Navigation
- Change Log
- Overview
- PowerShell Deploy Script Method – both upgrade and new
- vSphere Client Deploy OVF method – Upgrade Existing, or Deploy New
- Web-based Admin Interface
- Add UAG to Horizon Console
- Monitor Sessions
- Logs and Troubleshooting
- Load Balancing
- UAG Authentication – SAML, RADIUS
- Other UAG Configurations – High Availability, Network Settings, System Settings
💡 = Recently Updated
Change Log
- 2025 July 29 – updated Import OVF section for UAG 2503
- 2024 Jan 31 – SHA-1 thumbprint no longer supported. Replace with SHA-256 thumbprint (fingerprint).
- 2021 Sep 30 – Horizon Edge configuration – added instructions to disable CORS to fix HTML Access in Horizon 2106 and newer.
Overview
Unified Access Gateway provides remote connectivity to internal Horizon Agent machines. For an explanation of how this works (i.e., traffic flow), see Understand and Troubleshoot Horizon Connections at Omnissa Tech Zone.
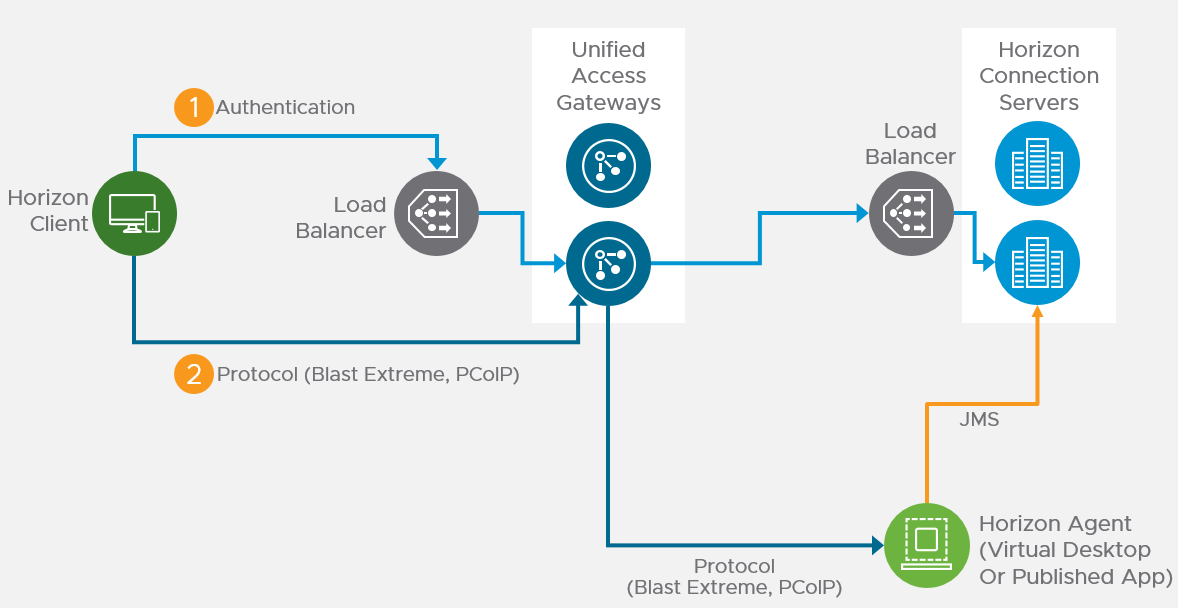
Unified Access Gateway (formerly known as Access Point) is a replacement for Horizon Security Servers. Advantages include:
- You don’t need to build extra Connection Servers just for pairing. However, you might want extra Horizon Connection Servers so you can filter pools based on tags.
- Between Unified Access Gateway and Horizon Connection Servers you only need TCP 443. No need for IPSec or 4001 or the other ports. You still need 4172, 22443, etc. to the View Agents.
- No need to enable Gateway/Tunnel on the internal Horizon Connection Servers.
- Additional security with DMZ authentication. Some of the Authentication methods supported on Unified Access Gateway are RSA SecurID, RADIUS, CAC/certificates, etc.
However:
- It’s Linux. You can deploy and configure the appliance without any Linux skills. But you might need some Linux skills during troubleshooting.
Horizon View Security Server has been removed from Horizon 2006 (aka Horizon 8).
- Some of the newer Blast Extreme functionality only works in Unified Access Gateway. See Configure the Blast Secure Gateway at Omnissa Docs.
More information at VMware Blog Post Technical Introduction to VMware Unified Access Gateway for Horizon Secure Remote Access.
Horizon Compatibility – Refer to the interoperability matrix to determine which version of Unified Access Gateway is compatible with your version of Horizon.
- The latest version of UAG is 2503.
- You usually want the Non-FIPS version.
- Then download the PowerShell deployment scripts on the same UAG download page.
- You usually want the Non-FIPS version.
Firewall
Omnissa Tech Zone Omnissa Horizon Blast Extreme Display Protocol, and Firewall Rules for DMZ-Based Unified Access Gateway Appliances at Omnissa Docs.
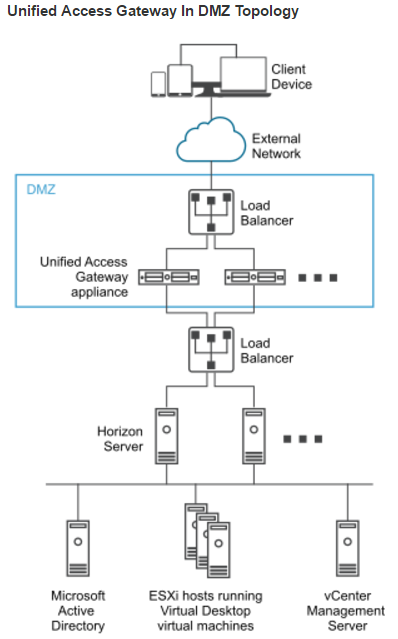
Open these ports from any device on the Internet to the Unified Access Gateway Load Balancer VIP:
- TCP and UDP 443
- TCP and UDP 4172. UDP 4172 must be opened in both directions. (PCoIP)
- TCP and UDP 8443 (for HTML Blast)
Open these ports from the Unified Access Gateways to internal:
- TCP 443 to internal Connection Servers (through a load balancer)
- TCP and UDP 4172 (PCoIP) to all internal Horizon View Agents. UDP 4172 must be opened in both directions.
- TCP 32111 (USB Redirection) to all internal Horizon View Agents.
- TCP and UDP 22443 (Blast Extreme) to all internal Horizon View Agents.
- TCP 9427 (MMR and CDR) to all internal Horizon View Agents.
Open these ports from any internal administrator workstations to the Unified Access Gateway appliance IPs:
- TCP 9443 (REST API)
- TCP 80/443 (Edge Gateway)
PowerShell Deploy Script
Omnissa Docs Using PowerShell to Deploy VMware Unified Access Gateway. The script runs OVF Tool to deploy and configure Unified Access Gateway. The PowerShell script is updated as newer versions of Unified Access Gateways are released. This is the recommended method of deploying Unified Access Gateway.
If you prefer to use vSphere Client to Deploy the OVF file, skip ahead to Upgrade or Deploy.
The PowerShell deployment script is downloadable from the UAG download page.
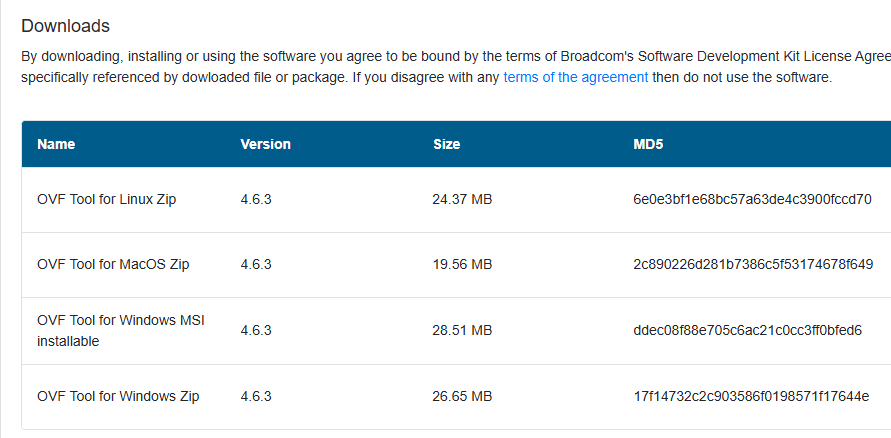
The PowerShell deploy script requires the OVF Tool:
- Download ovftool from Broadcom.
- On the machine where you will run the UAG Deploy script, install VMware-ovftool-…-win.x86_64.msi.
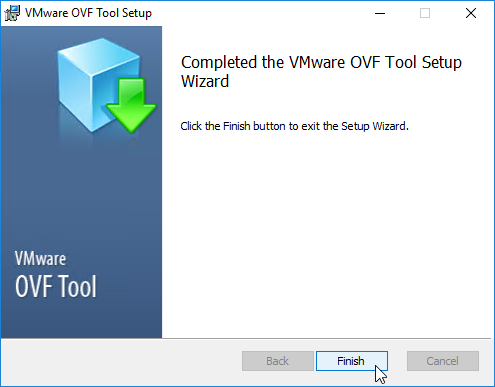
- In the Welcome to the VMware OVF Tool Setup Wizard page, click Next.
- In the End-User License Agreement page, check the box next to I accept the terms and click Next.
- In the Destination Folder page, click Next.
- In the Ready to install VMware OVF Tool page, click Install.
- In the Completed the VMware OVF Tool Setup Wizard page, click Finish.
Create or Edit a UAG .ini configuration file:
- Extract the downloaded uagdeploy PowerShell scripts for your version of Unified Access Gateway.
- If you have an existing UAG appliance, then you can download an INI of the configuration from the UAG Administrator page.
- Or copy and edit one of the downloaded .ini files, like uag2-advanced.ini.
- Or copy and edit one of the downloaded .ini files, like uag2-advanced.ini.
- A full explanation of all configuration settings can be found at Using PowerShell to Deploy Unified Access Gateway at Omnissa Docs.
- For any value that has spaces, do not include quotes in the .ini file. The script adds the quotes automatically.
- The name setting specifies the name of the virtual machine in vCenter. If this VM name already exists in vCenter, then OVF Tool will delete the existing VM and replace it.
- Add a uagName setting and specify a friendly name. You’ll later add this name to Horizon Console so you can view the health of the UAG appliance in Horizon Console.
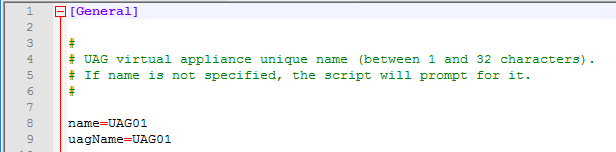
- You can optionally enable SSH on the appliance by adding sshEnabled=true.
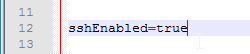
- For the source setting, enter the full path to the UAG .ova file.
- For the target setting, leave PASSWORD in upper case. Don’t enter an actual password. OVF Tool will instead prompt you for the password.
- For the target setting, specify a cluster name instead of a host. If spaces, there’s no need for quotes. For example:
target=vi://admin@corp.local:PASSWORD@vcenter02.corp.local/Datacenter/host/Cluster 1
- Specify the exact datastore name for the UAG appliance.
- Optionally uncomment the diskMode setting.
- For a onenic configuration (recommended), set the netInternet, netManagementNetwork, and netBackendNetwork settings to the same port group name.
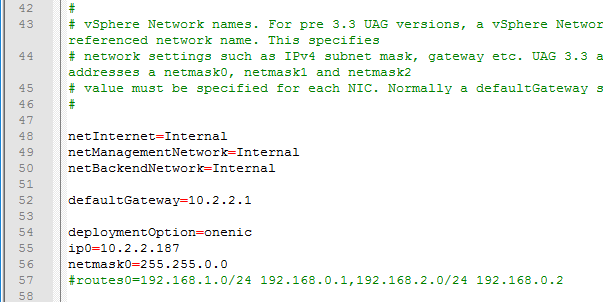
- Multiple dns servers are space delimited.
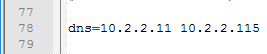
- For pfxCerts, UNC paths don’t work. Make sure you enter a local path (e.g. C:\). OVA Source File can be UNC, but the .pfx file must be local.
- There’s no need to enter the .pfx password in the .ini file since the uagdeploy.ps1 script will prompt you for the password.
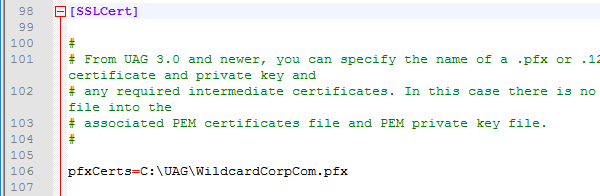
- proxyDestinationUrl should point to the internal load balancer for the Horizon Connection Servers.
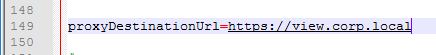
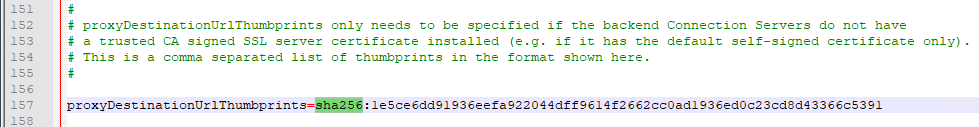
- For proxyDestinationUrlThumbprints, paste in the sha256 or higher thumbprint of the Horizon Connection Server certificate in the format shown.
- If your Horizon Connection Servers each have different certificates, then you can include multiple thumbprints (comma separated).
- Make sure there’s no hidden character between sha256 and the beginning of the thumbprint. Or you can just paste the thumbprint without specifying sha256. Note: sha1 is no longer supported. Edge and Chrome can show sha256 certificate fingerprint.
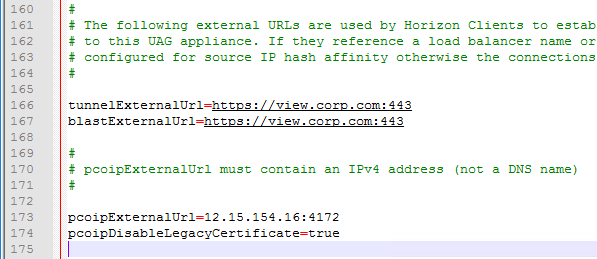
- Change the ExternalUrl entries to an externally-resolvable DNS name and a public IP address. For multiple UAGs, the FQDNs and public IP address should resolve to the load balancer. Note: your load balancer must support persistence across multiple port numbers (443, 8443, 4172).
