Navigation
- Change Log
- Overview
- OTP Encryption
- AAA vServer
- Push Service
- LDAP Policies/Actions
- nFactor Visualizer
- Number of Registered OTP Devices
- Traffic Policy for Single Sign-on
- Citrix Gateway and Authentication Profile
- Update Content Switching Expression for Unified Gateway
- Manageotp User Experience
- OTP Authentication User Experience
- CLI Commands
Change Log
- 2023 Mar 17 – added link to CTP Julian Jakob Citrix NetScaler – OTP Encryption Tool.
- 2021 Feb 1 – First factor – added info from Samuel LEGRAND Native OTP issues on Citrix ADC 13
- 2020 Apr 12 – Overview – added link to Andreas Nick OTPEdit: tool to register OTP devices without using manageotp
- 2019 Sep 27 – OTP Encryption – new in ADC 13.0 build 41
- New OTP features in ADC 13:
Overview
Citrix ADC 13 Native OTP lets you enable two-factor authentication without purchasing any other authentication product. A typical configuration uses Citrix SSO app (mobile VPN Client) to receive push notifications, or Google Authenticator to generate Passcodes. See the following for an overview:
- Citrix Blog Post NetScaler Unified Gateway Provides One Time Password (OTP), Natively
- Citrix CTX228454 NetScaler One Time Password (OTP) Guide for Dual Authentication or Registration
Here are some notes and requirements for Native OTP:
- Licensing – Citrix ADC Native OTP is part of nFactor, and thus requires Citrix ADC Advanced Edition or Citrix ADC Premium Edition licensing. Citrix ADC Standard Edition licensing is not sufficient.
- OTP Push Notifications require ADC Premium Edition
- Workspace app 1809 and newer with Citrix Gateway 12.1 build 49 and newer support nFactor authentication. Older Receivers and older NetScalers don’t support nFactor with Receiver, so you’ll instead have to use a web browser.

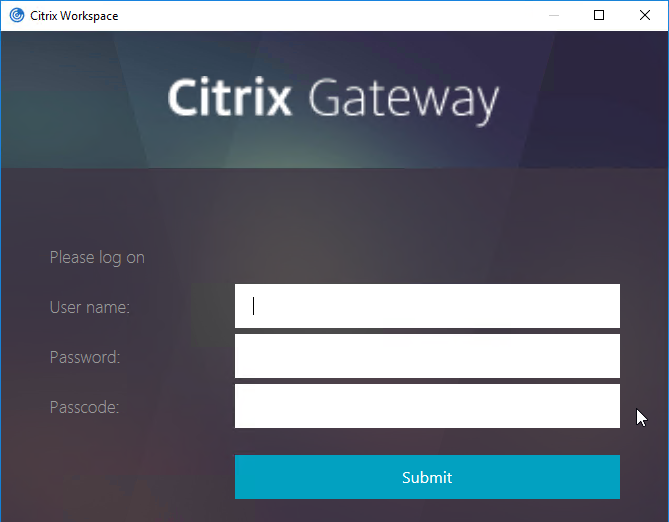
- Citrix Gateway VPN Plug-in 12.1 build 49 and later support nFactor when authenticating from the VPN Plug-in.

