Navigation
This post applies to all VMware Horizon 7 versions, including 7.13.3.
- Change Log
- Preparation
- Install – Horizon Security Server
- Security Server Certificate
- Load Balancing
- Enable PCoIP Secure Gateway
💡 = Recently Updated
Change Log
- 2023 Mar 22 – Updated Install section for Horizon Security Server 7.13.3.
- 2022 Mar 11 – Updated Install section for Horizon Security Server 7.13.2.
- 2020 Nov 9 – added link to VMware Code Script to manage Horizon 7.x Security Servers via the View-API without needing the FLEX based Administrator Console
- 2020 Oct 24 – Updated Install section for Horizon Security Server 7.10.3 (ESB).
- 2020 Oct 16 – Updated Install section for Horizon Security Server 7.13.
- 2020 Jun 5 – Updated Install section for Horizon Security Server 7.10.2 (ESB).
- 2020 Mar 18 – Updated Install section for Horizon Security Server 7.12.0.
Preparation
The newer Horizon Console does not support Security Servers. The older Flash-based Horizon Administrator won’t work for much longer, so take it as a clue that you should deploy Unified Access Gateways (UAG) to replace your Security Servers. Horizon 8 also does not support Security Servers.
Security Servers are intended to be deployed in the DMZ.
Horizon Security Server is installed on Windows. If you prefer a Linux appliance, see VMware Unified Access Gateway. Note: Some of the newer Blast Extreme functionality only works in Unified Access Gateway. See Configure the Blast Secure Gateway at VMware Docs.
Security Considerations for Horizon View 5.2 – http://www.vmware.com/resources/techresources/10371
Firewall Ports
If there is only one Security Server in the DMZ, create a NAT’d public IP to the Security Server. Create a public DNS entry that resolves to this IP address.
If your load balancer (e.g. NetScaler ADC, F5) is able to provide persistence across multiple port numbers, then you only need one public IP. For example, in NetScaler, this is called Persistency Groups.
If your load balancer doesn’t support persistence across multiple port numbers, then create three public IPs:
- Public IP NAT’d to the load balancer IP. Create a public DNS entry that resolves to this IP address. This is the DNS name that users will enter into their Horizon Clients.
- Public IP NAT’d to each of the Security Servers. Each Security Server must be exposed directly to the Internet. Create public DNS names that resolve to these public IPs. When installing Security Server, specify these public DNS names and not the load balanced DNS name.
Firewall Rules for View Connection Server at VMware Docs.
Open these ports from any device on the Internet to all Security Server and Load Balancer public IPs:
- TCP 80
- TCP and UDP 443
- TCP and UDP 4172. UDP 4172 must be opened in both directions.
- TCP and UDP 8443 (for Blast)
Open these ports from the Security Servers to internal:
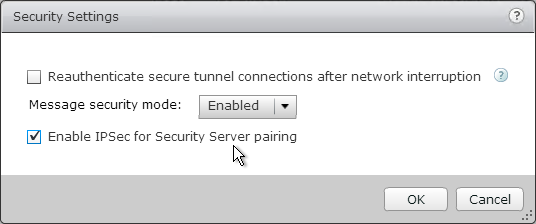
- If IPSec is enabled in View Administrator (Global Settings > Security > Edit), open ISAKMP Protocol (UDP 500) and ESP. Or if there is NAT between the Security Server and the Connection Server, open NAT-T ISAKMP (UDP 4500). Configuring a Back-End Firewall to Support IPsec at VMware Docs.
- TCP 8009 (AJP13) to the paired internal Horizon Connection Server.
- TCP 4001 (JMS) to the paired internal Horizon Connection Server.
- TCP and UDP 4172 (PCoIP) to all internal Horizon Agents. UDP 4172 must be opened in both directions.
- TCP 32111 (USB Redirection) to all internal Horizon Agents.
- TCP and UDP 22443 (HTML Blast) to all internal Horizon Agents.
- TCP 9427 (MMR) to all internal Horizon Agents.
- TCP 4002 for Enhanced Messaged Security – Change the JMS Message Security Mode to Enhanced at VMware Docs
Pairing Password
The newer Horizon Console does not support Security Servers. The older Flash-based Horizon Administrator won’t work for much longer, so take it as a clue that you should deploy Unified Access Gateways to replace your Security Servers.
- VMware Code Script to manage Horizon 7.x Security Servers via the View-API without needing the FLEX based Administrator Console
- In Horizon Administrator, on the left, expand View Configuration, and click Servers.
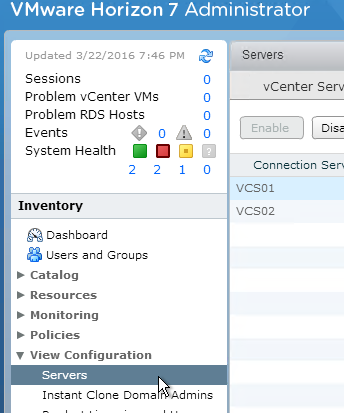
- On the right, switch to the Connection Servers tab.
