Navigation
Workspace app is the new name for Receiver. This post applies to all Workspace app versions, including the Current Release version 2409.10 and the LTSR version 2402 CU3.
- Change Log
- Workspace app versions
- Overview
- Uninstall Old Workspace app Clients
- Installation and Configuration
- Workspace app ADMX GPO Template
- Pass-through Authentication
- Automatically add StoreFront Accounts to Workspace app
- Control Shortcut placement on Desktop and Start Menu – and Workspace Control (Session Reconnect)
- Enable Prelaunch
- Control Device Mapping Prompts
- Desktop Lock
- Use Studio to configure Workspace app Accounts in Published Desktop
- Published Desktop – configure Workspace app to place shortcuts
- Script / Automate Workspace app Self-Service
- Microsoft Teams
- Troubleshoot:
💡 = Recently Updated
Change Log
- 2025 Jan 16 – updated article for Workspace app 2409.10
- 2025 April 2 – Versions – updated for Workspace app 2402 LTSR Cumulative Update 3
- GPO Settings – SSO in Win11 24H2 requires Enable MPR notifications for the System; Desktop Viewer Toolbar Options
- Registry Values – Remember USB connections
- 2023 Nov 15 – Global App Configuration Service is now available to all on-premises customers even if no Citrix Cloud entitlement.
- 2023 May 4 – Pass-through Authentication – added GPO setting Enable MPR notifications for the System
- 2023 Mar 22 – updated article for Workspace app 2303; anti-dll injection GPO setting
- 2022 Dec 19 – updated article for Workspace app 2212; app protection GPO setting
- 2022 Nov 4 – Versions – updated for Workspace app 1912 LTSR Cumulative Update 7 Hotfix 2
Workspace app Versions
Citrix Workspace app uses a YYMM (year/month) versioning format, of which version 2409.10 (24.9.10.28) is the newest Current Release. See Citrix Docs for the list of new features, some of which only apply to Citrix Cloud.
Workspace app 2311 and newer have a new installer interface.
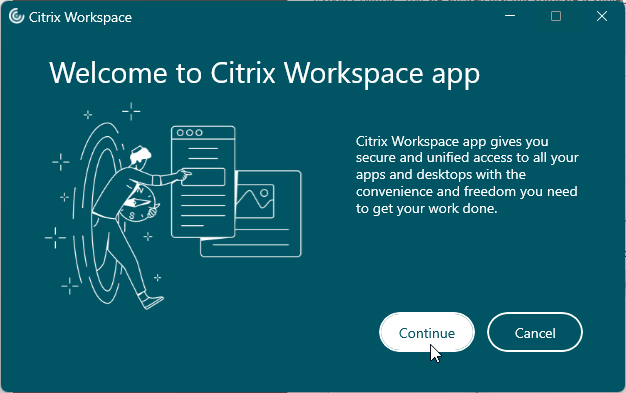
Workspace app 2303 and newer automatically install the App protection components with an option to start them after installation. Older Workspace apps have an option to install App protection and if you don’t select this and later want App protection then you must uninstall Workspace app and reinstall it.
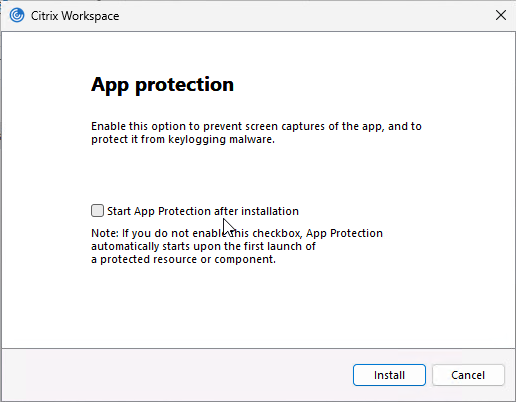
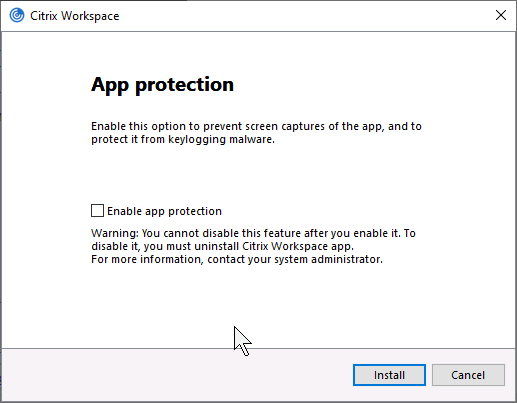
- See App Protection at Citrix Docs to enable App protection for the authentication screen. Workspace app 2305.1 and newer automatically start it for authentication if you have selected the Start App Protection check box during installation.
The newest Current Release version of Workspace app is version 2409.10.
The newest LTSR (Long Term Service Release) version of Workspace app is version 2402 Cumulative Update 3.
Workspace app Modules
The Workspace app installer deploys multiple modules. Here are the important ones:
- ICA Engine (wfica.exe) – process that uses the ICA protocol to connect to published apps and desktops.
- Self-Service (selfservice.exe) – gets icons from StoreFront and displays them in a Window. When an icon is clicked, Self-service passes the ICA file to the ICA Engine to establish a connection.
- Single Sign-on (SSON) for ICA (ssonsvr.exe) – captures user credentials and submits them to VDAs after an ICA connection is established
- Workspace Auto-Update (CitrixReceiverUpdater.exe) – Notifies users of Workspace app updates. The most recent name for this component is Citrix Workspace Update.
Custom ICA files are no longer supported. However, Ryan Butler has created a script that asks StoreFront for an ICA file. Explicit credentials are supported. Find the script at Github.
Workspace app Discovery and Beacon Process
If you are using Workspace app’s built-in user interface (instead of a web browser), then Workspace app first prompts you to perform discovery, which is also called Add Account.
Workspace app will contact the FQDN and request download of the StoreFront Provisioning File.
- If you entered a StoreFront FQDN, then Workspace app will download the Provisioning File directly from the StoreFront server.
- If you entered a Gateway FQDN, then Gateway will first prompt the user to authenticate. After authentication, Gateway will connect to its configured Account Services address, and download the Provisioning File from StoreFront. The Account Services address is configured in the NetScaler Gateway Session Profile on the Published Applications tab.
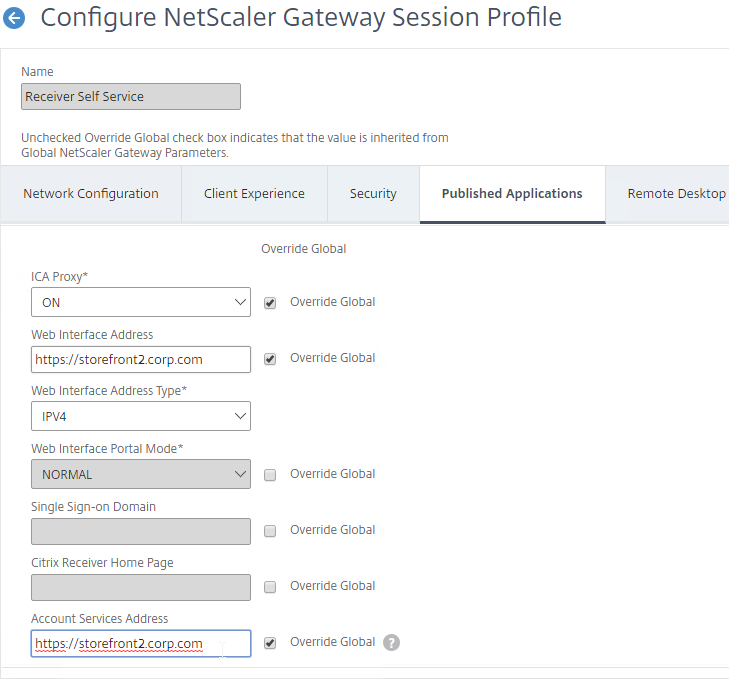
If your StoreFront server is configured with multiple stores, then the user will be prompted to select a store. Unfortunately, there’s no configuration option in NetScaler Gateway to force a particular store.
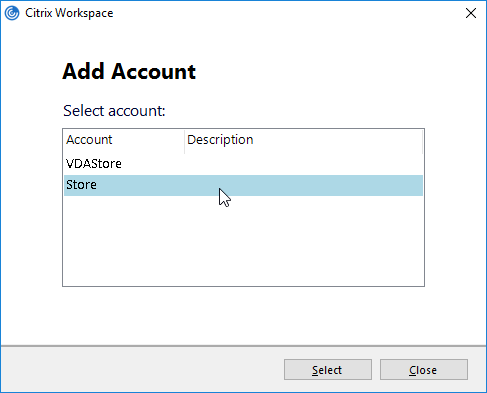
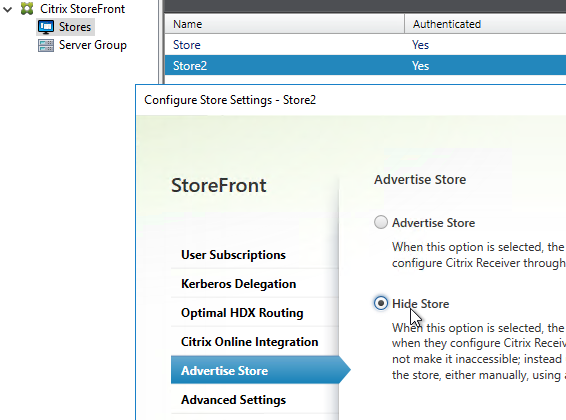
- One workaround is to hide the store that you don’t want visible externally. See How to configure Receiver to a Store that is not advertised for special syntax.
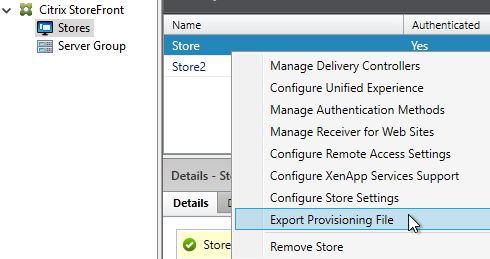
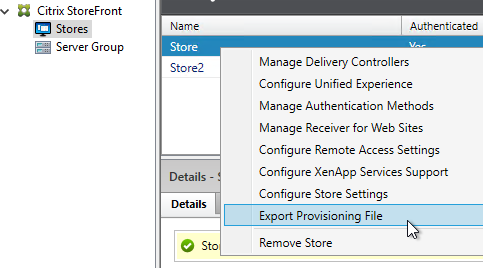
The Provisioning File downloaded from StoreFront is an XML document containing values for several items configured in the StoreFront console. You can export the Provisioning File from the StoreFront console by right-clicking a Store.
The ReceiverConfig.cr Provisioning File looks something like this:
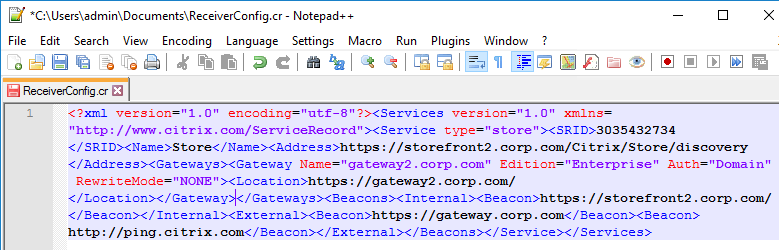
Here are the values in the Provisioning File:
- Address – the Base URL configured in StoreFront Console
- Internal Beacon – as configured in StoreFront Console. This can be the Base URL, or a manually specified URL.
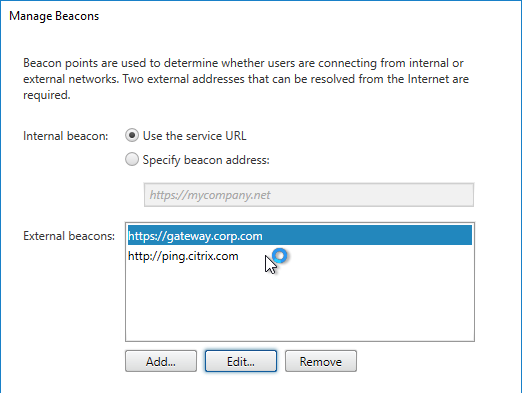
- External Beacons – as configured in StoreFront Console
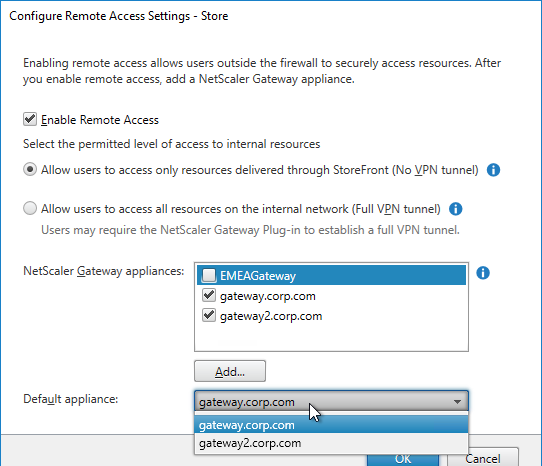
- Gateways – as configured in StoreFront Console. If there are multiple Gateways, when enabling Remote Access on the Store, then only one Gateway is selected as Default
- SRID – Store ID. An important value to consider for multi-datacenter configurations. The SRID is set when the Store is created. It can also be changed by editing C:\inetpub\wwwroot\Citrix\Roaming\web.config.
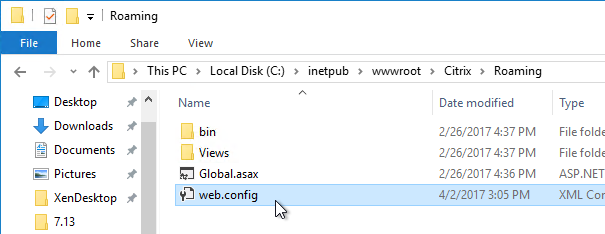
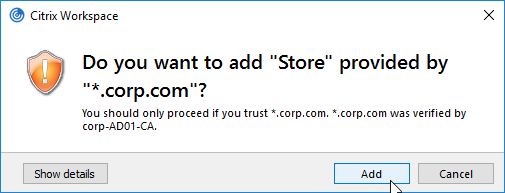
Workspace app reads the Provisioning File, and configures itself by inserting the file’s contents into the user’s registry. The values are located under HKCU\Software\Citrix\Dazzle\Sites and HKCU\Software\Citrix\Receiver\SR. If you performed discovery through NetScaler Gateway, notice that the internal Base URL is added to the user’s registry.
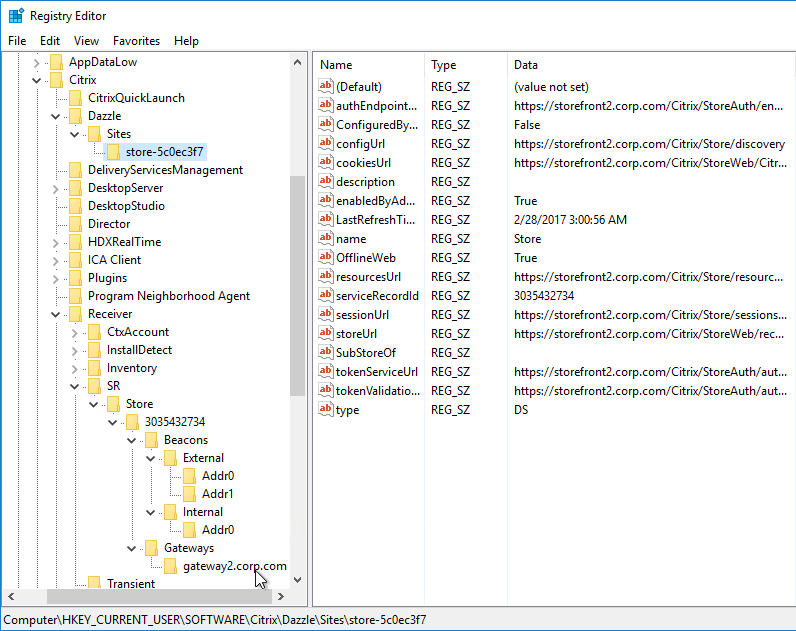
Once Workspace app is configured, it then performs the following steps:
- Attempt to connect to the Internal Beacon.
- If the Internal Beacon is reachable, connect directly to the StoreFront Base URL (Address).
- If the Internal Beacon is not reachable:
- Attempt to connect to the External Beacons. If the External Beacons are not reachable, then stop attempting to connect.
- Connect to the Gateway address configured in the Provisioning File. If there is more than one Gateway, connect to the Gateway that is marked as the Default.
Here are some interesting notes on this connection process:
- The FQDN you entered during Discovery has absolutely nothing to do with how Workspace app connects to StoreFront or Gateway. The actual connection process is controlled by the contents of the Provisioning File, not the Discovery address.
- If the Provisioning File has multiple Gateways defined, Workspace app uses whichever Gateway is marked as Default. Workspace app completely ignores whatever Gateway FQDN you entered during Discovery. To use a non-default Gateway, the user must manually select the other Gateway in Workspace app’s Advanced Preferences.
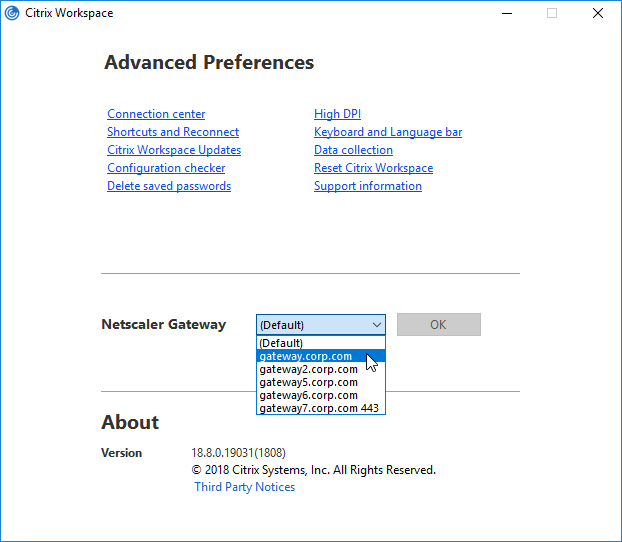
In StoreFront Console, if any configuration changes are performed that affect the Provisioning File, it takes an hour for Workspace apps to reconfigure themselves automatically. Or users can remove Accounts and re-add (or Reset Citrix Workspace) so that the updated Provisioning File is imported.
Here are some additional methods of performing Workspace app Discovery:
- After exporting the Provisioning File from StoreFront Console, distribute it to users, and ask them to double-click it.
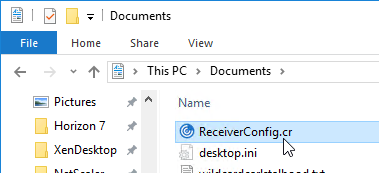
- After logging in to Receiver for Web (StoreFront), at the top right, click the username, and click Activate. This downloads the receiverconfig.cr file, which is identical to the one you can export from StoreFront Console. The user then must run the downloaded file.
Virtual Monitors
In Workspace app 1812 and newer, when connected to a published desktop on a single monitor, you can split the screen into virtual monitors. This feature is intended for large 4K monitors.
- In the desktop toolbar at the top of the screen, click Preferences.
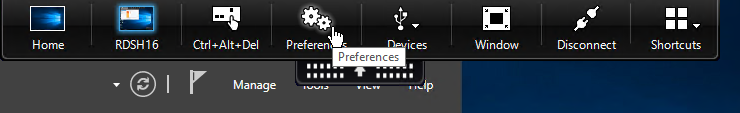
- Switch to the Monitor Layout tab.
- On the bottom, select Horizontal or Vertical, then click somewhere in the blue box to draw a line. The single monitor will be split along this line. You can set different DPI for each portion of the virtual display.
- Right-clicking one of the split sections changes that section to the primary display.
- Click OK when done.
- In the toolbar, click Window to resize it to a window, and then click Full Screen to cause your virtual monitor configuration to take effect.
Uninstall Old Clients
Workspace app installer can do a force uninstall of old clients before installing the new version:
- In Workspace app 2309 and newer, run CitrixWorkspaceApp.exe /CleanInstall /Silent
- In Workspace app 1909 and newer, run CitrixWorkspaceApp.exe /ForceInstall /Silent.
- In Workspace app 1908 and older (including Receiver), run CitrixWorkspaceApp.exe /RCU /Silent or CitrixReceiver.exe /RCU /Silent.
Citrix CTX325140: How to Remove Client Files Remaining on System after Uninstalling Receiver for Windows.
Installation and Configuration
Administrator privileges – Administrator privileges are required to install any missing prerequisites.
Internet required – Recent versions of Workspace app download and install Microsoft Edge WebView2 Runtime, .NET Desktop Runtime 6.0.20, .NET Framework 4.8, and Visual C++. Internet access is required for the Workspace app installer to download these install files. Or there’s an Offline Installer for Workspace app 2309 and newer.
.NET Desktop Runtime 6.0.20 – Workspace app 2309 and newer will install x86 .NET Desktop Runtime 6.0.20 if it’s not already installed.
This section contains a summary of all common command line switches, registry keys, and policy settings for Workspace app.
Links:
- Citrix Blog Post: Optimizing Citrix Receiver for Pre-launch and Single Sign-On
- Citrix CTX202002 How To Deploy Citrix Receiver for Windows Using SCCM 2012 R2
Workspace app 2203 LTSR CU2 and Workspace app 2212 and newer fix security vulnerabilities.
CitrixWorkspaceApp.exe current release version 2409.10 or LTSR version 2402 CU3 can be installed by simply double-clicking it.
