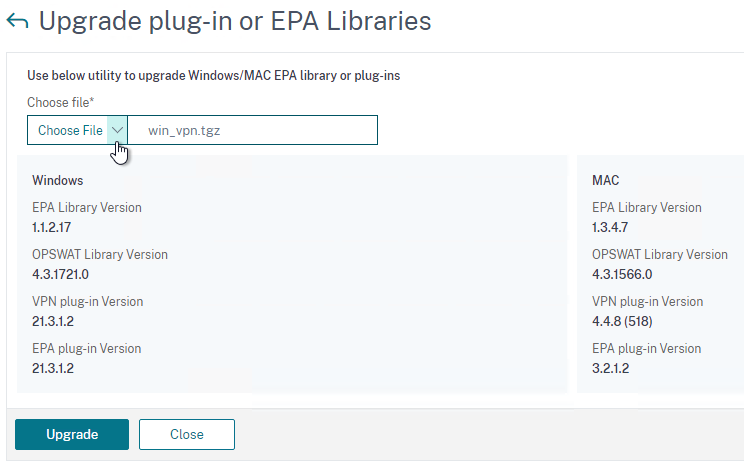
- This page shows you the versions of the currently installed plugins.
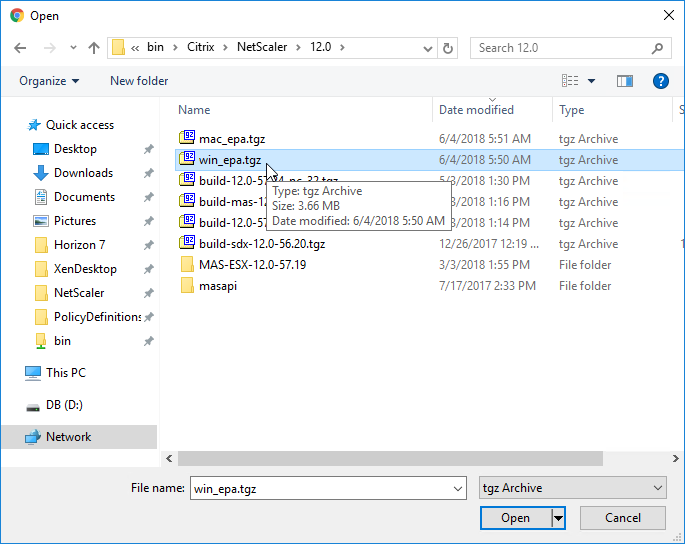
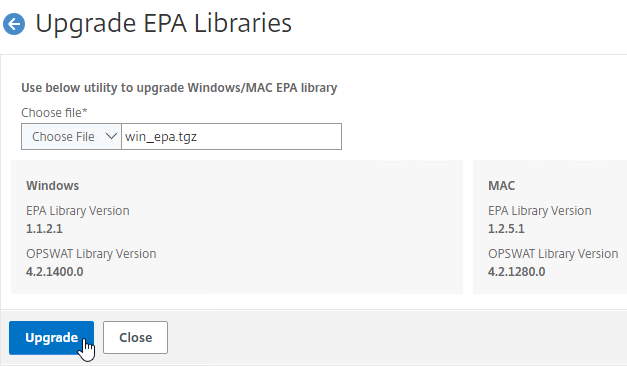
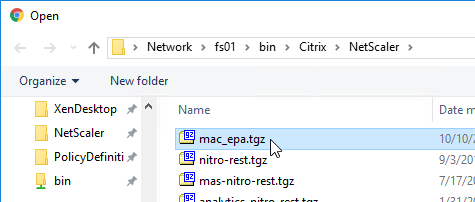
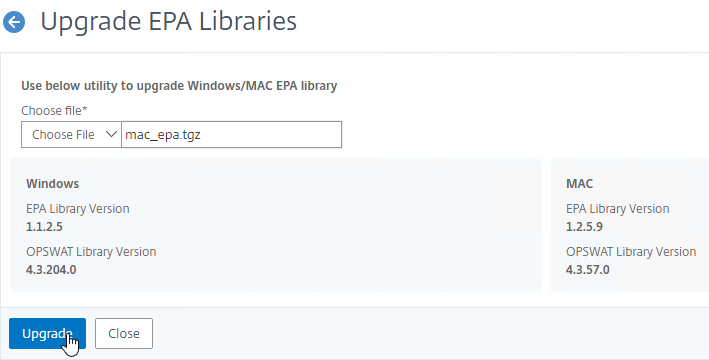
- Click Choose File and select the win_vpn.tgz file. Click Upgrade.
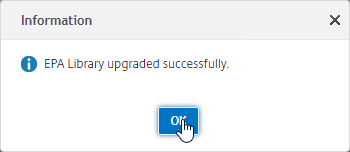
- Click OK when prompted that the upgrade completed successfully.
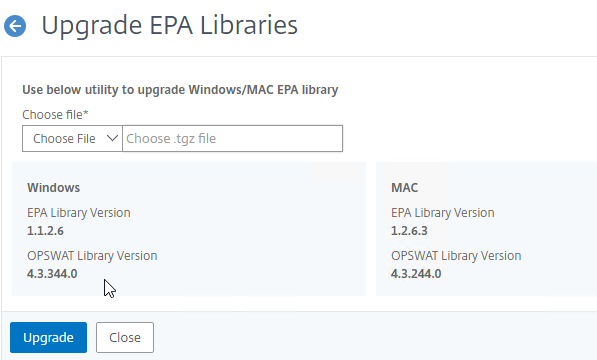
- Go back to the Upgrade plug-in or EPA Libraries page to see the new versions.
Citrix Gateway Plug-in Installation
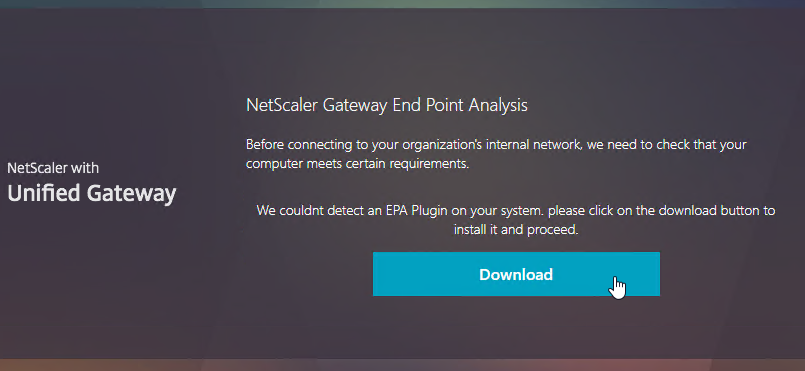
Here is what the user sees when launching the VPN session for the first time. This assumes the user is an administrator of the local machine.
- Wait for 10 seconds for the webpage to not detect Gateway Plug-in, and then click the Download button.
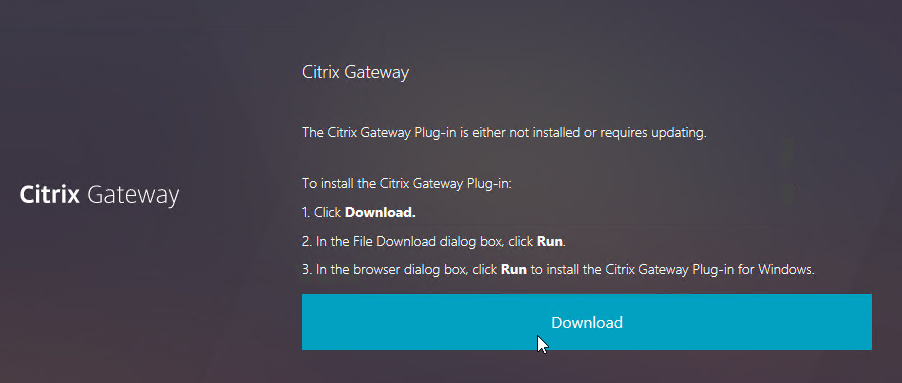
- Run the downloaded AGEE_setup.exe.
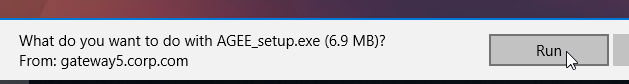
- In the Please read the Citrix Gateway Plug-in License Agreement page, click Install.
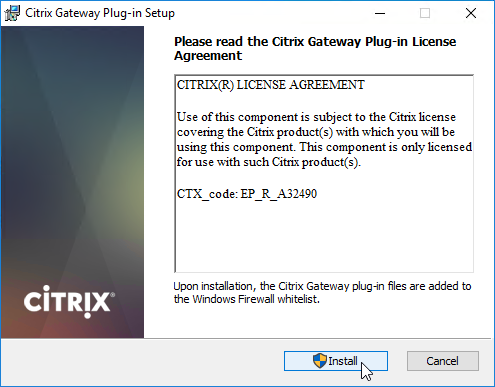
- In the Complete the Citrix Gateway Plug-in Setup Wizard page, click Finish.
- Click Yes to restart your system.
- In ADC 13.0 build 71.44 and newer, VPN plug-in for Windows supports Secure DNS update. This feature is disabled by default. To enable it, create the following on the client device: (source = 13.0-71.44 release notes) 💡
- HKEY_LOCAL_MACHINE\SOFTWARE\Citrix\Secure Access Client\secureDNSUpdate value of type REG_DWORD and set it to 1.
- When you set the value to 1, the VPN plug-in tries the unsecure DNS update first. If the unsecure DNS update fails, the VPN plug-in tries the secure DNS update.
- To try only the secure DNS update, you can set the value to 2.
- HKEY_LOCAL_MACHINE\SOFTWARE\Citrix\Secure Access Client\secureDNSUpdate value of type REG_DWORD and set it to 1.
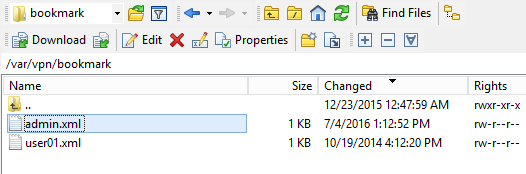
Only administrators can install the Citrix Gateway Plug-in. You can download the Gateway plug-in from the NetScaler appliance at /var/netscaler/gui/vpns/scripts/vista and push it to corporate-managed machines. Or you can download VPN clients from Citrix.com. The VPN client version must match the Citrix ADC firmware version.
To deploy the Gateway Plug-in using Group Policy, see CTX124649 How to Deploy NetScaler Gateway Plug-in and Endpoint Analysis Installer Packages for Windows by Using Active Directory Group Policy.
While a VPN tunnel is established, you can open the Gateway Plug-in to see status. If the Gateway Plug-in is merged with Workspace app, right-click Workspace app, click Advanced Preferences, click Citrix Gateway Settings, and click Open.
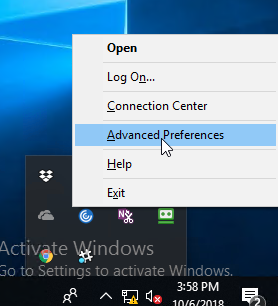
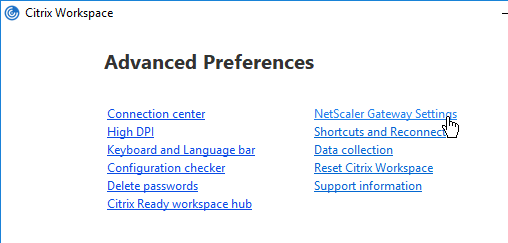
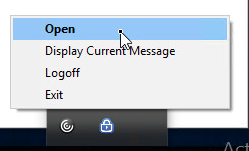
Or, if the Gateway Plug-in icon is separated from Workspace app, then right-click the Gateway Plug-in icon, and click Open.
The hamburger menu on the left lets you see more info about the VPN tunnel.
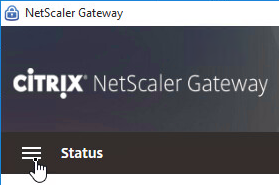
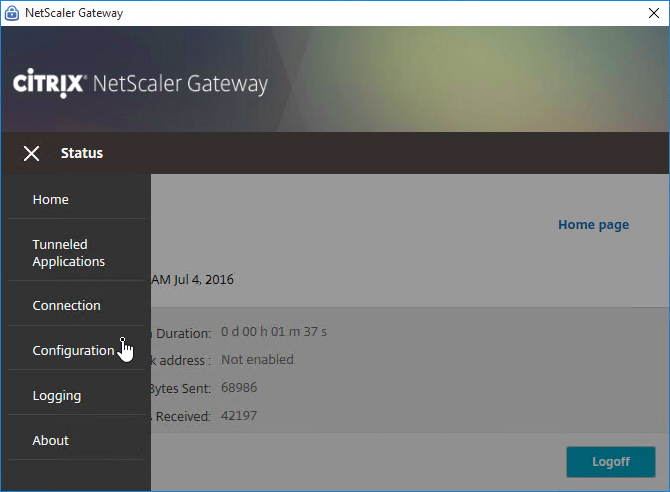
If the Gateway VPN session isn’t established, you can open the Gateway plug-in, and login. No browser needed.