When you run the PowerShell script, if the UAG appliance already exists, then the PowerShell script will replace the existing appliance. There’s no need to power off the old appliance since the OVF tool will do that for you.
- Open an elevated PowerShell prompt.
- Paste in the path to the uagdeploy.ps1 file. If there are quotes around the path, then add a & to the beginning of the line so PowerShell executes the path instead of just echoing the string.
- Add the -iniFile argument and enter the path to the .ini file that you modified. Press <Enter> to run the script.
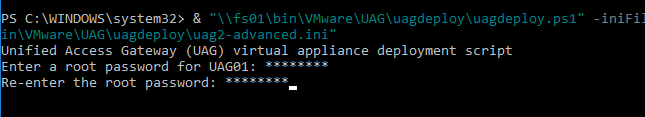
- You’ll be prompted to enter the root password for the UAG appliance. Make sure the password meets password complexity requirements.
- You’ll be prompted to enter the admin password for the UAG appliance. Make sure the password meets password complexity requirements.
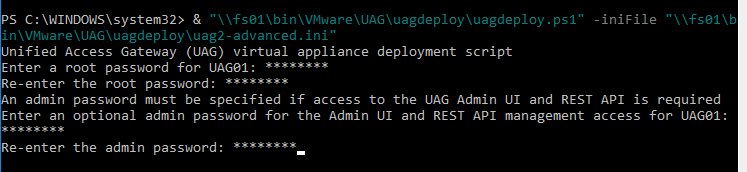
- For CEIP, enter yes or no.
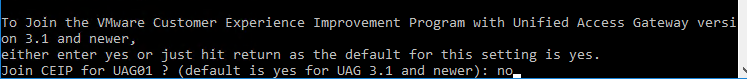
- For .pfx files, you’ll be prompted to enter the password for the .pfx file. Note: the .pfx file must be local, not UNC.
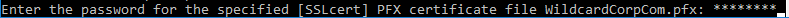
- OVF Tool will prompt you for the vCenter password. Special characters in the vCenter password must be encoded. Use a URL encoder tool (e.g., https://www.urlencoder.org/) to encode the password. Then paste the encoded password when prompted by the ovftool. The UAG passwords do not need encoding, but the vCenter password does.
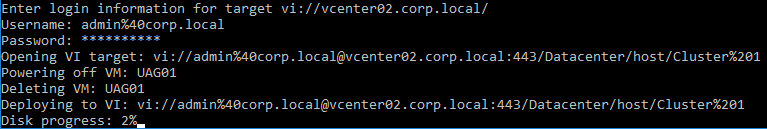
- The deploy script will display the IP address of the powered on UAG appliance.
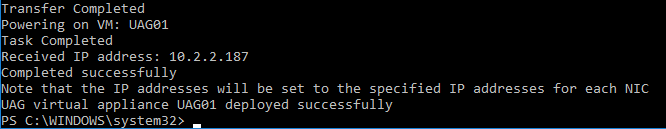
- Review settings in the UAG admin interface.
- Add the new UAG appliance to Horizon Console.
Upgrade
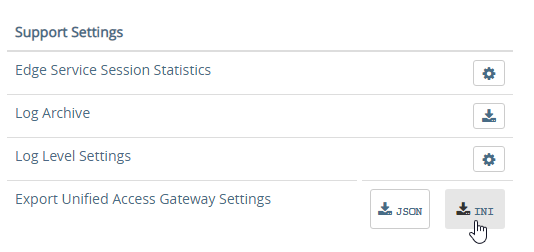
To upgrade from an older appliance, you delete the old appliance and import the new one. Before deleting the older appliance, export your settings:
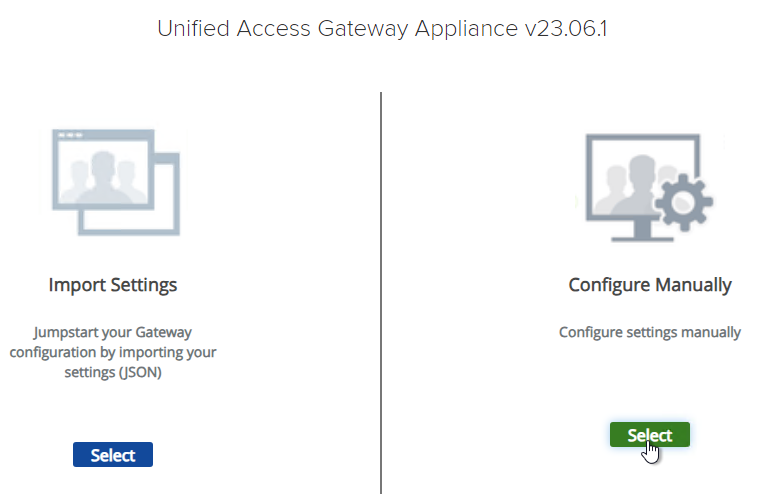
- Login to the UAG at https://<Your_UAG_IP>:9443/admin/index.html.
- In the Configure Manually section, click Select.
- Scroll down to the Support Settings section, and then click the JSON button next to Export Unified Access Gateway Settings.
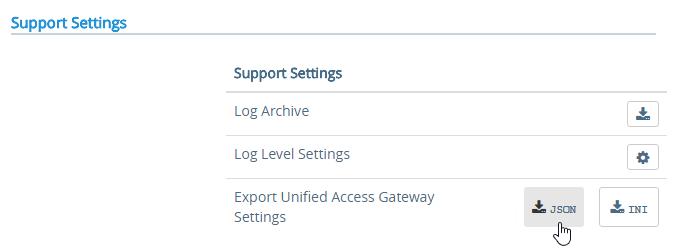
- Note: the exported JSON file does not include the UAG certificate, so you’ll also need the .pfx file. If RADIUS is configured, then during import you’ll be prompted to enter the RADIUS secret.
Deploy New
Horizon Compatibility – Refer to the interoperability matrix to determine which version of Unified Access Gateway is compatible with your version of Horizon.
- The latest version of UAG is 2503.
- You usually want the Non-FIPS version.
- You usually want the Non-FIPS version.
To deploy the Unified Access Gateway using VMware vSphere Client:
- If vSphere Client, right-click a cluster, and click Deploy OVF Template.
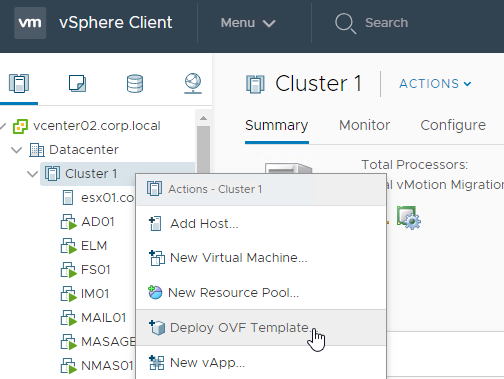
- Select Local File and click Upload Files. In the Open window, browse to the downloaded euc-unified-access-gateway.ova file, and click Next.
- In the Select a name and folder page, give the machine a name, and click Next.
- In the Review Details page, click Next.
- In the Select configuration page, select a Deployment Configuration. See Network Segments at Unified Access Gateway Architecture at Omnissa Tech Zone. Click Next.
- In the Select storage page, select a datastore, select a disk format, and click Next.
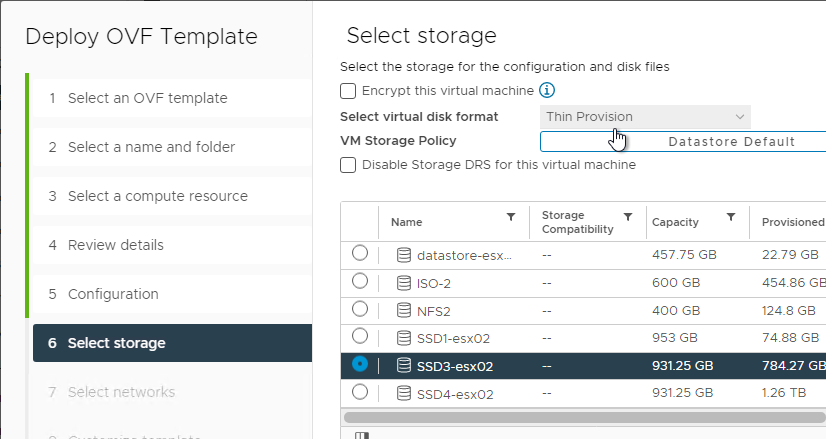
- In the Select networks page, even if you select Single NIC, the OVF deployment wizard asks you for multiple NICs. UAG typically goes in the DMZ.
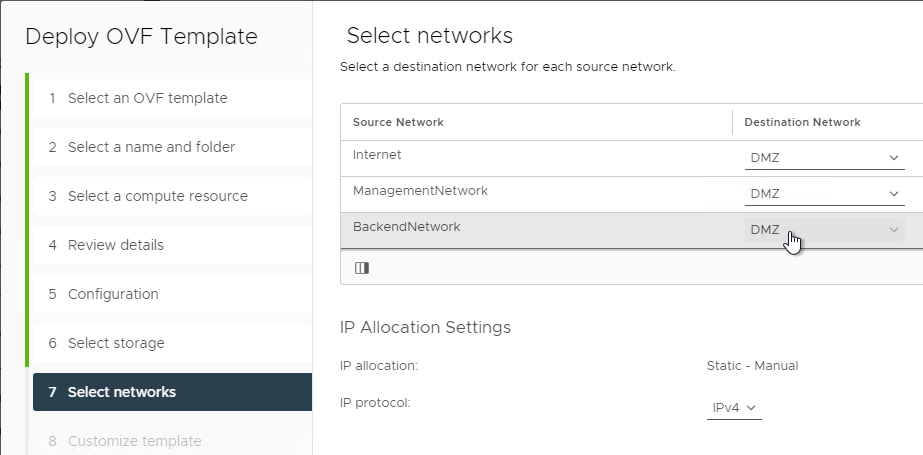
- In the Customize template page, select STATICV4, and scroll down.
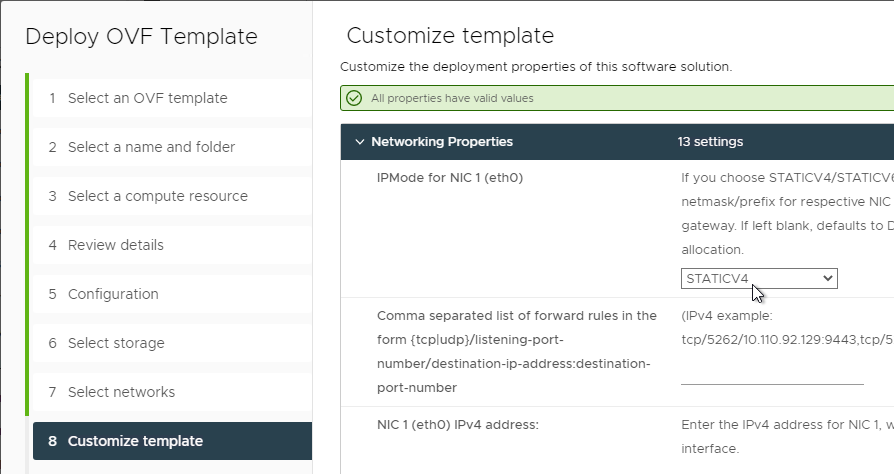
- In the NIC1 (eth0) IPv4 address field, enter the NIC1 (eth0) IPv4 address. Scroll down.
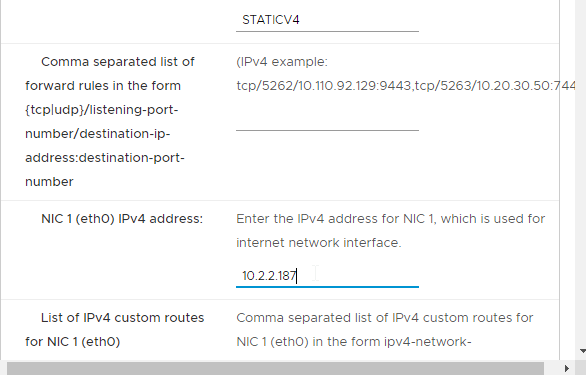
- Enter DNS addresses, Gateway, and Subnet Mask. Scroll down.
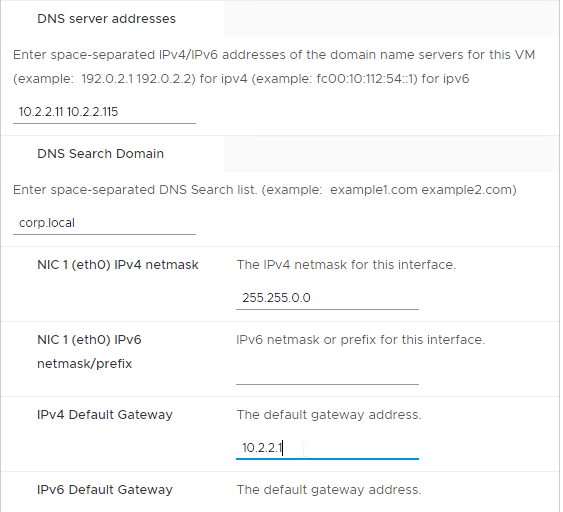
- Scroll down and enter more IP info.
- Scroll down.
- Enter a Unified Gateway Appliance Name.
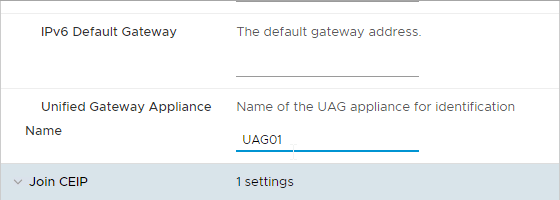
- Scroll down.
- UAG 2207 and newer let you specify the local root username.
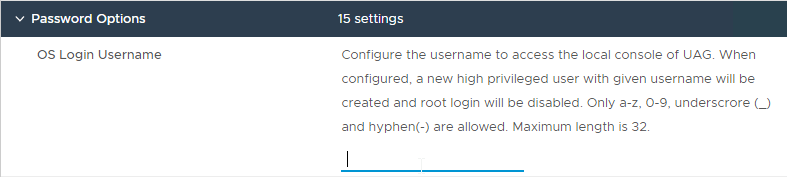
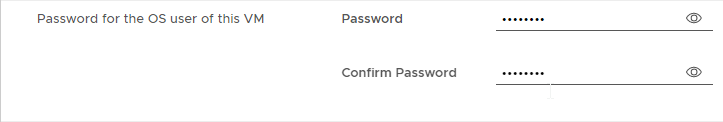
- Enter passwords.