- LTSR Workspace app does not support Browser Content Redirection.
- Workspace app 2006 and newer do not support Windows 7.
- Workspace app 2206 and newer enable DPI Matching by default. DPI Matching can be disabled through client-side group policy, or in the Advanced Preferences in Workspace app 2212 and newer. DPI Matching prevents connections to CVAD 7.15. Multi-session VDAs with version 1912, by default, have DPI Matching disabled, but can be enabled in the VDA’s registry. See CTX460068 for details.
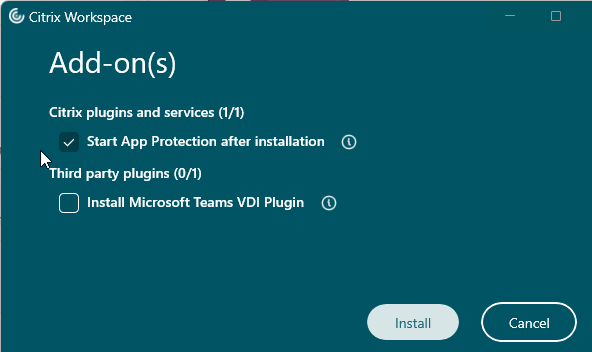
- Workspace app 2311 and newer have a new interface for installation.
- Workspace app 2402 and newer ask if you want to install the Microsoft Teams VDI Plugin or not. This is for Teams 2.1 and newer.
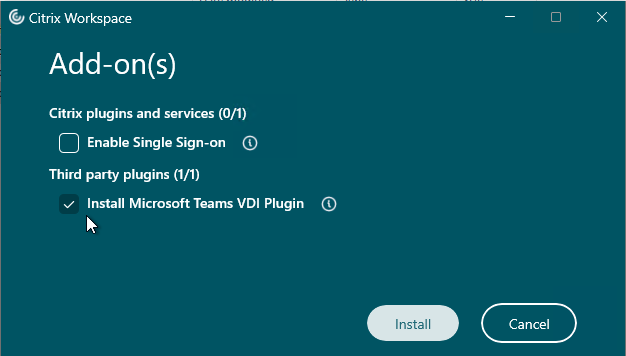
Administrator vs non-administrator
- Non-administrator – If a non-administrator installs Workspace app, then each non-administrator that logs in to the same workstation will have to reinstall Workspace app.
- Non-administrator installations are installed to %USERPROFILE%\AppData\Local\Citrix\ICA Client for each user.
- Administrator – If CitrixWorkspaceApp.exe is installed using an administrator account. then the Workspace app only needs to be installed once.
- Administrator installations are installed to C:\Program Files (x86)\Citrix\ICA Client.
- Administrator installations of Workspace app 1912 and newer can be manually upgraded by non-administrators by clicking Check for Updates. Older versions cannot be upgraded by non-administrators.
- Conflicts – If an administrator install of Workspace app is performed on a machine that has non-administrator installs of Workspace app, then the two installations will conflict. Best option is to uninstall non-admin Workspace app and Receiver before installing admin Workspace app. Otherwise, the user’s profile probably has to be reset before Workspace app is functional again.
- Citrix article CTX249920 Workspace App for Windows – Your apps are not available at this time – Issue when installing Citrix Receiver in not elevated/per-user install mode describes the HKEY_CURRENT_USER registry keys that must be deleted to fix this issue.
- For a script to clean-up the per-user installs, see Mark DePalma at Citrix Receiver Per-User Install Cleanup.
Global App Configuration Service
Global App Configuration Service (GACS) is a Citrix Cloud service that can push configurations to Workspace app clients. This Citrix Cloud service is now available to all on-premises customers even if you don’t own any Citrix Cloud entitlements.
- Login to https://citrix.cloud.com. If you don’t have a Citrix Cloud account, then login using your Citrix.com account credentials and it will create a Citrix Cloud account.
- Use the top left hamburger menu to go to Workspace Configuration.
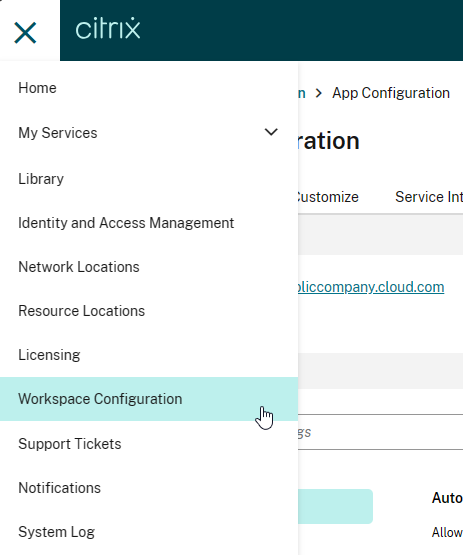
- Switch to the tab named App Configuration.
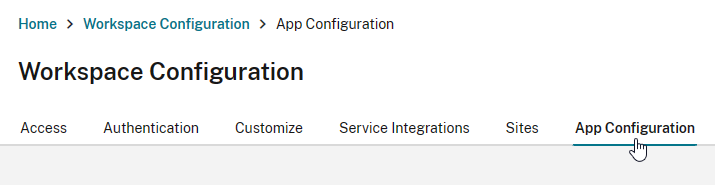
- Click Switch URL.
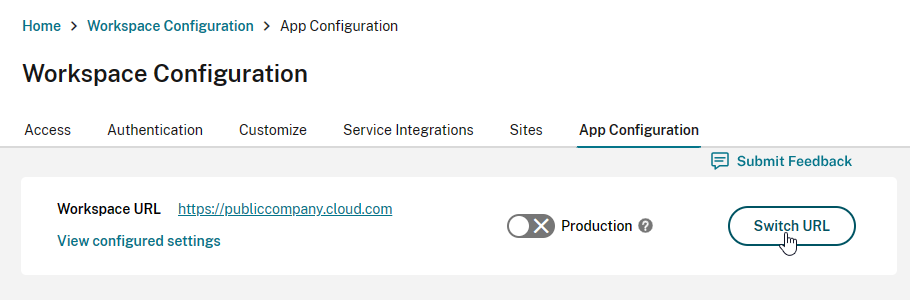
- Near the bottom, click Claim URL.
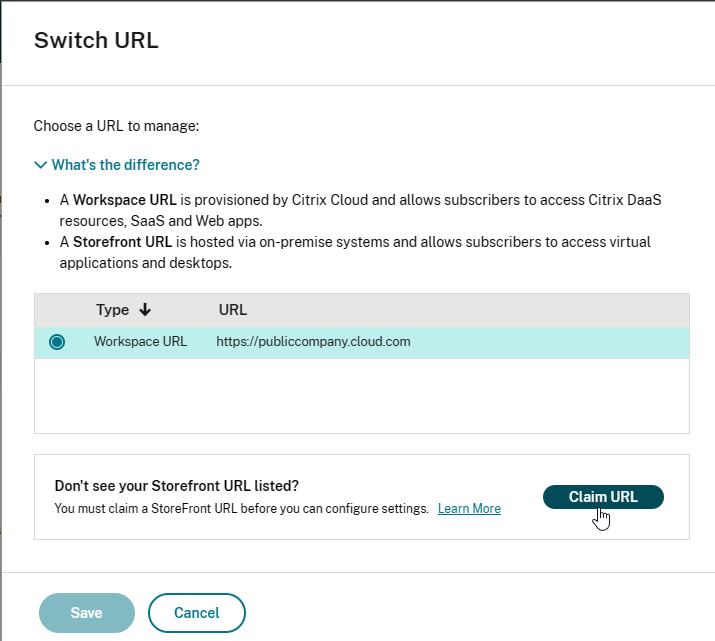
- Click Add URL to add your on-premises StoreFront/Gateway URL. See Citrix Docs for details. GACS uses this URL to determine which Workspace app clients should receive the settings that you configure.
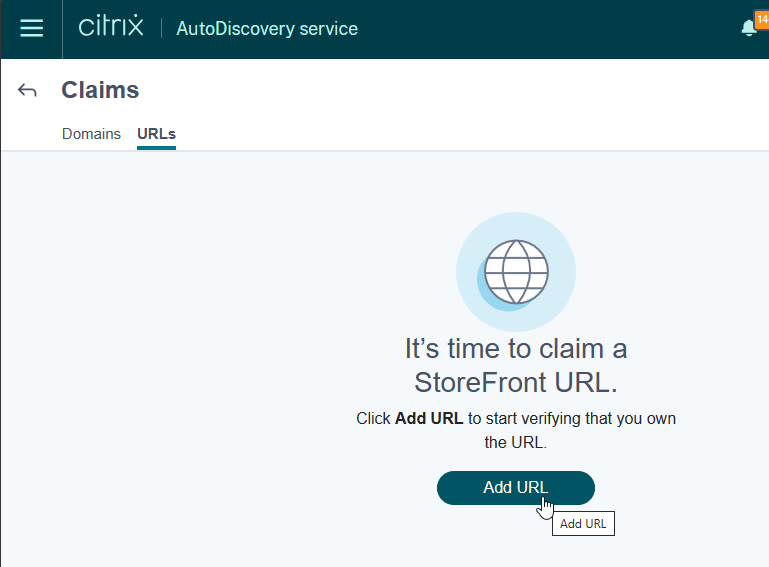
- Back in the App Configuration page, you can now configure Workspace app settings as desired. Workspace apps that have stores under the claimed URL will then receive these settings.
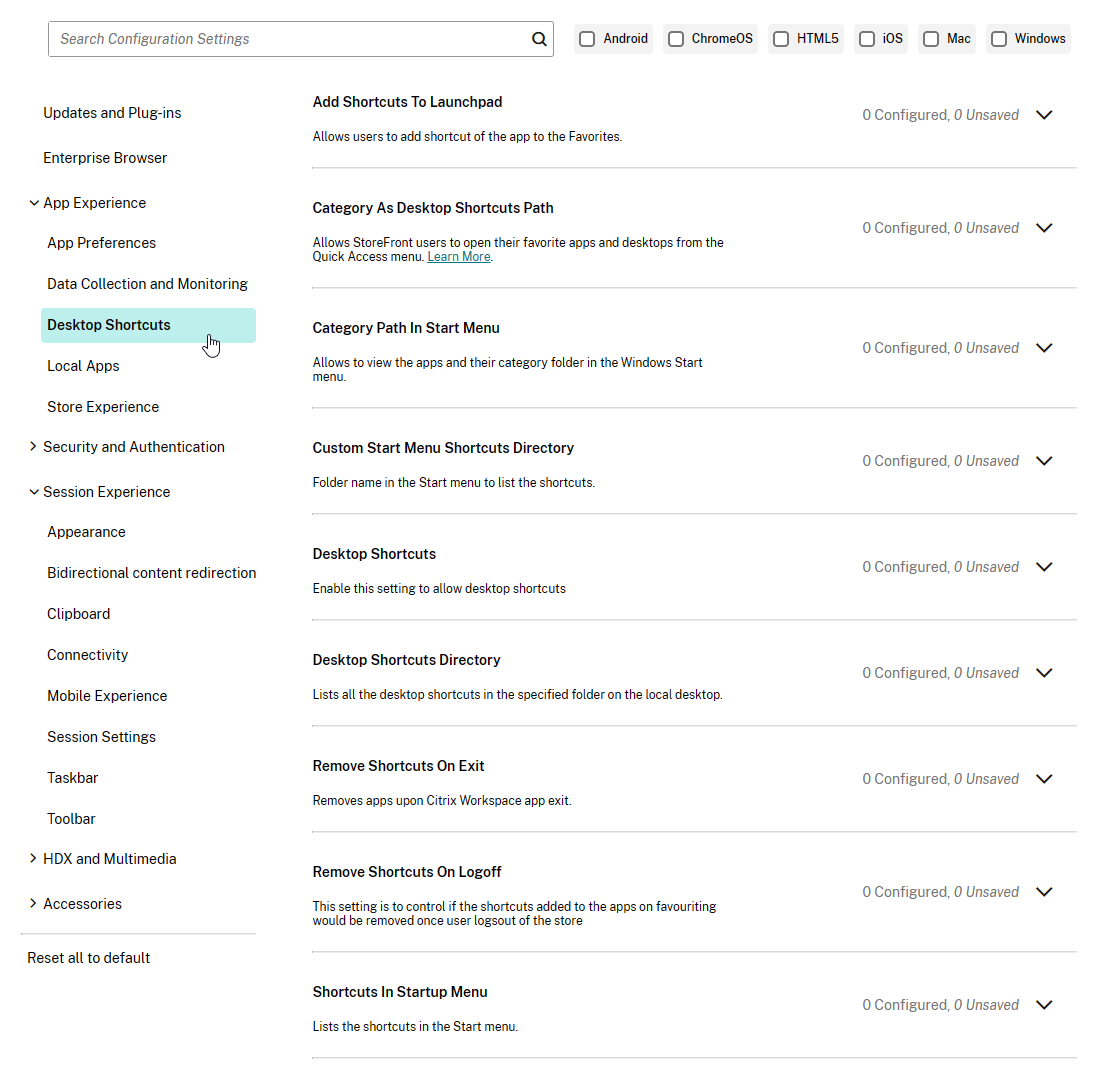
Auto-Update
Workspace app supports auto-update.
Some notes:
- If Workspace app 1912 or newer is installed as administrator, then non-administrators can click Check for Updates to manually update Workspace app. To prevent this, use group policy to disable Citrix Workspace Updates.
- Older versions of Workspace app cannot be upgraded by non-administrators.
- If Workspace app is installed on a VDA, auto-update is automatically disabled. This includes Remote PC.
- Auto-update can be limited to LTSR updates only.
- Auto-update is configurable through several mechanisms: group policy, StoreFront, Workspace app GUI, installer command line. See Configuring Citrix Workspace Updates at Citrix Docs.
- Workspace app 2107 and later let users select an Update channel.
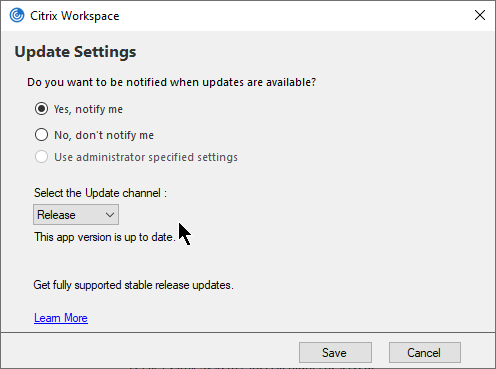
- See George Spiers Citrix Receiver for Windows Auto-Update.
Auto-update is configured using Workspace app group policy under the Citrix Workspace Updates, or Auto-Update node.
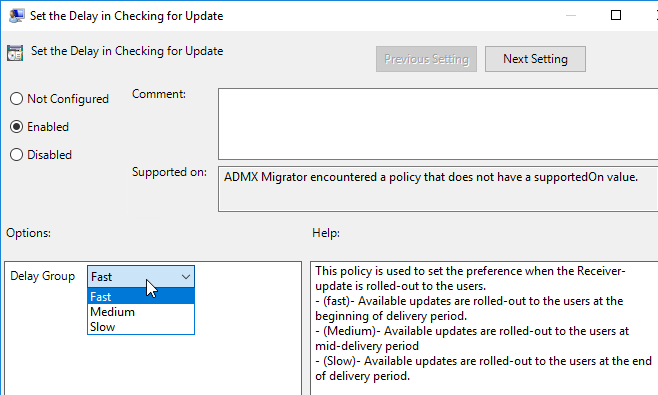
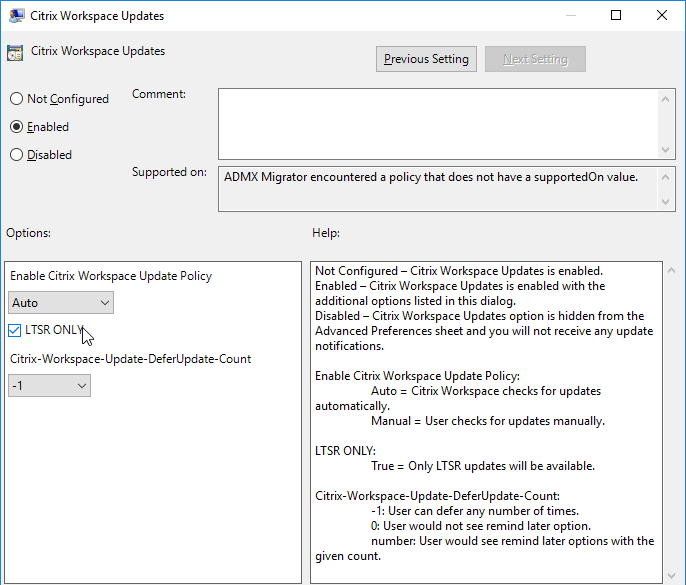
Or use Global App Configuration Service.
Workspace app Splash Screen
Workspace app shows a Splash Screen on first launch with the text “Citrix Workspace app extends the capabilities of Citrix Receiver”.

To prevent this splash screen, set the following registry value: (source = Dennis Span on Twitter)
- Key = HKEY_CURRENT_USER\SOFTWARE\Citrix\Splashscreen
- Value (REG_SZ) = SplashscreenShown = 1
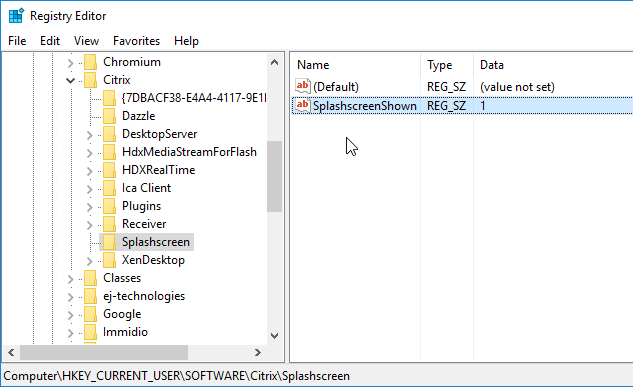
Add Account Wizard
After installation, Workspace app will launch and ask you to add an account. If Workspace app, notice the checkbox Do not show this window automatically at logon.
FTU (First Time Use aka Add Account Wizard) will be displayed only if a store is not configured. If a store is already configured via command line, GPO, or Citrix Studio, then FTU screen will not be available after installation. Otherwise, FTU can be suppressed by doing one of the following:
- Rename CitrixWorkspaceApp.exe to CitrixWorkspaceAppWeb.exe.
- Install using a command line switch:
- CitrixWorkspaceApp.exe /ALLOWADDSTORE=N
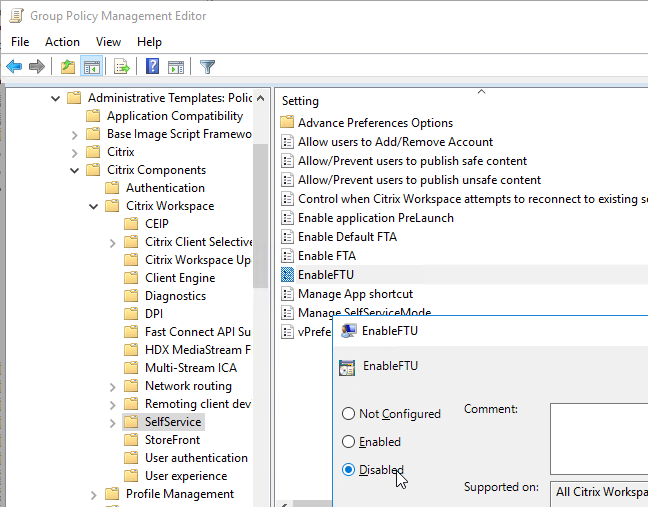
- Set the registry value: HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Citrix\EnableFTU=dword:00000000 (or EnableX1FTU =dword:0)
- Disable the EnableFTU policy setting in Receiver.admx.
- Change Registry values post installation to suppress the Add Account window. Under HKLM\Software\Wow6432Node\Citrix\Dazzle, set AllowAddStore value to N.
- Set the registry value: HKEY_LOCAL_MACHINE\Software\Citrix\Receiver\NeverShowConfigurationWizard (REG_SZ) = true
- Also see Suppressing Add Account dialog at Citrix Docs.
Discover Hidden Stores
When Workspace app is first launched, it must perform Discovery, which is the process of downloading the .xml provisioning file from StoreFront. Discovery is performed by entering a StoreFront FQDN or Gateway FQDN. To discover a hidden store (a store that’s not advertised), add ?StoreName to the end of the FQDN. CTX214819 How to configure Receiver to a Store that is not advertised.
CitrixWorkspaceApp.exe Command line switches
CTX227370 Citrix Workspace app Commandline Tool contains a GUI tool to build your installer command line.

For unattended installation of Workspace app, see CTA Dennis Span Citrix Workspace App unattended installation with PowerShell or Citrix Receiver unattended installation with PowerShell.
Installer Command Line Switches are detailed at Configure and install Receiver for Windows using command-line parameters at Citrix Docs. Common Command line switches include the following:
- /silent
- /includeSSON – enables pass-through authentication. GPO configuration is also required as detailed below.
CitrixWorkspaceApp.exe /includeSSON
- /ALLOWADDSTORE=A – by default, only SSL (HTTPS) stores are accepted. To allow non-SSL stores:
CitrixWorkspaceApp.exe /ALLOWADDSTORE=A
- /STORE0 – To add a store from the installation command line:
CitrixWorkspaceApp.exe STORE0="AppStore;https://Citrix.corp.com/Citrix/MyStore/discovery;on;App Store"
- Workspace App can discover the Store through NetScaler Gateway.
