Navigation
This page details creation of session profiles and policies for NetScaler Gateway 10.5 where ICA Only (formerly known as Basic Mode) is checked.
Partly based on Citrix Knowledgebase Article – How to Configure NetScaler Gateway with StoreFront
Session Profiles/Policies CLI Commands
The CLI commands are shown below:
add vpn sessionAction "Receiver Self-Service" -transparentInterception OFF -defaultAuthorizationAction ALLOW -SSO ON -icaProxy ON -wihome "https://storefront.corp.com" -ntDomain Corp -clientlessVpnMode OFF -storefronturl "https://storefront.corp.com" add vpn sessionAction "Receiver for Web" -transparentInterception OFF -defaultAuthorizationAction ALLOW -SSO ON -icaProxy ON -wihome "https://storefront.corp.com/Citrix/StoreWeb" -ntDomain Corp -clientlessVpnMode OFF add vpn sessionPolicy "Receiver Self-Service" "REQ.HTTP.HEADER User-Agent CONTAINS CitrixReceiver" "Receiver Self-Service" add vpn sessionPolicy "Receiver for Web" "REQ.HTTP.HEADER User-Agent NOTCONTAINS CitrixReceiver" "Receiver for Web"
Session Profiles
Or use the GUI to create the policies/profiles:
- On the left, expand NetScaler Gateway, expand Policies, and click Session.
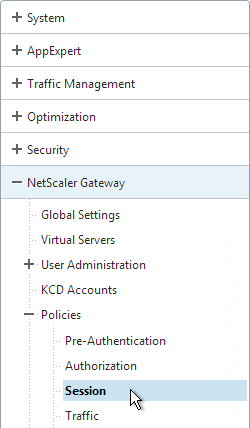
- On the right, switch to the Session Profiles tab, and click Add.
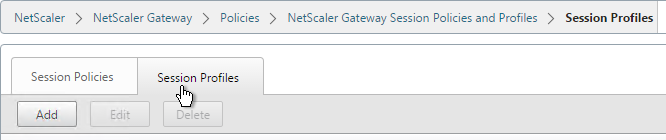
- Name the first one ReceiverSelfService or similar. This is for Receiver Self-Service (not in a web browser).
- Switch to the Client Experience tab.
- Check the Override Global box next to Clientless Access, and set it to Allow. Scroll down.
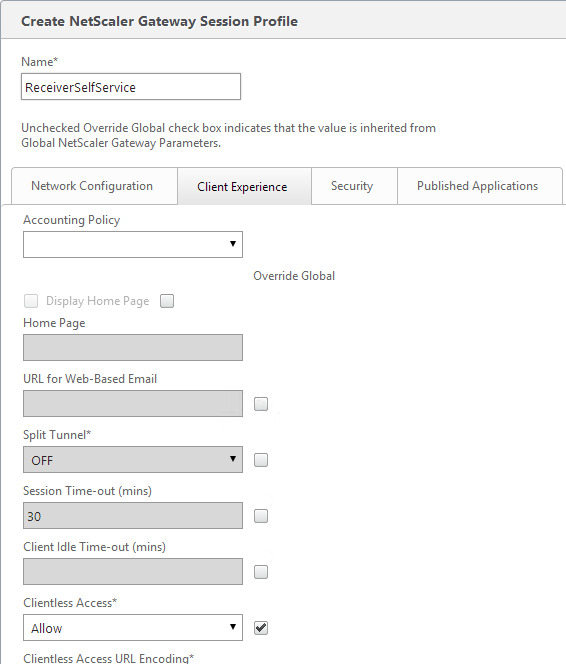
- Check the Override Global box next to Plug-in Type and set it to Java.
- Check the Override Global box next to Single Sign-on to Web Applications and enable it. Scroll up.
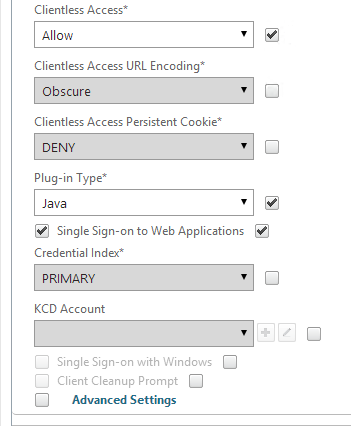
- If you need two-factor authentication, the session policy for Receiver Self-Service needs to be adjusted to indicate which authentication field contains the Active Directory password. On the Client Experience tab is Credential Index. This needs to be changed to SECONDARY. Leave the session policy for Web Browsers set to PRIMARY.
