Navigation
- Overview
- Prerequisites
- Create Session Profile
- Create Session Policy
- Bind Session Policy
- NetScaler Gateway Plug-in Installation
- Authorization Policies
- Intranet Applications
- DNS Suffix
- Bookmarks
- VPN Client IP Pools (Intranet IPs)
- StoreFront in Gateway Portal
- Quarantine Group 💡
💡 = Recently Updated
Overview
NetScaler Gateway supports five different connection methods:
- ICA Proxy to XenApp/XenDesktop – client is built into Citrix Receiver
- SSL VPN – requires NetScaler Gateway plug-in
- Clientless – browser only, no VPN client, uses rewrite
- Secure Browse – from MDX-wrapped mobile applications (XenMobile), uses rewrite
- RDP Proxy – only RDP client is needed
If Endpoint Analysis is configured, then an Endpoint Analysis plug-in is downloaded to the Windows or Mac client.
Users use SSL to connect to NetScaler Gateway Virtual Servers.
- NetScaler Gateway prompts the user for authentication.
- Once the user is authenticated, NetScaler Gateway uses Session Policies to determine what happens next.
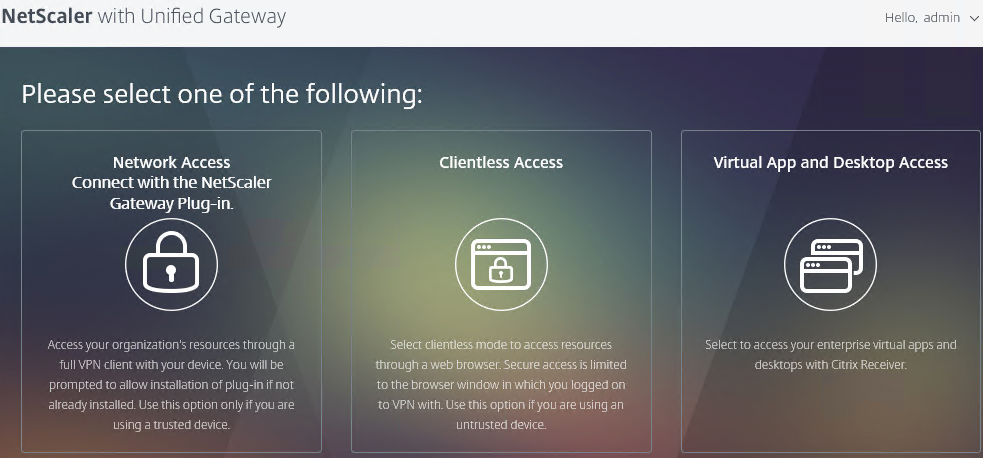
You can configure NetScaler Gateway Session Policies to only use one of the connection methods. Or NetScaler Gateway can be configured to let users choose between ICA Proxy, Clientless, and SSL VPN connection methods. Here’s a sample Client Choices screen using the X1 theme:
Enable SSL VPN in a Session Policy as detailed later. Then configure additional NetScaler Gateway objects including the following:
- DNS Servers and Suffix – enable DNS resolution across the VPN tunnel
- NetScaler Gateway Universal Licenses – all VPN users must be licensed.
- Intranet IP addresses – give IP addresses to VPN clients. If no client IP, then VPN clients use NetScaler SNIP to communicate with internal resources. Requires routing changes on internal network.
- Intranet Applications – if split tunnel is enabled, configure this object to dictate what traffic goes across the tunnel and which traffic stays local.
- Authorization Policies – if default authorization is DENY, use Authorization Policies to dictate what resources can be accessed across the NetScaler Gateway connection. These Authorization Policies apply to all NetScaler Gateway connections, not just VPN.
- Bookmarks – displayed on the built-in NetScaler Gateway portal page. Users click bookmarks to access resources across the VPN tunnel or clientless access (rewrite).
- Endpoint Analysis Scans – block endpoints that fail security requirements. Configured in Session Policies or Preauthentication Policies.
- Traffic Policies – Single Sign-on to internal web applications
- AAA Groups – bind Session Policies, Authorization Policies, Intranet Applications, Intranet IPs, Bookmarks, and Traffic Policies to one or more Active Directory groups. Allows different Active Directory groups to have different NetScaler Gateway configurations.
Prerequisites
Except for ICA Proxy, all NetScaler Gateway connection methods require a NetScaler Gateway Universal License for each concurrent session. Go to System > Licenses and make sure NetScaler Gateway User licenses are installed.
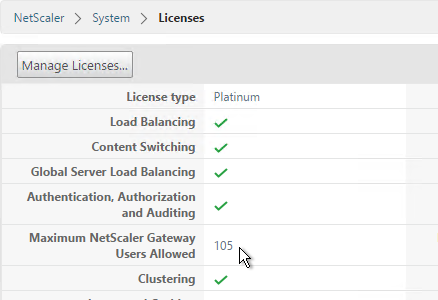
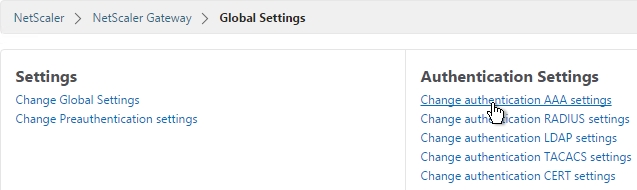
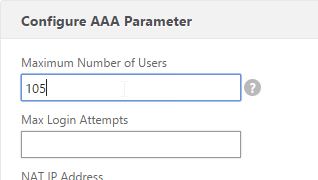
Also make sure the maximum AAA users equals the number of licenses. Go to NetScaler Gateway > Global Settings > Change authentication AAA settings.
DNS usually needs to function across the VPN tunnel. Go to Traffic Management > DNS > Name Servers to add DNS servers.
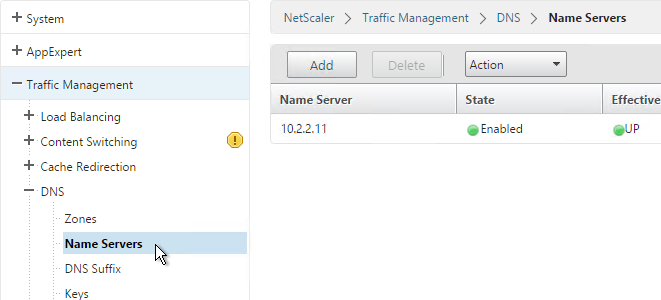
Create Session Profile
You can create multiple Session Policy/Profiles, each with different settings. Then you can bind these Session Policies to different AAA groups or different NetScaler Gateway Virtual Servers. You can also bind Endpoint Analysis expressions to a Session Policy so that the Session Policy only applies to machines that pass the Endpoint Analysis scan.
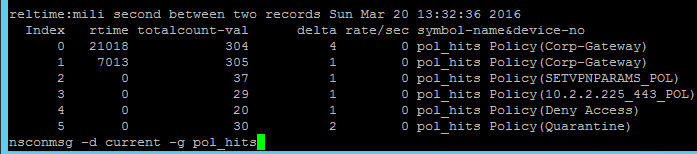
If multiple Session Policies apply to a particular connection, then the settings in the policies are merged. For conflicting settings, the Session Policy with the highest priority (lowest priority number) wins. Session Policies bound to AAA groups only override Session Policies bound to NetScaler Gateway Virtual Servers if the AAA group bind point has a lower priority number. In other words, priority numbers are evaluated globally no matter where the Session Policy is bound. You can run the command nsconmsg –d current –g pol_hits to see which Session Policies are applying to a particular connection.
Do the following to enable SSL VPN. First create the Session Profile. Then create a Session Policy.
- On the left, expand NetScaler Gateway, expand Policies, and click Session.
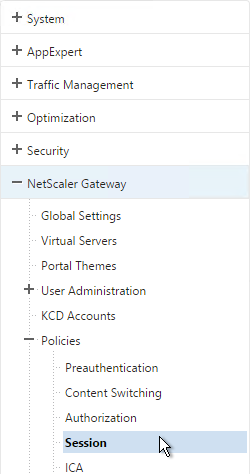
- On the right, switch to the Session Profiles tab and click Add.
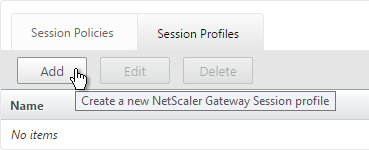
- Name the profile VPN or similar.
- In Session Profiles, every line has an Override Global checkbox to the right of it. If you check this box next to a particular field, then the field in this session profile will override settings configured globally or in a lower priority session policy.
