Navigation
- Preparation
- Install – Security Server
- Horizon 6 Security Server Certificate
- SSL
- Load Balancing
- Enable PCoIP Secure Gateway
Preparation
Security Servers are intended to be deployed in the DMZ.
Horizon View Security Server is installed on Windows. If you prefer a Linux appliance, see VMware Access Point.
Security Considerations for Horizon View 5.2 – http://www.vmware.com/resources/techresources/10371
Firewall Ports
If there is only one Security Server in the DMZ, create a NAT’d public IP to the Security Server. Create a public DNS entry that resolves to this IP address.
If there are two Security Servers and you intend to load balance them, create three public IPs:
- Public IP NAT’d to the load balancer IP. Create a public DNS entry that resolves to this IP address. This is the DNS name that users will enter into their Horizon Clients.
- Public IP NAT’d to each of the Security Servers. Each Security Server must be exposed directly to the Internet. Create public DNS names that resolve to these public IPs. When installing Security Server, specify these public DNS names and not the load balanced DNS name.
Note: your load balancer might be able to provide persistence across multiple port numbers and thus there’s no need for the server-specific public IPs. For example, in NetScaler this is called Persistency Groups.
Firewall Rules for View Connection Server at pubs.vmware.com.
Open these ports from any device on the Internet to all Security Server and Load Balancer public IPs:
- TCP 80
- TCP 443
- TCP and UDP 4172. UDP 4172 must be opened in both directions.
- TCP 8443 (for HTML Blast)
Open these ports from the Security Servers to internal:
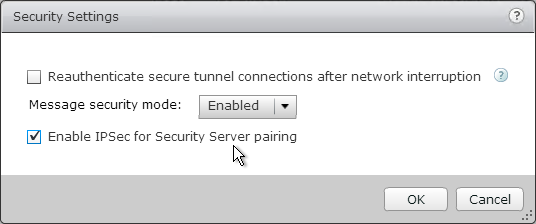
- If IPSec is enabled in View Administrator (Global Settings > Security > Edit), open ISAKMP Protocol (UDP 500) and ESP. Or if there is NAT between the Security Server and the Connection Server, open NAT-T ISAKMP (UDP 4500). Configuring a Back-End Firewall to Support IPsec at pubs.vmware.com.
- TCP 8009 (AJP13) to the paired internal Horizon 6 Connection Server.
- TCP 4001 (JMS) to the paired internal Horizon 6 Connection Server.
- TCP and UDP 4172 (PCoIP) to all internal Horizon View Agents. UDP 4172 must be opened in both directions.
- TCP 32111 (USB Redirection) to all internal Horizon View Agents.
- TCP 22443 (HTML Blast) to all internal Horizon View Agents.
- TCP 9427 (MMR) to all internal Horizon View Agents.
- TCP 4002 for Enhanced Messaged Security – Change the JMS Message Security Mode to Enhanced at pubs.vmware.com
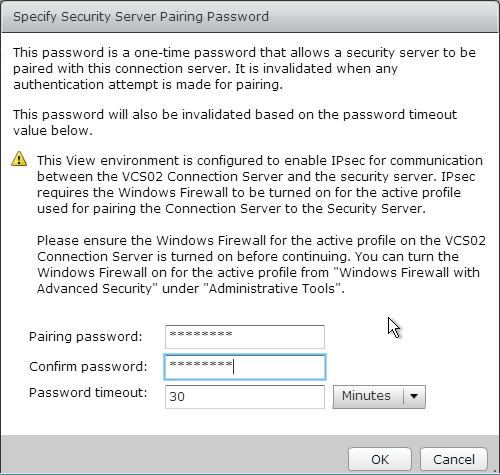
Pairing Password
- In View Administrator, on the left, expand View Configuration and click Servers.