- UAG 20.12 (2012) and newer let you specify Password Policy settings when deploying the OVF.
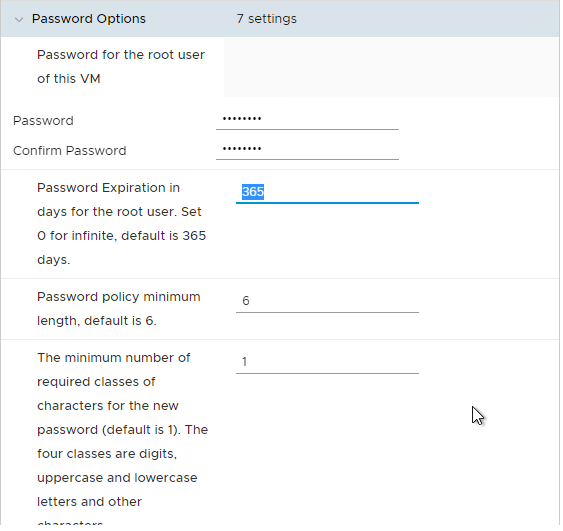
- UAG 20.12 (2012) and newer let you specify Password Policy settings when deploying the OVF.
- Scroll down and enter the password for the admin user.
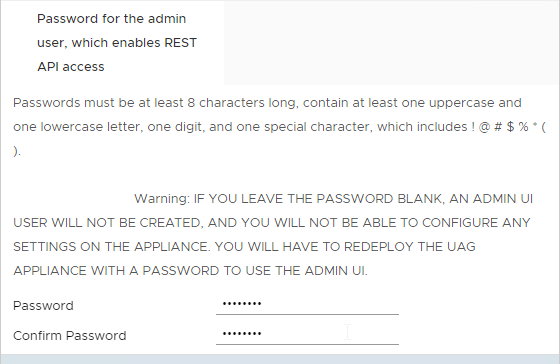
- UAG 2207 and newer have an adminreset command if you mess up the admin interface login. There’s also an adminpwd command to reset the password.
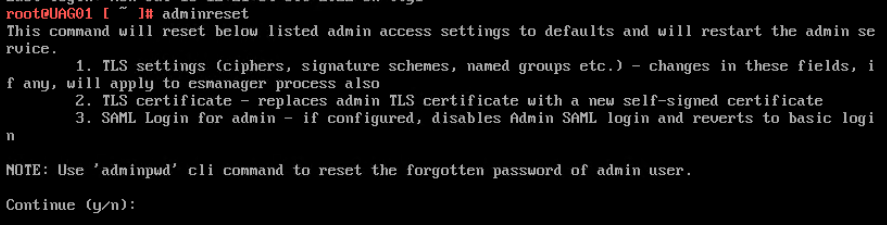
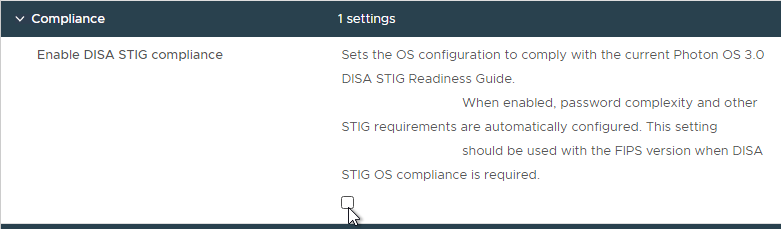
- UAG 2207 and newer have an option to enable DISA STIG compliance, usually on the FIPS version of UAG.
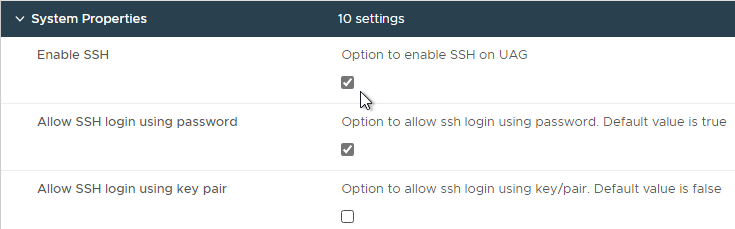
- There’s a checkbox for Enable SSH.
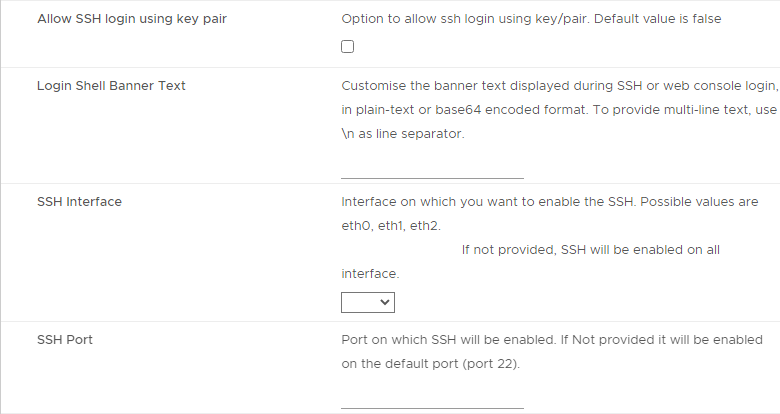
- In UAG 3.9 and newer, there’s an option to login using a SSH key/pair instead of a password.
- Newer versions of UAG have more SSH options.
- UAG 2207 adds Commands to Run on First Boot or Every Boot.
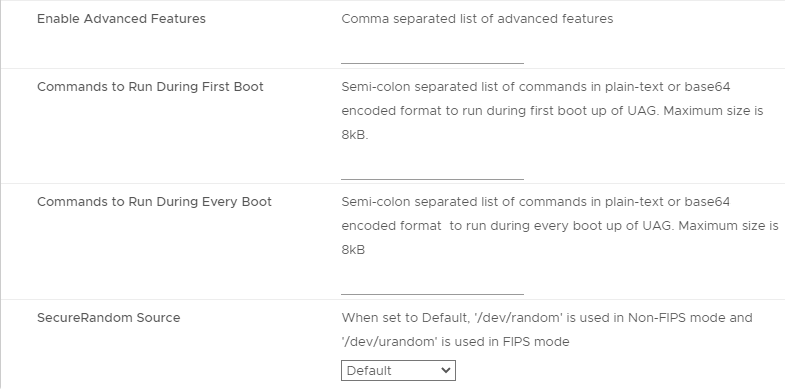
- Click Next.
- In the Ready to complete page, click Finish.
UAG Admin Interface
- Power on the Unified Access Gateway appliance.
- Point your browser to https://My_UAG_IP:9443/admin/index.html and login as admin. It might take a few minutes before the admin page is accessible.
- UAG 2207 and newer have an adminreset command if you mess up the admin interface login. There’s also an adminpwd command to reset the password.

Import Settings
- If you have previously exported settings, you can import it now by clicking Select in the Import Settings section.
- Browse to the previously exported UAG_Settings.json file and then click Import. Note that this json file might have old settings, like old ciphers. Review the file to ensure you’re not importing legacy configurations. If the .json file has a SHA-1 thumbprint, then edit the file and replace it with SHA-256 thumbprint (fingerprint).
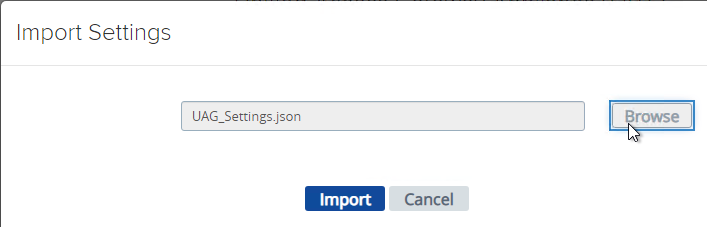
- It should say UAG settings imported successfully. If you don’t see this, then your .json file probably has a SHA-1 thumbprint.
- Press <F5> on your keyboard to refresh the browser.
- The .json file does not include the certificate so you’ll have to do that separately. In the Admin console, in the Advanced Settings section, click TLS Server Certificate Settings.
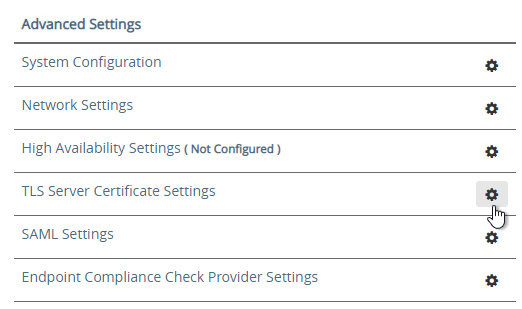
- Check the box next to Internet Interface. Optionally uncheck the box next to Admin Interface.
- Change the drop-down for Certificate Type to PFX.
- In the row Upload PFX, click Select and browse to your PFX file.
- In the Password field, enter the PFX password and then click Save.
Configure Horizon Settings
- To manually configure the appliance, under Configure Manually, click Select.
- Click the slider for Edge Service Settings.
- Click the gear icon for Horizon Settings.
- Click the slider for Enable Horizon.
- As you fill in these fields, hover over the information icon to see the syntax.
- The Connection Server URL should point to the internal load balanced DNS name (URL) for your internal Connection Servers.
- For the Connection Server URL Thumbprint, get the thumbprint from the internal Horizon certificate. Point your browser to the internal Horizon Connection Server FQDN (load balanced) and click the padlock icon to open the certificate.
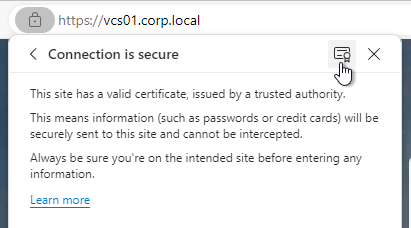
- On the Details tab, copy the SHA-256 Fingerprint. Note that SHA-1 thumbprint is no longer supported.
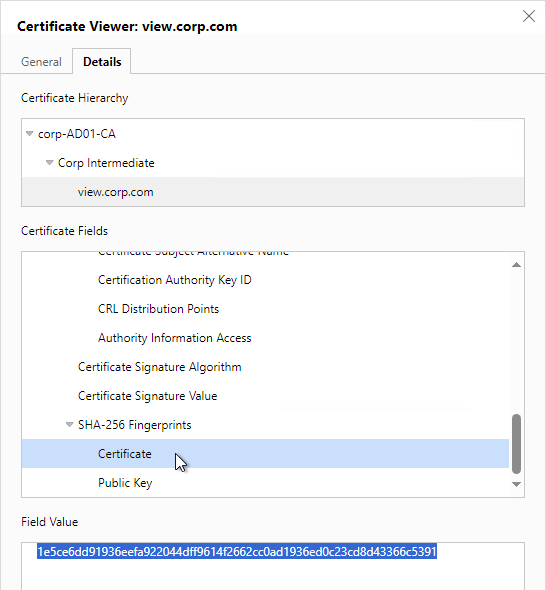
- For the Connection Server URL Thumbprint, get the thumbprint from the internal Horizon certificate. Point your browser to the internal Horizon Connection Server FQDN (load balanced) and click the padlock icon to open the certificate.
- In the Proxy Destination URL Thumb Prints field, type in
sha256=and paste the certificate thumbprint. - At the beginning of the Thumbprint field, immediately after the equals sign, there might be a hidden character. Press the arrow keys on the keyboard to find it. Then delete the hidden character.
- Enable the three PCOIP, Blast, and Tunnel Gateways and perform the following configurations:
- For PCOIP External URL, enter the external IP and
:4172. The IP should point to your external load balancer that’s load balancing UDP 4172 and TCP 4172 to multiple Unified Access Gateways. - For Blast External URL, enter https://<FQDN>:8443 (e.g. https://view.corp.com:8443). This FQDN should resolve to your external load balancer that’s load balancing UDP 8443 and TCP 8443 to multiple Unified Access Gateways.
- You could change the Blast port to 443 but this would increase CPU utilization on UAG. See Omnissa 78419 Unified Access Gateway (UAG) high CPU utilization.
- Link: Troubleshooting Blast at Omnissa Discussions
- For Enable UDP Tunnel Server, enable the setting.
- For Tunnel External URL, enter https://<FQDN>:443 (e.g., https://view.corp.com:443). This FQDN should resolve to your external load balancer that’s load balancing TCP 443 to multiple Unified Access Gateways.
- The external load balancer must be capable of using the same persistence across multiple port numbers. On NetScaler, this feature is called Persistency Group. On F5, the feature is called Match Across.
- For PCOIP External URL, enter the external IP and
- Then click More.
- Unified Access Gateway has a default list of paths it will forward to the Horizon Connection Server. You can edit the Proxy Pattern and add
|/downloads(.*)to the list so that users can also download Horizon Clients that are stored on your Horizon Connection Servers as detailed elsewhere at carlstalhood.com. Make sure you click Save at least once so it saves the default Proxy Pattern. Then go back in and add|/downloads(.*)to the end of the Proxy Pattern but inside the last parentheses. In UAG 2406, the default Proxy Pattern looks something like below:
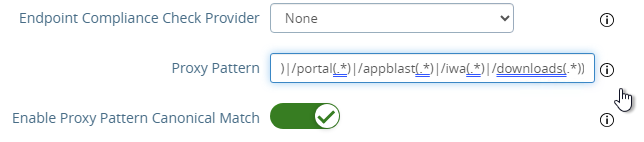
(/|/view-client(.*)|/portal(.*)|/appblast(.*)|/iwa(.*)|/downloads(.*))
- Scroll down and click Save when done.
- If you click the arrow next to Horizon Settings, then it shows you the status of the Edge services. It might take a minute or two to start working.
- In your Horizon Connection Servers, the Secure Gateways (e.g. PCoIP Gateway) should be disabled.
- Go to Horizon Console.
- Expand Settings and click Servers. On the right, switch to the tab named Connection Servers. Highlight your Connection Servers and click Edit.
- Then uncheck or disable all three Tunnels/Gateways.
- HTML Access probably won’t work through Unified Access Gateway. You’ll probably see the message Failed to connect to the Connection Server.