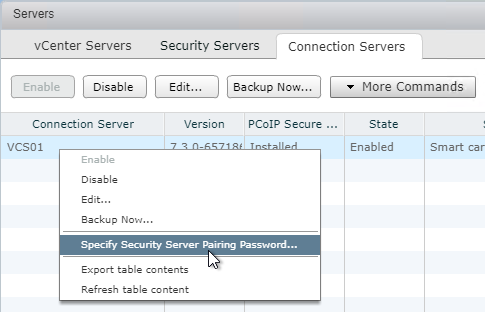
- Select the Horizon Connection Server to which the Security Server will be paired. Then click More Commands, and click Specify Security Server Pairing Password.
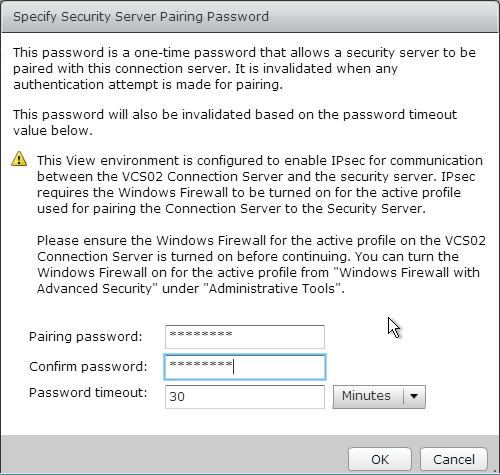
- Enter a temporary password, and click OK.
Install – Security Server
- Ensure the Horizon Security Server has 10 GB of RAM and 4 vCPU.
- Windows Server 2019 is supported for the Horizon Security Server 7.8 and newer.
- Login to the Horizon Security Server.
- Download Horizon 7.13.3 Horizon Connection Server.
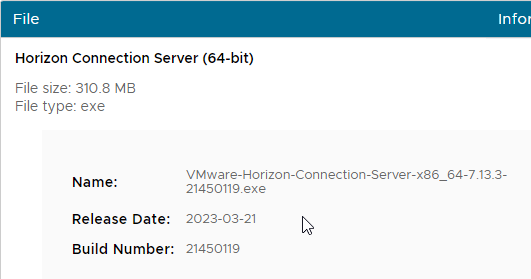
- If you are upgrading an existing Security Server, then you must prepare it for upgrade:
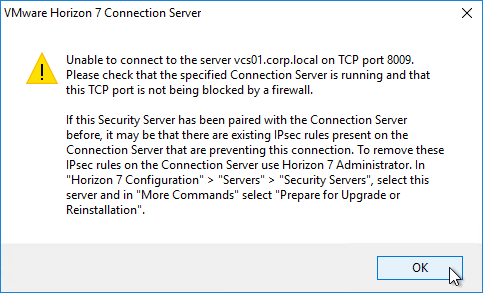
- In Horizon Administrator (Flash/Flex console), on the left, expand View Configuration, and click Servers.
- On the right, switch to the tab named Security Servers.
- Highlight the Security Server, then click the menu named More Commands and click Prepare for Upgrade or Reinstallation.
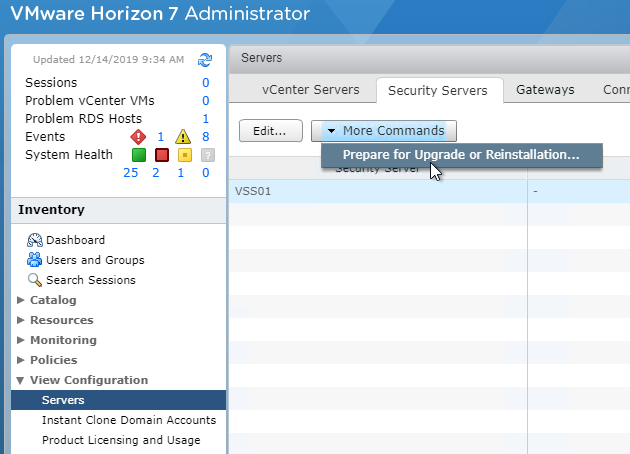
- Click OK to remove the IPSec rules.
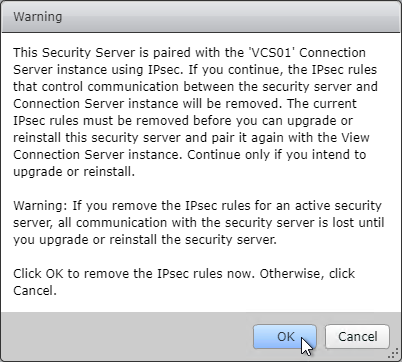
- On the Security Server, run the downloaded VMware-Horizon-Connection-Server-x86_64-7.13.3.exe.
- In the Welcome to the Installation Wizard for VMware Horizon 7 Connection Server page, click Next.
- In the License Agreement page, select I accept the terms, and click Next.
- In the Destination Folder page, click Next.
- In the Installation Options page, select Horizon 7 Security Server, and click Next.
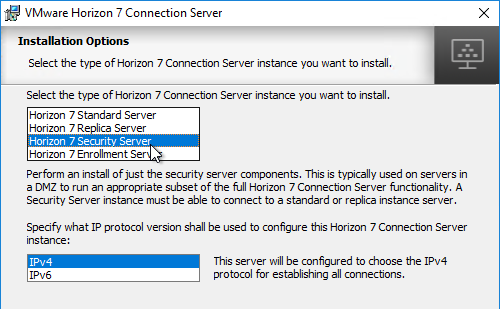
- In the Paired Horizon 7 Connection Server page, enter the name of the internal Horizon Connection Server that this Security Server will be paired with. If using a hostname, it must be resolvable (edit the local HOSTS file) to the correct IP. Also, the correct firewall ports are required. Click Next.