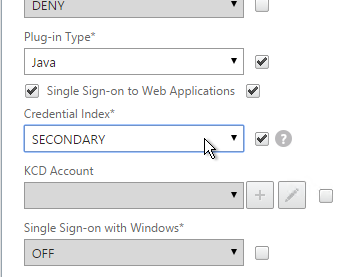
- On the Security tab, check the Override Global box next to Default Authorization Action and set it to Allow.
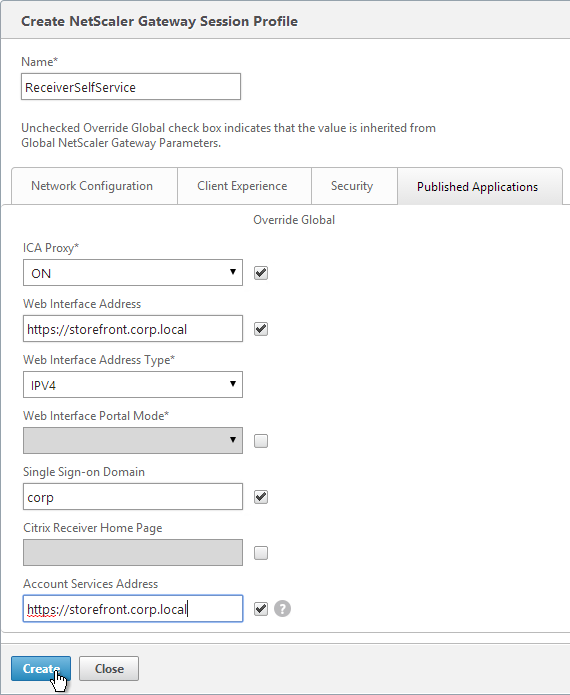
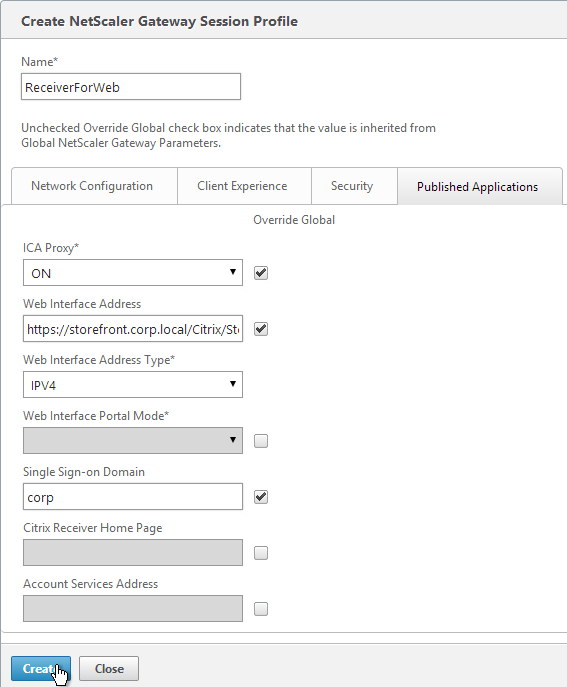
- On the Published Applications tab, check the Override Global box next to ICA Proxy and set it to ON.
- Check the Override Global box next to Web Interface Address, and enter the load balanced URL to the StoreFront servers. You can use an IP address. Don’t add any path to the end of the URL.
- If you only have one domain, then check the Override Global box next to Single Sign-on Domain and enter the name of your Active Directory domain. StoreFront needs to accept this domain name (Configure Trusted Domains).
- If you have multiple domains, then leave Single Sign-on Domain field blank, and ensure the LDAP authentication servers have userPrincipalName in the SSO Name Attribute field.
- For Account Services Address, enter the Base URL for StoreFront. NetScaler needs to be able to resolve this DNS name.
- Click Create.
- Highlight the existing session profile, and click Add. This copies the settings from the existing profile into the new one.
- Change the name of the second Session Profile to ReceiverForWeb or similar.
- On the Client Experience tab, Clientless Access should be set to Allow. Scroll down.
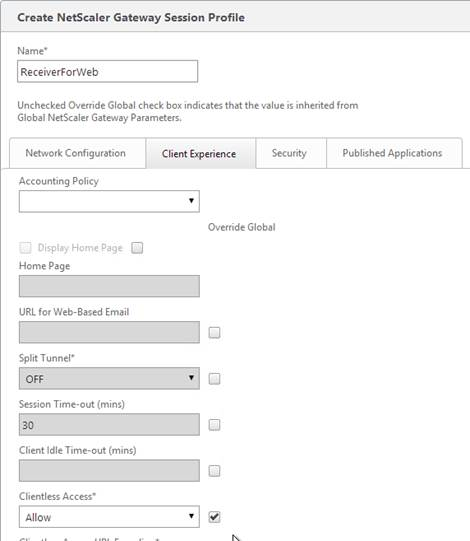
- Plug-in Type should still be set to Java.