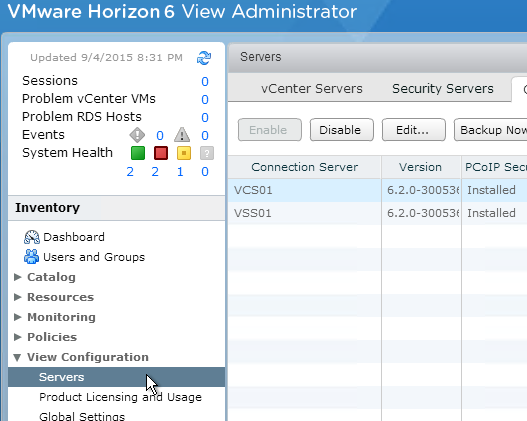
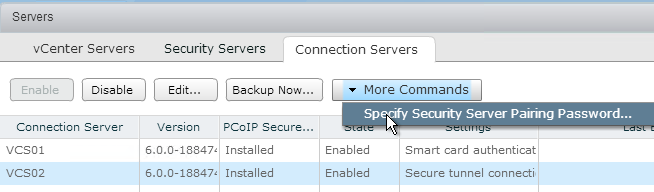
- On the right, switch to the Connection Servers tab.
- Select the Horizon 6 Connection Server to which the Security Server will be paired. Then click More Commands and click Specify Security Server Pairing Password.
- Enter a password and click OK.
Install – Security Server
- Ensure the Horizon 6 Security Server has 10 GB of RAM and 4 vCPU.
- Login to the Horizon 6 Security Server.
- Go to the downloaded Horizon 6 Connection Server 6.2.2 and run VMware-viewconnectionserver-x86_64-6.2.2.exe.
- In the Welcome to the Installation Wizard for VMware Horizon 6 Connection Server page, click Next.
- In the License Agreement page, select I accept the terms and click Next.
- In the Destination Folder page, click Next.
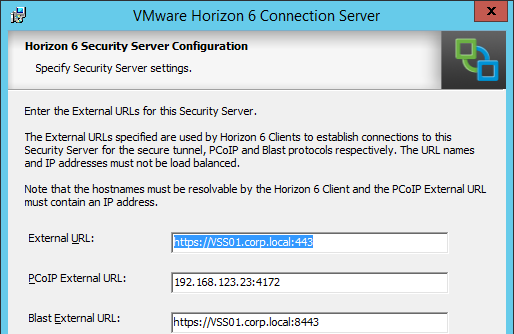
- In the Installation Options page, select Horizon 6 Security Server and click Next.
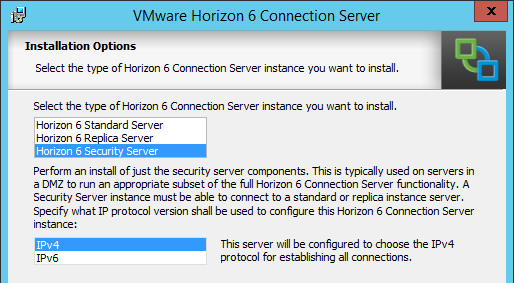
- In the Paired Horizon 6 Connection Server page, enter the name of the internal Horizon 6 Connection Server that this Security Server will be paired with. If using a hostname, it must be resolvable (edit the local HOSTS file) to the correct IP. Also, the correct firewall ports are required. Click Next.
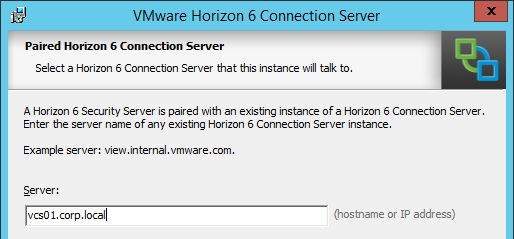
- In the Paired Horizon 6 Connection Server Password page, enter the pairing password specified earlier and click Next.
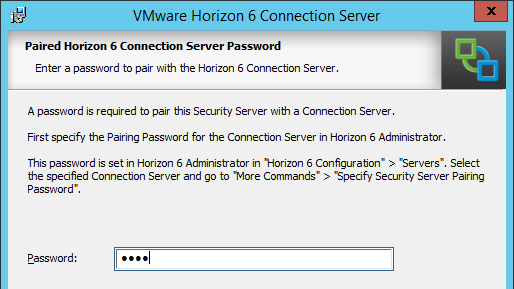
- In the Horizon 6 Security Server Configuration page, edit the URLs as appropriate. These URLs must be externally accessible. The top URL is a FQDN while the middle URL is an IP address. These can be changed later. Click Next.
