Navigation
💡 = Recently Updated
SmartAccess / SmartControl
SmartAccess and SmartControl let you change ICA connection behavior (e.g. disable client device mappings) based on how users connect. Decisions are based on NetScaler Gateway Virtual Server name, Session Policy name, and Endpoint Analysis scan success or failure.
SmartAccess can also control application/desktop icon visibility.
Prerequisites
Both SmartAccess and SmartControl have the same prerequisites. You can configure SmartAccess in XenApp/XenDesktop at any time, but it won’t work, until you do the following:
- NetScaler appliance license – SmartAccess works with all editions of NetScaler appliances. However, SmartControl only works with NetScaler Platinum Edition.
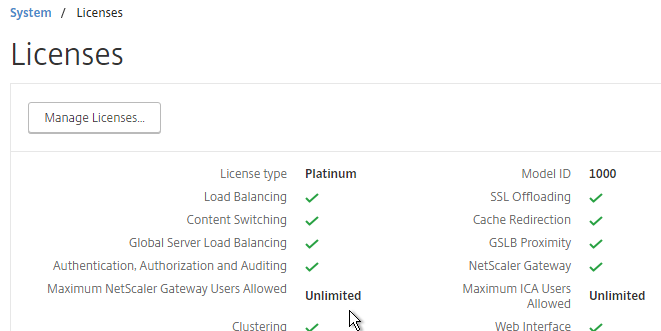
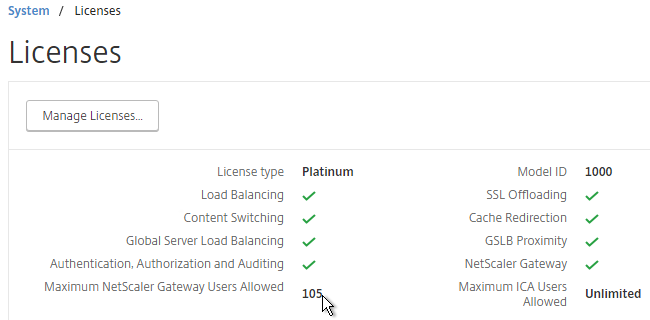
- On the NetScaler, go to System > Licenses and make sure you have NetScaler Gateway Universal Licenses allocated to the appliance.
- NetScaler 11.1 build 49 and later come with built-in Gateway Universal licenses: NetScaler Standard Edition = 500 licenses, NetScaler Enterprise Edition = 1000 licenses, and NetScaler Platinum Edition = unlimited licenses.
- The Universal licenses are allocated to the hostname of the appliance (click the gear icon), not the MAC address. In a High Availability pair, if each node has a different hostname, then you can allocate the licenses to one hostname, then reallocate to the other hostname.
- After installing licenses, go to NetScaler Gateway > Global Settings.
- On the top right, click Change authentication AAA settings.
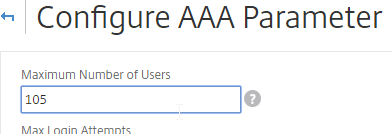
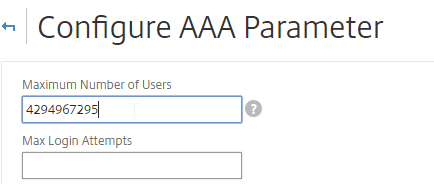
- At the top of the page, change the Maximum Number of Users to match your installed license count. Then click OK. In NetScaler 11.1 build 49 and newer, this value should already match the number of licensed users. In older builds, you must manually configure this setting, and if not configured, then it defaults to only 5 concurrent connections.
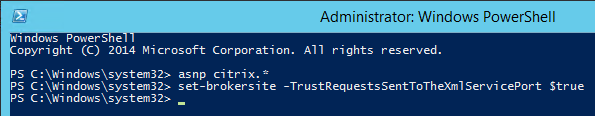
- On a XenApp/XenDesktop Controller, run PowerShell as Administrator.
- Run asnp citrix.* to load the snapins.
- Run Set-BrokerSite -TrustRequestsSentToTheXmlServicePort $true to enable Trust XML.
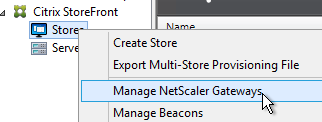
- In StoreFront Console, edit the existing Gateway object.
- Make sure a Callback URL is configured. The Callback URL must resolve to a NetScaler Gateway VIP on the same appliance that authenticated the user. The Callback Gateway’s certificate must match the FQDN entered here. If you are configuring Single FQDN for internal and external, then the Callback FQDN must be different than the Single FQDN.
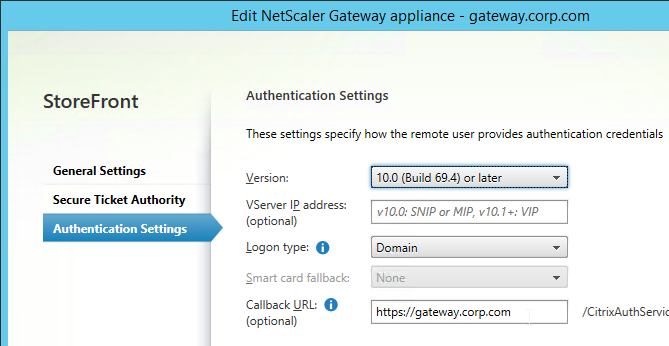
- On the NetScaler, go to NetScaler Gateway > Virtual Servers, and edit your Gateway Virtual Server.