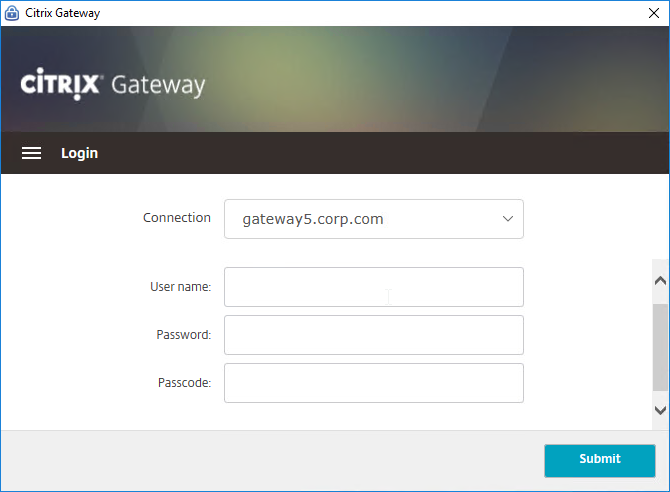
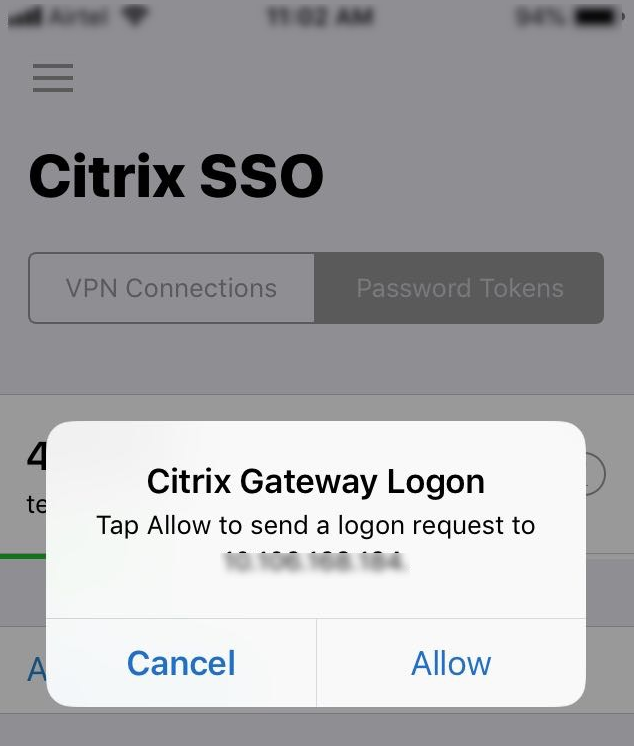
- Push notifications – Citrix ADC 13 and newer supports OTP push notifications of logon request to the mobile (iOS, Android) Citrix SSO app. Other authenticator apps are not supported for OTP Push, but they can be used with OTP Passcode.
- Authenticator – If not using Citrix SSO app, then Google Authenticator can generate passcodes. Christian in the comments indicated that Microsoft Authenticator also works. Click on plus sign -> other (Google,…).
- Internet for Push – Push notifications requires the Citrix ADC appliance to be able to send API calls across the Internet to Citrix Cloud.
- Active Directory attribute – Citrix ADC stores OTP device enrollment secrets in an string-based Active Directory attribute. Citrix’s documentation uses the userParameters Active Directory attribute.
- The LDAP bind account must have permission to modify this attribute on every user.
- The userParameters attribute must not be populated. Active Directory Users & Computers might set the userParameters attribute if you modify any of the RDS property pages.
- Enroll multiple devices – Citrix ADC 13 and newer lets you control the number of devices that a user can enroll.
- Manageotp is difficult to secure – The manageotp website is usually only protected by single factor authentication so external access must be blocked.
- Andreas Nick OTPEdit is an out-of-band tool to register OTP devices without using manageotp.
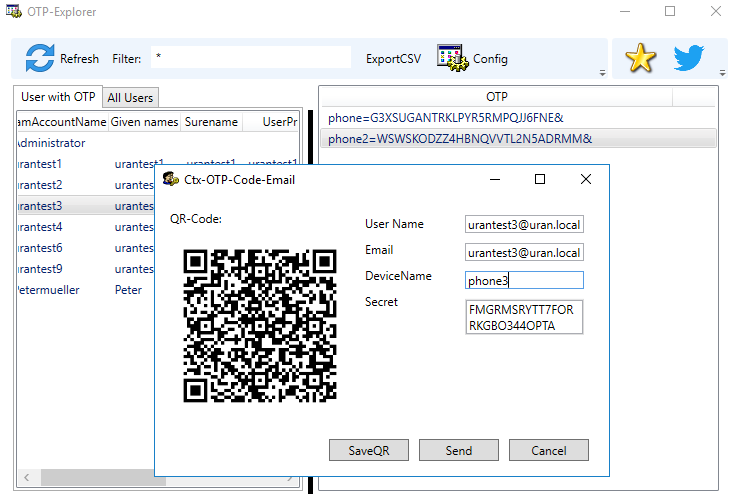
- Andreas Nick OTPEdit is an out-of-band tool to register OTP devices without using manageotp.
Notes on Citrix ADC Configuration Objects for OTP
Here are some notes on the Citrix ADC OTP configuration objects. Detailed instructions are provided later.
- Make sure NTP is configured on the Citrix ADC. Accurate time is required.