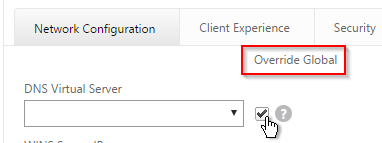
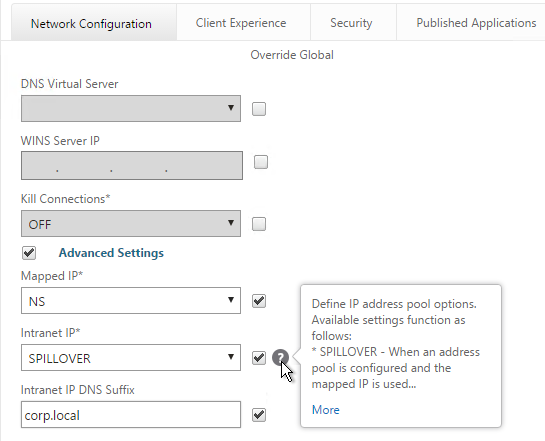
- Switch to the Network Configuration tab and check the box next to Advanced Settings.
- You will find a setting that lets you select a DNS Virtual Server. Or if you don’t select anything then the tunnel will use the DNS servers configured under Traffic Management > DNS > Name Servers.
- Configure the behavior when there are more VPN clients than available IPs in the address pool. This only applies if you are configuring Intranet IPs.
- There are also a couple timeouts lower on the page.
- Switch to the Client Experience tab. This tab contains most of the NetScaler Gateway VPN settings.
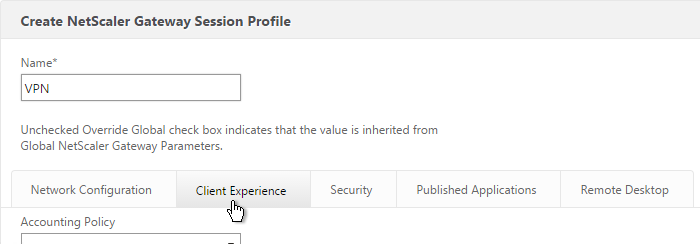
- Override Plug-in Type and set it to Windows/Mac OS X.
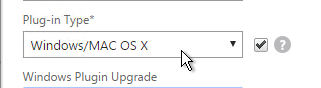
- Whenever NetScaler firmware is upgraded, all users will be prompted to upgrade their VPN clients. You can use the Upgrade drop-downs to disable the automatic upgrade.
- By default, if Receiver and NetScaler Gateway Plug-in are installed on the same machine, then the icons are merged. To see the NetScaler Gateway Plug-in Settings, you right-click Receiver, open Advanced Preferences and then click NetScaler Gateway Settings.
- You can configure the Session Policy/Profile to prevent NetScaler Gateway Plug-in from merging with Receiver. On the Client Experience tab, scroll down and check the box next to Advanced Settings.
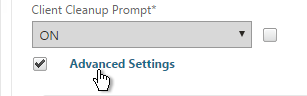
- Check the box next to Show VPN Plugin-in icon with Receiver. This causes the two icons to be displayed separately thus making it easier to access the NetScaler Gateway Plug-in settings.
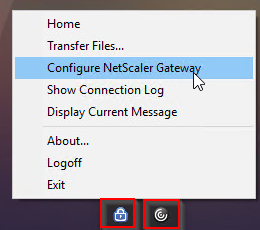
- On the Client Experience tab, override Split Tunnel and make your choice. Setting it to Off will force all traffic to use the tunnel. Setting it to On will require you to create Intranet Applications so the NetScaler Gateway Plug-in will know which traffic goes through the tunnel and which traffic goes directly out the client NIC (e.g. to the Internet).
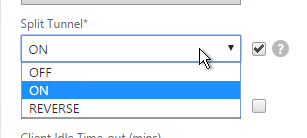
- On the Client Experience tab, there are timers that can be configured. Global Settings contains default timers so you might want to override the defaults and increase the timeouts. See Configuring Time-Out Settings at Citrix Docs for details.
- Client Idle Time-out is a NetScaler Gateway Plug-in timer that disconnects the session if there is no user activity (mouse, keyboard) on the client machine.
- Session Time-out disconnects the session if there is no network activity for this duration.
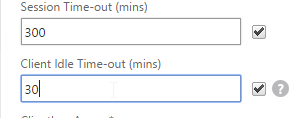
- In addition to these two timers on the Client Experience tab, on the Network Configuration tab, under Advanced Settings, there’s a Forced Timeout setting.
- By default, once the VPN tunnel is established, a 3-page interface appears containing bookmarks, file shares, and StoreFront. An example of the three-page interface in the X1 theme is shown below.
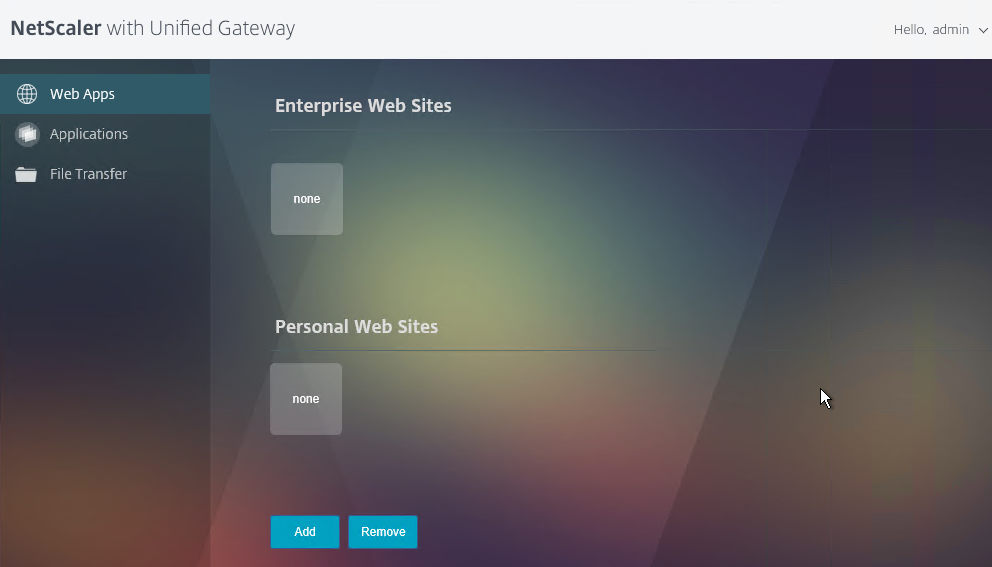
- On the Client Experience tab, the Home Page field lets you override the 3-page interface and instead display a different webpage (e.g. Intranet or StoreFront). This homepage is displayed after the VPN tunnel is established (or immediately if connecting using Clientless Access).
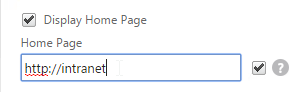
- On the Client Experience tab, there are more settings that control the behavior of the NetScaler Gateway plug-in. Hover your mouse over the question marks to see what they do.
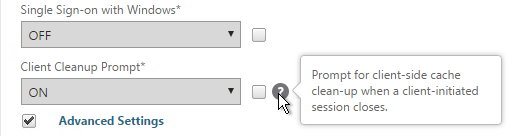
- Additional VPN settings can be found by clicking Advanced Settings near the bottom of the Client Experience tab.
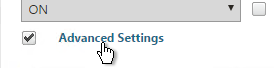
- Under Client Experience > Advanced Settings, on the General tab, there are settings to run a login script at login, enable/disable Split DNS, and enable Local LAN Access. Use the question marks to see what they do. Reliable DNS occurs when Split DNS is set to Remote.
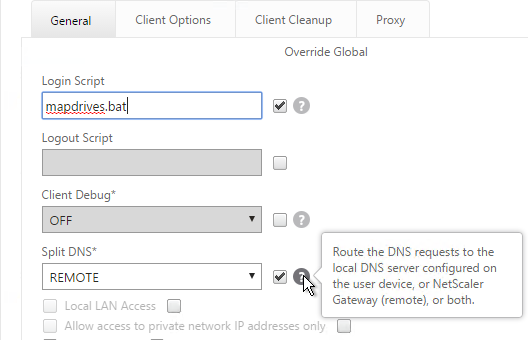
- Under Client Experience > Advanced Settings, on the General tab, is a checkbox for Client Choices. This lets the user decide if they want VPN, Clientless, or ICA Proxy (StoreFront). Without Client Choices, the VPN will launch automatically
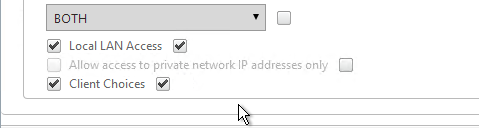
- On the main Client Experience tab, if you enabled Client Choices, you can set Clientless Access to Allow to add Clientless to the list of available connection methods.
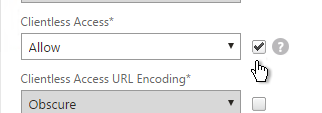
- An example of Client Choices is shown below:

- The Client Experience > Advanced Settings section has additional tabs for controlling the NetScaler Gateway Plug-in. A commonly configured tab is Proxy so you can enable a proxy server for VPN users.
- Back in the main Session Profile, switch to the Security tab.
- Set the default authorization to Allow or Deny. If Deny (recommended), you will need to create authorization policies to allow traffic across the tunnel. You can later create different authorization policies for different groups of users.
