Navigation
- Change Log
- Overview
- LDAP Policies/Actions
- Login Schemas
- Authentication PolicyLabel
- AAA vServer
- Traffic Policy for Single Sign-on
- NetScaler Gateway and Authentication Profile
- Update Content Switching Expression for Unified Gateway
- Manageotp
- CLI Commands
Change Log
- 2019 Feb 4 – Login Schemas – added link to Morten Kallesoee n-Factor – restrictions on native OTP management
- 2018 Oct 6 – Overview – Workspace app 1809 and newer with Citrix Gateway (NetScaler) 12.1 build 49 and newer support nFactor (and OTP) authentication.
- Updated screenshots for Citrix ADC 12.1
- 2018 June 15 – Login Schemas – added link to Stan Demburg NetScaler Native OTP – Prevent Enrollment Of Additional Devices Externally
- 2018 Mar 18 – in the Traffic Policy section, added info from Julien Mooren NetScaler – Native OTP is breaking SSL VPN.
Overview
NetScaler Native OTP lets you enable two-factor authentication without purchasing any other authentication product. A typical configuration uses Google Authenticator to generate Passcodes. See the following for an overview:
- Citrix Blog Post NetScaler Unified Gateway Provides One Time Password (OTP), Natively
- Citrix Docs Native OTP support for authentication
Here are some notes:
- NetScaler Native OTP is part of nFactor, and thus requires Citrix ADC Advanced Edition (aka NetScaler Enterprise Edition) or Citrix ADC Premium Edition (aka NetScaler Platinum Edition) licensing. NetScaler ADC Standard Edition licensing is not sufficient.
- Workspace app 1809 and newer with Citrix Gateway (NetScaler) 12.1 build 49 and newer support nFactor authentication. Older Receivers and older NetScalers don’t support it, so you’ll instead have to use a web browser. 💡
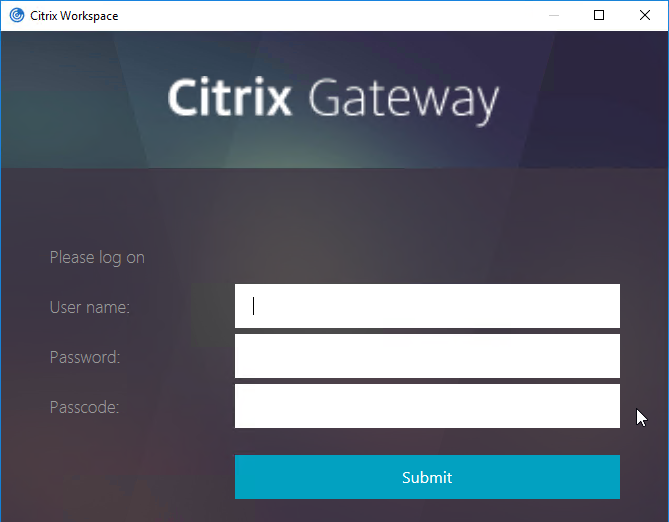
- Citrix Gateway VPN Plug-in 12.1 build 49 and later support nFactor when authenticating using the VPN Plug-in. 💡
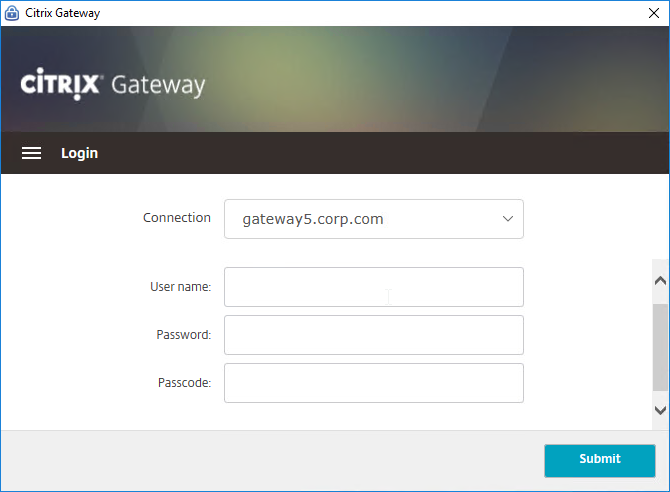
- nFactor requires a AAA vServer, which can be non-addressable – you don’t need any additional public IPs.
- OTP stores device enrollment secrets in an Active Directory attribute that accepts Strings. Citrix’s documentation uses the userParameters Active Directory attribute.
- The LDAP bind account must have permission to modify this attribute on every user.
- Users can enroll multiple devices. There’s no way to prevent this.
- The manageotp website is usually only protected by single factor authentication. Since users can add multiple devices, the manageotp website must be protected from external access.
- Christian in the comments indicated that Microsoft Authenticator also works. Click on plus sign -> other (Google,…).
Here are the OTP configuration objects:
- Make sure NTP is configured on the NetScaler. Accurate time is required.
- An LDAP Policy/Server with authentication disabled and OTP Secret configured. This one OTP-specific LDAP Policy/Server can be used for two scenarios:
- manageotp device enrollment
- Two-factor authentication to NetScaler Gateway after a device has been enrolled. This LDAP Policy/Server verifies the entered passcode.
- An LDAP Policy/Server with authentication enabled. This one policy is used for two scenarios:
- Single-factor authentication to the manageotp authenticator/device enrollment website.
- Two-factor authentication to NetScaler Gateway after a device has been enrolled.
- A single non-addressable AAA vServer with two Login Schemas for the following scenarios:
- A single-factor Login Schema for manageotp.
- A dual-factor Login Schema for NetScaler Gateway authentication.
- An Authentication Profile to link the AAA vServer to the NetScaler Gateway vServer.
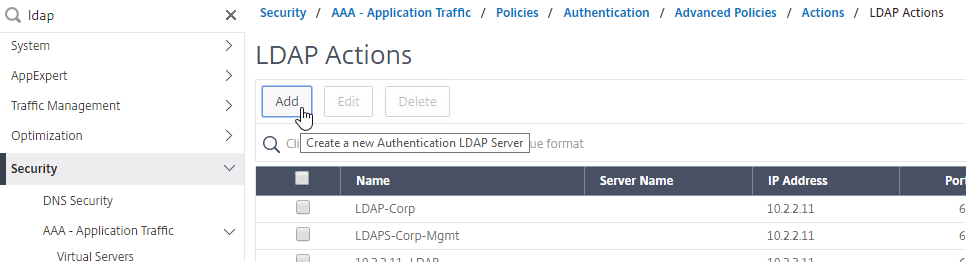
LDAP Policies/Actions
- Go to Security > AAA – Application Traffic > Polices > Authentication > Advanced Policies > Actions > LDAP.
- On the right, click Add.
- Create a normal LDAP Server if you don’t have one already. This one has Authentication enabled. This LDAP Policy/Server will be used for single-factor authentication to the manageotp website, and for first factor of dual-factor authentication to NetScaler Gateway (second factor is OTP). There are no special instructions for this LDAP Server.
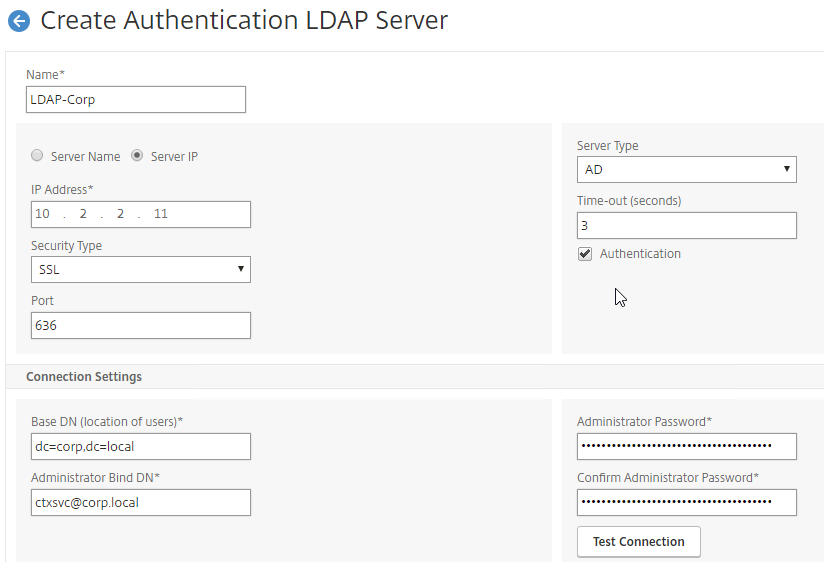
- Create a normal LDAP Server if you don’t have one already. This one has Authentication enabled. This LDAP Policy/Server will be used for single-factor authentication to the manageotp website, and for first factor of dual-factor authentication to NetScaler Gateway (second factor is OTP). There are no special instructions for this LDAP Server.
- Create another LDAP Action.
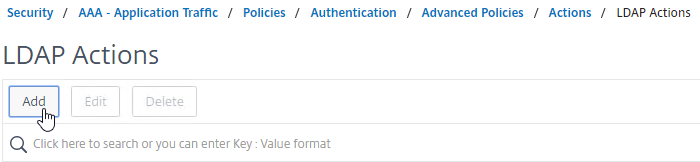
- This one is used by the manageotp site to set the OTP authenticator in Active Directory, so name it accordingly.
- On the right, uncheck the box next to Authentication. If you don’t uncheck it, you will see an error message after configuring the OTP Secret.
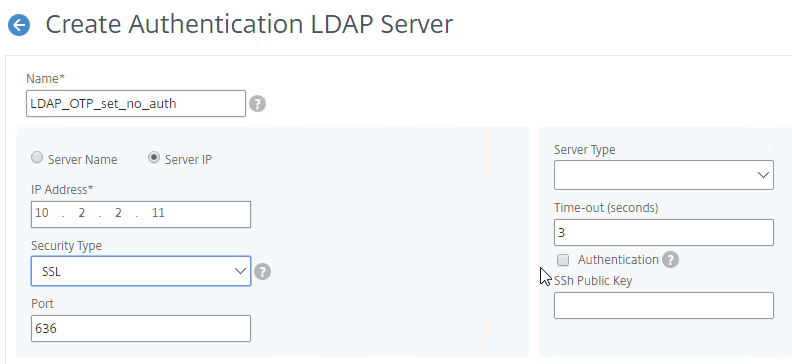
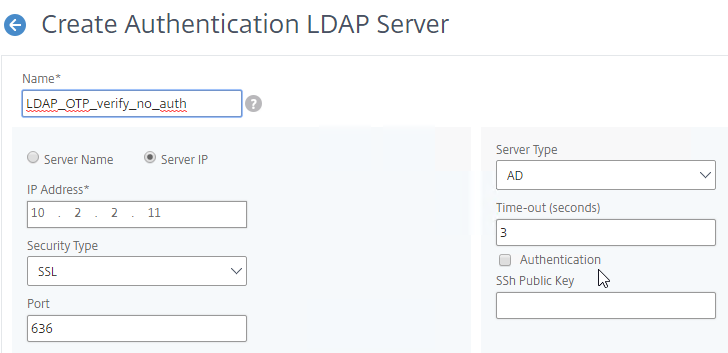
- Make sure the Administrator Bind DN has permissions to modify the OTP Secret Active Directory attribute for all users.