- In the Firewall Configuration page, click Next.
- In the Ready to Install the Program page, click Install.
- In the Installer Completed page, click Finish.
SSL
Horizon 6 Security Server Certificate
- Run mmc, add the Certificates snap-in and point it to Computer > Local Machine.
- Request a new certificate with a common name that matches the FQDN of the HTTPS Secure Tunnel URL or import a wildcard certificate. If using a load balancer, the FQDN must match the load balancer FQDN, not the Security Server FQDN. Also, the private key must be exportable.
- Note: the private key must be exportable. You can either click Details to mark the key as exportable or use IIS to create the certificate.
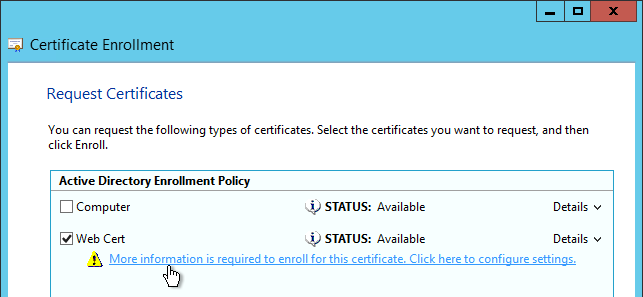
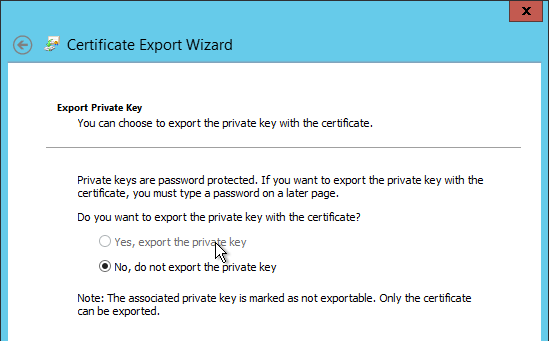
- After creating the certificate, try exporting it. If the option to export the private key is grayed out then this certificate will not work.
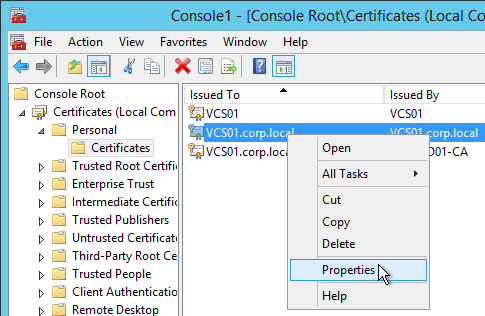
- In the list of certificates, look for the one that is self-signed. The Issuer will be the local computer name instead of a Certificate Authority. Right-click it and click Properties.
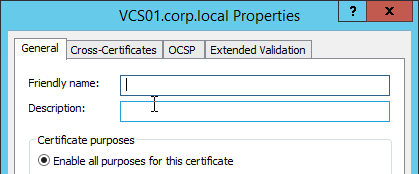
- On the General tab, clear the Friendly name field and click OK.
- Right-click your Certificate Authority-signed certificate and click Properties.
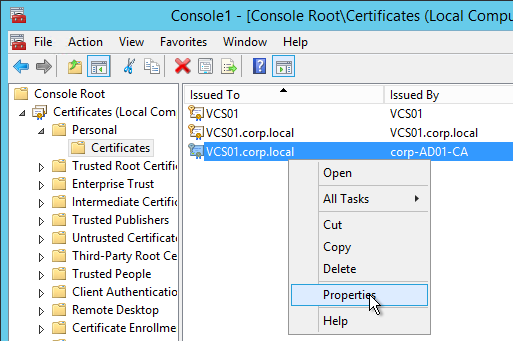
- On the General tab, in the Friendly name field, enter the text vdm and click OK. Note: only one certificate can have vdm as the Friendly name.
- Then restart the VMware Horizon 6 Security Server service.
