Navigation
Change Log
- 2024-02-29 – added link to Omnissa Tech Zone Deploying Horizon 8 and True SSO in Multi-Forest Environments
Overview
To configure SAML on Unified Access Gateway (UAG) you must have the following versions:
- UAG 3.8 or newer
- Connection Servers 7.11 or newer
- For Windows 10 version 2004, deploy Horizon 2103 (8.2) or newer.
True SSO is optional.
- SAML does not provide the user’s password to Horizon, which means that Horizon cannot perform single sign-on to the Horizon Agent machine and thus the Horizon Agent machine will prompt the user to login again. This usually means the user has to login twice.
- To eliminate the second logon on the Horizon Agent machine, implement True SSO, which generates certificates for each user and then uses those certificates to automatically sign into the Horizon Agent machine.
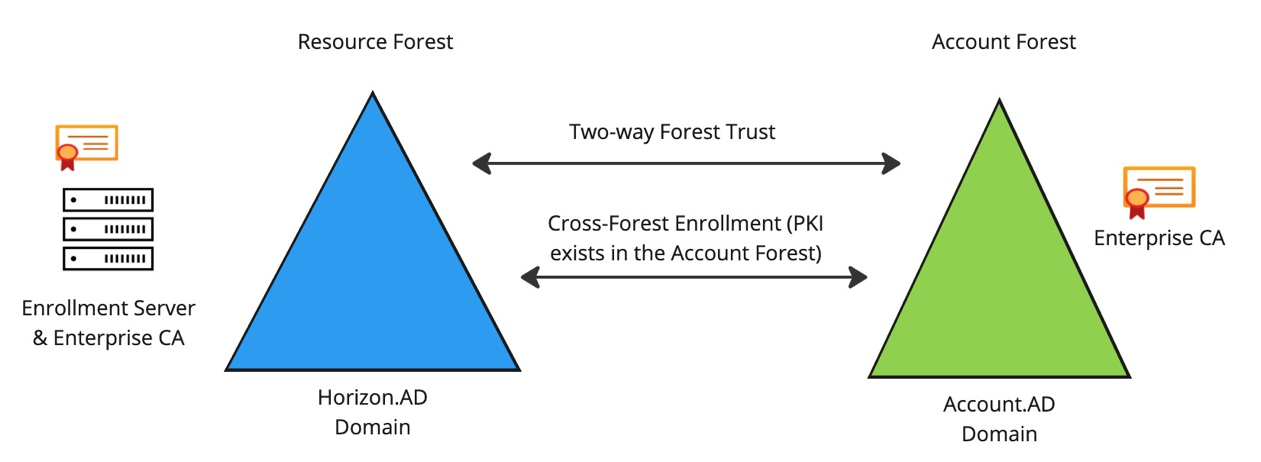
Horizon Enrollment Servers ask Microsoft Certificate Authority servers to generate the SSO certificates for each user. This is an identity operation and thus the Horizon Enrollment Servers should be treated like Domain Controllers.
- The Horizon Enrollment Server software must be installed on standalone servers (no other Horizon components).
- For High Availability you can build two Horizon Enrollment Servers.
- For multiple forests, see Omnissa Tech Zone Deploying Horizon 8 and True SSO in Multi-Forest Environments
When you use Horizon Client to connect to a UAG that is SAML-enabled:
- It opens the default browser and prompts the user to sign into your SAML Identity Provider. If the user is already signed in then the user won’t see any sign-in prompt.
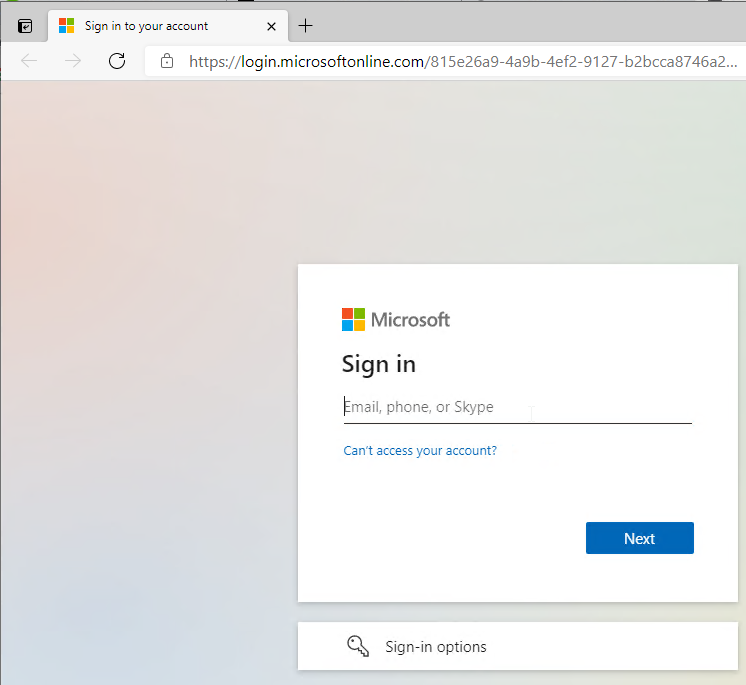
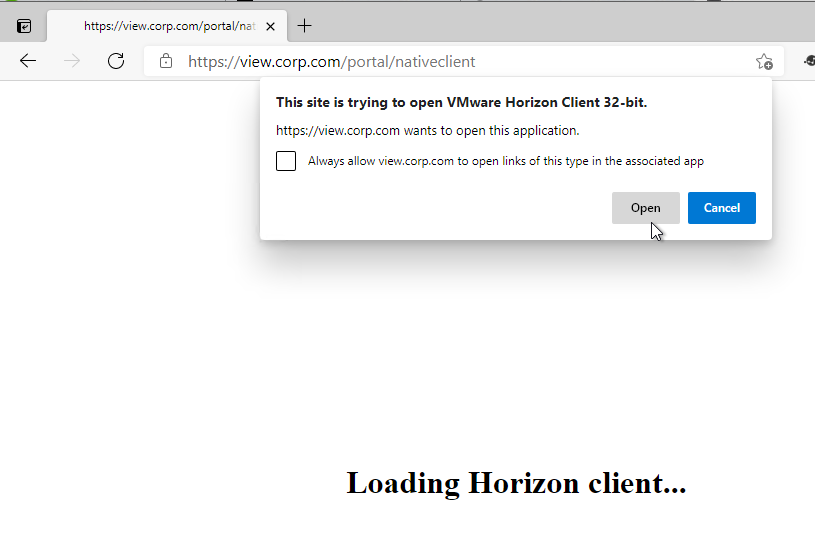
- After sign-in, the browser will then prompt the user to open Horizon Client.
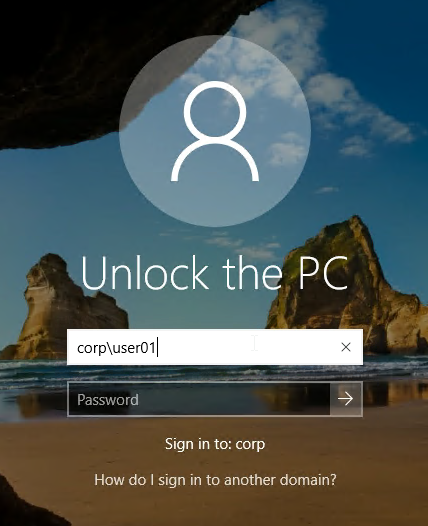
- If the user locks the desktop then the user will need to know the local Active Directory password to unlock it.
Certificate Authority
Horizon Enrollment Servers can use a Microsoft Certificate Authority that already exists. Or you can install Microsoft Certificate Authority on the Horizon Enrollment Servers. If you have two Enrollment Servers, then install Microsoft Certificate Authority on both of the servers.
- Install Microsoft Certificate Authority from Server Manager > Manage > Add Roles and Features.
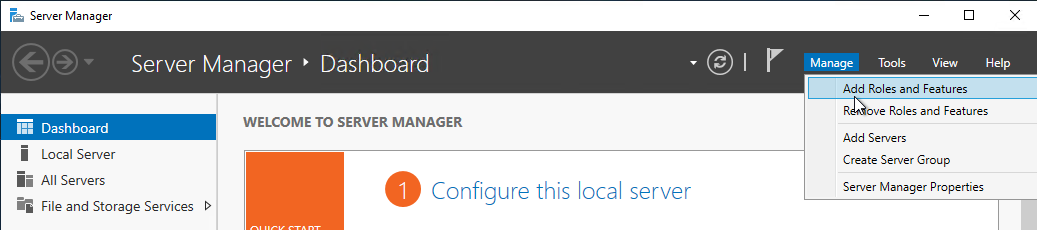
- Select Active Directory Certificate Services.
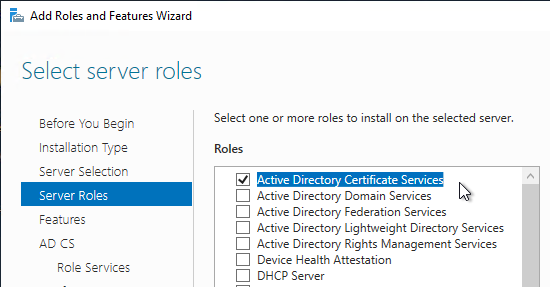
- The only Role Service needed for True SSO is Certification Authority.
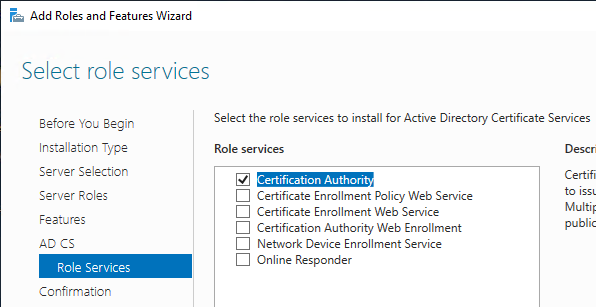
The Microsoft Certificate Authority must be an Enterprise CA.
- After role installation, click the flag icon and then click the link to Configure Active Directory Certificate Services.
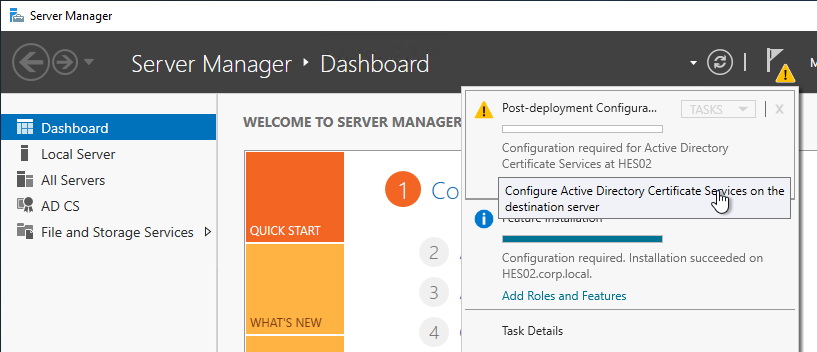
- In the Setup Type page, select Enterprise CA.
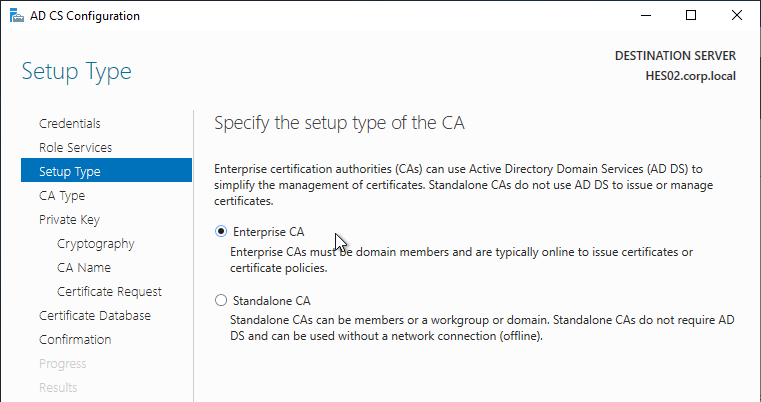
- In the CA Type page, if you already have a Root CA, then you can select Subordinate CA. Otherwise, you need at least one Root CA in your environment.