- If you cloned an existing LDAP Server, then make sure you re-enter the Administrator Password or the new one won’t work. Then click Test LDAP Reachability.
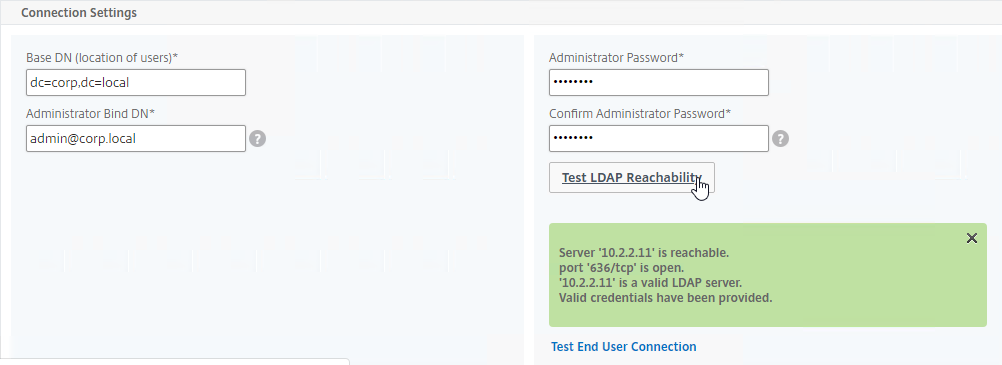
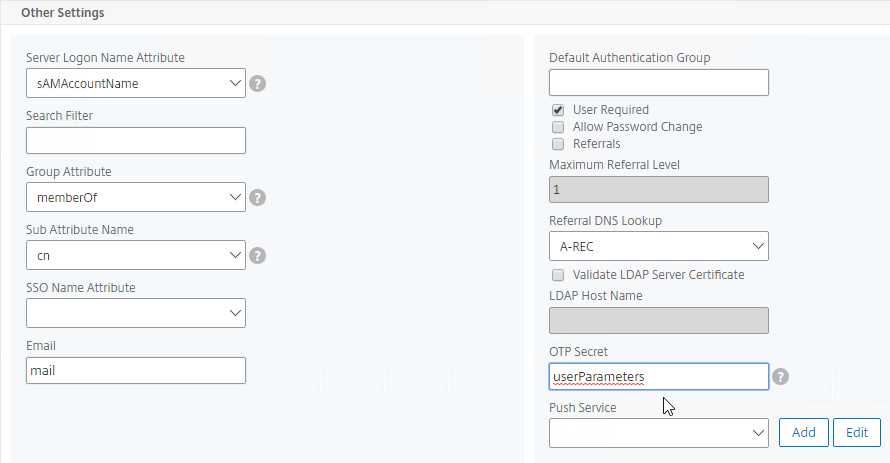
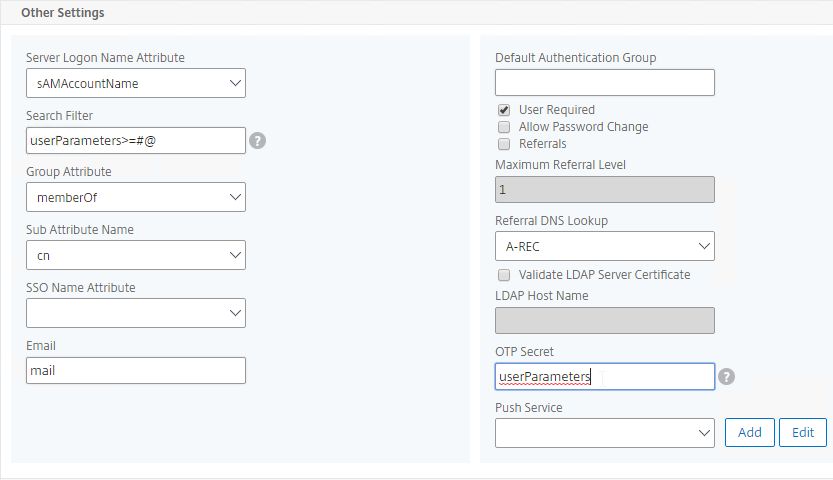
- Configure the Server Logon Name Attribute to match the one you configured in the normal authentication LDAP Server.
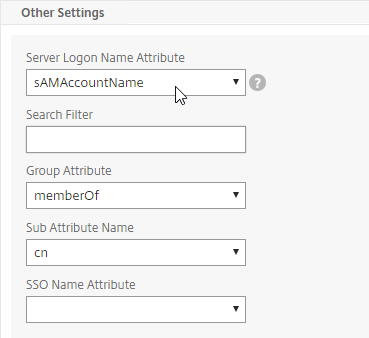
- In the Other Settings section, on the bottom right, find the OTP Secret field. Enter the name of the Active Directory attribute where NetScaler will store the user’s OTP secret. You can use the userParameters attribute if that attribute isn’t being used for anything else.
- Thomas Rolfs in the comments advises not to enable Nested Group Extraction in this LDAP Action.
- Click Create when done.
- Create another LDAP Action.
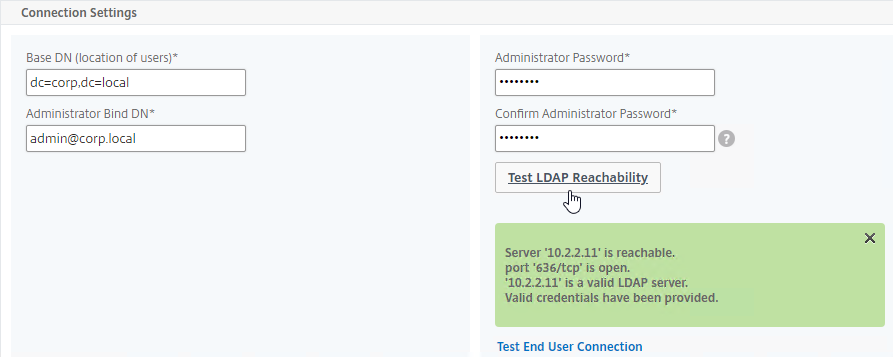
- This one will verify the OTP code entered by the user, so name it accordingly. The only difference from the prior one is the addition of an LDAP Search Filter.
- On the right, uncheck the box next to Authentication. If you don’t uncheck it, you will see an error message after configuring the OTP Secret.
- Make sure the Administrator Bind DN has permissions to read the OTP Secret Active Directory attribute.
- If you cloned an existing LDAP Server, then make sure you re-enter the Administrator Password or the new one won’t work.
- In the Other Settings section, configure the Server Logon Name Attribute to match the one you configured in the normal authentication LDAP Server.
- In the Search Filter field, enter the text userParameters>=#@. This syntax ensures that only users with enrolled authenticators can login. See George Spiers NetScaler native OTP for more info.
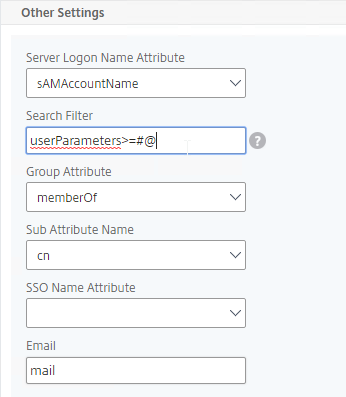
- In the Other Settings section, on the bottom right, find the OTP Secret field. Enter the name of the Active Directory attribute containing the user’s OTP secret.
- Click Create when done.
- Go to Security > AAA – Application Traffic > Policies > Authentication > Advanced Policies > Policy.
- On the right, click Add.
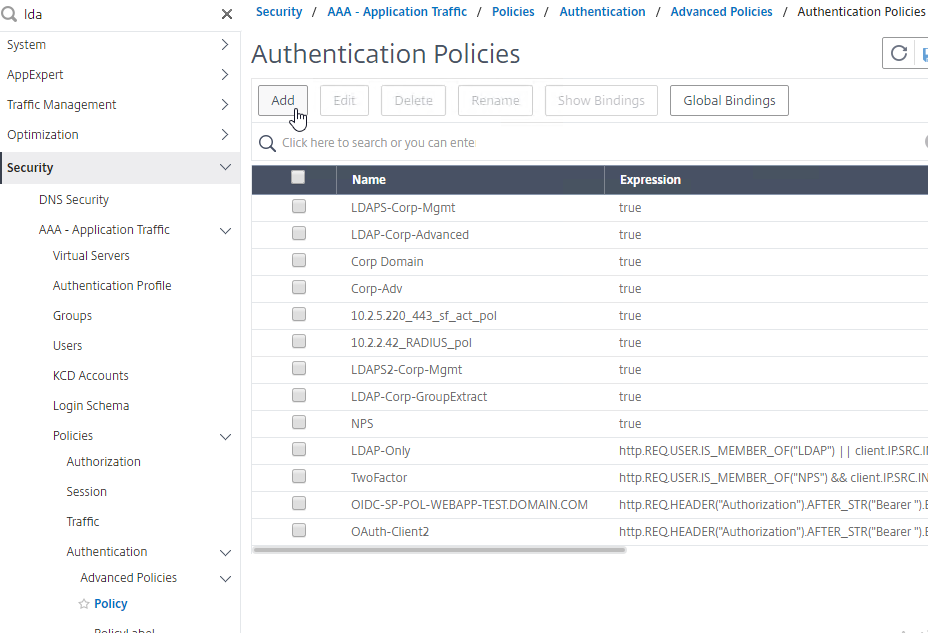
- You probably don’t already have an Advanced Authentication Policy for your normal LDAP server.
- Change the Action Type to LDAP.
- Select your normal LDAP server, which is the one that has Authentication enabled.
- Enter true as the expression. This uses Default Syntax instead of Classic Syntax.
- Click Create.