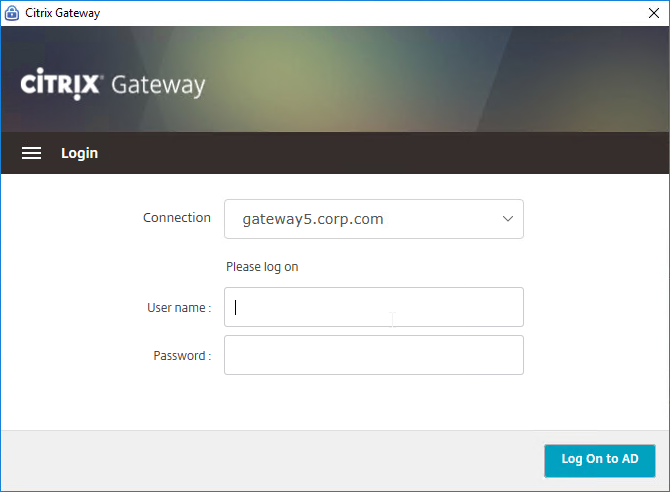
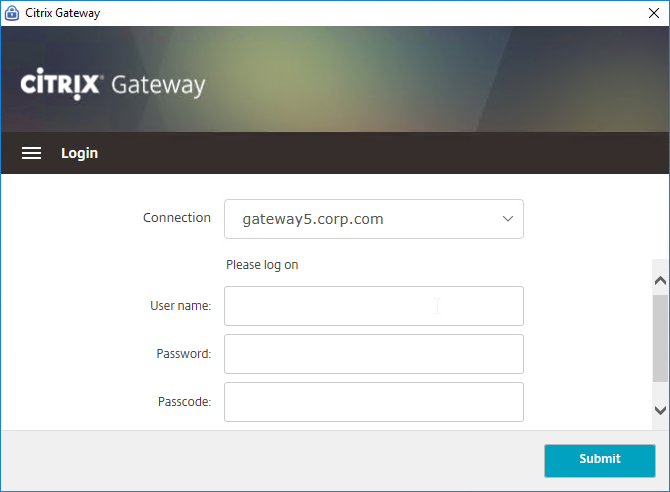
- Gateway Plug-in 12.1 build 49 with Citrix ADC 12 build 49 support nFactor authentication (e.g. Native OTP) in the Gateway Plug-in. Older versions do not support nFactor. 💡
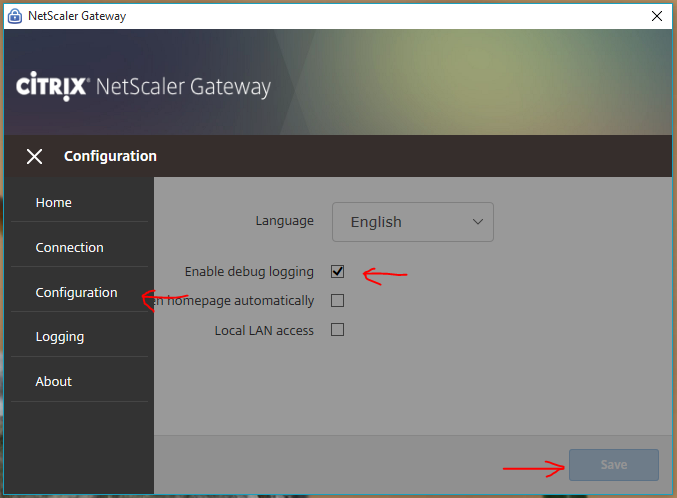
The Configuration page lets you enable Logging. Then the Logging page lets you collect the logs. See Citrix CTX138155 How to Collect Client VPN Logs for NetScaler Gateway.
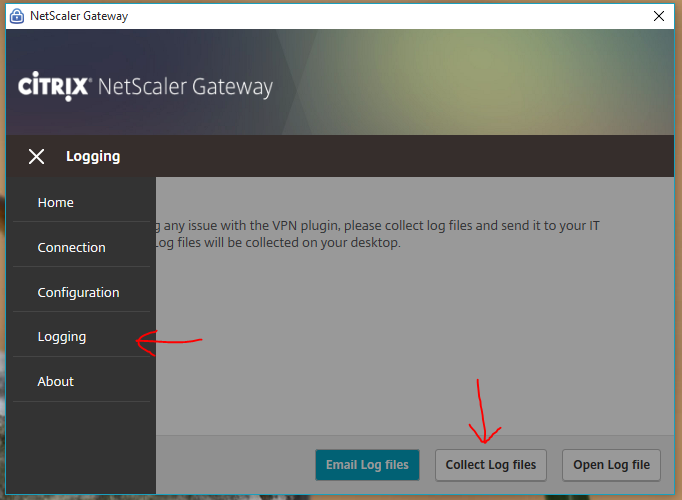
VPN Client (Citrix Gateway Plug-in) Session Profile Settings
Separate Icons for Workspace app and Gateway
- By default, if Workspace app, and Citrix Gateway Plug-in, are installed on the same machine, then the icons are merged. To see the Citrix Gateway Plug-in Settings, you right-click Workspace app, open Advanced Preferences, and then click Citrix Gateway Settings. This makes it difficult to log off.
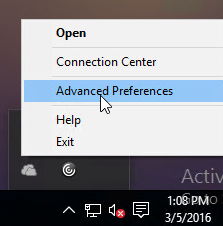
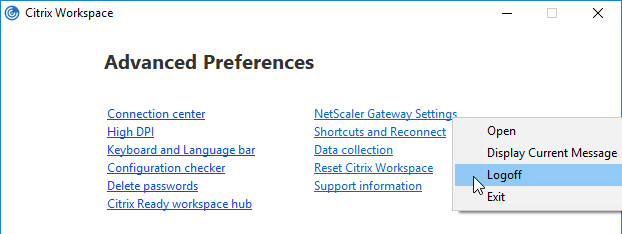
- You can configure the Session Profile to prevent the Citrix Gateway Plug-in from merging with Workspace app. Edit your VPN Session Policy/Profile. On the Client Experience tab…
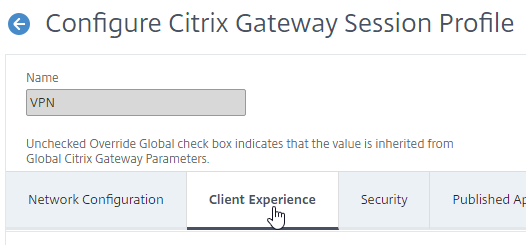
- Scroll down, and check the box next to Advanced Settings.

- At the bottom of the General tab, check the box next to Show VPN Plugin-in icon with Receiver.
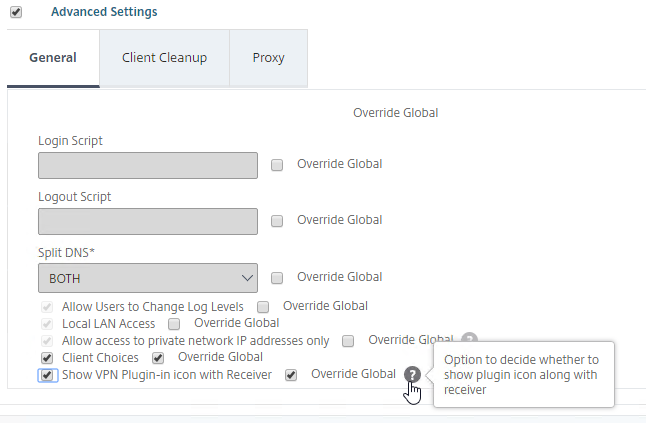
- This setting causes the two icons to be displayed separately thus making it easier to access the Citrix Gateway Plug-in settings, including Logoff.
Cleanup
- When the user logs off of VPN, a Cleanup page is displayed. This can be enabled or disabled in a Session Profile on the Client Experience tab.
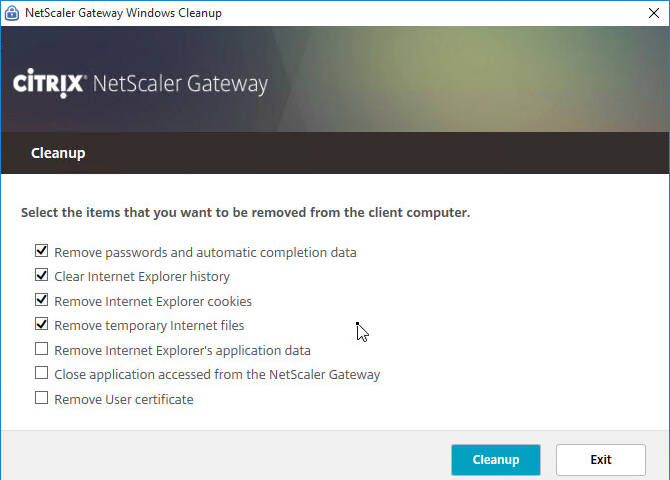
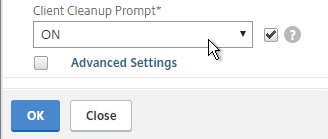
- The cleanup options can be forced in a Session Profile on the Client Experience tab…
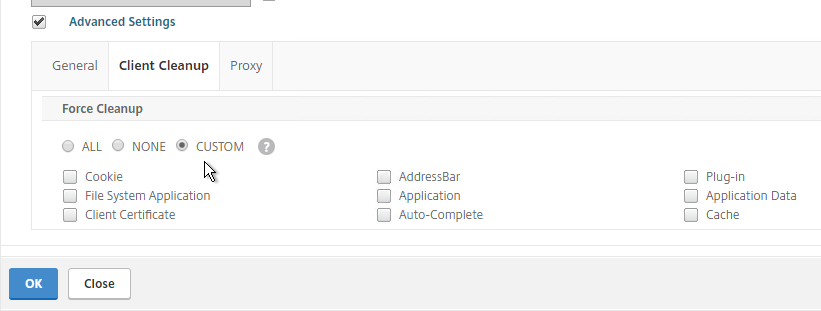
- Under Advanced Settings > Client Cleanup.
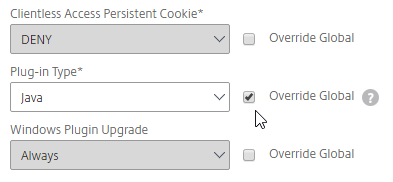
VPN Client Upgrades
- Whenever Citrix ADC firmware is upgraded, all users will be prompted to upgrade their VPN clients. You can edit a Session Policy/Profile, and on the Client Experience tab…
- Use the Upgrade drop-downs to disable the automatic upgrade.
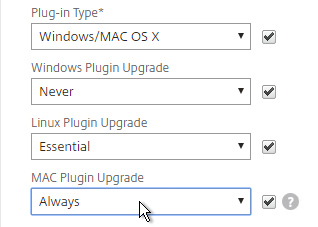
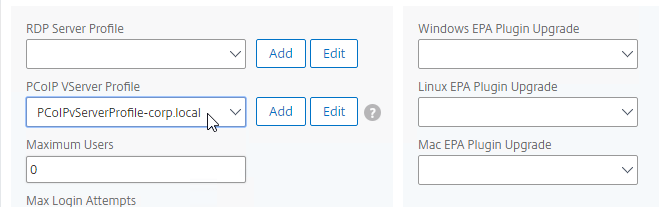
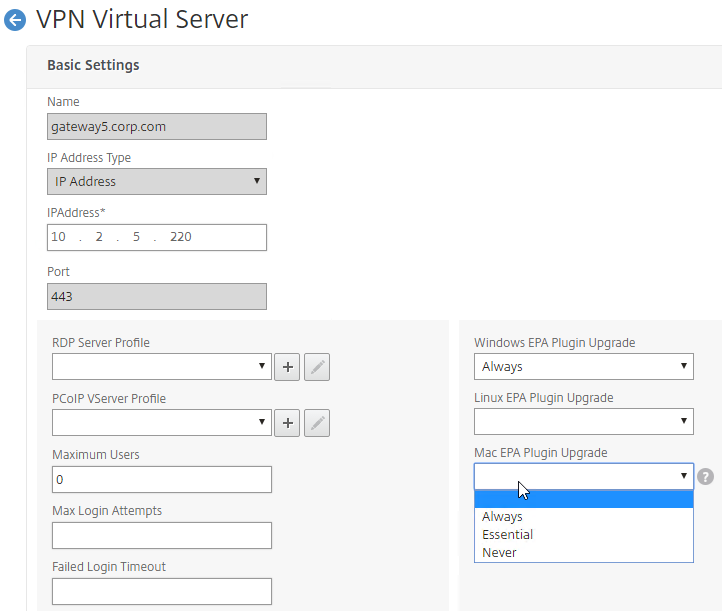
- The Plugin Upgrade settings are also configurable in the Gateway Virtual Server…
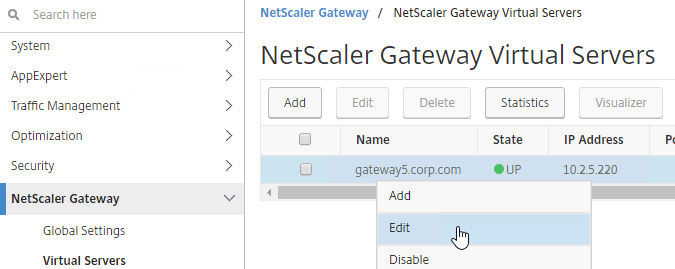
- In the Basic Settings > More section.