- In the Basic Settings section, click the pencil icon.
- Click More.
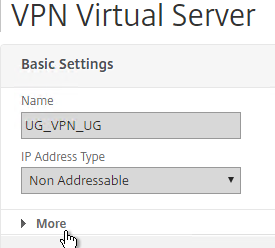
- Uncheck the box next to ICA Only, and click OK. This tells NetScaler Gateway to start using Universal licenses, and enables the SmartAccess and SmartControl features.
Once the prerequisites are in place, do the following as detailed below:
- Optionally, configure Endpoint Analysis.
- Configure either SmartControl or SmartAccess.
Endpoint Analysis
Endpoint Analysis scans are completely optional. You can configure SmartControl and SmartAccess without implementing any Endpoint Analysis.
Endpoint Analysis is supported on Windows and Mac devices. Other devices, like iOS and Android, do not support Endpoint Analysis. If you want to allow mobile device connectivity, then make sure you have an access mechanism (e.g. ICA Proxy) that works if the Endpoint Analysis scan fails.
There are two methods of Endpoint Analysis: pre-authentication and post-authentication. For pre-authentication, configure an Endpoint Analysis expression in a Preauthentication Policy. For post-authentication, configure the Endpoint Analysis expression on one or more Session Policies.
- With a Preauthentication Policy, if the Endpoint Analysis scan fails, then users can’t login.
- With a Postauthentication Policy, Endpoint Analysis doesn’t run until after the user logs in. Typically, you create multiple Session Policies. One or more Session Policies has Endpoint Analysis expressions. Leave one policy without an Endpoint Analysis expression so there’s a fallback in case the client device doesn’t support Endpoint Analysis (e.g. mobile devices). The name of the Session Policy is then used later in Citrix Policies and Citrix Delivery Groups.