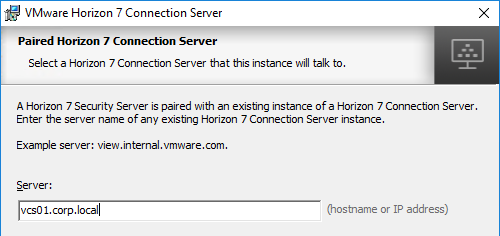
- In the Paired Horizon 7 Connection Server Password page, enter the pairing password specified earlier, and click Next.
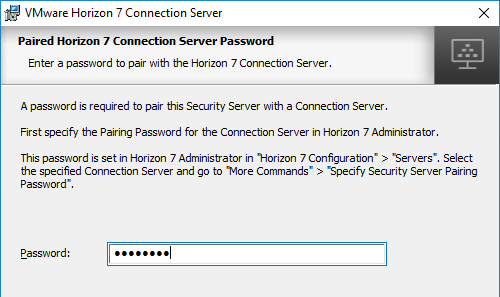
- In the Horizon 7 Security Server Configuration page, edit the URLs as appropriate. These URLs must be externally accessible. The top URL is a FQDN, while the middle URL is an IP address. These can be changed later. Click Next.
- In the Firewall Configuration page, click Next.
- In the Ready to Install the Program page, click Install.
- In the Installer Completed page, click Finish.
SSL
Security Server Certificate
- Run certlm.msc (Windows 2012+). Or run mmc, add the Certificates snap-in and point it to Computer > Local Machine.
- Request a new certificate with a common name that matches the public FQDN of the Security Server, or import a wildcard certificate.

- Note: the private key must be exportable. If using the Computer template, click Details, and then click Properties.

- On the Private Key tab, click Key options to expand it, and check the box next to Mark private key as exportable.

- In the list of certificates, look for the one that is self-signed. The Issuer will be the local computer name instead of a Certificate Authority. Right-click it, and click Properties.
- On the General tab, clear the Friendly name field, and click OK.
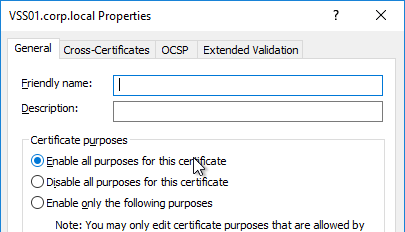
- Right-click your Certificate Authority-signed certificate, and try to export it.
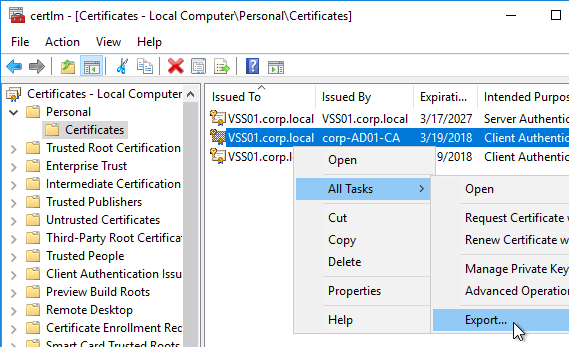
- On the Export Private Key page, make sure Yes, export the private key is selectable. If the option to export the private key is grayed out, then this certificate will not work. Click Cancel.

- Right-click your Certificate Authority-signed certificate, and click Properties.
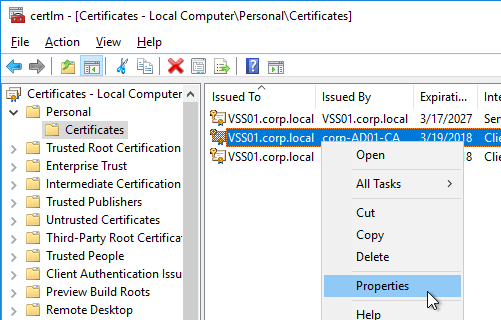
- On the General tab, in the Friendly name field, enter the text vdm, and click OK. Note: only one certificate can have vdm as the Friendly name.

- Then restart the VMware Horizon 7 Security Server service.
Load Balancing
See Carl Stalhood – Horizon View Load Balancing
Enable PCoIP Secure Gateway
- In View Administrator, on the left, expand View Configuration, and click Servers.
- On the right, switch to the Connection Servers tab.
- Right-click the Connection Server that is paired with the Security Server, and click Edit. Note: you can’t configure this directly on the Horizon Security Server, and instead must configure it on the paired Horizon Connection Server.