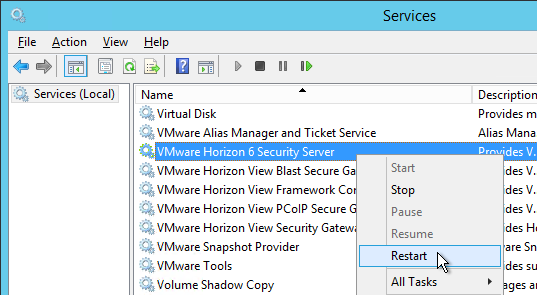
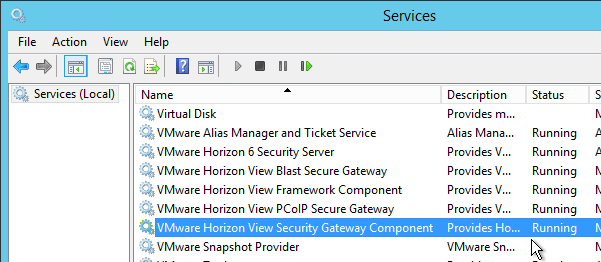
- If the VMware Horizon View Security Gateway Component won’t start then your certificate doesn’t have an exportable private key. The private key must be exportable.
Global Accepted Ciphers
VMware 2121183 Response to CVE-2015-4000 (a.k.a., Logjam) for Horizon View and Horizon 6 products: The default global acceptance and proposal policies are defined in View LDAP attributes. These policies apply to all Horizon 6 Connection Server instances in a replicated group and all security servers paired with them. To change a global policy, you can edit View LDAP on any Horizon 6 Connection Server instance.
For details about how to navigate to the correct View LDAP attributes, see the topics called Global Acceptance and Proposal Policies Defined and Change the Global Acceptance and Proposal Policies in the View Security guide. Note that although these links point to the 6.2 version of the guide, the topics are the same as those in the 5.2/5.3 and 6.0 versions of the guide.
- Change the pae-ClientSSLSecureProtocols attribute and the pae-ServerSSLSecureProtocols attribute as follows:
pae-ClientSSLSecureProtocols = "\LIST:TLSv1.2,TLSv1.1,TLSv1" pae-ServerSSLSecureProtocols = "\LIST:TLSv1.2,TLSv1.1,TLSv1"
This setting enables TLSv1.2 by default, to make use of the new cipher suites you will be adding when you set the next attributes.
- Change the pae-ClientSSLCipherSuites attribute and the pae-ServerSSLCipherSuites attribute as follows:
pae-ClientSSLCipherSuites = "\LIST:TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256, TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA, TLS_RSA_WITH_AES_128_CBC_SHA256, TLS_RSA_WITH_AES_128_CBC_SHA, SSL_RSA_WITH_RC4_128_SHA" pae-ServerSSLCipherSuites = "\LIST:TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256, TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA, TLS_RSA_WITH_AES_128_CBC_SHA256, TLS_RSA_WITH_AES_128_CBC_SHA, SSL_RSA_WITH_RC4_128_SHA"
Note that although these cipher suites are shown on separate lines to improve readability, when you edit this attribute, enter the cipher suites on one line with no spaces after the commas.
Also note that the last cipher suite shown in the list, SSL_RSA_WITH_RC4_128_SHA, should be omitted if all connecting clients support AES cipher suites.
To add 256-bit versions of the cipher suites, follow the instructions in the topic JCE Policy Files to Support High-Strength Cipher Suites in the View Security guide.
SSL Ciphers – Horizon 6 Security Server
Sven Huisman: Secure your Horizon View security server: from rating F to A-: see the blog post for detailed instructions.