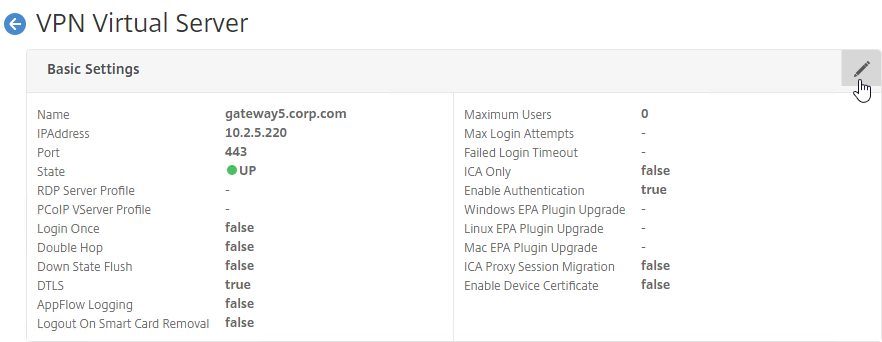
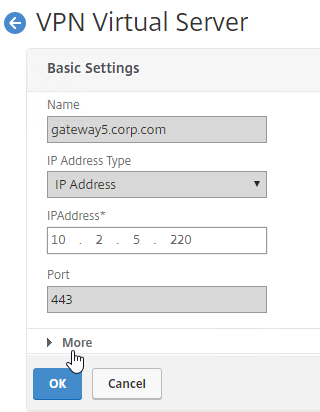
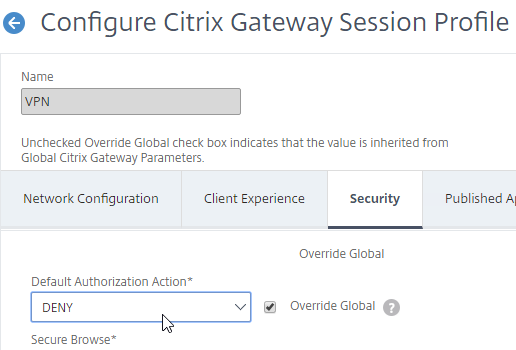
Authorization Policies
If your Session Profile has Security tab > Default Authorization Action set to Deny (recommended), then create Authorization Policies to allow access across the tunnel.
- On the left, under Citrix Gateway, expand Policies, and click Authorization.
- On the right, click Add.
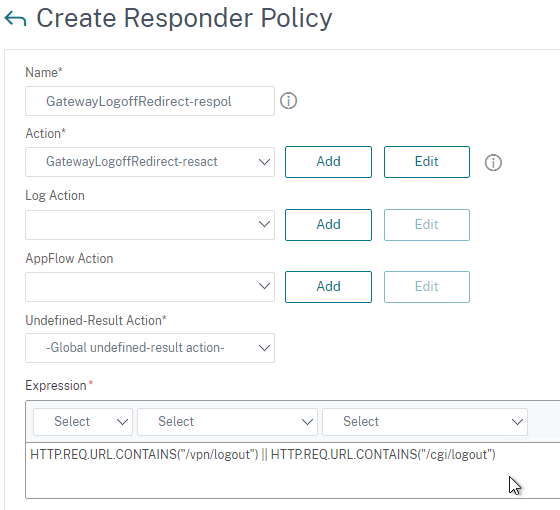
- Name the Authorization Policy.
- Select Allow or Deny.
- For the Expression, Citrix Gateway supports both Classic Syntax and Default Syntax.
- Default Syntax gives you much greater flexibility in matching the traffic that should be allowed or denied. Hit Control+Space on your keyboard to begin building a Default Syntax expression. You typically want to identify traffic based on Destination IP Address, Destination Port Number, HTTP Request URL, HTTP Host Header, etc. Common expressions include:
CLIENT.IP.DST.IN_SUBNET()CLIENT.TCP.DSTPORT.EQ()- You can also use
HTTP.REQ.USER.IS_MEMBER_OF("MyADGroup")in your expressions.
- CTX232237 NetScaler Unified Gateway Advanced Authorization Policy Support for UDP/ICMP/DNS Traffic explains new types of Authorization Policies in NetScaler 12.0 build 56 and newer.
CLIENT.UDP.DSTPORT.EQ(2080)CLIENT.IP.PROTOCOL.EQ(ICMP)CLIENT.UDP.DNS.DOMAIN.CONTAINS("citrix")
- Note: you cannot mix both Classic Syntax and Default Syntax. You must unbind every Classic Syntax Authorization Policy before you can bind Default Syntax Authorization Policies.
- Default Syntax gives you much greater flexibility in matching the traffic that should be allowed or denied. Hit Control+Space on your keyboard to begin building a Default Syntax expression. You typically want to identify traffic based on Destination IP Address, Destination Port Number, HTTP Request URL, HTTP Host Header, etc. Common expressions include:
- Click Create when done.
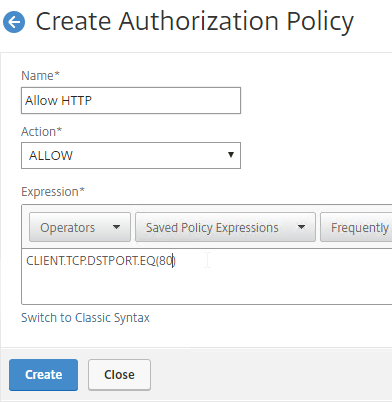
- Authorization Policies are usually bound to AAA groups. This allows different groups to have different access across the tunnel.
- Or, you can use
HTTP.REQ.USER.IS_MEMBER_OF("MyADGroup")in your Default Syntax expressions.
- Or, you can use
- Edit a AAA Group at Citrix Gateway > User Administration > AAA Groups.
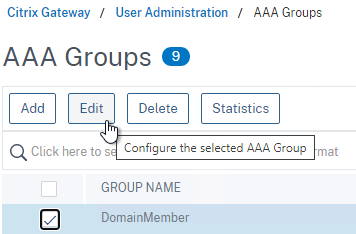
- On the right, in the Advanced Settings column, add the Authorization Policies section.
- Then click where it says No Authorization Policy to bind policies.
- CTX232237 NetScaler Unified Gateway Advanced Authorization Policy Support for UDP/ICMP/DNS Traffic explains new types of Authorization Policies in NetScaler 12.0 build 56 and newer.
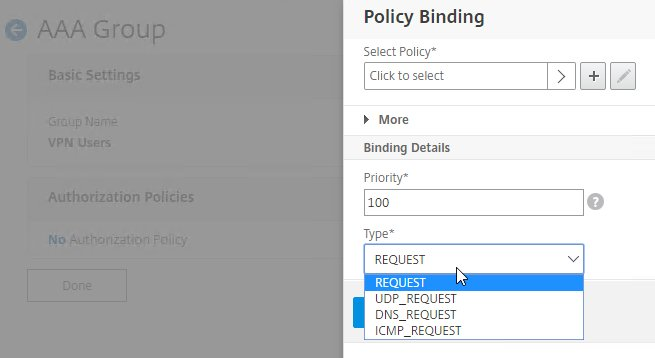
- CTX232237 NetScaler Unified Gateway Advanced Authorization Policy Support for UDP/ICMP/DNS Traffic explains new types of Authorization Policies in NetScaler 12.0 build 56 and newer.
Intranet Applications
If you enabled Split Tunnel, then you’ll need to create Intranet Applications to specify which traffic goes through the tunnel.
- On the left, under Citrix Gateway, expand Resources, and click Intranet Applications.
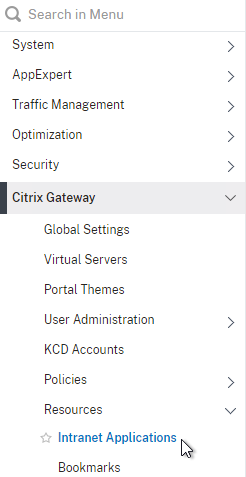
- On the right, click Add.
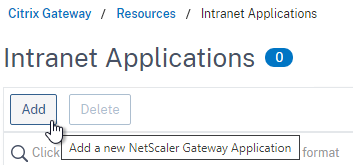
- Enter a name for the Internal subnet.
- Change the Interception Mode to TRANSPARENT.
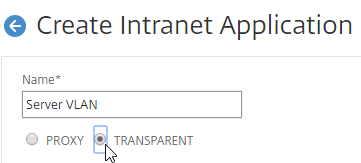
- Enter an IP subnet. Only packets destined for this network go across the tunnel.
- You typically specify a summary address for all internal subnets (e.g. 10.0.0.0/8).
- Alternatively, you can define minimal Intranet Application destinations as a security mechanism (assuming Split Tunnel is enabled), but Authorization Policies are more appropriate for that task.
- Click Create.
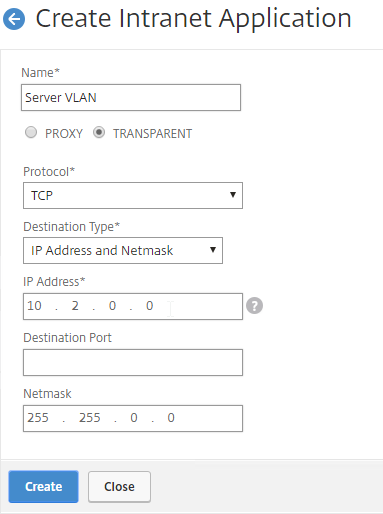
- Create additional Intranet applications for each internal subnet.
- Intranet Applications are usually bound to the Gateway Virtual Server, but you can also bind them to AAA Groups.
- On the right, in the Advanced Settings column, add the Intranet Applications section.
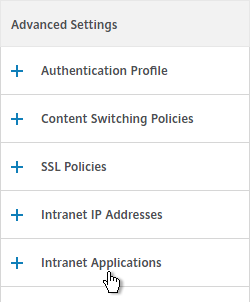
- On the left, click No Intranet Application to bind Intranet Applications.
DNS Suffix
Specify a DNS Suffix for Split DNS to function with single label DNS names. Citrix Gateway adds these DNS suffixes to DNS queries across the VPN tunnel.
- On the left, under Citrix Gateway, expand Resources, and click DNS Suffix.
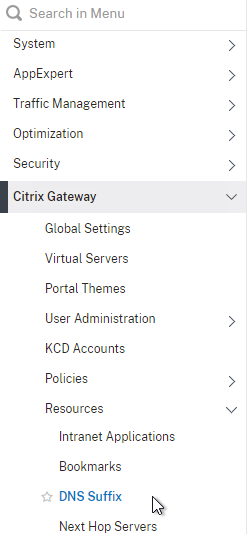
- On the right, click Add.
- Enter the DNS Suffix, and click Create. You can add multiple suffixes.
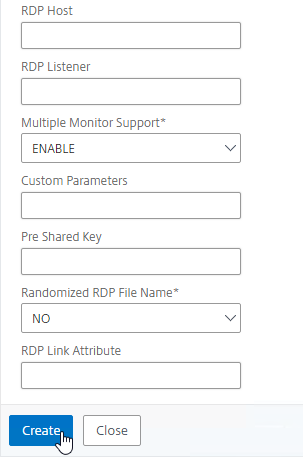
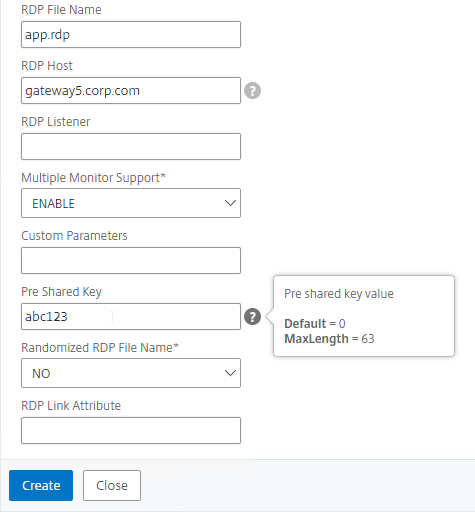
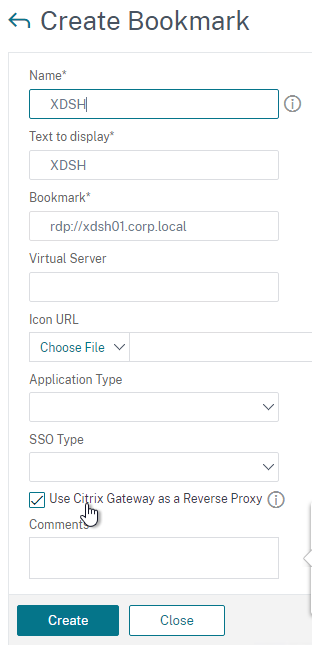
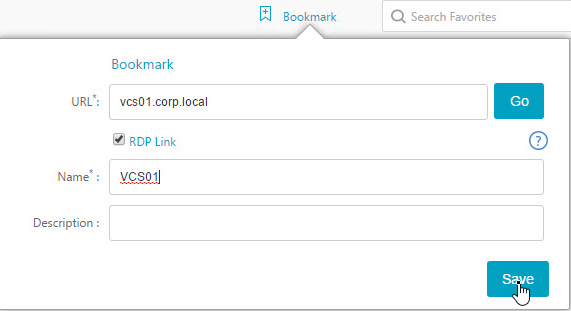
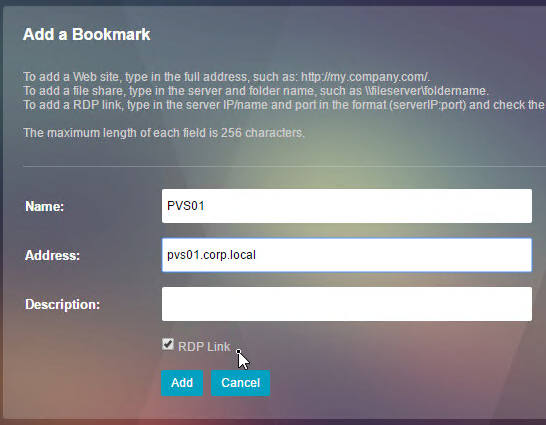
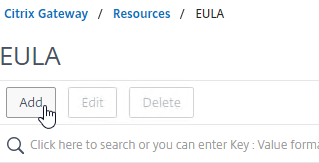
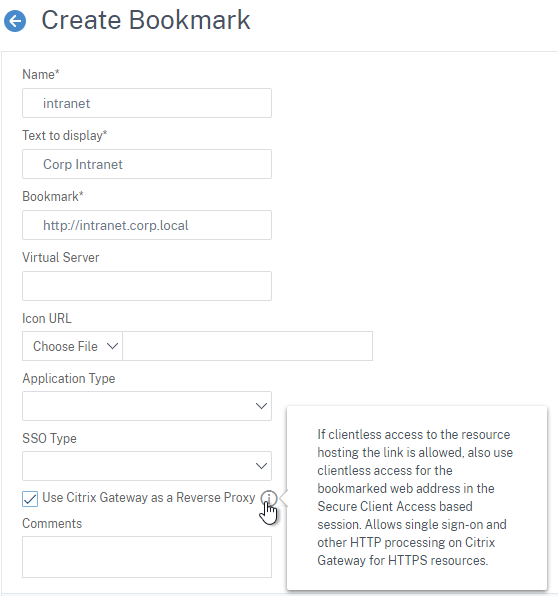
Bookmarks
Bookmarks are the links that are displayed in the default portal interface. They can point to websites, or RDP addresses. PCoIP bookmarks come from VMware Horizon Connection Server. ICA bookmarks come from Citrix StoreFront.
