Navigation
This post applies to all Omnissa Horizon versions 2006 (aka 8.0) and newer.
- Change Log
- Upgrade
- Install/Upgrade Connection Server
- Horizon Connection Server Certificate
- Horizon Portal:
- LDAP Edits
- Load Balancing
- Remote Desktop Licensing
- Antivirus
- Help Desk Tool – Timing Profiler
- Logon Monitoring
💡 = Recently Updated
Change Log
- 2025 April 16 – updated for Horizon 2503
- 2023 Jan 20 – added Horizon Console Certificate Management in Horizon 2212.
Upgrade
If you are performing a new install, skip to Install Horizon Connection Server.
Notes regarding upgrades:
- Horizon 2503 is an ESB release.
- For supported upgrade paths (which version can be upgraded to which other version), see Omnissa Interoperability Matrix.
- Horizon 2412 (8.14) and newer require newer Omnissa license keys.
- Horizon 2503 let you rename the AD LDS partition as detailed in Omnissa KB article AD LDS Application Partition Migration.
- Horizon 7 license key does not work in Horizon 2006 (8.0) and newer. You’ll need to upgrade your license key to Horizon 8.
- Horizon 8.x no longer supports Horizon Clients 5.x and older.
- According to Omnissa 78445 Update sequence for Horizon 7, Horizon 8, and compatible Omnissa products, App Volumes Managers are upgraded before upgrading Connection Servers.
- Upgrade all Connection Servers during the same maintenance window.
- Horizon Agents cannot be upgraded until the Connection Servers are upgraded.
- Horizon 2006 (8.0) and newer do not support Security Servers. The replacement is Unified Access Gateway.
- Composer was removed from Horizon 2012 (8.1) and newer. All editions of Horizon 2006 (8.0) and newer support Instant Clones. See Modernizing VDI for a New Horizon at Omnissa Tech Zone for migration instructions.
- Downgrades are not permitted.
- You can snapshot your Connection Servers before beginning the upgrade. To revert, shut down all Connection Servers, then revert to snapshots.
- For Cloud Pod Architecture, you don’t have to upgrade every pod at once. But upgrade all of them as soon as possible.
- All Connection Servers in the pod must be online before starting the upgrade.
- It’s an in-place upgrade. Just run the Connection Server installer and click Next a couple times.
- Once the first Connection Server is upgraded, Horizon 2006 (8.0) and newer lets you upgrade the remaining Connection Servers concurrently.
- After upgrading all Connection Servers to Horizon 2012 (8.1) or newer, see Omnissa 80781 Knowledge DML scripts for data population of new columns in view Events Database to backfill the Events Database with column data to improve Events query performance.
- Upgrade the Horizon Group Policy template (.admx) files in sysvol.
- Upgrade the Horizon Agents.
- Persona is no longer supported. The replacement is Omnissa Dynamic Environment Manager. Or Microsoft FSLogix. See Modernizing VDI for a New Horizon at Omnissa Tech Zone for migration instructions.
- If App Volumes Agent is installed, then uninstall it before you upgrade the Horizon Agent. See Omnissa 2118048 Agent installation order for Horizon, Dynamic Environment Manager, and App Volumes.
- Otherwise, Horizon Agent is an in-place upgrade. Just run the installer on your gold images and full clones.
- There’s no hurry. Upgrade the Horizon Agents when time permits.
- DEM Console should not be upgraded until all DEM Agents are upgraded.
- Upgrade the Horizon Clients.
- Horizon Clients can be upgraded any time before the rest of the infrastructure is upgraded.
Install/Upgrade Horizon Connection Server
The first Horizon Connection Server must be a Standard Server. Subsequent Horizon Connection Servers are Replicas. Once Horizon Connection Server is installed, there is no difference between Standard and Replica.
A production Horizon Connection Server should have 10 GB of RAM and 4 vCPU. Each Horizon Connection Server can handle 4,000 user connections.
Horizon 2503 (8.15) is the latest release.
- Horizon 2503 is also an Extended Service Branch (ESB) release, which is supported for 3 years from the April 2025 release date.
To install the first Horizon Connection Server:
- Ensure the Horizon Connection Server has 10 GB of RAM and 4 vCPU. Source = Hardware Requirements for Horizon Connection Server at Omnissa Docs.