CitrixWorkspaceApp.exe STORE0="AppStore;https://gateway.corp.com#MyStore;On;App Store"
- Workspace App can discover the Store through NetScaler Gateway.
- /SELFSERVICEMODE=False – disables the Self-Service interface and enables shortcut-only mode:
CitrixWorkspaceApp.exe /SELFSERVICEMODE=False
- /AutoUpdateCheck=auto /AutoUpdateStream=LTSR – enables Citrix Workspace Update notifications and sets it to LTSR Branch only. AutoUpdateCheck can also be set to manual or disabled. AutoUpdateStream can also be set to Current. See Configuring Citrix Workspace Updates at Citrix Docs.
CitrixWorkspaceApp.exe /AutoUpdateCheck=auto /AutoUpdateStream=LTSR
- /ENABLEPRELAUNCH=True – enables prelaunch:
CitrixWorkspaceApp.exe /ENABLEPRELAUNCH=True
- /ALLOW_CLIENTHOSTEDAPPSURL=1 – enables Local App Access:
CitrixWorkspaceApp.exe /ALLOW_CLIENTHOSTEDAPPSURL=1
Registry values
HKLM\Software\Wow6432Node\Citrix\Dazzle on the Workspace app machine. All are of type REG_SZ (string) unless specified. Note: several of these are configurable using the Reciever.admx group policy template.
- SelfServiceMode (REG_SZ) = False – Turns off Workspace app’s Self-Service interface.
- PutShortcutsOnDesktop (REG_SZ) = True – If Self-Service interface is disabled, places all shortcuts on desktop.
- UseDifferentPathsforStartmenuAndDesktop (REG_SZ) = True
- UseCategoryAsStartMenuPath (REG_SZ) = True or False
- UseCategoryAsDesktopPath (REG_SZ) = True or False
- StartMenuDir (REG_SZ) = name of folder on Start Menu where shortcuts are placed.
- DesktopDir (REG_SZ) = name of folder on Desktop where shortcuts are placed
- EnablePreLaunch (REG_SZ) = True – If SSON is enabled then PreLaunch is already enabled by default.
- AllowAddStore (REG_SZ) = A – Only if using http (instead of https) to connect to StoreFront.
- AllowSavePwd (REG_SZ) = A – Only if using http (instead of https) to connect to StoreFront.
- UserDomainName (REG_SZ) = pre-filled domain name
- InitialRefreshMinMs (REG_SZ) = 1 – minimizes the launch delay before contacting store
- InitialRefreshMaxMs (REG_SZ) = 1 – minimizes the launch delay before contacting store
- RefreshMs (REG_SZ) = 3600000 (1 hour) – interval for Receiver icon refreshes. 1 hour is the default value.
- RefreshMs (REG_SZ) = 18000000 – Citrix CTX213755 Citrix Receiver Shows Authentication Window Periodically When Receiver is Not Opened
- MaxSimultaneousFetches (REG_DWORD) = 6 – improves the time of loading icons in Start Menu
- MaxSimultaneousSubscribes (REG_DWORD) = 6 – improves the time of loading icons in Start Menu
- DontWarnOfRemovedResources (REG_SZ) = True – prevents dialog boxes when resources are removed from the server. (or False)
- SilentlyUninstallRemovedResources (REG_SZ) = True – prevents dialog boxes when resources are removed from the server
- PreferTemplateDirectory (REG_SZ) = UNC path or local path containing shortcuts copied by the prefer keyword. Give the shortcuts a short name.
- PnaSSONEnabled (REG_SZ) = True – Enables Single Sign-on for PNAgent (Web Interface).
- WSCReconnectMode (REG_SZ) = 3 (default) – If this Workspace app is running inside a VDA published desktop, set it to 0.
- If you’re having trouble getting sessions to reconnect, see Receiver 4.3 Desktop will not auto-reconnect when logging into a machine at Citrix Discussions
- AlwaysUseStubs (REG_SZ) = True. Workspace app and Receiver 4.3.100 and newer don’t create .exe stubs by default. Set this to create .exe stubs. Also see Citrix CTX211893 Controlling Shortcut behavior in Receiver 4.3.100.
- DontCreateAddRemoveEntry (REG_SZ) = True – don’t create “Delivered by Citrix” entries in Programs and Features
- DesktopNameFormatString = format string for shortcut names – For example “{0}_{1}_{2}_{3}”. See the link for details.
- SelfServiceFlags (REG_DWORD) = 4 – prevents duplicate shortcuts when roaming and Desktop is redirected.
- SelfServiceFlags = 5 to stop external SSON from prompting for authentication
- ReEvaluateNetwork (REG_SZ) = true – for Beacon detection with Single FQDN
To prevent the Win+G popup on Windows 10 machines:
- HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\GameDVR
- AllowGameDVR (REG_DWORD) = 0
To allow adding non-HTTPS stores to Workspace app:
- HKLM\Software\Wow6432Node\Citrix\AuthManager
- ConnectionSecurityMode (REG_SZ) = Any
To increase ICA bandwidth consumption over high latency links, set:
- HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Citrix\ICA Client\Engine\Configuration\Advanced\Modules\TCP/IP
- OutBufCountClient2 = Number of OutBufs (default is 44)
- OutBufCountHost2 = Number of OutBufs (default is 44)
- See CTX125027 How to Optimize HDX Bandwidth Over High Latency Connections for some recommended values (multiples of 44)
To prevent beacon probing from using proxy, set:
- HKEY_LOCAL_MACHINE\Software\WOW6432Node\Citrix\Receiver\inventory
- BeaconProxyEnabled (REG_DWORD) = 0
To enable foreground progress bar, set:
- HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Citrix\ICA Client
- ForegroundProgressBar (REG_DWORD) = 1
For client-to-server file type redirection, set:
- HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Citrix\ICA Client\Engine\Configuration\Advanced\Modules\ClientDrive
- NativeDriveMapping=”TRUE”
To fix USB devices that emulate a keyboard, set:
- HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Citrix\ICA Client\Engine\Lockdown Profiles\All Regions\Lockdown\Virtual Channels\Keyboard
- KeyboardTimer=”10”
To remember manually mapped USB devices when auto-connection is enabled, set: (2409 and newer)
- HKLM\SOFTWARE\Citrix\ICA Client\GenericUSB (same path for 32-bit and 64-bit, create the keys)
- RememberConnections (DWORD) = 0x1
To override the devices that are mapped using optimized channels instead of generic USB, see Citrix CTX123015 How to Configure Automatic Redirection of USB Devices
Group Policy Settings
Copy the Workspace app ADMX template (C:\Program Files (x86)\Citrix\ICA Client\Configuration\receiver.admx) to C:\Windows\PolicyDefinitions (or Sysvol). Also copy receiver.adml to C:\Windows\PolicyDefinitions\en-us (or Sysvol).
Edit a GPO that applies to client machines, go to Computer Configuration | Policies | Administrative Templates | Citrix Components | Citrix Workspace and configure the following:
- To enable pass-through authentication: go to | User Authentication |.
- Local Username and Password – Check the top two boxes.
- Also add the StoreFront FQDN to the Local Intranet zone in Internet Explorer.
- Single Sign-on for NetScaler Gateway (Workspace app 1808 and newer)
- To add a store, go to | StoreFront |
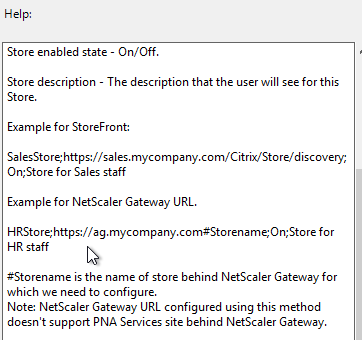
- StoreFront Accounts List – see the help text
- To enable Auto-Update, go to | AutoUpdate | or | Citrix Workspace Updates |. (the node was renamed in 4.11 and Workspace app)
- Enable or Disable AutoUpdate or
- Citrix Workspace Updates
- To modify the desktop viewer toolbar, go to | Client Engine |
- Desktop Viewer Toolbar Options (2409 and newer)
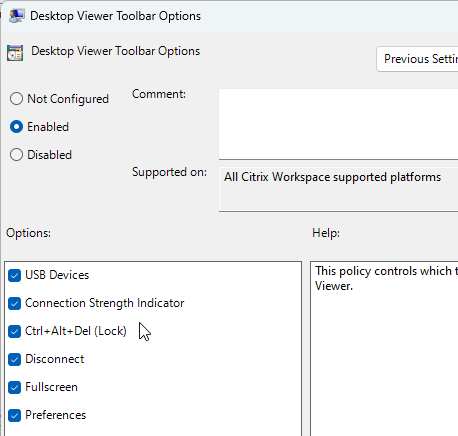
- Desktop Viewer Toolbar Options (2409 and newer)
- To enable Local App Access, go to | User Experience |
- Local App Access Settings
- To prevent the endpoint from sleeping while session is active, go to | User Experience |
- Power Management (2405 and newer)
- To configure the Self-Service interface, go to | SelfService |
- Set Manage SelfServiceMode to Disabled to completely disable the Self-Service window. This causes all icons to be placed on the Start Menu.
- Enable Manage App Shortcut and configure it as desired.
- To allow the Self-Service window, but prevent it from automatically opening (reside in systray), tick Prevent Citrix Workspace performing a refresh of the application list when opened. Source
- Enable Control when Workspace attempts to reconnect to existing sessions. If this is a VDA published desktop, set it to Disabled. Otherwise configure it as desired.
- Set Enable FTU to Disabled to prevent the Add Account wizard from displaying.
- Enable Allow/Prevent users to publish unsafe content if publishing content that’s opens a file or file share.
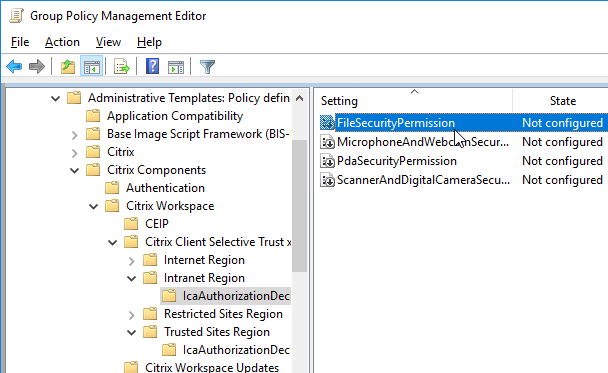
Enable automatic client drive and client microphone mapping:
- In a client-side GPO, add the GPO ADM template from http://support.citrix.com/article/CTX133565.
- Enable the setting Create Client Selective Trust Keys. See Below for details.
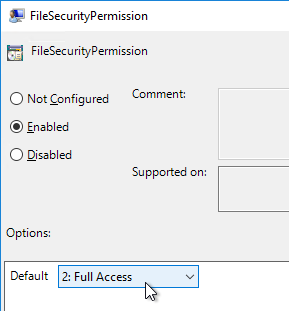
- Configure the FileSecurityPermission setting in one or more of the regions.
- Configure the MicrophoneAndWebcamSecurityPermission setting in one or more of the regions.
Citrix CTX203658 Start Menu Icons Set to Default (Blank Document) After Update to Receiver 4.3.100 – Windows 8 and newer
- Computer Configuration | Policies | Administrative Templates | Windows Components | File Explorer
- Allow the use of remote paths in file shortcut icons = enabled
For Single Sign-on in Windows 11 24H2 and newer, enable the following GPO setting:
- Computer Configuration | Policies | Administrative Templates | Windows Components | Windows Logon Options
- Enable MPR notifications for the System = enabled
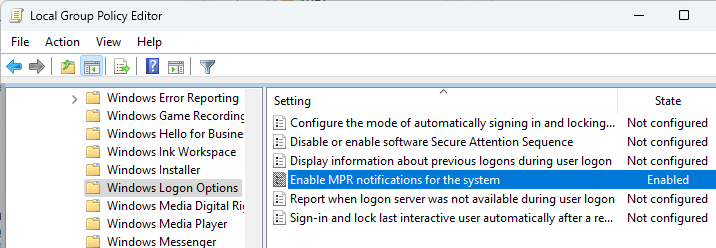
- Enable MPR notifications for the System = enabled
Deploy Workspace app using Active Directory
To deploy Workspace app using Active Directory, configure a GPO with a computer startup script that runs the Workspace app installer executable. Citrix provides sample scripts that can be downloaded from one of the Workspace app download pages (Workspace app current release version 2409.10, or LTSR version 2402 CU3, by expanding Downloads for Admins (Deployment Tools).
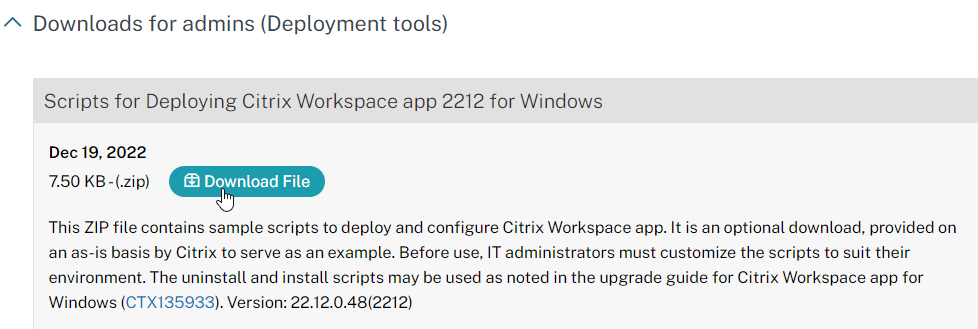
Also see CTA Dennis Span Citrix Receiver unattended installation with PowerShell.

Change Workspace App’s Store Configuration, including Reset Citrix Workspace
You can change Workspace app’s configured Store/Account with a couple command lines:
"C:\Program Files (x86)\Citrix\ICA Client\SelfServicePlugin\SelfService.exe" -deleteproviderbyname Corporate "C:\Program Files (x86)\Citrix\ICA Client\SelfServicePlugin\SelfService.exe" -init -createprovider Corporate https://storefront.corp.com/Citrix/Store/discovery
It is sometimes necessary to Reset Citrix Workspace by right-clicking the Workspace app systray icon, clicking Advanced Preferences, and clicking the Reset link. You can do this from the command line by running "C:\Program Files (x86)\Citrix\ICA Client\SelfServicePlugin\CleanUp.exe" -cleanUser -silent. See CTX140149 How to Reset Receiver Using the Command Line.
Workspace app Group Policy ADMX Template
Many of the Workspace app configuration settings must be configured in group policy. These Workspace app settings are only available after installing the GPO templates.
Alternatively, Citrix Cloud customers can use Global App Configuration Service to configure Workspace app. Today it’s a REST API, but Citrix has started adding a GUI at Workspace Configuration > App Configuration.
For GPO configuration:
- From a machine that has Workspace app installed, find the .admx and .adml files in the C:\Program Files (x86)\Citrix\ICA Client\Configuration.
- Copy the CitrixBase.admx and receiver.admx files. Also copy the en-US folder. In Workspace app, the files are still named receiver.admx.
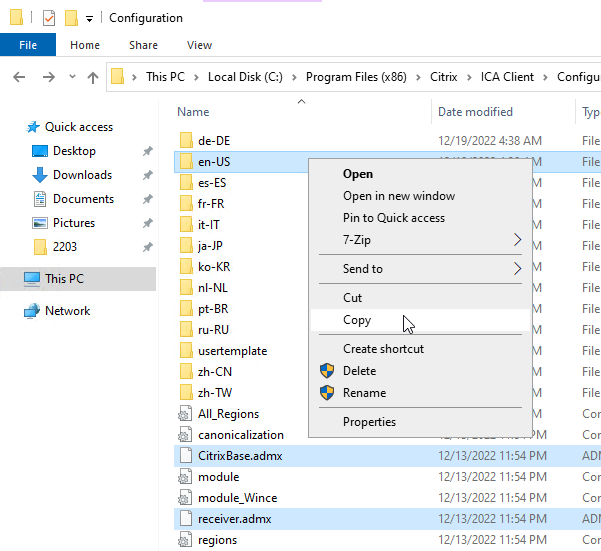
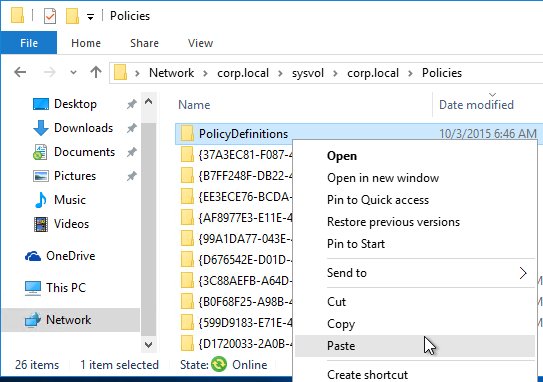
- Go to your domain’s SYSVOL share and in the Policies folder look for a PolicyDefinitions folder. If one exists, paste the .admx file directly into the PolicyDefinitions folder. If this folder doesn’t exist in SYSVOL, instead copy the .admx file to C:\Windows\PolicyDefinitions. Overwrite any existing Receiver ADMX files.
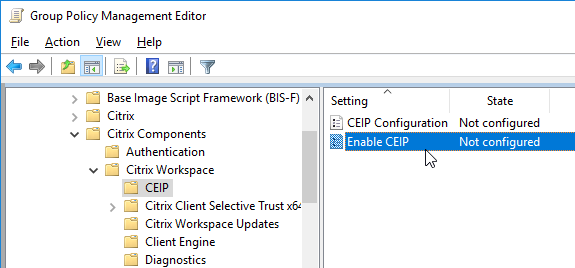
- The GPO settings can then be found at one of the following:
- Computer Configuration > Policies > Administrative Templates > Citrix Components > Citrix Workspace
- Computer Configuration > Policies > Administrative Templates > Citrix Components > Citrix Receiver
- For example, you can disable Customer Experience Improvement Program (CEIP) from here.
- See https://www.carlstalhood.com/delivery-controller-cr-and-licensing/#ceip for additional places where CEIP is enabled.
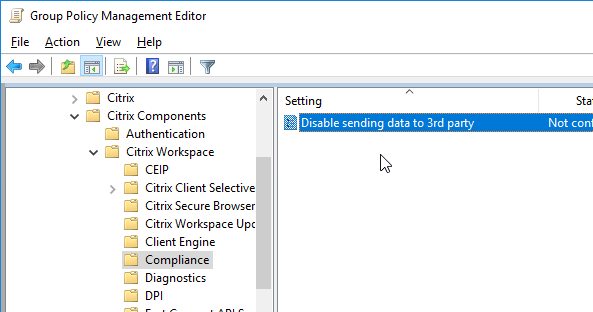
- Workspace app 1905 and newer has a setting to Disable sending data to 3rd party (e.g., Google Analytics).
- Workspace app 1905 and newer let you disable embedded browser caching.
- Workspace app 1905 and newer have NetScaler LAN Proxy under Network routing > Proxy.
- Workspace app 1808 and newer have User authentication | Single Sign-on for NetScaler Gateway.
- Citrix Workspace Updates, (aka AutoUpdate) can be configured using group policy. See Configuring Citrix Workspace Updates at Citrix Docs.
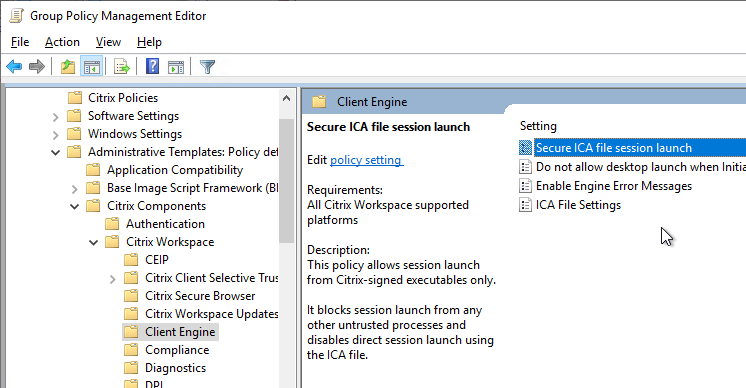
- Workspace app 1912 and newer can be configured to require in-memory ICA files only. The setting called Secure ICA file session launch is under the Client Engine node. See Citrix Docs for details on in-memory ICA files instead of writing ICA files to disk.
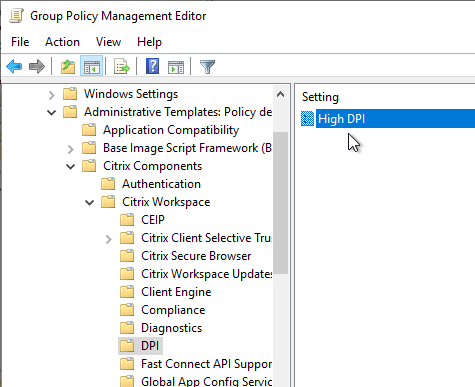
- The DPI node has a setting called High DPI that lets you disable DPI matching, which is enabled by default in Workspace App 2206 and newer.
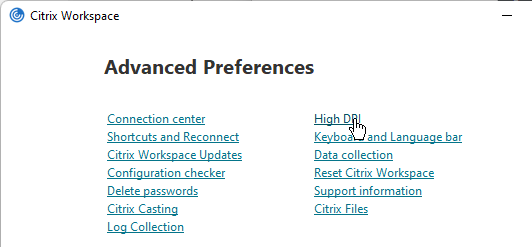
- Workspace app 2210 and newer let you use the GUI to re-enable High DPI.