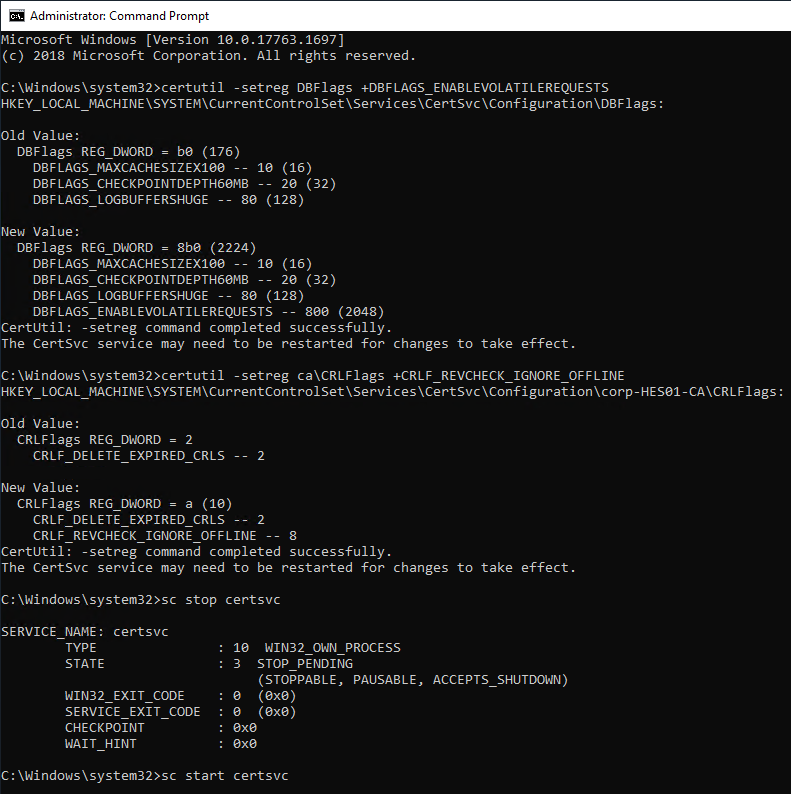
After Microsoft CA is installed, run the following commands:
certutil -setreg DBFlags +DBFLAGS_ENABLEVOLATILEREQUESTS certutil -setreg ca\CRLFlags +CRLF_REVCHECK_IGNORE_OFFLINE sc stop certsvc sc start certsvc
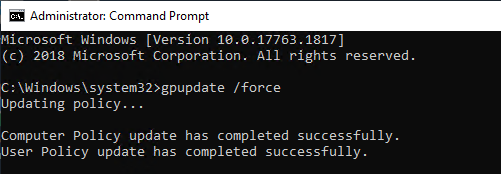
If you just built a new Certificate Authority server then True SSO won’t work until you run gpupdate /force on all of your Domain Controllers and Horizon Agent machines. Or wait several hours for group policy to update.
Certificate Template
- On the Certificate Authority machine, from Start Menu, run Certification Authority.
- Right-click the Certificate Templates node and click Manage.
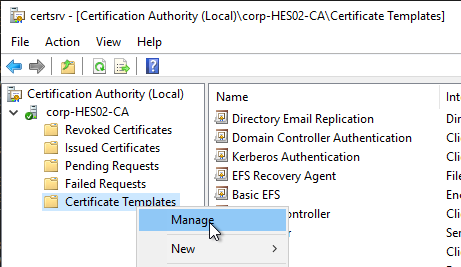
- Right-click the Smartcard Logon template and click Duplicate Template.
- On the Compatibility tab, change the drop-down for Certification Authority to Windows Server 2008 R2.
- Change the drop-down for Certificate recipient to Windows 7 / Server 2008 R2.
- On the General tab, name it True SSO or similar.
- Change the Validity Period to 1 day or similar.
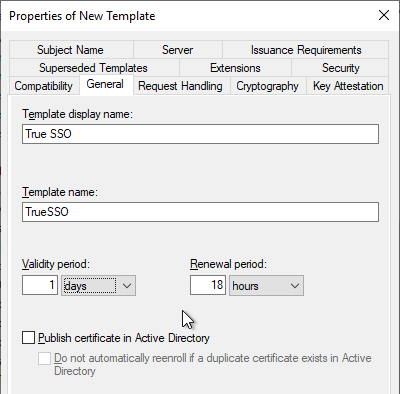
- On the Request Handling tab, change the drop-down for Purpose to Signature and smartcard logon.
- Check the box next to For automatic renewal of smart card certificates, use the existing key if a new key cannot be created.
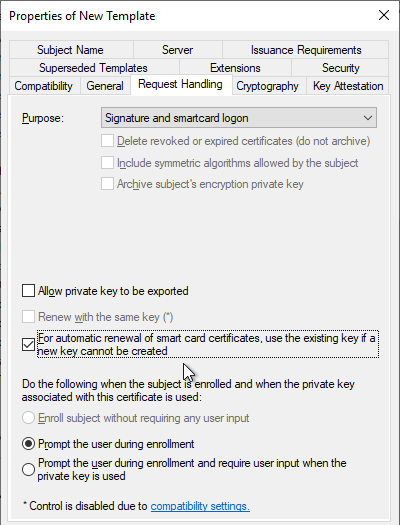
- On the Cryptography tab, change the drop-down for Provider Category to Key Storage Provider.
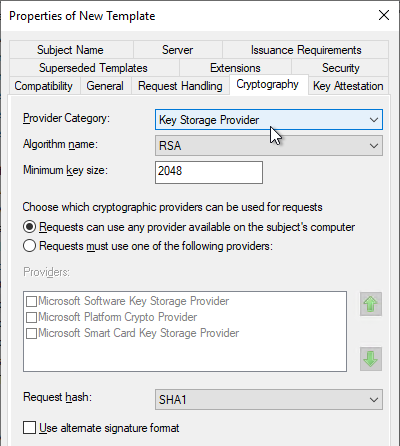
- On the Server tab, check the top box for Do not store certificates and requests in the CA database.
- Uncheck the bottom box for Do not include revocation information in issued certificates.
- On the Issuance Requirements tab, check the box next to This number of authorized signatures and enter 1 as the value.
- Change the drop-down for Policy type required in signature to Application policy.
- Change the drop-down for Application policy to Certificate Request Agent.
- At the bottom, change the selection to Valid existing certificate.
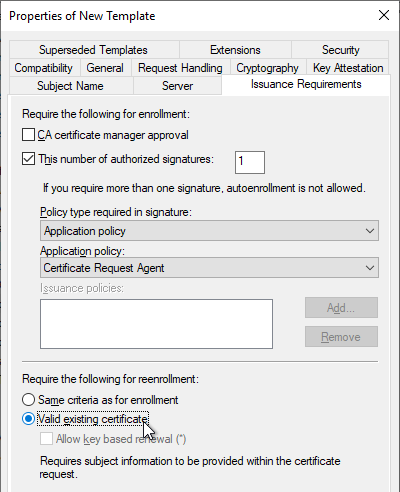
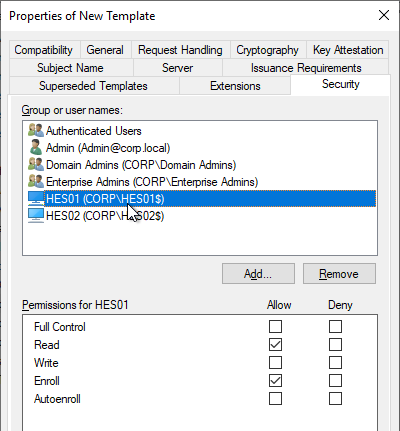
- On the Security tab, add your Horizon Enrollment Servers computer objects. This can be an AD group instead of individual servers.
- For each Enrollment Server computer object, on the bottom, check the Allow box for the Enroll permission. Click OK when done.
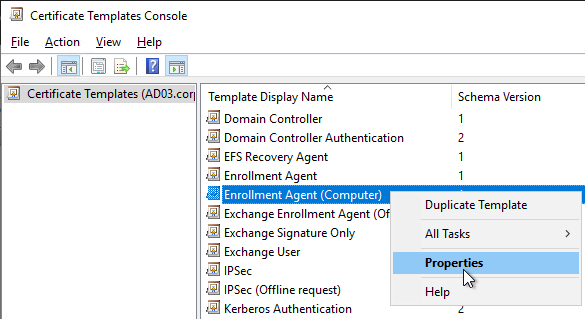
- Back in the Certificate Templates Console, right-click the Enrollment Agent (Computer) template and click Properties.
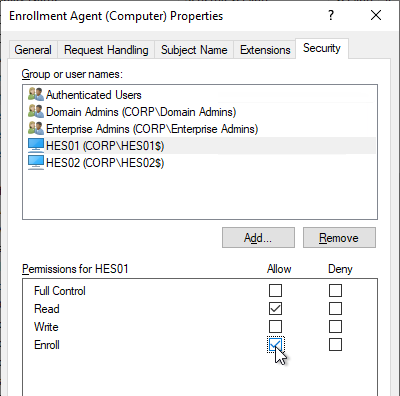
- On the Security tab, add your Horizon Enrollment Servers computer objects. This can be an AD group instead of individual servers.
- For each Enrollment Server computer object, on the bottom, check the Allow box for the Enroll permission. Click OK when done.
- Close the Certificate Templates Console.
- Back in the Certification Authority Console, with Certificate Templates highlighted on the left, if your environment has multiple CAs but this CA is dedicated to True SSO, then delete all templates from the right. Note: Domain Controllers must have certificates installed so make sure you have at least one other CA that is issuing Domain Controller certificates.
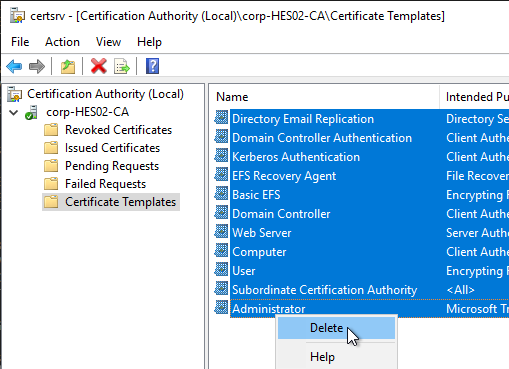
- Right-click Certificate Templates and click New > Certificate Template to Issue.
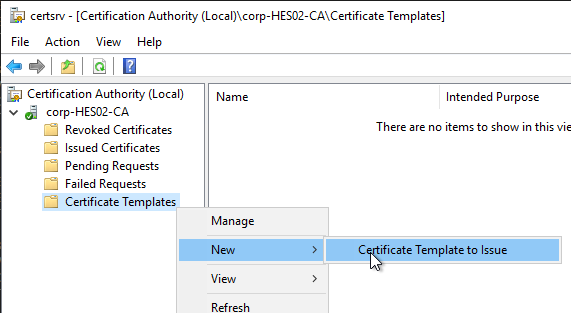
- Select Enrollment Agent (Computer) and click OK.
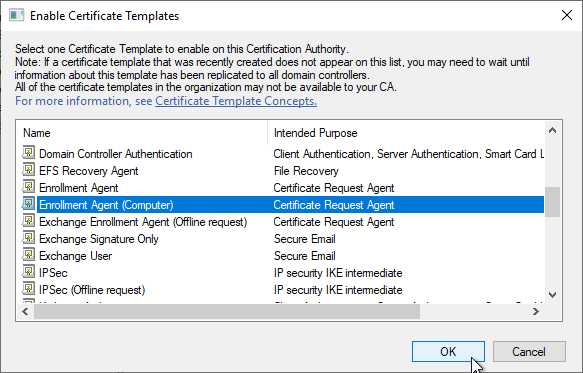
- Issue another certificate template but this time select the True SSO template.
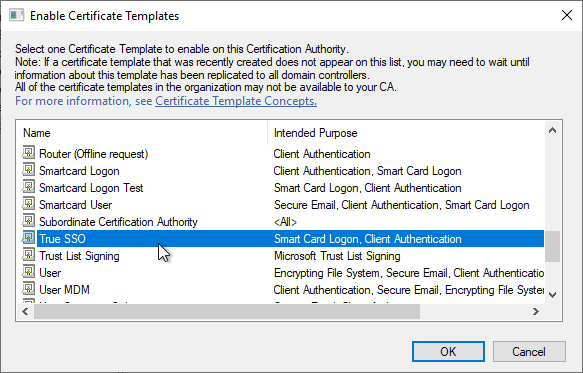
- Your CA should now show the two templates.
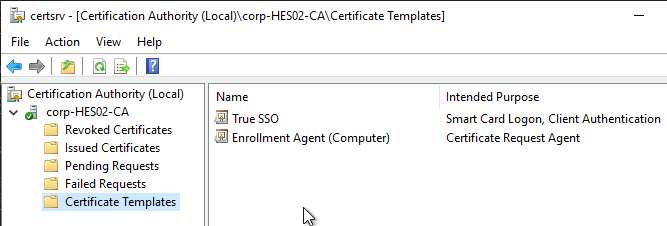
- If you have a second CA, and if it is dedicated to True SSO, then delete all templates from that CA. Then configure it to issue the same two templates.
Enrollment Server
Horizon Enrollment Server must be installed on dedicated machine(s) that don’t have any other Horizon components installed.
- Login to the new Horizon Enrollment Server that has at least 4 GB of RAM.
- Run certlm.msc.
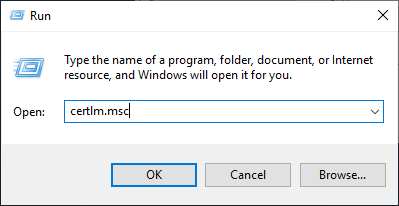
- Expand Personal, then right-click Certificates, expand All Tasks, and click Request New Certificate.