NetScaler has two Endpoint Analysis engines: the classic Client Security engine, and the newer OPSWAT Advanced EPA engine.
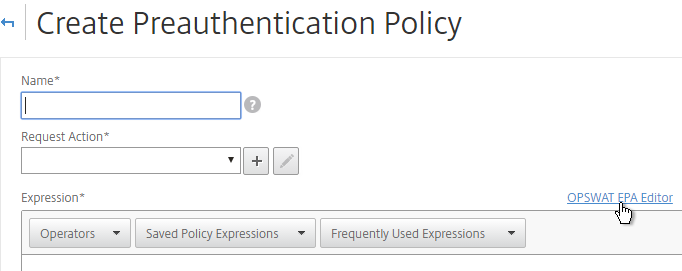
To configure OPSWAT Advanced EPA expressions:
- When creating a Preauthentication Policy or Session Policy, click the OPSWAT EPA Editor link.
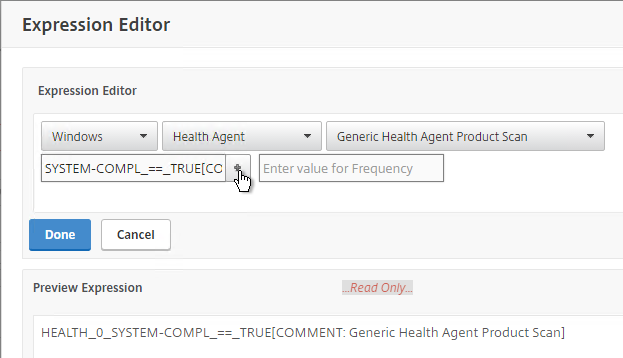
- Use the drop-down menus to select the scan criteria. Then click Done.
Additional EPA Info – See the following links for more Advanced EPA information:
- Advanced Endpoint Analysis Policy Expression Reference at Citrix Docs
- Citrix CTX220961 Pre authentication scan on Netscaler gateway for domain check
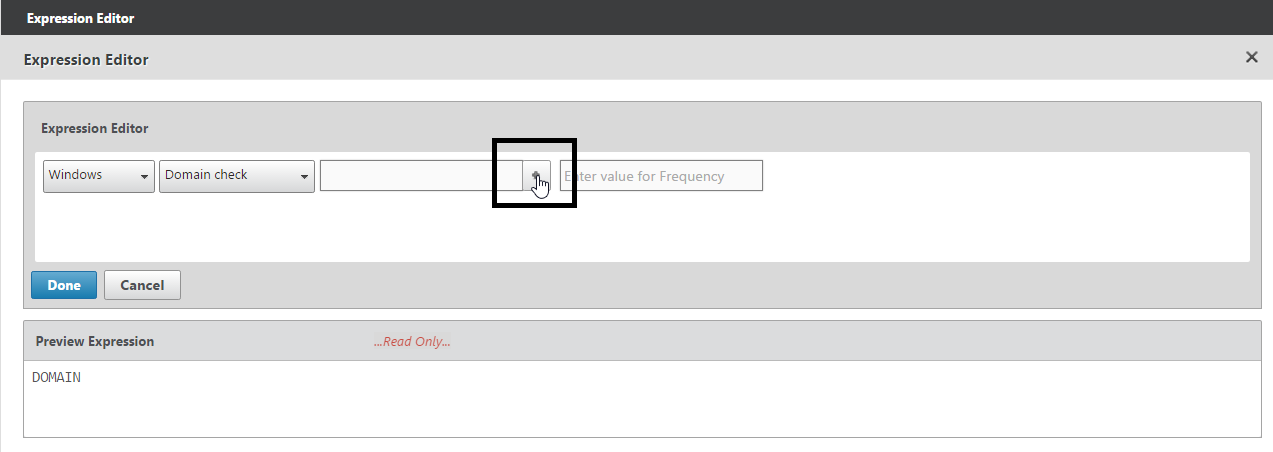
- Citrix CTX204764 Expression for EPA scan through NetScaler Gateway to check a generic antivirus and a generic firewall
CLIENT.APPLICATION('ANTIVIR_0_RTP_==_TRUE[COMMENT: Generic Antivirus Product Scan]') EXISTS && CLIENT.APPLICATION('FIREWALL_0_ENABLED_==_TRUE[COMMENT: Generic Firewall Product Scan]') EXISTS - Citrix Blog Post Patch Management Endpoint Analysis on NetScaler Gateway
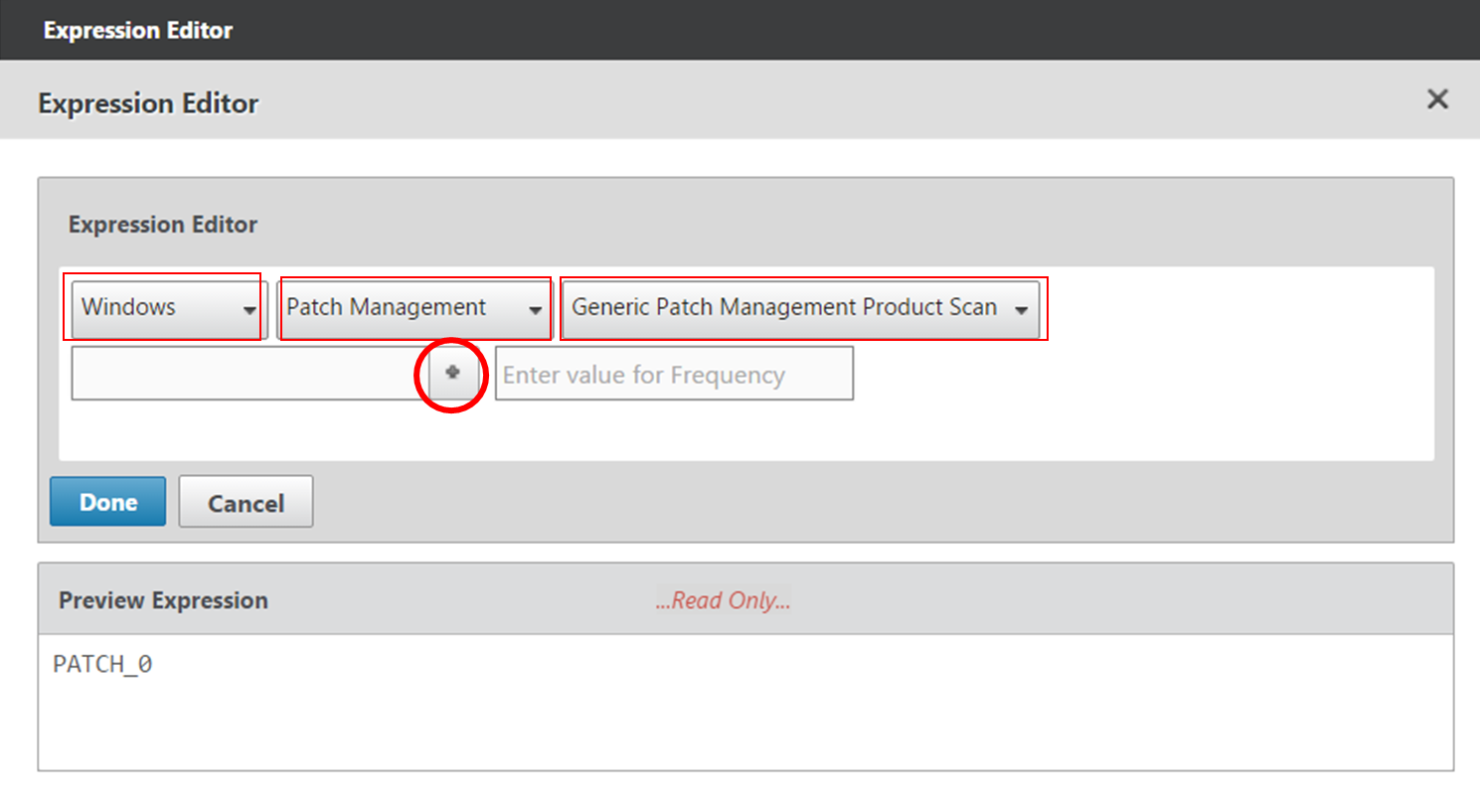
- Citrix CTX207623 OPSWAT Windows and MAC EPA Scan Support for NetScaler Gateway contains a list of applications supported by OPSWAT Windows and MAC EPA Scan
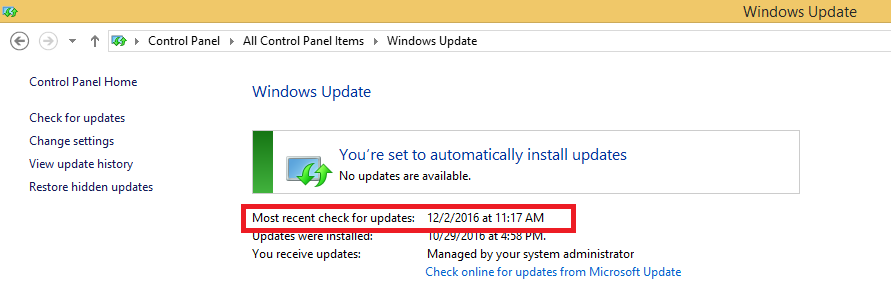
- Citrix CTX219296 How to configure EPA Expression to validate if the “Windows update” date is within specific time period
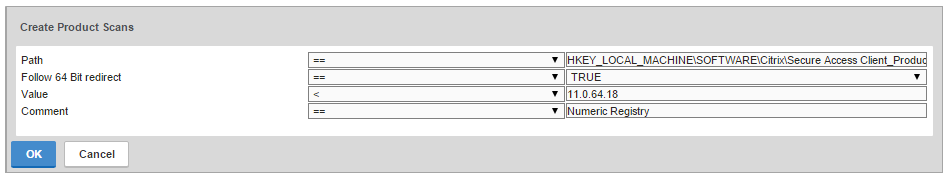
- Citrix CTX205267 How Do I Configure EPA for Registry Check?