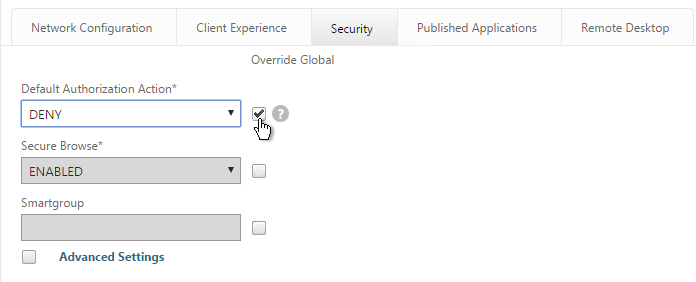
- On the Published Applications tab, set ICA Proxy to Off. This ensures VPN is used instead of ICA Proxy.
- Configure the Web Interface Address to embed StoreFront into the 3-pane default portal page. Note: additional iFrame configuration is required on the StoreFront side as detailed below.
- From Michael Krasnove: if you configured the Session Policy to direct users to StoreFront, then placing the following code in c:\inetpub\wwwroot\Citrix\StoreWeb\custom\script.js will cause StoreFront to end the VPN tunnel when the user logs off of StoreFront.
var LOGOFF_REDIRECT_URL = 'https://YourGatewayFQDN.com/cgi/logout'; // Prevent the default "logoff" screen from being displayed CTXS.Controllers.LogoffController.prototype._handleLogoffResult = $.noop; CTXS.Extensions.afterWebLogoffComplete = function () { window.location.href = LOGOFF_REDIRECT_URL; }; - Click Create when you’re done creating the Session Profile.
Create Session Policy
- In the right pane, switch to the Session Policies tab and click Add.
- Give the policy a descriptive name.
- Change the Action to the VPN Profile you just created.
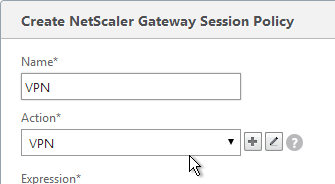
- Add a policy expression. You can enter ns_true, which applies to all connections.
- Or you can add Endpoint Analysis scans. If the Endpoint Analysis scan succeeds, then the session policy is applied. If the Endpoint Analysis scan fails, then this session policy is skipped and the next one is evaluated. This is how you can allow VPN if EPA scan succeeds but all failed EPA scans will get a different session policy that only has ICA Proxy enabled.
- To add an Endpoint Analysis scan, use one of the Editor links on the right.
- Configure OPSWAT scans in the OPSWAT EPA Editor.
- Configure Client Security Expressions in the Expression Editor.
- You can combine multiple Endpoint Analysis scan expressions using Booleans (&&, ||, !). Click Create when done.
Bind Session Policy
Most of the NetScaler Gateway objects can be bound to NetScaler Gateway Virtual Server, AAA Group, or both. This section details Session Policies, but the other NetScaler Gateway objects (e.g. Authorization Policies) can be bound using similar instructions.
- Bind the new session policy to a NetScaler Gateway Virtual Server or a AAA group. If you bind it only to a AAA group, then only members of that Active Directory group will evaluate the expression.
- To bind to a NetScaler Gateway Virtual Server, edit a NetScaler Gateway Virtual Server (or create a new one), scroll down to the Policies section and click the Plus icon.

- In the Choose Type page, select Session, Request and click Continue.
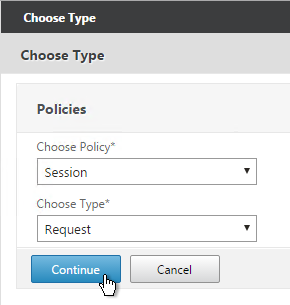
- Select one or more session policies. This is where you specify a priority.
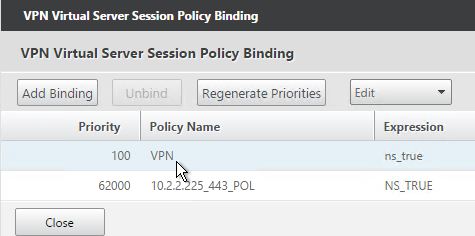
- To bind to a AAA Group, go to NetScaler Gateway > User Administration > AAA Groups.
- Add a group with the same name (case sensitive) as the Active Directory group name. This assumes your LDAP policies/server are configured for group extraction.
- Edit the AAA Group.
- On the right, in the Advanced Settings column, add the Policies section.
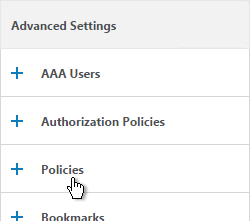
- Click the plus icon to bind one or more Session Policies.
- If you want these Session Policies to override the Session Policies bound to the NetScaler Gateway Virtual Server then make sure the Session Policies bound to the AAA Group have lower priority numbers.

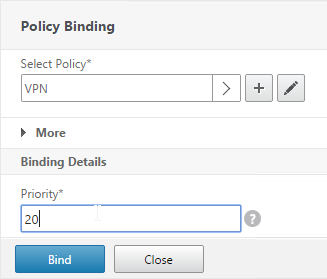
NetScaler Gateway Plug-in Installation
Here is what the user sees when launching the VPN session for the first time.
And then the 3-pane interface is displayed.
Only administrators can install the NetScaler Gateway Plug-in. You can download the Gateway plug-in from the NetScaler at /var/netscaler/gui/vpns/scripts/vista and push it to corporate-managed machines. Or you can download VPN clients from Citrix.com. The VPN client version must match the NetScaler firmware version.
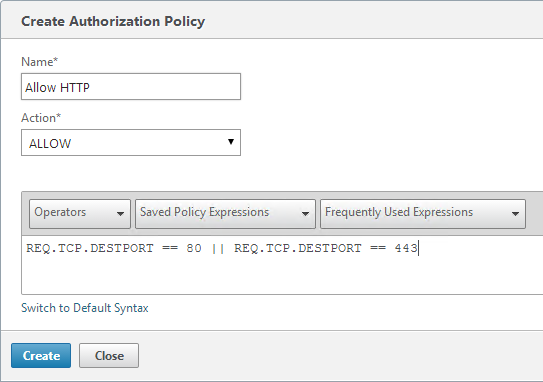
Authorization Policies
If your Session Profile has Security tab > Default Authorization set to Deny (recommended), then create Authorization Policies to allow access across the tunnel.
- On the left, under NetScaler Gateway, expand Policies and click Authorization.
- On the right, click Add.
- Name the Authorization Policy.
- Select Allow or Deny.
- NetScaler Gateway requires you to Switch to Classic Syntax. The other syntax option is for AAA.
- Enter an expression. Use the Expression Editor link to build an expression. You can specify destination IP subnets, destination port numbers, etc.
- Click Create when done.
- Authorization Policies are usually bound to AAA groups. This allows different groups to have different access across the tunnel.
- On the right, in the Advanced Settings column, add the Authorization Policies section.
- Then click where it says No Authorization Policy to bind policies.
Intranet Applications
If you enabled Split Tunnel, then you’ll need to create Intranet Applications to specify which traffic goes through the tunnel.
- On the left, under NetScaler Gateway, expand Resources and click Intranet Applications.
- On the right, click Add.
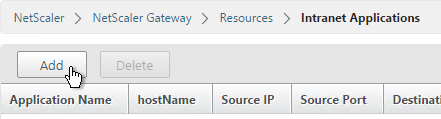
- Enter a name for the Internal subnet.
- Change the Interception Mode to TRANSPARENT.
- Enter an IP subnet. Only packets destined for this network go across the tunnel.
- Then click Create.
- Create additional Intranet applications for each internal subnet.
- Intranet Applications are usually bound to the Gateway Virtual Server but you can also bind them to AAA Groups.
- On the right, in the Advanced Settings column, add the Intranet Applications section.
- On the left, click No Intranet Application to bind Intranet Applications.
DNS Suffix
Specify a DNS Suffix for Split DNS to function with single label DNS names.
- On the left, under NetScaler Gateway, expand Resources and click DNS Suffix.
- On the right, click Add.
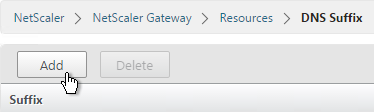
- Enter the DNS Suffix and click Create. You can add multiple suffixes.
Bookmarks
Bookmarks are the links that are displayed in the 3-pane interface. They can point to file shares or websites.
- Under NetScaler Gateway, expand Resources, and click Bookmarks.
- On the right, click Add.
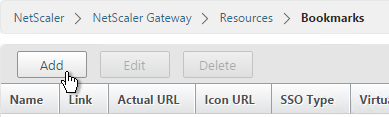
- Give the bookmark a name and display text.
- Enter a website or file share. For file shares you can use %username%.
- The other fields are for Single Sign-on through Unified Gateway. Click Create.
- Bookmarks (aka Published Applications > Url) are usually bound to AAA groups so different groups can have different bookmarks. But it’s also possible to bind Bookmarks to NetScaler Gateway Virtual Servers.
- If NetScaler Gateway Virtual Server, add the Published Applications section to bind Bookmarks.