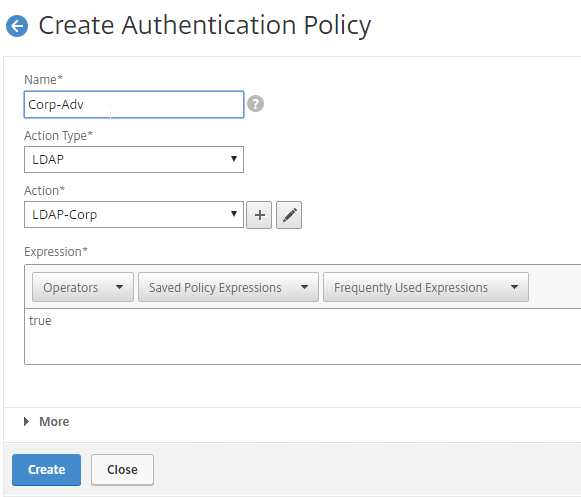
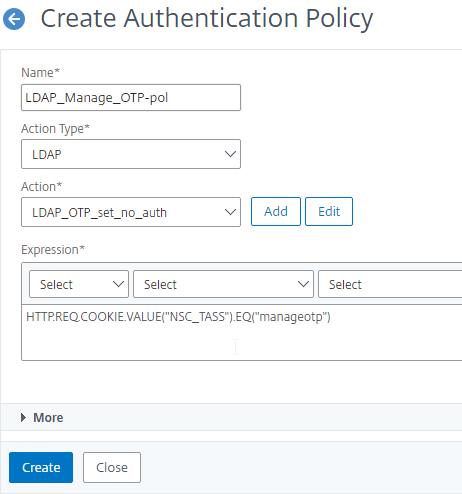
- Create another Authentication Policy.
- This policy is for OTP management so name it accordingly.
- Change the Action Type to LDAP.
- Select the Set OTP LDAP Server that has Authentication disabled and OTP Secret configured. This LDAP Action should not have the Search Filter configured.
- Enter HTTP.REQ.COOKIE.VALUE(“NSC_TASS”).EQ(“manageotp”) in the Expression box, and click Create.
- Create another Authentication Policy.
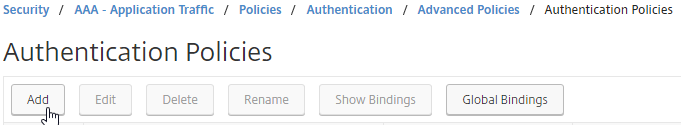
- This policy is for OTP verification so name it accordingly.
- Change the Action Type to LDAP.
- Select the OTP Verification LDAP Server that has Authentication disabled and OTP Secret configured. This LDAP Action should have the Search Filter configured to prevent unenrolled users from authenticating.
- Enter true in the Expression box, and click Create.
Login Schemas
- Go to Security > AAA – Application Traffic > Login Schema.
- On the right, switch to the Profiles tab, and click Add.
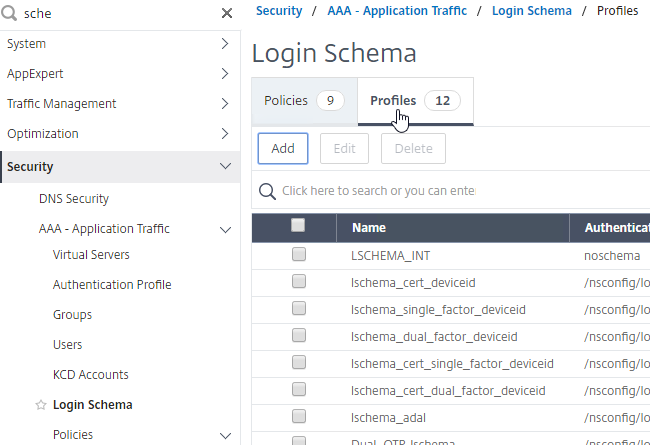
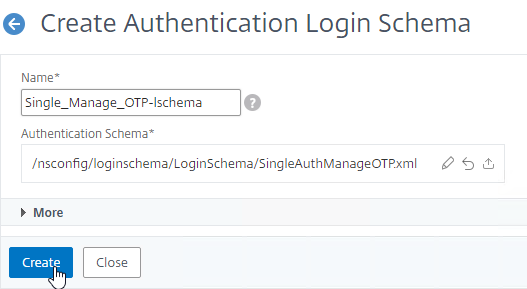
- This is the single factor Login Schema for manageotp so name the Schema accordingly.
- Click the Edit icon.
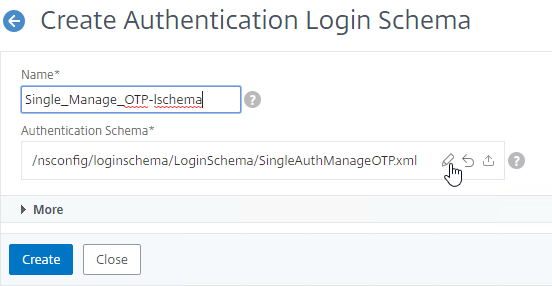
- On the left, click the LoginSchema folder to open it.
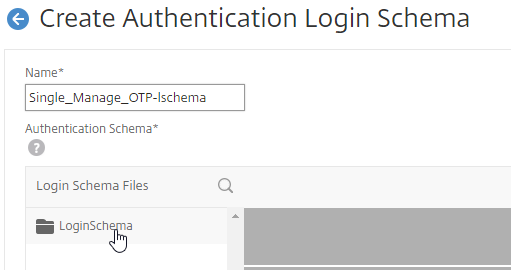
- Scroll down, and click SingleAuthManageOTP.xml to highlight it.
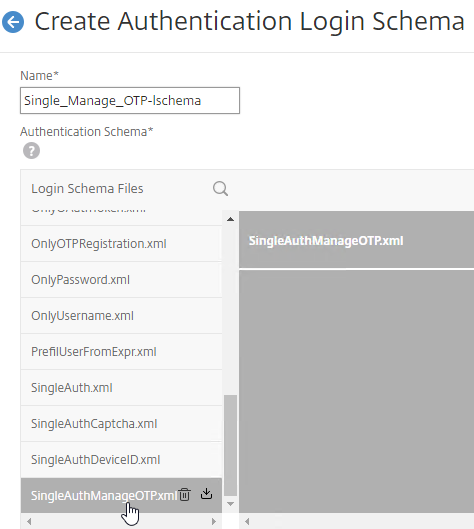
- On the top right, click Select.
- Click Create.
- Add another Login Schema profile.
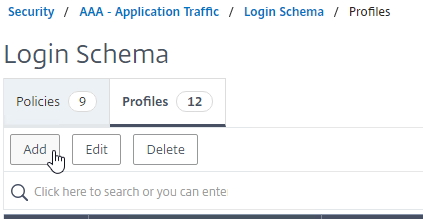
- This Login Schema is for two-factor authentication to NetScaler Gateway so name it accordingly.
- Click the edit icon. Follow the same procedure as above, but this time select /LoginSchema/DualAuth.xml.
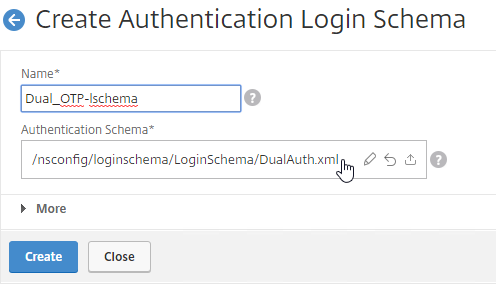
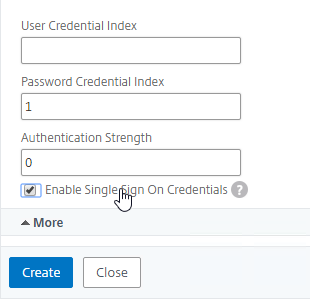
- Click More to reveal more options.
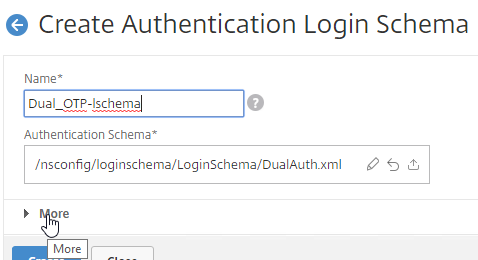
- Scroll down. In the Password Credential Index field, enter 1. This causes nFactor to save the user’s password into AAA Attribute #1, which we’ll use later in a Traffic Policy to Single Sign-on to StoreFront. If you don’t do this, then NetScaler Gateway will try to use the Passcode to authenticate to StoreFront, which obviously won’t work.
- Check the box next to Enable Single Sign On Credentials. Mark in the comments indicates that this checkbox is needed to Single Sign On to RDP Hosts.
- Click Create.
- On the right, switch to the Policies tab.
- Click Add to add a Login Schema policy.
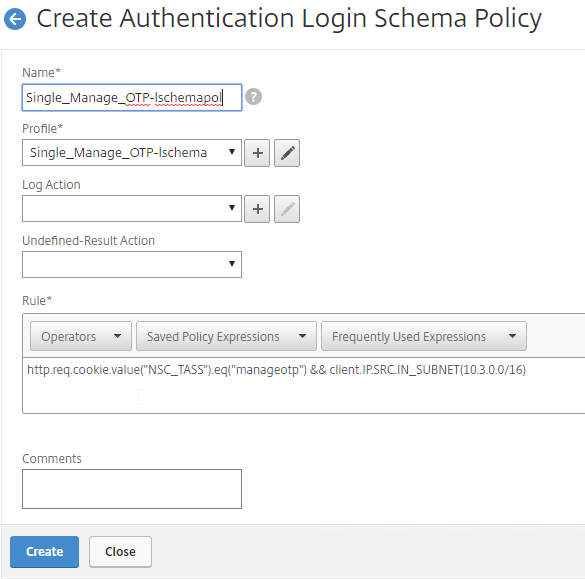
- In the Profile field, select the Single Factor Manage OTP Login Schema Profile.
- Name the Login Schema Policy for OTP management.
- In the Rule field, enter the following. This ensures that this single factor Login Schema is only used if the user enters /manageotp, and if the user is on the internal network. You don’t want manageotp to be accessible externally, because it’s only protected by single factor authentication, and it’s too easy to add multiple devices.
http.req.cookie.value("NSC_TASS").eq("manageotp") && client.IP.SRC.IN_SUBNET(10.2.0.0/16)- Stan Demburg at NetScaler Native OTP – Prevent Enrollment Of Additional Devices Externally at iRangers has a method of preventing external access to manageotp if the user already has a device enrolled.
- Morten Kallesoee at n-Factor – restrictions on native OTP management restricts manageotp if the user already has a device enrolled.