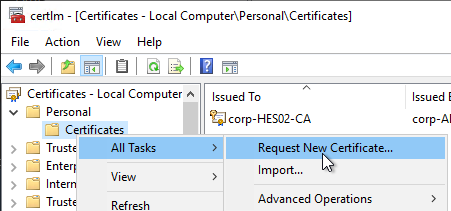
- In the Before You Begin page, click Next.
- In the Select Certificate Enrollment Policy page, click Next.
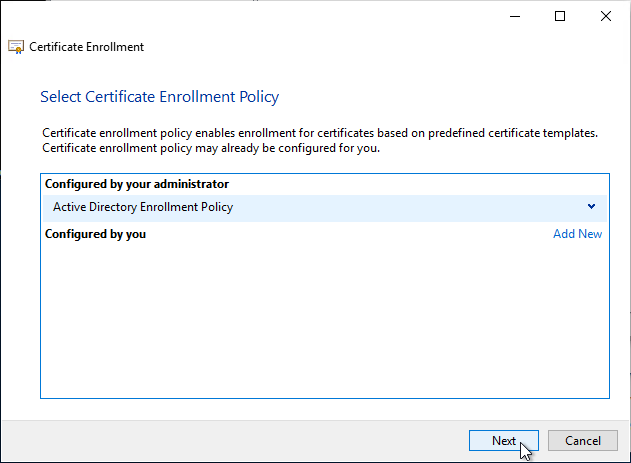
- In the Request Certificates page, check the box next to Enrollment Agent (Computer) and then click Enroll.
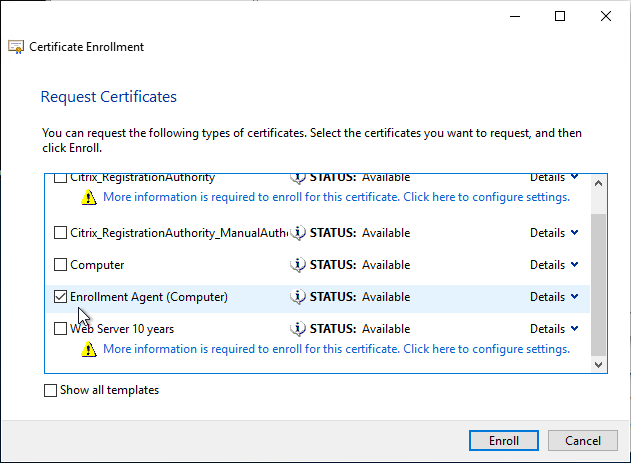
- In the Certificate Installation Results page, click Finish.
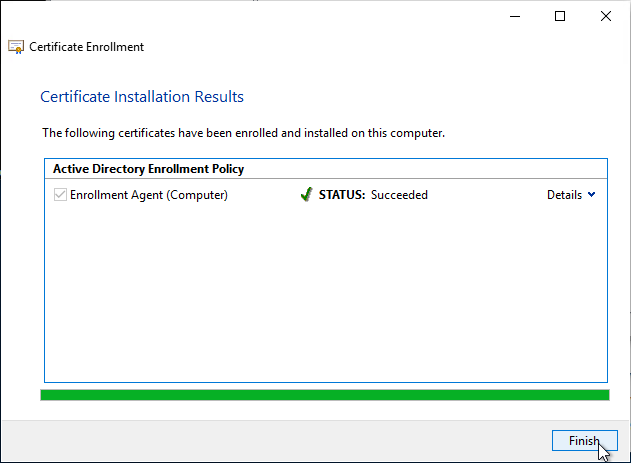
- Notice the expiration date on the Enrollment Agent certificate. Make sure you renew it before it expires.
- In the Before You Begin page, click Next.
- Go to the downloaded Horizon software and run VMware-Horizon-Connection-Server-x86_x64.exe.
- In the Welcome to the Installation Wizard for VMware Horizon Connection Server page, click Next.
- In the Destination Folder page, click Next.
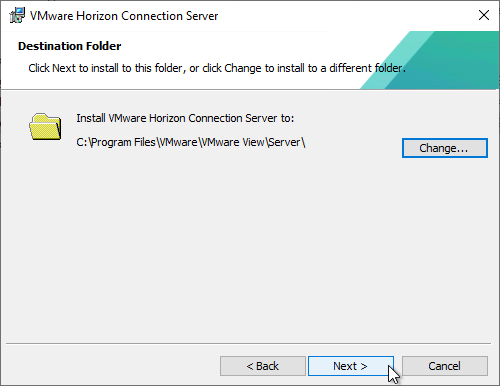
- In the Installation Options page, change the selection to Horizon Enrollment Server and click Next.
- In the Firewall Configuration page, click Next.
- In the Ready to Install the Program page, click Install.
- In the Installer Completed page, click Finish.
- If Microsoft CA is installed on the Enrollment Server, then run regedit.
- Go to HKLM\Software\VMware, Inc.\VMware VDM.
- Create a new Key named Enrollment Service.
- Under Enrollment Service, create a new String (REG_SZ) value named PreferLocalCa and set it to 1.
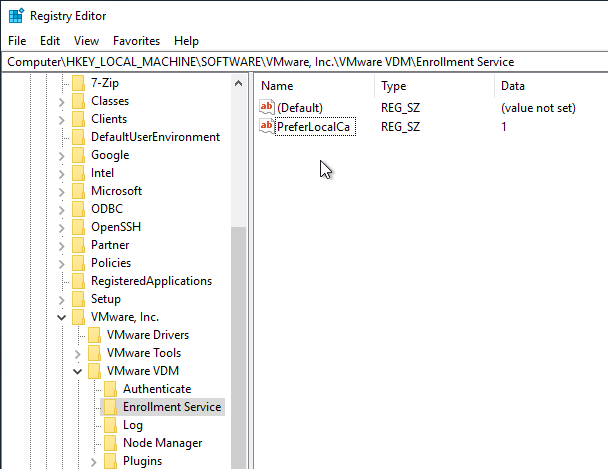
- Also add string values for UseKerberosAuthenticationToCa = false and UseNTLMAuthenticationToCa = true
- If you have two Enrollment Servers, then repeat this entire section on the other server. This includes requesting the Enrollment Agent certificate, installing the Enrollment Server software, and setting the PreferLocalCa registry value.
Trust
- Log in to a Connection Server and run certlm.msc.
- On the left, expand VMware Horizon View Certificates and then click Certificates.
- On the right, find the certificate with the Friendly Name vdm.ec, right-click it, expand All Tasks, and then click Export. All Connection Servers have the same certificate so you only need to export from one of the Connection Servers.
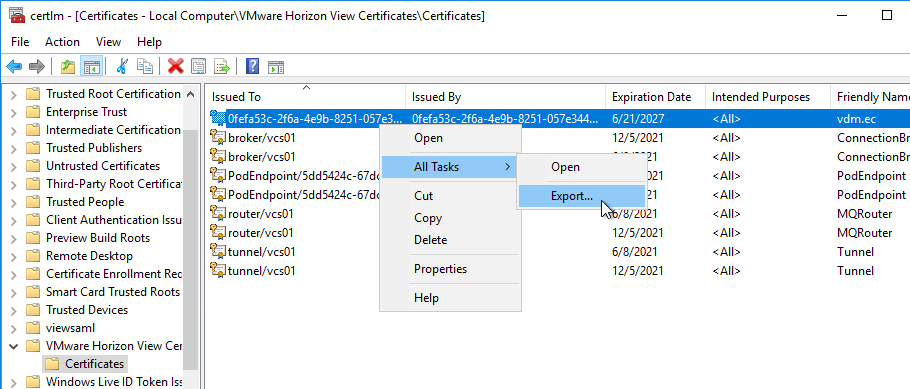
- In the Export Private Key page, select No, do not export the private key, and then click Next.
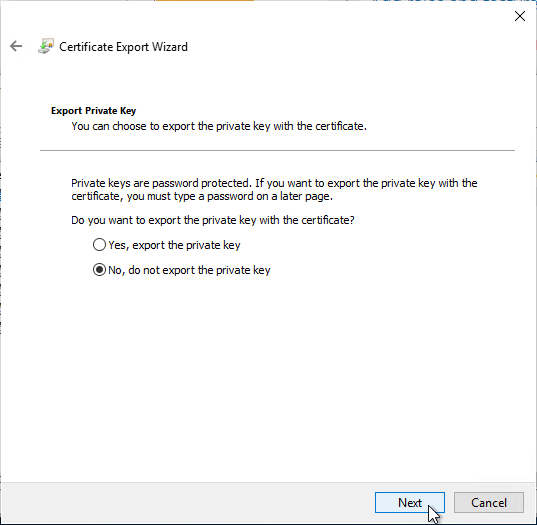
- In the Export File Format page, leave it set to DER, and then click Next.
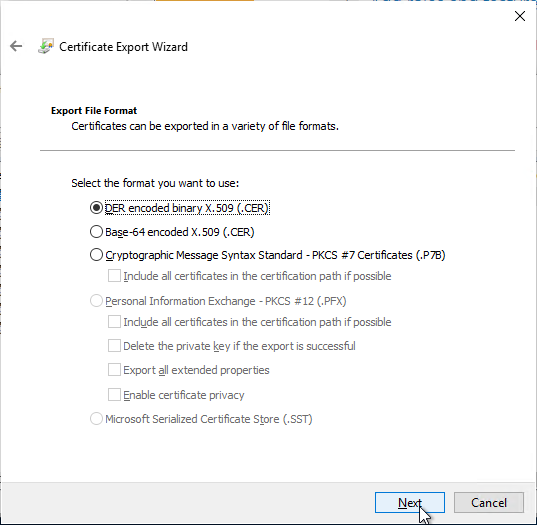
- Save the certificate to a file that you can access from your Enrollment Server(s).
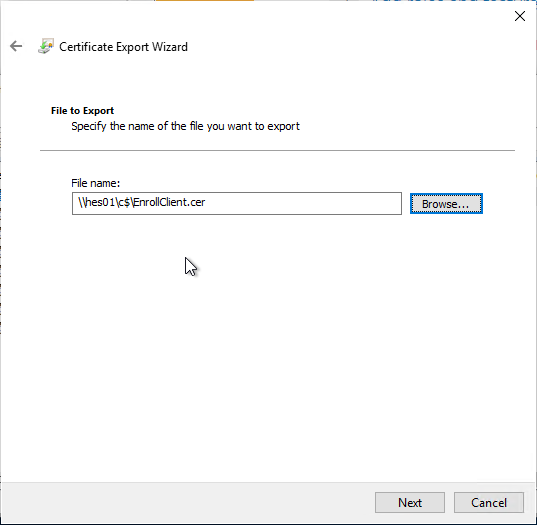
- Log in to an Enrollment Server and run certlm.msc.
- On the left, right-click VMware Horizon View Enrollment Server Trusted Roots, expand All Tasks, and click Import.
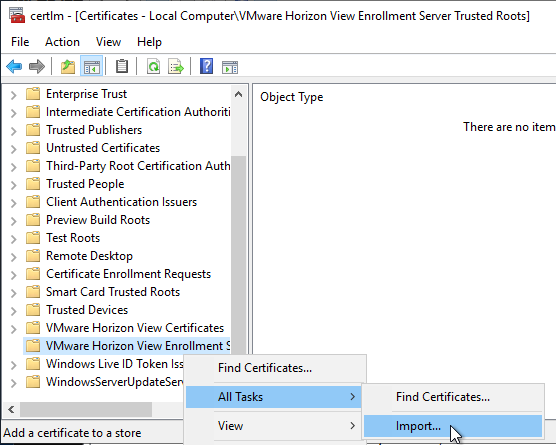
- In the Welcome to the Certificate Import Wizard page, click Next.
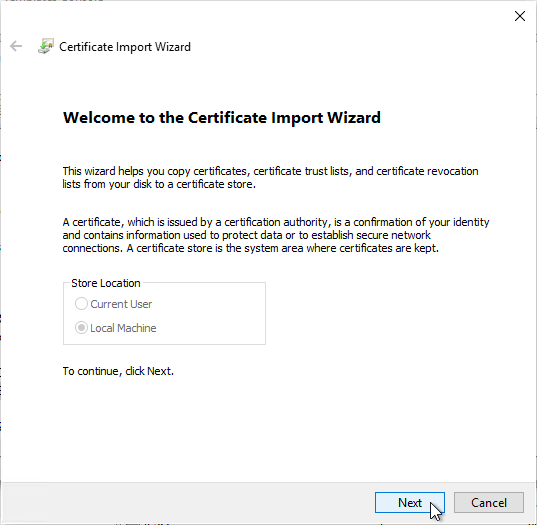
- In the File to Import page, browse to the certificate that you exported from the Connection Server and then click Next.