- Single Sign-on to Web Applications should be enabled.
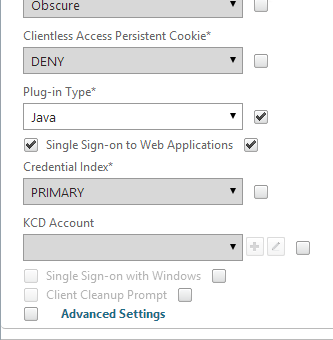
- If you need two-factor authentication, the session policy for Receiver for Web needs Credential Index set to PRIMARY. Only the Receiver Self-Service policy needs SECONDARY as detailed earlier.

- On the Security tab, the Default Authorization Action should still be Allow.
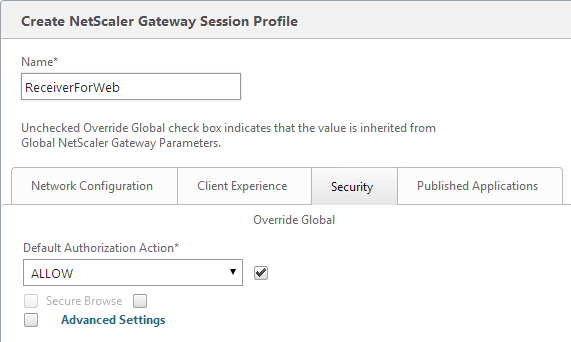
- On the Published Applications page, for the Web Interface Address field, add the path to your Receiver for Web site (e.g. /Citrix/StoreWeb).
- Everything else should be the same. If you only have one domain, then check the Override Global box next to Single Sign-on Domain and enter the NetBIOS name of your Active Directory domain. If you have multiple domains, then leave this field blank and ensure the LDAP authentication servers have userPrincipalName in the SSO Attribute field.
- Account Services Address is not needed in this profile but there’s no harm in leaving it.
- Click Create.
Session Policies
- On the right, switch to the Session Policies tab, and click Add.
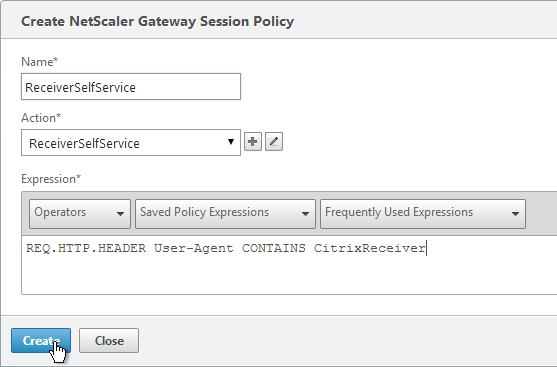
- Name the Policy ReceiverSelfService or similar.
- Change the Request Profile to ReceiverSelfService.
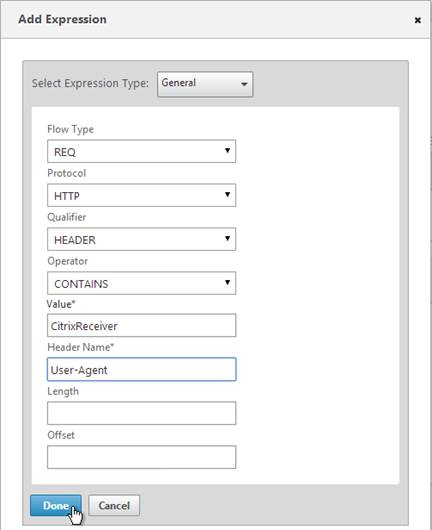
- In the Expression box, either type the following, or use the Expression Editor link to build the following expression:
REQ.HTTP.HEADER User-Agent CONTAINS CitrixReceiver
- Then click Create.
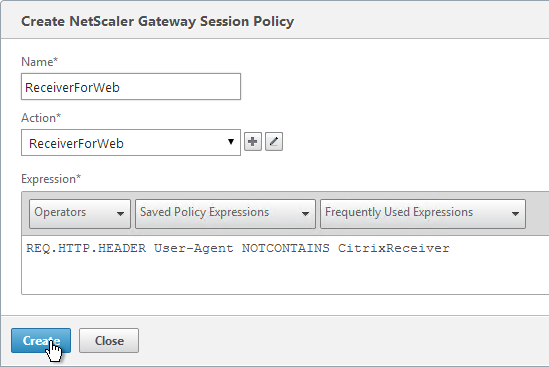
- Add another policy, and name it ReceiverForWeb or similar.