- Under Citrix Gateway, expand Resources, and click Bookmarks.
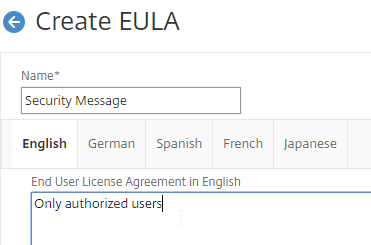
- On the right, click Add.
- Give the bookmark a name, and display text.
- Enter a website or RDP address.
- Optionally browse to an Icon file.
- You typically need to check Use Citrix Gateway As a Reverse Proxy, especially for Clientless Access (rewrite without VPN) to an internal website.
- The other fields are for Single Sign-on through Unified Gateway.
- Click Create.
- Bookmarks (aka Published Applications > Url) are usually bound to AAA groups so different groups can have different bookmarks. But it’s also possible to bind Bookmarks to Citrix Gateway Virtual Servers.
- If Citrix Gateway Virtual Server, add the Published Applications section to bind Bookmarks (Url).

- For AAA Group, it’s the Bookmarks section.
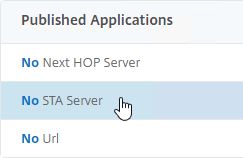
- On the left, find the Published Applications section, and click No Url to bind Bookmarks.
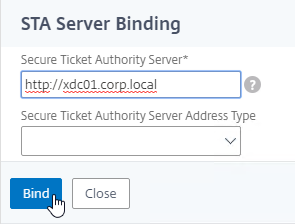
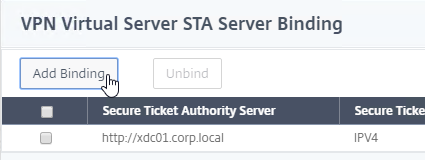
VPN Client IP Pools (Intranet IPs)
By default, Citrix Gateway VPN clients use Citrix ADC SNIP as their source IP when communicating with internal resources. To support IP Phones or endpoint management, you must instead assign IP addresses to VPN clients.
Any IP pool you add to Citrix Gateway must be reachable from the internal network. Configure a static route on the upstream router. The reply traffic to VPN Client IPs should be routed through a Citrix ADC SNIP. Or the Citrix ADC can participate in OSPF.
When a client is assigned a client IP, this IP address persists across multiple sessions until the appliance reboots, or until the appliance runs out of IPs in the pool.
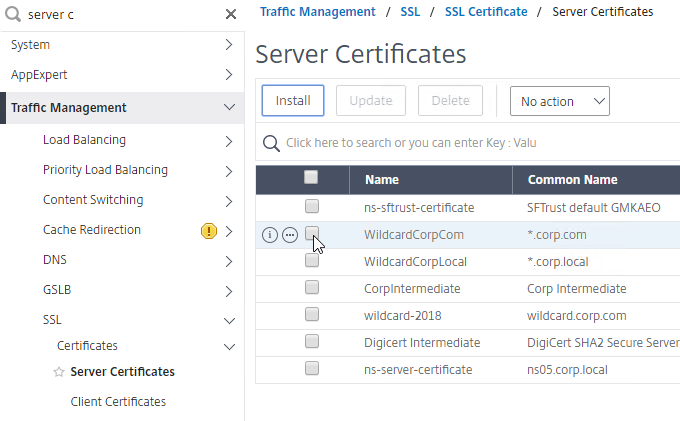
- Edit a Citrix Gateway Virtual Server, or a AAA group.
- On the right, in the Advanced Settings section, click the plus icon next to Intranet IP Addresses.
- On the left, click where it says No Intranet IP.
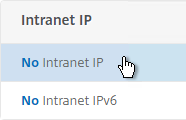
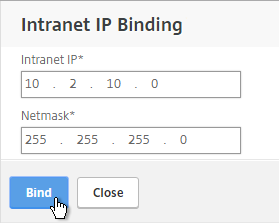
- Enter a subnet and netmask. Click Bind.
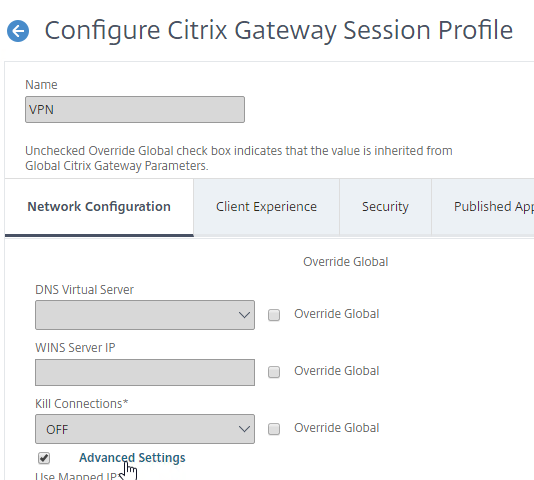
- In a Session Profile, on the Network Configuration tab, check the box next to Advanced Settings.
- Use the Intranet IP drop-down to configure the behavior when there are more VPN clients than available IPs in the address pool.
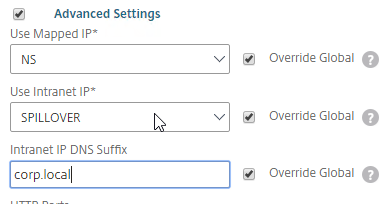
- If you set it to NOSPILLOVER, then users can only have one VPN session, as described in CTX218066 How to Limit One Session Per User on NetScaler Gateway?.
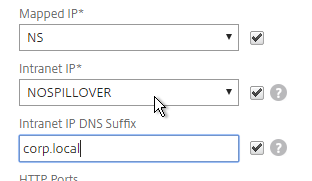
- If you set it to NOSPILLOVER, then users can only have one VPN session, as described in CTX218066 How to Limit One Session Per User on NetScaler Gateway?.
- To see the Client IP address, on the client side, after the tunnel is established, right-click the Citrix Gateway Plug-in, and click Open.
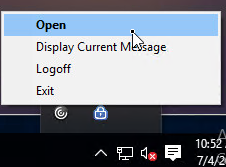
- See the Internal network address.
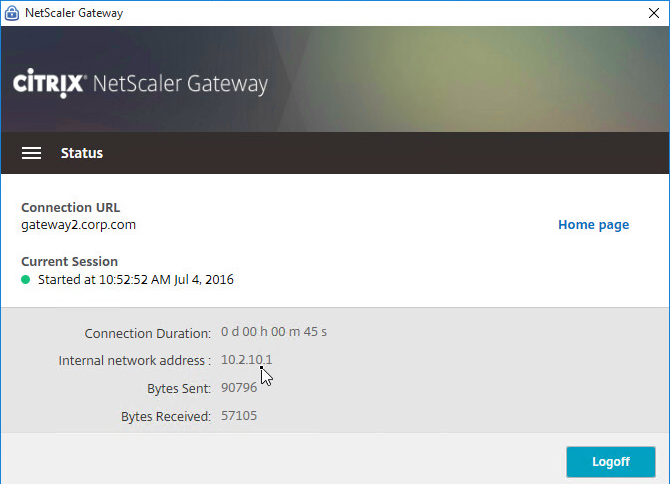
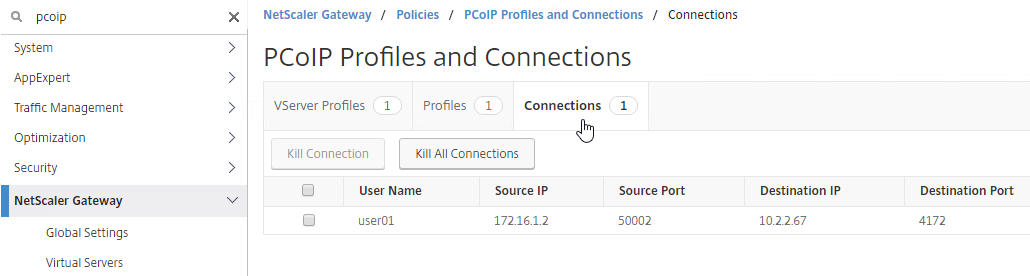
- To see the client IP on the Citrix ADC, go to Citrix Gateway, and on the right is Active user sessions.
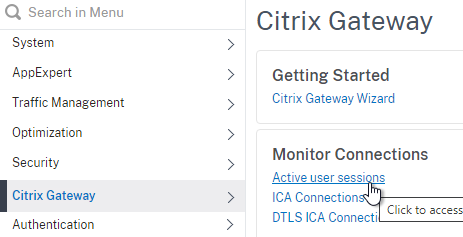
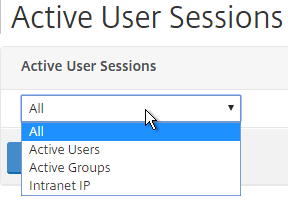
- Select one of the views, and click Continue.
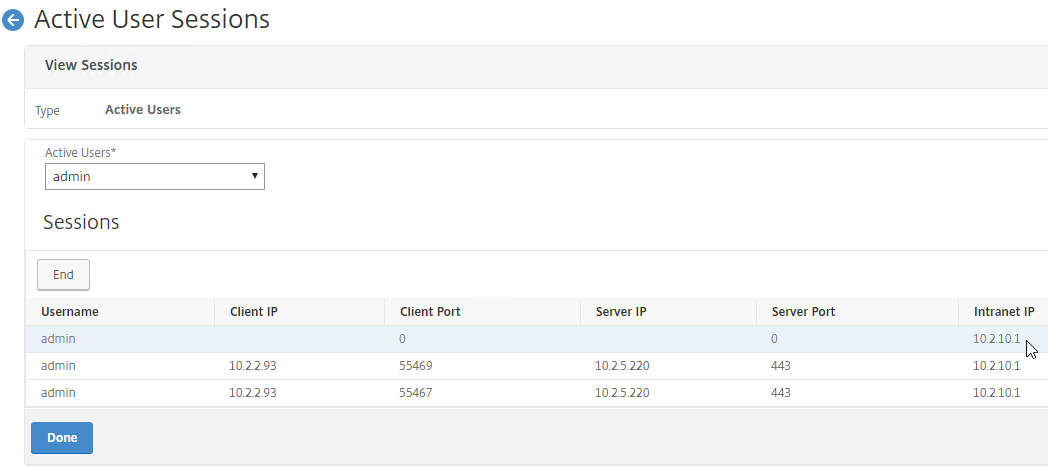
- The right column contains the Intranet IP.