- Click Create.
- Create another Login Schema Policy.
- In the Profile field, select the dual factor Login Schema.
- Name the Login Schema to indicate dual factor authentication.
- In the Rule box, enter true.
- Click Create.
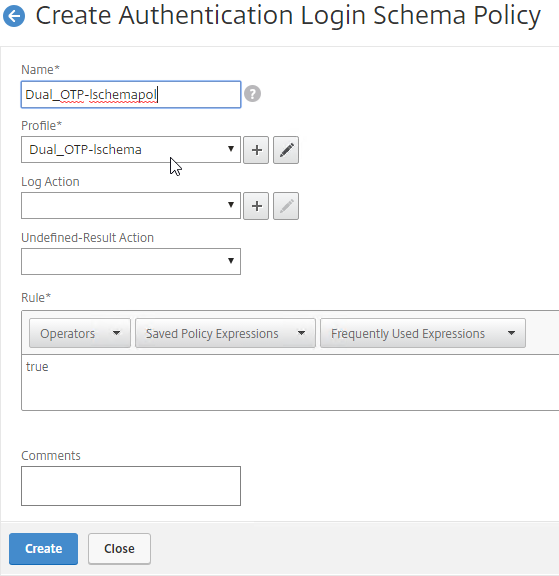
Authentication PolicyLabel
- Go to Security > AAA – Application Traffic > Policies > Authentication > Advanced Policies > PolicyLabel.
- On the right, click Add.
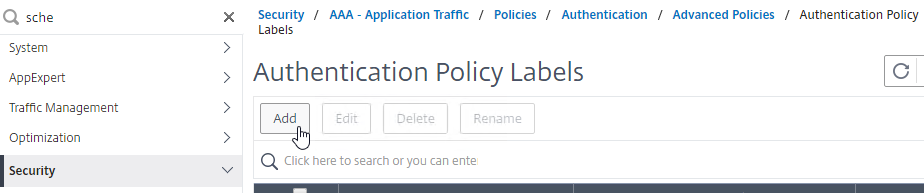
- This PolicyLabel is for OTP management, and OTP verification, so name it accordingly.
- In the Login Schema field, select LSCHEMA_INT, which means noschema.
- Click Continue.
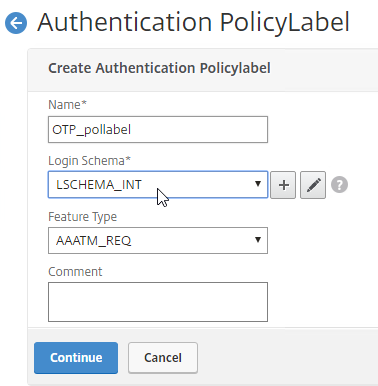
- In the Policy Binding section, Click to select.
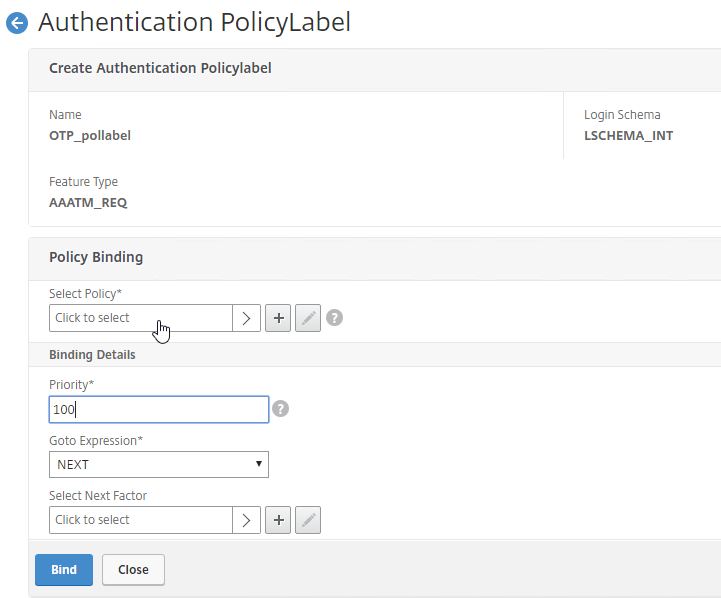
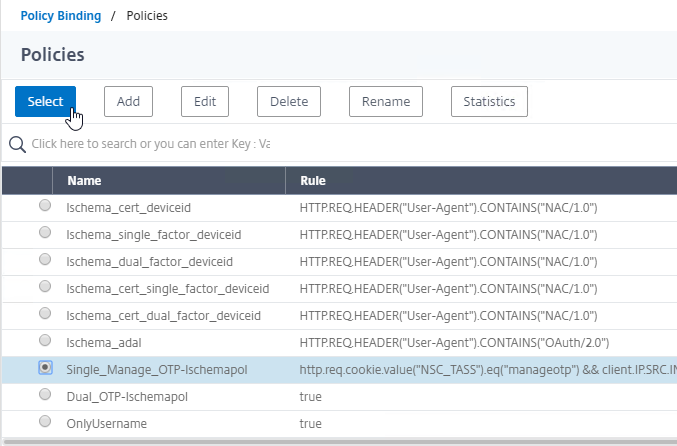
- Click the radio button button next to the Manage OTP LDAP Policy that has authentication disabled, and OTP Secret configured. This one should have a policy expression that limits it to manageotp only. Click Select.
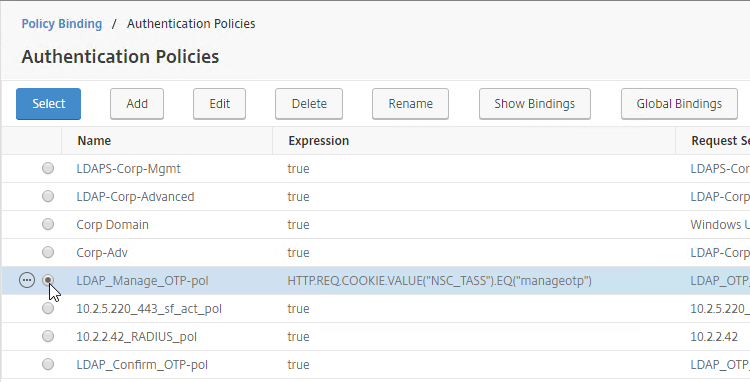
- Click Bind.
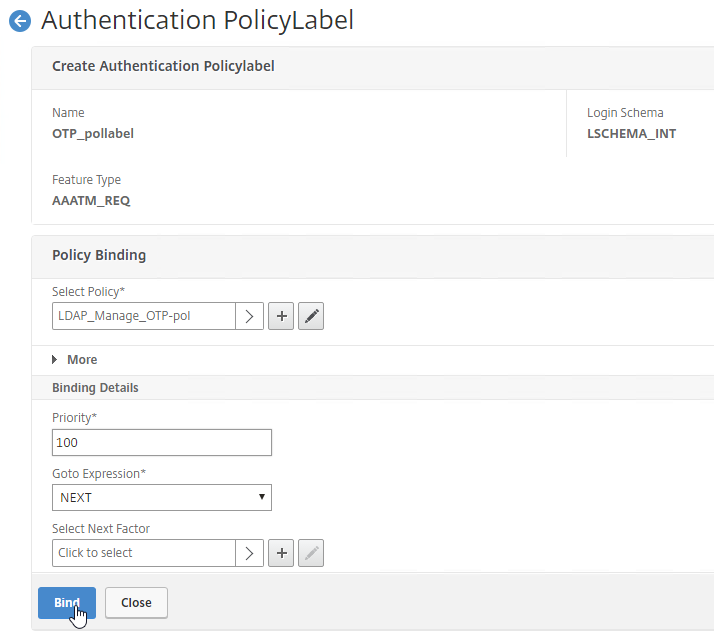
- Click Add Binding to add another one.
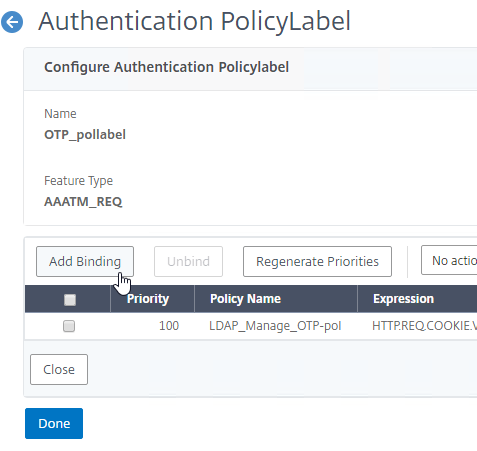
- Click to select.
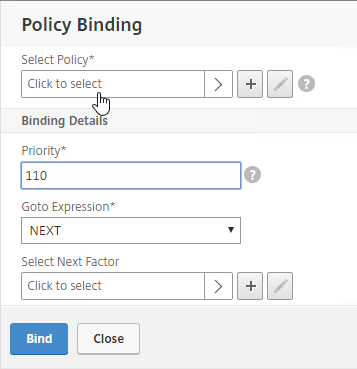
- Click the radio button next to the LDAP Policy that verifies OTP. Click Select.
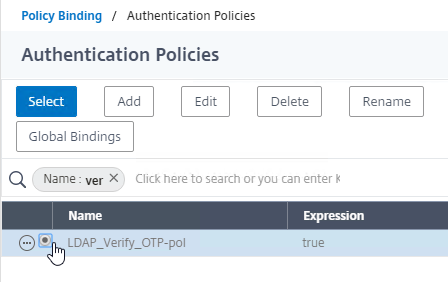
- Click Bind.
- Make sure the manageotp policy is higher in the list than the OTP Verification policy. To adjust priorities, right-click on the policies, and click Edit Binding. Click Done.
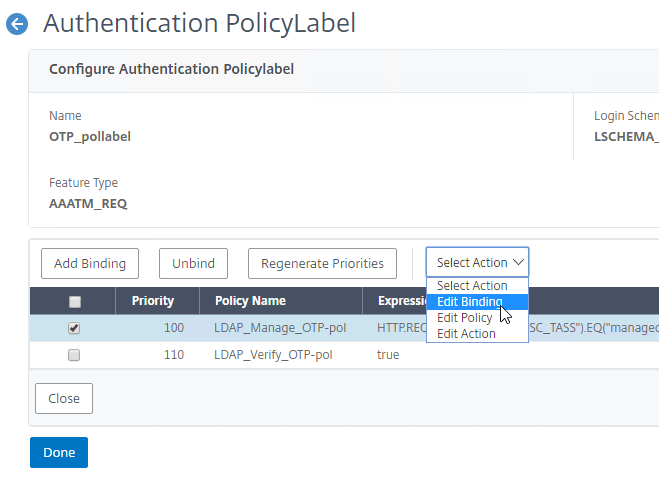
AAA vServer
- Go to Security > AAA – Application Traffic.