- Change the Action to ReceiverForWeb.
- In the Expression box, either type in the following, or use the Expression Editor. It’s the same as the previous expression, except it’s NOTCONTAINS instead of CONTAINS.
REQ.HTTP.HEADER User-Agent NOTCONTAINS CitrixReceiver
- Click Create.
Hi Carl,
With Web interface 5.4 we were able to use AAA groups and direct session policies to different PnAgent Config.xml files based on AD Groups, This provided us a way to present Desktops only for some folks, Apps only for few and Both for the rest.
by simply changing the group permissions we were able to remove or provide access to resources when connecting from mobile receiver clients.
How can i translate this to storefront? we would like the same functionality [dynamic store switch] avoiding our users to select a store?
Note: our need for separate stores stem for hiding resources with keywords and presenting only desktops/only apps/both with default to apps or desktop
Hi Carl,
I would appreciate your insight. I have an Azure based Netscaler. Working pretty well after considerable tinkering. I’m trying to set individual policies for particular clients as many examples present on the web (iPad, Chromebook, windows). On my system I cannot get the classic tests like CONTAINS CitrixReceiver to work. I’m monitoring policy hits and testing. I get “CONTAINS citrix” to work, CONTAINS iPAD works, but none of the other classic examples like “CONTAINS Chromebook/” (or crOS)
Any slick way for me to capture (short of Wireshark) the HTTP headers so I see why this conditional tests are not evaluating to TRUE?
Thanks
One option is to create a Responder of type “Respond With” and set the Action to display HTTP.REQ.HEADER(“User-Agent”). This should show you in a browser the actual User-Agent string that NetScaler is seeing. But probably won’t work for Receiver.
Another option is for your Responder to include a user-defined logging policy that logs HTTP.REQ.HEADER(“User-Agent”) to Syslog (/var/log/ns.log).
Thank You Carl for the prompt response. I’m afraid you’re assuming a much more advanced understanding of the Netscaler. Would you happen to know a URL that has some example of what you’re referring to?
I’ve been trying to setup custom audit or logging for this, but so far I can not find any results in any logs. Still the same problem I built the basic rule testing for CitrixReceiver using the expression builder. No hit on this policy. It’s entirely possible I’m missing something very fundamental regarding this part of the system.
Regards
Kevin
Hi Carl
Can you please help me with getting this to work on the netscaler web interface, all the posts that I see are with storefront but we use webinterface on the netscaler to present applications. I can get the default domain to work if I leave the sso blank in session policy but then it will not work for the trusted domain, or if I specify the trusted domain in the SSO on session policy then only that works the the other domain doesnt.
Thanks
Hi Carl , thank you for your awesome contribution, I have been scouring the websites and I am trying to find if you can have the configuration Netscaler gateway – Web Interface – Windows Receiver. I have set up my session policies , I can use receiver for Android no problem , but when I try it with the windows receiver get an error , server cannot be added or you cannot use this address. I use the same details for android and it connects. This is is not using storefront . They have no problem when using the access gateway physical appliance , but the VPX appliance does not work. Web interface works , Android works just windows receiver does not.
PNAgent for Windows is not able to authenticate with NetScaler Gateway. Mobile devices can, but Windows cannot. It should work internally, however.
Hi Carl as usual , you are the number 1 go to guy , thank you and kind regards. I did go through the netscaler 11 documentation but could not find anything that stated that windows receiver aka pnagent is not supported.Where would i get an official response to present to the customer.
See Remote Access via NetScaler Gateway at https://www.citrix.com/content/dam/citrix/en_us/documents/products-solutions/citrix-receiver-feature-matrix.pdf
Thank you kind regards
Hi Carl, many thanks for all your articles. They have been a great help on many occasions.
We have remote users that are coming in from outside our company and on their own devices.
We have 3 external sites http://www.oursite.com, gateway.oursite.com and dev.oursite.com. The first site is for just Published Apps and Desktops only, the second for SmartAccess users & the last for testing new functionality. These were split out for NS licensing reasons.
From Storefront 2.6, we created 3 stores; www, gateway and dev, one for each remote FQDN.
The Storefront servers are behind one LB VIP on Netscaler v11.0 63.16.
The Netscaler session policies set up work fine for NonReceiver clients, the users are directed to the respective Store depending on what FQDN they connect to.