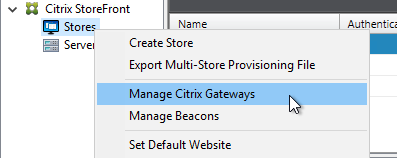
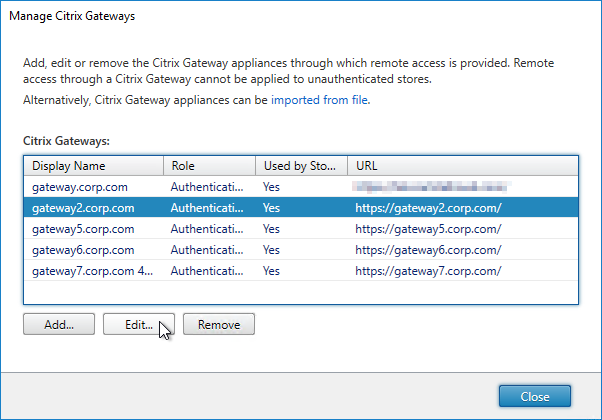
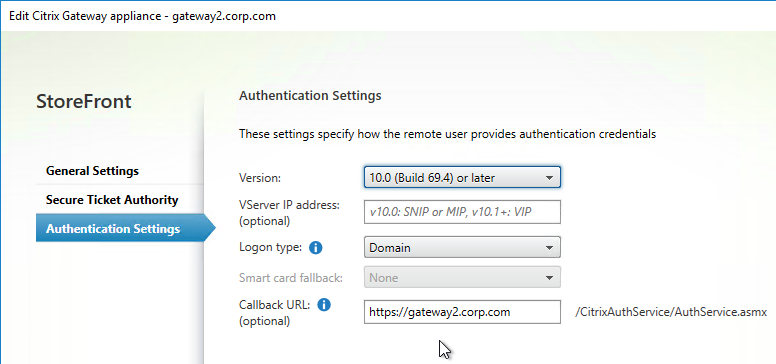
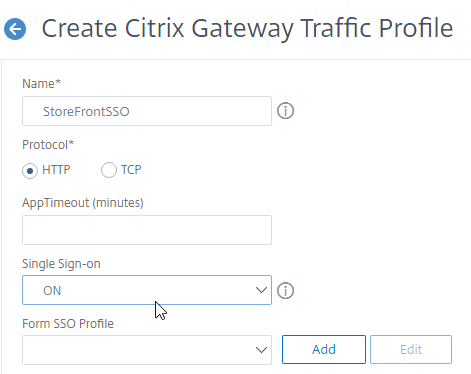
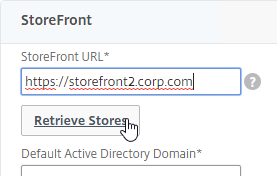
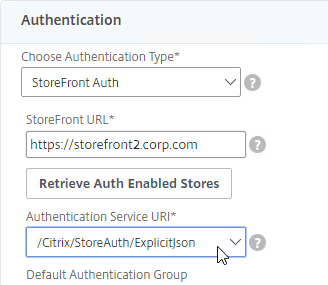
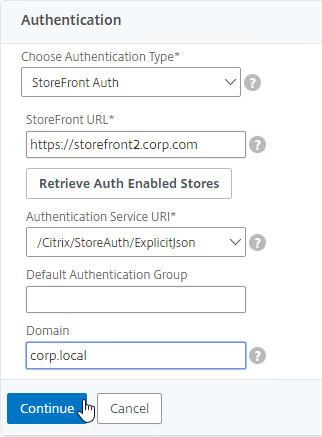
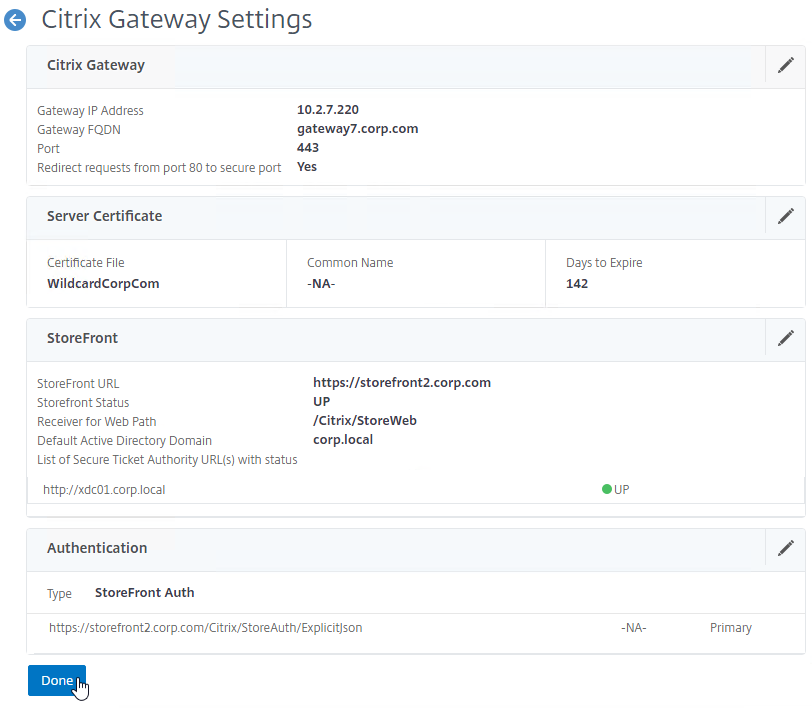
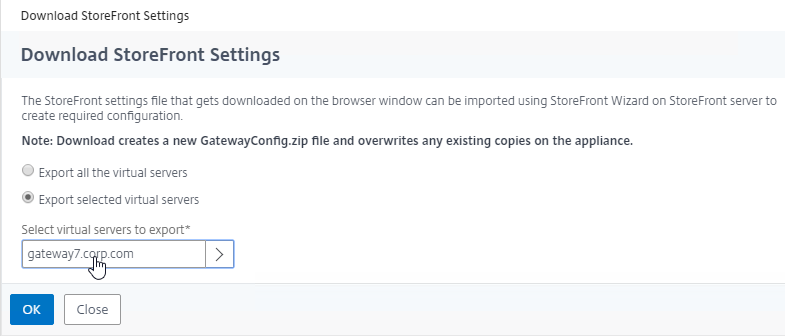
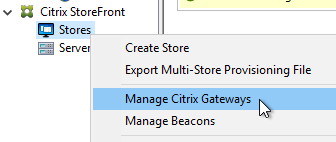
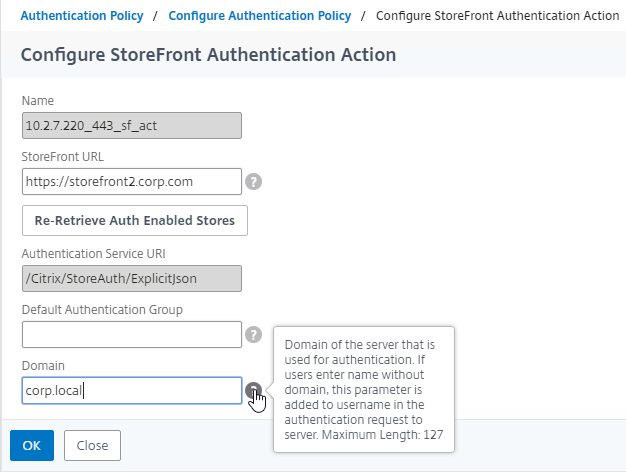
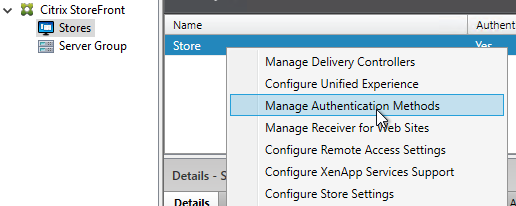
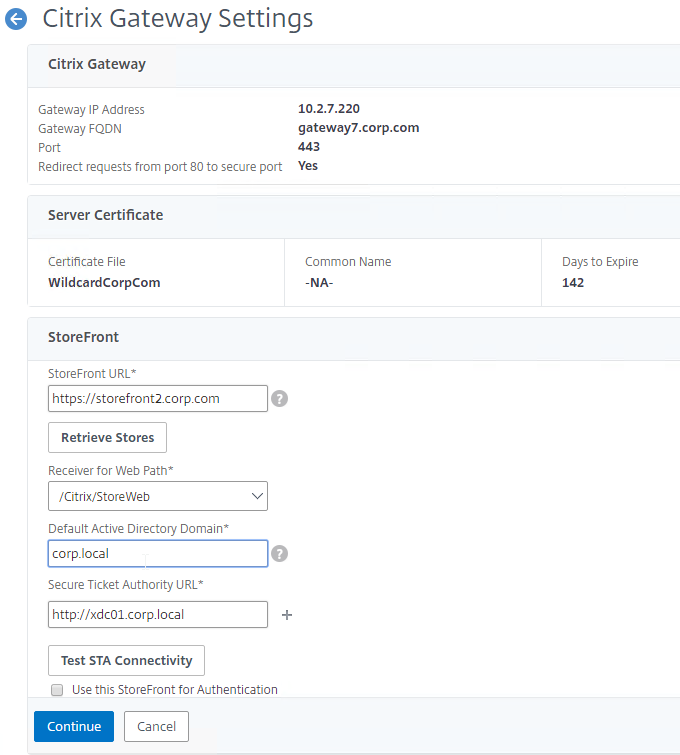
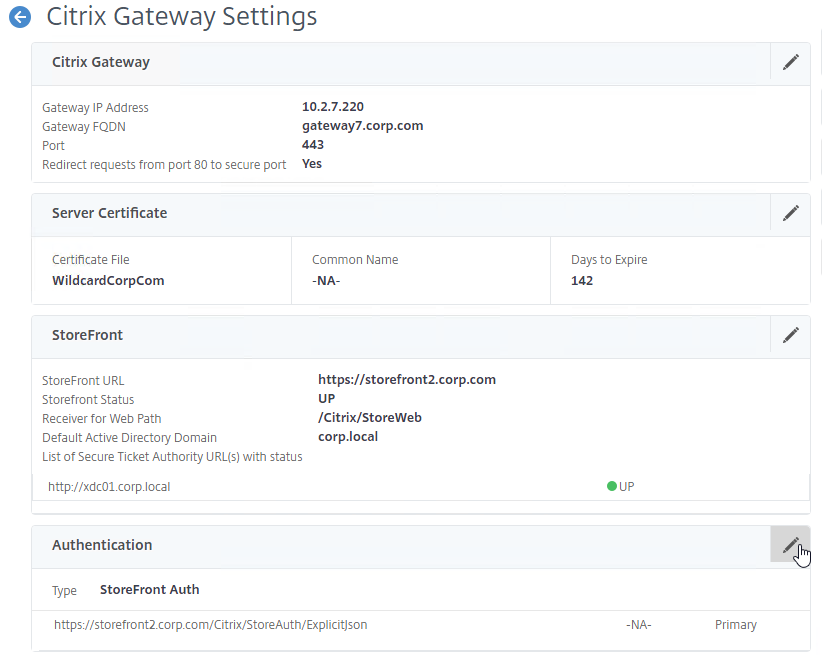
StoreFront in Gateway Clientless Access Portal
If you enabled the RfWebUI theme, then no StoreFront configuration is necessary.
But if you want to embed StoreFront in the other Gateway themes (X1, Default, Green Bubble), then follow these instructions.
- On StoreFront, edit the file C:\Inetpub\wwwroot\Citrix\StoreWeb\web.config.
- On the bottom, there are three sections containing X-Frame-Options. Change all three of them from deny to allow.
- Also change frame-ancestors from none to self.
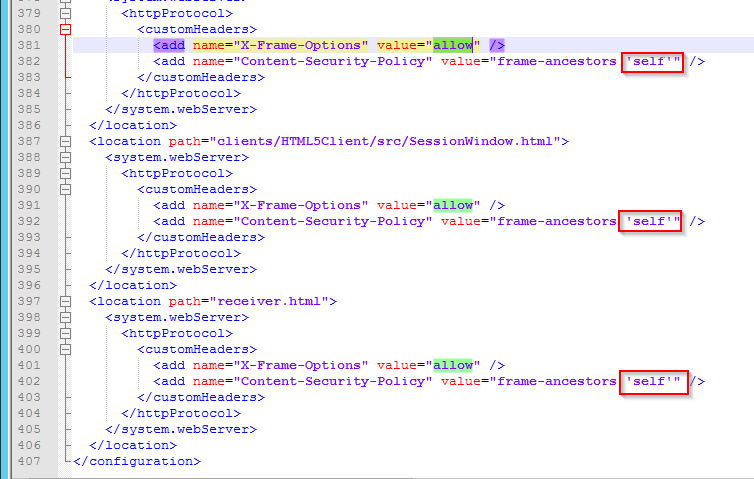
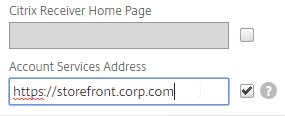
- In Citrix ADC, go to Citrix Gateway > Global Settings, and click Configure Domains for Clientless Access.
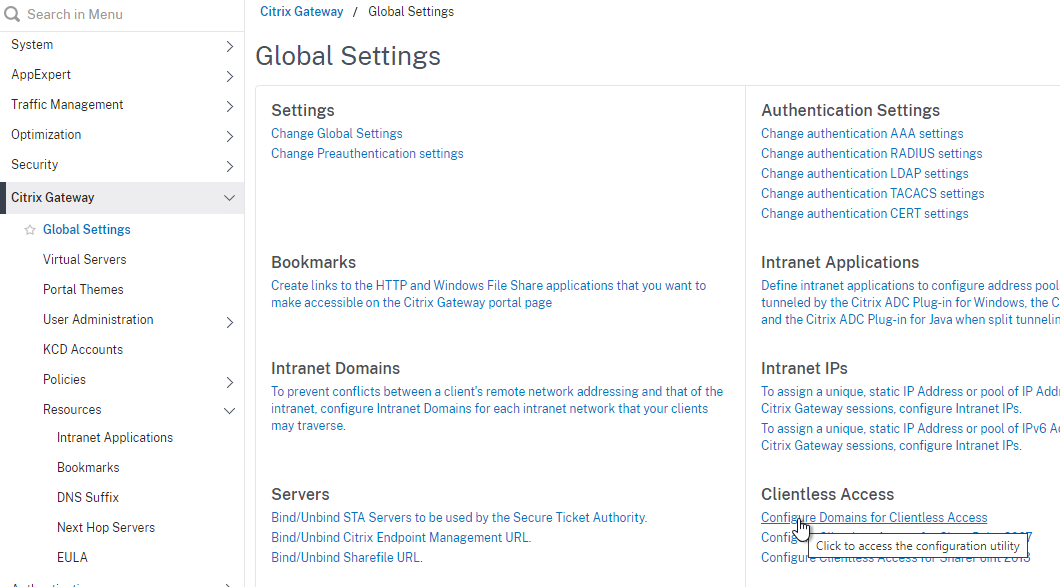
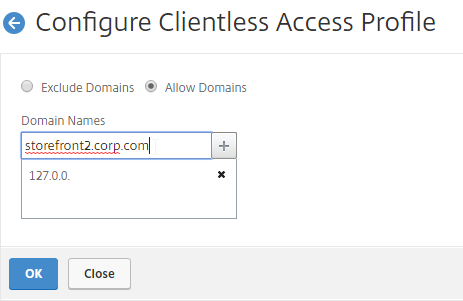
- Change the selection to Allow Domains, enter your StoreFront FQDN, and click the plus icon.
- Click OK.