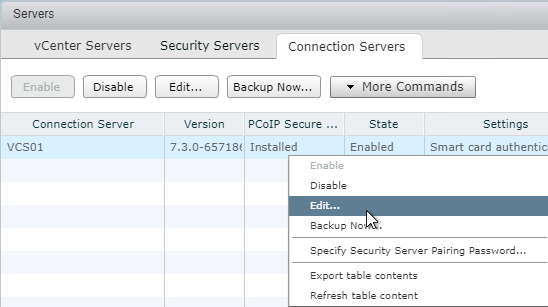
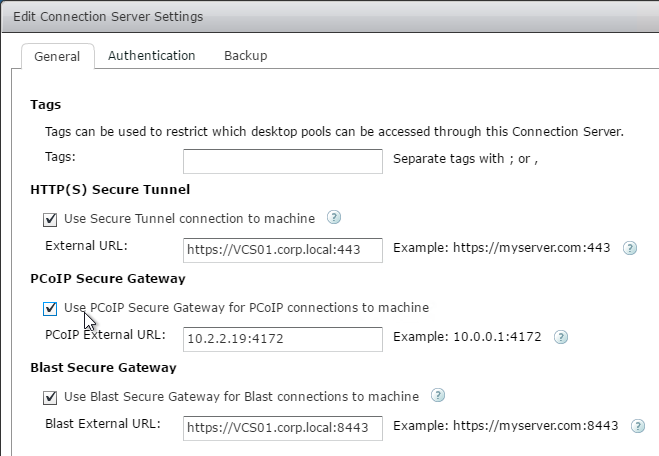
- On the General tab, check the box next to Use PCoIP Secure Gateway for PCoIP connections to machine. Also, make sure HTTP(S) Secure Tunnel and Blast Secure Gateway are enabled. Click OK.
Related Pages
- Back to VMware Horizon 7
Hi Carl, we have updated the certificate on our Horizon 8 Connection Server but we get a SSL_ERROR_NO_CYPHER_OVERLAP.
Do you have any clue on how to solve this ?
Problem solved, the private key had to be exportable according to this KB :https://kb.omnissa.com/s/article/2072459.
thanks for this page, we have an environment with a security server and connection server running 7.10.0, and we’re trying to get updated to 7.10.3 , the connection server gets updated 1st, and then when we try to do the security server, (login to admin console using flash browser), and use the more commands “Prepare for Upgrade or Reinstallation.’ step, the security server is not able to reach the server via local ip/dns etc,, the firewall connection rule is removed but something is still causing an issue. saying the server cannot connect to port 8009 or 8010 to run the preaper for upgrade step, which we’ve done already. Any suggestions? Only other thing we can think to do is remove the security server entirely and attempt to install in freshly.
It might be easier to simply replace Security Servers with UAG appliances.
Love your work, thanks for the pointer to the Security Server admin script. Just what I needed when fighting with the flash detection on legacy install of Firefox for flash.
Hi Carl,
First of all, Thanks for such a great Site and all the Posts and helping people like me who have no where to go even the VMware help takes long time to revert back and takes lot of time to answer the queries. but your posts and personal replies make our task much easier. Thanks a zillions for all your efforts.
We are planning to Upgrade from 7.12 to 8 (2006)
My only query is about Security server and UAG, Currently all users are accessing VDI environment from Internet via security server,
Horizon 8 does not support Security server, so UAG is sufficient to replace Security server or I need to keep both? Any config/changes required to the URL’s used as there is mentioning here that UAG requires Connection servers to have BLANK URL for PCoIP, Blast, SSL and Tunnels. OR this is required to be blank is Security server is present. we will be doing off with Security server is required.
Please let me know how to proceed with replacing Security Server with UAG and what to keep in Mind while doing so and any downtime is required for the same, Infact I was planning to replace Security server first and then Upgrade from 7.12 to 8 wile having UAG setup for 7.12 Environment.
Thank you very much for all your support and personal attention to each query
Thanks,
UAGs are very similar to Security Server. You define the URLs on the UAGs themselves, not in Horizon Console. In Horizon Console, you go to the Connection Servers and turn off the Gateways but you can leave the Gateway URLs alone.
You can build UAGs with the same URLs as your Security Servers and then do a cutover. Or you can use new URLs for your UAGs. To test FQDN URLs, you can modify HOSTS file on a client. The main challenge is PCoIP which doesn’t support FQDN.
Hi Carl! (great job you have here)
I wonder how to disable TLS1.0 on UAG blast, because I can only find instructions on how to do that on a Connection Server… Any idea?
In UAG 3.10, only TLS 1.2 and TLS 1.3 are enabled.
Hi Carl,
I got an issue getting virtual desktop being timed out when accessing the HTML like https://public-dns-name. It loaded going to the virtual desktop but then Chrome report – “” took too long and site cannot be reached. I can connect via internal network but cannot from external network. Apart from firewall ports, which logs of Security server and connection server should I lookup for troubleshooting?
Hallo Carl,
Might be directly related here but do you know how can we disable TLS1.1 for Blast. My security team is referring me to block TLS 1.1 on 8443. When I see VMware document they are only referring to absg.properties. Well this component is only on view connection server and not on view security server. Unless I’m missing it. SInce this is external audit, connection is getting tunnel via security server ? right?. Appreciate your help
I assume the same applies to Security Servers.
I recommend switching to UAG. In System Configuration, there’s a slider for TLS 1.1.
We had a similar issue as some with regards to the certificate – until we remembered to update the connection server settings for external URLs, which defaults to the FQDN ( and did not match our certificate).
Admin Console \ View Configuration \ Servers \ Connection Servers \
… changing both External URLs to match domain used in certificate.
Hi Carl
Can security servers and a UAG co-exist in the same environment using the same connection servers?
We are planning to deploy a UAG but have discovered some old security servers still running.
Cheers
Shane
The Connection Server that UAG uses must have the Security Gateways (PCoIP, Blast, SSL) disabled.
Would that have any impact on the existing security servers also using that connection server?