When a user logs on from Receiver, tested on Android and Windows, they get to Add Account page. When you put in http://www.oursite.com, click next, put in user credentials and hit next again, it gives a second Add Account page, where it lists the 3 Stores.
Is there any way that I can set up Netscaler/Storefront, so that depending on incoming FQDN, the receiver will only show the one respective Store?
any help greatly appreciated.
I don’t think much can be done in this release other than to build separate StoreFront servers for each store.
The next StoreFront does a better job of separating configs on a per-store basis but I haven’t tested Receiver’s behavior when there are multiple stores on one StoreFront server.
Hi Carl
Have you had a chance to test this and find a good workaround other than building seperate storefront servers?
Regards
Martin
One option is to hide stores and require users to enter the store name.
Otherwise, see https://docs.citrix.com/en-us/storefront/3-11/plan.html#par_anchortitle_87ff
With regard to point 10, “10.Check the Override Global box next to Web Interface Address and enter the load balanced URL to the StoreFront servers. You can use an IP. Don’t add any path to the end of the URL.”
I used this configuration on SF3.0 / NS10.1 and all was fine, however after an upgrade to NS11.0.62.10 the NSG -> SF redirect fails to work after a successful login.
It will only work after you put the full path to the SF Storename on the Web Interface Address URL for the RfW StoreFront Profile on the Published Applications tab. Once this change is made all works fine.
For Browser users, yes the path needs to be there. But not for Receiver Self-Service users. The first policy is for RSS and the second is for browsers.
hi Carl i really need you help, i have a wildcard domain certificate created on my storefront servers and imported also to the ddc and to the netscaler gateway. the netscaler gateway has also a wildcard public certificate pointing to the registered dns name . My issue is when i try adding an account to the citrix receiver on a computer which is not in our domain but still on the same network by pointing to the xxx.domain.local i get the message the certificate is not trusted but when i go via web browser i can get in by just ignoring the message, i there any way to add the account to the receiver without having that warning?
how can make the storefront load balancer on the netscaler work with pNAgent link? when i type that link into the receiver i get message that the server can not be contracted or is not available
My guess is that your internal certificate has a CRL Distribution Point that is not accessible by non-domain machines. If you have non-domain machines then I usually recommend a publicly signed certificate.
For PNAgent, you’re entering https://storefront.corp.com/Citrix/Store/PNAgent/config.xml?
no i enter .local for pnaagent, also i dont have any session profile for pnagent on the netscaler, dont know how to do it , i only have the two profiles from your guide the self receiver and the receiver for web.
can i change my load balancing storefront internal dns from pointing to storefront.corp.local to storefront.corp.com adn my netscaler vip and external dns change from storefront.corp.com
to storefrontlb.corp.com and atach the wildcard public certificate to both on the netscaler and leave the storefronts and the ddc which are internal with internal certificate so solve this issue?
also i am not using callback since i dont use domain passthrough, so i dont have it set up on my storefronts does callback affect my issue with the thin clients not being on the domain?
Using a public cert for anything directly accessed by users would work.
PNAgent doesn’t work through NetScaler Gateway so don’t do it.
question what is call back functionality exactly doing if i dont have single sign on and domain pass through enabled ?
Callback is only needed for SmartAccess (Access Control filters in your policies and published apps).
Dear Carl,
My Netsceler able to login , but after redirect Storefront receiver, AD user authentication is failure .
Do you have a Session Policy that is sending the correct domain name to StoreFront? Is StoreFront configured to accept the domain name? On StoreFront, look in Event Viewer > Applications & Services > Citrix Delivery Services.
thanks a lot. very helpfully for me.
Ah, OK! Now I see the difference.
THX!!
Hi Carl,
I read many of your posts and am thrilled. But I may believe this is an error. The URL for the Storefront server in the session profiles should read it:
https: //storefront.corp.local/Citrix/StoreWeb
or not?
There are two session profiles: one for Receiver and one for Browsers. The one for Receiver should only point to the root of the StoreFront URL. The one for Browsers (aka Receiver for Web) should point to the StoreWeb URL. Which one did I do wrong? You can also see http://support.citrix.com/article/CTX139963 for the official instructions.
Hi Carl,
I have a question. I have 10.5 NS with the existing mobile policy pointing to PNAgent/Config.xml of a Web Int that works fine. I am trying to replace this address with the SF site. The SF VIP and the full path to the store didnt work. What needs to go in Web Int address ?
Thanks
If you configured everything as detailed in this post, I would enable logging in Receiver. http://support.citrix.com/article/CTX132883
Did you re-activate Receiver so it downloads the provisioning file?