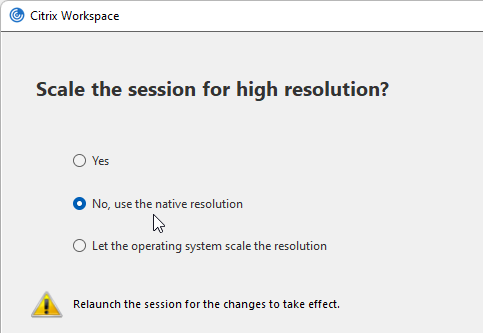
- Native resolution means DPI matching, whereas Yes means force high DPI.
- Workspace app 2210 and newer let you use the GUI to re-enable High DPI.
- Workspace app has settings to hide Advanced Preferences, enable/disable showing the DPI option, and enable/disable H265.
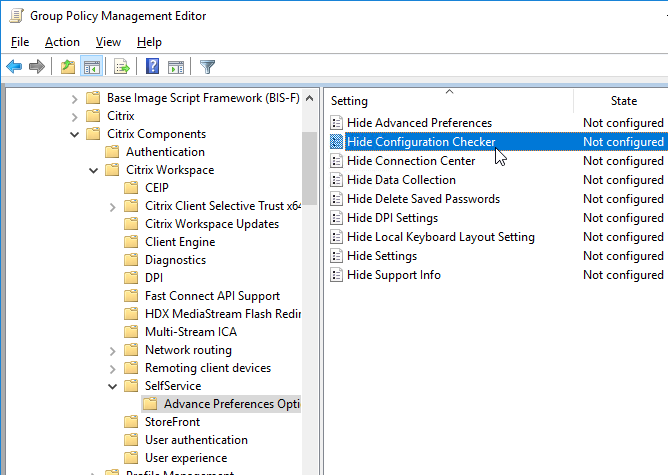
- Workspace app 4.8 and newer have SplitDevices GPO setting under Citrix Workspace | Remoting client devices | Generic USB Remoting. See Configuring composite USB device redirection at Citrix Docs.
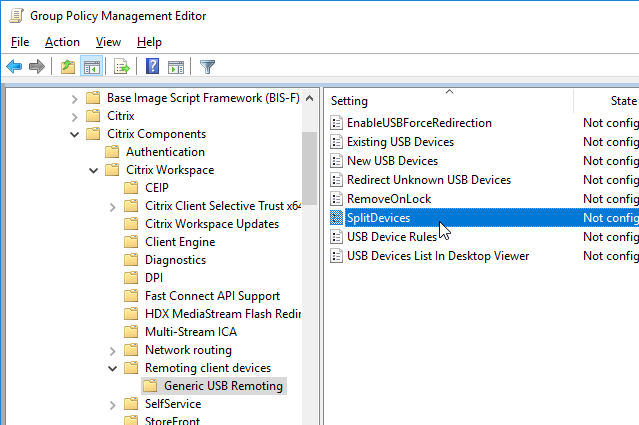
- Workspace app 2212 and newer by default disable App Protection for the authentication screen and icons list. To enable them, configure User authentication | Manage App Protection and SelfService | Manage App Protection.
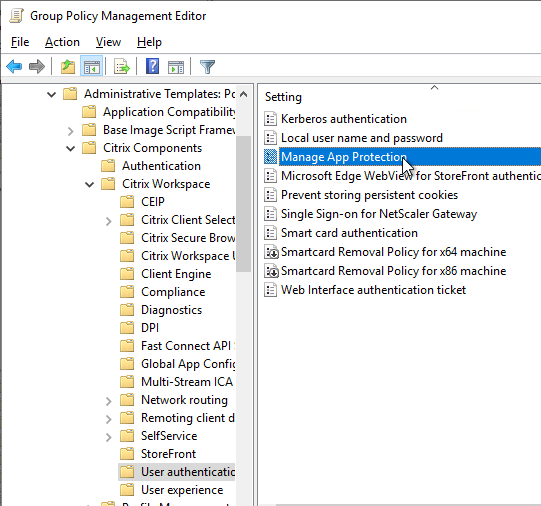
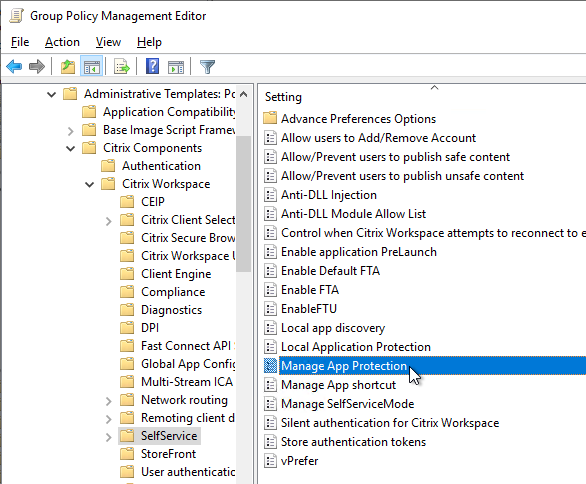
- Workspace app 2303 and newer have Anti-DLL Injection for App Protection. It is disabled by default. Enable it in a GPO at Citrix Components | Citrix Workspace | App Protection | Anti-DLL Injection. See Citrix Docs for details.

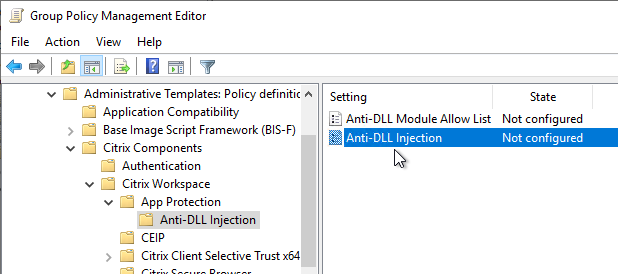
Pass-through Authentication
Citrix blog post – A Comprehensive Guide to Enabling Pass-Through Authentication with XenDesktop 7.5
- Run the command
Set-BrokerSite -TrustRequestsSentToTheXmlServicePort $True from a Windows PowerShell command prompt on a Delivery Controller.
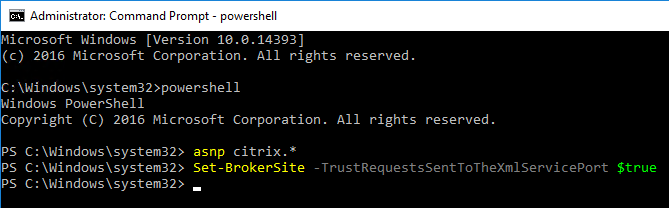
- In XenApp 6.5, this is a Citrix Policy > Computer > Trust XML Requests.
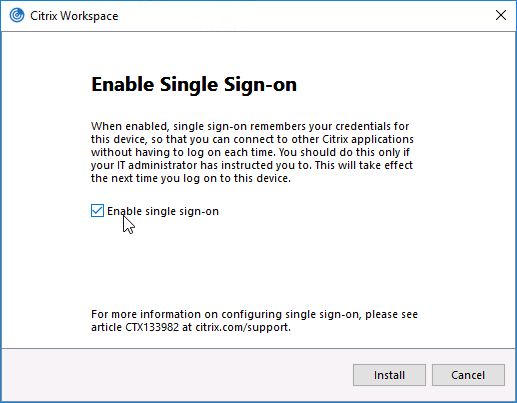
- Login to the PC as an administrator.
- If installing Workspace app, as an administrator, during installation, on the Enable Single Sign-on page, check the box next to Enable Single Sign-on. Then finish the installation.
- To verify that SSON is installed, go to C:\Program Files (x86)\Citrix\ICA Client and look for the file ssonsvr.exe.
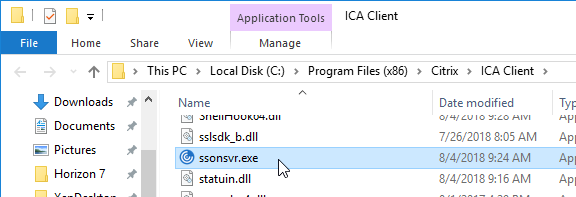
- And if you open regedit and go to HKLM\SYSTEM\CurrentControlSet\Control\NetworkProvider\Order, you should see PnSson in the ProviderOrder.
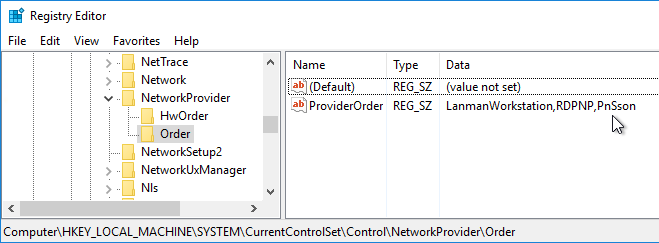
- Install the receiver.admx (and .adml) template into PolicyDefinitions if you haven’t already.
- Edit a GPO that is applied to the client PCs where the Workspace app is installed.
- Go to Computer Configuration > Policies > Administrative Templates > Citrix Components > Citrix Workspace.
- Expand Citrix Workspace and click User authentication.
- On the right, double-click Local user name and password.
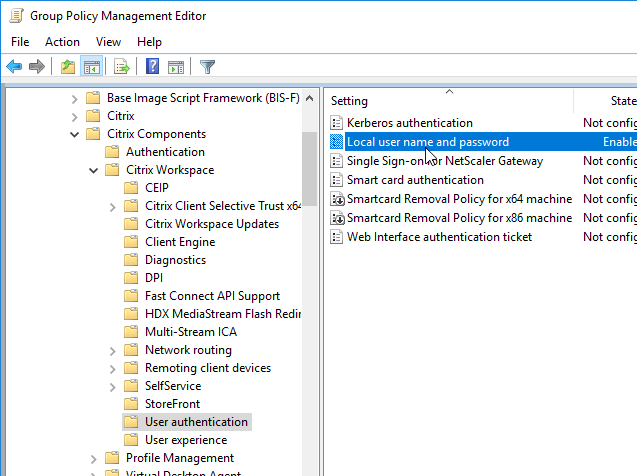
- Select Enabled and then check the box next to Allow pass-through authentication for all ICA connections. Click OK.
- In Workspace app 1808 and newer, you can enable Single Sign-on for NetScaler Gateway.
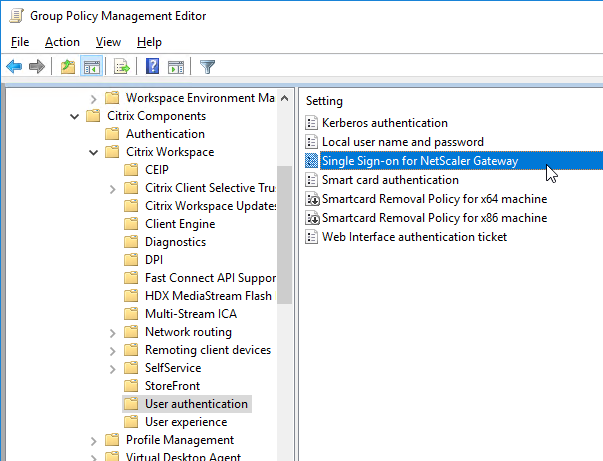
- Ensure that the internal StoreFront FQDN is in the Local Intranet zone in Internet Explorer. You can use a GPO to configure this on the client side.
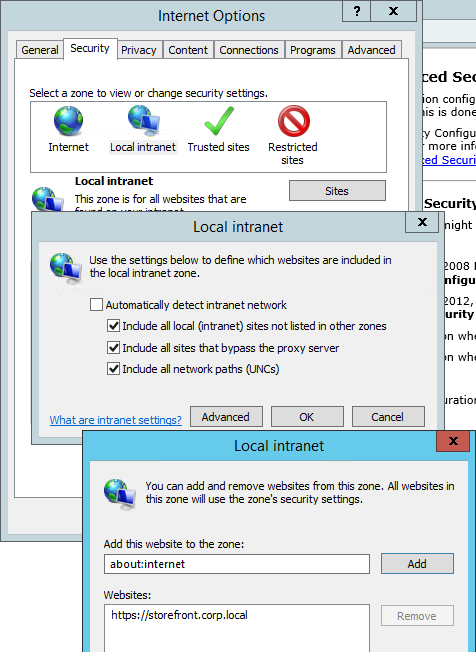
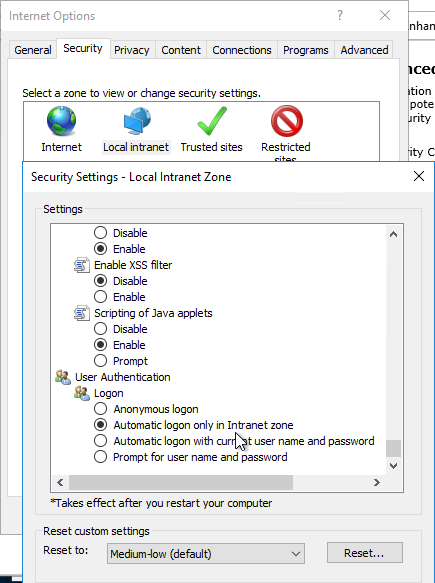
- Local Intranet zone should have Automatic logon only in Intranet zone enabled.
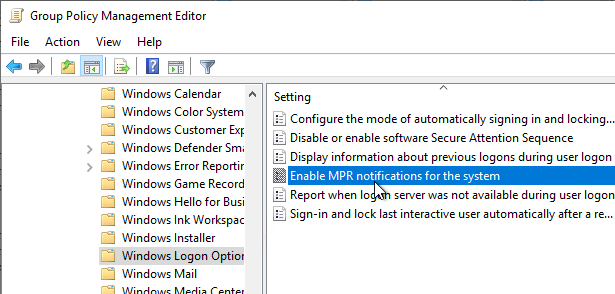
- For Windows 11 24H2 and newer, make sure the GPO setting Enable MPR notifications for the System is enabled at Computer Configuration | Policies | Administrative Templates | Windows Components | Windows Logon Options. Make sure HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\System\EnableMPRNotifications is set to 1 on the Workspace app machine.
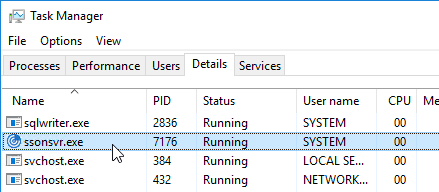
- Logoff Windows and log back on. In Task Manager you should now see ssonsvr.exe. This won’t appear unless you logoff and log back on.
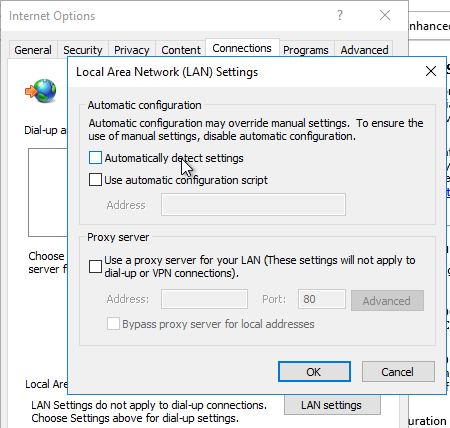
- If Workspace app won’t connect or is slow to enumerate icons, then you might have to disable Automatically detect settings in IE.
- Right-click the Workspace app icon and click Advanced Preferences.
- Click Configuration Checker.
- Check the box next to SSONChecker and click Run.
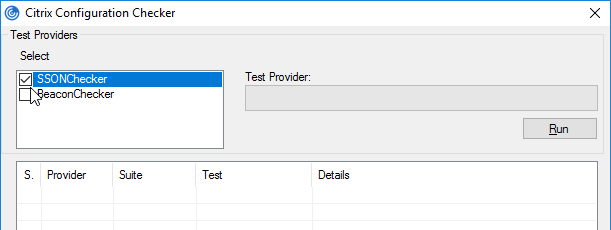
- The lines with red x will indicate the issue and corrective action.
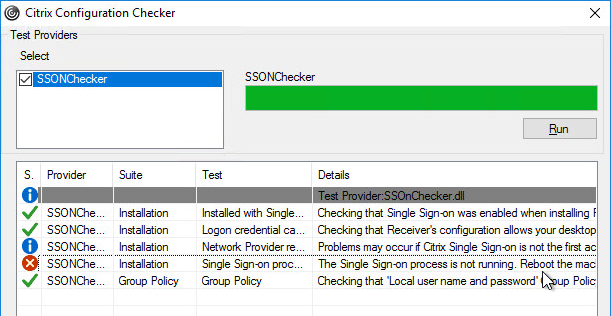
StoreFront Accounts
You can use a client-side GPO to add a store (Account) to Workspace app Self-Service.
- Install the receiver.admx (and .adml) template into PolicyDefinitions if you haven’t already.
- Edit a GPO that applies to endpoint devices that have Citrix Workspace app installed.
- Go to Computer Configuration > Administrative Templates > Policies > Citrix Components > Citrix Workspace > StoreFront.
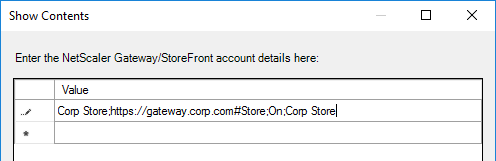
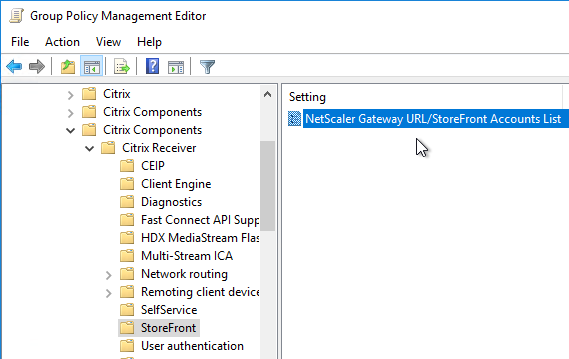
- On the right, double-click NetScaler Gateway URL/StoreFront Accounts List.
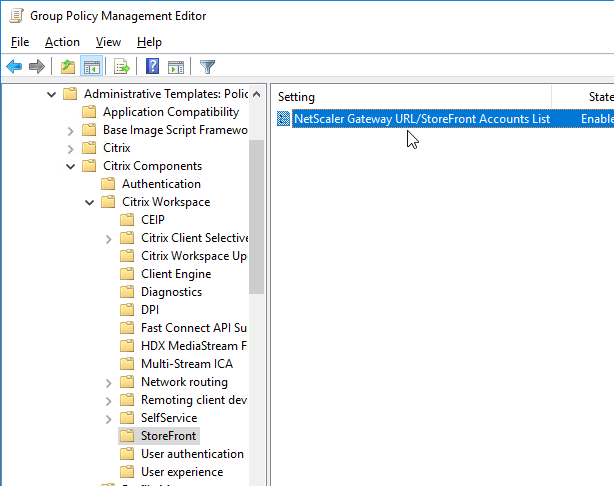
- Select Enabled, and then click Show.
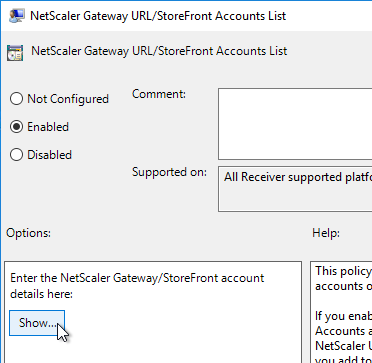
- Enter a store path based on the example shown in the Help box. Workspace app lets you enter a Gateway path. Then click OK.
- Note: Gateway paths work in GPO, but might not work when specified in the CitrixWorkspaceApp.exe installation command line.
Published Shortcuts and Reconnect
Citrix CTX200924 How to Customize App Shortcuts with Receiver for Windows
Workspace app has a user interface for setting Shortcut Paths. Right-click the Workspace app systray icon, click Advanced Preferences, and then click Shortcuts and Reconnect, or Settings Option.
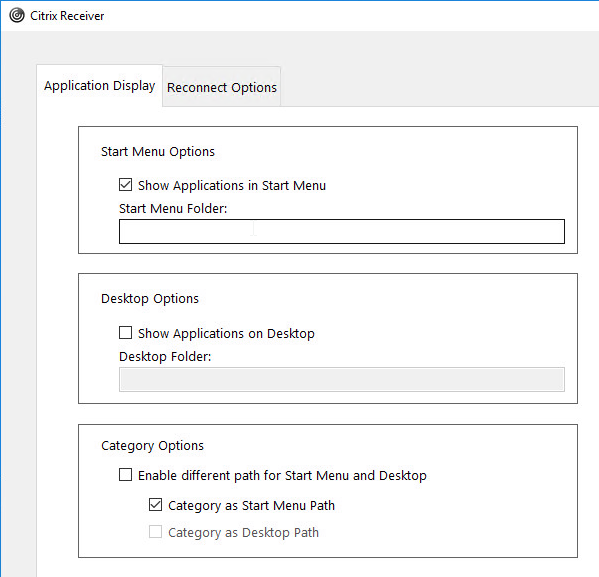
From Citrix Docs Configuring application delivery: There are several methods of controlling how Workspace app displays shortcuts on the Start Menu and Desktop as detailed below:
- Workspace app Registry values
- receiver.admx GPO Template
- From StoreFront in C:\inetpub\wwwroot\Citrix\Roaming\web.config
- Published App Keywords (e.g. prefer).