That’s the reason for my original question tbh. All docs say to disable the tunnels/gateways on the connection servers. Ours have all 3 tunnels enabled. I wasn’t sure if disabling these would affect the security servers or not as they have their own settings.
Thanks for taking the time to respond, much appreciated.
Security Severs require the paired Connection Servers to have the Gateways enabled. UAGs require the Connection Servers to have the Gateways disabled. Most larger environments have separate Connection Servers for internal vs external. UAGs talk to the internal Connection Servers. The External Connection Servers are paired with Security Servers.
On Horizon v7.11, when registering the UAG v3.8 in the Connection server UI, the version, IP address, location, etc. all say N/A and the status has a question mark. I’ve tried creating an internal DNS entry for uag.example.com to point to the internal UAG nic IP, but no luck. I have also tried using the public and private FQDN’s. How does the Connection server communicate with the UAG to get it’s status? Do I need to somehow give the connection server the admin password of the UAG to authenticate? Or do I need to add some firewall rules? I can find any info in VMware documentation about how this communication occurs, so any help would be greatly appreciated.
Usually I just establish a connection through the UAG and then it shows up. On the UAG, go to System Configuration and specify the name of the UAG. It must match what’s configured in Connection Server.
Hi Carl,
I’m attempting to access Horizon desktops remotely with a Wyse PCoIP device connecting through a Security server. I can log on and get presented the desktop pools. When I select a pool it tries to connect to a desktop and then times out. I can see in View Administrator that a desktop was assigned. I’ve been using local connections via Connection server for quiet sometime. This is my first attempt to get remote connections working as prep for Corona virus issues.
Doug
Is UDP/TCP 4172 open to the Security Server? On the paired Connection Server, did you enable PCoIP Secure Gateway and enter the public IP of the Security Server?
UDP/TCP 4172 are open but I’m confirming with the firewall group that UDP 4172 is open both ways. I did enable PCoIP Secure Gateway and enter the public IP of the Security Server on the Connection server (I only have the one which is paired to the Security server). But then local PCoIP clients that connect to the Connection server are unable to connect to a desktop.
Yep. For Security Servers you normally build separate Connection Servers that are only paired with the Security Servers. The address of the Security Server goes in the Security Server configuration, not the Connection Server configuration.
Note: Unified Access Gateway doesn’t need paired Connection Servers.
Is it possible to have just one Connection server to be used for both remote and local access? I put the local IP address back in the Connection server PCoIP Secure Gateway address and local connections are working again. Remote PCoIP connections still not working.
I would recommend implementing Unified Access Gateway (UAG) instead of Security Server. UAG doesn’t need any changes on the Connection Server other than disabling the Gateways/Proxies.
I don’t believe we have a license for UAG. I do have Security server functioning properly now.
UAG should be included with every Horizon license.
I see that now. I’ll need to investigate implementing it. Thanks for your help.
I really appreciate this post so I hope you can help me. On a recent pen test, it was discovered that port 4172 does not have a valid certificate. I have followed evertything in VMware docs to force PSG to use a custom SSL, but it refuses, continuing to use the self-signed instead. In the log I get the following error:
Failed to retrieve private key for current certificate – rejecting.
But they cert, has a private key. Any Ideas?
Maybe prevent the legacy certificate – https://docs.vmware.com/en/VMware-Horizon-7/7.4/horizon-installation/GUID-F9F9996C-2BB1-465B-ADAA-EAB993E1B1F5.html
Yea, I did that already. Its frustrating. I’m going to try a separate custom SSL for PSG.
Hallo Carl,
I would be glad if you give some direction.
I have followed your article end to end.
Things are not working when both view security servers are up and running.
When I bring one down, all works.
Which logs I should check. I keep getting 403 Forbidden in debug log on view security server.
2020-02-11T12:06:17.084+01:00 DEBUG (0AC4-0D08) [Processor] Accepted connection on port 443 from /172.16.1.252, port:25025
2020-02-11T12:06:17.084+01:00 DEBUG (0AC4-0CAC) [MessageFrameWork] KeyVault service got operation=getCertificateChain, ok=1, msecs=0
2020-02-11T12:06:17.084+01:00 DEBUG (0AC4-10E0) [KeyVaultBinaryUtils] (NetHandler) Removing root certificate from chain
2020-02-11T12:06:17.084+01:00 DEBUG (0AC4-0CA4) [MessageFrameWork] KeyVault service got operation=getCertificateKey, ok=1, msecs=0
2020-02-11T12:06:17.084+01:00 DEBUG (0AC4-0B00) [MessageFrameWork] KeyVault service got operation=getCertificateChain, ok=1, msecs=0
2020-02-11T12:06:17.084+01:00 DEBUG (0AC4-10E0) [KeyVaultBinaryUtils] (NetHandler) Removing root certificate from chain
2020-02-11T12:06:17.099+01:00 DEBUG (0AC4-0CA0) [MessageFrameWork] KeyVault service got operation=getCertificateKey, ok=1, msecs=16
2020-02-11T12:06:17.128+01:00 DEBUG (0AC4-0984) [PooledProcessor] Using secure protocol TLSv1.2 and cipher suite TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA
2020-02-11T12:06:17.160+01:00 DEBUG (0AC4-0C0C) [SimpleAJPService] (ajp:broker:Request27871) Request from /NETSCALERIP: GET /broker/xml
2020-02-11T12:06:17.192+01:00 DEBUG (0AC4-0CEC) [SimpleAJPService] (ajp:broker:Request27871) Response 403 Forbidden
Are you load balancing? What persistence is configured on the load balancer? The persistence needs to work across multiple port numbers.