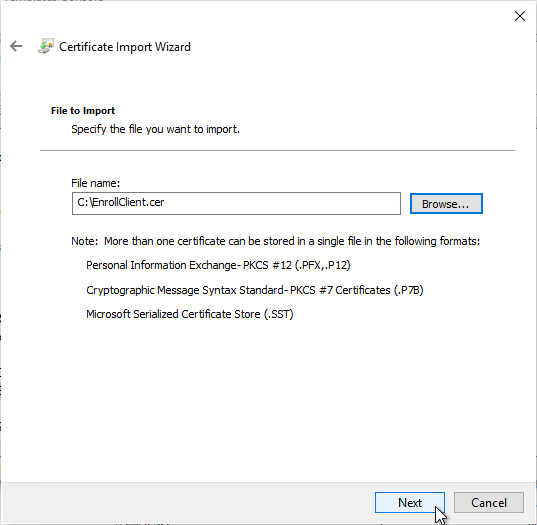
- In the Certificate Store page, VMware Horizon View Enrollment Server Trusted Roots should already be selected so just click Next.
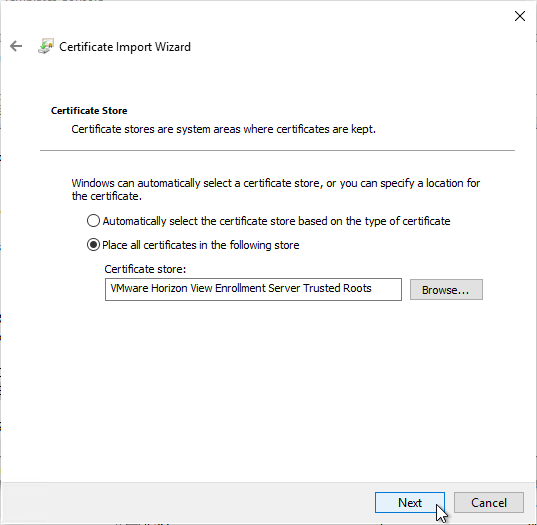
- In the Completing the Certificate Import Wizard page, click Finish.
- Repeat the certificate import process on the other Horizon Enrollment Server.
SAML to UAG
- Login to your SAML Identity Provider (IdP) and create an application for Unified Access Gateway.
- For Okta, see Omnissa Tech Zone.
- Azure AD has a gallery application to make configuration easier. Or use the following values:
- Identifier = https://*.HORIZON_UAG_FQDN.com/portal
- Reply URL (Assertion Consume Service URL = https://<HORIZON_UAG_FQDN>/portal/samlsso
- When done, it should look something like this:
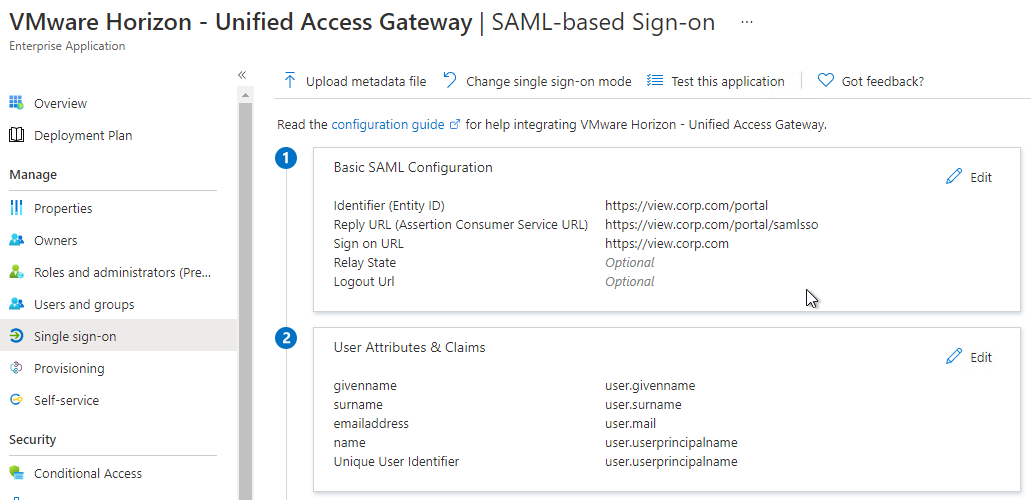
- Download the Federation Metadata XML from your Identity Provider. The Metadata Url doesn’t seem to work.
- Login to your UAG admin page (https://<HORIZON_UAG_FQDN>:9443/admin).
- Select Configure Manually.
- Scroll down to the section named Identity Bridging Settings and click Upload Identity Provider Metadata.
- In Unified Access Gateway 2312 and newer, click Upload IDP Metadata.
- Click Select in the IDP Metadata row.
- Browse to the metadata .xml file and then click Save.
- At the top of the page, next to Edge Service Settings click SHOW.
- Next to Horizon Settings click the gear icon.
- At the bottom of the page, click More.
- At the top of the page, change the drop-down for Auth Methods to SAML.
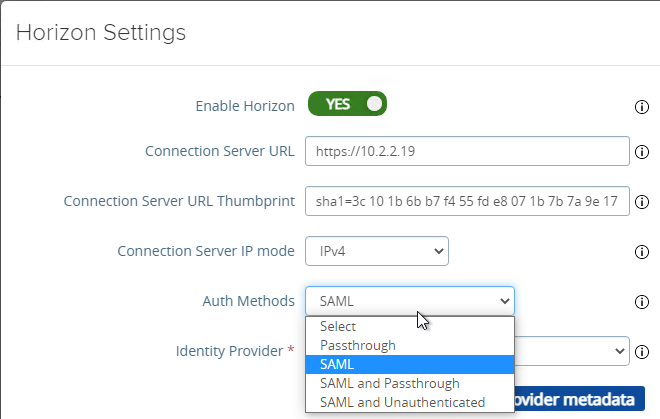
- Change the drop-down for Identity Provider to the SAML Identifier in the Metadata that you just imported.
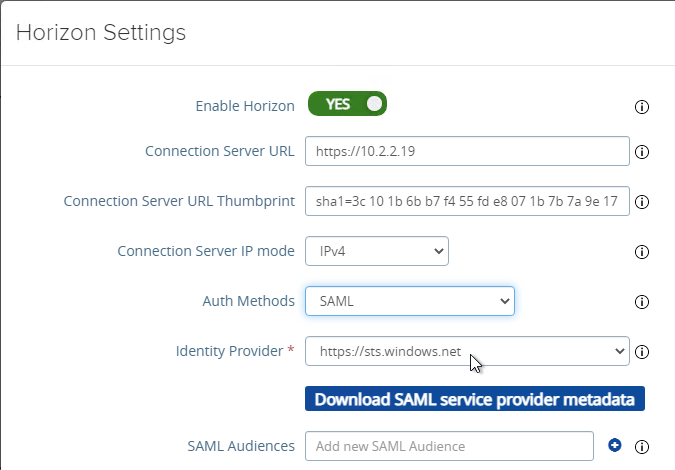
- At the bottom of the page click Save.
- Login to Horizon Console.
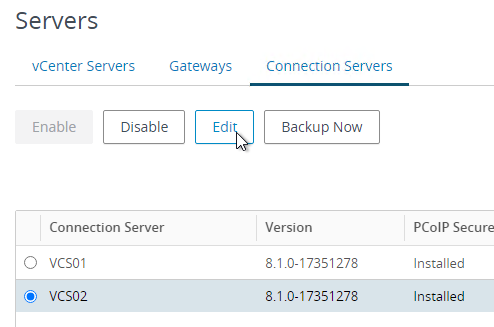
- In the left menu, go to Settings > Servers.
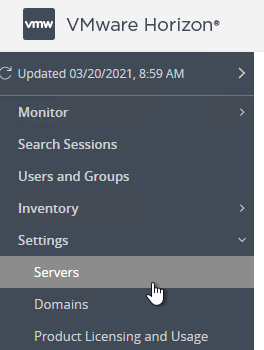
- On the right, click the tab named Connection Servers.
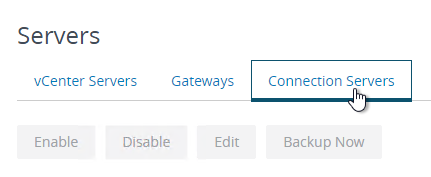
- Highlight a Connection Server that UAG talks to and click Edit.
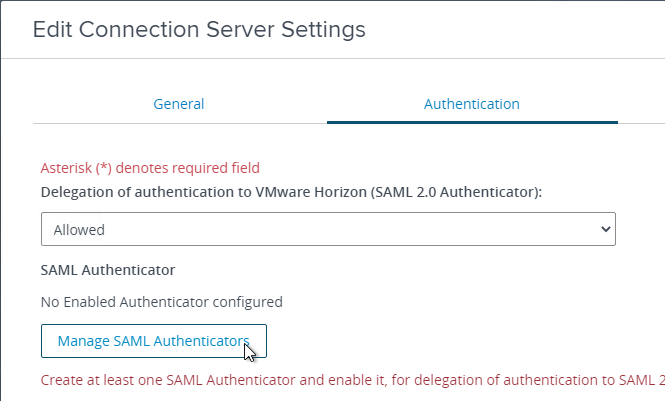
- Switch to the tab named Authentication.
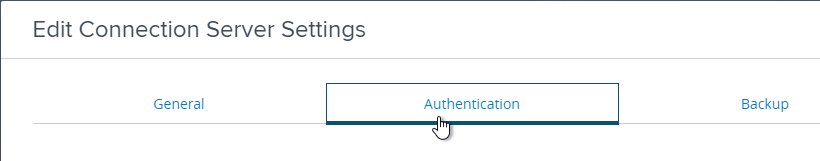
- Change the drop-down for Delegation of Authentication to VMware Horizon (SAML 2.0 Authenticator) to Allowed.
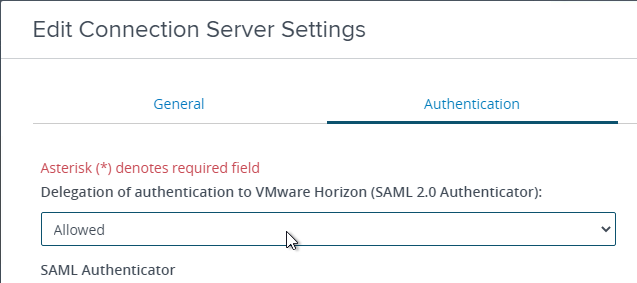
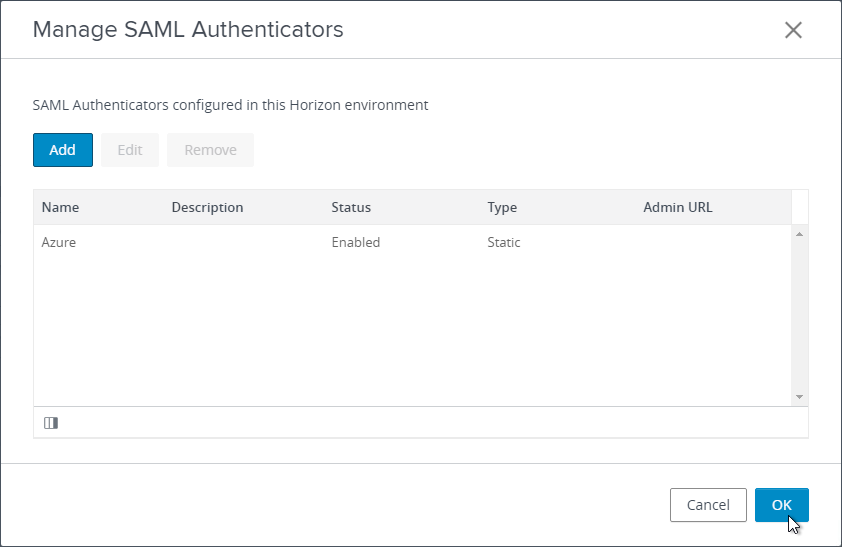
- Click the button named Manage SAML Authenticators.
- Click Add.
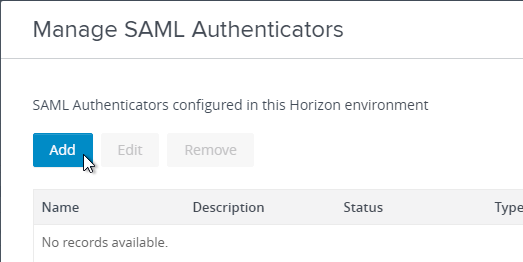
- Change the selection for Type to Static. Dynamic seems to only be valid for Omnissa Access.
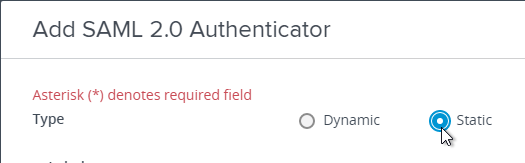
- Go to your Metadata .xml file and edit it with a text editor. Then copy its contents to your clipboard.