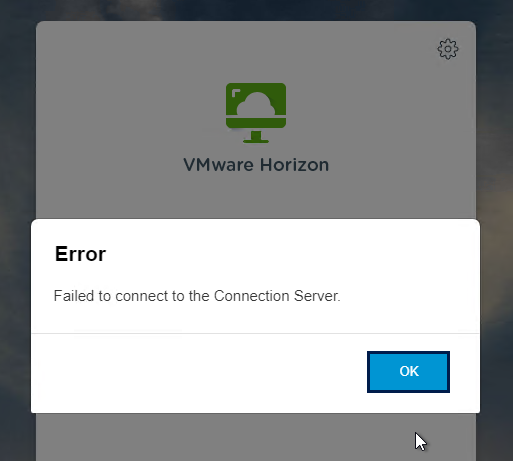
- To fix this, configure on each Connection Server the file C:\Program Files\Omnissa\Horizon\Server\sslgateway\conf\locked.properties (or C:\Program Files\VMware\VMware View\Server\sslgateway\conf\locked.properties) to disable Origin Check (checkOrigin=false) or configure the Connection Server’s locked.properties with the UAG addresses. Also see 2144768 Accessing the Horizon View Administrator page displays a blank error window in Horizon 7.
- Horizon 2106 and newer enable CORS by default so you’ll need to either disable CORS by adding enableCORS=false to C:\Program Files\Omnissa\Horizon\Server\sslgateway\conf\locked.properties (0r C:\Program Files\VMware\VMware View\Server\sslgateway\conf\locked.properties) or configure the portalHost entries in locked.properties as detailed at 85801 Cross-Origin Resource Sharing (CORS) with Horizon 8 and loadbalanced HTML5 access.
- After modifying the locked.properties file, restart the Omnissa Horizon Secure Gateway (or VMware Horizon View Security Gateway Component) service.
Add UAG to Horizon Console
In Horizon 7.7 and newer, you can add UAG 3.4 and newer to Horizon Console so you can check its status in the Dashboard.
- In UAG Admin console, under Advanced Settings, click the gear icon next to System Configuration.
- At the top of the page, change the UAG Name to a friendly name. You’ll use this case-sensitive name later.
- Click Save at the bottom of the page.
- In Horizon Administrator Console, on the left, expand Settings and click Servers. On the right, switch to the tab named Gateways. Click the Register button.
- In the Gateway Name field, enter the case-sensitive friendly name you specified earlier, and then click OK.
See status of UAG appliances:
- Use a Horizon Client to connect through a Unified Access Gateway. Horizon Console only detects the UAG status for active sessions.
- In Horizon Console 7.10 and newer, to see the status of the UAG appliances, on the top left, expand Monitor and click Dashboard.
- In the top-left block named System Health, click VIEW.
- With Components highlighted on the left, on the right, switch to the tab named Gateway Servers.
- This tab shows the status of the UAG appliances, including its version. If you don’t see this info, then make sure you launch a session through the UAG.
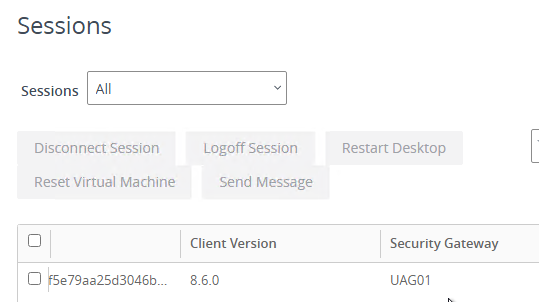
To see the Gateway that users are connected to:
- In Horizon Console 7.10 or newer, go to Monitor > Sessions.
- Search for a session and notice the Security Gateway column. It might take a few minutes for it to fill in.
UAG Authentication
SAML is configured in UAG 3.8 and newer in the Identity Bridging Settings section.
- Upload Identity Provider Metadata.
- Then in UAG Admin > Edge Service Settings > Horizon Settings > More (bottom of page), you can set Auth Methods (near top of page) to SAML only, which requires True SSO implementation, or SAML and Passthrough, which requires two logins: one to IdP, and one to Horizon.
- For complete True SSO instructions, see https://www.carlstalhood.com/vmware-horizon-true-sso-uag-saml/.
- For Okta and True SSO, see Enabling SAML 2.0 Authentication for Horizon with Unified Access Gateway and Okta: VMware Horizon Operational Tutorial at Omnissa Tech Zone.
- For Azure MFA, see Sean Massey Integrating Microsoft Azure MFA with VMware Unified Access Gateway 3.8.
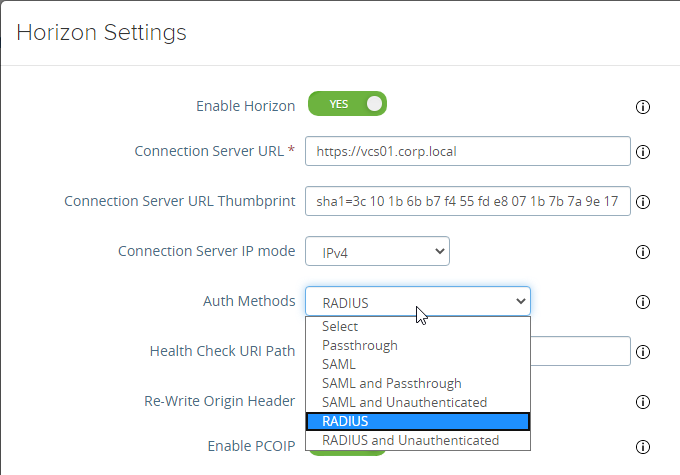
For RADIUS authentication:
- Enable the Authentication Settings section and configure the settings as appropriate for your requirements. See Configuring Authentication in DMZ at VMware Docs.
- When configuring RADIUS, if you click More, there’s a field for Login page passphrase hint.
- When configuring RADIUS, if you click More, there’s a field for Login page passphrase hint.
- Then in Edge Service Settings > Horizon Settings > More (bottom of page), you can set Auth Methods (near top of page) to RADIUS.
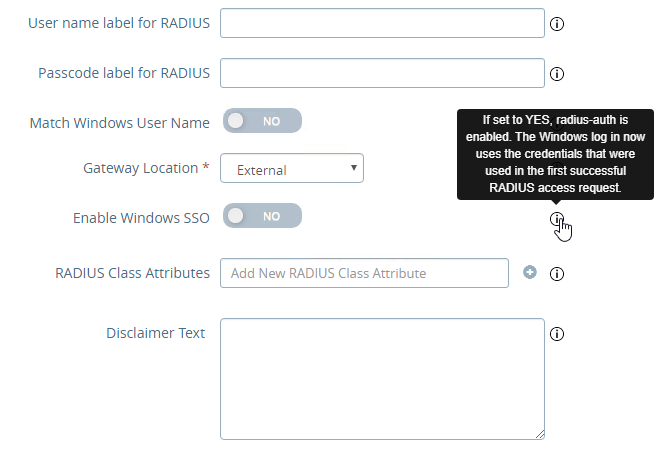
- If you scroll down the Horizon Settings page, you’ll see additional fields for RADIUS.
- In UAG 3.8 and newer, Passcode label field can be customized for MFA providers like Duo.
- If your RADIUS is doing Active Directory authentication (e.g. Microsoft Network Policy Server with Azure MFA), then Enable Windows SSO so the user isn’t prompted twice for the password.
Other UAG Configurations
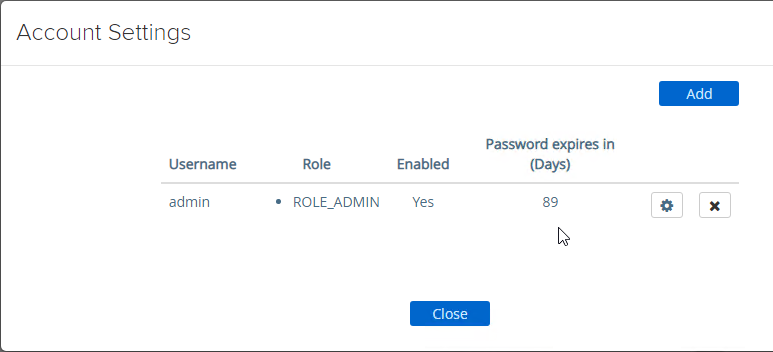
- UAG 3.8 and newer shows when the admin password expires in Account Settings in the Advanced Settings section.
- Ciphers are configured under Advanced Settings > System Configuration.
- The default ciphers in UAG 2412 are the following and include support for TLS 1.3.
TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256,TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384,TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305_SHA256,TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384,TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256,TLS_AES_128_GCM_SHA256,TLS_AES_256_GCM_SHA384,TLS_CHACHA20_POLY1305_SHA256
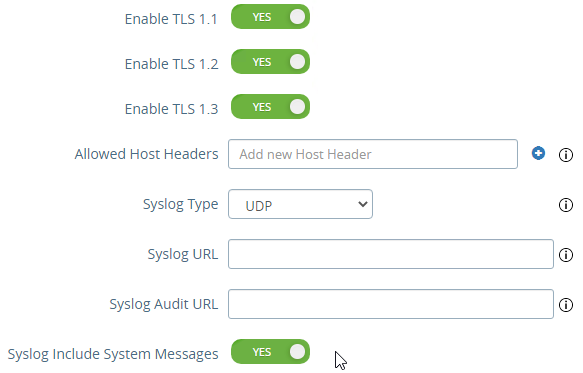
- In UAG older than 2103, Syslog is also configured here. In UAG 2103 and newer, Syslog is in a different menu as described below.
- At the bottom of the System Configuration page are several settings for SNMP, DNS, and NTP.
- UAG 20.12 (2012) and newer support SNMPv3.
- UAG 3.10 and newer have Admin Disclaimer Text.
- You can add NTP Servers.
- The default ciphers in UAG 2412 are the following and include support for TLS 1.3.
- Session Timeout is configured in System Configuration. It defaults to 10 hours.
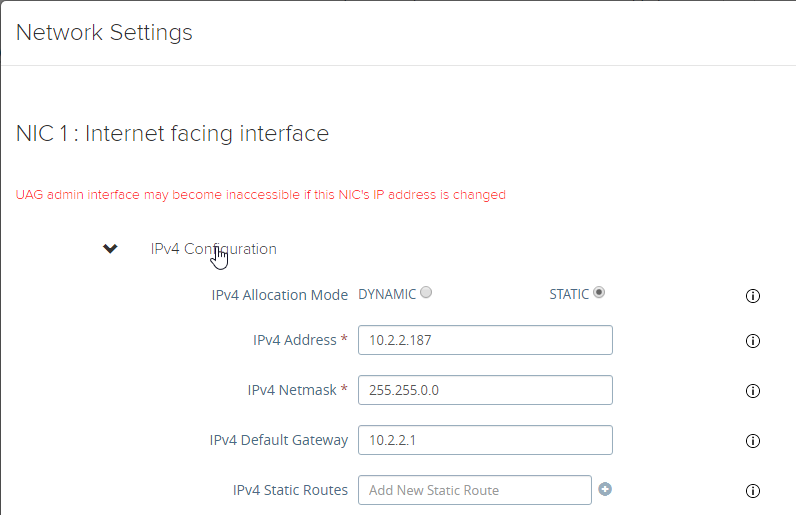
- UAG 3.6 and newer let you add static routes to each NIC.
- Click Network Settings.
- Click the gear icon next to a NIC.
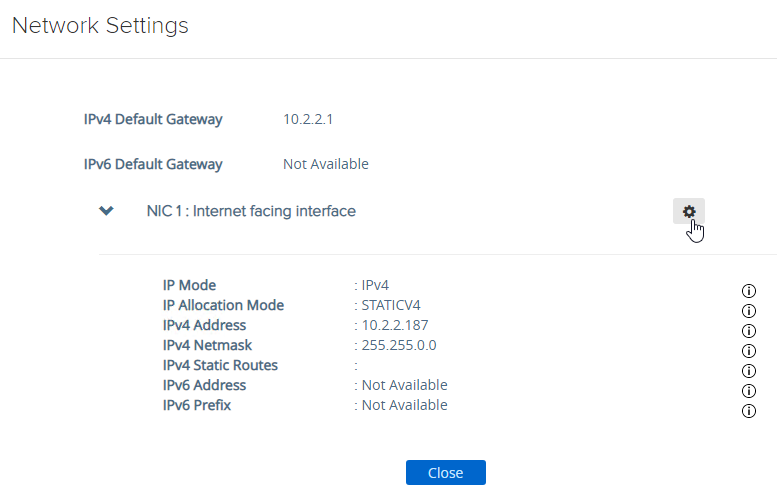
- Click IPv4 Configuration to expand it and then configure IPv4 Static Routes.
- Click Network Settings.
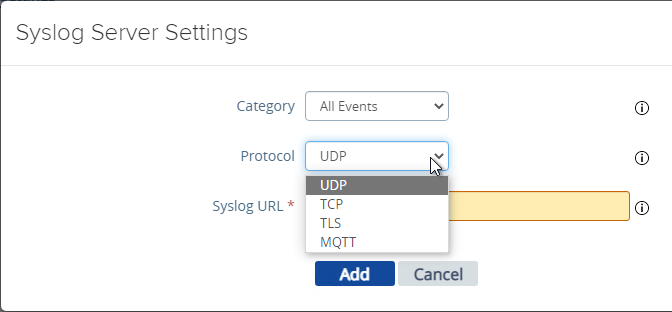
- UAG 2103 and newer have a different menu item for Syslog Server Settings.
- You can specify up to two Syslog servers.
- You can include System Messages.
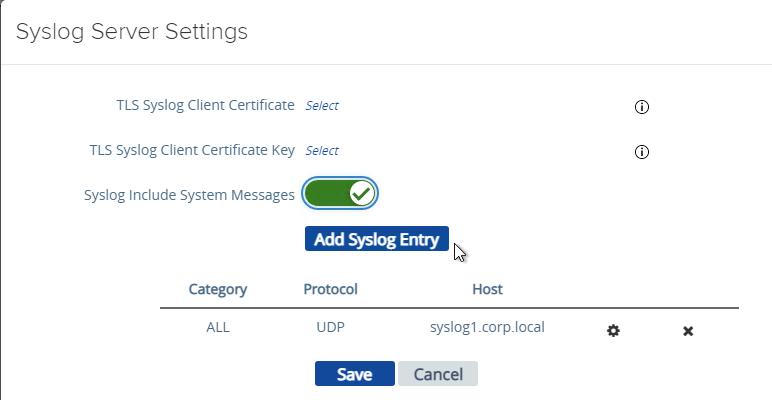
- UAG 2207 supports MQTT when adding Syslog servers.
- UAG 20.09 (2009) and newer can automatically install patches/updates when the appliance reboots.