I have followed article end to end. So it is source IP configured. We are using both Blast and PCoIP. And we are using security server.
Considering it is bit complicated setup, do you think below suggest session persistence is not working.
2020-02-11T15:33:24.402+01:00 DEBUG (0CAC-1124) [ProperoAuthFilter] (SESSION:2a59_***_8f94) Attempting to authenticate against gssapi
2020-02-11T15:33:24.402+01:00 DEBUG (0CAC-1124) [ProperoAuthFilter] (SESSION:2a59_***_8f94) Attempting to authenticate against cert-auth
2020-02-11T15:33:24.402+01:00 DEBUG (0CAC-1124) [CertificateAuthFilter] (SESSION:2a59_***_8f94) Client did not use Certificate Authentication, skipping or failing
2020-02-11T15:33:24.402+01:00 DEBUG (0CAC-1124) [CertificateAuthFilter] (SESSION:2a59_***_8f94) Failing Certificate authentication, bypassing for OPTIONAL mode
2020-02-11T15:33:24.402+01:00 DEBUG (0CAC-1124) [ProperoAuthFilter] (SESSION:2a59_***_8f94) Attempting to authenticate against windows-password
2020-02-11T15:33:24.402+01:00 DEBUG (0CAC-1124) [ProperoAuthFilter] (SESSION:2a59_***_8f94) Not authenticated, requesting login page for windows-password
2020-02-11T15:33:24.402+01:00 DEBUG (0CAC-1124) [AuthorizationFilter] (SESSION:2a59_***_8f94) paeCtx == null, forwarding to login page: /broker/xml
2020-02-11T15:33:24.402+01:00 DEBUG (0CAC-1124) [AuthorizationFilter] (SESSION:2a59_***_8f94) HTTP session ID old value: 9391-***-8EE0, new value: 796A-***-B8BE for 2a59_***_8f94
immediately after this log out starts.
Also, I have done Source IP per service, I have not used persistence group as directed by you. Does it matter.
Yes. Whichever Connection Server authenticated you on port 443 must also be the same Connection Server chosen for port 8443 or 4172.
Carl, you should “Buy me a coffee” on your website. Without this website, it is impossible to configure Netscaler. This is PSO guide even for Citrix PSO. Thanks a lot for putting your time in making this work.
Hi Carl, I have recently updated to version 7.11 since 7.4 and I have seen that the web console does not display Security Servers. Instead the flex console yes. Is it a bug?
Thank you.
I suspect that Horizon Console won’t support Security Servers. It’s time to convert to UAGs.
Hi Carl good morning,
We have an Horizon 7.10 environment with two connection servers running in Windows Server 2016.
When we try to connect to the environment using the Horizon client, we get the error:
“Is not possible to connect to the connection server. The server provided an invalid certificate”
In addition, in the horizon administrator withing events shows:
“Certificate is invalid for Secure Gateway at address y.y.y.y” for both connection servers.
Both connection servers have the TLS signed certificates installed and the Horizon administrator shows green check marks in both.
What are we missing? We run out of ideas.
Thank you.
If you point Firefox to a Connection Server, do you see any certificate errors?
Also try https://www.digicert.com/util/utility-check-ssl-certificate-chain.htm
Hi Carl,
If we try to connect directly to any connection server it’s works perfectly. The problem resides when connecting through a load balancer.
We know for sure that the problem is not in the load balancer because when pointing the load balancer to other connection servers we have running, it works so the problem must reside in the connection servers.
Regards.
Is your load balancer terminating SSL? Or is it simply passing through the SSL traffic? Do all of your Connection Servers have the same certificate that matches the load balanced FQDN? Is persistence enabled on your load balancer?
Hi Carl,
Is your load balancer terminating SSL? Or is it simply passing through the SSL traffic? My load balancer is just passing the traffic through.
Do all of your Connection Servers have the same certificate that matches the load balanced FQDN? My connection servers have their own CA signed certificate. Do we have to import the load balancer FQDN certificate into the Connection server’s certificate store? If so, once imported, do we need to keep both certificates on each connection server?
Is persistence enabled on your load balancer? Yes, it is.
Thank you.
If your load balancer is not terminating SSL, then you the Connection Servers need a certificate that matches the load balanced FQDN. You can use Subject Alternative Names to include multiple names.
Hi Carl,
Thanks fro your efforts.
We have Horizon 7.9 deployment 2 connection server, 1 security server, composer. All deployments are good but we face an issue when using WAN. We are using Riverbed Steelhead CX and created inpath rule.
WAN optimization working well when connecting to the VM using HTML on Blast protocol but unfortunately it is working for seconds when we using VMware horizon client then stopped while it is working on Blast HTML sessions very good, so kindly advise for this specially that both using same rule on Riverbed WAN optimization. the port is 8443 in destination between source (client ) and destination (security server:8443)
So kindly advise if this can be solved by VMware horizon or it is Riverbed configuration.
Thanks
Carl, in a HA environment were I have 2 security servers behind a load balanced vip and 2 internal connection servers (primary and replica), when I setup the second security server should I point it at the primary server or do they work in pairs and I need to point it at the second connection server?
Usually each Security Server is paired to a different Connection Server. For redundancy, you should have at least two pairs.