- Horizon 2111 (8.4) and newer support Windows Server 2022. Windows Server 2025 is supported in Horizon 2503 and newer. See 78652 Supported Operating Systems and MSFT Active Directory Domain Functional Levels for Omnissa Horizon 8.
- Horizon 2312 and newer no longer support Windows Server 2012 R2.
- Instant Clones in Horizon 2303 and newer require vSphere 7 or newer. vSphere 6.7 and older will not work.
- Download Horizon 2503 (8.15) Horizon Connection Server.
- Run the downloaded Omnissa-Horizon-Connection-Server-x86_64-2503-8.15.0.exe.
- In the Welcome to the Installation Wizard for Omnissa Horizon Connection Server page, click Next.
- In the Destination Folder page, click Next.
- In the Installation Options page, select Horizon Standard Server, and click Next.
- If this is a new pod (not an upgrade), then select if you are using Cloud Pod Architecture or not. If so, then select if the AD LDS partition has been renamed on the other pods or not. Click Next.
- In the Data Recovery page, enter a password, and click Next.
- In the Firewall Configuration page, click Next.
- In the Initial Horizon Administrators page, enter an AD group containing your Horizon administrators, and click Next.
- In the User Experience Improvement Program page, uncheck the box, and click Next.
- In the Operational Data Collection page, click Next.
- In the Ready to Install the Program page, click Install.
- In the Installer Completed page, uncheck the box next to Show the readme file, and click Finish.
Install Horizon Connection Server Replica
Additional Horizon Connection Servers are installed as Replicas. After installation, there is no difference between a Replica server and a Standard server.
A production Horizon Connection Server should have at least 10 GB of RAM and 4 vCPU.
To install Horizon Connection Server Replica:
- Ensure the Horizon Connection Server has at least 10 GB of RAM and 4 vCPU. Source = Hardware Requirements for Horizon Connection Server at Omnissa Docs.
- Horizon 2111 (8.4) and newer support Windows Server 2022. Windows Server 2025 is supported in Horizon 2503 and newer. See 78652 Supported Operating Systems and MSFT Active Directory Domain Functional Levels for Horizon 8.
- Horizon 2312 and newer no longer support Windows Server 2012 R2.
- Download Horizon 2503 (8.15) Horizon Connection Server.
- Run the downloaded Omnissa-Horizon-Connection-Server-x86_64-2503-8.15.0.exe.
- In the Welcome to the Installation Wizard for Omnissa Horizon Connection Server page, click Next.
- In the Destination Folder page, click Next.
- In the Installation Options page, select Horizon Replica Server, and click Next.
- In the Source Server page, enter the name of another Horizon Connection Server in the pod. Then click Next.
- In the Firewall Configuration page, click Next.
- In the Ready to Install the Program page, click Install.
- In the Installer Completed page, click Finish.
- Load balance your multiple Horizon Connection Servers.
- Horizon Console > Settings > Servers > Connection Servers tab shows multiple servers in the pod.
Horizon Connection Server Certificate
Horizon Console Certificate Management
Horizon 2212 and newer have a Certificate Management section in the Horizon Console under Settings. Horizon 2312 and newer can manage cluster certificates in addition to machine certificates.
-
The Administrators role in Horizon does not include the Certificate Management permission.
- Go to Settings > Administrators. On the right, switch to the tab named Role Privileges. Click Add.
- Name the role CertificateManagement or similar. Select the Manage Certificates privilege, which might be on page 2. Click OK.
- Switch to the tab named Administrators and Groups. Select your Horizon Admins group and click Add Permissions.
- Select your new CertificateManagement role and click Finish.
- If you log out, log back in, and then go to Settings > Certificate Management, the buttons should no longer be grayed out. You can either import an existing cert, or click Generate CSR to create a new cert. If you click Generate CSR, then there’s no way to use this interface to combine the signed certificate with the key, so it’s probably better to use some other method of creating a certificate and export it as a .pfx file.
- Click Import to upload a PFX file to the Connection Server that you are currently connected to. For Machine Identity, you’ll have to repeat this process on each Connection Server.
- In certlm.msc on the Connection Server, notice that it sets the vdm friendly name on the imported cert, but it doesn’t remove the vdm friendly name from the old cert. You’ll need to manually remove the vdm friendly name from the old cert.