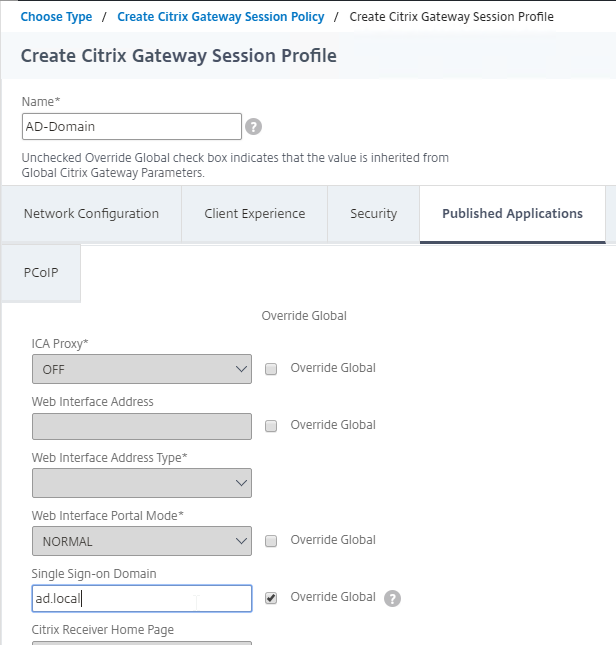
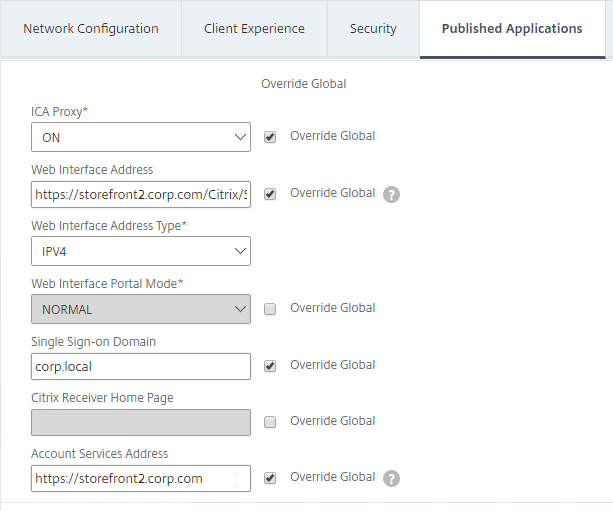
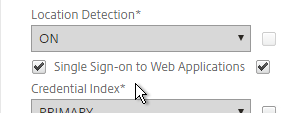
- In a Session Policy/Profile:
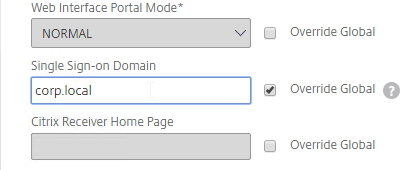
- On the Client Experience tab, make sure Single Sign-on to Web Applications is enabled.
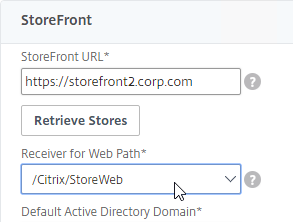
- On the Published Applications tab, configure the Web Interface Address to point to the StoreFront Receiver for Web page.
- Configure the Single Sign-on domain to match what’s configured in StoreFront.
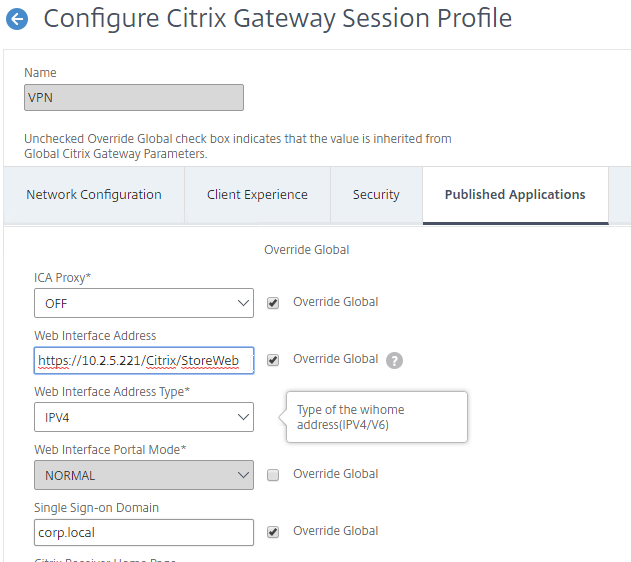
- You might have to override the Web Interface Portal Mode.
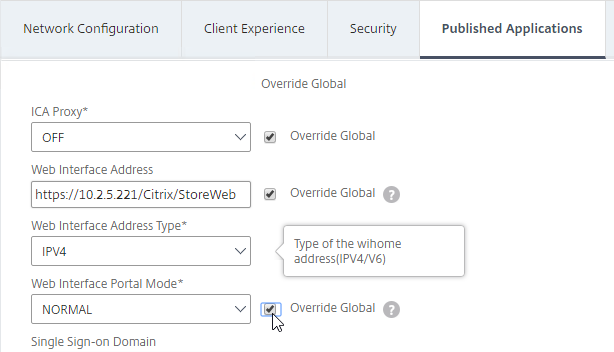
- On the Client Experience tab, make sure Single Sign-on to Web Applications is enabled.
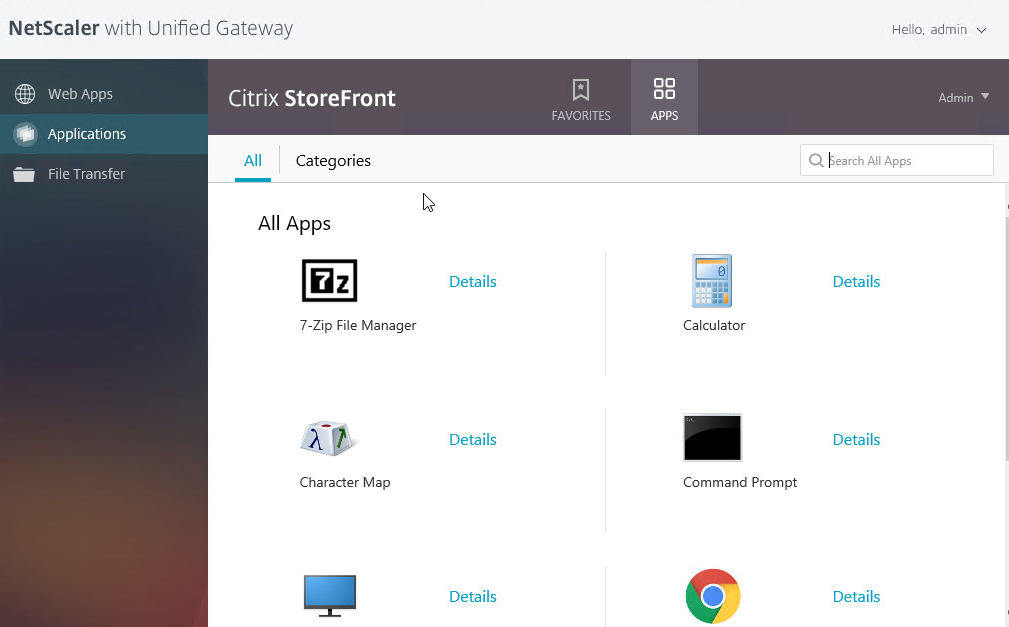
- The Applications page of the 3-page portal (e.g. X1 theme) should automatically show the StoreFront published icons.
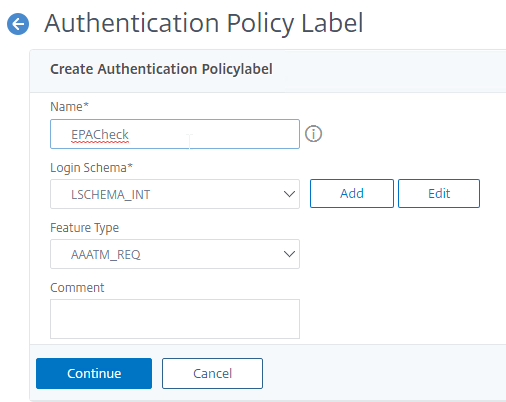
Quarantine Group
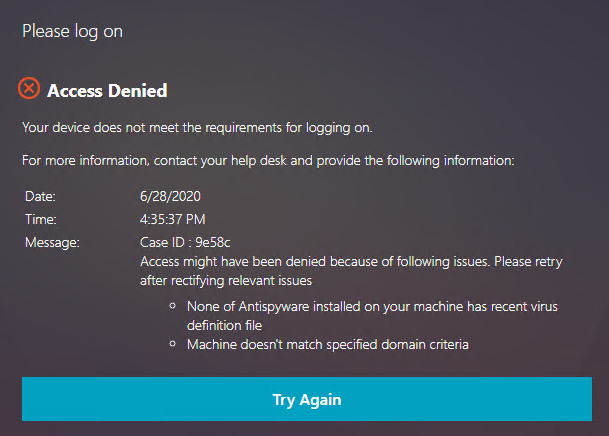
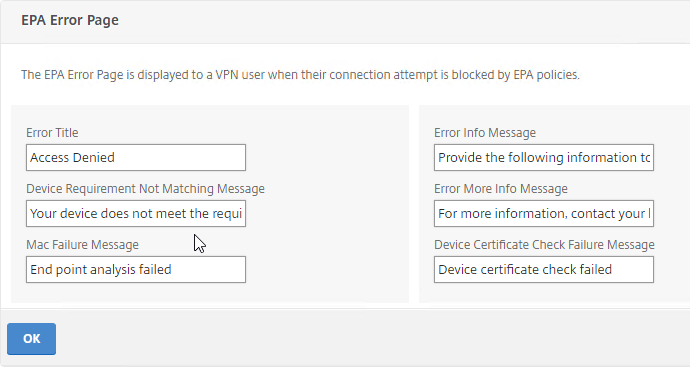
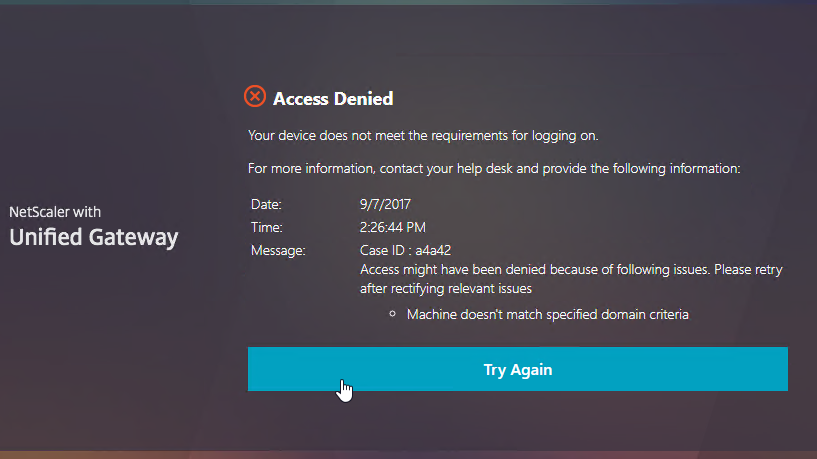
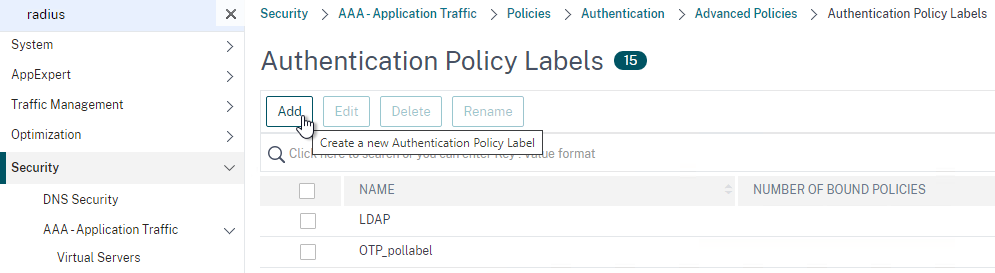
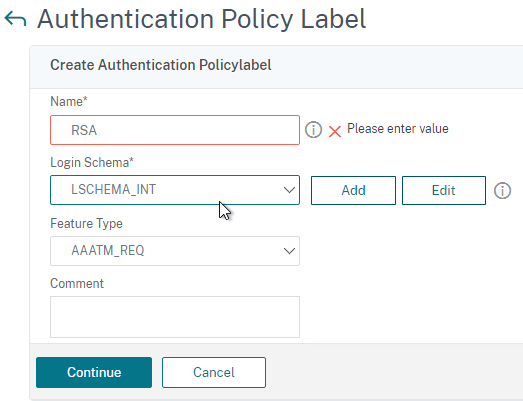
Citrix Gateway can be configured so that if Endpoint Analysis scans fail, then the user is placed into a Quarantine Group. You can bind session policies, authorization policies, etc. to this quarantine group. Policies bound to other AAA groups are ignored.
- Go to Citrix Gateway > User Administration > AAA Groups.
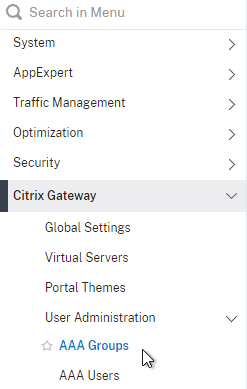
- Add a new local group for your Quarantined Users. This group is local, and does not need to exist in Active Directory.
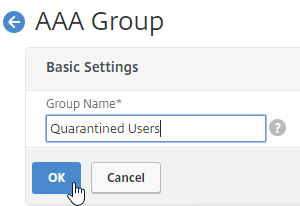
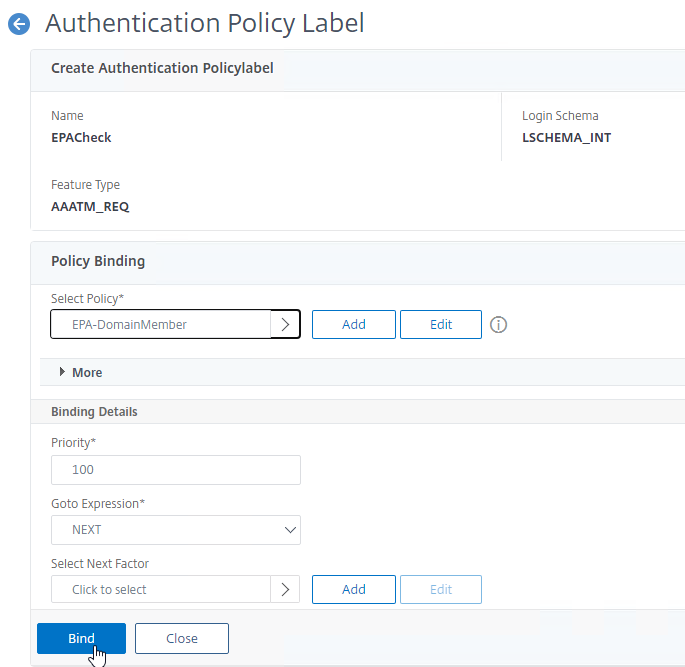
- Bind session policies, authorization policies, etc. to your quarantine AAA group. These policies typically allow limited access to the internal network so users can remediate. Or, it might simply display a webpage telling users how to become compliant.