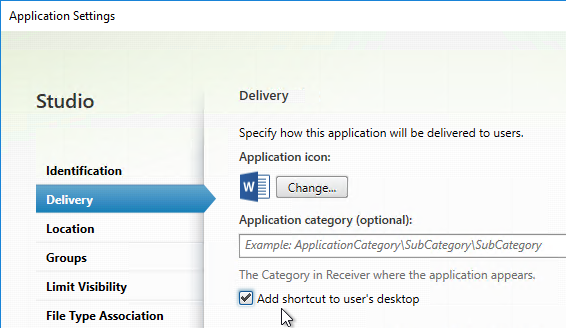
- Workspace app and Receiver 4.2.100 and newer supports published app Delivery configuration for adding the shortcut to the desktop. This only works if the app is a Favorite, or if Favorites are disabled, or Mandatory Store.
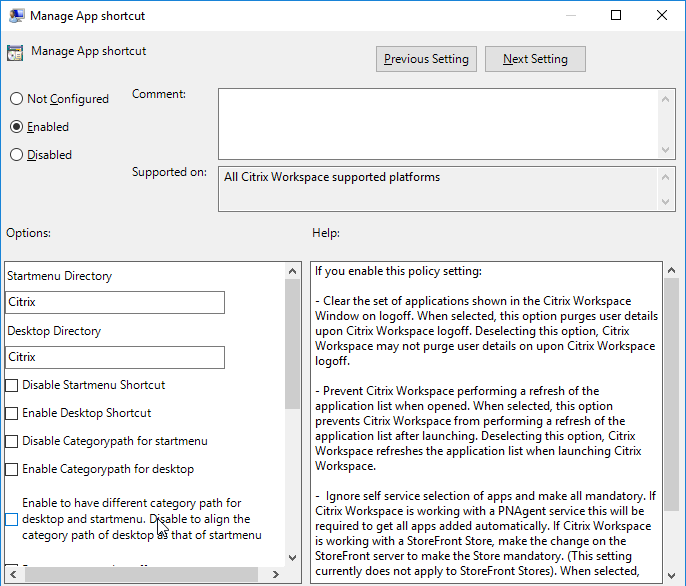
Under HKLM\Software\Wow6432Node\Citrix\Dazzle (or HKCU\Software\Wow6432Node\Citrix\Dazzle) are several registry values related to shortcuts. Some of the settings only apply if SelfServiceMode is set to False. Here are some common options:
- SelfServiceMode – set to False so Receiver disables the Self-Service interface and automatically places all published shortcuts on the Start Menu and/or Desktop. More details in Configuring application delivery at Citrix Docs.
- PutShortcutsOnDesktop – set to True to place every app on the desktop
- DesktopDir – Workspace app places every shortcut on the desktop so it’s probably best to place them in a folder.
- StartMenuDir – If there is potentially a conflict between local apps and remote apps, then you should place the Start Menu shortcuts in a folder.
- PreferTemplateDirectory (with KEYWORDS:prefer=shortcutname) – copies the shortcutname from the template directory to the Start Menu and/or Desktop.
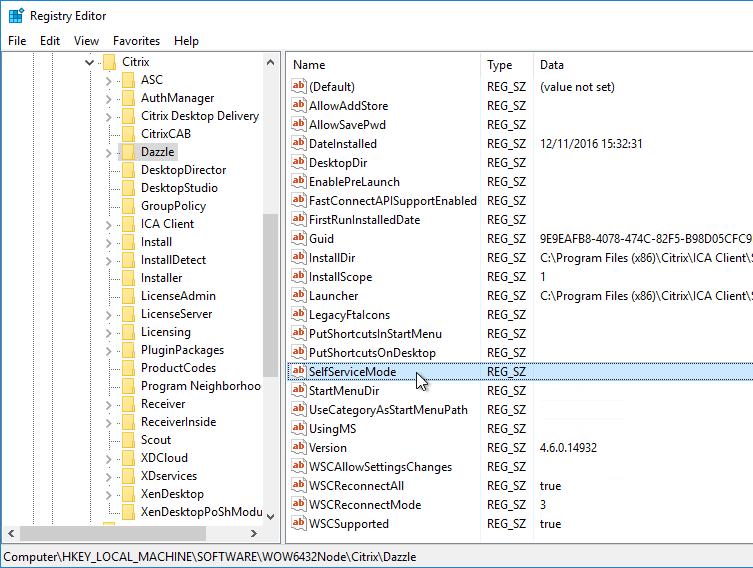
If you import the receiver.admx (and .adml) into the PolicyDefinitions folder, under Computer Configuration > Administrative Templates > Citrix Components > Citrix Workspace (or Receiver) is a node called SelfService.
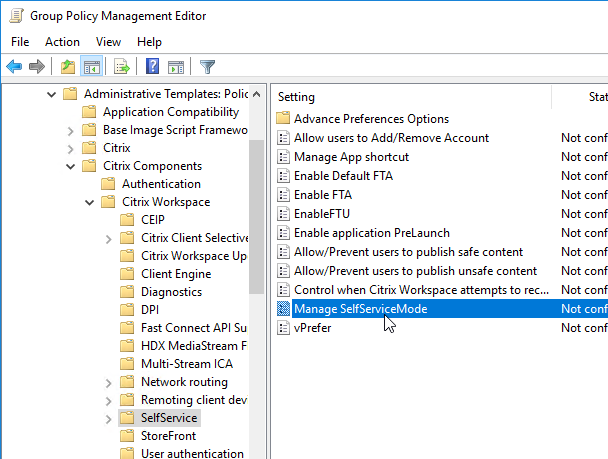
Disable the Manage SelfServiceMode setting to hide the Workspace app Window.
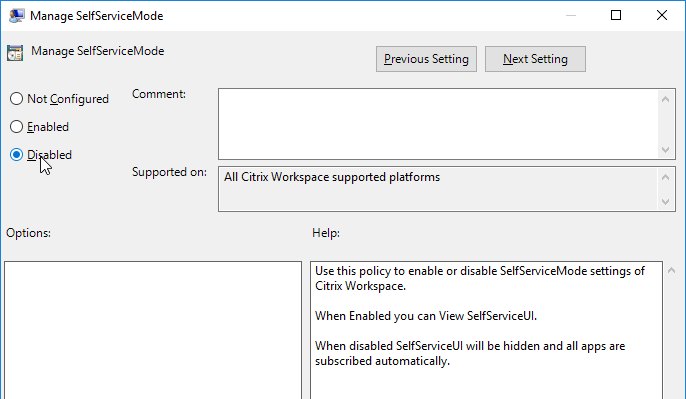
Enable the Manage App shortcut setting to control placement of shortcuts.
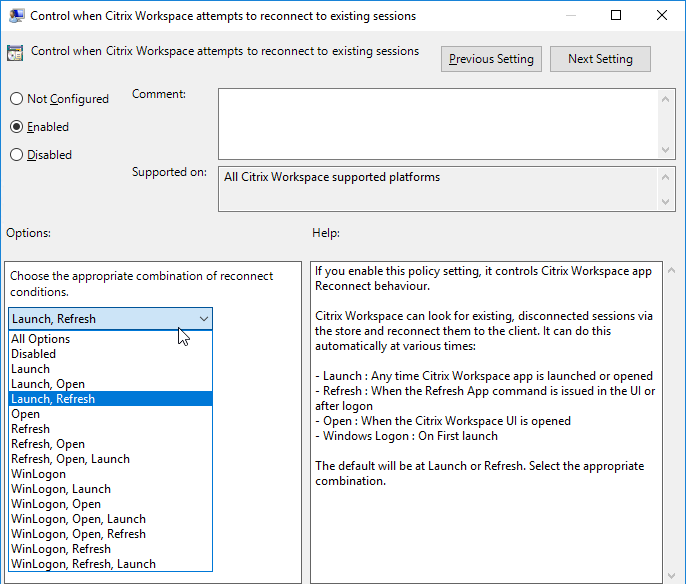
Workspace app and Receiver 4.2.100 and newer have the ability to configure (or disable) Workspace Control using group policy. Enable the setting Control when Citrix Workspace attempts to reconnect to existing sessions and configure it as desired.
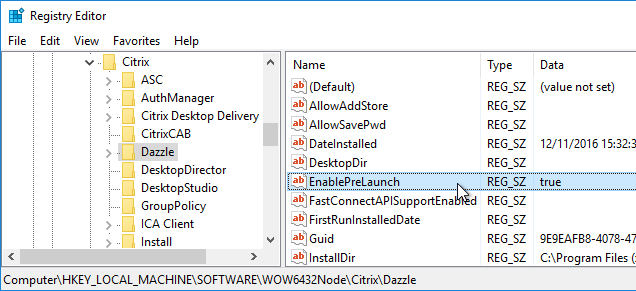
Prelaunch
Staring with Receiver 4.2, prelaunch is automatically enabled if Workspace app is installed with SSON enabled. Otherwise, set registry values to enable prelaunch. Receiver 4.2.100 prevents the prelaunch icon from appearing on the Start Menu.
- HKLM\Software\[Wow6432Node\]Citrix\Dazzle
- EnablePreLaunch (REG_SZ) = true or false
Additional customizations can be configured at:
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Citrix\ICA Client\Prelaunch
- Name: State
- REG_SZ: 0 = disable, 1 = just-in-time pre-launch, 2 = scheduled pre-launch
- Name: Schedule
- REG_SZ: HH:MM|M:T:W:TH:F:S:SU where HH and MM are hours and minutes. M:T:W:TH:F:S:SU are the days of the week. For example, to enable scheduled pre-launch on Monday, Wednesday, and Friday at 1:45 p.m., set Schedule as Schedule=13:45|1:0:1:0:1:0:0 . The session actually launches between 1:15 p.m. and 1:45 p.m.
- Name: UserOverride
- REG_SZ: 0 = HKLM overrides HKCU, 1 = HKCU overrides HKLM
Device Access Behavior (Client Selective Trust)
When connecting to a XenApp/XenDesktop session, you might see the following:
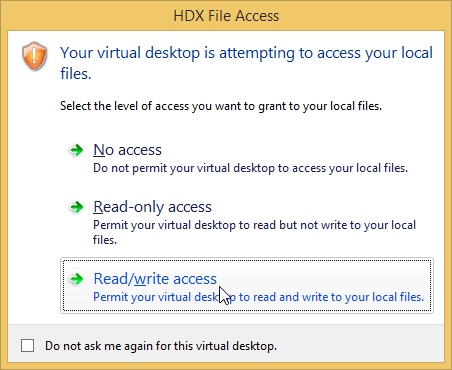
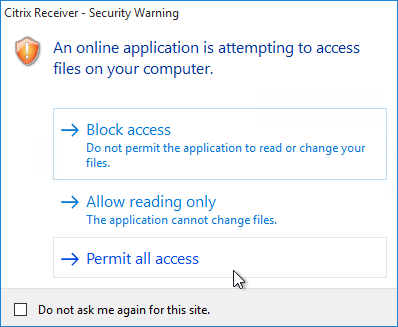
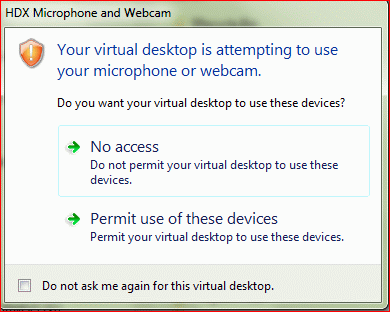
To configure the default behavior, see the Citrix Knowledgebase article How to Configure Default Device Access Behavior of Receiver, XenDesktop and XenApp. Note: there is a bug fixed in Receiver 4.2.100 and newer.
- Download the ADMX file from http://support.citrix.com/article/CTX133565.
- Copy the .admx and .adml files to PolicyDefinitions (Sysvol, or C:\Windows).
- The .adml file goes in the en-US folder.
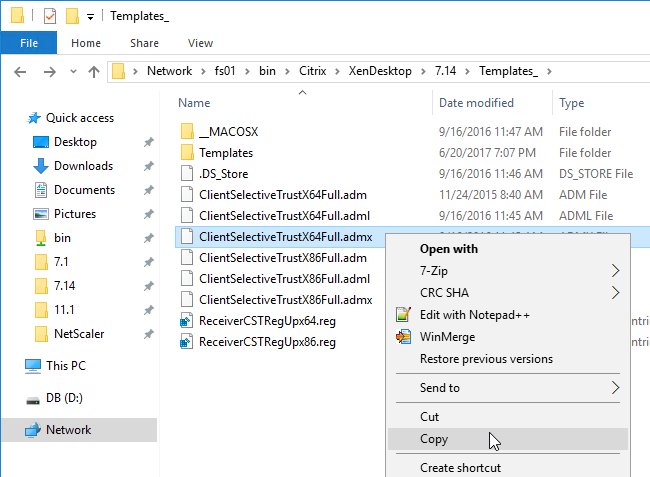
- Edit a GPO that applies to the endpoint devices that are running Receiver.
- Go to Computer Configuration | Policies | Administrative Templates | Citrix Components | Citrix Workspace (or Receiver) | Citrix Client Selective Trust (x64).
- Enable the setting Create Client Selective Trust Keys.
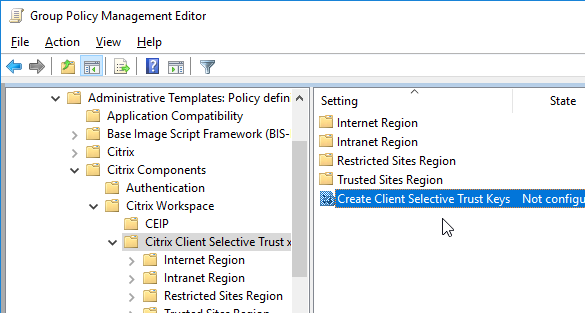
- Then expand the regions, and configure the permission settings as desired.
Desktop Lock
As an alternative to Workspace app Desktop Lock, see Transformer in Citrix Workspace Environment Manager.

External links:
- Dale Scriven YouTube video – Citrix Desktop Lock installation and configuration
- Jarian Gibson and Andrew Morgan – Citrix Receiver Desktop Lock
- An alternative to Desktop Lock – ThinKiosk
Use Studio to configure Workspace app Accounts in Published Desktop
In published desktops, Workspace app can be used for placement of shortcuts on the user’s Start Menu and Desktop. Use group policy to hide the common program groups and then use Workspace app to place published applications back on the Start Menu and Desktop based on user’s group membership and subscription preference.
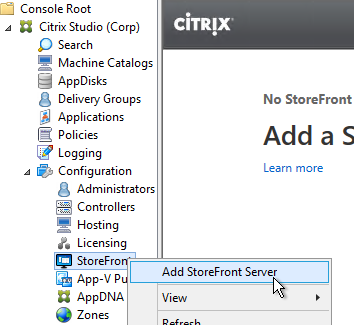
- In Citrix Studio, on the left, expand the Configuration node, right-click StoreFront and click Add StoreFront.
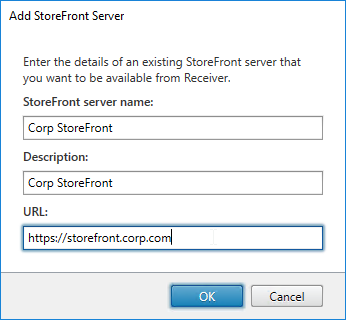
- Enter a descriptive name for the StoreFront server.
- Enter the internal https URL of the load balanced StoreFront servers. Add the path to your store (e.g. /Citrix/Store) and then /discovery on the end of the URL. The full URL would be similar to https://citrix.corp.com/Citrix/Store/discovery. Click OK.
- Edit a Delivery Group that has a published desktop and Citrix Workspace app installed.
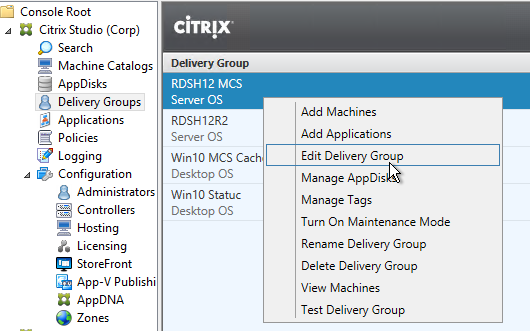
- On the StoreFront page, change the selection to Automatically, using the StoreFront servers selected below, and then check the box next to the StoreFront URL. Click OK. Now when users launch the published desktop, Workspace app will be automatically configured with this URL.
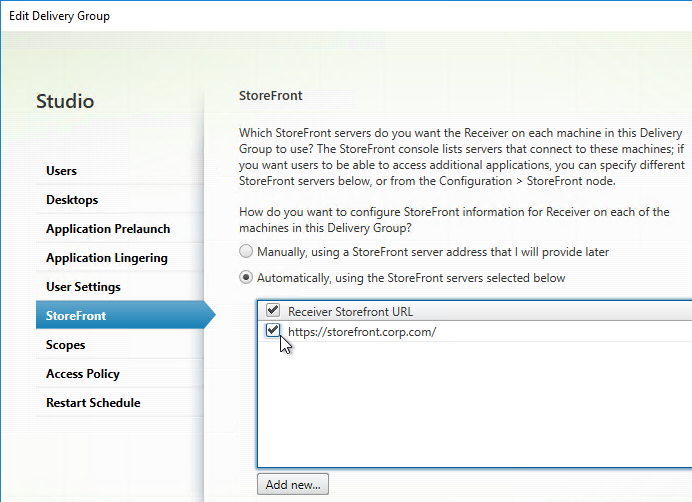
Published Desktop – use Workspace app to control Shortcuts
If you install Workspace app inside a published desktop (Workspace app on a VDA), then Workspace app can get icons from StoreFront and put those icons on the user’s published desktop Start Menu and Desktop. This is an alternative to using a User Experience Management product to control shortcut placement.
Note: Workspace app tends to be slow to create Start Menu shortcuts, so make sure you perform a Proof of Concept to determine how this functionality impacts logon times.
Configuration of Workspace app inside a published desktop is simplified if you have the following minimum versions:
- Workspace app installed inside the VDA
- VDA 7.17 or newer
- StoreFront 3.14 or newer
If you meet these minimum version requirements, then Workspace app installed in the VDA automatically tries to launch published applications on the same local VDA rather than trying to launch them from a different VDA (aka double-hop). This feature is called vPrefer.
- If you don’t meet these minimum version requirements, then you’ll need to use the older Prefer Keyword method of handling Workspace app shortcuts as detailed later.
- For a detailed explanation of vPrefer, see Citrix Blog Post VPrefer: Session Sharing Between a Published Desktop and a Published Application Made Easy
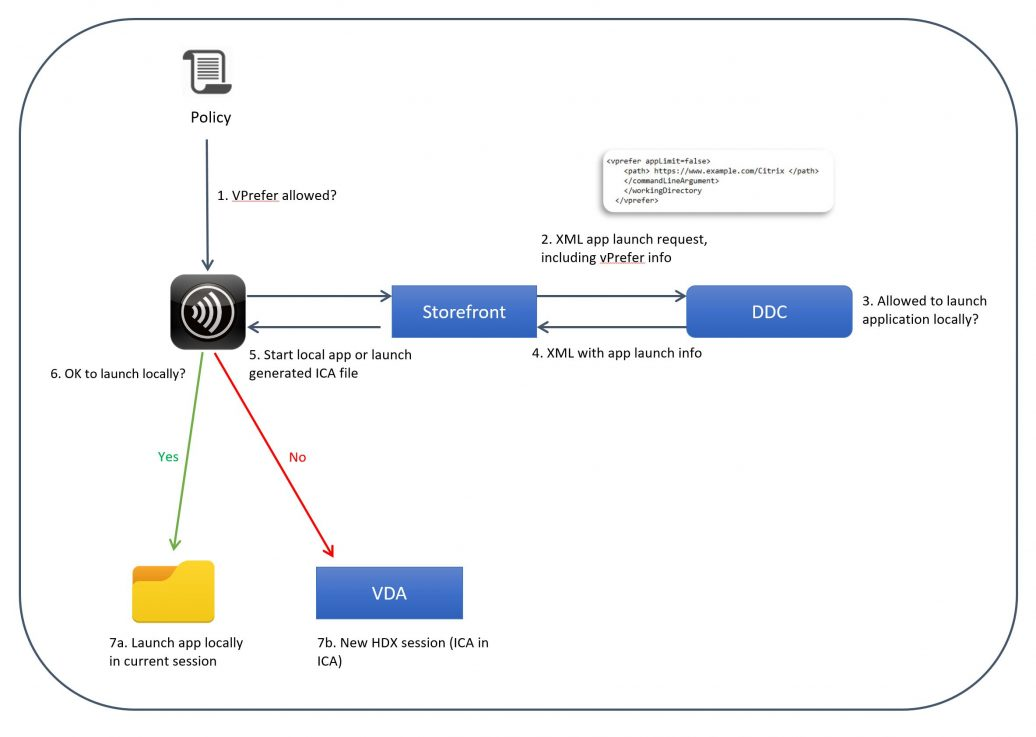
Do the following for all versions of Workspace app, VDA, and StoreFront, whether using the Prefer keyword or not:
- Make sure Workspace app or Receiver version 4.11 or newer is installed on the VDA.
- Install the Workspace app ADMX files if you haven’t already. For vPrefer, make sure they are the ADMX files from Workspace app.
- Enable the Group Policy setting Remove common program groups from Start Menu and apply it to non-administrators.
- This removes all Public (aka All Users) Start Menu shortcuts. Workspace app will re-add the shortcuts based on user group membership.
- On the VDA, configure the following Workspace app Registry keys (or corresponding settings in the receiver.admx GPO template):
- HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Citrix\Dazzle\WSCReconnectMode=”0″ so Workspace app doesn’t try to reconnect to the published desktop you’re already running.
- HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Citrix\Dazzle\SelfServiceMode to False. This turns off the Workspace app Self-Service GUI and acts like all icons are subscribed. Otherwise, only subscribed (favorited) icons would be placed on the Start Menu and Desktop.
- HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Citrix\Dazzle\UseCategoryAsStartMenuPath = True. This creates a Start Menu folder based on the published app’s configured Category.
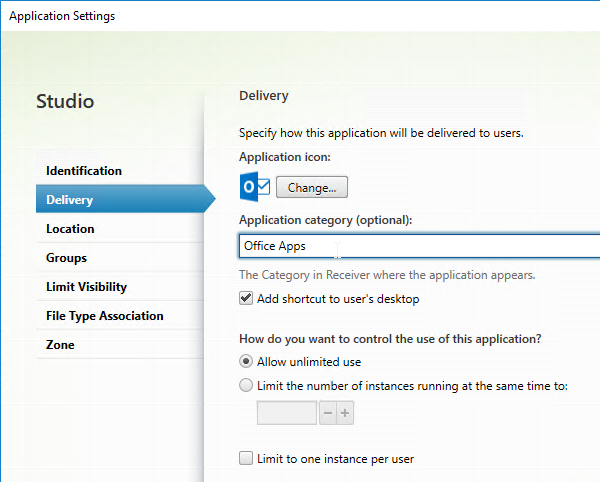
- Configure each desired published app to Add shortcut to user’s desktop.
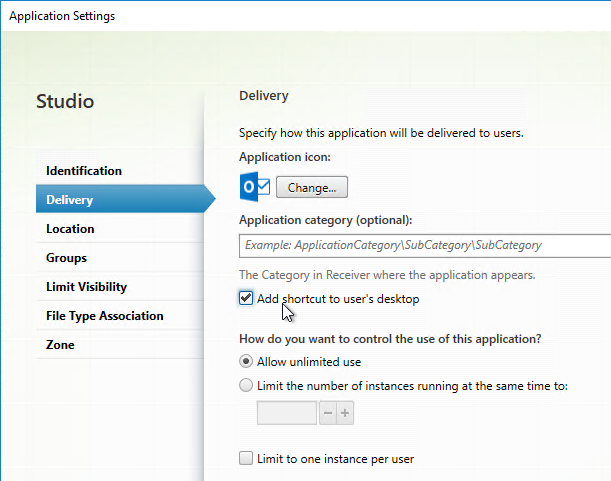
- Or, configure HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Citrix\Dazzle\PutShortcutsOnDesktop = True to place all icons on the desktop.
- To control icon placement, configure the following registry values:
- HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Citrix\Dazzle\StartMenuDir to place published applications in a sub-folder. Note: Windows Server 2012 and Windows 10 and newer only supports a single level of Start Menu folders, so setting this effectively turns off published app categories.
- HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Citrix\Dazzle\DesktopDir to place published applications in a sub-folder on the desktop.
- Pass-through authentication:
- In a GPO that applies to the VDA, import the receiver.admx file, and set Local user name and password to Enabled. Check the box next to Allow pass-through authentication for all ICA connections.
- If you’re using Gateway internally, and if Workspace app 1808 or newer, then also enable Single Sign-on for NetScaler Gateway.
- In a user-level GPO that applies to the VDA, add the StoreFront FQDN to the Local Intranet zone. Make sure it is not in the Trusted Sites zone, or enable Automatic logon with current user name and password for the Trusted Sites zone.
- Make sure ssonsvr.exe is running after you login to the VDA. If not, troubleshoot it.
- When configuring Citrix Profile Management, make sure !ctx_startmenu! is not excluded from roaming.
- In Citrix Studio, configure a Delivery Group with delivery type = Desktop and Applications. Assign users to the delivery group, and the individual published applications (if visibility is limited).
- In Citrix Studio, edit each published application, and on the Delivery tab, specify a category. This will become the Start Menu folder name.
- If Workspace app Self Service Mode (GUI) is enabled, in Studio, edit each application, and add KEYWORDS:Auto and/or KEYWORDS:Mandatory to the published application description. This forces the applications to be subscribed/favorited. Only subscribed (or Favorite) apps are displayed in the Start Menu and Desktop. Unless you disable Workspace app’s SelfService interface as described earlier.
- Another option is to go to the StoreFront Console, click Stores on the left, and on the right, click Configure Store Settings, and click Disable User Subscriptions. This causes all apps to appear on the Start Menu and/or Desktop depending on Workspace app configuration.
- Create a group policy that applies to VDAs, and configure the group policy to define the Store URL for Workspace app similar to https://citrix.corp.com/Citrix/Store/discovery. Replace the FQDN with your load balanced StoreFront FQDN. Also replace the path to the store with your store path. Make sure there is /discovery on the end. By default, Workspace app and Receiver only support https.
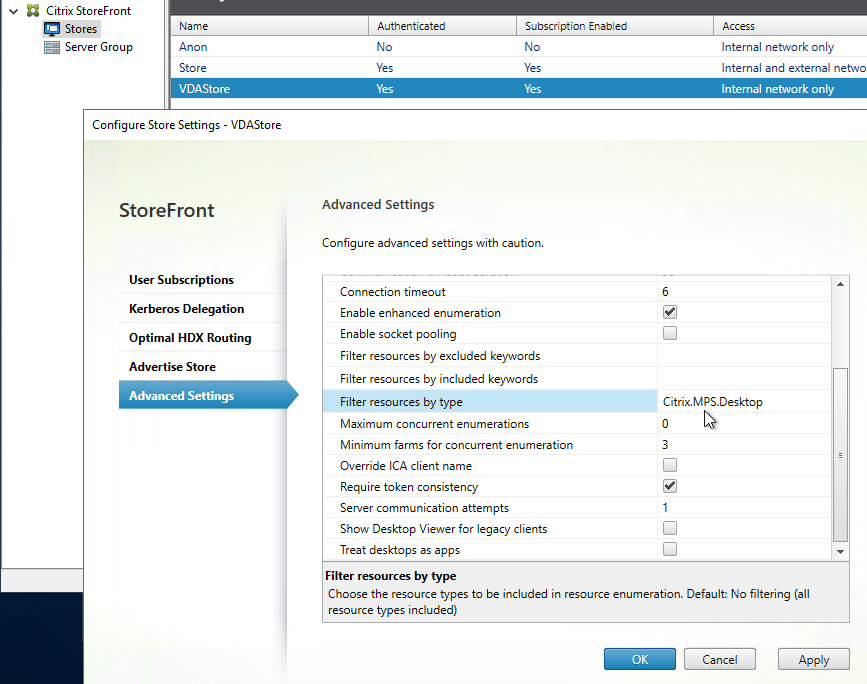
- Your StoreFront store probably delivers both application and desktop icons. If you want to filter out the desktop icons, then create a new StoreFront store, and configure the Workspace app on the VDA to connect to the new Store.
- In StoreFront Console, click the store for VDAs, and click Configure Store Settings. On the Advanced Settings page, in the Filter resources by type row, choose Citrix.MPS.Desktop.
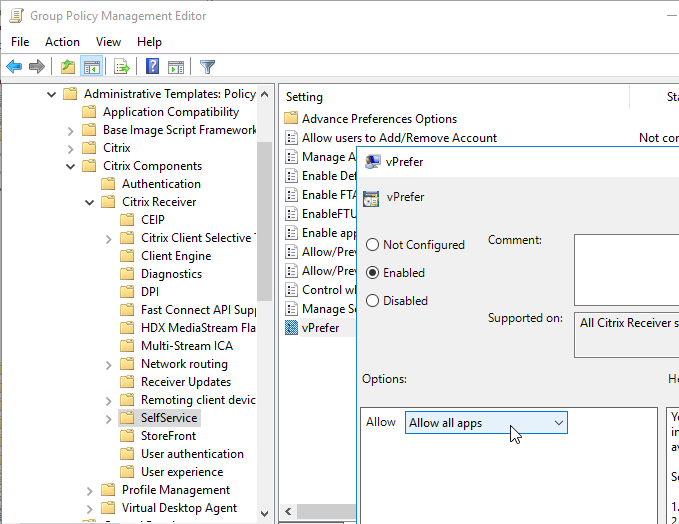
- For vPrefer in Workspace app, VDA 7.17 (or newer), and StoreFront 3.14 (or newer), edit a GPO that applies to the VDAs.
- Go to Computer Configuration | Policies | Administrative Templates | Citrix Components | Citrix Workspace (or Receiver) | SelfService.
- Edit the setting vPrefer. This setting is only in Workspace app ADMX templates from Workspace app.
- Set it to Allow all apps. Source = 7.17 vPrefer – not working with 32Bit Apps at Citrix Discussions.
- On your Delivery Controller, in PowerShell, run set-brokersite -TrustRequestsSentToTheXmlServicePort $true
- This is required for Pass-through Authentication from Workspace app.
- Configure your client devices to connect to the published desktop.
- When users connect to the published desktop, Workspace app will auto-launch and hopefully auto-login.
- If Workspace app Self-Service Mode is disabled, all published applications should automatically appear in the Start Menu and Desktop.
- If Workspace app Self-Service Mode is enabled, then only applications with KEYWORDS:Auto and/or KEYWORDS:Mandatory in the published application description will be displayed. Users can open the systray icon to subscribe to more applications.
- Users can copy icons from the Start Menu to the desktop. Make sure the user Copies the icon and doesn’t Move it.
- Users can then launch applications directly from the Start Menu, from the Desktop, or from the Workspace app (if the Self-Service interface is enabled).
- If Workspace app 4.11 (or newer), VDA 7.17 (or newer), and StoreFront 3.14 (or newer), then vPrefer is enabled by default. When launching an app icon that came from Workspace app, Workspace app checks the local VDA machine to see if the application can be launched on the local VDA instead of by creating a new Citrix double-hop session.
- If the application is installed locally on the VDA then the local application shortcut should launch quickly. If the application is on a different delivery group then a second (double-hop) Citrix HDX/ICA connection will be established.
- If the user deletes Workspace app shortcuts from the Start Menu, you can get them back by going to the systray icon and refreshing the applications. Or sometimes you have to reset Workspace app.
If you are running components older than Receiver 4.11, VDA 7.17, and StoreFront 3.14, then you’ll need to configure the prefer keyword to get Receiver delivered icons to launch on the local VDA instead of in a new double-hop Citrix connection.
- Enable the Group Policy setting Remove common program groups from Start Menu and apply it to non-administrators.
- For applications that are installed on the same VDA that is publishing the desktop, configure Group Policy Preferences to recreate the application shortcuts based on Active Directory group membership. Applications on other delivery groups are handled by Receiver.
- Or use the prefer keyword to copy shortcuts from the PreferTemplateDirectory.
- On the VDA, configure the following Receiver Registry keys (or corresponding settings in the receiver.admx GPO template):
- HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Citrix\Dazzle\PreferTemplateDirectory = a UNC path or local path containing shortcuts to be copied by the prefer keyword. This can point to C:\ProgramData\Microsoft\Windows\Start Menu.
- In Citrix Studio, configure a Delivery Group with delivery type = Desktop and Applications. Assign users to the Delivery Group and the applications (if visibility is limited).
- In Studio, edit each application and change KEYWORDS:Prefer to KEYWORDS:prefer. Notice the lower case p. It doesn’t work with uppercase P.
- With the prefer keyword, if you publish an application that is also created using Group Policy Preferences, the Group Policy Preferences icon will take precedence. This is good. Otherwise the Receiver published application icon would result in a new Citrix double-hop session.
- See Ralph Jansen Citrix Receiver 4.1 Prefer keyword examples
- If using the prefer keyword with the PreferTemplateDirectory, enter it as KEYWORDS:prefer=shortcutname where shortcutname is the name of the shortcut that is copied from the Template directory.
- In Studio, edit each application and change KEYWORDS:Prefer to KEYWORDS:prefer. Notice the lower case p. It doesn’t work with uppercase P.
- Configure your client devices to connect to the published desktop.
- When users connect to the published desktop, Group Policy Preferences will create shortcuts to local applications.
- Receiver will auto-launch and hopefully auto-login.
- If Receiver Self-Service Mode is disabled, all published applications should automatically appear in the Start Menu and Desktop.
- If Receiver Self-Service Mode is enabled then only applications with KEYWORDS:Auto and/or KEYWORDS:Mandatory in the published application description will be displayed. Users can open the systray icon to subscribe to more applications.
- For published applications with KEYWORDS:prefer=shortcutname, Receiver should copy icons from the template directory to the Start Menu and/or Desktop. See below for considerations.
- Users can copy icons from the Start Menu to the desktop. Make sure the user Copies the icon and doesn’t Move it.
- Users can then launch applications directly from the Start Menu, from the Desktop, or from the Receiver (if Self-Service interface is enabled).
- If a local shortcut (e.g. Group Policy Preferences shortcut, or copied from template directory) matches a published application with KEYWORDS:prefer then the local shortcut will override the published application icon.
- If the application is installed locally on the VDA then the local application shortcut should launch quickly. If the application is on a different delivery group then a second (double-hop) Citrix HDX/ICA connection will be established.
- If the user deletes Receiver shortcuts from the Start Menu, you can get them back by going to the systray icon and refreshing the applications. Or sometimes you have to reset Receiver.
Notes regarding Prefer Template Directory
- Prefer Template Directory can point to C:\ProgramData\Microsoft\Windows\Start Menu, which is the All Users Start Menu.
- The shortcuts copied from the Prefer Template Directory are renamed to match the published app name.
- For prefer local apps, any command line parameters specified in the published app are ignored. If you need these command line parameters, add them to the shortcut in the Prefer Template Directory.
- If you have multiple published apps pointing to the same prefer local shortcut, then only one copy will be made, and it will have the name of only one of the published apps. To workaround this, in the Prefer Template Directory, create separate shortcuts for each published app, and adjust the published app prefer keyword accordingly.
- Jan Hendrik Meier Automatic Shortcut generation for local installed applications in a Citrix XenDesktop / XenApp 7.x environment has a script that can create shortcuts based on the published apps with prefer keyword. These shortcuts can then be copied to your Prefer Template Directory.
How to Script/Automate Workspace app and Receiver Self-Service
From Citrix Knowledgebase article Driving the Citrix Receiver Self-Service Plug-in Programmatically: by default, Workspace app Self-Service (SSP) activities are driven by user interaction. However, SSP exposes sufficient information for its activities to be scripted.
When SSP builds a shortcut, it builds it to a small stub application in a file %appdata%\Citrix\SelfService\app-name-with-spaces-removed.exe for each resource. These files allow SSP to create a fake ‘install’ record for Add/Remove Software. Running these .exe files causes the application to launch. Note: Workspace app and Receiver 4.3.100 and newer don’t create stubs by default. To enable, set HKLM\Software\Wow6432Node\Citrix\Dazzle\AlwaysUseStubs (REG_SZ) = true.
If you want to drive SSP directly for launch instead of through an .exe stub, look at the keys under HKCU\Software\Microsoft\Windows\CurrentVersion\Uninstall. There will be keys in there named farm-name@@server-farm-name.app-friendly-name. In these keys you’ll find a LaunchString value that shows the relevant parameters. These parameters are user-independent and can therefore be cloned from a reference user to a general case. You can copy and reuse these parameters without interpretation.
Running the command selfservice.exe –init –ipoll –exit starts SSP, performs a refresh (interactive poll) from the current provider, and forces a clean exit.
Additional command line parameters are detailed at Driving the Citrix Receiver Self-Service Plug-in Programmatically.
Citrix Workspace app come with a .dll file that implements the Citrix Common Connection Manager SDK. You can use the CCM SDK to do the following:
- Launch Sessions
- Disconnect Sessions
- Logoff Sessions
- Get Session Information
Citrix was kind enough to develop a PowerShell module that calls functions from the .dll. Get the CCMPowershellModule from Github. The PowerShell module contains functions like the following:
- CCMTerminateApplication
- CCMLaunchApplication
- CCMGetActiveSessionCount
- CCMDisconnectAllSessions
Launcher Scripts
Ryan C Butler Storefront ICA file creator at Github. See Create an ICA File from Storefront using PowerShell or JavaScript for more info.
Stan Czerno – Powershell Script to launch one or more Published Applications from Citrix Storefront 2.x through 3.11: the script launches a browser, connects to StoreFront (or NetScaler Gateway), logs in, and launches an icon. This is a very well-written script that uses a .dll file from Citrix Workspace app to display session information.
Citrix Solutions Lab StoreFront Launcher Script at Github. It attempts to closely resemble what an actual user would do by:
- Opening Internet Explorer.
- Navigating directly to the Receiver for Web site or NetScaler Gateway portal.
- Completing the fields.
- Logging in.
- Clicking on the resource.
- Logging off the StoreFront site.
David Ott StoreFront App/Desktop Launch Testing Script uses Internet Explorer to login to StoreFront and launch a resource. Sends email with the result. Uses wficalib.dll to get session information.
Microsoft Teams
Citrix and Microsoft jointly support the delivery of Microsoft Teams from Citrix Virtual Apps and Desktops using optimization for Microsoft Teams. The Teams optimization components are built into VDA and Workspace app. There is no need to install anything separately. The feature is based on Browser Content Redirection so don’t exclude that feature when installing the VDA.
Microsoft Teams optimization/offloading requires the following:
- Newest version of Microsoft Teams machine-wide installation (ALLUSER=1)
- Newest version of Citrix VDA
- Newest version of Citrix Workspace app.
Feature matrix and version support at Citrix Docs shows the required versions of Teams, Citrix VDA, and Citrix Workspace app for various Teams features.
See Citrix Docs Optimization for Microsoft Teams.
Troubleshooting – Citrix QuickLaunch
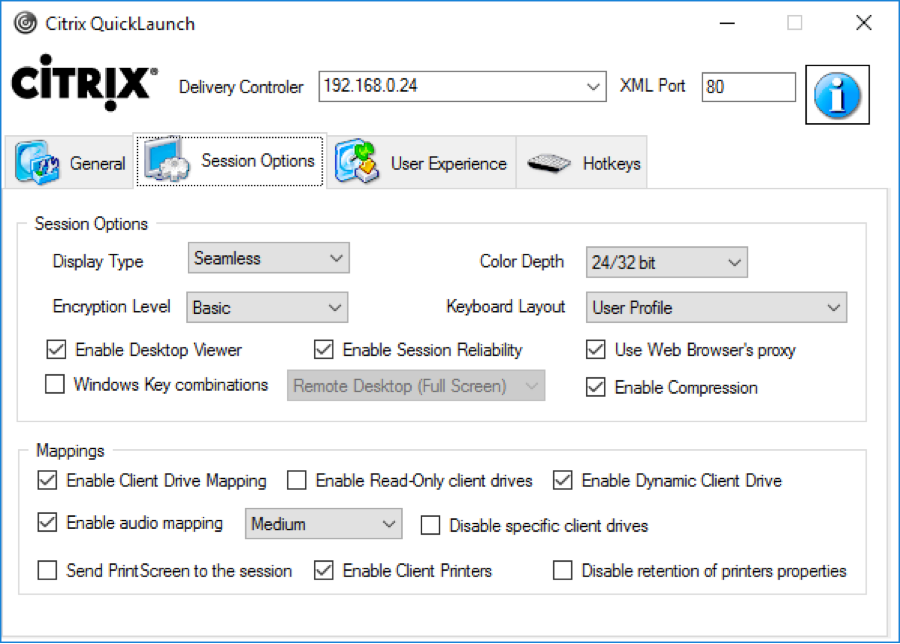
Citrix CTX219718 QuickLaunch Tool (Testing Application and Desktop Launch) lets you launch Citrix sessions directly from a Controller without needing StoreFront.
You enter a Controller address, credentials, and then it shows you the published resources. You can pick a resource, edit properties on the other tabs, and then Connect. This allows you to easily try different connection properties.