- If the AAA feature is not enabled, then right-click the AAA node, and click Enable Feature.
- If the AAA feature is not enabled, then right-click the AAA node, and click Enable Feature.
- Go to Security > AAA – Application Traffic > Virtual Servers.
- On the right, click Add.
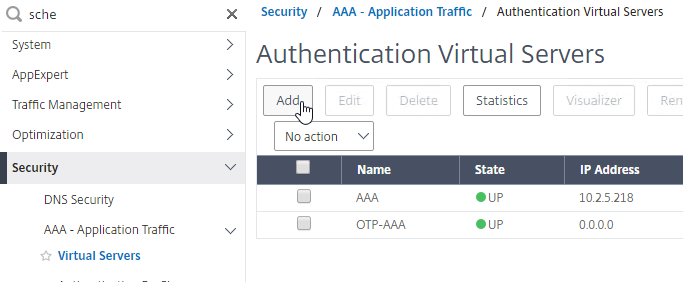
- This AAA vServer is for OTP so name it accordingly.
- Change the IP Address Type to Non Addressable.
- Click OK.
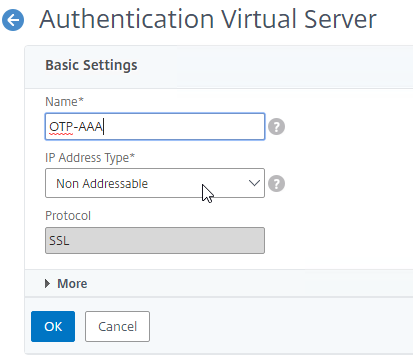
- Click where it says No Server Certificate.
- In the Server Certificate Binding section, click Click to select.
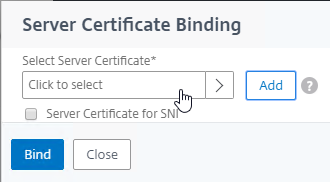
- Click the radio button next to a certificate, and click Select. You can use the same certificate as NetScaler Gateway.
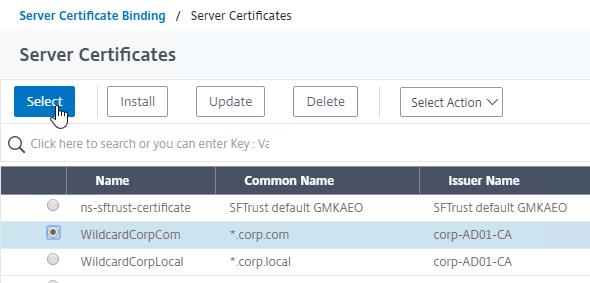
- Click Bind.
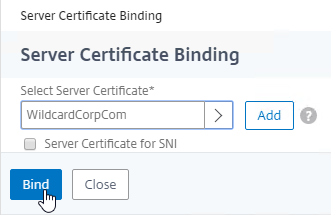
- In the Server Certificate Binding section, click Click to select.
- Click Continue to close the Certificate section.
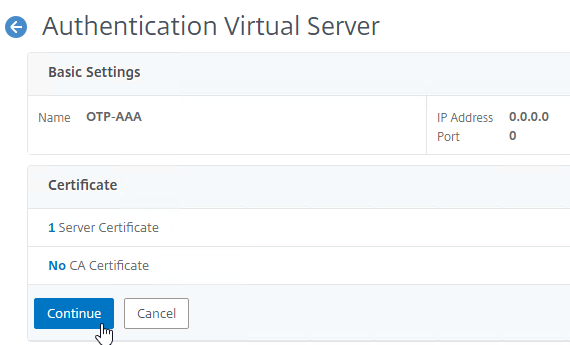
- In the Advanced Authentication Policies section, click where it says No Authentication Policy.
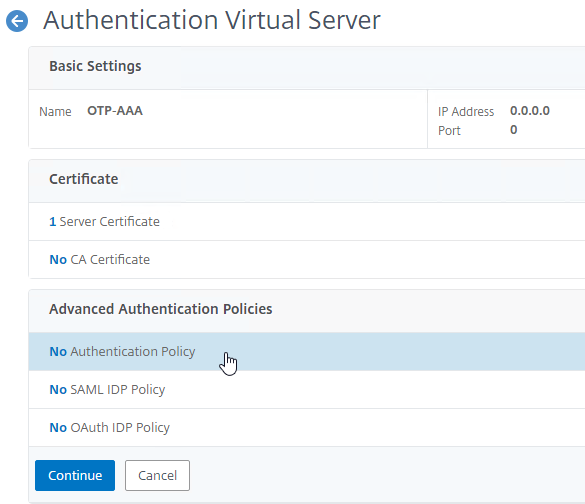
- Click where it says Click to select.
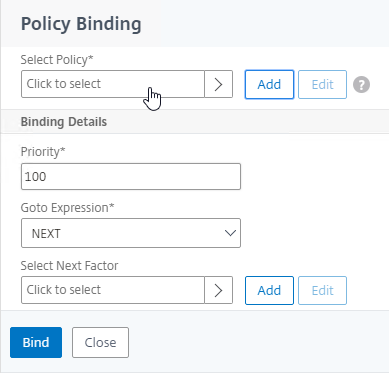
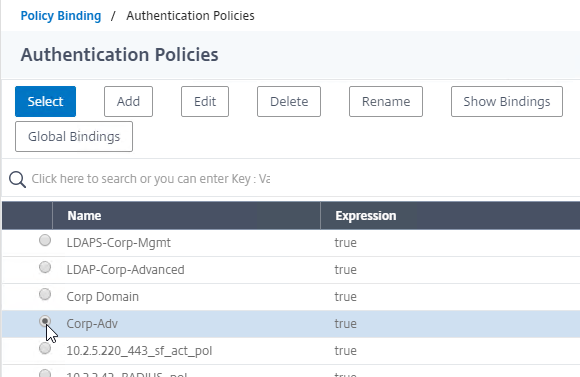
- Click the radio button next to the normal LDAP Policy that has authentication enabled. Then click the blue Select button.
- In the Select Next Factor field, click where it says Click to select.
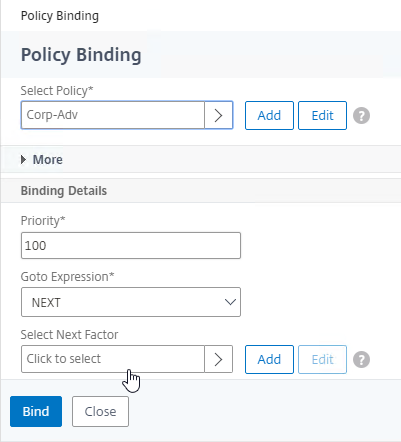
- Click the radio button next to the OTP PolicyLabel, and click Select.
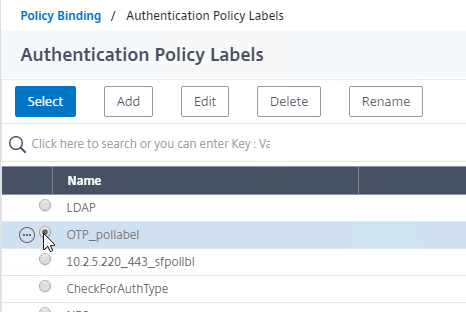
- Click Bind.
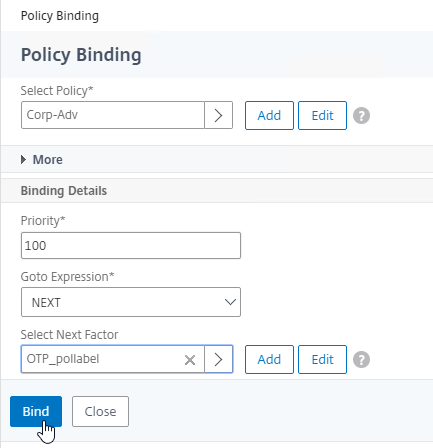
- Click where it says Click to select.
- In the Advanced Authentication Policies section, click Continue.
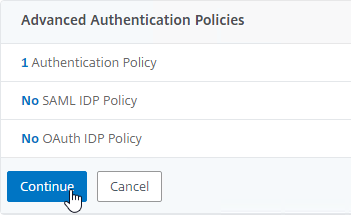
- On the right, in the Advanced Settings column, click Login Schemas.
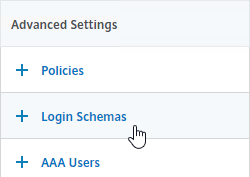
- On the left, scroll down, and click where it says No Login Schema.
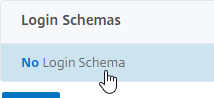
- Click where it says Click to select.
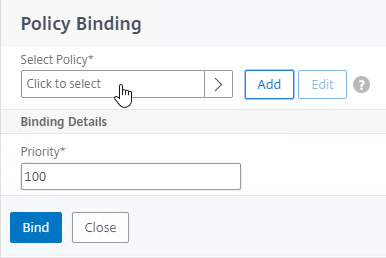
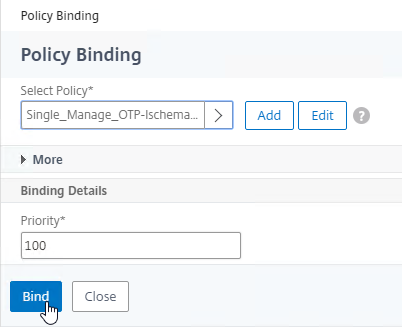
- Click the radio button next to the Manage OTP Login Schema, and click Select.
- Click Bind.
- Click where it says Click to select.
- Click where it says 1 Login Schema.
- Click Add Binding.
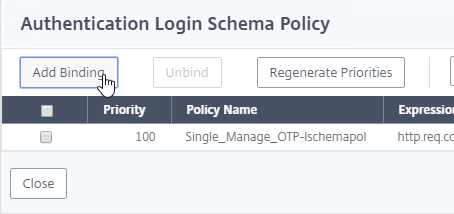
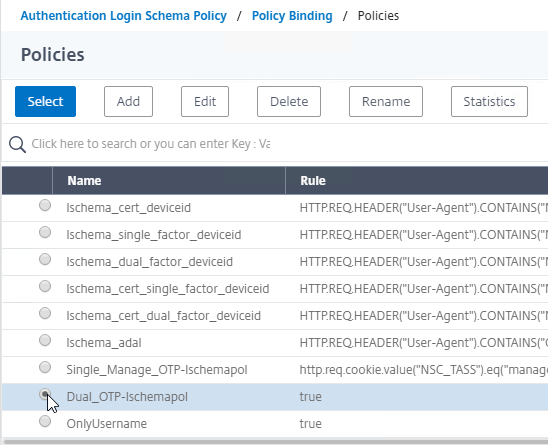
- Click where it says Click to select.