- AAA vServer – nFactor requires a AAA vServer, which can be non-addressable. You don’t need any additional public IP for OTP.
- An Authentication Profile links the AAA vServer to the Citrix Gateway vServer.
- Citrix Cloud – For Push notifications, create a Citrix Cloud account. No Citrix Cloud licensing needed. Citrix ADC uses Cloud API credentials to authenticate with Citrix Cloud.
- NSC_TASS cookie – To access the manageotp web page, users add /manageotp to the end of the Gateway URL. Citrix ADC puts this URL path into a cookie called NSC_TASS. You can use this cookie and its value in policy expressions for determining which Login Schema is shown to the user.
- Login Schema for manageotp – The built-in Login Schema file named SingleAuthManageOTP.xml has hidden fields that enable the manageotp web page. If the Login Schema Policy expression permits the SingleAuthManageOTP.xml Login Schema to be shown to the user, then after authentication the user will be taken to the manageotp web page.
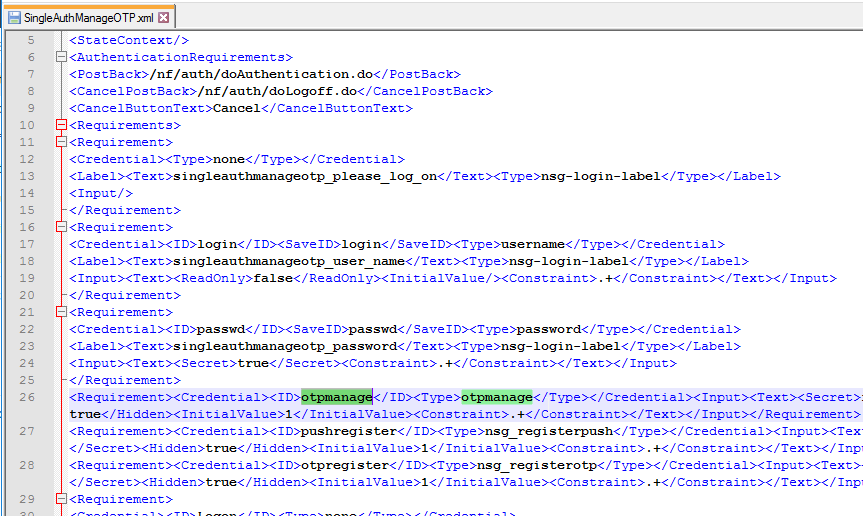
- LDAP authentication is expected to be bound to the same factor as this SingleAuthManageOTP login schema.
- The next factor is a LDAP Policy/Server with authentication disabled (unchecked) but with arguments specifying the Active Directory attribute for the OTP Secret and Push Service configuration.
- Login Schema for OTP authentication – The built-in Login Schema file named DualAuthPushOrOTP.xml performs the two-factor authentication utilizing the push service. There’s a checkbox that lets users choose Passcode instead of Push. This login schema has a Credential called otppush.
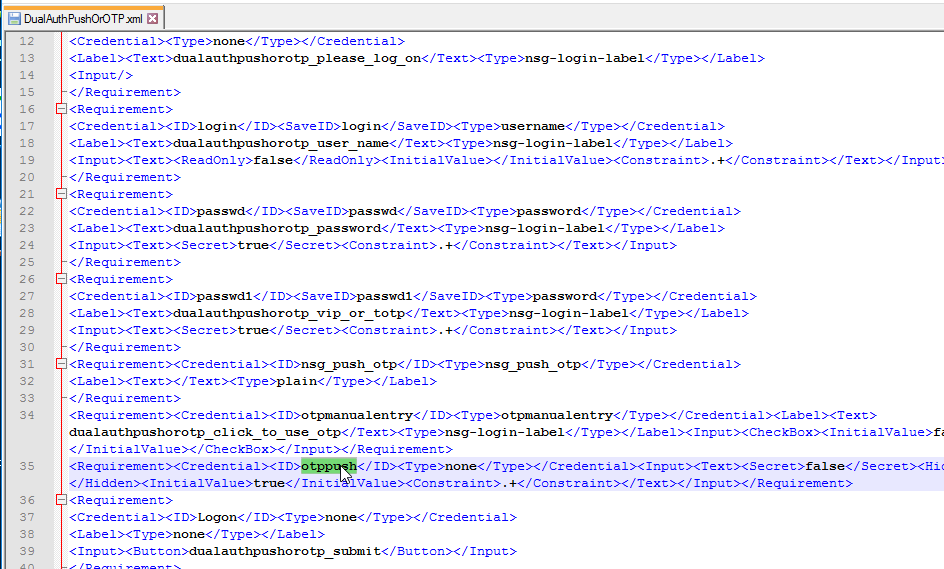
- If you prefer to not use Push, then you can use a normal DualAuth.xml Login Schema file since for passcode authentication there are no special Login Schema requirements other than collecting two password fields.