- For AAA Group, it’s the Bookmarks section.
- On the left, find the Published Applications section and click No Url to bind Bookmarks.
VPN Client IP Pools (Intranet IPs)
By default, NetScaler Gateway VPN clients use NetScaler SNIP as their source IP when communicating with internal resources. To support IP Phones or endpoint management, you must instead assign IP addresses to VPN clients.
Any IP pool you add to NetScaler must be reachable from the internal network. Configure a static route on the upstream router. The reply traffic should be routed through a NetScaler SNIP. Or the NetScaler can participate in OSPF.
When a client is assigned a client IP, this IP address persists across multiple sessions until the appliance reboots or until the appliance runs out of IPs in the pool.
- Edit a NetScaler Gateway Virtual Server or a AAA group.
- On the right, in the Advanced Settings section, click the plus icon next to Intranet IP Addresses.
- On the left, click where it says No Intranet IP.
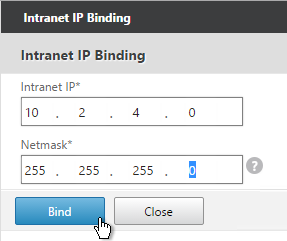
- Enter a subnet and netmask. Click Bind.
- To see the Client IP address, on the client side, right-click the NetScaler Gateway Plug-in and click Configure NetScaler Gateway.
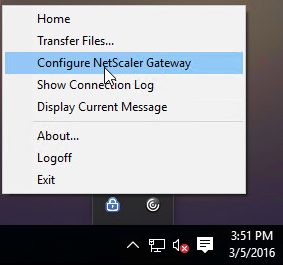
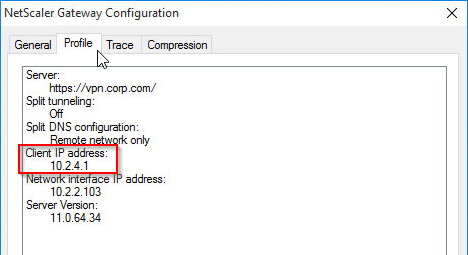
- Switch to the Profile tab to see the Client IP address.
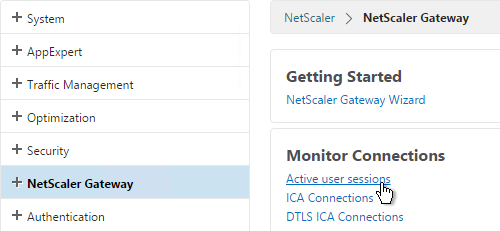
- To see the client IP on the NetScaler, go to NetScaler Gateway and on the right is Active user sessions.
- Select one of the views and click Continue.
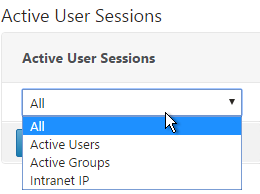
- The right column contains the Intranet IP.
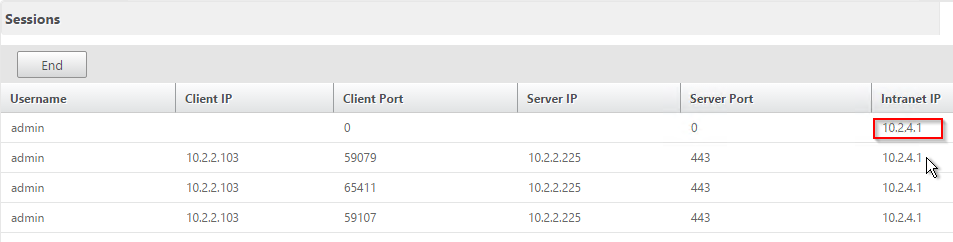
StoreFront in Gateway Portal
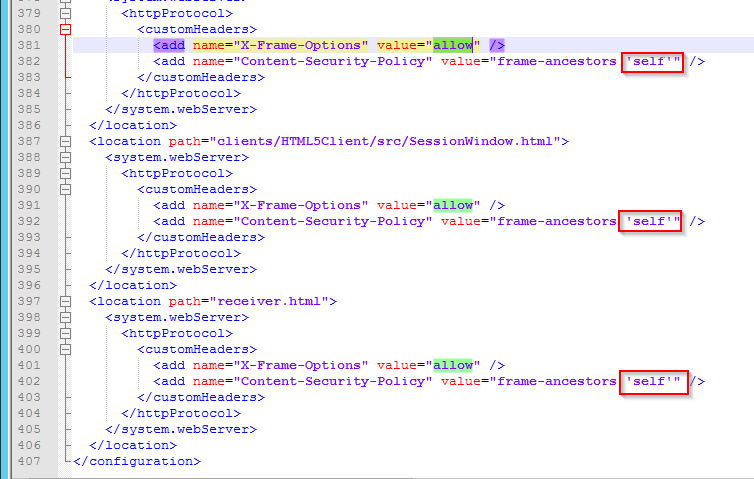
- If you want to enable StoreFront to integrate with NetScaler Gateway’s default portal, edit the file C:\Inetpub\wwwroot\Citrix\StoreWeb\web.config.
- On the bottom, there are three sections containing frame options. Change all three of them from deny to allow.
- Also change frame-ancestors from none to self.
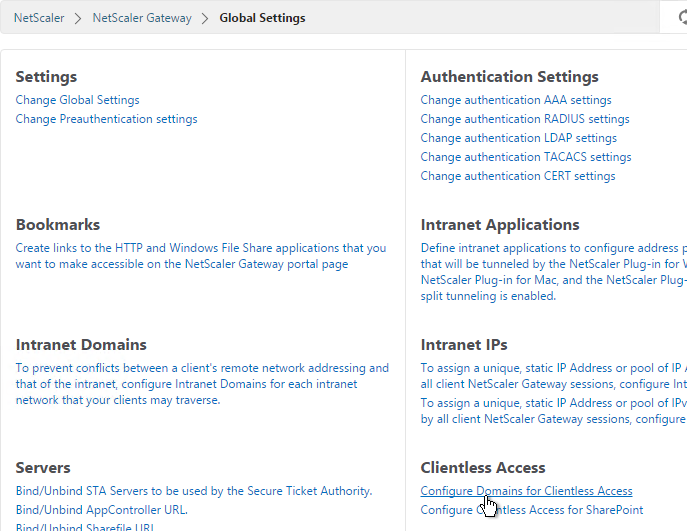
- In NetScaler, go to NetScaler Gateway > Global Settings and click Configure Domains for Clientless Access.
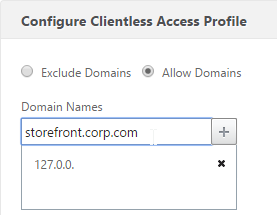
- Change the selection to Allow Domains, enter your StoreFront FQDN and click the plus icon.
- Click OK.
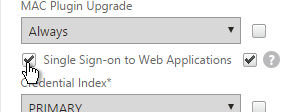
- In a Session Policy/Profile, on the Client Experience tab, make sure Single Sign-on to Web Applications is enabled.
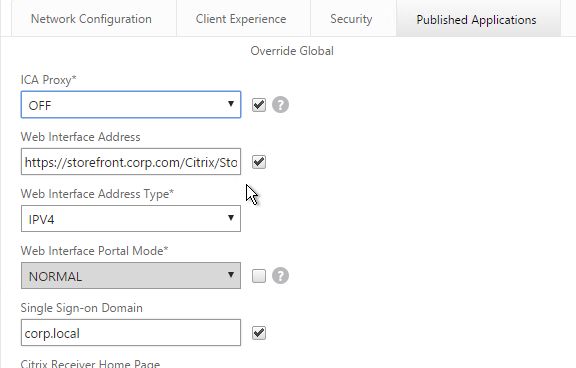
- On the Published Applications tab, configure the Web Interface Address to point to the StoreFront Receiver for Web page.
- Configure the Single Sign-on domain to match what’s configured in StoreFront.
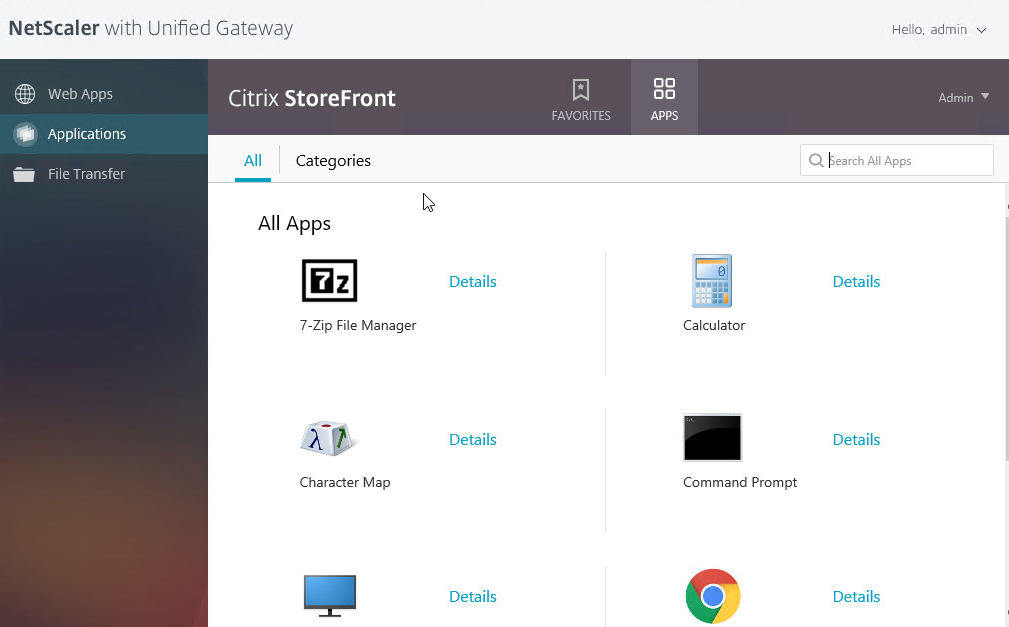
- The Applications page of the 3-page portal should automatically show the StoreFront published icons.