Hi Carl,
Can i ask you a question, were using Horizon View 7.6 and our SSL cert. is about to expire so i did the cert. request from within the Certificate manager on our connection server, imported the newly purchased SSL cert. in the Certificate Manager on the connection server (private key included), then did a export with Private Key and All Extended Properties.
Then imported the SSL certificate (with the Private Key) in the Certificate manager on out Security Server.
On both servers the certificate Friendly Name was renamed to vdm and the old SSL certificate was
But in Horizon View the Security Server shows an error message;
Status : The service has minor issue, The BLAST Secure Gateway is not working properly
IPSec Status : Not in Use
SSL Certificate : Valid
When i check the running Services on the Security Server i see that the “VMware Horizon View Blast Secure Gateway” is Paused, starting this manually gives the following message :
Windows could not start the VMware Horizon View Blast Secure Gateway service on Local Computer
The service did not return an error. This could be an internal Windows error or an internal service error.
When our users try to connect to our external Portal they get the following error message using the Horizon Application:
Connection Failed
Error: An SSL error occurred
Please verify that Connection Server Address and network settings are correct and try again.
And this error when they try to connect using a web browser :
Secure Connection Failed
An error occurred during a connection to myportal.company.com. Cannot communicate securely with peer: no common encryption algorithm(s). Error code: SSL_ERROR_NO_CYPHER_OVERLAP
But when i re-import my old SSL certificates and rename them to vdm on both Connection and Security Server the problem is gone and everything works fine.
Do you have any idea how to solve this problem.?
When you imported the new certificate, did you make sure the key is exportable?
What kind of certificate? Is it a ECDSA instead of RSA? What is the key size? There might be a log under c:\programdata\vmware\vdm that details the issue.
Yes the key is exportable, the certificate imported on the Security server shows that is has the private key, the certificate is an RSA type and the keysize I chose when ordering the certificate was 4096, but the certificate it self shows the public key as being RSA (2048)
I just checked the log file and it shows the following;
C:\ProgramData\VMware\VDM\logs\Blast Secure Gateway\absg.log
[2019-06-04 15:01:49.642] [ERROR] 3000 [absg-master] – keystoreutil.exe failed to load certificate from [ ‘windows-local-machine’, ‘MY’, ‘vdm’ ] 1 Key CryptExportKey get size FAILED (error 2148073483)
Found the issue this morning, so thought i’d share it.
When i tried to (as a test) export the certificate from the security server i noticed that the ‘export private key’ option was greyed out, this meant that during the import of the SSL certificate this option was not enabled (i probably didn’t notice it), even tho when i viewed the certificate it said ‘you have a private key for this certificate’, i removed the certificate and re-imported it this time i did check the option ‘make private key exportable’, rebooted both Connection and Security server after this just to be sure and the SSL error is gone.
To ensure the private key is exportable, try exporting the key. If the private key export option is grayed out, then it’s not exportable.
FIPS Mode On with Horizon 2209
RSA Sha 384 4096 on Horizon 2209 wouldn’t even load correctly.
RSA Sha 384 2048 on Horizon 2209 would load but the Blast Gateway throws the
keystoreutil.exe failed to load certificate from [ ‘windows-local-machine’, ‘MY’, ‘vdm’ ] 1 Key CryptExportKey get size FAILED (error 2148073483)
any ideas?
Is the certificate exportable?
Here’s some FIPS info. Cert must be there before installing Horizon. https://docs.vmware.com/en/VMware-Horizon/2209/horizon-installation/GUID-0BBDF7E2-AB3C-472C-B5AA-1A66F7D3E9DF.html
Hi Carl,
I’m getting this same error and my cert is exportable. Any suggestions?
I have everything up and running both internally and externally. My only issue is accessing externally through a web browser.
I just get a blank grey screen after clicking on the desktop link, this works internally through a web browser.
Any usggestions?
Thanks
Is port 8443 open from the Internet? Is port 22443 open from Security Server to every Horizon Agent? Does the Blast Secure Gateway have the correct URL?
Hi Carl,
thanks for the response. I can confirm port 8443 is open from the internet to the security server and port 22443 is open from the security server to all horizon agents.
For my “Blast Secure Gateway URL”, I have it set to my public facing URL with :8443 on the end. Is this correct?
Thanks
All working now
Thanks
How did you fix it?
We were able to solve our issues, our Wildcard certificate was created using the CNG Key Template which is unsupported by View, you have to use the Legacy Key Template.
Hello Carl. Cannot install Security Server (DMZ), error during installation “Error 28083 IPSec setup failed”. What could be wrong?
Is the Windows Firewall service running?
Yes, it is and all necessary ports are opened. Error occurs when using IPSec pairing option, without IPSec everythink is fine and SS connects to CS properly.
Did you install in FIPS mode?
no, without fips mode
Carl,
Thanks for a very helpful article! I do have one question on the certificate portion of this:
We purchased a GeoTrust wildcard certificate for our domain. As such, I did not go through the export portion of the certificate process that you outlined above (steps 1-6, notably the portions where you described how to make the private key exportable, then exported the certificate).
I did update the friendly name of the self-signed certificate by setting it to blank, then imported my GeoTrust certificate in to the same Personal->Certificates store, and set its friend name to vdm, and restarted the services.