- Both methods expect an authenticating LDAP Policy/Server to be bound to the same Factor as the Login Schema.
- The next factor should be a non-authenticating LDAP Policy/Server that optionally has the the Push Service defined and must have the OTP Secret attribute defined.
- Single Sign-on to StoreFront – The OTP dual authentication Login Schema essentially collects two passwords (AD password plus push, or AD password plus passcode). Later, Citrix Gateway needs to use the AD password to perform Single Sign-on to StoreFront. To ensure the AD password is used instead of the OTP passcode, configure the OTP dual authentication Login Schema to store the AD password in a AAA attribute and then use a Citrix Gateway Traffic Policy/Profile to utilize the AAA attribute during Single Sign-on to StoreFront.
- nFactor Visualizer – Citrix ADC 13 has a nFactor Visualizer to simplify the OTP configuration. Or you can manually create the LDAP Policies/Actions, the Login Schema Policies/Profiles, the PolicyLabels, and then bind them to a AAA vServer.
OTP Encryption
ADC 13.0 build 41 and newer let you encrypt the OTP secrets stored in Active Directory.
ADC uses a certificate to encrypt the contents of the Attribute. It currently is not possible to configure the certificate from the GUI, so you’ll need to SSH to the ADC and run the following command:
bind vpn global -userDataEncryptionKey MyCertificate
![]()
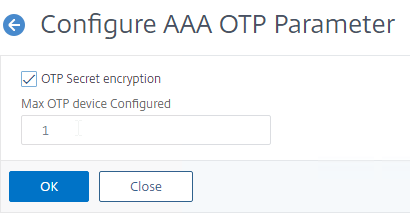
To enable OTP attribute encryption:
- In the ADC menu, go to Security > AAA – Application Traffic.
- On the right, click Change authentication AAA OTP Parameter.

- Check the box for OTP Secret encryption and then click OK.
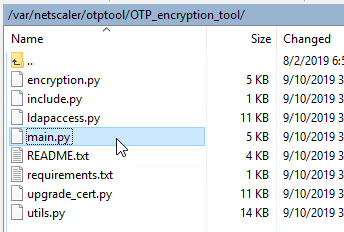
- If you have a previous implementation of ADC OTP that stored unencrypted OTP secrets, then use the Python OTP encryption tool at
/var/netscaler/otptool/OTP_encryption_toolto encrypt the AD attribute using the userDataEncryptionKey certificate. The same tool can be used to change the encryption certificate. More details at OTP encryption tool at Citrix Docs. Also see CTP Julian Jakob Citrix NetScaler – OTP Encryption Tool.
AAA Virtual Server
Create a AAA vServer that is the anchor point for our OTP nFactor configuration.
- Make sure the time is correct on the NetScaler. Click the Configuration tab to see the current System Time. Make sure NTP is configured at System > NTP Servers.
- Go to Security > AAA – Application Traffic.
- If the AAA feature is not enabled, then right-click the AAA node, and click Enable Feature.
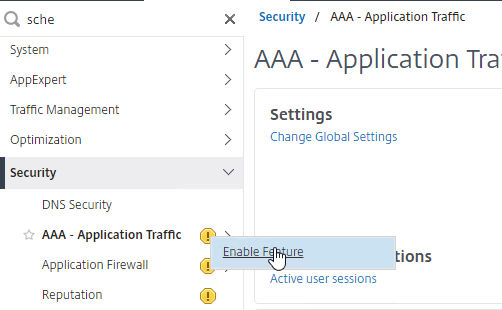
- Go to Security > AAA – Application Traffic > Virtual Servers.
- On the right, click Add.