- In the Advanced Settings section, click Appliance Updates Settings.
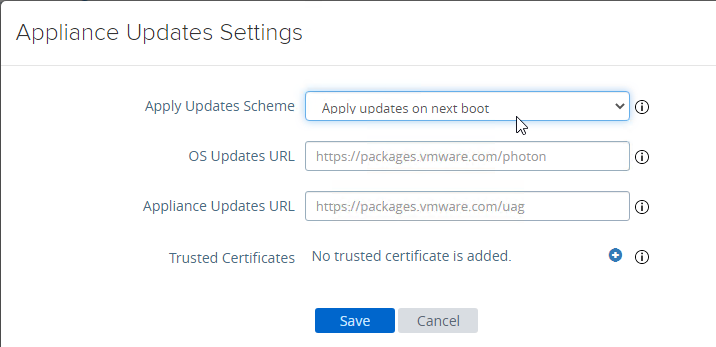
- For Apply Updates Scheme, select an option. Click Save.
- In the Advanced Settings section, click Appliance Updates Settings.
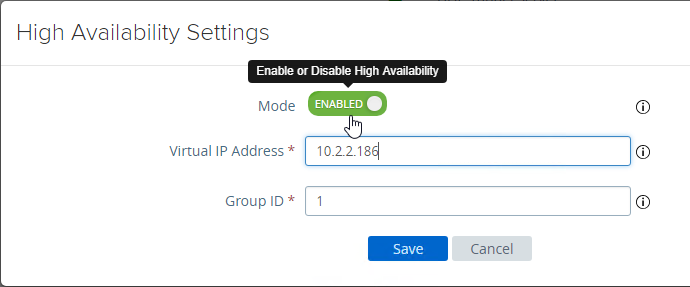
- UAG supports High Availability Settings.
- With the High Availability Virtual IP address, you might not need load balancing of the UAG appliances. See Unified Access Gateway High Availability at Omnissa Docs.
- The High Availability feature requires three IP addresses and three DNS names:
- One IP/FQDN for the High Availability Virtual IP.
- And one IP/FQDN for each appliance/node.
- The Horizon Edge Gateways should be set to node-specific IP addresses and node-specific DNS names. Each appliance is set to a different IP/FQDN.
- The Virtual IP (and its DNS name) is only used for the High Availability configuration.
- The YouTube video High Availability on VMware Unified Access Gateway Feature Walk-through explains the High Availability architecture.
- The High Availability feature requires three IP addresses and three DNS names:
- Set the Mode to ENABLED.
- Enter a new Virtual IP Address which is active on both appliances.
- Enter a unique Group ID between 1 and 255 for the subnet.
- Click Save.
- On the second appliance, configure the exact same High Availability Settings.
- With the High Availability Virtual IP address, you might not need load balancing of the UAG appliances. See Unified Access Gateway High Availability at Omnissa Docs.
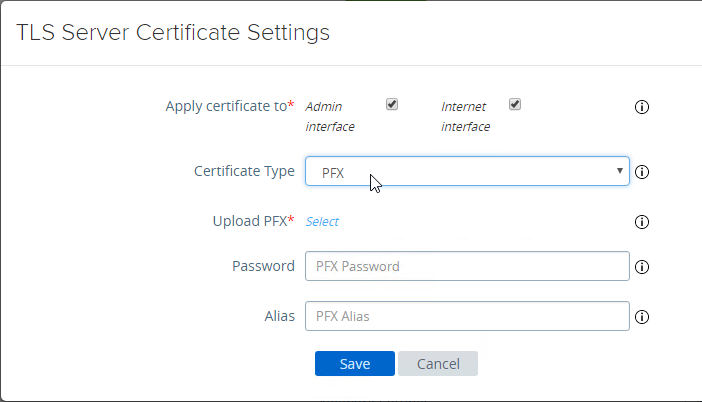
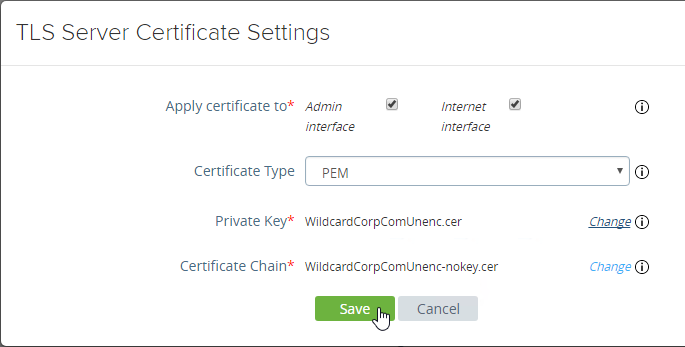
- To upload a valid certificate, scroll down to the Advanced Settings section, and next to TLS Server Certificate Settings, click the gear icon.
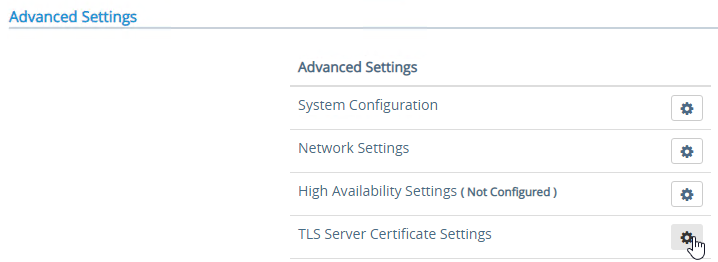
- In Unified Access Gateway 2312 and newer, click Edit in the Internet section.
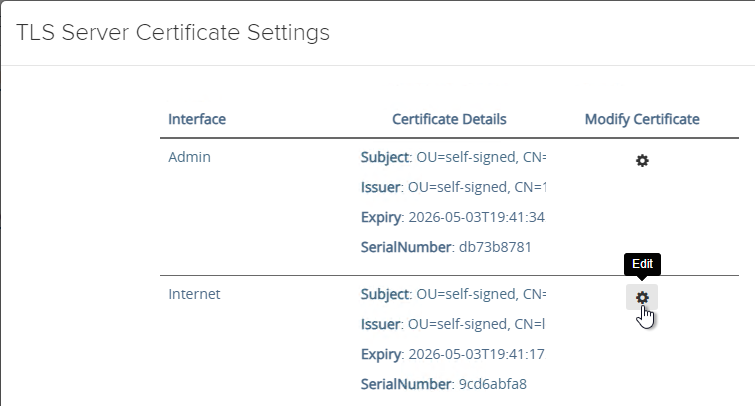
- In Unified Access Gateway 3.2 and newer, you can apply the uploaded certificate to Internet Interface, Admin Interface, or both.
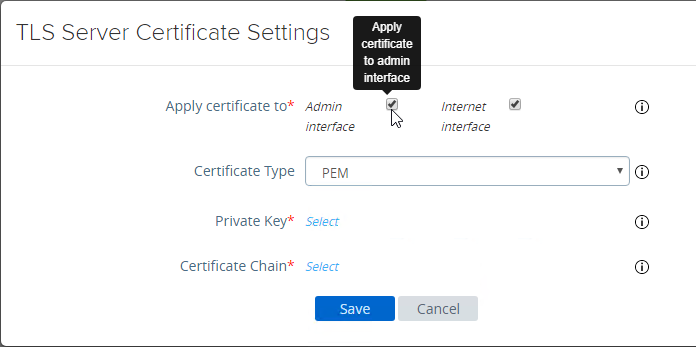
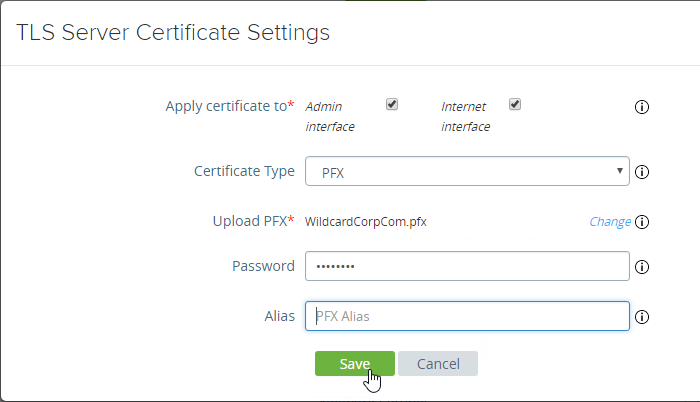
- In Unified Access Gateway 3.0 and newer, change the Certificate Type to PFX, browse to a PFX file, and then enter the password. This PFX file certificate must match the Public FQDN (load balanced) for Unified Access Gateway. If your load balancer is terminating SSL, then the certificate on the UAG must be identical to the certificate on the load balancer.
- Leave the Alias field blank.
- Click Save.
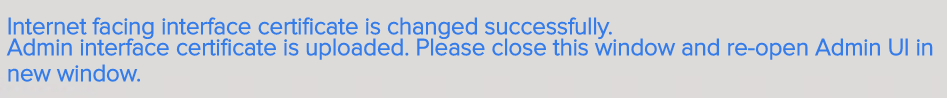
- If you changed the Admin Interface certificate, then you will be prompted to close the browser window and re-open it.
- In Unified Access Gateway 2312 and newer, click Edit in the Internet section.
- Or, you can upload a PEM certificate/key (this is the only option in older UAG). Next to Private Key, click the Select link.
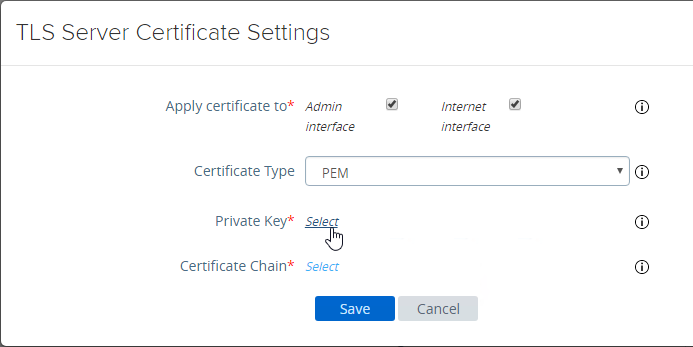
- Browse to a PEM keyfile. If not running Unified Access Gateway 3.0 or newer, then certificates created on Windows (PFX files) must be converted to PEM before they can be used with Unified Access Gateway. You can use openssl commands to perform this conversion. The private key should be unencrypted.
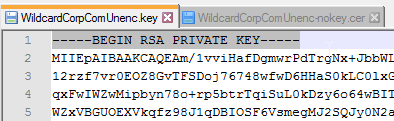
- Browse to a PEM certificate file (Base-64) that contains the server certificate, and any intermediate certificates. The server certificate is on top, the intermediate certificates are below it. The server certificate must match the public FQDN (load balanced) for the Unified Access Gateway.
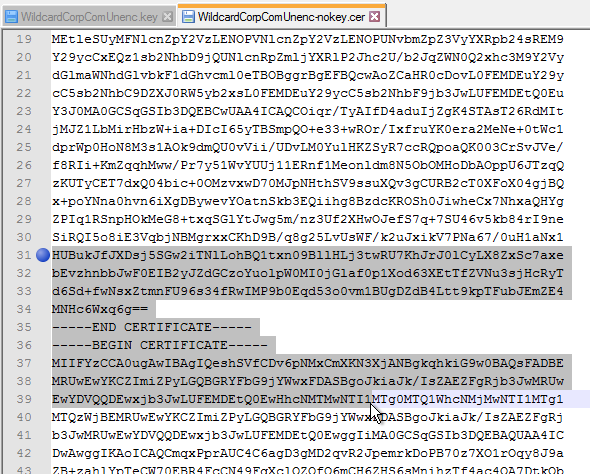
- Click Save when done.
- Browse to a PEM keyfile. If not running Unified Access Gateway 3.0 or newer, then certificates created on Windows (PFX files) must be converted to PEM before they can be used with Unified Access Gateway. You can use openssl commands to perform this conversion. The private key should be unencrypted.
- UAG 3.1 and newer have an Endpoint Compliance Check feature. The feature requires an OPSWAT subscription. Newer versions of UAG can deploy the OPSWAT agent. It’s pass/fail. See Configure OPSWAT as the Endpoint Compliance Check Provider for Horizon at VMware Docs.
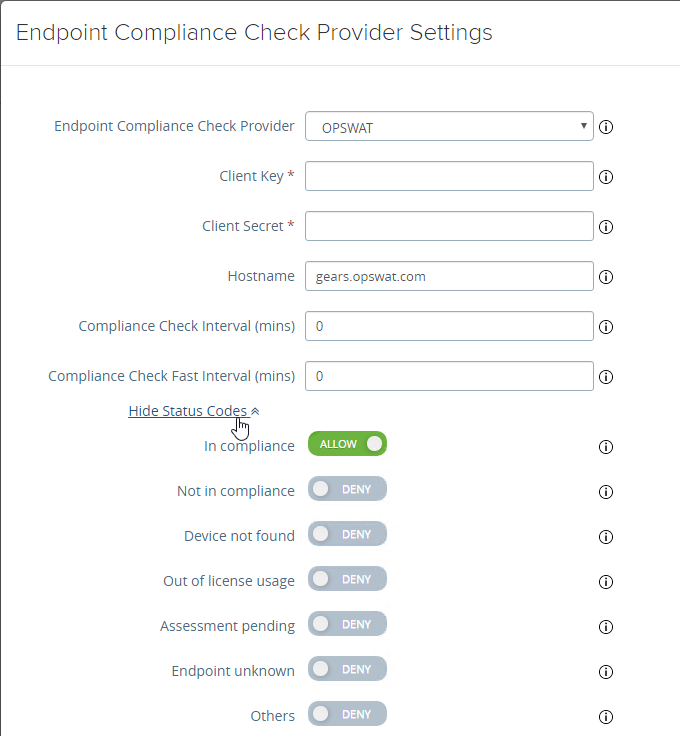
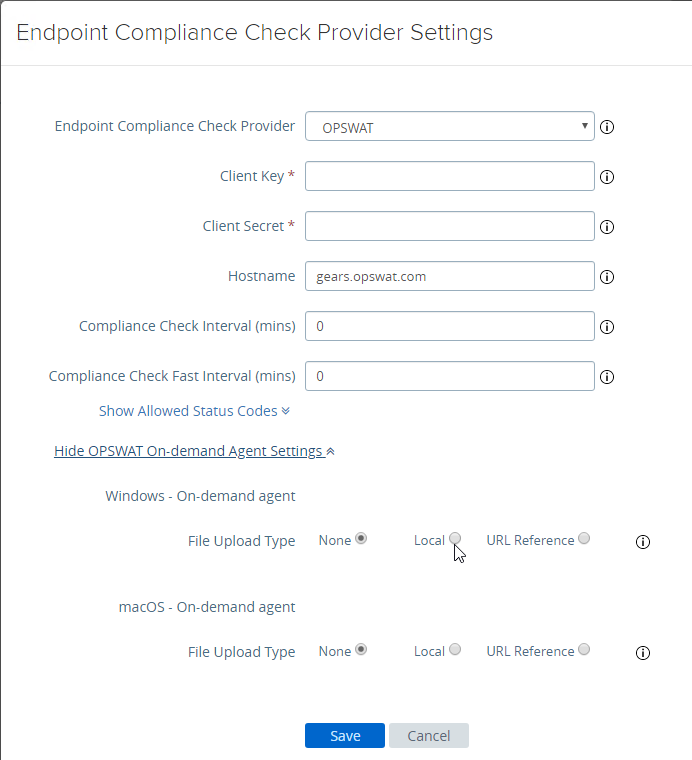
- UAG 3.9 and newer let you upload the Opswat Endpoint Compliance on-demand agent executables. Horizon Client downloads the executables from UAG and runs them. See Upload OPSWAT MetaAccess on-demand agent Software on Unified Access Gateway at VMware Docs.