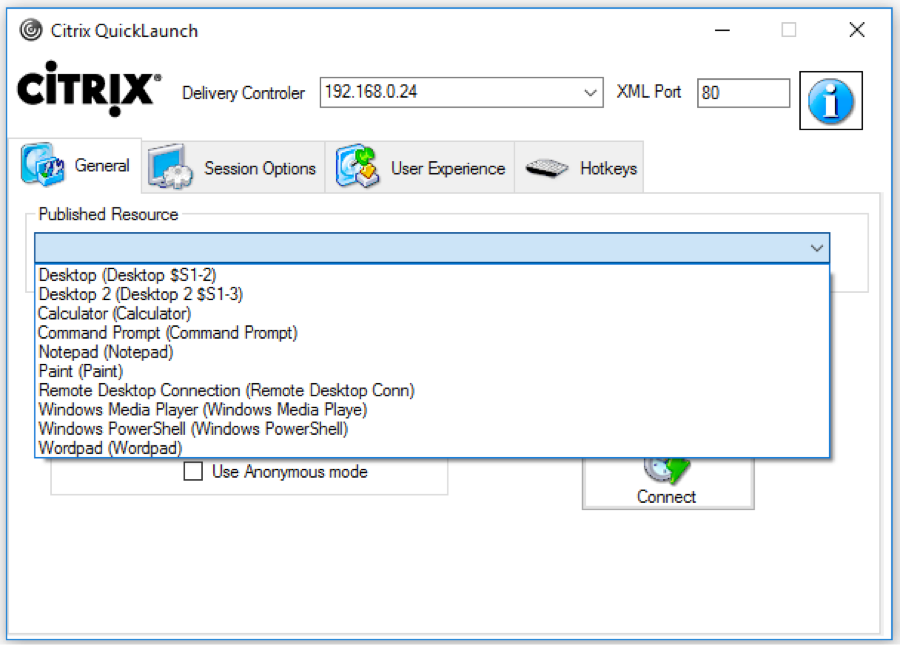
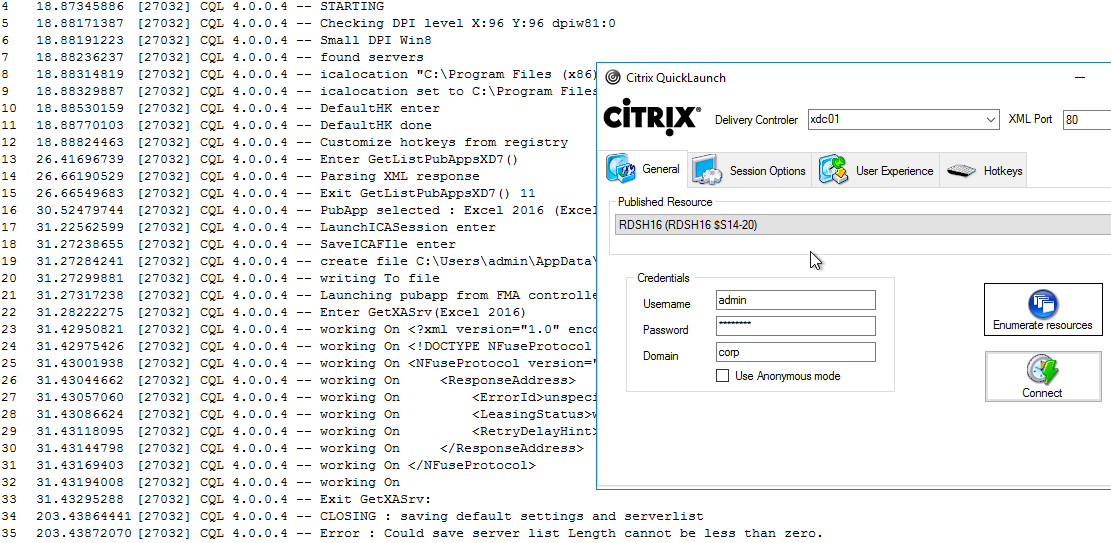
If you run into problems launching a session, use Sysinternals DebugView while running CQL in Debug mode (/debug switch).
Troubleshooting – Workspace app Logging
In Workspace app 2309 and newer, if you right-click the Workspace app icon in the system tray, there’s a Troubleshooting menu with a Collect Logs option.
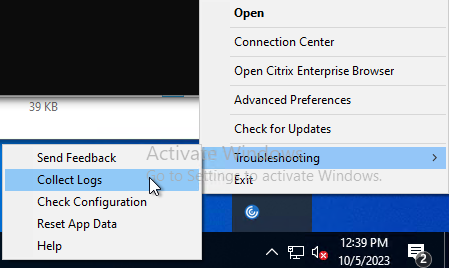
You can also access Log Collection from Advanced Preferences.
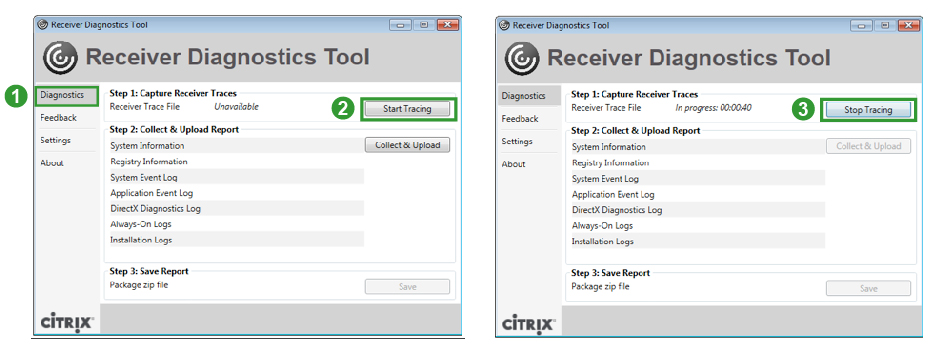
There are a couple methods of logging Workspace app for Windows operations. One method is CTX141751 Citrix Receiver Diagnostics Tool – For Windows, which creates a CDF trace that can be parsed by CDFControl.
Another method is CTX132883 How to Enable Logging on Receiver for Windows Using Registry Entries. The logfiles in %USERPROFILE%\Appdata\Local\Citrix\ are human readable. And CTX206102 Enable SSON Logging Using Registry Key.
Instead of creating the registry keys manually, you can use the following .reg file provided by Wolfgang Thürr:
Windows Registry Editor Version 5.00 ;only for x64 windows os ;import with admin rights ;restart your computer to activate the logging and tracing settings ;create C:\TEMP for the launch ICA log and SSON logn (no environment variables can be used) ;general Workspace app and Receiver logging ;************************ ;logpath: %USERPROFILE%\Appdata\Local\Citrix\Receiver [HKEY_LOCAL_MACHINE\SOFTWARE\ Wow6432Node\Citrix] " ReceiverVerboseTracingEnabled" =dword:00000001 ;Authentication Manager logging ;***************************** * ;logpath: %USERPROFILE%\Appdata\Local\ Citrix\AuthManager [HKEY_LOCAL_MACHINE\SOFTWARE\ Wow6432Node\Citrix\ AuthManager] "LoggingMode"="verbose" "TracingEnabled"="True" "SDKTracingEnabled"="True" ;Self Service logging ;******************** ;logpath: %USERPROFILE%\Appdata\Local\ Citrix\SelfService [HKEY_LOCAL_MACHINE\SOFTWARE\ Wow6432Node\Citrix\Dazzle] "Tracing"="True" "AuxTracing"="True" "DefaultTracingConfiguration"= "global all –detail" ;save launch ICA ;*************** ;logpath: C:\TEMP\ica.log (no environemnt variables allowed) [HKEY_LOCAL_MACHINE\SOFTWARE\ Wow6432Node\Citrix\ICA Client\Engine\Configuration\ Advanced\Modules\Logging] "LogConfigurationAccess"=" true" "LogConnectionAuthorisation"=" true" "LogEvidence"="true" "LogICAFile"="true" "LogFile"="C:\\TEMP\\ica.log" "LogStartup"="true" ;Receiver Always On Tracing ;************************** ;generates ETL Files for analyzing with CDFControl see CTX111961 for details ;can be configured or overruled by GPOs (icaclient.admx) ;path %USERPROFILE%\AppData\Local\ Temp\CTXReceiverLogs [HKEY_LOCAL_MACHINE\SOFTWARE\ Policies\Citrix\ICA Client\AoLog] "EnableTracing"=dword:00000001 ;Single Sign-on Logging ;************************** ;https://support.citrix.com/article/CTX206102 [HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Citrix\Install\SSON] "DebugEnabled"="true" "LogPath"="C:\\Temp"
Troubleshooting – Duplicate Stores
Stores are sometimes duplicated in Workspace app, especially if you are running Workspace app inside a VDA. (h/t Dan High)
StoreFront URLs can be defined in several places:
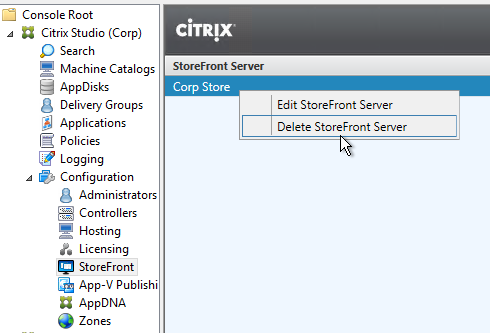
- In Studio, go to Configuration > StoreFront and delete all URLs configured here.
- Look in GPOs for Computer Configuration > Administrative Templates > Policies > Citrix Components > Citrix Workspace > StoreFront > NetScaler Gateway URL/StoreFront Accounts List. Remove any URLs configured here.
- In the client-side registry, at HKLM\Software\Wow6432Node\Citrix\Dazzle\Sites, you might see store addresses that were specified during a command line installation of Workspace app.
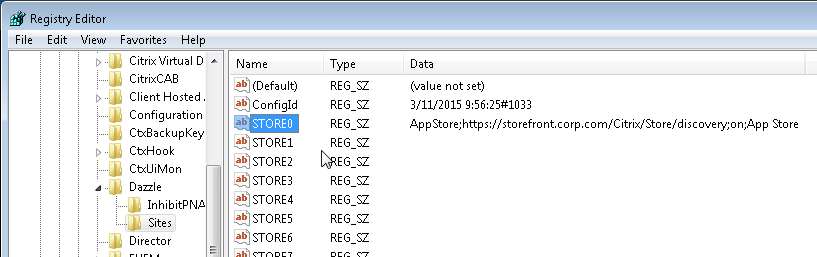
- When Citrix Workspace app switches between StoreFront servers in multiple datacenters, it’s possible for each datacenter to be treated as a separate Workspace app site. This can be prevented by doing the following. From Juan Zevallos at Citrix Discussions:
- Match the Base URL in all datacenters.
- Match the SRID in all datacenters – The SRID can be safely edited in the C:\inetpub\wwwroot\Citrix\Roaming\web.config. Make sure to propagate changes to other servers in the group.
- Match the Delivery Controller names under “Manage Delivery Controllers” – The XML brokers can be different, but the actual name of the Delivery Controller/Farm must be identical.
If you are running Workspace app on a VDA, once you’ve removed the configured URLs shown above, do the following to clean up the VDAs:
- On the VDA, HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Citrix – Delete the number folders representing policy entries.
- On session host VDAs, HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Terminal Server\Install\Software\Citrix – Remove the entries for storefront in the following folders.
- Under \receiver\ctxaccount delete all entries.
- Under \SR\Store delete the entries.
- On the VDA, C:\ProgramData\CitrixCseCache – Delete all files
- On the VDA, C:\ProgramData\Citrix\GroupPolicy – Delete all folders and files.
- Run gpupdate and logoff.
- In the user’s registry, HKEY_CURRENT_USER or the profile registry hive. Possible profile reset.
- Under Software\Citrix\Dazzle\Sites – Delete all entries.
- Under Software\Citrix\Receiver\ctxaccount – delete all entries.
- Under Software\Citrix\SR\Store – delete the entries.
- Verify no cached profile folders for user on server.
Hi Carl, My question is different from what you have up there. I have been tasked to configure vpn (Cisco ASA) connection with our storefront 3.5. I have successfully configured the vpn but I couldn’t get SSON to work. I tried the VPN connection with web Interface and the SSON worked fine. Do you know how to make it work with storefront.
Thanks in advance
What exactly is not working?
Is the client machine domain-joined? Do you get the list of apps? When launching an app, are you asked to login?
Excellent article Carl, you are the Heroo.
Please i want your advice. I configured SSO like above with enabled session prelaunch. It is working fine and establishing the prelaunch session only the first time i logon to windows or if i go manually to citrix receiver and refresh apps from there. I configured the parameter RefreshMs =60,000 (1minute) to refresh and prelaunch session after 1 minute if the session is closed but it is not working. I need help to program that periodic refresh. It seems that it is not working. I am using Citrix XenApp 7.6 FP3 with Citrix receiver 4.4.1.
Your advice will be highly appreciated.
Carl, How do i enable the Client Selective Trust in Linux OS 13.1 receiver installed on HP ThinPro
hi , i am having issues with Device Access Behavior (Client Selective Trust) when using windows 10; The option on the popup message to don’t ask me again disappeared.
“don’t ask me again” check box has diappered
Receiver 4.5?
Hi Carl,
I have an issue installing Citrix Receiver 4.4 LTSR.I am executing the silent installation with following command .
CitrixReceiver.exe” ADDLOCAL=”ReceiverInside,ICA_Client,SSON,AM,SELFSERVICE,USB,DesktopViewer,Flash,Vd3d,WebHelper” ALLOWADDSTORE=A ALLOWSAVEPWD=N ENABLE_SSON=Yes EnableCEIP=false DESKTOPDIR=”My Citrix Applications” /includeSSON /silent STORE0=”MyApps;https://myapps.abcd.com/Citrix/abcd/discovery;on;My Applications”
Application installs succcesfully,But after installation it prompt with login screen to enter the user name and password.Please Suggest how can i suppress that prompt in silent installation.I have tried with following parameter but no luck.
/SELFSERVICEMODE=False
PLease Suggest
Regards
Dinesh D
After installation, you logoff/logon so SSON works properly?
Or are you saying that it’s launching automatically after installation? If it’s installing as System, why would it launch for a user?
It is launching automatically after installation,I am executing it in the system context.Please suggest me the option.
If you rename it to CitrixReceiverWeb.exe, does that work?
Now i have removed STORE0=”MyApps;https://myapps.abcd.com/Citrix/abcd/discovery;on;My Applications” and used this parameter ./SELFSERVICEMODE=False .Now the applications works.
Thanks for your quick reply 🙂
Hello Carl,
My requirement is to place published applications shortcut placed on user desktop. I have followed the steps suggested by you and noticed that there’s no or Properties in the webconfig file on the storefront servers which are running 3.5 however i am able to locate the same on my storefront version 2.6
Could you please suggest what i need to modify on storefront version of 3.5.
Regards,
Shekhar Reddy.
I see it in my StoreFront 3.7 server. Edit “C:\inetpub\wwwroot\Citrix\Roaming\web.config”. Search for “
Hello Carl,
I am Curios on why the decided to allow us to add the NetScaler URL/Store in receiver now?
What is the advantage for domain join computers? Does the SSON now work through Netscalers?
PCI deployments where Citrix is deployed behind a firewall and hence NetScaler Gateway?
New issue: Receiver 4.5, Storefront 3.7 – setup to display icons on the desktop, like PnAgent, but some of the icon pictures are the Receiver icon (bullseye) instead of the application icon picture?
Same problem in older Receiver?
Can you post the question and screenshot to http://discussions.citrix.com?
Hi Carl,
I am trying to use “CitrixReceiver.exe Command line switches” for accessing the store via Remote access through Netscaler gateway. But it never popups the authentication. Looking at the wireshark, it does /Citrix//discovery (which we specified in the command line switch) and gets 302 (/vpn/index.html) found. Citrix receiver never progresses after getting this redirect from Netscaler.
This is working fine if I go directly to Storefront.
Isn’t it possible to use command line installation for remote access through netscaler? Kindly clarify if I have missed something.
Thanks
Bagavathi
Command line doesn’t work through Gateway. No idea why not.
Thanks Carl for your quick response.
Does this help?
https://twitter.com/_JasonSamuel/status/776115329453920258
Thanks Marco, this might help. I would try that.
Carl, if I right click the receiver icon in the tray and click open, receiver launches. I can click the + sign, click on an application, it puts the icon in the window, and I can launch the application. It just does not put the icons on the desktop like PNAgent.
This was fixed in newer versions of Receiver. Unless you configured Receiver to not put any icons on the desktop.
This is the command line I am using, but the client will not connect to WI.
citrixreceiver.exe” /ALLOWADDSTORE=A /includeSSON /STORE0=”PNAgent;https://citrix.bronsonhg.org/Citrix/PnAgent/config.xm
Maybe a copy/paste issue but the “l” is missing from “xml”.
It should work internally, but not externally. Does it work if you launch Receiver and type in the path manually?
Also, I think it should be the following:
/STORE0=”PNAgent;https://testserver.net/Citrix/PNAgent/config.xml;on;My PNAgent Site”
Carl, can you post the command line you used to install Receiver 4.x so it would work with Web Interface like PnAgent? Thanks.
It’s the same install. The only difference is that you point the store to https://MyWIServer/Citrix/PNAgent/config.xml instead of pointing it to a StoreFront Store.
Hi Carl!
In Citrix 4.5, I used to be able to launch apps from URL (change), automatically pass user credentials (self built exe) to Citrix WI. The Citrix app would then prompt only for RSA passcode before launching.
The functionally of launching apps from URL had been removed from Citrix 7.6 due to architecture change. I also cannot “save user password” in the receiver, if connecting from the internet via Netscaler Gateway. Is there a work around that allows to launch a Citrix app from a desktop shortcut using stored user Citrix credentials on the client’s PC and to be prompted only for RSA passcode? Many thanks!
Maybe something like this? https://www.czerno.com/Blog/post/2016/08/26/powershell-script-to-launch-one-or-more-published-applications-from-citrix-storefront-2-x-through-3-6
Thanks Carl! Unfortunately, very few clients are allowed to run PSS or can elevate privileges.
Hi Carl,
Ok something weird here I have moved this user to a different published server desktop win 2008 r2 in the same xenapp 7.8 environment. There are 2 published server desktops in the storefront one win 2008 r2 and the second win 2012 r2. The same user gets removed from one delivery group which has access to the win 2012 r2 (this is the one I can apply the policy but the prompt still comes up to the user) the other a win 2008 r2 delivery group this one has the same policy applied to the servers and delivery groups and is not being prompted for the file access permissions. ??Any thoughts
Hi Carl
So this would be the clients receiver correct and not the VDA server? At this time the policy is being applied to the VDA server win 2012 r2.
Receiver yes.
Sometimes you run Receiver on VDAs but only for double-hop.
Hi Carl ! Thanks for the info. I have a small problem by installing Citrix receiver through command line.
We are testing the Citrix Receiver upgrade through the command line.. Intially I noticed Add and Remove button is not available after upgrade. Then I added AllowAddstore parameter to the command as below.
CitrixReceiver.exe /silent /RCU /includeSSON ALLOWADDSTORE=A STORE0=”Name1;https:///Citrix//discovery;on;description” STORE1=”Name2;https:///Citrix//discovery;on;description”
Now installing using the above command I can see Add and Remove button. But only Add is active and the Remove button is grayed out. So seems like we can only add stores not remove the existing ones. As per Citrix article, AllowAddStore=S or A should enable users to add and remove stores if they need
Please help if I am missing any important command line parameters.
Also we faced issues like Duplicate Stores being created after using these command line and also the existing icons before upgrade getting grayed out. This is fixed only if we do Reset receiver settings after the upgrade, which i can do with the below command line.
“C:\Program Files (x86)\Citrix\ICA Client\SelfServicePlugin\CleanUp.exe” –cleanUser -silent
If you specify a store using command line or through GPO, then Receiver assumes it is administrator controlled and won’t allow it to be deleted.
One option is to clean the registry at HKLM\Software\Wow6432Node\Citrix\Dazzle\Sites and then reset Receiver.
Hi Carl
Is it possible to remove the email discovery option from the Receiver “Add Account” prompt when adding an account? The reason being is we have added a few new email domains to our organization and I don’t want to have to go through the process and cost of creating a new SAN cert with all the new domains as users are trying to add their accounts using the new domains and failing.
Cheers
I’m not aware of any way to remove it.
Ahhh duh very true. Thank u once again.
Ok thank u.
Why do I have to create new store?
Couldn’t I just use the same one?
Yes, but it would affect everybody using that store.
Carl
For some reason when I place apps on users desktop. Xendesktops icon is coming over as well. I only want applications on desktops. Not desktops on desktops. I have place app on users desktop enabled. So when the user signs in the launch their xendesktop session. The app appear on their desktop like it’s supposed to. But it’s showing xendesktop icons as well confusing them. Ever seen this?
You can create a separate store and filter desktops in that store – https://www.carlstalhood.com/storefront-3-5-tweaks/#hideapps
Hi Carl,
I am at a complete loss here… hoping you or someone else can lend a hand.
I have xenapp6.5 dishing out a financial application to 20 school districts…
We started with Receiver 4.4.1, using the same install script below to deploy receivers with pre-populated stores (PNA). (edited for post) Web Interface 5.4.0.59, Prompt, Direct Access, The server is part of a farm.
set CommandLineOptions=/silent ALLOWADDSTORE=A ALLOWSAVEPWD=A /STORE0=”Application;http:///Citrix/PNAgent/config.xml;on;DistrictName”
start /wait %DeployDirectory%\ReceiverCleanupUtility.exe /silent
REM
start /wait %DeployDirectory%\CitrixReceiver.exe DONOTSTARTCC=1 %CommandLineOptions%
REM
start regedit.exe /S citrixhttp.reg (this just allows authentication over port 80)
Endlocal
After the install, the workstation gets rebooted, and then the credentials are entered and the checkbox to save them is checked.
The district is connecting to a shared server where several other districts are connecting to use the same app… with the same configuration, and the same policies.
I’ve had them try 4.4.0 as well.. and 13.0 only to have the same behavior.
They did a fresh windows install from an iso(windows 7), applied windows updates, and installed citrix… same results with the random credential popups. (not on a domain – so that rules out group policy).
I’ve looked at traffic on both firewalls involved – no drops
I’ve been using the same scripted install on my windows 10 machine for 2 months now and have not come across the problem myself. I also have a Lab configured the same way here (with 10 stores on each machine), and they are not forgetting credentials…
Ideas?
Thank you so much, this site is a great resource!
I think I my have accidently edited out the line that says this problem is ONLY affecting one district out of all my deployments…
This is direct to Web Interface and not through NetScaler Gateway?
Any proxy server or other network filtering in that district?
direct access, no netscaler, no proxy, same firewall rules as other districts
I’ve posted in the Citrix Forums, and no help yet, So I thought I would ask here.
I’ve currently deployed Receiver 4.4.1000.16 (simple install enableSSON and silent) I then use GPO to configure Receiver using .admx to set Storefront Site:
[ Apps;https://storefront.domain.com/Citrix/Apps/discovery;on;Apps ]
I now need to change the Base URL for Storefront to citrix.domain.com
I can update the GPO and all new clients get the new site, but existing clients, no such luck….The GPO updates the HKLM policies path, but the user’s profile does not reflect this change.
Any Ideas? Is there a way to swap out the clients URL. How should this work with a large organization
Previous versions we used [ ConfigURL ]
There is a GPO setting in Receiver.admx under the StoreFront folder that lets you configure StoreFront URLs. It should be possible to change that. I tested it recently and it changed an existing config to a new config.