- CTX221121 Create EPA Scans to Detect Receiver on Clients. Clients without Receiver installed are sent to the a page with a link to the Receiver Download page, and Clients with Receiver are allowed through to their ICA applications
CLIENT.SYSTEM('REG-NON-NUM_HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Citrix\\Install\\ICA Client\\InstallFolder') EXISTS
To configure Client Security expressions:
- When creating a Preauthentication Policy or Session Policy, click the Expression Editor link.
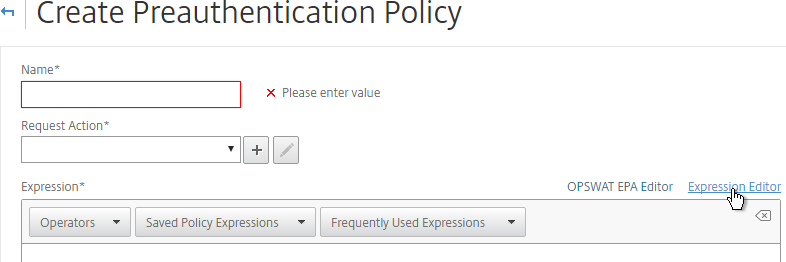
- Change the Expression Type to Client Security.
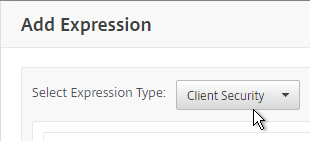
- Use the Component drop-down to select a component. A common configuration is to check for domain membership as detailed at CTX128040 How to Configure a Registry-Based Scan Expression to Look for Domain Membership.
You can also use EPA expressions when configuring a Quarantine Group.

Once the Preauthentication and/or Session Policies are created, bind them to your NetScaler Gateway Virtual Server:
- Edit a NetScaler Gateway Virtual Server.
- Scroll down to the Policies section, and click the plus icon.

- Select either Preauthentication or Session, and select the policy you already created. Then click Bind.
EPA Troubleshooting
Citrix CTX209148 Understanding/Configuring EPA Verbose Logging Feature:
- Go to NetScaler Gateway > Global Settings.
- On the right, click Change Global Settings.
- On the Security tab, click Advanced Settings.
- Scroll down, check the box next to Enable Client Security Logging, and click OK.
- When the scan fails, the user is presented with a Case ID.
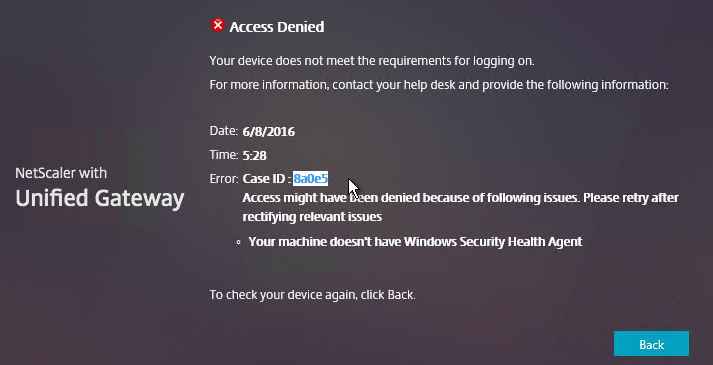
- You can then grep
/var/log/ns.logfor the Case ID. Or search your syslog.
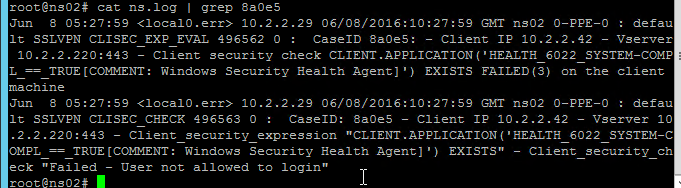
To determine why your EPA scans fail, on the client machine, go to HKEY_LOCAL_MACHINE\SOFTWARE\Citrix\Secure Access Client.
Make a DWORD value named “EnableEPALogging“, and set the value to 1.