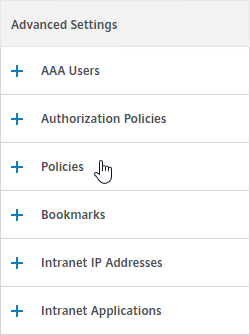
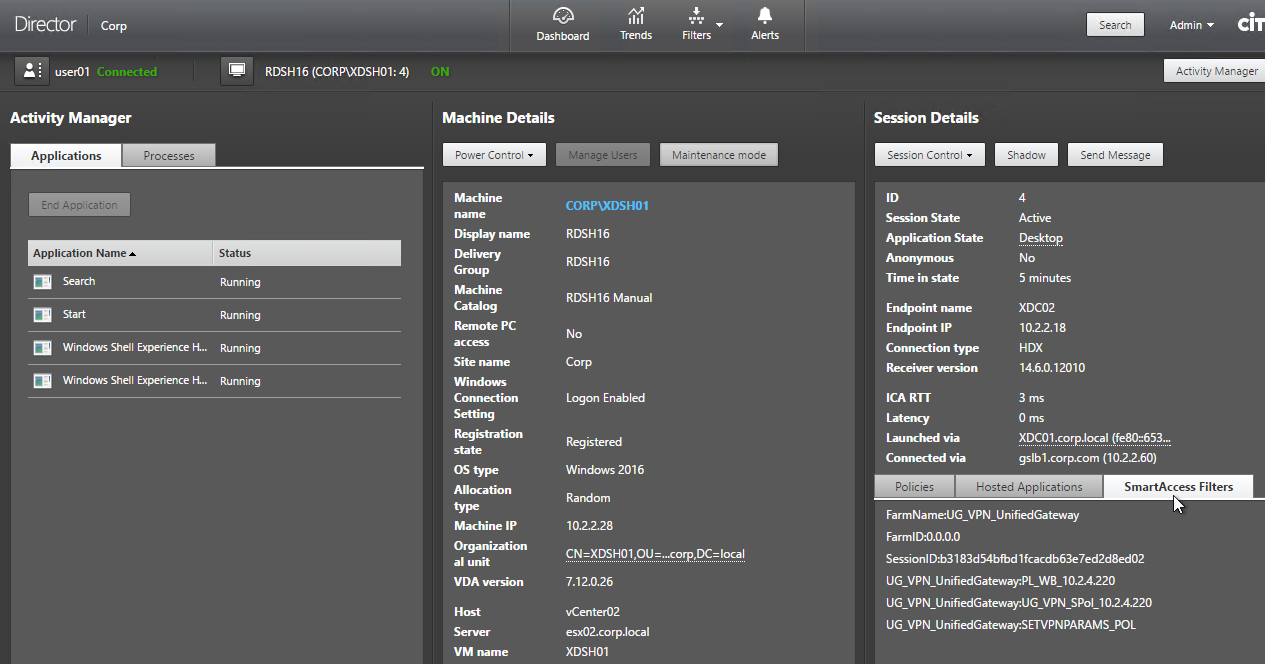
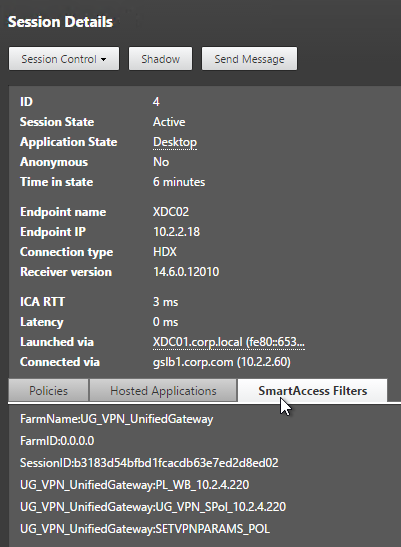
- The Session Policy bound to the Quarantine Group is usually different than the Session Policies bound to other AAA groups. You can use the variation in Session Policy names for SmartAccess.
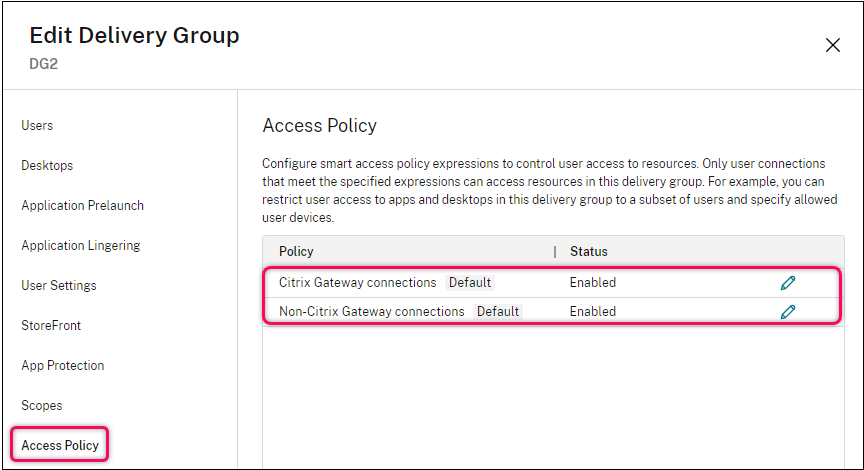
- One option is to configure the Delivery Groups > Access Policy so that icons are shown for Session Policies bound to non-quarantine AAA Groups, but not for the Session Policy that is bound to the Quarantine Group.
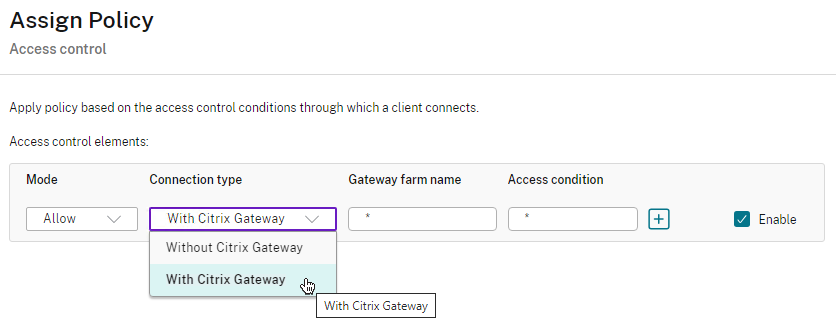
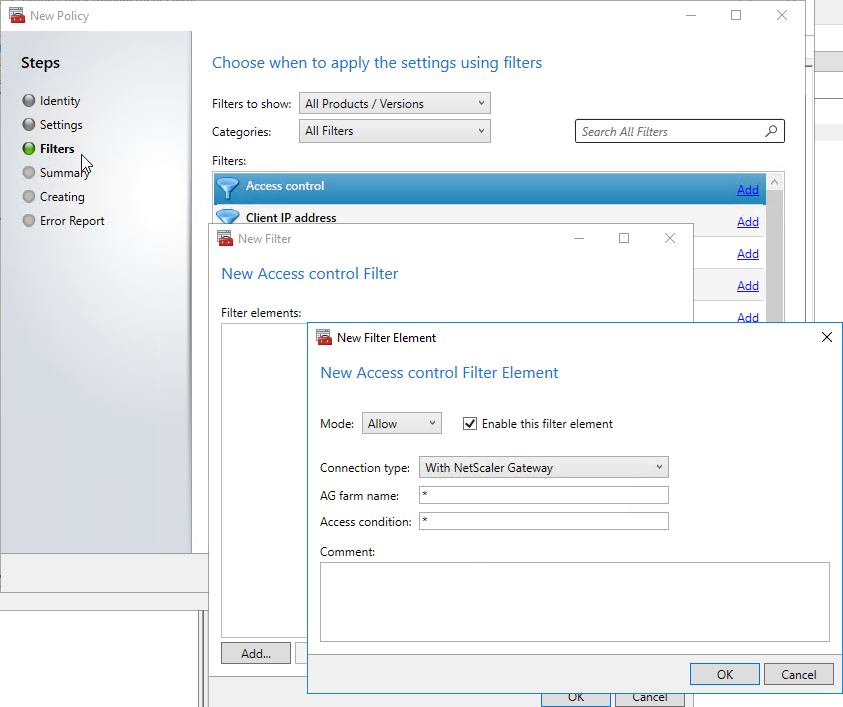
- Another option is to configure Citrix Policies > Access Control to disable functionality for the Quarantine Group Session Policy, but not for other AAA Group Session Policies.
- Add a new local group for your Quarantined Users. This group is local, and does not need to exist in Active Directory.
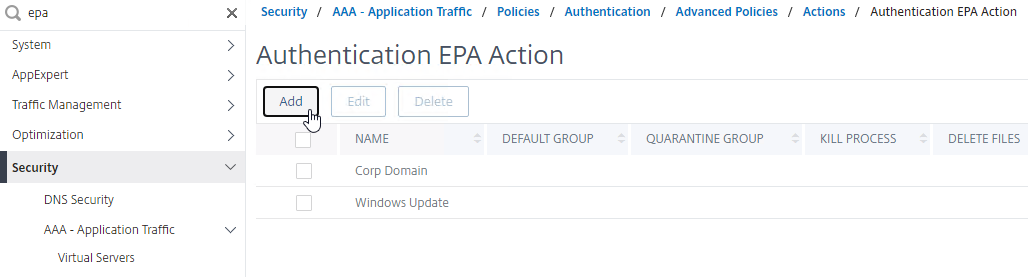
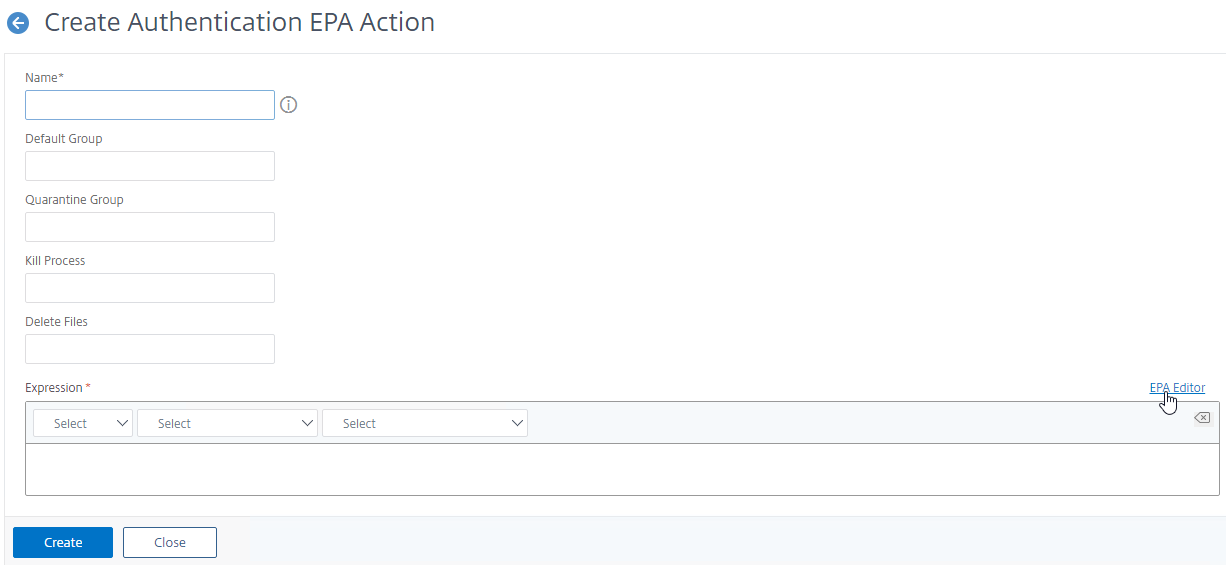
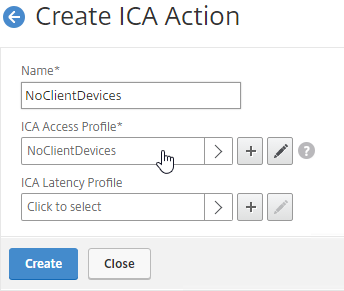
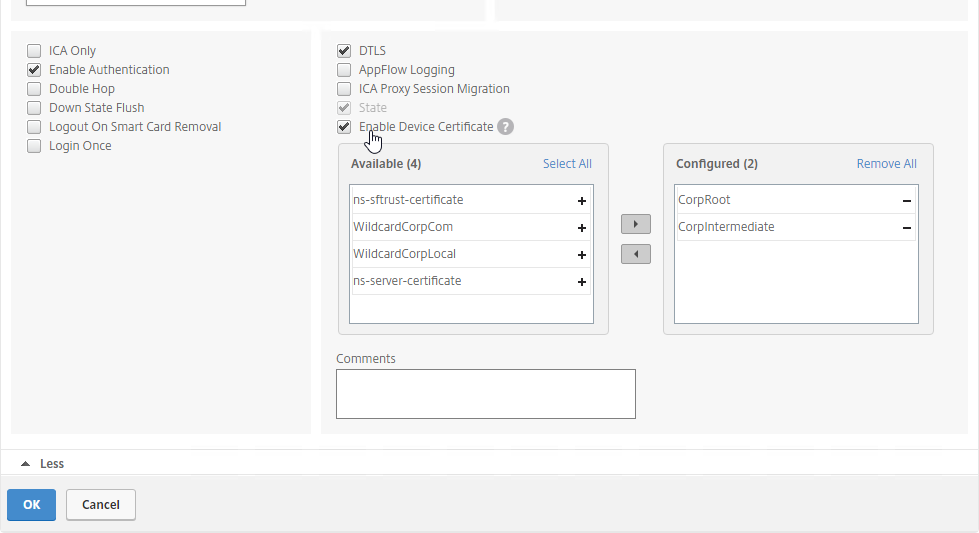
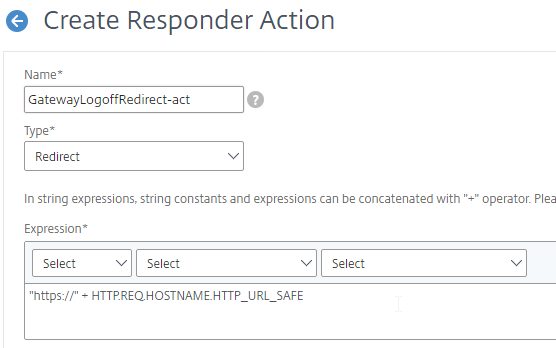
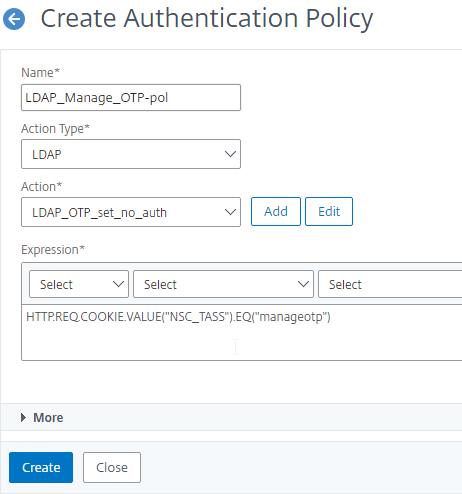
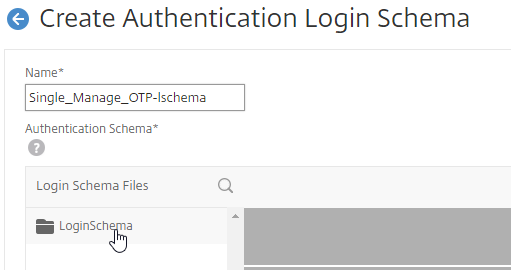
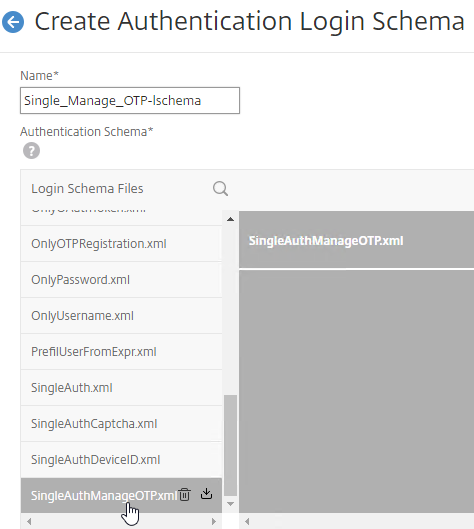
- Create or edit a Session Profile to include a Client Security Expression that checks for compliance.