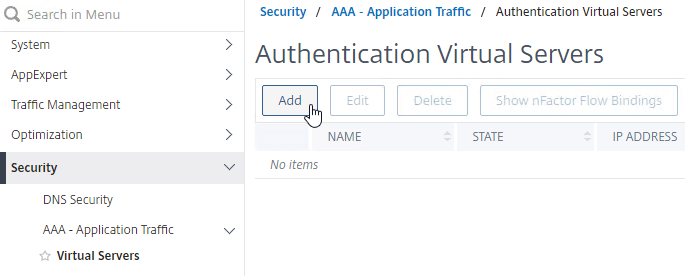
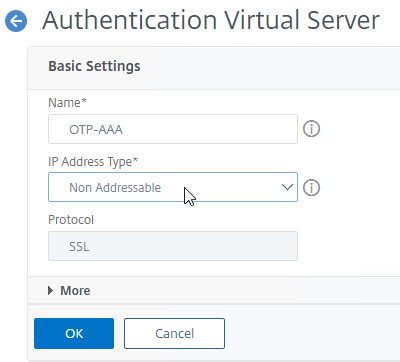
- This AAA vServer is for OTP so name it accordingly.
- Change the IP Address Type to Non Addressable. You don’t need to specify any additional IP address.
- Click the blue OK button.
- Click where it says No Server Certificate.
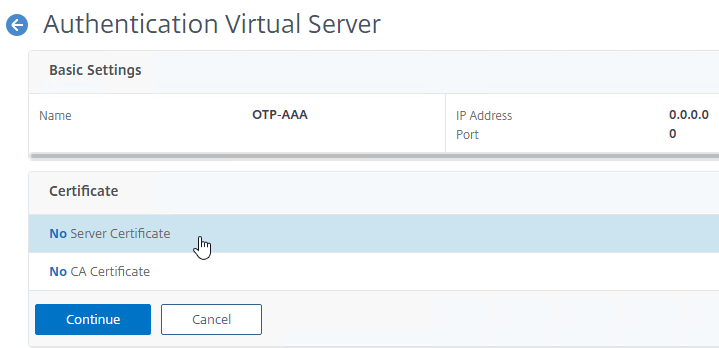
- In the Server Certificate Binding section, click Click to select.
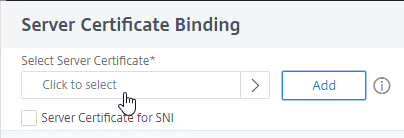
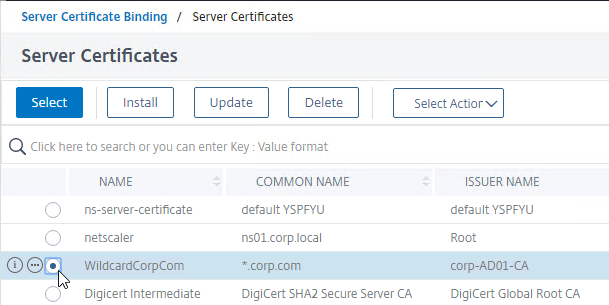
- Click the radio button next to a certificate, and then click the blue Select button at the top of the page. You can select the same certificate as the Citrix Gateway Virtual Server.
- Click Bind.
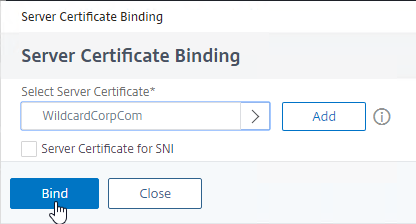
- In the Server Certificate Binding section, click Click to select.
- Click Continue to close the Certificate section.
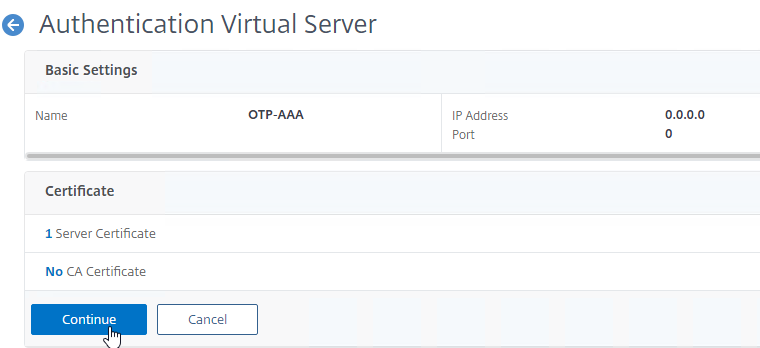
- In the Advanced Authentication Policies section, don’t bind anything and just click Continue. We’ll bind a nFactor Flow later.