After attempting the scan again, you’ll find the file %localappdata%\Citrix\AGEE\epaHelper_epa_plugin.txt with details for each scan expression.
NetscalerAssasin EPA OPSWAT Packet flow and Troubleshooting shows a Wireshark trace of an EPA scan.
SmartControl
The SmartControl feature lets you configure some of the SmartAccess functionality directly on the appliance. See Configuring SmartControl at Citrix Docs for detailed instructions.
Note: SmartControl requires NetScaler Platinum Edition.
- If you are using a Preauthentication Policy to run an Endpoint Analysis scan, edit the Preauthentication Profile.
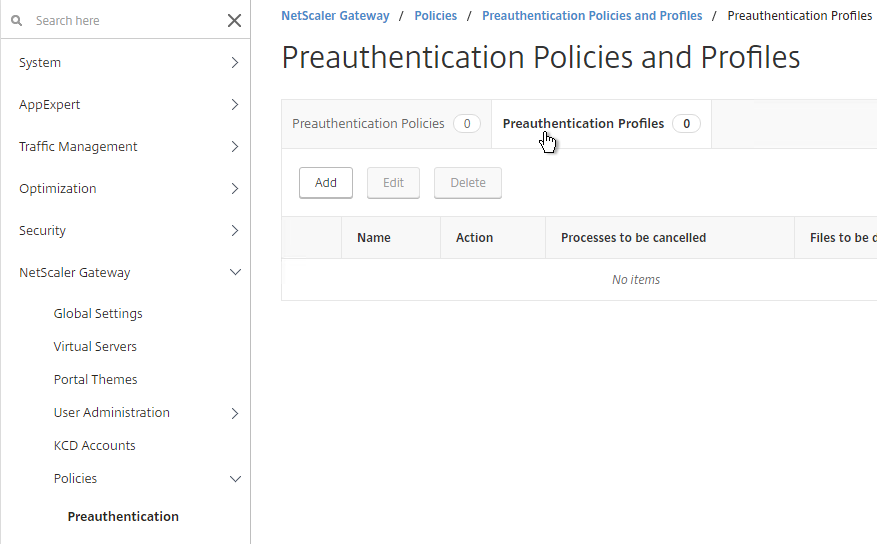
- Configure the Default EPA Group with a new group name. You’ll use this group name later.
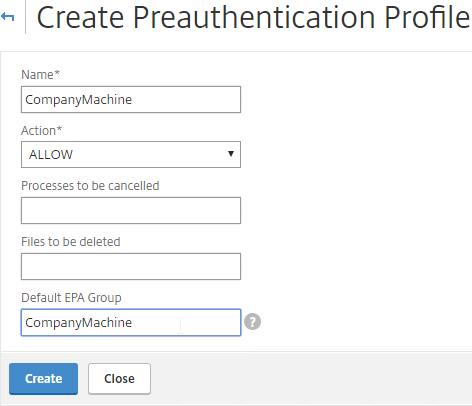
- If you are instead using a Session Policy/Profile to run the post-authentication Endpoint Analysis scan, edit the Session Profile, on the Security tab, use the Smartgroup field to define a group name for users that pass the scan. You’ll use this group name later.
- On the left, expand NetScaler Gateway, expand Policies, and click ICA.
- On the right, switch to the Access Profiles tab, and click Add.
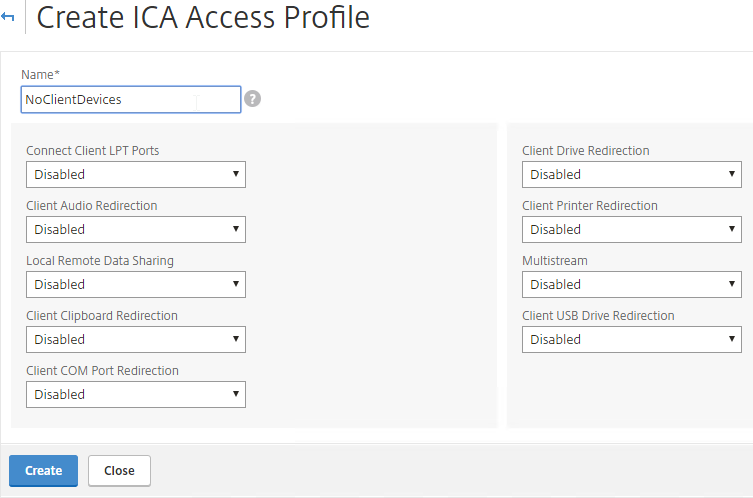
- Configure the restrictions as desired, and click Create.
- Switch to the ICA Action tab, and click Add.
- Give the Action a name. Select the ICA Access Profile. Click Create.
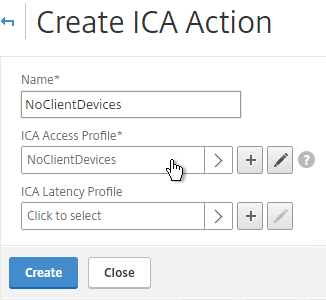
- Switch to the ICA Policies tab, and click Add.
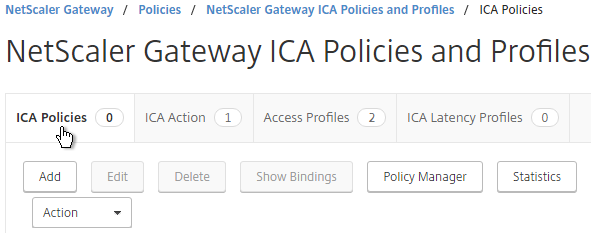
- Select the previously created ICA Action.