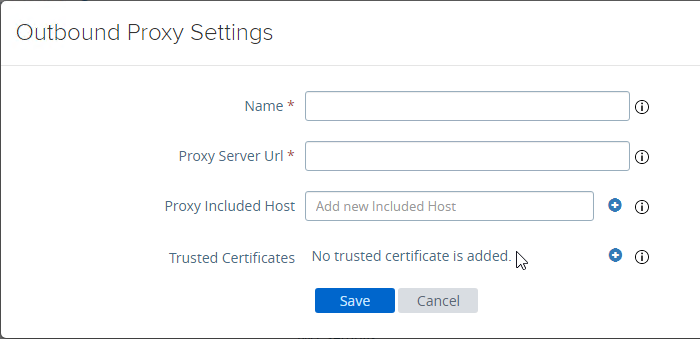
- In UAG 20.09 and newer, Outbound Proxy Settings can be configured to allow UAG to contact the Opswat servers when checking for device compliance.
- UAG 3.9 and newer let you upload the Opswat Endpoint Compliance on-demand agent executables. Horizon Client downloads the executables from UAG and runs them. See Upload OPSWAT MetaAccess on-demand agent Software on Unified Access Gateway at VMware Docs.
- Scroll down to Support Settings and click the icon next to Export Unified Access Gateway Settings to save the settings to a JSON file. If you need to rebuild your Unified Access Gateway, simply import the the JSON file.
- The exported JSON file does not include the UAG certificate, so you’ll also need the .pfx file.
- The exported JSON file does not include the UAG certificate, so you’ll also need the .pfx file.
- If you point your browser to the Unified Access Gateway external URL, you should see the Horizon Connection Server portal page. Horizon Clients should also work to the Unified Access Gateway URL.
Monitor Sessions
In UAG 3.4 and newer, in the UAG Admin interface,
- At the top of the page, next to Edge Service Settings, you can see the number of Active Sessions on this appliance.
- At the bottom of the page, under Support Settings, click Edge Service Session Statistics to see more details.
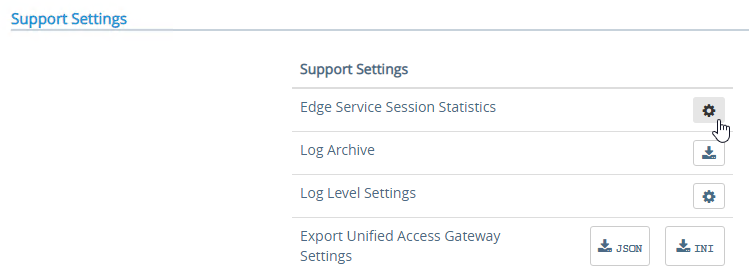
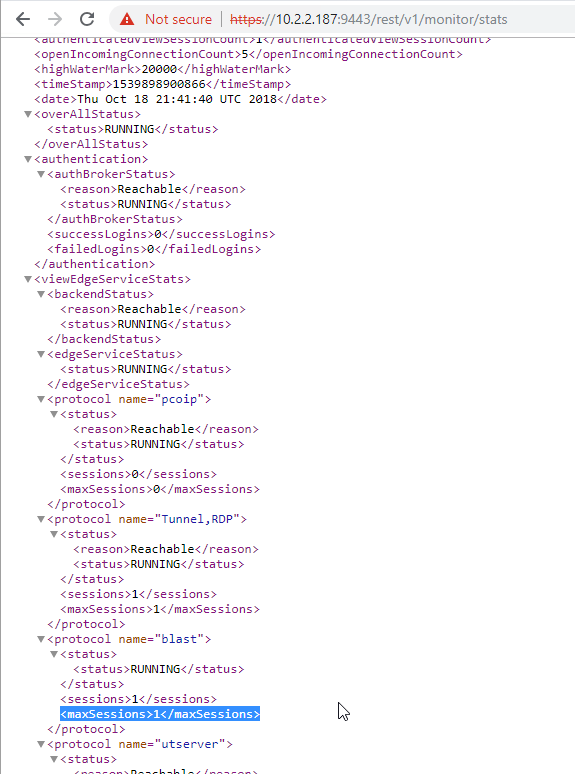
In older versions of UAG, to see existing Horizon connections going through UAG, point your browser to https://uag-hostname-or-ip-addr:9443/rest/v1/monitor/stats.
Logs and Troubleshooting
You can download logs from the Admin Interface by clicking the icon next to Log Archive.
You can also review the logs at /opt/vmware/gateway/logs. You can less these logs from the appliance console.
Or you can point your browser to https://MyApplianceIP:9443/rest/v1/monitor/support-archive. This will download a .zip file with all of the logfiles. Much easier to read in a GUI text editor.
For initial configuration problems, check out admin.log.
For Horizon View brokering problems, check out esmanager.log.
By default, tcpdump is not installed on UAG. To install it, login to the console and run /etc/vmware/gss-support/install.sh
- More info at Justin Johnson Troubleshooting Port Connectivity For Horizon’s Unified Access Gateway 3.2 Using Curl And Tcpdump
Load Balancing
If NetScaler, see https://www.carlstalhood.com/vmware-horizon-unified-access-gateway-load-balancing-citrix-adc/ load balance Unified Access Gateways.
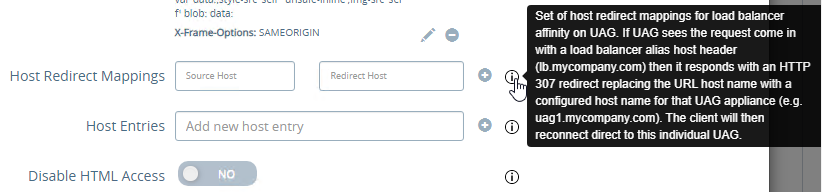
To help with load balancing affinity, UAG 3.8 and newer can redirect the load balanced DNS name to a node-specific DNS name. This is configured in Edge Service Settings > Horizon Settings > More (bottom of page).
Related Pages
- Back to Omnissa Horizon 8
Hi All, we are getting some issue about when using Horizon client from external URL to connect UAG server fail said “the connection server authentication failed. The Tunnel server presented a certificate that didn’t match the expected certificate.
On Connection Server Dashboard view “Server’s certificate subject name does not match the server’s External URL. Server’s certificate is not trusted.”
We are configured UAG TLS Server Certificate settings
(Assigned Admin interface PFX)CA signed cert
(Assigned Internet interface PFX) Public cert
All certificated is valid.
On Internal test lab has been tested successfully
– Horizon client and HTML without any problem
– External URL or Internal URL of UAG
– Internal connection to connection server
– External URL to connect UAG server in HTML (Public PC)
Failed
– External URL to connect UAG server in Horizon Client (Public PC)
May I know any someone can help? Thanks.
Is your load balancer or firewall configured to terminate SSL? If so, make sure the load balancer/firewall cert and the UAG cert are identical.
Any chance you know how to enable secure cookies on the EUC? I am looking for documentation on it, however I am not finding much. It keeps getting flagged in my vulnerability scans.
We don’t have these issues
Maybe your connection servers , not the UAG.
Thanks for the reply Mike,
I’ll check the connection servers as well. If anyone has experience with applying the ‘secure’ cookie setting on a connection server, I would appreciate the help finding the documentation.
Maybe your load balancer can rewrite the cookie.
Hello Carl Sir and Everyone, may I know how to do the UAG register on Horizon, since by following the steps as instructed (Add UAG to Horizon Console step 7), input the gateway name as specified within UAG system configuration, my Horizon doesn’t show the UAG status (Version, IP…) as normal as the post shows.
I guess there would be accompanied with some context behind to work like DNS or something, may you please give me a guide? Thanks!
The name is case sensitive. Then make sure you start a connection through the UAG.
hi guys – Anyone seen it where deploying via powershell using an ini file downloaded from an exisiting UAG it simply doesn’t deploy any of the Edge service settings? ie Horizon settings etc
It deploys with the correct IP and name / networks, but just doesnt enter these
Doesn’t error either
Hi Paul W,
I had a problem with new ini, it’s exactly just doesn’t configuring Edge Settings, I tried few times and I’m the end I configured it manually.
Thanks RA
Very frustrating as I have 16 to upgrade/configure ! But I guess I wil have to
I guess the quickest thing then could be deploy via Powershell to IP it,
Then import config on top and that should do most stuff
IT doesnt even seem to read the certificate either even though it asks for a password
Paul W,
Do you have an iOS users? On my UAG’s enabled 2FA (X.509+Passthrough) and when I running the Horizon iOS Client it’s shows Error – “Access denied. No valid certificate provided”.
The same user certificate in Horizon Client on Windows machines working fine and even same certificate working fine in Citrix Workspace iOS Client, but not working in Horizon iOS Client 🙁
With only Passthroug (Password) iOS Horizon Client also working fine.
hmm, i have heard of this before on Mac client but i cant really remember the fix, I think we normally just upgrade client if available. sorry!
Hey Jeff,
great article, always a big help.
recently we had to do a fast upgrade to the latest Unified Access Gateway 2209 and using one connection server (“fresh” replica install) for external connections version 7.13.2. So they are kind of “paired”.
we did an export of the old uag setting and imported them again.
Connections with the Horizon Client work like always.
But when I enter our URL in one Browser, I do not get a nice grapical interface, where I am able too choose, if I want to install the client or use HTML Access.
You only get the text with the links for HTML access or install / start the clients.
those links for html access are directing to https://extern.address.de/portal/webclient/index.html – which leads to 404 error.
any ideas or heard about this problem?
best regards
Rick
What Proxy Pattern is configured in Edge Settings > Horizon Settings > More?
configured is this – must be default?! never added or edited that
/|/downloads(.*)
The default is below. Your export/import preserved an older proxy pattern.
(/|/view-client(.*)|/portal(.*)|/appblast(.*))
thanks Carl
that did the trick
Hi Carl,
Thank you for this article. I actually would like to put an USG with a direct public IP but it seems that the USG need a NAT to work. It is possible to put a public IP on the USG ?
Thank you
I’m not aware of any NAT requirement. Typically, you connect it to a DMZ VLAN that has DMZ IP addresses and then you NAT a public IP to the DMZ IP. But I don’t see any reason why you can’t connect the UAG directly to a public subnet and assign a public IP.
Is there any way to upgrade a UAG without building news old to replace the old ones?
No.
You could export the config, replace the appliance, then import the config. That process should be documented in this article.
Hi Ed,
You can use the Powershell scripts to deploy new UAGs quickly. There is also a VMware fling that helps you deploy it similar to how you would deploy a vCenter appliance. The fling is called the Unified Access Gateway Deployment Utility.
I don’t find Unified Access Gateway Deployment Utility. Can anyone provide me with the program? I would appreciate a link to download it. Because the one that appears in many pages is no longer operative.
Hi Carl, Is there any way to upgrade a UAG to a new version besides creating new ones and swapping them out with the old ones?
Nope. VMware chose the cloud operations model where machines are replaced and never upgraded in-place.
Does anyone use RADIUS auth with MSCHAPv2? We have that configured and it’s working great when the user has a valid password. Unfortunately, when the user’s password is expired, the UAG login process isn’t presenting any screens to allow the user to change their password. If the user’s password gets reset via other means, they are able to log in again via the UAG.
Does anyone have any experience with this? Any settings in the UAG that could be tweaked to allow the user to update an expired password during the login process?
Hi Daniel, yes we use this and have the exact same issue. Have you found a way to overcome this at all. Currently we have a policy in place to tell them on the desktop that their password will expire in x number of days and to change it before it expires so they don’t get to the point where they have this issue.
Experiencing same exact issues. Using Dou and NPS. So far no luck with any Duo config that would allow in-line password resets. Outside of resetting PW before it expires, anyone found a working solution?
Hi Carl. Version 2207 comes with a non-root user , having sudo privileges (pure root is unavailable)
In my case I named it uagadmin.
uagadmin@UAG [ ~ ] passwd
As I change its password with passwd command I cannot connect to the appliance the new password via ssh. And also via vmware console screen the passwords (old and new) cannot log into the machine.
Any suggestions of why this is happening?
Hey Pavel, I observed that non-root user (with sudo privileges) to be optional. If you do not specify any username for that non-root user during deployment, the default root account would be accessible as usual.
If the password is not working you could probably reset it using single user mode. There is a page in their docs with title Troubleshooting Root Login Issues (https://docs.vmware.com/en/Unified-Access-Gateway/2207/uag-deploy-config/GUID-F1B90F5A-DC1A-4175-B345-A4984F9AF757.html). It can be used for reset passwords of non-root admin user as well. Once you login with single user mode, slightly modify the command ‘passwd’ to ‘passwd uagadmin’ (without quotes).
Also note that the uagadmin user is not a root user, but sudo privileged, so you will have to prefix sudo when running the commands that require root privileges
Hi Carl, first of all nice blog. It helped me a lot. I have a question about DR. We have a very simplet setup, with 2 uag’s and 2 connection servers. Since i don’t have any experience with the UAG’s i’d like to know if there is something particular i need to do for disaster recovery for the UAGs? Is a “simple” backup of the vm enough or is this not supported to restore the UAG from a backup?