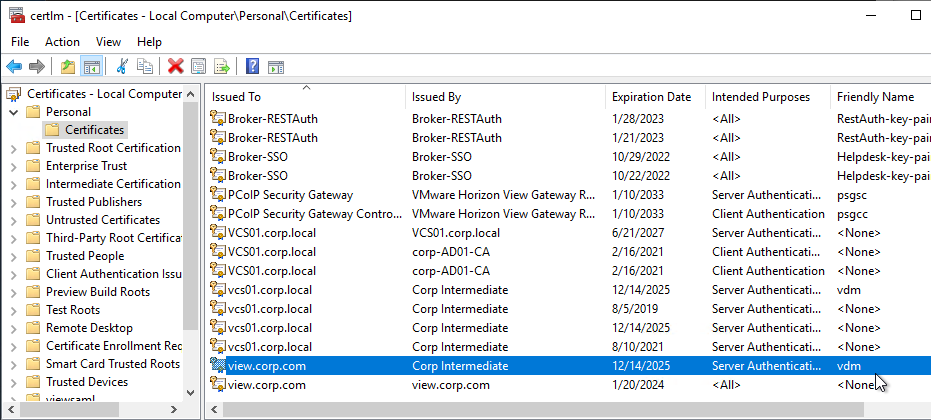
- Then open services.msc and restart the Omnissa Horizon Secure Gateway service or VMware Horizon View Security Gateway Component service.
- Repeat this process on the other Connection Servers.
- Go to Settings > Administrators. On the right, switch to the tab named Role Privileges. Click Add.
Install Cert Manually
Alternatively, install a certificate without using Horizon Console:
- Run certlm.msc. Or run mmc, add the Certificates snap-in, and point it to Computer > Local Machine.
- Request a new certificate with a common name that matches the FQDN of the Connection Server or import a wildcard certificate.
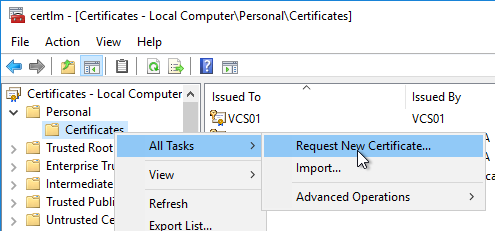
- Note: the private key must be exportable. If using the Computer template, click Details, and then click Properties.
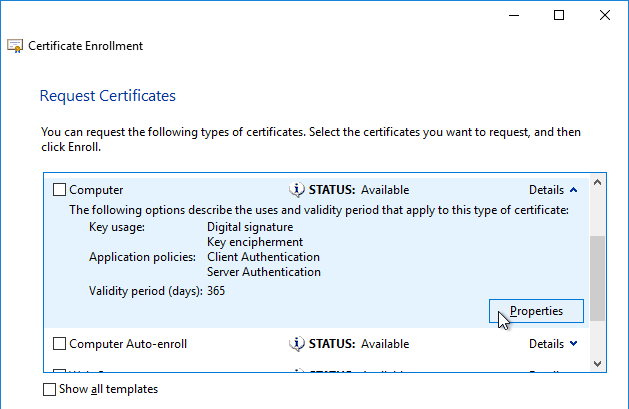
- On the Private Key tab, click Key options to expand it, and check the box next to Mark private key as exportable.
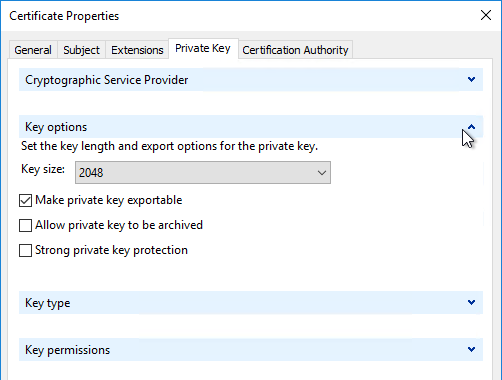
- In the list of certificates, look for the one that is self-signed. The Issuer will be the local computer name instead of a Certificate Authority. Right-click it, and click Properties.