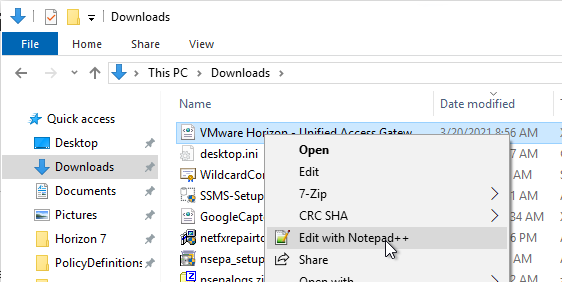
- Back in Horizon Console, in the SAML Metadata field, paste in the contents.
- Give your SAML 2.0 Authenticator a name and click OK.
- Click OK to close the Manage SAML Authenticators window.
- Edit other Connection Servers that UAG talks to and go to the Authentication tab.
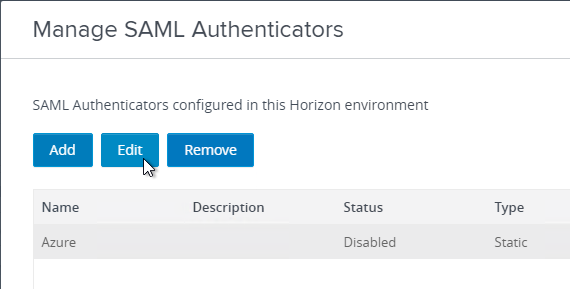
- Set SAML 2.0 Authenticator to Allowed and then click the Manage SAML Authenticators button.
- The previously created SAML Authenticator should already be there so just click Edit.
- At the bottom, check the box next to Enabled for Connection Server and then click OK. Repeat on any other Connection Server that UAG talks to.
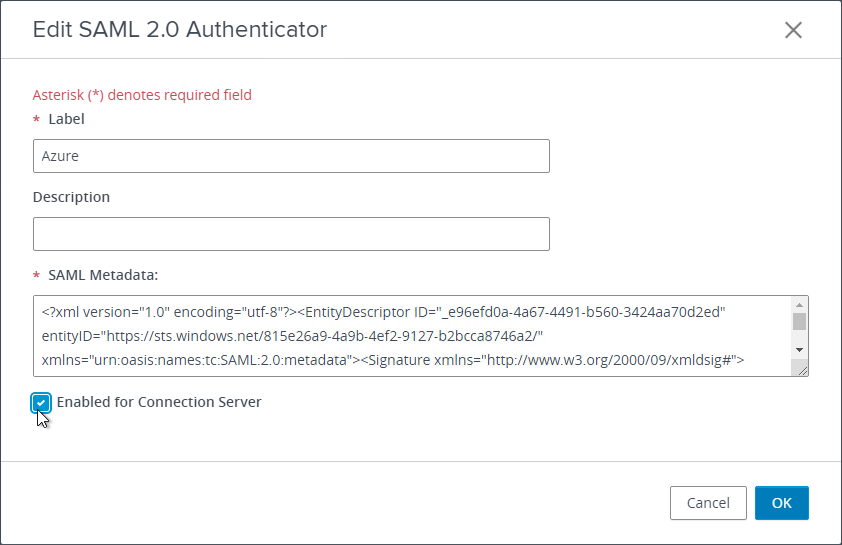
- In Horizon Console, if you go to Monitor > Dashboard and then click VIEW in the System Health section.
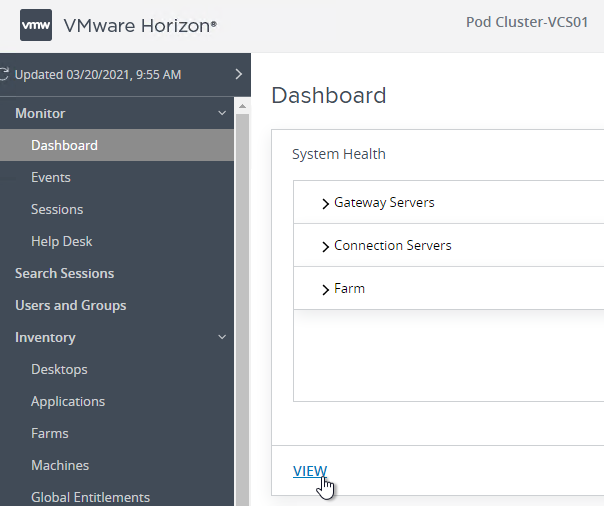
- On the left go to Other Components. On the right go to the tab named SAML 2.0. You should see your SAML Authenticator.
Enable True SSO
Login to one of the Connection Servers and open a Command Prompt as administrator. The commands in this section have case sensitive parameter names. These commands are vdmutil, not vdmadmin.
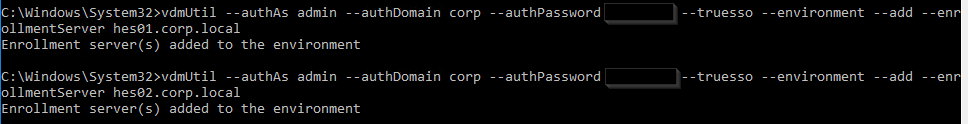
Run the following command to add each Enrollment Server. Notes:
- For the
--authPasswordfields, you enter"*"(with quotes) to be prompted to enter the password instead of specifying it at the command line. --authAsfields do not include the domain name since domain is a different field.
vdmUtil --authAs admin-username --authDomain domain-name --authPassword admin-user-password --truesso --environment --add --enrollmentServer enroll-server1-fqdn,enroll-server2-fqdn
Run the following command to see the available certificate authorities and certificate templates for a particular domain.
vdmUtil --authAs admin-username --authDomain domain-name --authPassword admin-user-password --truesso --environment --list --enrollmentServer enroll-server-fqdn --domain domain-fqdn
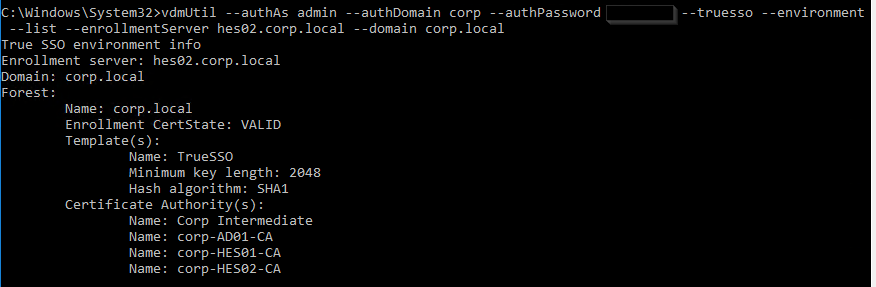
Run the following command to enable the Enrollment Servers for a particular domain. This syntax configures the Enrollment Servers as active/passive (failover). Note: certificateServer is the CA name from the previous command and not the server’s FQDN.
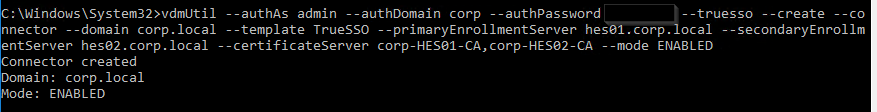
vdmUtil --authAs admin-username --authDomain domain-name --authPassword admin-user-password --truesso --create --connector --domain domain-fqdn --template TrueSSO-template-name --primaryEnrollmentServer enroll-server-fqdn --secondaryEnrollmentServer enroll-server-fqdn --certificateServer ca1-common-name1,ca2-common-name --mode enabled
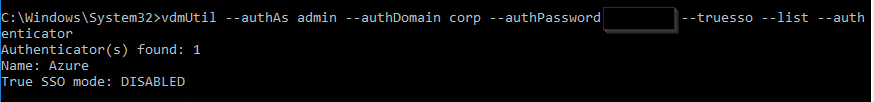
Run the following command to see the SAML Authenticators configured in Horizon Console.
vdmUtil --authAs admin-username --authDomain domain-name --authPassword admin-user-password --truesso --list --authenticator
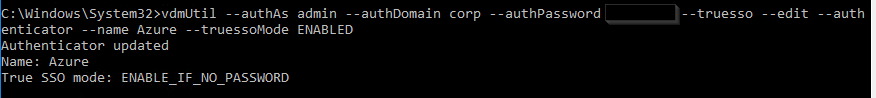
Run the following command to enable True SSO for a particular SAML Authenticator. Enter either ENALBED or ALWAYS.
vdmUtil --authAs admin-username --authDomain domain-name --authPassword admin-user-password --truesso --authenticator --edit --name authenticator-name --truessoMode {ENABLED|ALWAYS}
For more info, see Command-line Reference for Configuring True SSO at Omnissa Docs.
If you prefer to load balance your Enrollment Servers instead of active/passive, do the following:
- On a Connection Server, run adsiedit.msc.
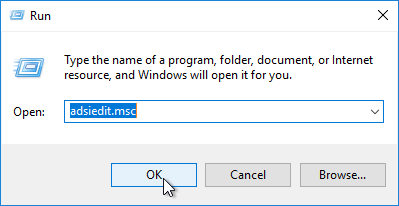
- Change the Connection Point to dc=vdi,dc=vmware,dc=int.
- Change the Computer to localhost and then click OK.
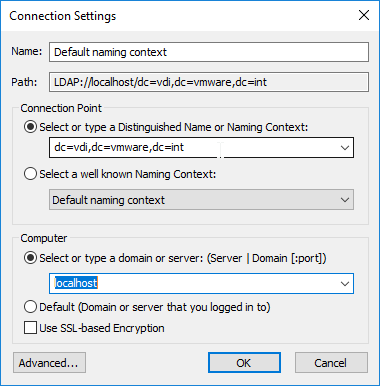
- On the left, expand Properties, and then click Global.
- On the right, double-click Common.
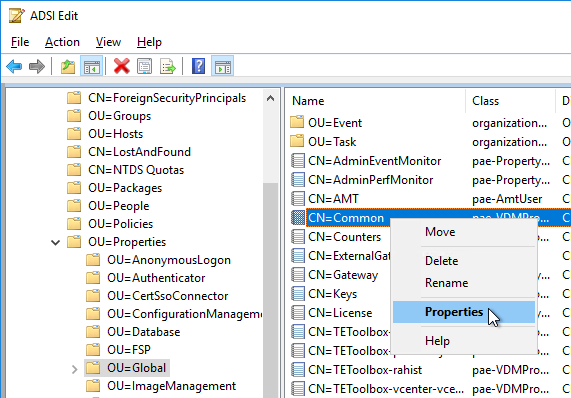
- Find pae-NameValuePair in the list and Edit it.
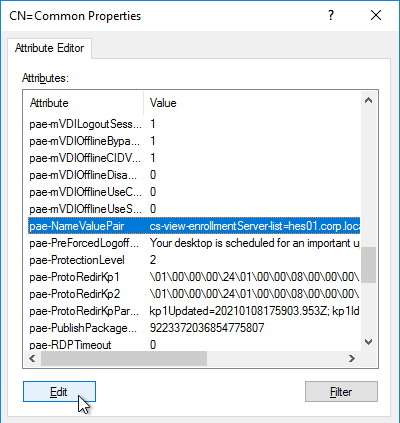
- Enter cs-view-certsso-enable-es-loadbalance=true and then click Add.
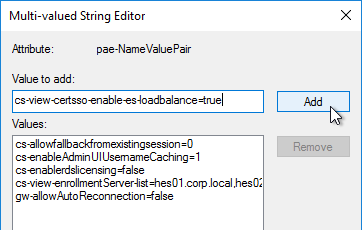
- Click OK a couple times to close everything.
You can view the status of True SSO in Horizon Console.
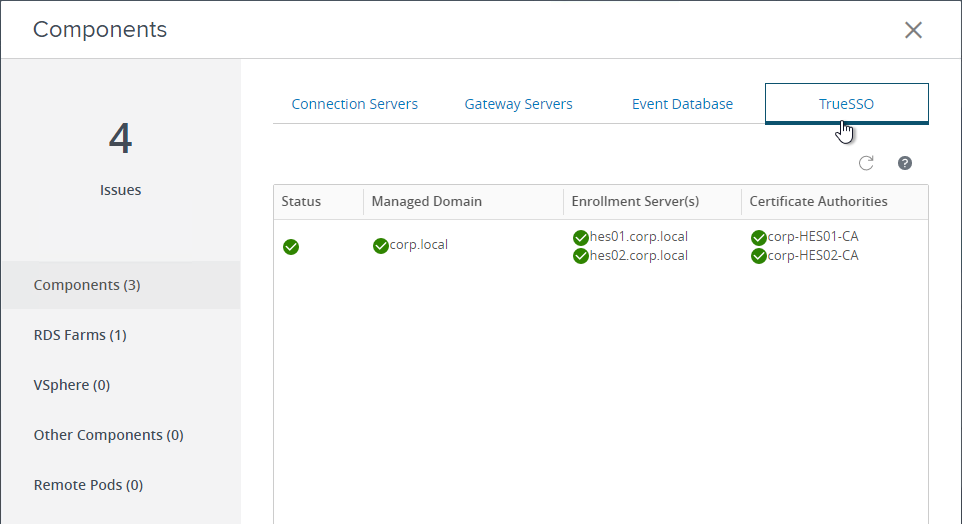
- In Horizon Console, go to Monitor > Dashboard and on the right, in the System Health section, click VIEW.