However, when I then tried to access the server, I got an SSL error stating “ERR_SSL_VERSION_OR_CIPHER_MISMATCH”, along with a message that the site couldn’t provide a secure connection.
Any idea on what I might have done wrong, or any procedure changes that apply when using an existing wildcard certificate?
I set the friendly names back to their original settings and restarted the service, which allows me access to the security server again (with an invalid cert message). I’m no expert on certificates, so if I’ve made some basic mistake with this process, I won’t be terribly surprised…
Thanks in advance for any assistance you’re willing to provide.
Does your GeoTrust certificate have a private key? If you double-click it, on the first tab, on the bottom, there should be a message that there’s a private key.
Carl,
Thanks for following up on this. Looks like my default certificate did not have a private key. I’m going to refresh it with one that does include a private key. However, when I start that process (right click Certificates + All tasks + Request New Certificate), the first thing that pops up is the process that creates a new Certificate Enrollment Policy. That process prompts me for an Enrollment Policy Server URI. As the Horizon Security Server is not currently part of an A/D forest, does that mean that I need to install the Certificate Enrollment Policy Web Service and Certificate Enrollment Web Service on this machine?
If these topics are extraneous, I do apologize. My experiences with SSL certificates is pretty limited.
Thanks again!
You should be able to go to any IIS Server, run IIS Console, click the server, in the middle click Server Certificates and create a CSR. After you get the CSR signed, complete it in IIS, export the certificate from IIS, and then import to your Connection Servers.
I noticed this error “The service has minor issue.The PCOIP Secure Gateway is not working properly” in dashboard for 1 Connection Server which is paired with Security Server. Another Connection Server is working fine which is not paired is working fine. Disabling PCOIP tunneling in Connection Server settings has been a workaround. However, it is recommended to keep PCOIP tunneling checked. Any insight on this ?
We are noticing the same exact issue. Did you find a fix?
Carl, do you have any idea?
Thanks,
Matt
What version of Horizon?
We just upgraded from 7.2 to 7.6 and that is where we are running into this issue.
Thanks,
Matt
Was a resolution for this found? I have the same on 2 new connection servers.
Version: 7.6.0
Status: The service has minor issue.The PCOIP Secure Gateway is not working properly.
Hi,
This got resolved in 7.7
Hi Carl,
I am in need of some help here, Security server and Connection server are in place, Certificates are installed, access to virtual desktops from within the network is fine, users connect to virtual desktops using Horizon client and Connectionserver.domain.com as the address.
There is need to provide external access as well, i.e., from internet. the subdomain is available and configured, public IP is configured and Firewall is in place.
Front end firewall NAT the traffic to DMZ network (192.168.2.x) where security server is located (192.168.2.27) the same firewall NAT traffic again to Production network(10.10.10.x) where connection server is located (10.10.10.26)
I can see traffic on firewall coming to security server on port 443 TCP, from security server to connection server 8009 and 4002., But there is no traffic logged from connection server to security server.
User experience: open horizon client, enter url view.domain.com, user is prompted to provide credentials, upon providing credentials the error message immediately pops “You are not Entitled to use the system” the same user can access from within the network.
Apart from Desktop Pool Entitlements, you have to add the users under “Remote Access” tab found in “Users and Groups” section (left navigation menu). These are the users whom you want to be able to access desktops over internet or VPN.
I’m having an issue connecting from the outside, I set up 2 factor with our Radius Server. I get the prompt for our token and it takes it, but it just spins at Authenticating after i enter my Domain login. I have ports 1812 and 1813 open but im not sure if their is another port i need to open. I can login internally with no issues.
Does it work through Security Server without RADIUS configured?
RADIUS is enabled on the paired Connection Server. Does it work when pointing the client to the paired server?
What Horizon Client version?
Carl,
just a question.
We configured two security servers in DMZ paired with two dedicated connection servers.
Everything works with horizon View client installed on a pc and by webclient but using ipad/android app always go to timeout.
We configured a load balancer following your guide and it’s working too, only mobile client go to timeout.
Any ideas?
Thanks
I came across similar situation where I use Blast Extreme protocol on my android phone and i always got timeout.
Solutions:
At security server settings, make sure your Blast External URL matches your external FQDN/IP address and change the port 8443 to custom port if port forwarding is configured at firewall.
example:
Horizon Mobile Client address: https://vdi.abc.com
Then your Blast External URL will be: https://vdi.abc.com:8443 (If custom port for 8443 is configured at firewall, just change the port number)
Same if IP Address is used instead of FQDN.
in my case, I used ip address.
Carl,
Yes. I am using Horizon 7. I configured the pool to use Blast. When I configured the security server, it’s using port 8443. my external blast URL is https://mydesktop.domain.com:8443.
Thanks for your quick reply
8443 should only be used if you are connecting through a browser. Do you have the same issue with Horizon Client?
You can also use procmon on the client to verify the ports that are being used. If TCP, netstat will show you the connection. If UDP, then netstat won’t help you.
How can I use Blast Extreme protocol? I heard its uses only port 443 .This simplifies access and allows users to access it in many locations where ports 8443 and 8172 are blocked. I did not see any where to select this protocol. I saw only Blast and it needs port 8443 .
most places only port 443 is opened and no way you can access view desktops . any Solution for this?
Are you using Horizon 7? Edit your pool and set Blast as the protocol. It defaults to TCP 443 but you can use a GPO to enable UDP 443.