Quarantine Group
NetScaler Gateway can be configured so that if Endpoint Analysis scans fail, then the user is placed into a Quarantine Group. You can bind session policies, authorization policies, etc. to this quarantine group. Policies bound to other AAA groups are ignored.
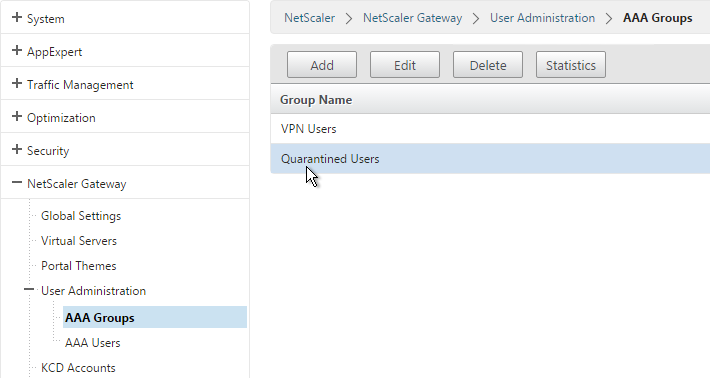
- Go to NetScaler Gateway > User Administration > AAA Groups.
- Add a new local group for your Quarantined Users. This group is local and does not need to exist in Active Directory.
- Create a new Session Profile.
- On the Security tab, check the box next to Advanced Settings.
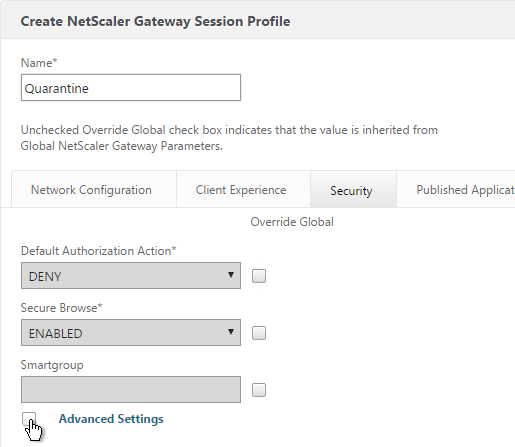
- Check the box to the right of Client Security Check String.
- Use the Editor links to add an Endpoint Analysis expression.
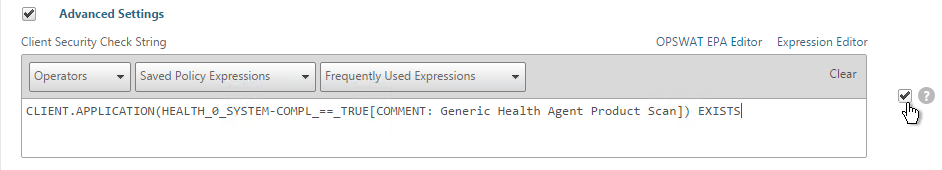
- Just below the Client Security Check String, select the previously created Quarantine Group.
- Click Create when done.
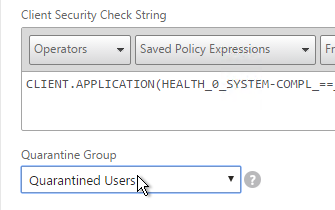
- Create a Session Policy and select the Session Profile you just created.
- Enter ns_true as the expression. Then click Create.
- Edit your Gateway Virtual Server and bind the new session policy.
- Bind session policies, authorization policies, etc. to your quarantine group. These policies typically limit access to the internal network so users can remediate. Or it might simply display a webpage telling users how to become compliant.
- To troubleshoot Quarantine policies, use the command
nsconmsg –d current –g pol_hits.
- Another option is to use the session policy bound to the Quarantine Group for SmartAccess configuration.
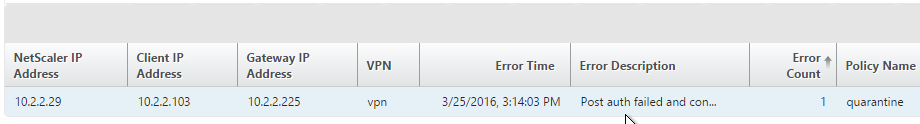
- Gateway Insight (Insight Center 11.0 build 65 and newer) shows users that failed EPA scans and their quarantine status.
Absolutely amazing walkthroughs Carl, you are my go to bible for many Citrix deployments and issues. I am hoping you can clear something up with IIP IP pools and the Netscaler located in Azure. As described by this article – https://docs.netscaler.com/en-us/citrix-adc/current-release/deploying-vpx/deploy-vpx-on-azure/configuring-address-pools-on-azure.html you need to apply the private IP addresses in the Azure NIC config, only issue is Azure supports only 256 IPs per NIC. Is this something you have experienced? is there any other way around this? Thank you in advance.
I haven’t tried it in AWS, but I wonder if you can configure route tables to route the Intranet IP Pool through a SNIP. You would have to disable source/destination check on the VM.
Great thank you for the reply, I will give it a go. Wonder if there is a limit on VPN connections on the SNIP as I heard that there maybe port exhaustion on 1000s of VPN connections, only heard that this happened on a Cisco device though.
Hi Carl
i am having issues with split tunnel . i have local lan 192.168.1.0 as well as company having the same subnet
how can i configure split tunnel so that company traffic goes via the netscaler VPN.
Also the netscalers are in the DMZ. what ports have i to open on the dmz to the backend for full vpn
See https://support.citrix.com/article/CTX126953
Otherwise you might have to configure Intranet Applications very precisely (/32) instead of an entire subnet. Or change your local subnet.
Hi Carl
Thanks for your reply. I have removed local Lan access.
MY DNS name resolution is not working at all.
i tried split Tunnel ON , OFF with Split DNS remote
i am able to ping with IP address . Tried LB DNS Virtual server too
Am i missing something
Hi Carl, I have setup a new VPX with the latest firmware 12.1 build 62.23 , configured VPN gateway and anyway all good able to reach my internal resources but i have a very weird issue , i can ping my internal servers network etc
but i can’t use nslookup with host name
so basically if im connected to vpn i can ping and reach all my network
but the weird issue for me as an IT why i can’t nslookup hostname
i have dns suffix and dns virtual server setup
again able to resolve my FQDN XX.domain.com and even ping XX also able to ping them,
but can’t resolve hostnames
I’m not sure if this a bug or I’m missing something ?
How is your split DNS configured?
Do you have any PBRs for your management network?
actually I configued the basic , like added under traffic management > dns > name servers TCP and UDP
also DNS suffix my domain FQDN
in VPN my session policy, configured under network configuration > DNS cirtual server and select my DNS vserver , split tunnel is off.
and I don’t have PBRs ..
I have 2 NICs in this VPX , one dedicated management nic
and the other one is DATA , which is the servers VLAN ..
again Carl I have no complain at all everything working fine all applications etc
but for me and the IT members it is an issue that we can’t perform NSLOOKUP while connected to VPN
and the issue I really dont know where to look and how to start
Hi Carl sorry just wanted to add splitdns set on both , i tried remote only , and still the same
Hi again Carl , I downgraded from 12.1 build 62.23 which was just released two days ago
into 12.1 55.18 and now all good.. nslookup is working fine
it must be a bug
I do have 2 another appliances which were working fine “nslookup” until i upgraded them now and then gave the same issue too
can’t nslookup, very very weird one,
just wanted to add , if i’m connected to vpn and then nslookup IP , ex nslookup 1.1.1.1
then i do see in netscaler under dns > records > PTR records all the arp
like 1.1.1.1.in-addr.arpa <- because a user tried to nslookup 1.1.1.1
so netscaler is able to resolve but for some reason not sending the result back to the user 🙁
Hi Carl,
Thank you for the article.
I have question that is important. I have a mobile phone which is in our corporate network and that needs to be access external public server through SLL VPN . from the mobile it needs to be able to route internet access for phone to other external IP . how can we allow external public server for the mobile to be access to specific IP on internet from our internal network with SSL VPN solutions?