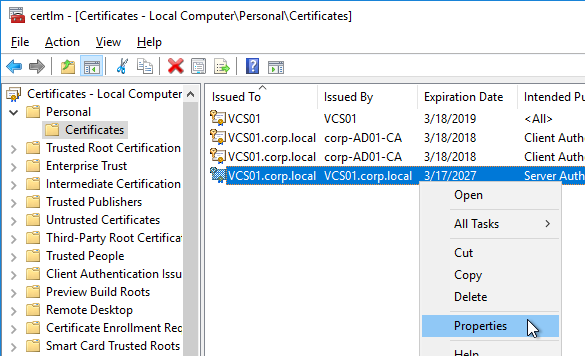
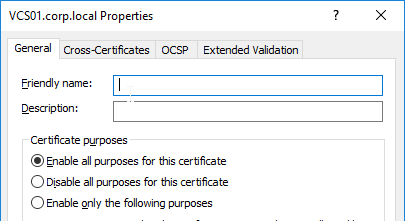
- On the General tab, clear the Friendly name field, and click OK.
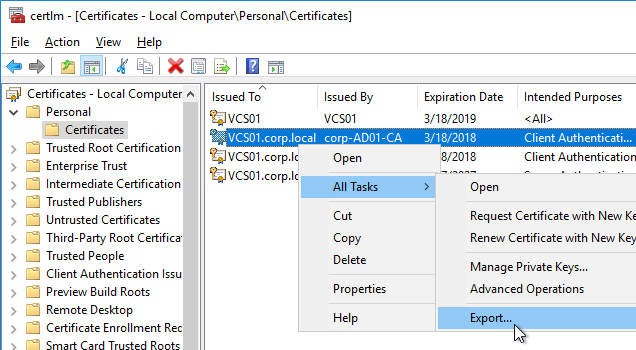
- Right-click your Certificate Authority-signed certificate, and try to export it.
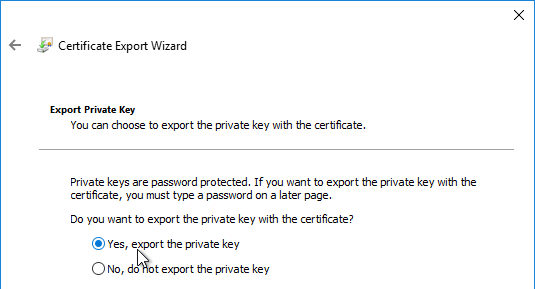
- On the Export Private Key page, make sure Yes, export the private key is selectable. If the option to export the private key is grayed out, then this certificate will not work. Click Cancel.
- Right-click your Certificate Authority-signed certificate, and click Properties.
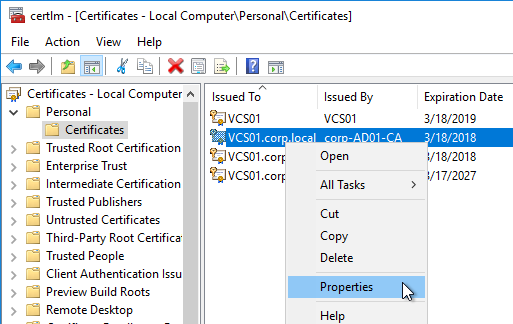
- On the General tab, in the Friendly name field, enter the text vdm, and click OK. Note: only one certificate can have vdm as the Friendly name.
- Then open services.msc and restart the Omnissa Horizon Secure Gateway service or VMware Horizon View Security Gateway Component service. It will take several minutes before you can connect to Horizon Administrator Console.
- Horizon Console > Monitor > Dashboard > System Health > View > Components > Connection Servers should show the Machine Identity Certificate as Valid.
Horizon Portal – Client Installation Link
If you point your browser to the Horizon Connection Server (without /admin in the path), the Install Omnissa Horizon Client link redirects to the Omnissa.com site for downloading of Horizon Clients. You can change it so that the Horizon Clients can be downloaded directly from the Horizon Connection Server.
- These instructions changed in Connection Server 2406.
- On the Horizon Connection Server, go to C:\Program Files\Omnissa\Horizon\Server\broker\webapps\portal or C:\Program Files\VMware\VMware View\Server\broker\webapps\portal.
- Create a new folder called downloads.
- Copy the downloaded Horizon Client 2503 for Windows to the new C:\Program Files\Omnissa\Horizon\Server\broker\webapps\portal\downloads folder.
- Run Notepad as administrator.
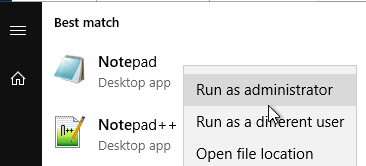
- Open the file C:\ProgramData\Omnissa\Horizon\portal\portal-links-web-client.properties or C:\ProgramData\VMware\VDM\portal\portal-links-html-access.properties file with a text editor (as Administrator).