- With Components selected on the left, on the right is a tab named TrueSSO.
Is there anyone that could help with the error “Unable to save permission changes on Copy of Smartcard. A referral was returned from the server.”? I get this when trying to add the enrollment server computer object during the Certificate Template section- step 18.
Thanks for these instructions. Very helpful.
I had to do one thing slightly differently. In the TrueSSO certificate template, I also had to give access to the Connection Server on the Security tab. If I only gave access to the Enrollment Server then when I ran the vdmUtil command to add the connector template I got an error saying “connector template is not present on the primary enrollment server”.
hey
I done all configuration as per your above documents , I am using UAG +Ping fed+ Saml 2.0 configuration . All configuration show properly view dashboard and es_diag but still it prompt user name /password twice , Where to look I am strauggle on this last 10 days ..
Thanks
Do you have the Remote Desktop GPO setting to Always Prompt for Password? Do you have any credential handlers (e.g, Imprivata, Duo ,etc.) installed on the Horizon Agent machine?
I dont see GPO having issue , it was working properly with Radius authication . We are using Pingfedaration
Maybe there’s something in the VDM logs on the Horizon Agent machine. Look in C:\Programdata\VMware\VDM\logs.
Anything in Event Viewer showing certificate errors when doing authentication to the Domain Controllers? All Domain Controllers must have SSL certs. All Domain Controllers must trust the True SSO certificates and be able to access the Certificate Revocation Lists.
Send Cert-Request(s) to the enrollment service:
EnrollmentInterface::SendMsgToEnrollmentPlugin(SubmitRequest) begin
Call to CertEnroll failed: Error Verifying Request Signature or Signing Certificate The revocation function was unable to check revocation because the revocation server was offline. 0x80092013 (-2146885613 CRYPT_E_REVOCATION_OFFLINE) – 0x0000000080092013 (The revocation function was unable to check revocation because the revocation server was offline.) – ErrorCode = 2148081683 (0x0000000080092013), 1
EnrollmentInterface::SendMsgToEnrollmentPlugin(SubmitRequest) end
SubmitRequest Failed
Response ErrorCode = “-2146885613”
I see following error when I run es_diag –
ErrorText = “Error Verifying Request Signature or Signing Certificate The revocation function was unable to check revocation because the revocation server was offline. 0x80092013 (-2146885613 CRYPT_E_REVOCATION_OFFLINE) – 0x0000000080092013 (The revocation function was unable to check revocation because the revocation server was offline.)”
FailureReason = “SubmitFailureMayRetry”
Is your Root CA offline? If so, then you might have to power on the Root CA so it can update its CRL.
Need help i trying configure TrueSSO with help your above documents , All setting proper as mentioned but getting issue .
C:\Temp>es_diag.exe /enrollmenttest /esNAme:MyHEN /certauth /domain:mydomain /caserver:CER03VM /requester:myuser /template:TrueSSO /debug
Execute EnrollmentDiags::EnrollmentTest:
Connect to the Enrollment Service: MyHEN
Failed to connect channel: certificaste auth failed
Failed to connect a channel to the Enrollment Service.
The Certificate used to Authenticate to the ES may not be trusted.
For more information please see the Horizon View log-file on this system and on the Horizon View Enrollment Server.
Is it otherwise working? Did you run it from the connection server so it can try certauth using the certificate on the connection server?
Carl, your instructions are the best! You’re a life saver. Thanks for all you do!
We are moving to Azure AD as SAML Idp.
Have configured UAG with SAML and deployed TrueSSO and linked Connection Server.
After authenticating to Azure, the SSO to RDS farm does work (Horizon successfully logs user in to RDS host), but the SSO to the cloud apps (ServiceNow, WorkDay, M365) does not work. I am prompted for creds for any cloud /Saas app.
If i set UAG with SAML+Passthrough, cloud app SSO does work in RDS farm, but of course this cases prompt for AD creds after Azure AD auth which we want to avoid.
Any suggestions?
Is single sign-on enabled in Azure AD Connect so internal users can authenticate to Azure AD using Kerberos? https://learn.microsoft.com/en-us/azure/active-directory/hybrid/how-to-connect-sso
If you instead doing Hybrid Azure AD join, then you might need certificate-based authentication. https://learn.microsoft.com/en-us/azure/active-directory/authentication/concept-certificate-based-authentication
Do I need really need to installed Certificate Authority enrollment server or Just need make registery mention in your article & import CB certificate ?
You can use a Certificate Authority that is installed on a different server.
Thanks , I have already multiple enrollment servers I can use or I need setup dedicated Horizon enrollment server .
Enrollment Server is something you install from the Connection Server installer. You need at least one Enrollment Server. Then you configure it to use a Certificate Authority server. I normally put Enrollment Server on a dedicated VM.
Why want sperate horizon enrollment server as we have microsoft CA /enrollment server there
Are you asking about VMware Horizon Enrollment Server? It’s a VMware install. It needs to be installed somewhere.
Hey Carl, awesome writeup. I was wondering if you were able to get SAML working just between the UAG and the Connection server? As in using the UAG as the SAML IDP, downloading that metadata and pasting it over on the Connection server.
I’ve done the above and then set the UAG to require x509 auth. I can sign into the UAG just fine using a cert on a smartcard but when it goes to pass to the Connection Server I get an error. It looks like the connection server can’t understand what the UAG is sending it.
Hello, I just wanted to know when configuring SSO with UAG SAML; if people join through the Horizon Client, they get a pop up to the windows display login through a web browser. Is there any way to avoid that and make it interactive through the horizon client instead?
I’m leaving an image here for a similar problem I had with Cisco AnyConnect and we managed to solve it, all we want is to display the login through the horizon client…
Example: https://imgur.com/EM5gYHH
Thank you in advance, this blog helped me a lot to learn about horizon
I don’t think Horizon Client has an embedded HTML viewer, so it uses the browser instead.
This is by design, it need a browser to authenticate to azure
Hi Carl,
Thank you for this post.
If we use true sso and saml the users are prompting the credentials. Do we have to still set a registry?
Best regards,
Miguel
There’s an RDP GPO setting called Prompt for Password or something similar. Is that enabled?
Hi Carl,
we disabled “Always prompt for password upon connection”. Unfortunately the prompte remains (https://docs.vmware.com/en/VMware-Horizon-7/7.13/horizon-remote-desktop-features/GUID-611FBE11-3D42-411F-9F2B-6AA3D86401DC.html)
On the point -> SAML to UAG Federation Metadata XML URL is not working. The encoding of the file for the URL “App Federation Metadata Link” results in a file in “UTF-8 BOM” and for “Federation Metadata XLM” in “UTF-8”. Both are accepted by the UAG without complaint (configuration is saved successfully), but redirect to Azure only in UTF-8.
Once again, Carl saves my day. Could not figure out why my second connection server was missing the TrueSSO configuration and why I was unable to add the enrollment servers to the 2nd CS. Turns out I forgot to add them first, going through the clearly outlined steps made me realize I forgot to add them first. Thanks once again!
Hello Carl.
Thanks for the well-documented write-ups. Please I have a question.
1. when i configured the UAG application in Azure i used the VMware UAGs premade application. Do i need to create a customized application for UAG?
2. I configured the true SSO but when i checked the dashboard now, it showed no record of True SSO being configured. Please assist
1. If the premade app works, then go for it.
2. Does True SSO work? Maybe you missed some commands.
The Pre made app worked perectly for me on a fresh install. SAML also, worked when using your instructions. My question though is that I have 2 connection servers, one for inside, and one for out. Out uses UAG. When I get to stage “Enable Tru SSSO” in the instructions, it says to run the command on “one of the Connection servers.” Does this mean it will be enabled on both, or just the server I run it on? Internaly I do not use UAG, and users are able to SSO direct to Connection Server. I was hoping to only enable this on the Connection server that uses UAG.
Thank you again for you time.
The command line tool is included with the installation of Connection Server. Running the tool modifies LDAP so it should replicate to the other Connection Servers.
In Horizon Console, go to Servers and edit a Connection Server. On the Authentication tab edit the Authenticator. There’s a check box if the Authenticator is enabled on the selected Connection Server or not.
So, If dont enable on SAML Auth on the Connection Server, the settings do not do anything… ok… I folowed your directions, and everything just works. as long as you go step by step. Also, its a good idea to have Enrollment server spun up before you start. That way you dont have to jump around document.
Thank you Again.
Hello Carl we have implemented True SSO following this and it worked well.
I have a issue currently when logging in. I will go to our site and enter my credentials and approve the MFA and then the webpage goes to…….https://login.microsoft.com/kmsi
It spins on that webpage until it will eventually time out with a horizon landing page error “authentication has timed out” I will hit ok to the error and then I can click into horizon and it lets me in like it should have originally done. Also if I stop Microsoft spinning page from above and refresh it does the same thing and will let me in.
I am unable to see anything in Azure logs or horizon logs. Have you seen this?
Hi Carl – Everything working great with our 7.13 env. What I would like to know is that if I can utilize the same pair of Enrollment servers for a different Horizon environment that I have built. Export/Import cert and go on from there?
I haven’t tried that.
Jeff we are in the process to implement the same ( same pair of enrollment servers for a completely different horizon environment within the same Active directory domain). Any inputs from you is much appreciated.
Carl – Great Article
Question – I have 1 Azure tenant, 2 AD Domains (Separate Forests) – 1 Prod & 1 External. Prod is linked to Azure. Set everything up based on this article all is working. Now I need to connect my 2nd Domain that is not part of Azure. Do I need to setup a Second UAG Server, not enable SSO and connect it to my connection Servers and just tag it (not sure if I need to tag or not)? This way the external users can go to a different URL, hit the secondary UAG and get to the second domain desktops.
That looks right.
I followed everything and the Dashboard of the Connection servers shows green across the board for TrueSSO, but I am getting this error when logging into a desktop:
The attempted logon is invalid. This is either due to a bad username or authentication information. An untrusted certificate authority was detected while processing the certificate used for authentication.
Any idea what I need to do? I had an existing CA and I added the ENROLL server as a new Enterprise CA as a Subordinate.
Jim
Is your Microsoft CA in Enterprise Mode?
Is this cross-domain? Are the CA root certs in the PKI Enterprise certificate stores for smart card authentication?
Yes….the CA is in Enterprise Mode.
This is not cross-domain.
I believe so, but how would I double check that last question?
Jim
https://learn.microsoft.com/en-us/troubleshoot/windows-server/windows-security/import-third-party-ca-to-enterprise-ntauth-store
Did you get this resolved? I have the same error.
Hi all,
i have the exact same issue … if i use es_diag to request a certificate as end user on a workstation i receive the certificate, i also checked PKI View and the certificates are present , i work with a Root Enterprise CA and 2 Sub CA’s … advice would be appreciated … , thanks !!
We are using Windows CA’s, and I confirmed the CA’s certs are listed in the domain controller’s “Intermediate Certificate Authority” in certlm.msc.
On a few users/child-domains they receive: “The attempted logon is invalid. the is either due to a bad username or authentication information. An untrusted certificate authority was detected while processing the certificate used for authentication.”.
I can run es_diag from the enrollment server and it works fine/receives no errors.
Any ideas?
Are the root certificates that issued the True SSO certs deployed to each domain?
I believe I’ve found the issue. Testing with the es_diag.exe tool, running the following command first:
es_diag.exe /enrollmenttest /domain:example.com /requester:example\test.user /template:TrueSSOCert /caserver:example-horizonsso01-ca /certfile:testuser.cer
To test and generate/save the virtual smart card login certificate. This command requested 1 cert and successfully received and saved the cert from the CA.
Then running the following command to test the login:
es_diag.exe /LogonTest /CertFile:testuser.cer
Would return: LsaLogonUser failed – Logon Failure: the user has not been granted the requested logon type at this computer
Going off some old memory I had, I checked the local groups and the user was not a member of any group in the builtin Remote Desktop Users group under Computer Management.
I added the entitlement group to the builtin Remote Desktop Users group and re-ran the “es_diag.exe /LogonTest /CertFile:testuser.cer” command the received:
Successfully performed S4U x.509 Certificate logon
Updated Group Policy to push this out and am currently awaiting feedback from users.
Great article! I struggled a bit trying to figure the following error:
Failed to create connector
Connector certificate servers are not present on the primary enrollment server
It turns out I misinterpreted the vdmutil command for the –certificateServer parameter. This should not be the fqdn and should be the name that appears on the vdmUtil –truesso –environment –list command.
Hopefully my struggles will help someone else out there.
I’ve made the same mistake, so I just added a note to the text. Thanks for the feedback.
We just resolved our issue with this as well today and it was that we populated the CAServer parameter with FQDN so we got the error. The VMware documentation does say CA Common Name – not FQDN, but that’s easily to overlook!