In our environment we have netscaler in DMZ behind the firewall. to allow public IP access which firewall rules do we need to open to communicate with public server.
Regards,
Ilyas Ahmed
Citrix has a VPN client for iOS and Android. Is that what you’re asking?
If the VPN client needs to reach a destination through a VPN tunnel, then the VPN tunnel endpoint (NetScaler) needs to be able to route and connect to the destination. If you assign Intranet IP (aka IP Pool) to the phone, then only the phone’s VPN address needs authorization.
Hi Carl,
Thank you for your reply,
Yes, I am asking about Citrix SSO client which supports SSL VPN.
We have a machine in which android base software is running and it is already connected to our corporate network to access our internal server.
To connect external public server, I am planing to use SSL VPN for android devices . My question here is can we allow outbound traffic via SSL VPN? If I assign internet IP as public IP will that be work?
If I allow SNIP to access public IP in firewall will mobile devices connect external IP? Please reply
Sorry for my English.
Regards,
Ilyas Ahmed
Hello Carl,
I have recently deployed VPN capability to a NS 11.1 version on VPX also incorporating the drop down menu option following “https://support.citrix.com/article/CTX203873” article. Instead of using this technique for Domain, I am using for Apps and VPN so user can choose what they like. The session/profile policies are bound to user groups that are added to the adv security. This solution has worked on MPX and SDX 10.5 and 11 before. Prior to using this article, there was a manual process that I had followed.
Here are my challanges:
1. It takes a couple of tries when a VPN user gets through. The download the client window pops up everytime and the process takes forever. There are times when the process doesnt go thru and user is back to the prompt to log on.
2. The cleanup utility is set to be OFF but it comes up in the end
3. The 3 pane window comes up. The plan is to show storefront instead so users can launch the apps
Do you think this process is resource intensive and VPX needs to be beefed up?
hello Carl
I have setup unified gtw
I connect from a client with the plug in vpn client
All is ok I can see the active sessions on my netscaler
I create some applications on UG allk ok
but I dont understand
I want to for ex ping from cmd of my internal ip dont work
I cannot ping any of my servers
I have changed my policy session to allow
I can ping from the web page
Tks for help
Do you have Intranet IPs (IP pool) configured? If so, did you add a static route on your internal network so replies can return to NetScaler?
Hi Carl,
Here’s an interesting one. I have a Netscaler 11.1 (in Azure). I have a carefully tested DFS namespace. I have (after some effort) succeed in accessing this DFS namespace when connected via the VPN Gateway. In fact all the current namespaces properly resolve and are accessible. Sites are working and the Folder referrals are exactly as they should be. Testing is with a domain joined laptop running Windows 10.
Here’s the deal… The DFS shares are only accessible for a few minutes, then they become unavailable (act like their off line, or indicates “empty”). When this happens I can manually open any of the actual file shares directly on their respective servers, so I have not lost connectivity. Something with either name resolution or some other mechanics of DFS????
I have set this up according to MS documentation so that all DFS is using FQDN referrences. Rebooting the laptop and reconnecting does not restore DFS access. In fact in my most recent test I can not get the DFS shares functional through the tunnel. Very weird.
Remote connection is actually the corporate guest WiFi so the traffic all on fast links (unless Azure is hanging something up).
Very interested in your thoughts on this one.. Hopefully it is something you’ve seen before.
Thanks
Kevin
What build of NetScaler?
Hello Carl and community – I have a question regarding Advanced End Point Analysis (EPA scans).
1. It appears EPA only works with Windows and Mac clients via the use of a plug-in, yet I haven’t found information that states if EPA works with both the receiver for Windows and Mac and also browsers on those devices, or just the browser.
Thoughts?
Thanks,
Brandon
Just the browser.
When configuring two separate IP Pools for two separate AAA groups, is it possible to allow those two subnets to see one another? Ex:
IP Pool A – 10.10.32.0/24
IP Pool B – 10.10.33.0/24
I need both of these subnets to talk (ping, RDP, etc…) to each other. Dose the routing ever leave the NetScaler in this case? Thank you for all your expert wisdom. It has been a tremendous help in implementing.
-Darin
I believe that’s true but i don’t think I’ve tested it yet.
So, my VPN clients cannot even see each other when they belong to the same IP Pool. Just to make things easier, I just have everyone in the same IP Pool now, 10.10.32.0/22.
However, they cannot see one another when logged in. Ex. 10.10.32.2 cannot see 10.10.32.3.
Since they belong to the same subnet, I do not understand why not. Is there a security setting within the NetScaler Gateway configuration that needs to be enable for client to client communication?
Thanks again!
Hello Carl,
You give a lot of time to the Citrix community, thanks.
If you are still watching this thread – we are rolling out 11.1 Netscaler and working on SSL VPN.
Everything connects well and web based speed tests are good however SMB file transfers are around half what our Cisco SSL VPN provides. Any guidance as to what might be happening? I’ve reviewed several performance tuning steps with little change. One area that was a common help under Cisco was the MTU setting however under Citrix you are limited to nothing lower than default LAN MTUs of 1500 and up. There is detection enabled but in my experience with Cisco which also has detection, the MTU setting itself was the most effective.
Any difference in ciphers?
Is the NetScaler a VPX instead of a MPX?
You should be able to set MTU on NetScaler – https://support.citrix.com/article/CTX117322
According to that article the default MSS is 1460 which is likely enough although I have had some perform better in the 1360 range. This is also for 10/10.1 but likely fine for 11.1. In the end this did not improve speed. I was reading – https://support.citrix.com/article/CTX211877 which outlines the default NET profiles and what each is for. I’m finding however that some of the settings are not as described in the defaults and am wondering if they were meddled with or if the document is no longer accurate. I’ve seen docs recommending Westwood, Reno and BIC among other settings so I’m not sure what to follow anymore. The Netscaler does not have an identical path (switch/firewall/etc.) as the Cisco but we did find that connections over AT&T broadband are actually faster over Citrix whereas every other connection seems to favor Cisco – completing tests at twice the speed of Citrix. This would seem to show that there is nothing on the client PC or main network to blame. If it were, there wouldn’t be any tests that performed better under Citrix, unless AT&T has a love for Netscaler SSL? I’ve now tried several of the NET Profiles as well as tinkering with individual settings. The nstcp_default_mobile profile brought me closest to Cisco but the old Cisco often tests at twice the speed. Since nstcp_default_mobile performed noticeably better than other profiles at SMB transfers it gives me hope that there is a combination that will bring it at least close to Cisco. Any other suggestions before we sift through WireShark?
Thanks again,
MR
Just a suggestion to check that you don’t have multiple interfaces on the same network on your Netscaler appliance for your backend SNIP. This can result in the MAC address changing when the snip communicates with the backend servers resulting in lower performance.
This article describes setting the MSS is that the same as MTU ?
Yes. Google will explain the minor difference between the two.
Has anyone heard if Citrix has plans on supporting captive portal through the netscaler plugin?
how to mac binding for VPN user
Hi Carl
is it possible to have multiple ssl vpn connections to different NetScalers? and is it possible to prevent multiple ssl vpn connections?
Like one connection to company a and the second connection to company b
I don’t think I’ve tried that. I’ve only seen one Gateway Plugin running on a machine so I suspect it’s only one connection per client machine.
We are using Netscaler SSLVPN along with intranet ip’s so we can manage the remote vpn sessions internally. One issue we’ve come across with all our envt’s, is that the same intranet ip is given to multiple end points. So in our reverse dns lookup, you could have 3 or 4 hostnames now with the same ip address. So if one user logs in and gets a x.x.x.2 address and than logs off, than someone else logs into the sslvpn, they could also get the .2 address. Thus when doing a nslookup, we could get both their hostames replying. We’ve tested this behavior on both 11.0 and 11.1 versions of the firmware. We opened up a case with citrix, but they said its not a netscaler issue, that we need to include a logoff script in the session policy to delete the pointer record in DNS at logoff. Curious if you’ve come across this at all. Thanks
Would DNS Scavenging help?
I think it would, but this issue can occur anytime throughout the day. yesterday we were doing testing and within one min of a tester logging out, a new tester signed on and was given the old intranet ip of the previous user, creating a second reverse dns record of the same ip.
Is the IP pool too small so that it has to reuse IPs?
No its a /24 subnet we’ve defined and we only have 3-4 testers and are seeing the issue.
Hi Carl,
where we need to keep drive mapping batch file on user machine?
Thanks,
Krishna
Carl, insightful as always: there are 2 things we are fighting with on 11.1.
1. The VPN Client icon, while it shows up in 11.0, it doesnt for 11.1, despite the option being checked in the Global Session policy
2. SSL VPN DNS View are not evaluating (as noted here: http://discussions.citrix.com/topic/362472-ssl-vpn-dns-view-not-evaluating/ & http://discussions.citrix.com/topic/347447-dns-views-for-internal-vs-external-domain-name-over-cag-ssl-vpn/). In 11.0, vpn users could not even access those resources without Split Tunneling being turned on. In 11.1, with Split Tunneling turned off, they now can, however they are still getting the external IP (still) instead of the internal one. Thoughts?