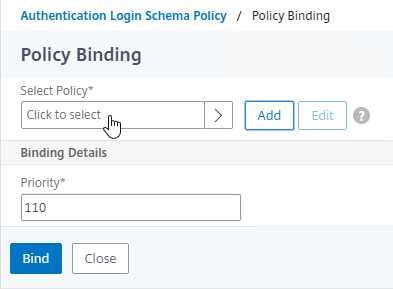
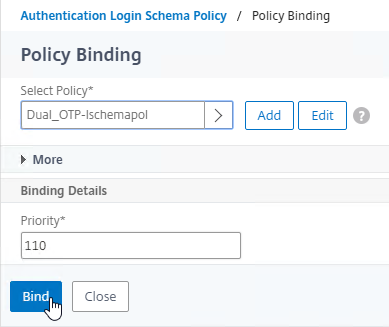
- Click the radio button next to the dual factor Login Schema, and click Select.
- Click Bind.
- Make sure the single factor Manage OTP Login Schema is higher in the list (lower priority number) than the dual factor Login Schema. Click Close.
- Click Add Binding.
- On the right, in the Advanced Settings column, click Portal Themes.
- On the left, scroll down, select RfWebUI as the Portal Theme, and click OK.
- Click Done.
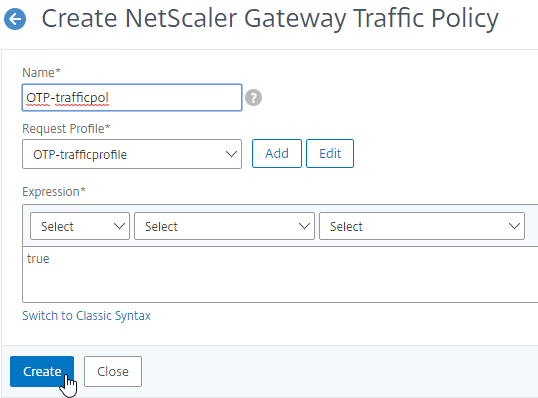
Traffic Policy for Single Sign-on
- On the left, go to NetScaler Gateway > Policies > Traffic.
- On the right, switch to the Traffic Profiles tab, and click Add.
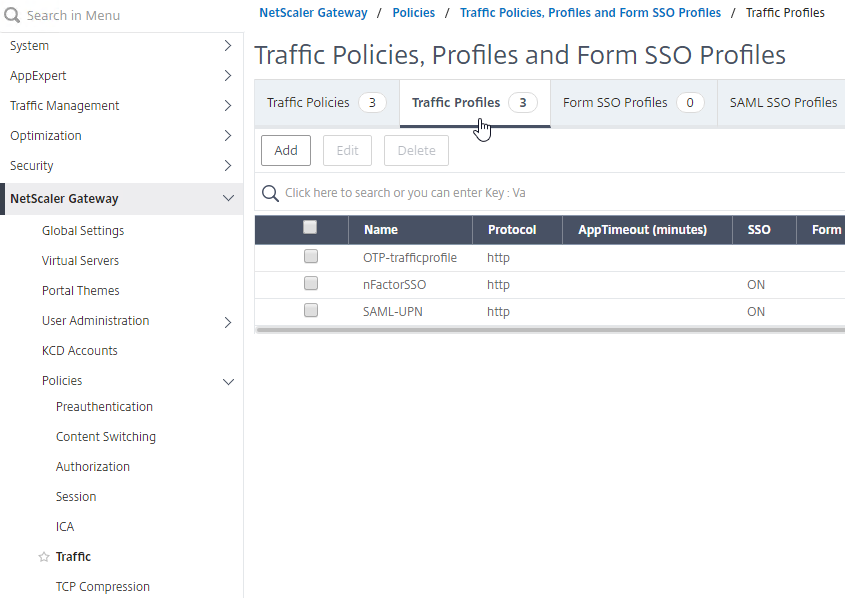
- This Traffic Profile is for OTP and/or nFactor. Name it accordingly.
- Scroll down.
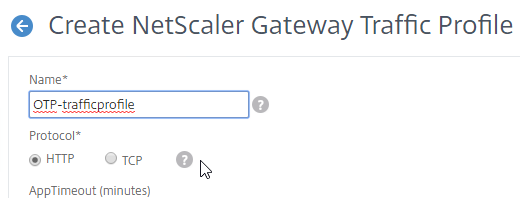
- In the SSO Password Expression box, enter the following. This is where we use the Login Schema Password Attribute specified earlier.
http.REQ.USER.ATTRIBUTE(1)
- Click Create.
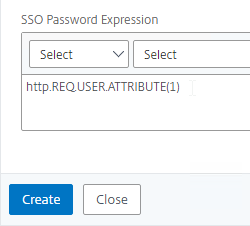
- On the right, switch to the Traffic Policies tab, and click Add.
- In the Request Profile field, select the Traffic Profile you just created.
- Name the Traffic Policy.
- In the Expression box, enter true (Default Syntax).
- If your NetScaler Gateway Virtual Server allows full VPN, change the expression to the following. Source = Julien Mooren at NetScaler – Native OTP is breaking SSL VPN.
http.req.method.eq(post)||http.req.method.eq(get) && false
- If your NetScaler Gateway Virtual Server allows full VPN, change the expression to the following. Source = Julien Mooren at NetScaler – Native OTP is breaking SSL VPN.
- Click Create.
NetScaler Gateway and Authentication Profile
- Go to NetScaler Gateway > Virtual Servers.
- Edit an existing Gateway vServer. If you don’t have one, see the other NetScaler Gateway topics on this site.
- Scroll down to the Policies section, and click the plus icon.
- Change the Choose Policy drop-down to Traffic, and click Continue.
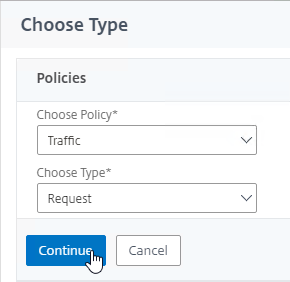
- Click to select.
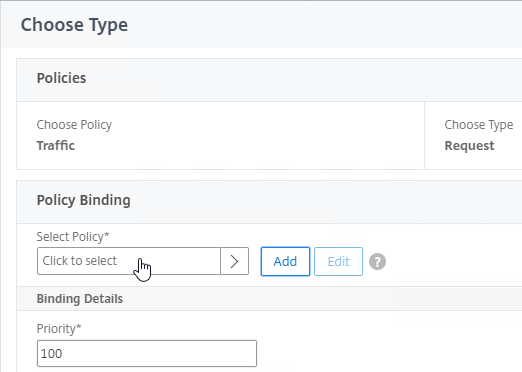
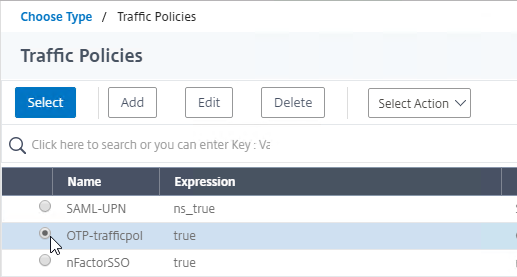
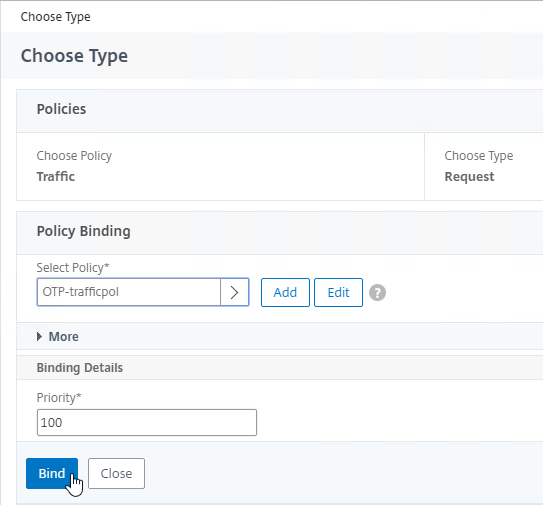
- Click the radio button next to the Traffic Policy you created earlier, and click Select.
- Click Bind.
- On the right, in the Advanced Settings column, click Authentication Profile.
- On the left, scroll down to the Authentication Profile section.
- Click Add to create one.
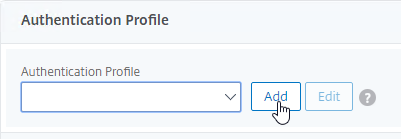
- Authentication Profile links the NetScaler Gateway vServer with the OTP AAA vServer, so name it accordingly.
- In the Authentication Virtual Server section, Click to select.
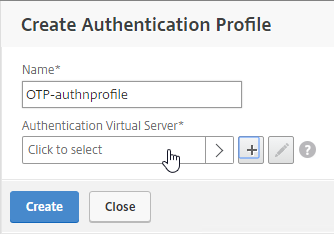
- Click the radio button next to the OTP AAA vServer, and click Select.
- Click Create.
- Scroll down again to the Authentication Profile section, and click OK.
- The Portal Theme bound to the Gateway vServer should be RfWebUI, or a derivative.
- Go to System > Profiles.
- On the right, switch to the SSL Profile tab.
- Edit the ns_default_ssl_profile_frontend profile.
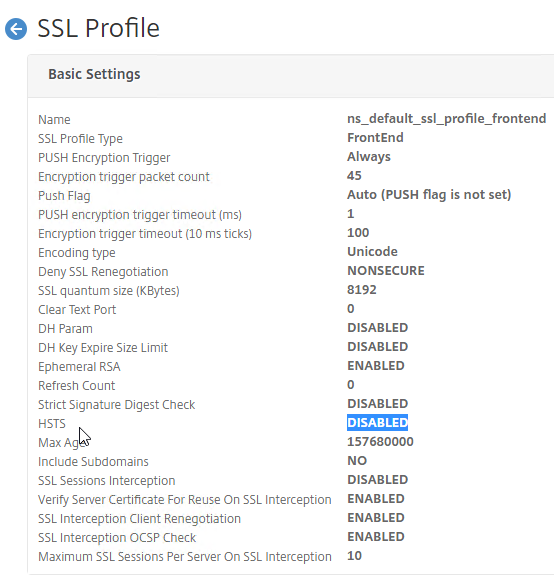
- Make sure HSTS is not enabled in the profile, or RfWebUI, and manageotp won’t work correctly. This is probably a bug. Note: the Rewrite method of enabling HSTS should work.