Otherwise, you’d have to remove the account and re-add it. One way is to run CleanUp -cleanUser http://support.citrix.com/article/CTX140149
Is it possible to make the icawrapper.msi the default install client from StoreFront? I’ve tried running the script to update the client location, but it does not seem to be applying.
I’ve never tried it. Does IIS MIME types allow .msi files?
We are enabling PNAgent look for Receiver 4.4 and putting an APP folder on the user’s XenApp 6.5 desktop. We did this with version 3.3 and 3.4. We install the client with these settings and it works in a basic environment. Our issue occurs because we redirect profiles and desktops to a network share. With redirection turned on the APP folder will not come up. But if I log on with an account that does not have redirection turned on then the APP folder does create. Any ideas on possible resolution for this?
Under Receiver Group Policy ADMX #2, you state: “If this folder doesn’t exist in SYSVOL, instead copy the .admx file to C:\Windows\PolicyDefinitions.”
Are you meaning if the Domain SySvol is not there (IE, non-domain joined laptop) or are you avoiding setting up the PolicyDefinitions folder (https://support.microsoft.com/en-us/kb/3087759) for some reason?
\\domain.com\sysvol\domain.com\Policies\PolicyDefinitions. If this folder exists, put the .admx file there. If this folder doesn’t exist, put it in local C: drive.
If you want it in sysvol, then you need to copy C:\Windows\PolicyDefinitions to sysvol. I wouldn’t do that without discussing it with the AD team.
Love the site – thank you for keeping up with the information You have helped with previous packaging and GPO creations. In regards to using the Receiver Cleanup Utility within SCCM, I’m wondering if you have best practice on RCU being a dependency for 4.3.100 deployment – what is a common detection method to detect the RCU, so the installation can continue with the install of 4.3.100? Thank you.
If you’re upgrading a Receiver that was originally installed as administrator, then in theory, you don’t need RCU. The hard part is upgrading Receivers that were installed by non-administrators.
Just FYI if anyone with same issue – was trying to package RCU as an Application using script, but there’s no standard reliable verification. It was much easier to create two separate Packages instead (the receiver and the RCU), test they work first, and then make a third to combine them with the RCU as first requirement. Now they can work as independents, or as one. We have multiple older installations over 1700 machines, and we are only approved to use 4.3.100.10, thanks to Imprivata not supporting 4.4 yet. Good luck.
hi carl, have you maybe a idea? i put it in the forum, but i was not sure, if i am the only one with this problem, or nobody use it as i, or whatever 🙁
—————
hi all
we have here a XenApp 7 Farm, and now we want Rollout the new Citrix Receiver 4 with SSON on the local PC’s from User. So all is looking good, every User have now a “Citrix Applications” Folder in there Startmenue where we deliver all Citrix Applications. New feature from Citrix is, that the Receiver hide the Applicatins in his Folder, when he see that a local Application is also installed, so let us make the example:
Acrobat Reader DC – installed on PC
Acrobat Reader DC – installed on Citrix XenApp7 Server
PC from User:
Acrobat Reader DC in Startmenue visible – yes
Acrobat Reader DC in Citrix Startmenue Folder visible – no
That is pretty cool function.
So i want make same now with all my Internet – Shortcuts and Applications what we can start from a network share. So i begin with creating a GPO where i put all my Shortcuts in. After i have finished i test in on my local PC. And voila it works as it should. All Shortcuts from GPO will create in Startmenue localy, and in the Citrix Startmenue, after reset Citrix Receiver, they dont show me again any Internet Shortcuts or Applications. PERFECT.
So i try it again on a other PC. And it will not work.
So what is different?
My PC was a Windows 7 – 32bit
Other PC was a Windows 7 – 64bit
So why Receiver makes all wright on a 32bit Machine, and on a 64bit System it will not hide Icons in the Citrix Startmenue??
Anyone a idea?
regards
frank
http://discussions.citrix.com/topic/379075-citrix-receiver-local-shortcuts-disable-in-citrix-startmenue/
Are the shortcuts pointing to C:\Program Files instead of C:\Program Files (x86)?
hi carl, my only design failure was in the GPO:
in the GPO – Shortcut Settings, you must set as “Location:Programs” and not “Location:Start Menu”
after change that, now i have wright Shortcuts on 32bit and 64bit Windows OS!
Hi Carl,
Thanks for the time you spend looking after this site, and the knowledge that you are sharing
We are trying to get a single-sign-on solution working, but having issues with the final connection to the desktop.
We have a XenDesktop 7.8 environment, StoreFront 3.5, Windows 7 with VDA7.8 – and Windows XP Client Machines with Receiver 4.2
Our StoreFront servers do not have an SSL cert installed and clients are connecting to a XenApp Services URL (we have some very old receiver clients on the network too, and have a task to update them all – so need to use the services URL)
We have set our brokers to trust requests sent to the xml ports
Our XP clients are configure with the includesson and allowaddstore=a settings so that they can connect to the http:// store
The receiver clients connect OK to the Store, authenticate seamlessly and can see the resources that we publish for them. When we start a desktop the broker passes off to the Win7 XenDesktop – but the Win7 XenDesktop doesn’t process the logon request and sits at the logon screen (presented to the client) – before the XenDesktop machine chops the connection off and reboots
Any ideas? If we don’t include the includeSSON setting in our install string, we get prompted for credentials by receiver, but can ultimately connect OK to the XenDesktop machine
Thanks in advance!
Paul
I seem to recall the newer Receivers not working properly on Windows XP. Try using real PNAgent instead (e.g. Receiver Enterprise 3.4).
Thanks Carl – we had issues with Receiver Enterprise 3.4 and dual monitors, applications would maximise over both screens as soon as we upgraded Web Interface to StoreFront.
Receiver 4.2 doesn’t give those errors for us – so 4.2 is preferred over 3.4, even if we can’t get single sign on working
Thanks, Paul
Carl, I am currently using Citrix Receiver 3.1 because the newer versions cause an issue (one of the program that are ran in the Citrix Platform freezes) My Citrix Receiver version 3.1 updates itself to the newest version on it’s own. I uninstall the newest version, reinstall 3.1, followed by the screwdrivers and approx. 1 week later the Citrix Receiver will be updated at some point in the middle of the night. Does anyone have any clue as to what would cause this to happen and can the receiver registry be altered to block the auto update and install?
Thank you,
Maybe this? http://discussions.citrix.com/topic/362289-citrix-receiver-updater-message/
“Can you post this to Citrix Discussions so the Citrix Product Managers can see it?” Where can I find it?? Harry
http://discussions.citrix.com
Hi Carl,
we found the answer for the Windows key behaviour with two monitors. It is a registry setting:
HKEY_LOCAL_MACHINE \SOFTWARE\Citrix\ICAClient\Engine\Lockdown Profiles\All Regions\Lockdown\Virtual Channels\Keyboard\ Open Key: TransparentKeyPassthrough Set the value to: Remote
Weird is that this setting is totally not necessary for the laptopscreen itself (when you only run Citrix on the laptop).
And also weird… it worked fine until the update of the receiver to the latest version, meaning, either the correct key has been removed by the update or the new receiver needs this registry key for this specific WIndows behaviour (which is weird again, because it is the default Windows behaviour that works fine on the internal laptop monitor).
Regards,
Harry
Can you post this to Citrix Discussions so the Citrix Product Managers can see it?
Carl, Thanks for all the work and support you offer the Citrix Community. I found an old forum post that helped me out. I thought you might want to add it to your list
http://discussions.citrix.com/topic/339324-domain-passthrough-method-when-authenticated-user-seeing-published-application-in-control-panel-program-and-features/
Added. Thanks.
I installed the latest Citrix Receiver (14.4.1000.16, while the installed one was probalby the 14.3…) on a user PC with two monitors. Now the user complains that the default Windows behaviour, jumping from one monitor to the other of moving the Citrix window from monitor 1 to 2, or displaying Citrix spread over the 2 monitors etc (I can hardly follow what the user does with the monitors, I am lucky to only have one monitor). Is there a way to control that sort of behaviour?
I’m not sure I understand the question. Did the user expand the published desktop to the two monitors? You do that by moving the desktop between the two monitors (partly on both of them) and maximize it.
Carl,
Do you know how to get the reciever to sso when the users go home? i was hoping to use a certificate for seamless two factor but seems that it only works via the web.. i hate to have my users von in and use there Citrix apps. We have trained our users to use the client mot the web. Any recommendations?
AFAIK the native Windows Receiver doesn’t support cert based authentication. It also doesn’t support external SSON. (Perhaps via SmartCard? I don’t know.)
But you still should have no problem at all, as long as you use Storefront. Storefront in combination with NetScaler Gateway and Receiver 4.x allows you to login in externally without using a Browser. Citrix Receiver discovers through Storefront Beacon configuration, that it is external and starts a PopUp for authentication. If you are internal or external makes no difference anymore. You always start your App Shortcuts. Internal you have SSON. External the Receiver gives you a prompt.
Hi Carl,
“5. When configuring Citrix Profile Management, make sure !ctx_startmenu! is not excluded. You can do one of the following: edit the Studio policy, edit the GPO, or edit the .ini file.”
This step needs to speed up enumerates apps?
Are the stubs use is faster then default mode on the receiver 4.4.x with disabled the selfservice mode?
Hi Carl,
Can i use reciever with SSON if i DONT have a storefront?
With Web Interface? Yes it works. It’s basically the same process.
Hi Carl.
I have installed latest receiver.
using xenapp 6.5 , enabled pass thru
have enabled single sign ON when installing client
have added servername.com to intranet zone, have checked Security/Internat/Custom/Auto login with current u/p
have set the following gpo’s http://i.imgur.com/7QvVyFB.png
*****
1.
if i start reciever app i see this: http://i.imgur.com/W4VRolo.png
i would assume this would use SSON?
If i open the citrix app i am prompted for a store even tho i have told that to be Suppressed via GPo ( Enable FTU)
If i manually set my server and manually login here and choose applications i see all my servers. http://i.imgur.com/YVYWhIp.png
My end goal is to have these “citrix desktop” added to desktop as a shortcut so users can just run it. Is this not possible without a store? I currently use the PNagent with the old online plugin to achieve this. .
2.
if i launch web interface i see this page . http://i.imgur.com/yM9pzmM.png
if i choose pass thru and logon it logs in with my credentials. If i then launch “citrix desktop” it will start.
How do i get this page to default to Pass Thru/.
Thanks in advance.
See http://discussions.citrix.com/topic/360337-citrix-receiver-42-passthru-with-webinterface-542x/#entry1862854
Hi mate, already had “PnaSSONEnabled”=”true” present, so reading last comment indicates this is not supported on my version of citrix.?
I thought I was able to get it to work using PNAgent. But I haven’t done Web Interface in quite a while. It’s not difficult to setup a StoreFront server.
Are you connecting using an https URL?
When adding the store, are you entering https://MyWebInterface.company.com/Citrix/PNAgent/config.xml
Hi, I am setting up XenApp/XenDesktop 7.7 with UPM with the VDA on Windows 10 Non-Persistent Desktops. I have the XenApp shortcuts coming through to the StartMenu (start menu not roamed) and am Pinning the shortcuts to the Taskbar. On logging back on to a new desktop, the shortcuts appear pinned but then when the apps are published to the desktop the pinned shortcut gets removed from the “User Pinned/Taskbar” folder and subsequently stops working. Non-XenApp Pinned shortcuts like IE/File Explorer roam fine. Have you ever managed to get XenApp shortcuts that are pinned to the Taskbar to roam on Non-Persistent Desktops before? Any help would be much appreciated.
I think I tried something similar in the past and saw the same behavior when Receiver refreshes the icons. Try posting your question to discussions.citrix.com.
The link to ThinKiosk doesn’t work anymore 🙂
Interesting. If I refresh the page, it works. I wonder if it’s a problem with the Referer header.
Carl,
These are great informationals that you are providing thank you. Regarding Device Access Behavior and assigning the file access response instead of the user being prompted.
I am running xenapp 7.8, the template has been added and configured as per instruction above. The policy has the vda in the scope of the policy and is running a server desktop of win 2008 r2. I have followed the steps in this portion enabling the client selective trust for intranet and when I login I still get prompted for access prompts. The policy is set and refreshed and when reviewing in policy resultant the settings show up. Have I missed something here?
Regards
Ray
What version of Receiver? I’ve seen issues with certain IE security zones. Not sure if it’s been fixed.
Hi Carl,
I should mention that I also made no access in all the other regions for all selections. The only region that was allowed any access was in Intranet. The receiver product version is 14.4.
Regards
Ray
Hi Carl,
The version of receiver is 14.4. I did end up having success on the VDA hosting win 2008 R2. I am now having the same issue when clients are accessing a hosted server desktop on win 2012 r2. VDA I have set up the key and access as per the article. You mention IE security zones maybe causing issues, can you be more specific so I can verify if this is the culprit? Are there known issues for this setup on a vda that is win 2012 r2?
Thanks
Ray
Hi Carl,
The following is an extract from the ctx article, the first line indicates to me that you can make the changes in the ADM template and it creates the required reg keys. Do you still need to import the key on the clients and make the changes?
In the ADM template there is the ‘Create Client Service Trust Key’ value, which can be used to automatically create all the required registry keys otherwise import registry keys first and make changes in registry values as explained and then apply ADM files and perform changes for ADM files. If you have applied ADM files first and then registry changes, there could be a possibility of continued unresolved issues. Using ADM files ONLY and not importing registry hive or making changes to registry values will not resolve the issue. Both steps are required and should be applied in the correct order: Step 1. Registry Hive, Step 2. ADM File.
It is also applicable for Citrix Receiver 4.x.
Thanks
Ray
I just use the ADM to create the registry keys.
Hi Carl,
Just so I am clear. If you use the ADM template and make the changes to the policy on the selected items like filesecuritypermission to full access as in the article and apply this policy to the VDA in my case a win 2012 r2 box hosting a server desktop. The user should not get a prompt? I have applied these changes with no success to each of the parts of the citrix client selective trust.
You apply the settings to whatever machine Receiver is running on.
Great article. Having downloaded the ADMX files from the receiver download page, and adding them to SYSVOL (central policy store)
I get the following error in policy editor, and no receiver options show as a result seemingly
“Policy presentation element ‘Part_SSL_SecurityComplianceMode’ in referenced presentation ‘Polcy_SSLLockdown’ does not exist.
FILE \\domain.com\SysVol\domain.com\Policies\PolicyDefinitions\receiver.admx, line 99, column 83”
anyone else hit this problem?
I’ve hacked the file a bit to no avail;
I just tried the templates for 4.4.1000 and it works. Did you copy the language file to the correct language folder? Do you maybe have conflicting files?
Thank you for confirming they should work
I found an old receiver.adml from either the 4.3 receiver or my original xenserver install disc, once I cleared it out all is well
thanks again
issues with getting the receiver admx templates to work, copied them to the correct locations on the DC< however my group policy manager still is trying to pull from local store and not central store, no citrix policies show up, any ideas?
Are you editing a domain GPO and not a local GPO?
when opening GP editor it says from the domain controller, FQDN, however at the administrative templates it says retrieved from local store
Is EnableLocalStoreOverride configured? https://support.microsoft.com/en-us/kb/2917033
Hi, Carl. Maybe you know. Are the Citrix Receiver 4.4.100 compatible with the Citrix Receiver Desktop Lock 4.4?
Not sure. But since it’s only an incremental upgrade, I assume it works. Let me know if it doesn’t work for you.
Hi Carl,
With XA 7.X (tried 7.6.300 and 7.8) and seamless published apps, if you CTRL+F1 and lock your session then Disconnect it, start a new published app the session is unlocked without the user ever entering his password. This wasnt the behavior in XA 6/6.5. Is there any setting in the receiver we can work with?
Browser? Or Receiver Self-Service?
Maybe configure lower timeouts for both so launching new icons requires authentication again.
We currently turn off the selfservice and turn on icons to desktop, I’ve tried with the selfservice tho, it has the same behavior. When you say lower timeouts, are you refering to this http://discussions.citrix.com/topic/347176-session-time-out-for-windows-receiver/ (your comment in particular).
It would still not prevent a user from stealing another’s session while he’s gone for a quick break, say 15 mins.
Typically the local device has it’s own lock screen timeout.
Does the same behavior occur in RDP RemoteApp?
If it used to work but now it doesn’t, you’d have to call Citrix Support to find out what happened.
But ultimately, there’s only so much technology can do. Users should be trained to not leave unlocked devices.
Yes I agree, thing is, most if not all of our clients use dumb thin clients not joined to the domain with auto logon. If they enter credentials it is in Citrix Receiver, local device timeout isnt configured.
Two things changed;
XA 7.6-7.8 vs 6.5
and the VDA is on 2012 R2 instead of 2008 R2.
If this is by design, I guess educating users to close Citrix Receiver (so it forgets the credentials) might be a solution.
Hi Carl
Im using Server 2008 R2 HSD – Xendesktop 7.6. We have repainting issues sometimes when moving windows, any hotfixes for it. I have tried the registry fixes for it but no difference.
http://support.citrix.com/article/CTX204071
Have you enabled Legacy Graphics Mode?
Is VDA 7.6.300 installed?
Hi Carl yes its been enabled but it still happens a little when moving some applications around. No I haven’t got 7.6.300.
Hi Carl,
maybe the wrong post to comment, but do you have any idea how to check on server’s side if the user has allowed access to local resources?
Thank you!
Best regards
Fabian
P.S. Keep up the great work. This page is way more useful than any other related to Citrix!
Maybe run a script as the user that tries to connect to \\client\c$.
I’m not sure what client drive mapping changes on the server side. Maybe you can find a registry key or something?
Hello, i have installed receiver 4.4 on a server with the citrix VDA. When a user logs on to the desktop he gets the following message from the citrix receiver 4.4: Your changes could not be saved due to an invalid configuration of the account XXX. After clicking OK verything is normal and i can start published applications on the desktop. Does anyone know about this error?
Maybe an issue with SSON? Or the Base URL is not https?
In Studio, did you create a StoreFront URL and assign it to the Delivery Group? I’m not a fan of that method.
sson is okay en de url is also https. I am also not a fan of the storefront url in the delivery group. It creates double icons for me….
after receiving this ‘error’ message i clicked advanced preferences on citrix receiver and clicked reset receiver. Now the message doesnt come up any more and me receiver is logged on in stead of logged off. The only strange thing is i cant do this on other servers because this option is not available….
Hi, Carl,
I follow your steps to configure store from GPO. After link GPO to the OU, I see Store in reg, but when i try login in VDI, the receiver show me pop up and ask me for email or store.
Can you help me?
Thanks
Maybe incorrect syntax? The Explain box should indicate the correct syntax.
Or maybe Reset Receiver first.
Hi Carl, I have used those GPO’s for app shortcuts and sometimes I get issues sometimes my start menu apps get duplicated and when I hit refresh on receiver it goes back to normal..
Secondly, my thin clients connect to a internal store which presents desktops and apps
Once I go to Citrix XenDesktop my receiver connects to the same store, I have self service enabled though and the app shortcuts go to start menu. I would like the published XenDesktops not to be shown and only the Apps? Any way to do that and will have any impact on that store?
You can create a separate store and hide Desktop icons in that store. https://www.carlstalhood.com/storefront-3-5-tweaks/#hideapps
hi i tried this already in StoreFront 3.0.44, I created a Store and used the customisation tool to hide desktop category and then pointed our existing windows gpo to point to the new store. After it pointed to the new store, the start menu was still the same and showed published desktops and apps?
Maybe because desktops are marked as favorites? Or the desktops have the keyword “TreatAsApp”? Did you verify that RFWeb to the new store hides the desktop icons?
Where do you check if Desktops are marked as favourites?
RFW did hide the store
Where do you check the keywords for Desktops in Studio? Right clicking the delivery group? I believe they don’t have that in though, but would like to check.
I found where it is but no TreatAsApp there..
What extacly is unstable? Just curious i dont have issues with this..
Hi again!
Tried to exclude AppData\Roaming\Citrix/SelfService for test server, and that broke app launch using stubs.. after exclusion the exe files did not get created in C:\Users\Users\AppData\Roaming\Citrix\SelfService.. strange..
Hi Carl.
Is it possible to have app shortcuts placed on desktop with SelfService enabled?
Thanks,
Rohit
In newer versions of Receiver, yes. When you publish your app, on the Delivery page there’s a checkbox to put the app on the desktop.
Or you can configure the client-side registry/GPO to put all shortcuts on the desktop. My Receiver article has that configuration.
Hi Carl,
Thank you for your quick response. I have already tried both the options above and as soon as I enable SelfService, the icons on the desktop become unusable. Any ideas?
Thanks,
Rohit
Hi Carl!
Thanks for great website with tons of great information!!
One question: We use appstubs for launching published apps inside published desktop.
Use shortcut like this:
C:\Users\%username%\AppData\Roaming\Citrix\SelfService\app.exe
– This works great!
Problem is that the UPM profile gets bloated with exe stub files..
Is it safe to exclude the selfservice folder in AppData\Roaming\Citrix.. ?
I have 1000x exe files for the same application… 😉
The stub files are supposed to speed up Receiver. Otherwise it has to re-create them at each launch. I’m curious why you have so many. Maybe a bug? Or maybe you’re excluding something else which is causing the stubs to stop working? But yes, I suspect you can exclude the stubs from roaming.
Also, there is some Stubs info at http://discussions.citrix.com/topic/374225-stub-executables-not-being-generated-by-latest-receiver-version/