If we configure the SSLVPN with dual factor authentication LDAP and Radius where would the user enter there credentials? Can this be done through the VPN client or does it need to be done through the front end web portal or can it be both?
11.1 accepts authentication through the Gateway plug-in, including two-factor. nFactor doesn’t seem to work.
Ok. So is nFactor an issue with SSLVPN all together or just through the plug-in? Thanks again Carl
Just the plug-in. Some auth only works in web browsers.
ok. do you know which browsers and are there any future releases that you know of where the vpn client are scheduled to support nfactor? thanks again Carl
The Citrix Receivers have the same problem. I expect Citrix to eventually address the limitation.
We have a captive portal landing web page that is setup to authenticate laptop users connecting in from public-access networks i.e hotels, starbucks, airports etc.. If we were to implement the SSLVPN always on functionality on the Netscaler how can we configure this so that once users connect using the always on VPN the NS can pass the users credentials through without sending them to the captive portal login to authenticate.
We are looking to implement SSLVPN through the NetScaler GW with “split tunnel” configured off. If we issue certificates to the endpoints do we need to generate and install a public ssl certifcate on the netscaler to authenticate the endpoints using certificates?
Get the CA certificate and bind it to the Gateway vServer as a “CA” certificate. This can be any CA. Then you can enable Client Certificate Authentication.
Ok. Thanks Carl. Appreciate the response.
Is it in any way possible to skip the version check of the EPA plugin? I want to update my MPX but NetScaler wants to update or downgrade if not the exact same version of EPA plugin is present as the NetScaler firmware version. Is there a workaround? Users are not allowed to install the plugin themselves and I am not able to roll out a new client to everyone over night. Is there a workaround for this problem?
I think the file /netscaler/ns_gui/epa/epa.html has the version number in it. It might be possible to change the file.
Hi Carl,
I also would not be able to run different versions of client EPA plugins. But I came across this article and I will test it with the client: https://www.citrix.com/blogs/2013/10/23/take-control-of-epa-client-updates-and-other-vpn-customizations/
Regards, Christian
I don’t think this works on 11.0 and newer. The epa.html is quite different than 10.5.
Hi Christian
have you tried this option with 11.1 and got any issue?
Hi Carl!
Is it possible to create a SSL-VPN with Two Factor Authentication (2FA)?
I’ thinking of something like a token from a mobile phone, for example?
Of course. Anything RADIUS should work. Just add the RADIUS server and bind it to to the Secondary authentication on the Gateway vServer.
Is it possible to increase the limit to bind maximum 128 Intranet Applications to an AAA group? Or can I add domains with wildcards (*.corp.domain)? I have to add about 400 subnets to a aaa group.
If you do multiple AAA groups, does it merge them beyond 128?
I have not tried that. I only have one group for all VPN users and the Intranet Applications are bound to that one group. When trying to connect the error in the connection log appears “395 intranet application confirmed, Exceeds the limit of 128”.
So you mean to create a second group, add the users also to the second one and see if the error still appears?
I suspect it won’t work but you’re welcome to try.
Hello Carl,
I have a problem with a VPN plug-in v11.1.48 client, which is behind a proxy and he gets no connection over the proxy to the Netscaler gateway.
What can I configure on the Netscaler differently to make this connection? What do I have to consider?
It is possible to establish a connection to the Netscaler gateway through a proxy?
Is the proxy terminating SSL? If so, that won’t work.
No, the proxy don’t terminate SSL. I have the possibility on the netscaler to configure which IP addresses or networks over the Tunell must go?
Of course. Enable Split Tunnel. Configure Intranet Applications and bind them to the Gateway vServer or to AAA Groups.
Hi Carl:
Great article as always. I find most of what I need on your site as, yes. great as the product is, the documentation definitely has gaps. Question: I am doing clientless VPN and the customer has two stipulations: 1. to limit access to the gateway by AD domain and 2., to limit access in the VPN to specific sites. The first one, not so tough; the second, I’m unclear on this. How do I create a site ACL in the gateway, i.e., I would specify a certain webpage as home, from where the user is limited to two other sites (host names)?
Bonus question. Once in, how do I limit access to an additional URL by AD Group?
Appreciate your help.
Phil
NetScaler has authorization policies based on destination IP address. You can bind these authorization policies to a AAA Group that matches your AD group.
Another option is to assign Intranet IPs to your AAA group. Then use a different device to control access from those source IPs.
That seems to apply to the second question. Perhaps I’m not wording correctly.
Login to the gateway sends the user, via session policy “Client Experience” to a page on server “A”
On this home page, which can also be used internally, there are links to pages on severs B, C. D and E.
I want the user to be able to select link B or C but to fail on D.
Is this not a just a response policy of some sort? (if hostname not A,B or C)
Link E is the tricky one. I want only members of a given AD group to be able to select it, but lets set that aside for now.
Phil
If it goes across the VPN tunnel, then Authorization policies or firewall rules are your option. If doing clientless, then you might be able to do Responder policies using HTTP.REQ.USER.MEMBER_OF expressions.
Hello Carl,
Thanks for the article, it’s very interesting, and i have a question:
we have out Test NS VPX Gateway updated from version 10.5 to 11.0, and our client have at this moment all the version 10.5. When I try with a Client Plug-in v10.5 to connect to the new v11 VPX Gateway, the Plug-in start the Upgrade routine but I receive the error message that “the version from Plug-in and the Version from Gateway are different” and the upgrade don’t continue. Could you tell me where and what can I check?
Thanks,
Hector
If NetScaler doesn’t recognize the version correctly, that’s usually an issue with browser cache.
Hello Carl,
Thankyou for your answer. I have emptied the cache from the browser but still the same message “plugin and Gateway Version differently”. Do you have another idea what can i check?
Worst case you could uninstall the Plugin and let it reinstall.
Carl,
If the Gateway was in the DMZ, what is needed to allow the SSL Tunnel to access everything and anything on the corporate LAN? Firewall rules?
In my lab I go from Internet > NAT to VIP on VPX (which sits in the LAN). The SSL VPN tunnel has access to everything (as if I was connected to the corporate network)
In my PROD environment, I go Internet > NAT to VIP in DMZ > Lan. My SSL VPN tunnel only has access to a very limited bunch of resources. Port 80 HTTP for example.
If you are using Intranet IPs, then firewall needs to allow those IPs. If you’re not using Intranet IPs, then firewall needs to allow the SNIP.
Hi Carl
Thanks a lot for your articles. I was able to install it a few month ago but now we changed the system and after I installed the version 11.0. 64.34 I have some problems with the VPN.
First it takes always the default Session Policy with the Global Settings but I need to allow just some AD Group users I have set in the AAA authentication settings.
And as second problem, my logon script is not running after the VPN connection is established.
The difference before was I did a version Update from 11.0 63 to 11.0 64 and there was no SETVPNPARAMS_POL in the Session Policies and no SETVPNPARAMS_ACT in the session profiles.
How can I bypass this policy?
Thank you and Regards
Jose
The global settings are always applied. That’s why you need to override them.
Are you saying that non-authorized users are able to login? In that case, configure your LDAP policy with a search filter.
Or are you saying that your ICA Proxy only users are getting VPN as an option? In that case, make sure Client Choices is overridden and turned off.
Carl,
I was able to follow your steps to do full VPN and i also got SSO working with full VPN. After SSO worked i am now unable to launch my applications, i am getting the following error messages.
“Cannot connect to the citrix xenapp server. SSL Error 43. The proxy denied access to the port 1494” I confirmed that i can access that port on the xenapp servers from the netscaler with no issues. Do you have any thoughts on this?
How is ICA routed? Is it ICA Proxy through Gateway? Or is it internal through the VPN? If internal, do your authorization policies include the IPs/ports? If ICA Prox, are the STAs configured correctly?
I have ICA off at the moment and i am using FULL VPN. STAs are configured on the netscaler. If i break SSO it works but once SSO works it fails.
StoreFront has a gateway object defined and remote access is enabled on the store? Then it should be using ICA Proxy. Follow http://support.citrix.com/article/CTX115304 to make sure SSLProxyHost is in the .ica file.
Make sure your Authorization policies include the VDA IPs on 1494/2598.
Hi Carl, Great post.
I have a question I would like to ask in regards to a client site I am setting up. We NetScaler configured as above with an LDAP group AAA bound for VPN access, and Web based access works as expected. However when a user in the VPN group tries to logon to Receiver the logon fails.
I am assuming this is something with the bind order, but I have the policies set lower than those set on the vServer so I am a little stumped. Any ideas would be great.
Regards
Chris
In the Receiver policy, Override Global for Client Choices and leave it unchecked.
Hi Carl, unfortunately this is already set.
Hello Carl,
Great article. I have always admired your work and have been following your blog from some time now.
I have a question regarding your statement on session timeout: “Session Time-out, is a total session timer (doesn’t care if user is working or not).” Your statement actually fits for Forced time out under network settings of session profile.