Update Content Switching Expression for Unified Gateway
If your NetScaler Gateway Virtual Server is behind a Unified Gateway (Content Switching Virtual Server), then you must update the Content Switching Expression to include the manageotp paths.
- In the NetScaler GUI, navigate to Configuration> Traffic Management > Content Switching > Policies.
- On the right, select the Unified Gateway Content Switching Policy, and then click Edit.
- Append the following expression under the Expression area, and then click OK.
|| HTTP.REQ.URL.CONTAINS("/manageotp")
Manageotp
- Point your browser to https://mygateway.corp.com/manageotp or similar. Simply add /manageotp to the end of your Gateway URL.
- Notice it’s only single-factor authentication. Login using normal LDAP credentials.
- Click Add Device.
- Enter a device name, and click Go.
- Launch the Google Authenticator application on your phone. Click the plus icon in Google Authenticator, and scan the QRCode that is shown on the screen.
- Christian in the comments indicated that Microsoft Authenticator also works. Click on plus sign -> other (Google,…).
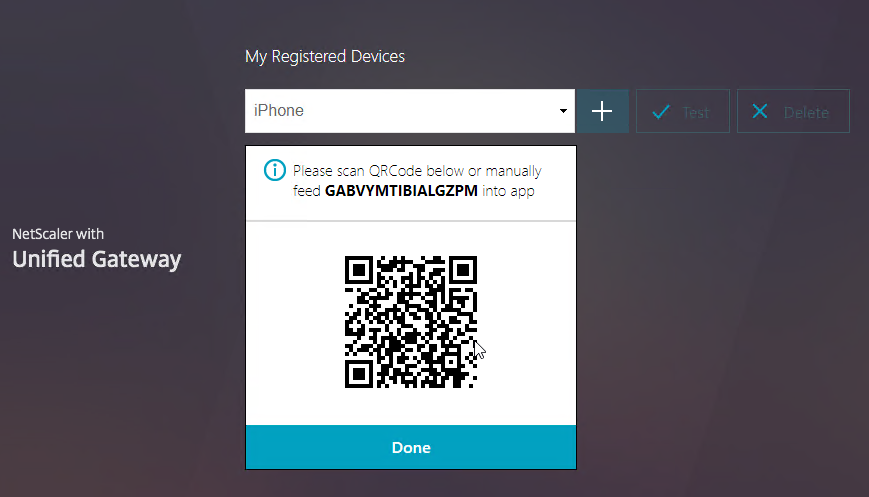
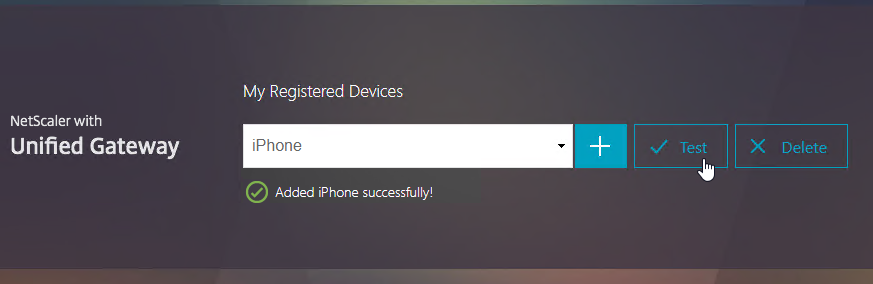
- Click Test.
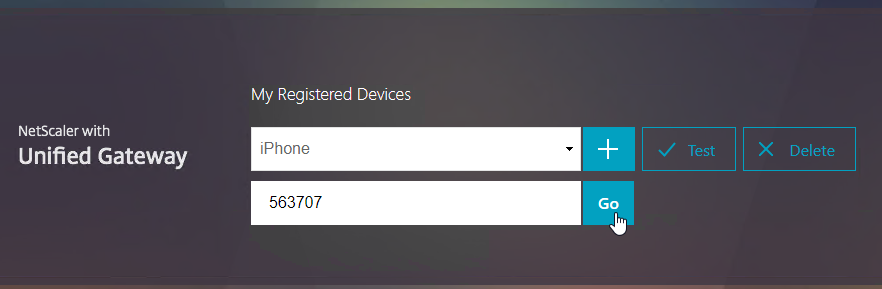
- Enter the passcode shown in your Authenticator, and click Go.
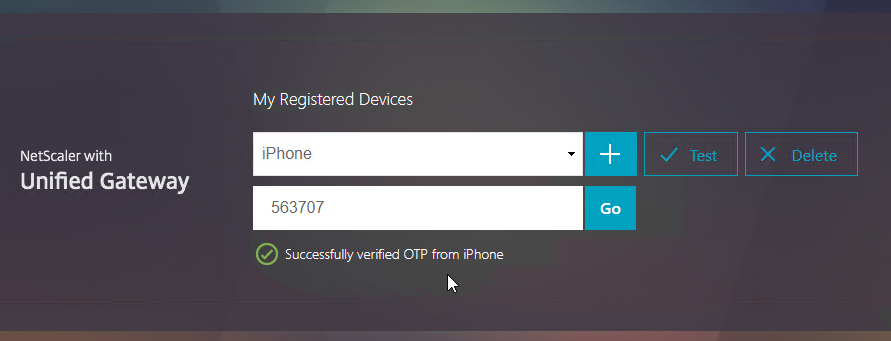
- If you logoff of manageotp, and access your Gateway URL normally, you’ll be prompted for two-factor authentication. Use the passcodes shown in your Google Authenticator application.
- It should Single Sign-on into StoreFront.

CLI Commands
Here’s a complete CLI configuration.
add ssl certKey WildcardCorpCom -cert WildcardCorpCom.pfx -key WildcardCorpCom.pfx -inform PFX -passcrypt "abc" add authentication ldapAction LDAP-Corp -serverIP 10.2.2.11 -serverPort 636 -ldapBase "dc=corp,dc=local" -ldapBindDn ctxsvc@corp.local -ldapBindDnPassword abc -encrypted -encryptmethod ENCMTHD_3 -ldapLoginName sAMAccountName -groupAttrName memberOf -subAttributeName cn -secType SSL -passwdChange ENABLED -Attribute2 userParameters add authentication ldapAction LDAP_OTP_set_no_auth -serverIP 10.2.2.11 -serverPort 636 -ldapBase "dc=corp,dc=local" -ldapBindDn admin@corp.local -ldapBindDnPassword abc -encrypted -encryptmethod ENCMTHD_3 -ldapLoginName sAMAccountName -groupAttrName memberOf -subAttributeName cn -secType SSL -authentication DISABLED -OTPSecret UserParameters add authentication ldapAction LDAP_OTP_verify_no_auth -serverIP 10.2.2.11 -serverPort 636 -ldapBase "dc=corp,dc=local" -ldapBindDn admin@corp.local -ldapBindDnPassword abc -encrypted -encryptmethod ENCMTHD_3 -ldapLoginName sAMAccountName -searchFilter "userParameters>=#@" -groupAttrName memberOf -subAttributeName cn -secType SSL -authentication DISABLED -OTPSecret UserParameters add authentication Policy Corp-Adv -rule true -action LDAP-Corp add authentication Policy LDAP_Manage_OTP-pol -rule "HTTP.REQ.COOKIE.VALUE(\"NSC_TASS\").EQ(\"manageotp\")" -action LDAP_OTP_set_no_auth add authentication Policy LDAP_Confirm_OTP-pol -rule true -action LDAP_OTP_verify_no_auth add authentication loginSchema Dual_OTP-lschema -authenticationSchema "/nsconfig/loginschema/LoginSchema/DualAuth.xml" -passwordCredentialIndex 1 add authentication loginSchema Single_Manage_OTP-lschema -authenticationSchema "/nsconfig/loginschema/LoginSchema/SingleAuthManageOTP.xml" add authentication loginSchemaPolicy Single_Manage_OTP-lschemapol -rule "http.req.cookie.value(\"NSC_TASS\").eq(\"manageotp\") && client.IP.SRC.IN_SUBNET(10.3.0.0/16)" -action Single_Manage_OTP-lschema add authentication loginSchemaPolicy Dual_OTP-lschemapol -rule true -action Dual_OTP-lschema add authentication policylabel OTP_pollabel -loginSchema LSCHEMA_INT bind authentication policylabel OTP_pollabel -policyName LDAP_Manage_OTP-pol -priority 100 -gotoPriorityExpression NEXT bind authentication policylabel OTP_pollabel -policyName LDAP_Confirm_OTP-pol -priority 110 -gotoPriorityExpression NEXT add authentication vserver OTP-AAA SSL 0.0.0.0 bind ssl vserver OTP-AAA -certkeyName WildcardCorpCom bind authentication vserver OTP-AAA -portaltheme RfWebUI bind authentication vserver OTP-AAA -policy Single_Manage_OTP-lschemapol -priority 100 -gotoPriorityExpression END bind authentication vserver OTP-AAA -policy Dual_OTP-lschemapol -priority 110 -gotoPriorityExpression END bind authentication vserver OTP-AAA -policy Corp-Adv -priority 100 -nextFactor OTP_pollabel -gotoPriorityExpression NEXT add vpn trafficAction OTP-trafficprofile http -passwdExpression "http.REQ.USER.ATTRIBUTE(1)" add vpn trafficPolicy OTP-trafficpol true OTP-trafficprofile add authentication authnProfile OTP-authnprofile -authnVsName OTP-AAA add vpn vserver Gateway.corp.com SSL 10.2.5.220 443 -downStateFlush DISABLED -Listenpolicy NONE -authnProfile OTP-authnprofile set ssl vserver Gateway.corp.com -sslProfile ns_default_ssl_profile_frontend add vpn sessionAction "Receiver For Web" -transparentInterception OFF -defaultAuthorizationAction ALLOW -SSO ON -icaProxy ON -wihome "https://storefront2.corp.com/Citrix/StoreWeb" -ntDomain corp.local -clientlessVpnMode OFF -storefronturl "https://storefront2.corp.com" add vpn sessionPolicy "Receiver For Web" "HTTP.REQ.HEADER(\"User-Agent\").CONTAINS(\"CitrixReceiver\").NOT" "Receiver For Web" bind vpn vserver Gateway.corp.com -portaltheme RfWebUI bind vpn vserver Gateway.corp.com -policy "Receiver For Web" -priority 100 -gotoPriorityExpression NEXT -type REQUEST bind vpn vserver Gateway.corp.com -policy OTP-trafficpol -priority 100 -gotoPriorityExpression END -type REQUEST bind ssl vserver Gateway.corp.com -certkeyName WildcardCorpCom
https://www.youtube.com/watch?v=IL_ocv6w8nM is private?