- Go back to the downloads folder and copy the Horizon Client filename.
- In Notepad, modify link.win32 and link.win64 by specifying the relative path to the Horizon Client executable under /downloads. There’s only one Horizon client for both 32-bit and 64-bit. The following example shows a link for the Horizon win64 client.
link.win64=/portal/downloads/Omnissa-Horizon-Client-2503-8.15.0-14236595709.exe
- Then Save the file.
- Restart the Omnissa Horizon Servlet Host service or the VMware Horizon View Web Component service or restart the entire Connection Server.
- It will take a few seconds for the ws_TomcatService process to start, so be patient. If you get a 503 error, then the service is not done starting.
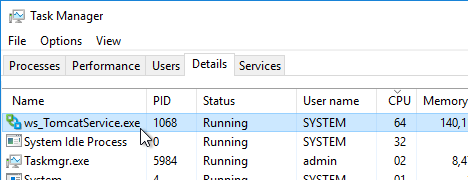
- Now when you click the link to download the client, it will grab the file directly from the Horizon Connection Server.
- Repeat these steps on each Connection Server.
Portal Branding
Paolo Valsecchi at VMware Horizon 8: customize the login page details how to brand the Horizon portal page.
LDAP Edits
Mobile Client – Save Password
If desired, you can configure Horizon Connection Server to allow mobile clients (iOS, Android) to save user passwords.
- On the Horizon Connection Server, run ADSI Edit (adsiedit.msc).
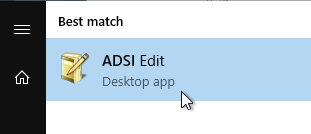
- Right-click ADSI Edit, and click Connect to.
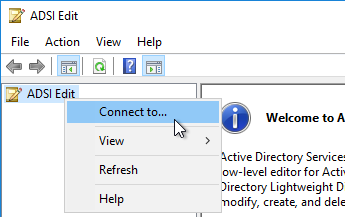
- Change the first selection to Select or type a Distinguished Name, and enter dc=vdi,dc=vmware,dc=int.
- Change the second selection to Select or type a domain or server, and enter localhost. Click OK.
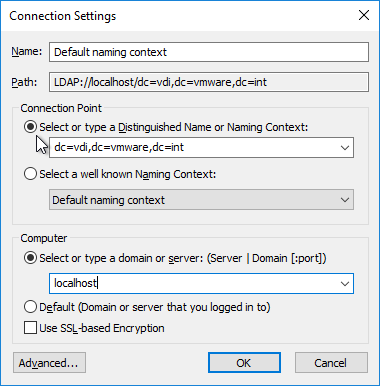
- Navigate to Properties > Global. On the right, double-click CN=Common.
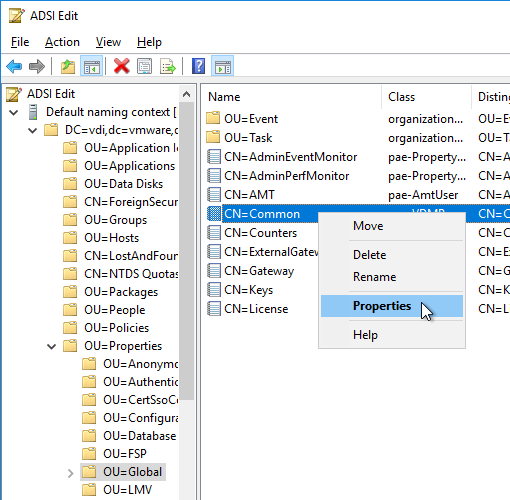
- Scroll down, click to highlight pae-ClientCredentialCacheTimeout, and click Edit.
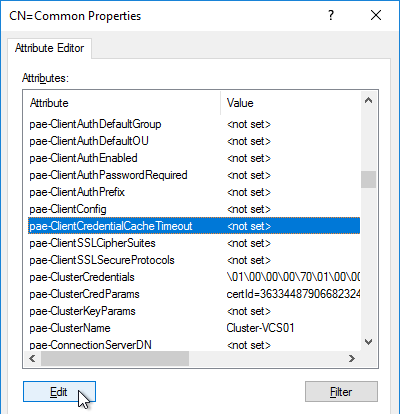
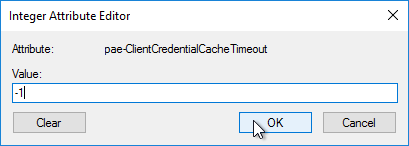
- Enter a value in minutes. 0 = no saving of credentials. -1 = no timeout. Click OK.