- Enter an expression. You can use HTTP.REQ.USER.IS_MEMBER_OF(“MyGroup”).NOT where MyGroup is the name of the SmartGroup you configured in the session profile or preauth scan. Click Create when done.
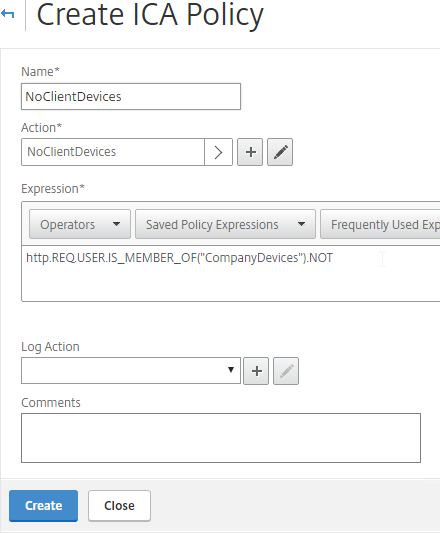
- Edit your Gateway Virtual Server.
- Scroll down to the Policies section, and click the plus icon.

- Change the Policy Type to ICA, and click Continue.
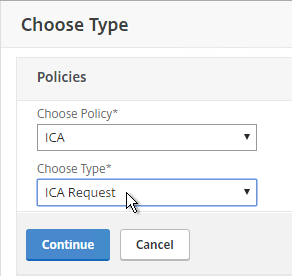
- Select the SmartControl policy you created earlier, and click Bind.
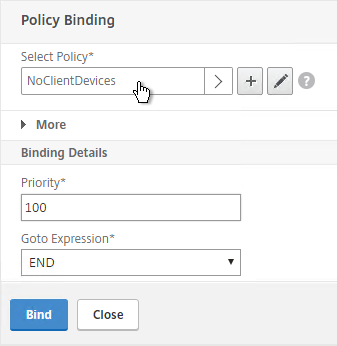
SmartAccess
CTX138110 How to Configure the SmartAccess feature on Access Gateway Enterprise Edition Appliance
In XenApp/XenDesktop, edit a Citrix policy, and add the Access Control filter. If you are using GPO to deliver Citrix Policies, then only Citrix Policies in the user half of the GPO support Access Control filters.
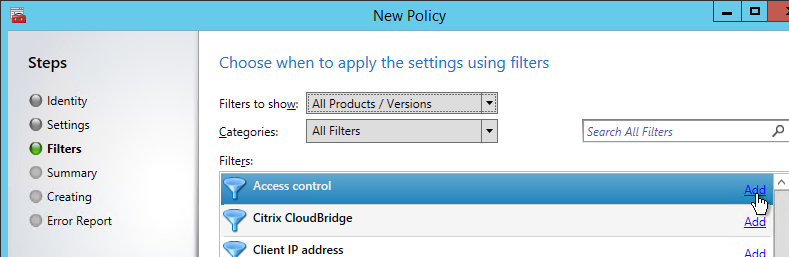
You can leave the default wildcards for farm name and condition to match all NetScaler Gateway connections. Or you can match specific NetScaler Gateway / Session Policy connections:
- AG farm name = name of the NetScaler Gateway Virtual Server.
- Access condition = name of the NetScaler Gateway Session Policy.
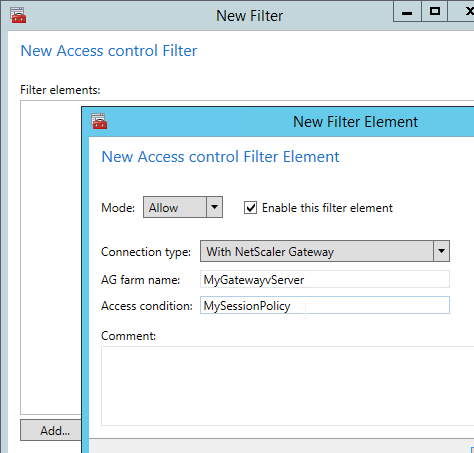
You typically create a Citrix policy to turn off all client device mappings for all external users. Then you create a higher priority Citrix policy that re-enables client device mappings for those users that passed the Endpoint Analysis scan expression on a particular Session Policy.
If you edit a Delivery Group, there’s an Access Policy page where you can hide or show the Delivery Group for all NetScaler Gateway connections, or for specific NetScaler Gateway Virtual Server / Session Policy connections.