VM Backup is fine. Another option is to download the config (JSON) and during restore you deploy a UAG and import the JSON and SSL cert.
thnx for the confirmation, this is what I supposed.
We recommend deploying UAG with PowerShell and making all changes from the ini and redeploying it. This way the UAG doesn’t contain any state and restoring or upgrading is easy.
thnx!
Hi Carl,
I’ve noticed that when the “Discard SSO Credentials” global settings are configured on the CS, active sessions tunneled through UAG will drop if you restart the connection server that was used when the connection was first established.
The sessions won’t disconnect immediately, but rather a few minutes (or even hours) later, depending on the time configured for “Discard SSO Credentials”.
If I set it to “Never”, this problem doesn’t occur at all.
Have you seen this as well?
Hi Carl, Can you give me some suggestions about the UAG service.
I want to check the UAG Server is running or not in the VMware by write some script. Do you have any ideas ? Please help me. Thanks a lot
You could set a GET request to /favicon.ico. This is how load balancers verify the UAG is reachable.
Hi Carl,
Thank for you suggestion.
When I try to make a request to the UAG.domain/favicon.ico by using the CUL command in Powershell. I get an error like : the connection was closed. An unexpected error occurred on a send. I tried to add tls12 but it doesn’t work.
Any help or suggestion on this ?
Thank you so much
Hey Carl, when setting up High Availability on a UAG w/o a load balancer how does the Horizon Client know which UAG to connect to on the secondary connection ( in my case the External Blast URL )? Is that sent back to the client during the Primary connection ( XML API )
Source IP persistence.
Hi Carl
thank you for maintaining this great blog.
Question : Do you have any recommendations in regards to Idle Connection Timeout, Session Timeout settings when loadbalancing UAGs and Vconnection Servers :
client -> loadbalancer -> uags -> loadbalancer -> connection server.
I would think timeouts should be set so that :
(Loadbalancer persistence timeout) = (UAG : Session timeout) = (Connection Server : Forcibly Disconnect) = 10h and
(Loadbalancer Idle connection timeout) = (UAG : Idle connection timeout) = . (Connection Server : idle timeout setting – where is this ?)
https://kb.vmware.com/s/article/56636 – does not explicitly states this. It also talks about Connection Servers only.
many thanks
I usually set persistence timeout to same as Forcibly Disconnect.
client idle timeout doesn’t matter since establishing a new client connection should honor the previous persistence timeout.
Hi Carl,
I have recently set up the UAG to access our VDI from External protected with Microsoft MFA. The only thing is that I have a strange problem. Once authenticated via Browser on UAG and Connection Server, I see my Pools, but once I click connect, it is stuck at “loading”, and it doesn’t continue. When I do the same directly from the Connection Server the connection just works fine. Do you have any Idea what this could be?
Thank you in advance and best regards,
Tim
Does it work in Horizon Client?
The browser tries to connect to the UAG on port 8443. There’s a Blast External Gateway URL in UAG config. Is that URL valid from the client?
Hello Carl, people,
I understand where we have to change the certificate on UAG admin console, what about the certificate on the UEM console for TUNNEL configuration ? There are 2 certificates ( frontend cert & backend cert ) That certs are changed automatically or have to be renewed also ?
Hi, What is the point of the ‘TLS Server certificate’ settings when each ‘Edge’service has an option to upload an ssl. Which one of the 2 settings should be used? Thanks
Hi Carl. The certificate on the URL for external users which is configured on UAG is getting expired next week.
So do we have to follow any additional steps apart from uploading the new certificate in the UAG admin console?
And also do we have to delete the old certificate ? Because I am not able to see the old certificate in UAG.
Nope. Just upload the new one by selecting ‘Internet’ when uploading.
The old one will be deleted when you replace the UAG during upgrade.
Thanks a lot Carl. Will do that. And one more thing. Is there a way to see the old certificate in the UAG appliance because when I checked the TLS settings in UAG I found nothing.
It’s probably a file somewhere in the UAG filesystem. I don’t know the location.
Great post. We just stood up a UAG appliance and all is well excepting PcoIP connections from the client: brief black screen and session fails. PcoIP connections work properly when the client is within the corporate network. Double-checked that port 4172 is open on connection servers and edge firewall. Blast and HTML work fine both inside and out of corp network. Any thoughts?
It’s usually a persistence problem on the load balancer.
hi Carl , this page has been a godsend for us here.
We’ve got 1 problem though with the RSA connection in the 21.11.1 UAG.
The UaG is using a SecureID Certifcate now instead of the sdconf.rec file so we’ve had to turn on the connection API
We’ve got connection to the RSA SecurID Server but when we try to connect it we get:
“The Authentication Method Could not be configured. A SecurID connectivity or configuration error has occured”
Did you open the new port number 5555? https://docs.vmware.com/en/Unified-Access-Gateway/2203/uag-deploy-config/GUID-A711DCF2-B699-4D4F-8E99-A8AE7CFF1705.html
Carl – Thanks for the article! I’ve actually reviewed a few of your articles on the UAG in the past, by far the most helpful that I have seen thus far. A question for you (as well as everyone on the forum) – I recently deployed the newest version of the UAG in my environment (UAG 22.03) and am having a strange issue with the web interface. Users are able to log in without an issue to the installed client. The page loads, but the CSS is broken so it shows all the text from top to bottom. The link to the VMware page to download the client works. The link to launch web access is there, but if users click on it, it returns this error:
This uag.company.com page can’t be found No webpage was found for the web address: https://uag.company.com/portal/webclient/index.html
HTTP ERROR 404
The CSS being broken and the lack of web access seem related, although I haven’t been able to find anyone else having the same issue. Plenty of issues with .local domains (which we don’t have) and issues with the entire portal being blank/white screen (which I am not seeing either). This was working fine on the older version of the UAG. I tried rolling back to the older VM temporarily which still works just fine, seems like a potential bug in the newer version. Any thoughts? Thanks!
What is configured in your Proxy Pattern (Edge Settings > Horizon Settings > More)? I think the defaults changed and you might have imported an older config.
That is definitely a possibility! I have “(/|/downloads(.*))” in the Proxy Pattern field and Enable Proxy Pattern Canonical Match toggle is enabled. I tried removing the leading and trailing backets matching what you have and resaving the configuration but that didn’t fix the issue. Might require a reboot for that change to apply? Otherwise, I also just noticed that I don’t have PCoIP enabled. I don’t think I did before either, but could that also be an issue?
Try (/|/view-client(.*)|/portal(.*)|/appblast(.*)|/downloads(.*))
https://docs.vmware.com/en/Unified-Access-Gateway/2203/uag-deploy-config/GUID-9049DE97-856B-431B-8CCD-387EA19DDC62.html
Wow, that worked! Thank you. I wasn’t aware that proxy pattern controlled so much. From the bit of research I had done previously, it looked like it primarily controlled the ability to download the client from the portal or not. Apparently it controls much more than that. Really appreciate your help!
You are a life saver. I have been racking my brain on this for 2 days after upgrading UAG.
Thanks for all of the great content that you put out!
Hi Carl,
First I wanted to say thank you very uch for your blogs reaging all the Workspace ONE Stuff, you safed me more than one times already 🙂
Now to my problem, I have deployed a completely new UAG version 2207 and enabled and configured the Secure E-Mail Gateway Service. Everything went fine, service is started, healthscreen shows all is good but if I try to access the configured external DNS for the SEG I alway get the error message “HTTP Error 404 – Website not found)… We do not have configured any Proxy and there is no other service active on the UAG, If I try to access https://segDNS/favicon.ico, it is showing something… Its really strange, we use a public SSL certificate which includes many Alternative names which we imported in the TLS Server Certificate Settings as well as on the SEG Settings…
May you have an idea about that?
Could it be that this is a Load Balancer topic?
Thanks in advance and BR
Michael
Hi Carl – thank you so much for this: it’s an institution! I’m currentyl deploying UAGs for a customer (on vSphere for Horizon) and would really like to do nothing more than the PowerShell-Deploy. As base for the .INI-File I used “uag3-securid.ini” as the customer need RSA two-factor auth for access via UAG.
Problem is, that the deployment script does not set the values set in the [SecurIDAuth] section. The UAG deploys successfully, even including HA-Settings, but in “Horizon-Settings > more > Auth Methods” there is no entry for “SecurID”. Also in “Authentication Settings”, “RSA SecurID” is still disabled and clicking the wheel brings up an empty dialog.
Do you know how to make this work from the .INI-File? The values entered there are correct and SecurID works immediately when I enter them into the Admin-GUI. When I do an .INI-File export, the values are identical to the ones in my file.
Do you have a clue how to get this working?
Chris, a colleague of mine recently had the same behavior and wrote me, how he solved it. I only read his note and auto translated his answer from German through DeepL but hope this helps:
The error was that the section in the SecureID sample file is at the end, but the Auth Settings for SecurID must be ready BEFORE you can select SecurID as Auth Method in the dropdown in the Horizon Settings.
Yes, this exaclty is the point: As soon as you move the [SecurIDAuth] section to a place before the [Horizon] section in the .INI-File, everything works as expected and RSA SecurID is deployed successfully.
Once again proof for the decay of VMware’s product quality:
Not a single person at VMware can have tested if the .INI-File works with the Powershell-Script before putting it out for production use, else this flaw would have been come to attention. w00t !!!
Strange UAG cert issue…. we have a working config but with an expiring external wildcard cert on UAG. We’ve created a new wildcard cert signed by same CA as old. After installing new cert on UAG, the connection attempts fail on horizon client with ‘The connection to remote computer ended’. If we set the horizon client to ‘Do not verify identity of certificates’ then all connections work fine. Something is up with new cert it seems but no clue what. Is there anything that needs to be checked on cert being imported? I think we’ve tried both pem and pfx of same cert……
Do you have a load balancer in front of UAG? Is that load balancer terminating SSL connections? If so, then the cert on the load balanced must be exactly the same as the one on the UAG.
We actually did have an F5 in front and then pulled it out when this issue started. So now clients hit one UAG server which points to one connection server before hitting the backend agents. Issue persists. Selecting use proxy or bypass cert checking in horizon client allows client app to connect to desired app. We’re on with support……. fingers crossed.
And big thanks Carl for your years of support…… you’ve saved my bacon a number of times.
When you export PFX from certlm.msc, there’s an option to export the entire chain. IIS doesn’t do this, but certlm.msc does.
Thanks for help….. to close the loop the issue was an oversight on our part. We did not remove/update the installed Blast Proxy Certificate in UAG. Removing this made the client connect without issue.
I could use a little help here. Running UAG version 2111.2 without any issues. I tried to deploy a 2203 UAG but the external facing web interface gives me a 404 error. I can access the admin interface fine and all horizon services are green. I imported the JSON config and cert from my 2111.2 UAG. I saw in your article to use the ESB version of a UAG, 2111.2, if you are using a ESB build of your connection server, but there is no 2203 version of the connection server. I am running the newest version on my connect server already. Any help anyone can provide would be greatly appreciated.
Maybe it’s caused by an invalid Proxy URL list in Horizon Edge Settings.
2203 UAG should work with 2111 Connection Server since there is no such thing as 2203 Connection Server.
Thanks Carl, for pointing me in the right direction. It was my proxy pattern. I set it back to the default and it is working as expected now.
We found that having two (or more) UAGs in HA mode, PCoIP will not work if you use the VIP for the external tunnel and external PCoIP entries. Each UAG needs its own IP address in those fields or else you will get a black screen on connecting to the VM.
In HA mode I believe that’s correct since you don’t have a load balancer ensuring persistence for the second connection.
Carl,
can you show me where to place those UAG IP addresses in the UAG configuration?
Do i change it at PCOIP External url and Tunnel Exernal url with the IP address of the UAG
Thanks in advance!
In HA mode (no load balancer), the tunnels/gateways should be set to appliance specific FQDNs and public IP addresses. Each UAG has separate FQDN/IP Address.
Paul, can you explain me further where to put the UAG addresses, because we have the same problem!
Thanks in advance!
Yeah, external Gateway and PCoIP gateway need the IP of the UAG appliance, not the VIP.
Thank you Paul for the explanation!
Hello Carl,
My customer is using VMware Horizon 8 and the users connect the vdi desktops through SSL vpn.
Users reporting they are having an issue with them re-connecting after idle time.
Adding UAG will improve the issues. Kindly suggest.
Hello Carl,
My customer using horion8 and users connect through ssl vpn access the vdi desktop.
Users reporting that they are having an issue with them re-connecting after idle time.
Please suggest
I have two UAGs and have HA running using the built in HA settings. Intermittently, users are sometimes unable to connect and are silently dropped from the horizon client. The logs indicate VRRP errors but I have no idea why. The set up is dead simple. Any thoughts?
VRRP errors are usually associated with some application needing to have either Forged Transmits or Promiscuous mode enabled on the portgroup the VMs are connected to.
Hi Carl – We have deployed a new Horizon environment with 4 UAG’s behind a Kemp LM using a VIP. It all works fine out the box, there are no issues. We simulated a failure scenario by taking a UAG down whilst users are connected. Obviously they get disconnected but we are having an issue with them re-connecting. It is intermittent but basically, they hit a new UAG on the primary connection (443), authenticate and get their desktop pool, but at the point they select their desktop pool and try to connect on the secondary connection, it fails with a connection to remote computer ended. They can keep re-trying and eventually it will let them in but the time is random – I’ve seen it take over 4 hours sometimes. We know that if we reboot the LM, it fixes the issue but struggling to understand why this is occurring after a UAG failure?
Do you have multiple Load Balancing Virtual servers on different port numbers? Do they all share the same persistence table? Maybe the 4172/8443 load balancers are not detecting the down connection server and thus are using the prior persistence.
We have a HA pair of LM’s for the UAG’s and the same for the Connection Servers. I assume they all share the same persistence table. It is when a UAG goes down, not a connection server. The LM recognises the UAG is down and users are able to make the primary connection back to another UAG but the secondary connection to launch the desktop fails. Its like the protocol being used it being held open somewhere from the old UAG? If we change protocol on the client, you can then log in again back to your original session if that makes sense?
Do you have a single configuration for all ports? Or do you have separate configurations for each port number: 443, 4172, and 8443.
Maybe the 4172 and 8443 load balancers don’t recognize that the UAG is down. Or maybe the 4172 and 8443 listeners don’t use the same persistence table as the 443 listener. This guide https://support.kemptechnologies.com/hc/en-us/articles/217737323-Horizon-7-and-Horizon-8 shows port following.