Biometric Authentication – iOS Touch ID, iOS Face ID, Fingerprints, Windows Hello
Biometric authentication, including Touch ID, Face ID, and Fingerprints, is disabled by default. To enable: (source = Configure Biometric Authentication at Omnissa Docs)
- On the Horizon Connection Server, run ADSI Edit (adsiedit.msc).
- Right-click ADSI Edit and click Connect to…
- Change the first selection to Select or type a Distinguished Name and enter dc=vdi,dc=vmware,dc=int.
- Change the second selection to Select or type a domain or server and enter localhost. Click OK.
- Navigate to Properties > Global. On the right, double-click CN=Common.

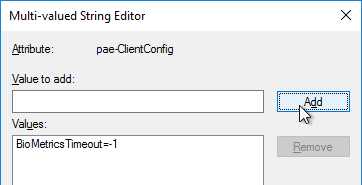
- Find the attribute pae-ClientConfig and double-click it.
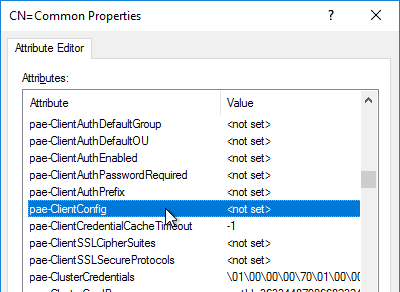
- Enter the line
BioMetricsTimeout=-1, and click Add. Click OK. The change takes effect immediately.
Load Balancing
See Carl Stalhood’s Horizon Load Balancing using Citrix NetScaler.
Remote Desktop Licensing
If you plan to build RDS Hosts, then install Remote Desktop Licensing somewhere. You can install it on your Horizon Connection Servers by following the procedure at https://www.carlstalhood.com/delivery-controller-2402-ltsr-and-licensing/#rdlicensing.
Antivirus
Omnissa Tech Zone Antivirus Considerations in a Horizon Environment: exclusions for Horizon View, App Volumes, User Environment Manager, ThinApp
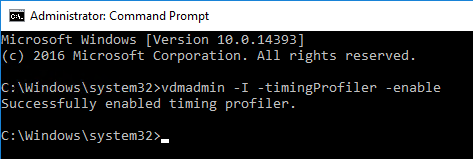
Help Desk Tool Timing Profiler
Run the following command to enable the timing profiler on each Connection Server instance to view logon segments in the Help Desk tool. See Omnissa Docs for more info.
vdmadmin -I -timingProfiler -enable
Related Pages
- Back to Omnissa Horizon 8
We recently upgraded both the Connection servers, UAG and Clients to 2506 and now can’t connect to the VMware machines, getting the following error:
“VDPCONNECT_GATEWAY_TIMEOUT: The connection to the remote computer encountered a gateway timeout. The gateway could not reach the agent or its connection to the agent was refused because the protocol service is not running or the protocol service port is blocked by a firewall. If the issue persists, please contact your system administrator.”
Couple things to look at,
Make sure to check the connection server settings in the console, sometimes on an upgrade the secure gateway setting gets selected.
Do you use a Load balancer? There is a property file under server\sslgateway\conf IIRC. You need to make sure that it contains the informatio for you load balance name/IP.
We are using Horizon Cloud in Azure now, so I am going off of memory…
Long Time Listener, First Time Caller. Appreciate your work, Carl.
Performing in-place upgrades we are seeing the ‘VMware Horizon Indirect Display Driver’ remaining as a device. For clients that use PCoIP that then transition to Blast (Remote Access), we have seen issues where additional screens are appearing and consequentially the client side display settings are not honoured (These are physical windows machines 10/11) – One horizon window, 3 monitors.
Removing it resolves the issue – Interested in seeing if anyone else is experiencing the same thing?
In addition, the in-place upgrade does not seem to remove and repoint ‘all traces’ of ‘VMware’ particularly with folder structures. Is this observed by anyone else?
Also,
Cannot say something to the first part of your comment but wanted to say that the old “Vmware” folder structures are still present in partial after in-place upgrades. Especially on the Connection Server where files like the locked.properties and equal customized files resided. I deleted them after checking “form and function” of the upgraded environment.
did you manage to solve the “failed to connect to connection server” error when trying to reach from html browser?