Hi Carl,
I’m trying to launch Citrix workspace using passthrough SSO (enabled on app when installed) from a Horizon VDI (windows 10) and it always prompts me for credentials. On a standalone workstation, the passthrough happens without prompts. Does the horizon enviroment required to setup an Enrollment server with TrueSSO configured?
Does the Horizon Agent machine ask you for your Windows password? If so, then Windows should have your password for CWA. If you SAML without Horizon knowing your password, then CWA can’t do SSO.
When i click the weblink to the Horizon portal, it prompts me for credentials (AD) and then it takes me to the “APPs” tab when i see the VDI and click on it. It then launches the VDI without being asked to log into Windows.
the issue exists on the master VDI host, without launch through the horizon portal as well.
When you installed CWA, did you choose the pass-through auth (single sign-on) option? Is ssonsvr.exe running in your session? Right-click the CWA icon, click Advanced Preferences and run the Configuration Checker for SSON.
Yes. As mentioned before, SSON was included at install of CWA and the checker tests are successful.
I just tried Workspace app on a Horizon Agent with a Blast connection, and it worked. Did you add the StoreFront URL to the Local Intranet zone?
Hi !
First, thank you for the great documentation, helped a lot.
I have one problem, the connexion server does not seem to understand that the user is part of on-premise groups.
So if some pools are entitled to AD Groups, when the user part of that group connect trough saml, he doesn’t see any pools. But if I entitle directly the user, it works.
Sorry for my english, I hope it’s clear
Having the same issue in our DRaaS environment. Horizon TrueSSO health is all Green in the Admin Console. Time synchronization and certificates are good as well. Any ideas on how to resolve this?
I dont know if this applies to your configuraton, but I remember seeing in the docs that SAML does not support nested groups, Members have to be direct members of AD group.
I’ve finally figured out,
you need to put the VCS computer account in the Windows Authorization Access group
In some cases your users have a bad security settings
https://kb.vmware.com/s/article/52849 and https://kb.vmware.com/s/article/2103964
Hi Carl, thank you for this great documentation. Question I have is as follows; when accessing the horizon client it redirects to Azure for authentication. The browser opens and loads the horizon client. But the browser session stays open with “Loading Horizon Client” . Is it possible to close this site after a couple of seconds? at this moment the user needs to close this by hand
Not that I know of.
Here’s one for you. First, I’ve used your site to set this up. SO MUCH BETTER THAN VMware’s documentation. Thank you soooo much. Here’s our newest challenge before deployment.
We have multiple Azure tenants and pulling from the same virtual desktop pools. When we setup the SAML w/AZURE and test with our corporate domain it works perfectly.
HOWEVER, when we do the same thing for a different tenant it fails. We created the VMware app within Azure and, of course, we get a different XML ID. The issue we see is the UAG only allows for one XML upload so the redirect for authentication doesn’t work. Any thoughts?
Here’s the comment from my fellow tech as we work on this.
-Test: Add a new UAG and point to the same “MFA enabled” connection server
-Result: FAIL
-Next step: Need to deploy a new connection server to pair it with the new UAG.
-Emotional status: VMware sux
Have you tried VMware Access (VMware Identity Manager)?
When setting UAG to only use SAML, some users in Horizon console can not see apps or desktops that are assigned to them by using AD groups. They only see apps/desktops that are assigned directrly to them.
This however is not a problem when using saml and passtrough.
TrueSSO all green and works for other users.
Any idea how to troubleshoot it?
have you ever figured this out ? I have the same problem
First thank you for all your documentation. Very helpful. Second we are running into an interesting issue and curious if anyone has any suggestions.
User A opens and logins into VMware Horizon Client on shared(kiosk) workstation
Successful through MFA prompt from Azure
User completes work in virtual desktop and closes VMware.
User B opens VMware Horizon on shared (kiosk) workstation. (Never puts in username or Pw)
Virtual Desktop is automatically launched with User A’s credentials.
I’m guessing a cookies issue. Does it work if you close the browser?
You are absolutely correct. I have been doing some testing and clearing history, cookies, closing the browser does correct it. Just a moment ago, made a CA policy to require reauthentication of MFA after 1 hour of nonuse in Azure. If anyone has any better suggestions that do not rely on the user clearing/closing browser I am all ears.
UAG has a setting to Always Force SAML Auth. Does that work?
Hey Carl, great guide. I was in a bit of a rush getting this up and running so I implemented a single Horizon Enrollment Server thinking I could deploy a second at a later time. However, I’m having trouble. I was able to get the second ES added but I can’t seem to edit the connector to utilize it as a secondary Enrollment Server. Here’s the command I’m attempting to use:
vdmUtil –authAs username –authDomain domain –authPassword “*” –truesso –connector –edit –domain domain-fqdn –secondaryEnrollmentServer enroll-server2-fqdn
I’ve tried other variations as well; including the original primaryEnrollmentServer, specifying the certificateServer, I’ve even tried changing the mode (disabled) but nothing seems to work. The result is always:
Failed to update connector
Encountered unexpected error during execution.
Any help would be greatly appreciated.
I got it work in what I think is a slightly unorthodox method: deleted the original, single Enrollment Server connector and created it again with all Enrollment Servers (in my case, just two). I don’t know if disabling the authenticator was necessary but I figured it wouldn’t hurt.
vdmUtil –authAs admin-username –authDomain domain-name –authPassword “*” –truesso –edit –authenticator –name Azure –truessoMode DISABLED
vdmUtil –authAs admin-username –authDomain domain-name –authPassword “*” –truesso –delete –connector –domain domain-fqdn
vdmUtil –authAs admin-username –authDomain domain-name –authPassword “*” –truesso –create –connector –domain domain-fqdn –template TrueSSO-template-name –primaryEnrollmentServer enroll-server-fqdn –secondaryEnrollmentServer enroll-server-fqdn –certificateServer ca1-common-name,ca2-common-name –mode ENABLED
vdmUtil –authAs admin-username –authDomain domain-name –authPassword “*” –truesso –edit –authenticator –name Azure –truessoMode ENABLED
All is well now. Thanks again for your terrific resources.
Nice.
Hi Carl thanks for this.
What would be the firewall requirement from UAG to Azure?
Are you asking about SAML? If so, then all communication is performed by the user’s browser.
The only exception is SAML metadata. The UAG would need to be able to access the SAML metadata URL.
Hi Carl
We are using SAML & TrueSSO and its working for initial login to VDI desktop. Horizon client connects to UAG and then redirects to idp website. auth is working and Horizon client is connecting to pool and TrueSSO enables login to vdi session without any additional input needed.
but if the user locks the vdi session (closes the lid of notebook, windows+L, Screensaver, what ever) and the user unlocks the physical device, the vdi sessions stays locked on the login screen. the horizon client performs not an unlock of the vdi session…
can you tell me, if this behavior is as expected or if this should work or could work with some tweaks?
regards tohil
What version of Horizon? 2111 mentions True SSO unlock. But I think it’s only for Workspace ONE Access. https://docs.vmware.com/en/VMware-Horizon/8%202111/rn/vmware-horizon-8-2111-release-notes/index.html and https://docs.vmware.com/en/VMware-Horizon/2006/horizon-console-administration/GUID-9522ACDA-91A1-4666-BCA5-FC48777746C5.html
Hi Carl and tohil.
We have the exact same problem, as we are using Okta, not WSO Access. I’ve just been told by VMware Support that the TrueSSO unlock is only supported with WSO Access.
I just can’t live with it ! We have a case opened at Okta. I hope they will come with a more acceptable answer…
Hi Carl,
I have used the latest Horizon 8 components and was able to get this to work perfectly! So thanks for that.
I do have a strange issue, since implementing TrueSSO with AzureAD Enterprise Apps and the enrollment server my user sessions no longer show up in the connectionbroker console. I do see active sessions listed on the UAG but no longer in the CB console. I do see events in the CB showing people logging on etc but i dont see them actionally logged in on the VDI in the console. It also always says that all VDIs are available but they are all used by users.
Is this a known issue with SAML? Or is the connection broken between CB and UAG? I did re-establish the connection just to be sure.
Hi all,
How can I use Horizon 7.13.0 + Azure SSO with multiple domains?
I have 2 UAG and 1 CNS.
When I configure the SAML on CNS, with Azure SSO Metadata, I can use only with one specific domain. When I try to add another SAML configuration, CNS complain with duplicate entityID, because it’s our tenant ID.
I can’t configure dynamic SAML because CNS don’t accept “?”.
Thanks!
Hi Alexandre,
I don’t know if this will help, but I had a similar issue where I have 2 UAG and each going to their own Connection Server. I could only create one static entry within Horizon, due to the duplicate entityID, so my UAG that matched the metadata worked. The other would authenticate against Azure, but then I would get an error trying to get to the connection server. After some trial and error, I tried the FederationMetadata.xml from my tenant and both now work.
You get get the FederationMetadata.xml by going to https://login.microsoftonline.com//FederationMetadata/2007-06/FederationMetadata.xml
If you already created your static entry within Horizon, replace the metadata with the FederationMetadata.xml and it should solve your issue since you’ll only need the one static entry. After this hopefully both your UAG should start working.
Carl, thank you for these wonderful guides!
WordPress munched the URL, it should be:
https://login.microsoftonline.com/YOUR_OFFIC365_DOMAIN/FederationMetadata/2007-06/FederationMetadata.xml
We have a Horizon environment where we are trying to enable SAML SSO authentication. Currently, the SSO configuration is working when users access our Horizon environment from the outside but internally we are receiving the following message:
“This Horizon server expects to get your logon credentials from another application or server, not directly through the client login screen. If you usually access Horizon from another application, please launch that application.”
Are users connecting through UAG? If not, on the Connection Server, did you set the SAML Authenticator to Required instead of Allowed?
users are notconnecting through UAG?on the Connection Server, SAML Authenticator set to Required instead of allowed
Change it to Allowed.
If i change it to allowed, it is loading the Ad login credentials page and not getting redirected to the Saml authenticator page.like the Microsoft sign in page
Correct. If you want an actual SAML authentication flow, then users need to connect through UAG or VMware Workspace ONE Access.
Hey Carl – thank you for your instructions. Question on the True SSO used with UAG.
We have Horizon 2206 – with a UAG + Connection server – not using workspace one.
We have enabled the enrollment server, CAs etc.. but are running into the same issue
where after authenticating through our IDP – Cisco DUO.. we get the error message .
This Horizon server expects to get your logon credentials from another application or server, not directly through the client login screen. If you usually access Horizon from another application, please launch that application.
Our connection server is set to Allowed
Did you ever get this working? I am currently setting up exactly the same with Cisco Duo and getting the same error message about login credentials.
I was able to resolve this issue by changing the SAML Response setting for NameID format in my Duo configuration. I set this up in Duo using the “Generic SAML Provider” application. I resolved this issue by changing the NameID form at to:
urn:oasis:names:tc:SAML:1.1:named-format:emailAddress
Hello, I was facing the same issue and for some older users the UPN in AD was not updated to match the SSO. When I switched from .local to .com everything worked out
I face the same problem for users whose email doesn’t match upn. I’ve tried to modify saml claims in azure application, setting user.mail as uniqueID with no luck. Any idea?
Just an update that can be useful to someone. Being authenticated on azureAD via mail address, and being mapped by adconnect
ONPREM AD mail address –> AAD userprincipalname
we need to set
Unique User Identifier = user.onpremisesuserprincipalname
(both mail and userprincipalname were populated with mail, but horizon requires actual UPN to authenticate users).
Thank you! Worked like a charm. One note, becareful when adding CAs, DO NOT include your root CA. Your root CA will be listed when you run:
vdmUtil –authAs admin-role-username –authDomain domain-name –authPassword admin-user-password –truesso –environment –list –enrollmentServer enroll-server-fqdn –domain domain-fqdn
But do not include it, only Sub CAs should be used in this command:
vdmUtil –authAs admin-role-username –authDomain domain-name –authPassword admin-user-password –truesso –create –connector –domain domain-fqdn –template TrueSSO-template-name –primaryEnrollmentServer enroll-server-fqdn –secondaryEnrollmentServer enroll-server-fqdn –certificateServer ca1-common-name1,ca2-common-name –mode enabled
Hi Carl. I have used your documentation on several occasions and have always been very happy with the results. I appreciate all the work it takes to keep up with all of “this tech”.
I have a question in regards to TRUE SSO not running through a UAG. The scenario I have is: internally a clients Horizon implementation follows this path VMware Client –> to Load balanced Connection server VIP (on ADC)–> VDI Machine.
I am currently setting up TRUE SSO and before I get to far my question is with the process flow described will TRUE SSO work with just the Connection Servers configured and no UAG?
Hi Eric, I’d like to know if you ever figure this out? We are implementing SAML through UAG but our internal clients do not go through UAG and we’d like SAML as well with TRUE SSO.
We never implemented because a majority of the internal users use zero client WYSE devices. We will be setting the UAG to SAML and Pass through only, while leaving the Connection Server Authentication as is.