Thanks for pointing that out. I removed the link.
We have Citrix native OTP as a MFA configure for our customer with all infra i.e. ADC, VDI, StoreFront and all component in domain1.
Customer is establishing transitive trust relationship with domain2.
Now, does user from domain2 will be able to authenticate to gateway using Native OTP which is configured for domain1?(by assuming the service account will have all the required access in domain2 as well to read and write userparameter inside AD.)
Hi Carl,
Thank you for another nice guide.
I configured as above, but at the first try to register a device using /manageotp page, after correct authentication by LDAP, the page shows:
“Session absent to manage otp for user, probably misconfiguration. Please contact your adminsitrator.” (with that typo, in NS 13.0 92.12nc).
At ns.log appears:
…default SSLVPN Message 6150 0 : “OTP registration/management is invoked when there is no session or valid otp action”
The aaad.debug do not shows errors.
What can be the error?
Tks,
Denis
Did you do something in the first ldap action to retreive the Active Directory attribute and later check it? that maybe mess things up.
userParameters
For Example:
First factor LDAP Server (with authentication = ON) –> Attribute Fields –> Attribute 1 –> the Active Directory attribute (userParameters).
Than later during the second factor –> Create a policy with NO_AUTH and check if that userParameter excists with the following Expression:
AAA.USER.ATTRIBUTE(1).LENGTH.GE(4)
hi Carl,
Thanks for the blog i have configured the OTP setup on our environment. but when we try to access the manageotp page to register the device it asks user name and password after put the user name password get an error ” try after some time or contact your helpdesk”
Please help
What do you see in “cat /tmp/aaad.debug”? Anything interesting in /var/log/ns.log?
Thanks Carl
Please, in a Netscaler native OTP scenario, in the registration part (after the user has entered their Active Directory credentials), is it possible for the user to register or receive the QR code in their email? or some other method by initial mail to register?
Thanks you
Hello,
Is it possible that the URL https://site/manageotp is not accessible to all users who have MFA enabled? We need you to only access http://site/manageotp the first time when you set up the device.
Without this block, any user can delete their MFA and link another one, and we want it to only be done from IT.
There might be a way to hack it. Somebody might have already posted instructions on how to do it. But I usually don’t recommend Native OTP because of the difficulty in locking down the manageotp site.
Helo guys,
What we did on a client:
We created a group in AD with users who could access /manageotp. And inside the AAA VIP, we created a policy that validated if the user was part of this group, he could access /manageotp. If you weren’t part of the group, you would block access to the page. That worked fine.
You have to create this policy inside the OTP-AAA along with the plicy of Corp-Adv and OTP_pollabel (following the Blog document).
try to do this in homologation, in our client we adjusted and it is working.
can you please give more details on this solution?
Hello Karl
Thanks for a great article as always, everything seems to have worked.
Now I try it the other way around, so first factor OTP then LDAP , so that the LDAP factor can not be blocked by repeated failed attempts.
so I did the following:
1.authpol: LDAP no auth
2.polllabel: OTP verify
3, polllabel: LDAP auth
but unfortunately it did not work, I get the error message “Failure_reason “External authentication server denied access” on level polllabel: LDAP auth
Any idea what the reason is ? Looking forward for your comments. Thanks.
Dear Carl, thanks for the great walkthrough – always a fan of your work. One question. I´ve built up above setup and everything is working well with Citrix SSO App… but the customer states that registering other devices or authenticator apps do not work. It is not writing the userParameters property to the ad-object… I assume I have to add another OTP-Registration Profile … but how… ? Any help would be highly appreciated… Bets regards!
Martin, saw this same issue in testing and found that once you enable the Push Service the /manageotp page only allows a single device. Disabling the Push Service allows the user to add multiple devices up to the set limits. Makes sense since there isn’t a builtin mechanism to define which device should be used for push while the others can be used for OTP. If multiple devices existed, which one would it push too? Not sure there is a way around this.
Hi Carl,
Hi Carl, Thanks a lot for this article.
I have ADC in Primary Site using native OTP configuration. For DR ADC how can we sync same OTP configuration. my requirement is for both Primary and DR site user should have same OTP. Is there any posiblity to achive this?
Hi Carl, thanks for the great article but have a problem using SSO to RDP back-end with native OTP. Have created a gateway with an authentication profile doing LDAPS first and then native OTP. Traffic policy and loginschema attribute(1) are set. When launching the RDP bookmark it prefills the username but does not SSO and have to type in the LDAP password to connect. Any advice?
Hi Carl, Can we use any alternative for SSO Traffic policy, we are using 12.1 just as AAA authentication virtual server in citrix cloud
we have two domain and want to have separate MFA solutions.
its resolved now, we added gateway server
Failed to add device it says. The Native OTP was working earlier, no change was implemented recently. What could be the problem? Any tips for troubleshooting?Cheers
Hi Mark,
did you solve this problem? I just implemented native OTP as a PoC and run into the same problem.
Hello Christian,
Did you manage to solve the problem? I have the same error when trying to add the device
Hi Mark, I have the same problem. Before, it worked correctly. Did you find the problem?
Hi everyone, just a security concern. We have configured OTP and everything works like a charm. However, if an LDAP account is compromised, someone can easily connect to the OTP page (single authentication), change device and then, access all applications. Is there a way to secure this ? Is it wise to let OTP accessible from Internet ? Thank you for your suggestion.
the way i have got around this is created a security group members have to be in to get to the otp page externally. we are then only letting people have timed access to register there devices then access is taken away. if they change devices policies will be in place to contact for access to be given again.
Does anyone know if it is possible (some Responder maybe), inhibit the option to delete the device for users? I have already limited the number of devices for users (to just 1), but I would like to not let ordinary users delete and add another device instead.
This function should only be enabled for the NetScaler administrator.
It’s possible ?
Hi,
I have citrix gateway 12 vpx
For some reason he writes me this message
The server met an error. Please try again or contact your administrator
Once I change the setting in the Clientless Access session profile from OFF to ON I can connect
What could be the reason?
I have google auth working and I can login.
My problem is I can ping everything that I want on my internal network, but it seems like UPD/TCP traffic is not allowed.
Also maybe this is because my DNS and Default gateway is wrong. Is there any way to pull from a DHCP server? I can’t figure out a place to configure a default gateway on the netscaler.
/manageotp page is getting redirected to login page
Help!
Hi
I tray no open the URL of my citrix getway
https://sasinsgw.lab.local\manageotp
to register for the first time but i get the passcode line instead the first register web
I wants to deploy this where 4 domains including child domains configured on ADC and 4 seperate LDAP configured..
My concern- do I need to add 2 ldap actions and other policies per LDAP server, which means 4×2=8 ldap actions/policies to enable this Native otp feature?
That sounds right.
Thanks for the response Carl. Any specific requirement to configure Native OTP on Multi-Domain environment?
awesome ! Thank you soo much for this all of works !
Hello Carl, I am working in an environment where no machine has internet access neither LDAP server nor the Citrix ADC when I am trying to add a device in manage OTP page, I am getting error saying “failed to add ”
Can you help me fixing this please
Environment background:
-ADC Version 12.1 55.18nc
-ADC and LDAP is in same network
-ADC LDAP does not have internet access
-Client PC and mobile has internet access
Check /var/log/ns.log for errors. You can do a “tail -f /var/log/ns.log” while trying to register a device.
Just to add more info, it happen the same to my env. because i didn’t use a user with proper permission for LDAP binding, user must have write acces to userParameters atribute
Hi Carl,
Thank you so much on this.
I follow exactly what you did here but upon logging initially to enroll my device I cannot able to login and the error says
“KB questions and answers not registered”.
Hope you can help me on this one. 🙂 thanks!
Hello people,
I was thinking …………. is it possible to enable OTP only for external accesses? (internal users would not need to use OTP).
What should I do in this case?
Hello
I have configured Citrix Native OTP the following all works
can register a device
can get pass the logon with your username and OTP, but when it goes to redirect you to the store front I get cannot complete request. I have gone through everything.
if I take the otp setting off and use single factor works fine and can get to the store front.
I have noticed on the store front server when the issue happening getting this error.
CitrixAGBasic single sign-on failed because the credentials failed verification with reason: Failed. and it shows the user testing password as the username. very odd behaviour.
CitrixAGBasic single sign-on failed because the credentials failed verification with reason: Failed.
The credentials supplied were;
user: Passwordxxxxxxxxxx
domain: mydomain.local
event ID 7
ADC Formware version NS13.061.48nc
any pointers?
Thanks
I’m guessing there’s something wrong with the Traffic Policy or the Login Schema and puts the password in the AAA Attribute number.
in the traffic profile sso urser expression is set to AAA.USER.ATTRIBUTE(1) then in the traffic policy it links to the profile and expression is true.
thank you I have now sorted this 🙂
Hi Darren,
Make sure that you configured the traffic policy that is mentioned in the article, also SSO should be turned ON in Traffic Profile.
Thanks,
Harsh Kumar
Thankyou Carl, your guide was invaluable in aiding our OTP setup
Hello Everyone!
How to configure on LDAP server that is balancing (I have a VIP on NetScaler doing Balance to 2 LDAP Server) ?
I did the configuration based on IP of VIP (with two LDAP Server), but when enable the OTP on my Gateway VIP, the portal stoped (cannot complete your request).
Did you configure the Traffic Policy?
What error are you seeing in StoreFront Server > Event Viewer > Applications and Services > Citrix Delivery Services?
In fact, it gives the error before the Citrix Gateway Portal login appears.
I did a test removing the customized portal and the Login page appeared, but without OTP. And I couldn’t log in (User and password incorrect). Without OTP it works.
RfWebUI theme?
Yes, and Portal Custom too.
Traffic Policy configured
I redid the configuration on top of the RfWebUI theme, I customized it on VIP and OTP.AAA (TrafficPolicy) and it worked.
Thank you! Your blog and explanations are great, congratulations!
/manageotp page is getting redirected to login page, can you please help me in this
we are getting the same. anyone solve this?
I’m also getting the same issue. Has the latest version of ADC broken this?
Make sure you’re using https://site/manageotp and not just http