We recently upgraded to 2503 and the html client started to give this error after some time and it works fine in incognito or with UAG cookies removed!
good morning, new installation connection server 2503 and when I go up
server-connection server and I edit one of the 2 I receive this message:
Failed to fetch GSS Authenticator Configuration
I can’t make any changes
Hi Carl,
Is the BioMetricsTimeout=-1 is a “must” for allowing Windows Hello for Business? because it is not mentioned anywhere on Omnissa documentation.
Hello,
We have a term license that does not expire until next year.
After an upgrade to 2503 from 2111, we have the 59 day(s) remaining message to migrate the omnissa license. Failure to do so will result in the admin console entering degraded mode.
We also cannot end session.
We are looking at opening a ticket with support.
Anyone have any ideas or suggegtions?
Perpetual license was removed after 220x version. So you need to contact your license manager to get new license which will be valid either for one year or 3 years based on your agreement. No more perpetual license.
Thanks for all the replies.
You need a new license key generated from the licensing portal. Link and several others changes that needs to be looked after can be found here:
https://kb.omnissa.com/s/article/6000681#License_Module
talk to your account person from omnesia, they will issue you a term key which you can use.
Upgrading from 2212 to 2503 and noticed something odd with the installer, it didn’t prompt for any questions. Is this something new? Is it pulling in the existing ‘role’ of the currently installed connection server?
We have horizon 7 installed and running on our network. We decided to install horizon 8 2503 on the same network to link the vcenter and eventually shut down the old server. Both servers were installed as standard single pod. The problem is I can’t log in using smart card to the new server while I still can on the old one, I added all certs in users certificate chain to the trusted.key file but still can login.
In the console Security Settings: Go to Certificate Settings > Certificate Authentication > Certificate Authentication Mapping Controls. From the drop down, select UPN and Predefined Alternate Security Identities (Legacy). Bounce the server and try again.
Thanks I only selected the UPN legacy and it worked to let me login to the web client but I still can’t login to horizon client. Horizon client is the latest.
Is there LDAP settings I missed to allow smart card authentication from the client?
The smart card still lets me login to horizon 7.
when i tried to go to the console interface, i am getting can’t reach this page. the server has CA issued cert and the friendly name is set to vdm.
In the latest Horizon client versions, from 23.12 I think, TLS v1.3 is default.
If your smartcard doesn’t support TLS v1.3, you need to change the client to use TLS v1.2. This can be done either in GPO or registry.
I have been unable to find any smartcard that supports TLS v1.3. Maybe someone in here can point me/us in the right direction. Maybe by Google skills just suck.
recently performed an in place upgrade from 8.13 to 8.15 on the connection server. there is 1 uag and 1 connection server sitting behind it.
all was working before the ugrade.
now all of a sudden after the upgrade I get the “failed to connect to connection server” error when trying to reach from html browser. on the horizon client I get “authentication failed error: http error 403”
nothing has changed in the environment other than doing a point and client in-place upgrade from 8.13 to 8.15
Omnissa support haven’t been able to be of real assistance so far, outside of what we’ve already independently troubleshooted already.
What is in your locked.properties file?
Also, if you are entering /admin, make sure you add a slash on the end: /admin/
yep, that’s the first place I look. The locked. properties file had the same entries it did when everything was working before the upgrade
it had:
allowUnexpectedHost=true
portalHost=
checkOrigin=false
I’ve been troubleshooting, by modifying the entries a bit to add remove entries.
I’ve added the enableCors=false
the locked.properties file looked unchanged when I originally looked at it after the upgrade.
We have the same Problem here. Did you find a solution?
Same here, any solution?
So Omnissa support has finally acknowledged that there is an issue with 8.15 Connection Servers with UAGs. First, you MUST use the 8.15 (2503) UAG. Second, the Horizon Client in question cannot be newer than 8.13 (2406) which makes iPads and Androids quite the pain since that version bugs you about upgrading to the rebranded Omnissa client. HTML should work fine through the UAGs but until they figure it out we’re screwed to force folks to either not use the UAGs (we don’t for on prem/VPN folks) or make them use the HTML interface instead of using the client.
idk what happened between yesterday and today but I’m happy to report all clients work now! I’ve tested 8.14 and 8.15 through the UAGs from Android and from Windows and they all now work!!! No clue what changed but my guess is 8.14 and 8.15 phone home to something when they connect through the UAGs and it’s some external url that was at issue that y’all fixed! Our iPads are connecting! Whatever they did fixed it without us having to update anything on our side nor the client side.
we had recently implemented a load balancer upstream from the uag. The traffic was being forwarded from that load balancer which triggered errors in the uag as an invalid origin host.
we had to put the load balancer IP into the allow-origin hosts header entry on the uag.
did you manage to solve the “failed to connect to connection server” error when trying to reach from html browser.