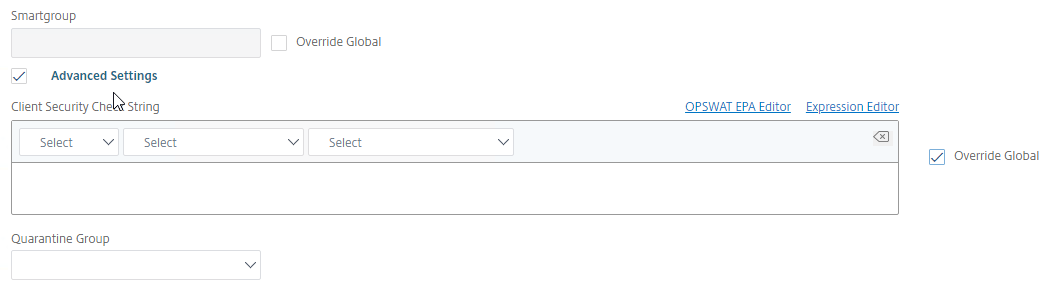
- In the Session Profile, on the Security tab, check the box next to Advanced Settings.
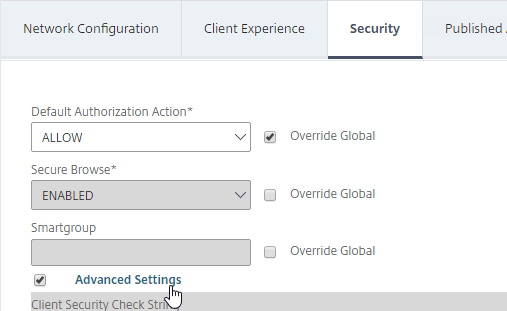
- Scroll down, and check the box to the right of Client Security Check String.
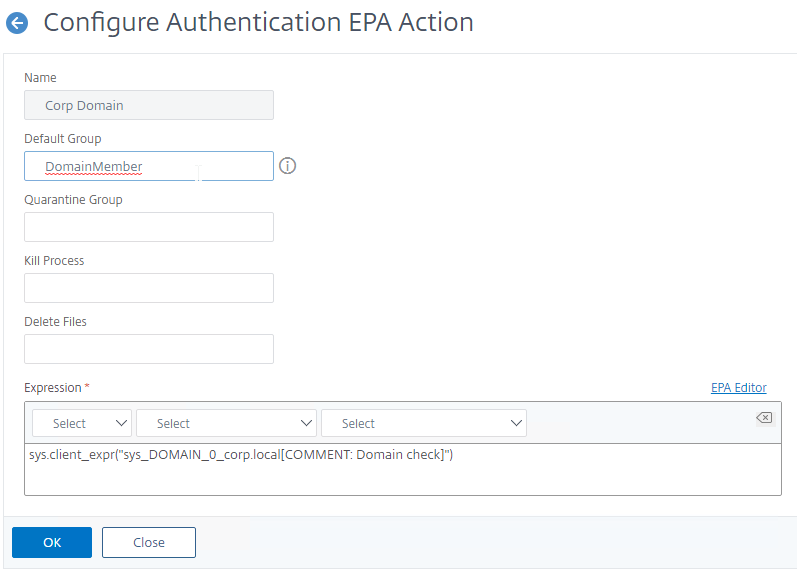
- Use the Editor links to add an Endpoint Analysis expression.
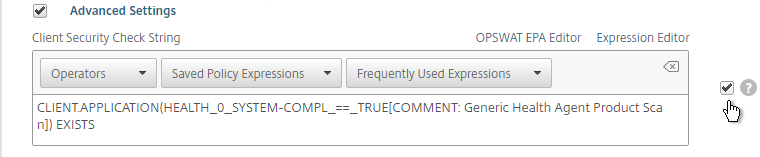
- Just below the Client Security Check String, select the previously created Quarantine Group. If the Client Security Check String EPA Scan fails, then the failed users are added to the Quarantine Group and removed from all other AAA Groups.
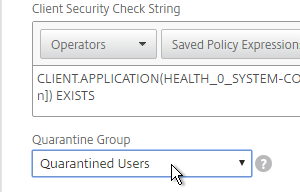
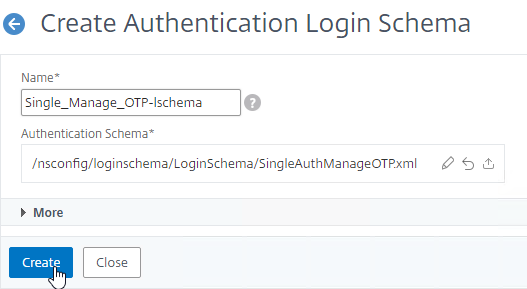
- In the Session Profile, on the Security tab, check the box next to Advanced Settings.
- Click Create when done creating or editing the Session Profile.
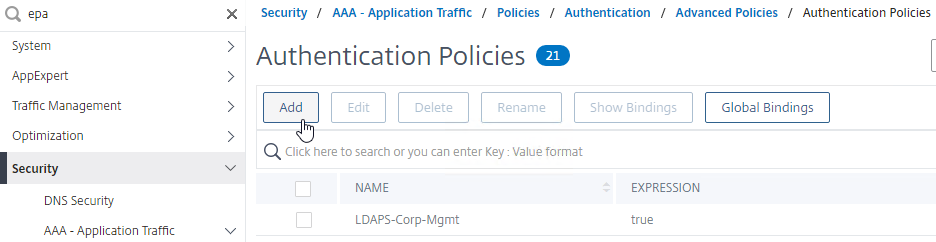
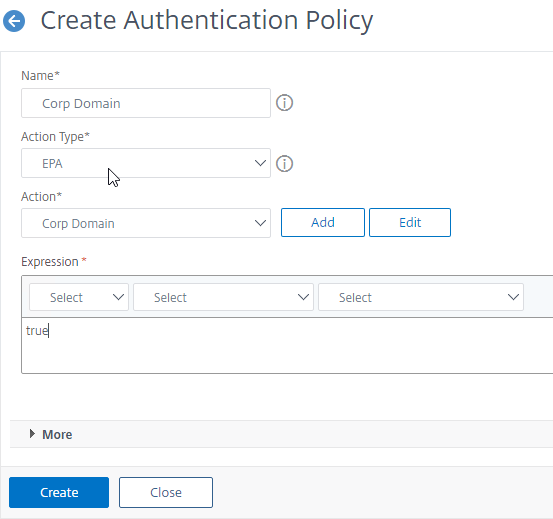
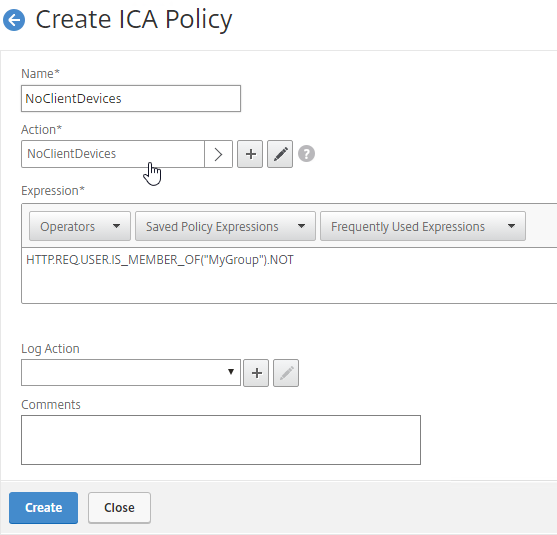
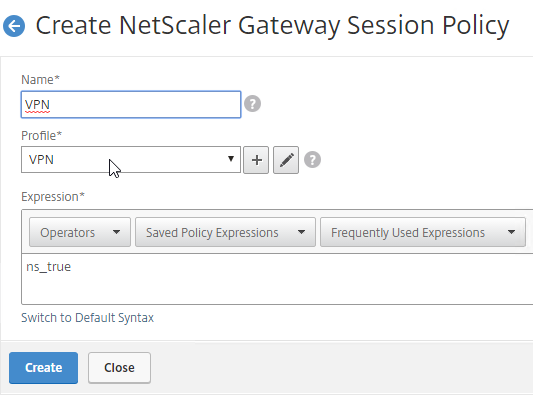
- Create a Session Policy for the Session Profile that contains the Client Security Check String.
- Enter ns_true as the expression.
- Then click Create.
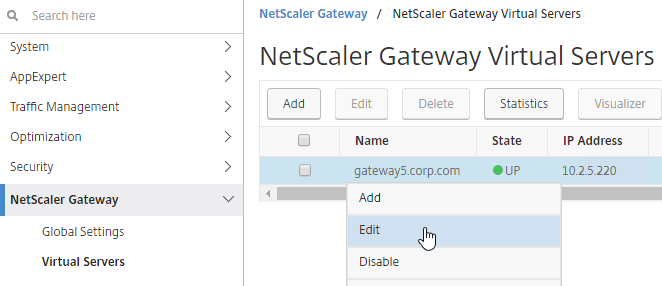
- Edit your Gateway Virtual Server, and bind the Session Policy/Profile that has the Client Security Check String configured.

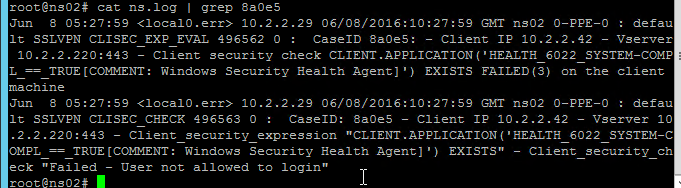
- To troubleshoot Quarantine policies, use the command
nsconmsg –d current –g pol_hits.
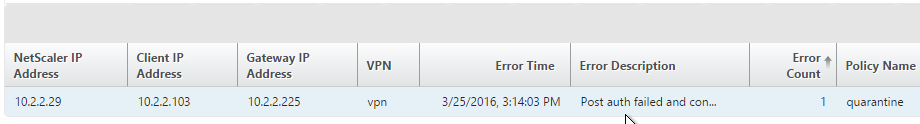
- Citrix ADM Gateway Insight shows users that failed EPA scans, and their quarantine status.