- Site or Farm name = NetScaler Gateway Virtual Server name
- Filter = NetScaler Gateway Session Policy name
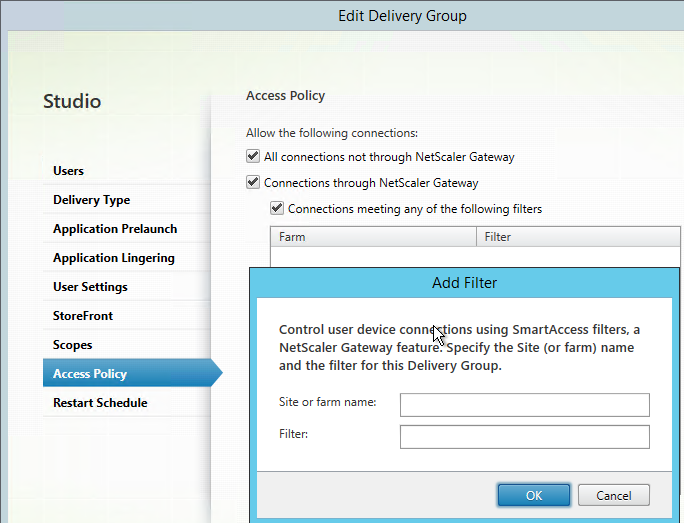
This configuration is only available at the entire Delivery Group. It is not possible to perform this configuration for only specific published applications, unless they are on different Delivery Groups.
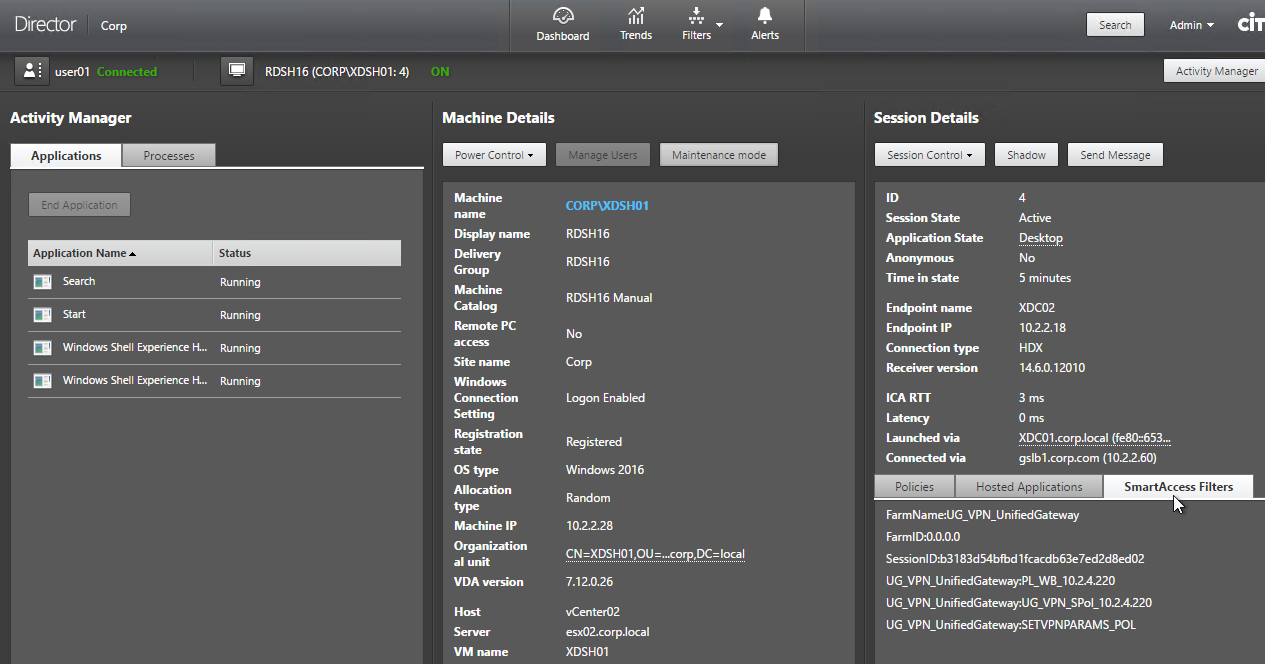
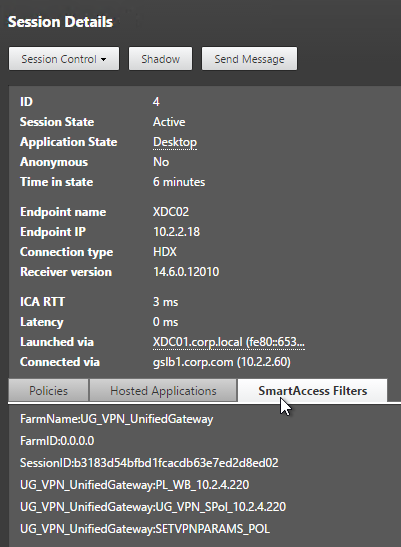
When connected to a session, Director shows SmartAccess Filters on the session Details page. Notice the Farm Name (vServer name) and Filter Name (Session Policy name)
How do I configure a policy for a select security not allowed to login to Citrix via Netscaler externally, internally they are allowed?
Are you using Gateway for both internal and external?
You could have two LDAP policies/servers – one for external, one for internal. The external one would have an LDAP Search Filter to restrict access. The internal one would have a policy expression for Client IP that matches your internal subnets and no LDAP search filter.
I have run into a case where I would like to update the OPSWAT on NSGW without having to upgrade the entire VPX.
I noticed if you go to Configuration>Netscaler Gateway there is a link tp upgrade EPA libraries. I have opened a couple of tickets with Citrix on this and all I am told is that you need to upgrade the appliance to the latest firmware. Do you know if there is a way to update just the EPA libraries without upgrading the appliance?
Hi Carl,
Delivery group access policy’s “Filter” works with “ANY” of the following filters. With Netscaler policy rule length limit of 1500 char, I want to add multiple rules with “ALL” filters apply. It is not available via Citrix Studio GUI. Is there other way to enable access policy with “ALL” filters apply?