We recently upgraded to 2503 and the html client started to give this error after some time and it works fine in incognito or with UAG cookies removed!
We have same issue. may i know if you fix this issue?
Did you ever get this resolved ? I have the same problem.
When upgrading the Connection Server (from 2412 to 2503), should I do anything in the Horizon Console first?
– Take a snapshot I believe always is a good practice.
– But should I disable provisioning? (Servers/vCenter Servers/Disable Provisioning)?
– Or/And disable the Connection Server (Servers/Connection Servers/Disable)?
– Anything else?
Omnissa recommends disabling provisioning, but I usually don’t bother. I would snapshot the Connection Server VMs first.
I recently upgraded horizon environment from 2312 to 2412. After the upgrade PCOIP connections (both internal and external) are not working. I am getting a black screen and then the connection disconnects. RDP and Blast sessions are working fine without any issues. As far as I am aware there are no firewall changes that blocks traffic to port 4172. Are there any changes to PCOIP connections with build 2412?
Is the PCoIP Gateway enabled on your Connection Servers? I assume the issue is with internal connections.
Hello Carl, The issue is with both internal and external connections. PCOIP secure gateway is not enabled on connection servers.
They added “PCOIP Ultra” support but it’s not enabled by default.
What version your agents are running ?
Hello Patrick, the agents are on version 8.12.1-23507832
It seems agent was the issue. Updated the agent to latest version 8.14 and PCOIP sessions are working again.
Thank you for your guides Carl, you do an awesome job!
Does anybody have a valid link to download Horizon Connection server and associated files on the Omnissa site? I can’t find it anywhere anymore. Everything I find has either a broken link or routes to ThinApp downloads. Much appreciated.
Call Omnissa Support to get it. I think Omnissa is required to remove anything saying VMware from their website.
Sounds good, we’ve had a ticket open with support and are waiting a response. I was hoping there was an easier way. 😆
Hi Carl,
I have recently upgrade my Horizon Connection Server from 2111 to 2406. Since the upgrade, the USB devices are unavailable. I have uninstalled the old Horizon Agent from the VM, old Horizon Client from the laptop, and installed the latest version. I have also tried to delete all the certificates from VMWare Horizon View Certificates and VMWareView on MMC.exe.
Any ideas?
Did you enable the USB Redirection component when installing Horizon Agent? Is USB Access enabled in Global Policies in Horizon Admin Console?
Hi Carl,
Thanks for the reply.
Yes, USB Redirection component was enabled when installing Horizon Agent and USB Access is enabled in Global Policies in Horizon Admin Console.
I have reached out to Omnissa Support but they also cannot figure it out.
Very odd issue.
I’m setting up a new 2406 build and am having issues with the UAG loading externally. Accessing https://uag.domain.com times out – but if I run Test-NetConnection uag.domain.com -port 443 the TCP test succeeds, so I’m feeling good about the external firewall not being an issue. I’m using an externally-signed wildcard certificate for all systems, and the UAG is configured to point to the IP address of the connection server to avoid any DNS issues.
On the UAG admin console, the Horizon Connection and all sub-services are lit up green.
When I add the Gateway to the Horizon console, something interesting I see is that the Version and IP show up as “N/A”. Is this worth digging into, and potentially a sign of an issue with my UAG/Connection Server config?
N/A just means that there haven’t been any connections through the UAG.
Does the UAG have multiple interfaces? Are you able to connect to the portal from the same network as the UAG?
Yes, the UAG has two interfaces – Management and Internet.
I’m unable to load the UAG portal from the same network, both by DNS name and IP. I’ve added a static route to the Internet interface for internal routing.
Another item to add, when I use the Horizon client and try to connect to the UAG URL, I get the message “Connection Failed. Error: An SSL error occurred”
Hi Andrew
Did you ever get this resolved ? I have the same problem.