As far as I know session time out will only trigger if there is no traffic coming from client to VPN vserver for the specified time out period.
Correct me If I am wrong…
Anyways Great work 🙂
I can’t find any clear documentation on this. I wonder if “session timeout” refers to clientless VPN while “forced timeout” refers to Gateway Plug-in.
You might be correct. This article says “no network activity”. http://docs.citrix.com/en-us/worx-mobile-apps/10/xmob-worx-home/xenmobile-authentication-pin-prompts.html
Hi Carl, thank you for another great article!
I have the following questions regarding Netscaler Gateway 11:
– Is the VPN plugin compatible with old XenApp farms using Web interface instead of storefront? I have had problems with recent Receiver versions (had to use ICA Only plugin instead) and I wonder if the same kind of uncompatibility could happen with the VPN pulgin.
– Have you tested the File Transfer feature? I was never able to make it work with NS 9.3 because it uses deprecated SMB protocol which is not supported in recent versions of Windows servers. Would that work now?
-Are there any special considerations to migrate NS Gateway configuration (authorization policies, intranet applications, etc.) from versión 10.1 to 11.0? Is there any change in the sintaxis of commands?
Thanks in advance!!!
1. VPN plugin creates a generic VPN tunnel. In theory, any traffic can run on top of it. ICA Only plugin could send ICA traffic across the tunnel to the old Citrix farm. I’m not aware of any limitation.
2. I have not tested File Transfer. It’s an old feature that is still in 11.0. I see this thread – http://discussions.citrix.com/topic/359725-file-share-bookmark-upload-fails/
3. The configuration commands are the same. If you have a test VPX appliance running 10.1, load your config on it, upgrade it, and see if everything still works. Or you can copy your 10.1 Gateway commands to an 11.0 test appliance and see if they work.
However, themes are totally different.
Carl
Can u explain the difference between netscaler plugin compare to citrix reciever? I have never used the plugin for netclarer.
NetScaler Gateway Plug-in is for VPN connections. It’s installed automatically when you connect to a NetScaler Gateway that has Full VPN enabled.
Hi Carl,
I am trying to enable Storefront to integrate with Netscaler Gateway (“Storefront in Gateway Portal” part). I have to say it works correctly if you point to the Storefront web server directly. However, if i tried to point to a VIP (which load balanced SF servers with Netscaler) it will ask under the application tab to authenticate again so wont show the resources straigh away.
Have you tried pointing to the NS LB VIP and not the SF itself? does it work?
Please see below the settings used:
NS 11 build 65.31
SF version 3.5 on W2K12 R2.
Full VPN with ICA proxy OFF.
SF VIP: I tried with persistence Source IP or CookieInsert. Cert CA and Server binded (same as the SF servers). 2 “Service group members” with Header X-Forwarded-For added.
It works pointing to the SF itselft but not pointing to the SF LB VIP created ( will require to authenticate again).
Please let me know if you need more info.
Thanks,
Kamel
Is one SSL and the other is HTTP?
What errors are you seeing in the StoreFront event log?
Is StoreFront loopback enabled with OnUsingHttp?
I use ssl for all with the same cert for SF and the NS LB VIP . Weird, now it is working using the NS LB VIP (the settings are: persistent/CookieInsert, Cookie Name/NSC_SFPersistent, Service group with two SF members, Header/X-Forwarded-For, Monitoring the StoreName)
Carl,
your site has always provided very helpful information for me. i followed your steps but i cannot keep to get the integration going with SF into the GW. i am looking to do this was since i am now using the VPN Plug-in my SSO is not working to the SF. Also, i noticed that edge sight/insight is not logging the traffic when using the VPN Plug-in. Please let me know what you think.
thanks.
If StoreFront is https then NetScaler can’t intercept the traffic to inject credentials.
If ICA goes across the tunnel instead of through ICA Proxy then I suspect that AppFlow won’t work. You’d need to force StoreFront to use ICA Proxy instead of direct connections (through the tunnel).
thanks for the quick reply. i am forced to use VPN Plug-in because of the timeout. I was told that ICA does not do the time out on the netscaler. If you know of a way to get the timeout working and have the AppFlow working as well that would be great.
Hi Carl,
Thank you so much for the insightful articles , they are a massive help !
I have been trying to get “Storefront in Gateway Portal” to show and the “Application” icon does not show i have followed your article and Jen Trendelkamps article also.
I logged a call with Citrix and they said it wasn’t a supported configuration and they gave me best effort support … and the best effort support could not get it working either .
Can you let me know what version of storefront you used in your configuration example ?
I did 3.5. Don’t forget to add it to the Clientless Domains.
If you have Client Choices enabled, are you able to access StoreFront and automatically log in?
Thanks for the quick reply , yes i have configured the “Domains for Clientless Access” with the storefront FQDN .
Yes i can login to storefront automatically (SSO) when using “Virtual App and Desktop Access” from the Client Choices page.
I have the exact same problem. The Applications Tab won’t appear. I followed your instructions and nothing changes. NS11 64.34 / SF3.0.1
I got it. You have to do an iisreset after editing the web.config and then Global Override Webinterface Mode -> Normal
https://blog.trendelkamp.net/2015/09/netscaler-gateway-single-sign-on-to-storefront-in-clientless-access-mode/#comment-193
Carl, truly fabulous and detailed article. I don’t know where you find the time and gather the experience to do all this and still have a day job.
Q: for clientless browser VPN, how does storefront manage launching apps? does it rely on HTML5 clients or does it still use the local native receiver? Does SF need to be configured with the gateway still?
There are two ICA engines: regular full Receiver (Windows, Mac, Mobile, Linux, etc.) and Receiver for HTML5. Both require NetScaler Gateway to handle proxy from public IP to internal IPs. Receiver for HTML5 uses WebSockets to Gateway. Regular Receiver uses ICA (wrapped in SSL) to Gateway. Receiver for HTML5 does not require any client-side software but regular Receiver does. Full Receiver is more functional than HTML5 Receiver.
If I want to use HTML5 with NetScaler. How can I configure? I have created HTTP profile to enable WebSockets but I still cannot use HTML5. However, I have configured with StoreFront and tested directly to StoreFront link that it’s ok to use HTML5 but not work with NetScaler gateway to logon.
I’m testing some configuration on a VPX (from my production environment into a isolated test environment). I can’t get the Gateway Virtual Server to show UP. I’ve gone through the procedure you have set up, along with guides I have found on several other sites/forums. I’m not sure what is causing the status to be down as the Netscaler won’t give me any useful feedback other than DOWN. The only real deviation I have from the guide I’ve done is to use a self-signed (Server Test Certificate), which in my current case should be adequate (the production Netscaler appliances have a proper cert). Any advice as to what I should try to do to get the Virtual Server online?
That usually means the cert isn’t bound to the Gateway. Or SSL is not enabled. Go to System > Settings > Basic Features and make sure SSL is enabled.
Note: most browsers won’t accept self-signed certs where self-signed means Issuer and Subject are the same.
Hi Carl,
Client is asking to disable SSLv3 on internal virtual server in netscaler. Is this is recommended ? or is there any disadvantage of disabling it. As we dont have netscaler test environment , do we have any way to test it before deploying it in production ?
If an HA pair, you could disable it on the secondary and make sure the NSIP is still reachable. You’d have to repeat the config on the primary.
SSLv3 should always be disabled.
Another option is to enable Default SSL Profiles, which automatically disables SSLv3.
All NetScaler customers are entitled to NetScaler VPX Developer Edition. You can test on that.
It means TLS 1.2 should be enable on all the Browsers as well ?
Of course. Why wouldn’t you?
If the topic is disabling SSL v3 on the VIP, I shouldn’t think doing so on the Secondary would be relevant. Though I do agree that it should be disabled in general – a few years ago. All browsers will have a minimum of TLS 1.0 enabled but I find that TLS 1.1 and 1.2 has to be enabled in IE, manually or by GPO.
Hi Carls,
Good Morning.
As we have disabled SSLV3 due to security, we got a request from client to remove cipher methods RC4 DES, 3DES as well as These cipher methods are no longer considered secure. we disabled these chipher methods and suddenly Citrix stopped working. Even Netscaler login page was not coming up.
What we can do in this case if we going to remove cipher methods RC4 DES, 3DES . We do have our legacy environment 5.0 and 7.6 running along with Storefront 3.6. Will it break any communication b/w netscaler and storefront ?
Please suggest what we can do best here.
StoreFront should have no problem with newer ciphers. Web Interface might not accept the newer ciphers.
Did you follow this article? https://www.citrix.com/blogs/2016/06/09/scoring-an-a-at-ssllabs-com-with-citrix-netscaler-2016-update/
Hello Carl,
Thanks for the article.
Is the SSL VPN for netscaler is similar as the Cisco VPN which can be used for RDP to the servers through the Internet or it is just for applications?
Thanks,
Pavan
It provides a full VPN tunnel so any traffic can go through it.
Citrix has a separate RDP Proxy feature – https://www.carlstalhood.com/netscaler-gateway-11-rdp-proxy/