We are using Method 1 of Source IP Affinity and our set up looks like the picture they have put at the start of Section 8 so our 4 UAG’s sit inside each of the Source IP Affinity rules. When the UAG goes down, it is marked as down across all the rules.
Hi everyone, does anybode know what this error message means:
An error has occured: {“errno”:”EHOSTUNREACH”,”code”:”EHOSTUNREACH”,”syscall”:”connect”,”address”:”10.15.2.103″,”port”:2443}
User get this error sometimes when they connect with a browser to from home to the vdi desktop. The VMware UAG version we use is 2111.2 and the Horizon version 7.13.1. We use instant clone pools
Hope someone could help! Thanks in advance!
Is port 22443 open between the UAG and the Horizon Agents?
I assume the 2443 in your error message is supposed to be 22443.
Hi Carl,
yes, port 22443. is open between the UAG and de agents (VDI desktops)
Hi Carl, love your blogs. Wonder if you can give me a clue on something I am seeing in latest version. So previously we have 2 UAG appliances in a cluster for Secure Email Gateway access. On both appliances they showed a green icon all the time. Since deploying the new UAGs in a cluster, it always appears now that the node in “Backup” mode shows the status of “Down” with a red icon for the Secure Email Gateway and the primary shows green. However, if I shut the primary node down and the Backup takes over the role, the status of the Email Gateway service is now showing Up and Green. I cant find any reference to this being expected behaviour now, but its tricky to know if there is an actual issue here.
Hi Carl, I cannot see the images on your site on this page no matter which browser or what I do to try to fix it – or, does anyone else have this issue? Thanks!
I had that issue, turns out my company was blocking them as they were deemed as “personal site/blog” I assume because they have a WordPress prefix on them. Not sure if you are behind a corp proxy or not. But at least that was my case.
I have a question regarding certificates for the UAG. I am upgrading to 2111.2 and I was able to import my old settings after standing up a new UAG, but I was not the person who made the cert when they were first stood up so I’m not sure how that was done. Do you just make a generic .csr on a windows box and then upload it to a CA? Or do you make it and then export is as a .PFX?
I am unsure of how the certificate needs to be made and added to the UAG as it’s not exportable from the old one. I assume I need to make new.
Thanks for any help.
Create a CSR on Windows. Get it signed by a CA. Export the full cert and private key to a PFX file. Upload to both UAGs so they have the same cert. Keep a copy of the PFX in case you have to rebuild.
Hi Carl,
I have a deployment question on this new UAG where DR is part of the setup. Can I deploy a pair of UAG in Production Site and at the same time I deploy another pair of UAG in DR site as cold-standby appliance? by doing such if any disaster happen on Production site, can I manually configure or import the production UAG settings into DR-UAG? *Deployment of WS1 SaaS based
Or alternatively using backup and restore software approach to recover the UAG in DR site? *Assuming the same FQDN DNS record will be mapped to DR-IP Segment as well as the internal corporate resources.
Yes. GSLB active/passive is common between two UAG sites. Or manually change the DNS record.
So it’s possible to import back the UAG-Prod configuration into UAG-DR and then manually change the DNS record if the DR segment is using different DNS record or leave it unchanged if the DNS record is maintained across the DR site.
Yes. Or you can prebuild the backup UAG.
The config import does not include the certificate, so you’ll have to import that separately.
Have you heard about people on macs getting grey screens when finally connecting to the desktop? Even when using chrome etc? At this point i dont know anything like version of IOS etc but windows people are fine, mac people getting grey screens.
Hi Carl
We have upgraded our UAG due to the log4J issue. Now we have a strange issue with 2FA. If we use a old horizon client <= 8.3 you are able to login with no problems, but if you use the new 8.4 version or html access nothing happens after login with username+password. either html access or version 8.4 will prompt the the 2FA
Do you have any suggestions
Kind regards
Jens
This issue? https://www.stephenwagner.com/2021/12/02/duo-mfa-radius-issues-with-vmware-horizon-8-version-2111-uag-unified-access-gateway/
Hi Carl,
thank you so much, it is very helpful your Blog!
Probably u can help me with this question:
Is there a possibility to get the information which security Gateway a user gets from the Windows Client?
Something like is written in the Environment Variables?
I need to know if a user is logged in local in the network or remote logged in.
Thanks for your help!
Regards,
Tobias
Inside the virtual desktop are environment variables that might give this info. Or in Horizon Console if you view the sessions it should show you which Gateway the user used.
Is there something you need to do to enable SFTP and work with winSCP
Carl, thank you very much for your work. I hope you can help me solve my problem. I’m trying to setup my uag (2106) behind Cloudflare. In other words I would like to proxy all the connections to the uag through Cloudflare, but I’m having http 429 error (too many connections). Have you got any clue on how to solve this? Thank you in advance
Does anyone here happen to have a definitive answer on CVE-2021-44228 and CVE-2021-45046 (log4shell) as they pertain to the Horizon UAG?
We applied the workaround that VMware published here (https://kb.vmware.com/s/article/87092) to mitigate CVE-2021-44228 but now CVE-2021-45046 suggests that workaround may not be enough to mitigate the threat “in certain non-default configurations.” Anyone happen to know if the UAG would be considered a “non-default configuration”?
TIA!
Daniel
Hi everyone,
does the automatic update of the UAG appliance work for someone? I tried it with Version 2012,2103 and 2106.
It does not work.In the logfile i found follow message:
Package update with url https://packages.vmware.com/uag/21.06.2/updates.json failed as server returned errorcode – 404
Same problem here, there is no json files in that URL.
yep really wanting this to work to upgrade 2111 to 2111.1
anyone had any luck?
Hi Carl – Thanks for this amazing article. Hopefully quick question. Our insurance company does not like the HTML portal being open to the world. And we don’t use it. We only use the Horizon Client. Is there an easy way to disable the portal without breaking the client? We use mostly Blast, but some users are RDP due to licensing. Thanks!
Search https://docs.vmware.com/en/Unified-Access-Gateway/3.1/com.vmware.uag-31-deploy-config.doc/GUID-1B8665A2-485E-4471-954E-56DB9BA540E9.html for “disable html access”.
Wow, thanks for that fast response.
We found that, but it only disables the ability to use HTML5 web access to the resources. It doesn’t seem to shut down the web portal completely.
Try enable.webclient=false https://docs.vmware.com/en/VMware-Horizon-HTML-Access/2106/html-access-installation/GUID-10FAB7F4-D1AC-455F-8F99-3EDAF316E7AB.html
Looks like there might be a problem with the new uagdeploy PowerShell scripts, I had to deploy using the 2106 scripts as none of the Horizon settings were being set on the UAGs using the new scripts. Horizon was not enabled on the UAGs and all settings were blank. 2106 scripts with 2111 ova file worked ok.
Thanks Paul I will try this to
the 2209 seems to have same problem
do they not even test it lol?
Hi everyone, been fighting this loosing battle for a while. Wandered onto your site via Google search. In a nutshell, we utilize per-app-VPN for our 3000 iPhones. When on a public network whether cellular or wi-fi all works as it should. When a user attempts to navigate to a URL configured to tunnel inbound, it works without hesitation. However, when the user attempts this same URL while on our corporate network the phone gives a “No Internet Connection” error. The site never loads.
UAG 3.3, yes I know its old.
VMware Workspace One support says it’s a UDID mismatch causing the issue. They also said in a different call that the feature wasn’t available yet where the phone can sense whether or not to utilize the VPN and trusted networks. Basically, the phone can get to those internal sites without the VPN stood up when they are on the corporate network. The phone just doesn’t know that.
Any input would be very helpful.
Thanks,
K
Is UAG reachable internally?
Maybe put the phones on a Guest network where they can be treated as external.
Hi, we found several issues when customer devices where having IPv6 adresses when using basic staticV4 on UAG.
You should check if the devices get IPv6 assigned.
Your network team should then be able to adress the ip assignment and change it to IPv4 if thats the case, that should fix the issue.
This can also happen for mobile APNs, only solution we found was getting a different APNs.
Hi Carl, deploy UAG 2016 a month ago, everything seems to work fine except periodically, user gets HTTP 504 error when trying to connect to their VDI. Everything looks good from UAG admin console. Only fix I found so far is to reboot the UAG server. Any idea why this is happening?
We just deployed 2106.1 UAG and we have been having issues where after several hours it would start to drop connections. Eventually leading Horizon Admin console to say the UAG is unreachable. Even though the UAG is reachable via ping from the connection server as well as the vCenter.
We sent logs to VMWare and they said it was bug with SSL Handshake dropping? Anyone else having this issue?
Yes, engineering is looking into our case. Hope to have an answer in couple days.
We have similar issues , we need to deploy UAG every few months as we get ERR_CONNECTION_REFUSED.
This may sound like a stupid question (although I am of the opinion that the only stupid questions are the ones to which you do not know the answer yet remain unasked)…
If you deploy a newer UAG appliance, using the INI file of an old appliance as a template, and perform a direct replacement (same name, same IP etc.) does the new appliance automatically register itself (updating the software version) in the Horizon console, or does the old one need removing and the new one adding?
When UAG sends traffic to Connection Server, the UAG adds its name. Connection Server matches the UAG name with the UAG name in its config. So the only “registration” is the UAG name. As long as the UAG name is identical, then it will work.
Thank you
I’m running into an issue where users, when connecting through a UAG only, are getting disconnected after almost exactly 450 minutes. Connecting to the connection server directly does not exhibit the issue. Our setup is an external URL > external VIP > UAGs in the DMZ > internal VIP > Connection servers. Any idea where the issue might be? We have our logoff timer set to run after 30 minutes of being disconnected.
From the UAG:
07/02 17:22:43,140[nioEventLoopGroup-9-3]INFO proxy.HttpsBackendConnector[operationComplete: 128][ip][user][Horizon][87be-***-7b98]: Connected to backend channel: [id: 0x2d59d8fd, L:/ip:57550 – R:url/ip:443]
07/02 19:22:43,137[nioEventLoopGroup-9-2]INFO session.SessionRequestHandler[channelRead: 65][ip][user][Horizon][87be-***-7b98]: Too many connections opened for session: 87be-***-7b98, max channels allowed: 16
07/02 19:22:43,137[nioEventLoopGroup-9-2]INFO networkcore.HttpsRequestRouter[channelInactive: 111][ip][user][Horizon][87be-***-7b98]: [id: 0xb64dc9b1, L:/ip:6443 ! R:/ip:50023]: Request router channel became inactive
07/02 19:22:43,138[nioEventLoopGroup-9-2]INFO networkcore.HttpsRequestRouter[operationComplete: 278][ip][user][Horizon][87be-***-7b98]: [id: 0xa700e63c, L:/ip:62524 ! R:url/ip:443] backend channel is closed
07/02 19:52:53,969[pool-7-thread-1]INFO processor.ViewSession[terminateSession: 447][ip][user][Horizon][87be-***-7b98]: Horizon session:87be-***-7b98 terminated due to inactive – Current Session count:1778, Authenticated Sessions: 104
07/02 19:52:53,971[nioEventLoopGroup-3-1]INFO session.SessionManager[doPostSessionRemovalCleanUp: 454][ip][user][Horizon][87be-***-7b98]: Session : 87be-***-7b98 is removed
from the connection server:
2021-07-02T15:53:54.817-04:00 INFO (0284-06C4) [Audit] DISCONNECTED:Server:[OUs];DNS:[hostname];IP:[ip];IP6:null;USER:[user];USERDN:[userid];BROKERUSERSID:[sid];
2021-07-02T15:53:54.817-04:00 INFO (0284-06C4) [DesktopTracker] User user disconnected from machine [machine] for desktop [pool]- session allocated at July 2, 2021 8:23:06 AM EDT, connected for 450 mins 42 secs
In UAG System Configuration, what do you have configured for Session Timeout?
Session Timeout value is 36000000
That is 600 minutes, what does the VIP have as timeout for load balancer persistence timeout?
I have been assured the load balancer persistence timeout is 10 hours, and I have no reason to doubt otherwise, but I personally have not been able to confirm that with my own eyes (no access).
“Too many connections opened for session” is suspicous. Then “Request router channel became inactive”. 30 minutes later it disconnects. Do you see the same behavior with other sessions?
Yes, this is impacting multiple sessions. Disconnects happen almost always at 450 minutes plus a few seconds. When the disconnect occurs, they’re kicked out entirely, they have to reauthenticate through RSA, Active Directory, etc. Their VM session stays logged in though (only for 30 min). On the UAGs, Maximum Connections per Session is set 16 (default value). Client Connection Idle Timeout is set to 36000 (10 hours). I suspect increasing the session count will give me more than 450 minutes, but that doesn’t lead to a root cause. Any thoughts on that?
Hi Dan! I just started recently experiencing the same behavior in my environment, did you ever find a solution?
Same behavior for us. VMware Support has been unable to identify the cause after weeks of troubleshooting.
Would really appreciate any notes you have!
Are you terminating SSL on the load balancer? Or is it just forwarding the SSL session to the UAGs? If terminating, then you might have to turn off connection multiplexing. https://avinetworks.com/docs/18.2/configure-avi-vantage-for-vmware-horizon/
Carl – Yes, we are terminating SSL on the NetScaler. We’ll look into disabling multiplexing. Oddly, everything had been working fine for almost a year. The only recent change was upgrading from Horizon 7.13.0 to 7.13.1.
Thanks for the response!
We went the route of disabling our Horizon UDP VIP’s and leaving only the TCP VIP’s. As I understand, that should effectively disable multiplexing for our Horizon traffic.
Now, we’re seeing intermittent disconnects as opposed to daily (some days it happens for some users, some days not). We continue to see the same message in the UAG logs when disconnects occur – “Too many connections opened for session: ***, max channels allowed: 16”.
Hoping someone else has found a solution they can share.
We’ve successfully setup a UAG for Azure MFA auth along with TrueSSO and it works fine for Windows endpoints (or endpoints with a browser) – is there a way to have that same UAG either fallback to RADIUS for endpoints that don’t support a browser or perhaps setting Azure MFA to do a simple SMS code or MS Authenticator prompt? Thanks!
Jeff – responding to old post, but maybe will help someone along the way. If you want to use Azure AD with zero or thin clients that don’t have a browser you can use NPS with Azure MFA extension as an on-premise RADIUS proxy for Azure AD. In that configuration you use RADIUS auth at the UAG, pointed back to the NPS server(s). Note to support all methods of MFA from Azure requires use of PAP, if you use CHAP it supports some but not all methods. By methods I mean [authenticator app | phone call | SMS | email ]. This NPS setup is similar to how DUO can be used with an on-prem RADIUS proxy.