- Update the JCE Policy Files to Support High-Strength Cipher Suites
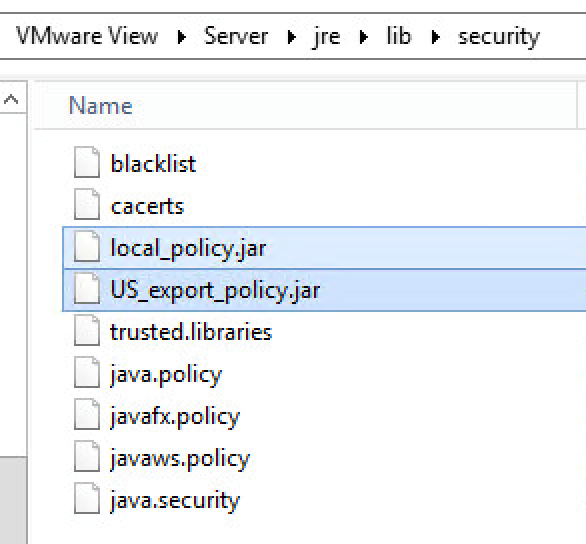
- Use ADSIEdit to change pae-ServerSSLCipherSuites, pae-ServerSSLSecureProtocols, pae-ClientSSLCipherSuites, and pae-ClientSSLSecureProtocols
- Or you can edit C:\Program Files\VMware\VMware View\Server\sslgateway\conf\locked.properties
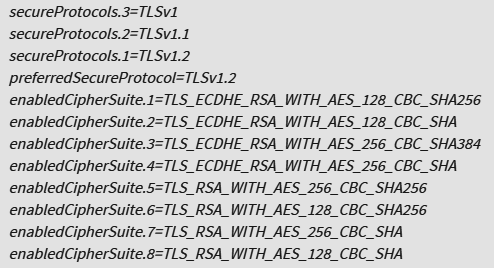
- If this Horizon 6 Connection Server or View Security Server is publicly accessible, check it at ssllabs.com.
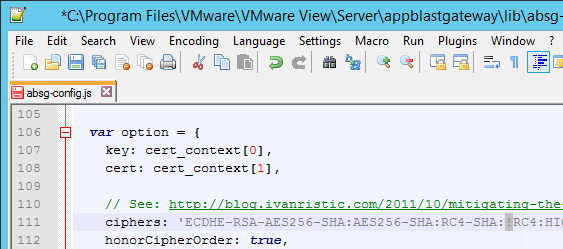
Disable RC4 – Blast Secure Gateway
VMware 2122359 Disable RC4 on Blast Secure Gateway: RC4 is already disabled in Horizon 6.2. Follow this procedure for older versions of Horizon View.
- Run an elevated text editor and open the file C:\Program Files\VMware\VMware View\Server\appblastgateway\lib\absg-config.js.
- Scroll down to line 111 and change :RC4: to :!RC4:.
Load Balancing
See Carl Stalhood – Horizon View Load Balancing
Enable PCoIP Secure Gateway
- In View Administrator, on the left, expand View Configuration and click Servers.
- On the right, switch to the Connection Servers tab.
- Click the Connection Server that is paired with the Security Server and click Edit. Note: you can’t configure this directly on the Horizon 6 Security Server and instead must configure it on the paired Horizon 6 Connection Server.
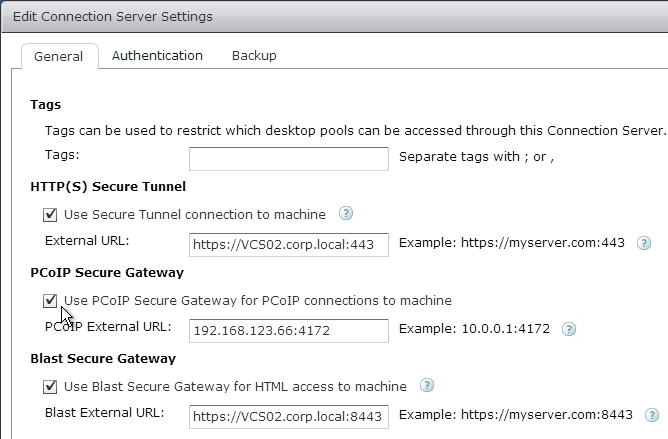
- On the General tab, check the box next to Use PCoIP Secure Gateway for PCoIP connections to desktop. Also, make sure Secure Tunnel and Blast Secure Gateway are enabled. Click OK.
Related Pages
- Back to VMware Horizon 6
Hi Carl, can you help. In my lab I have an RDS setup that works fine but I cannot access anything from outside. I have Proper Certs by that i mean purchased Certificates on both the connection and Security Server. I am able to connect internally either by the connection or Security Server.