Thank you for all your help
Regards
Hi Carl,
I am trying to enable smartaccess to restrict an access to delivery group
The difference is the portal is Unified gateway. So Site or Farm name = NetScaler Gateway Virtual Server name is pointing to Content switch entry. Gateway is none addressable IP.
In one blog I read that:
“Note: If you are using a Content Switch to direct users to Netscaler Gateway (with a non addressable IP), you might have to adjust the Content Switch Policy or create a dummy ‘Call back’ vServer to address the Storefront Callback setup”
What would you suggest for this scenario? I point to content switch entry – result is delivery group is hidden no matter if policy passes or not
Thank you
Azer
I would think that the Access Control configuration needs the name of the Gateway Virtual Server, not the Content Switching Virtual Server. If you trace the traffic between StoreFront and Gateway (or StoreFront and Controller), you’ll see the Smart Access headers. Director also tells you the filter names.
Hi Carl,
Yup, used Gateway Virtual server name and it worked!
Thank you
Hi Carl,
Will we benefit from the new licensing model if we upgrade an existing appliance from 11.0 to 11.1 build 49 and later?
Yes.
Hello Carl and Citrix Community
We have a requirement to enable redirection (drive/printers) for only company managed (Windows) devices coming in through our external NetScaler.
We would like to use multiple factors from the device to determine if they are managed, such as, the domain the device is a member of, validating a company provided device/client certificate is present and valid on the device, or other meaningful checks.
Setup – We are using NetScaler 11.1.x HA pair, and have a single access gateway virtual server setup for only access to XenApp. We use two-factor auth and have two session policies/profiles, which are fairly standard (Contains Receiver or Does Not Contain Receiver), so we don’t prevent any device types (Receivers, Browsers, Mobile Devices, etc.)
Question: How can we configure the NetScaler/Citrix to meet the requirement of interrogating Window devices to determine if they are managed by the company and send them to a specific session policy? that XenApp can use, while making the checks as seamless as possible for all end users, regardless of the device type?
I have been reading quite a bit about this, yet I’m still unsure as to what is the best method to use or if this is even possible when just using the NetScaler to access XenApp. I was thinking we could use post authentication EPA and other policies as we would want devices which fail the checks to be able to use XenApp (just without redirection capabilities) and the devices which pass the checks and are deemed to be managed to be allowed to use redirection.
Thoughts?
Thank you,
Brandon
Yes to postauth. Leave one Session Policy without an EPA expression. Have you tried it?
Device certificate? I can’t remember if Device Certificate can be optional instead of mandatory. And I can’t remember if there’s a policy expression to validate device certificate. User certificates can be optional, and there are policy expressions for user certificates.
Hello Carl:
Does NS 11.1 support native EPA scans without using the Gateway plugin, I am trying to look up domain membership of the machines while people connect via NS UG
The EPA plugin is completely separate from the Gateway (VPN) plugin. Is that what you’re asking? The EPA plugin is downloaded first. If a user doesn’t need VPN, then the VPN plugin is never downloaded.
I was wondering if NetScaler natively supports checking the computer(whether domain based or not) without using any plug-in. Typically users have the Citrix receiver installed, did not want to install any additional plug-ins
Unfortunately not. Microsoft can do that because they can embed code into Windows, but Citrix (and other vendors) cannot.
Hey Carl, another great article!
My question is around the actual universal license entitlements. Does this mean if you purchase NetScaler Platinum you now get Unlimited Universal Access Licenses??
We are working with a customer looking to offer traditional SSL VPN through NetScaler, along with their existing XenDesktop deployment that uses SmartAccess mode. Our concern was they would not have enough licenses to offer both unless they purchased more Universal Access licenses. That said, they already own NS Platinum and are showing “Unlimited” next to Maximum NetScaler Gateway Users.
If 11.1, yes, Platinum has unlimited Universal licenses.
Hi Carl
Does any Citrix docs statement smart control require NetScaler Platinum Edition
No. It requires NetScaler Gateway Universal licenses. You can get these license through several means, including NetScaler Platinum.
Hi, I have several parameters to use in my preauthentication policy. I need to allow multiple Antivirus, multiple Operating Systems, and multipe browsers. Do you know how to do that?
Because if I create several preauthentication policy and if the client match with only one , he will be allowed to connect.
For the browser it is worst, because EPA will only scan the browser installed, and not the browser in use. So if the user has the latest version of chrome installed, but use IE10, it will work too..
Thank you for your help
You can add multiple expressions to a single policy and use boolean operations (e.g. ||) between them. To make it easier to read, add the named expressions to AppExpert > Expressions > Classic. Then you can reference the expression name in the preauth policy.
OK, it’s going to be very complicated, if I understand correctly I have to insert every combinaison of OS and antivirus with boolean operations? And for for browsers, we agree that we cannot detect the browser in use, we can only detect if the browser is installed on the device with the correct version?
You can use User-Agent string to detect browser. Or use Javascript (e.g. jReject) to detect browser version.
For the booleans, that’s why I suggested creating named expressions and then referencing the named expressions in your preauth policy.
Another option is to do a generic Windows security scan to detect if Windows thinks AV, firewall, and patches are configured correctly.
Thank you I’m gonna try that. Have a Nice day 🙂