After having set-up the Enrollment Servers, my understanding is that you would set your Connection Servers authentication method to SAML. This would need to be done on each Connection Server. Then there is configuration to be done on the Connection Servers to work with the Enrollment Servers. In case you have not looked at the url https://docs.vmware.com/en/VMware-Horizon-7/7.13/horizon-administration/GUID-88491AB1-46EF-482C-878F-DD35E03E6AD7.html
Hi Eric, thank you for your answer. We are in the process of migrating from Wyse zero clients to Wyse thin clients and they support SAML. Got some issues with SAML auth page not coming up internally but hopefully support will help with this. Thanks again!
Dominic,
Good luck with your project. Hope answer helped or at least informed you.
Hi Carl,
Is it possible configure X.509 Certificate with Truesso?
Hi Carl, thank you for your fantastic work.
After updating Enrollment Server and Connection server from 18964782 to 19067837 I get an error on TrueSSO.
** The primary enrollment server is not connected to the certificate server
Already tried to remove and re-create the environment and connection, and reinstall the enrollment server, with no luck. Of course the CA is online on the same server as the Enrollment server.
Thank you.
I’ve found the solution here: https://digitalworkspace.blog/2022/01/05/minikb-truesso-enrollment-server-unable-to-connect-to-ca-the-authentication-service-is-unknown/
From the URL:
This issue is related to some changes in the service authentication mechanism implemented in Enrollment Server code. To resolve it, force the Enrollment Server service to use NTLM when authenticating to the CA service by adding those registry values:
a. HKEY_LOCAL_MACHINE\\SOFTWARE\\VMware, Inc.\\VMware VDM\\Enrollment Service\\UseNTLMAuthenticationToCa => TRUE
b. HKEY_LOCAL_MACHINE\\SOFTWARE\\VMware, Inc.\\VMware VDM\\Enrollment Service\\UseKerberosAuthenticationToCa => FALSE
Thanks for posting this; I ran into this while upgrading from 2106 to 2111 (8.4.0-19446835). As soon as I put the registry keys in, it started to work; I didn’t even have to reboot the services or box.
Hi Carl,
I have deployed TRUE SSO with DUO as an IDP. after configuring TRUE SSO showing Green in horizon administrator, but while login its prompting again for the 2nd login which has to be eliminated (the purpose of SSO)
Hi Carl,
Can we just use Workspace One Access (with TrueSSO) as a landing portal and accessing horizon vdi without UAG?
Hi Carl,
We have had an issue since deployment of TrueSSO and UAG. Users successfully authenticate but when selecting a desktop, they have to log on to the Win10 VDI too. This does not affect all users all of the time, but it is a daily occurrence randomly with some of the user base. I have logged a SR with VMware and MS as VMware TS saw a timeout when requesting the cert, on the 2 dedicated VDI Sub CA’s (Sub CA are also Enrollment servers), we see event 77 which MS said we can ignore. Event 77 does not log each time a user has to manually log in to the desktop so I believe this is a red herring. I also see no network issues between VDI Sub CA and DC’s, however VMware are pinning this on event 77? es_diag shows successful connection, and I have been over the config multiple times to ensure it is correct. True SSO is working, but it is not 100% consistent..
Have you seen anything like this in the past?
Thank you. .
hi Carl,
I am getting this error of “Failed to create connector, Connector certificate servvers [NameHere] are not present on the primary enrollment server”
I have running only 1 enrollment server in my lab
Thanks
use the name of the certificate authority you created instead of the server name
worked for me
Hi all,
i run into a problem with truesso. The afds part is working wel. but de truesso to the vm is not working. i get an error about the certificate wich is not trusted.
so i run:
C:\Users\admmlan\Desktop>es_diag.exe /ListEnvironment /esname:mdb-vw-enroll01 /certauth /logtoscreen
Execute EnrollmentDiags::ListEnvironment:
Connect to the Enrollment Service: mdb-vw-enroll01
2021-11-08T11:27:59.251+01:00 WARN (1418-1B48) [es_diag] CERTSSL: Unable to find certificate in store VMware Horizon View Certificates
2021-11-08T11:27:59.251+01:00 WARN (1418-1B48) [es_diag] ConnectChannelByCertSsl cert not found
Failed to connect channel: certificaste auth failed
Failed to connect a channel to the Enrollment Service.
The Certificate used to Authenticate to the ES may not be trusted.
For more information please see the Horizon View log-file on this system and on the Horizon View Enrollment Server.
i followed te artical more than once and i have no installation errors. what is my problem?
note i use an existing MS CA.
The error suggests an issue with the Trust configuration – https://www.carlstalhood.com/vmware-horizon-true-sso-uag-saml/#trust
Does the vdm.ec cert exist on the Connection server?
Hi Carl,
Yes al certificates are there. Also i see in de horizon dashboard bij other components that saml 2.0 the adfs connection is gray with no status. all the lines in your howto with the vdmutil i did without any error.
Hello –
Was there ever a solution found for this problem? I’m seeing the same issue on my setup.
Thanks.
I am Enabling the True SSO, but getting error when entering this command “Run the following command to see the available certificate authorities and certificate templates for a particular domain”
-enrollment server is not Online-
can you tell me what’s the issue, I am following the same article which you have been published
I am getting the same issue. Thought it was a firewall issue but after turning the firewall to allow and able to ping, I still get “not online”. The service on the enrollment server is running. Anyone experience and/or fix this?
My issue was with the cert exported from that pod. I reimported to the enrollment server then had to run the add command with remove. Then add back to get it to work. I was trying with two enrollment servers I had setup in another pod so figured it had to be something to do with this connection server.
Hey Carl,
At the step to create the connector for True SSO I get this error and can’t figure out:
Connector certificate servers {my dedicated ca and enrollment server} are not present on the primary enrolment server.
Many thanks for your support.
Hi Carl, Got it fixed now I’m stuck to the client dekstop auth page saying: The attempted logon is invalid. this is either due to a bad username or authentication information… etc
This could be an issue with domain controllers not trusting the smart card certificate or some other crypto problem. There are event logs (e.g. CAPI2, Kerberos) that might provide more details.
Hi, i have tis also, Do you have an solution?
Yes I did and documented in my blog article here at the end: https://danyleclerc.blog/2021/10/18/vmware-horizon-passwordless-experience-powered-by-okta/#more-252
I have this exact same error. Did you ever figure this out? My error states, “Failed to create Connector, Connector certificate servers [CA server name] are not present on the primary enrollment server.”
Carl,
How do you setup the Azure enterprise app for multiple UAG? If you have uag01.domain.com uag02.domain.com, and they are behind vdi.domain.com? How can I configure the enterprise app for the two UAG names and the LB name? The UAG are both set to re-erite their host names and not hide behind the lb vdi.domain.com
When UAG does the redirect to Azure AD for the authentication request is each UAG is sending a different Reply URL? I think Azure AD lets you add multiple Reply URLs to a single Enterprise App.
Otherwise, send the Reply URL to the load balancer FQDN and either UAG can process the SAML Assertion. After that, SAML is no longer involved and the rest is Connection Server with True SSO.
its a good article for SSO, but I have a question as you are using MS Azure as a IDP, can we use DUO instead of Azure as a IDP ?
Any SAML IdP should work. Have you tried it?
because just 2F authentication showing in DUO portal for Horizon View
any help if we use ADFS as idp?
Are you asking how to do it? It shouldn’t be any different than any other SAML IdP.
Carl,
We followed your steps but we are receiving an error stating “request is not supported”
Trying to implement True SSO as well. We are getting the error when logging in “request is not supported.” Engaged VMware support but they were not helpful. Any ideas?
That might mean that the domain controllers don’t have certs or the domain controllers don’t trust your CA-issued certificates. Event Viewer has a CAPI2 log. Domain Controllers have a Kerberos log.
Hey Carl,
Thanks for the response. I checked the CAPI2 logs on the domain controllers as well as the enrollment servers. I see everything successful for the certificate generation. I don’t see any errors in the Kerberos logs. Any other ideas? I’ve been spinning my tires all week with this error.
did you ever figure this out?
Great article. One thing to add is that if you do this over multiple pods the same enrolment servers can be used. We have two pods and to add the second pod it was as simple as importing the connection cert into the enrolment servers to setup trust then running the vdmutil commands on the pod.
Hello Carl,
We are currently on Horizon 7.12. and Im working on bringing a passwordless login to my users using a FIDO2 Biometric key. However once I started to check on the TrueSSO Feature VMWare states its not working when you use the Direct Connect Plugin which we do due to our Nvidia vGPUs. Do you know of a way to use TrueSSO in our scenario or is this limitation might be lifted in a later Horizon Version?
I suspect that True SSO requires Connection Servers.
Are you able to RDP to the machines intead of Direct Connect Plugin?
Yes, once I allow it on the vdi I can RDP to it instead of horizon client.
We are implementing as below:
Client –> UAG [Integrated with ADFS SAML (UserId/Passwd+2nd Factor )] –> VCS server TRUESSO enabled +SAML authenticator created
This one not working as expected:
1. When authentication happens 1st time — userID + Passwd AND 2nd Factor from ADFS
2. It asks again UserID+Passwd and then user can see desktop pool
3. Launch machine it login automaticall.
Want to understand if above design is supported or not.
If Yes then where could be an issue as we suspect NUs VCS server is not understanding the SAML reqst coming from UAG
On the UAG, at Horizon Settings > More, is Authentication set to just SAML? Or is it set to SAML + Passthrough. It should be just SAML.
Thanks for the reply.
It set to SAML
On top of it we sending assertion nameID as UPN format
Also now behavior has been changed some what.
As per vmware feedback we provided UPN in SAML response instead SAMaccount name.
Its gives error like serve expecting credential from different application.
UAG — SAML only
VCS SAML authenticator — Allowed
SAML response — UPN format
Log lines as below:
User Principle Name in Ad : XXX@nus.edu.sg
We have already tried with this and we end up in same error. I am attaching the older debug log file where we set passing parameter to XXX@nus.edu.sg
2021-06-11T15:10:39.877+08:00 DEBUG (1224-1F24) [SamlUtil] (SESSION:1476_***_4886) Using SAML Authenticator: http://vafs-c.nus.edu.sg/adfs/services/trust
2021-06-11T15:10:39.880+08:00 DEBUG (1224-1F24) [SamlAuthFilter] (SESSION:1476_***_4886) Processing Saml Type-A Assertion
2021-06-11T15:10:39.882+08:00 DEBUG (1224-1F24) [SamlAuthFilter] (SESSION:1476_***_4886) SAML auth received a valid UPN: XXX@nus.edu.sg
2021-06-11T15:10:39.882+08:00 DEBUG (1224-1F24) [WinAuthUtils] (SESSION:1476_***_4886) Sending UPN to winauth service: XXX@nus.edu.sg
2021-06-11T15:10:39.905+08:00 ERROR (0EF4-21D0) [ws_winauth] Failed to bind to LDAP://ext.nus.edu.sg (The user name or password is incorrect.)
2021-06-11T15:10:39.910+08:00 ERROR (0EF4-21D0) [ws_winauth] Failed to bind to LDAP://stf.nus.edu.sg (The user name or password is incorrect.)
2021-06-11T15:10:39.917+08:00 ERROR (0EF4-21D0) [ws_winauth] Failed to bind to LDAP://stu.nus.edu.sg (The user name or password is incorrect.)
2021-06-11T15:10:39.917+08:00 ERROR (1224-1F24) [ProperoAuthFilter] (SESSION:1476_***_4886) Error performing authentication: Error instantiating PAEContext for mohirech@nus.edu.sg: com.vmware.vdi.common.winauth.WinAuthException: Failed to retrieve user information for the users with given upns: Failed to obtain sid for user – sid not available – ErrorCode = 1
2021-06-11T15:10:39.918+08:00 DEBUG (1224-1F24) [ProperoAuthFilter] (SESSION:1476_***_4886) Error performing authentication com.vmware.vdi.logger.Logger.debug(Logger.java:44)com.vmware.vdi.broker.filters.FatalAuthException: Error instantiating PAEContext for XXX@nus.edu.sg: com.vmware.vdi.common.winauth.WinAuthException: Failed to retrieve user information for the users with given upns: Failed to obtain sid for user – sid not available –
We tried providing nameID in SAML as below format as well:
XXX@stf.nus.edu.sg
XXX@nus.edu.sg
nusstf\XXX
XXX
all having similar issue.
How do you slove the problem?
Hello
I have used alot of your really great documentation/tutorials.
For the POC that we are doing at the moment is UAG saml SSO. I dont know if it is missing in the documentation or if there is something with our setup. I found out that I needed “/view-client/(.*)” in proxy pattern settings in the UAG to be able reach the html client.
/ Henrik
Thank you Carl.
Hi Carl, did we absolutely need Horizon Entreprises licence for trueSSO? Can TrueSSO work with Horizon Standard licence ?
I’m not aware of any licensing limitations.