My problem is from outside. I am in a view 6.2 environment, I have set the PCOIP url to my Public IP and the security Sever is resolvable by its fqn on the internet. I have also port forwarded ports 4172 and 8443 on my router for the security server. My security server is on my Public dns so its name is resolvable
When I try to connect from external I get route token missing. It doesn’t matter if I use https or http i get the same.
Please any advise will help as this driving me mad.
Are you using HTML Blast? Or are you using the full Horizon Client?
The Security Server is paired with a Connection Server. On the paired Connection Server, did you enable the Security Gateways?
Hi Carl Stalhood, I have a little problem for my Security server connection. In fact, I already configure everything, my router has the TCP 80, tcp 443 and tcp/udp 4172 ports open, there is no port redirection. The only thing I dont configure yet, it s the public DNS of my public IP… So do you thing that s why I cannot acces using a vmware horizon client to my security server ? I mean when I type the pubic IP adress in an internet browser I can access to the horizon index page. Or maybe it s something to configure in the view administration portal ?
Thanks in advance for your answer !
Regards.
FB
Are you able to connect the View Client and see the list of icons?
In View Administrator, did you specify the public IP for PCoIP Secure Gateway? On the paired Connection Server, did you enable PCoIP Secure Gateway?
In the View Administrator->View configuration6>Servers->Securityserver I put in the PCoIP Secure gateway : Public_IP:4172, in the External URL : https://localhostname:443
in the View Administrator->View configuration6>Servers->ConnectionServer I activate SecuredTunnel : https://FQDN:443, I activate PCoIP : Public_IP:4172 (is that correct ? or I need to put the local_IP of the Connection server ?), and I activate Blast Secure GateWay (but i guess is not yet necessary is nt ? ),
and no, with the View client I cannot access to nothing… (for connect myself i only click View Client-> Add new server->Public_IP) and after a lot of secondes, there is the error “expiration delay Reached”
when I use the InternetBrowser and type https://Public_IP I found 2 icons, VMware Horizon HTML Access and Installer vmware horizon client, if I click in the VMware Horizon HTML Access, I have the login window, but because I have not configured the BlastAccess it doesnt work….
I m really lost… do you think it s regarding some configuration I forgot ? (DNS name ?)
Thanks again Carl 😀 ! It s really nice to have somebody who helps 😀 !
Regards.
FB
I suspect that View Client requires a DNS name so the certificate is trusted. Simply edit your local HOSTS file.
That woooooooorks 😀 !
Nice 😀 !
And if I just go to the ViewClient->ConfigureSSL->Do not verify server identity certificates it works without an entry in the HOSTS file 😀 !!
after your last answer I knew that it was a problem regarding the SSL Certificate… Actually my SecurityServer has not a SSL certificate valid outside my local network… that s why the problem happens… do you have a site where I could purchase a good Certificate but not that expensive 😀 ? (an advice of course ^^)
Thank you very much for your help Carl 😀 !!
Really 😀 !
You re a good guy 😉 !
Regards
FB
Hi Carl,
I want to renew Certificate on my Security Server, but when I click Request a new certificate, I dont see any Certificate Enrollment Server listed, so what should I do?
Thanks for your advice.
There should be the default one from AD. That doesn’t work? Or maybe you don’t have an Enterprise CA. This is most likely a Microsoft issue.
If you have a regular public cert then you use IIS to renew it (request a new certificate).
Carl Thanks for the write up. I’m trying to setup a demo horizon environment and one thing that I can’t figure out is what network cards I should have on the Security Server. Currently I have 2 one with public IP and one with private. Is that what you had in your example here too ?
Also, the issue I’m heaving is that I can’t access horizon on the public IP. I can access it on the Security Server via https://127.0.0.1, but it seems that the server doesn’t bind to public IP address. I doubled checked the FQDN and the IP’s configured and didn’t see any typos. Do you have any ideas what it might be ?
Thanks,
Mike
Here’s a VMware article – http://kb.vmware.com/selfservice/microsites/search.do?language=en_US&cmd=displayKC&externalId=1024610
I personally only ever do a single NIC in the DMZ and let physical firewalls filter the traffic.
If you do a
netstat -aon | find "443", it should show 443 bound on all IPs.Does it work from a machine on the same subnet? What is the default gateway? Typically the gateway should be an Internet router and use static routes for internal destinations.