- You can optionally improve the SSL ciphers on this AAA Virtual Server but it’s probably not necessary since this AAA vServer is not directly addressable.
- Nothing else is needed at this time so click the blue back arrow on the top left.
Push Service
If your Citrix ADC has Internet access, then you can enable OTP Push Authentication. The ADC must be able to reach the following FQDNs:
- mfa.cloud.com
- trust.citrixworkspacesapi.net
Create an API Client at citrix.cloud.com:
- Go to https://citrix.cloud.com and login. Your cloud account does not need any licensed services.
- On the top left, click the hamburger (menu) icon, and then click Identity and Access Management.
- Switch to the tab named API Access.
- On this page, notice the Customer ID. You’ll need this value later.
- Enter a name for a new API client and then click Create Client
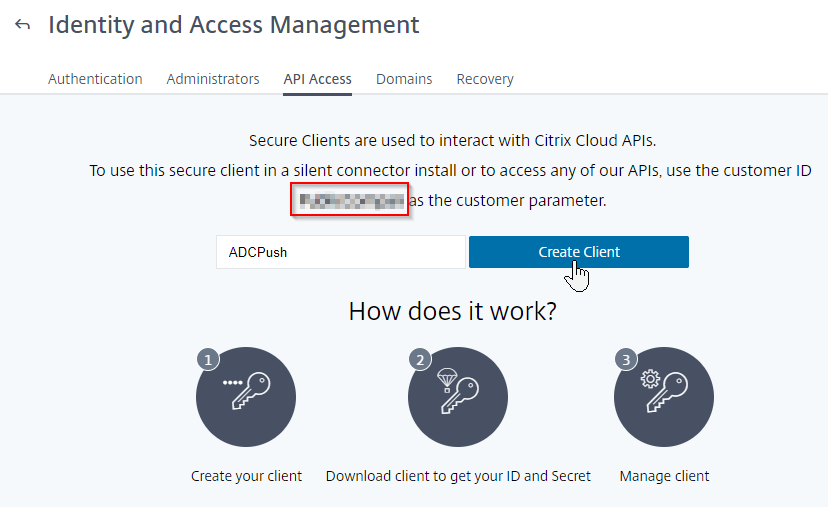
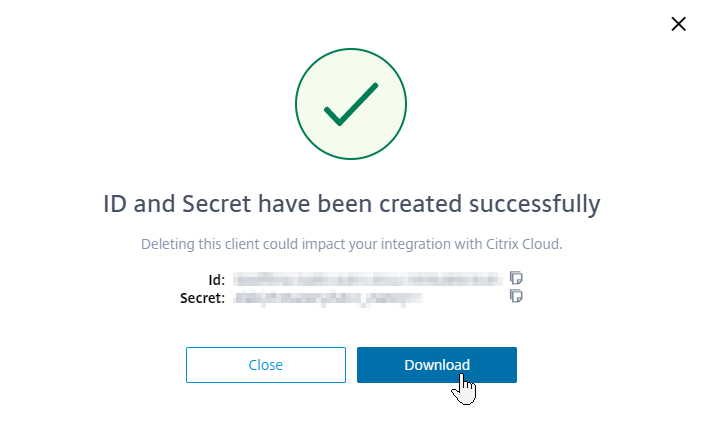
- Click Download to download the client credentials.
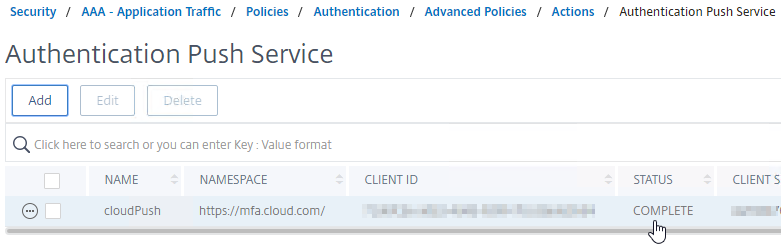
On ADC 13, create the Push Service:
- In Citrix ADC 13 management GUI, navigate to the Push Service node. The easiest way to find it is to enter Push in the search box on the top left.
- On the right, click Add.
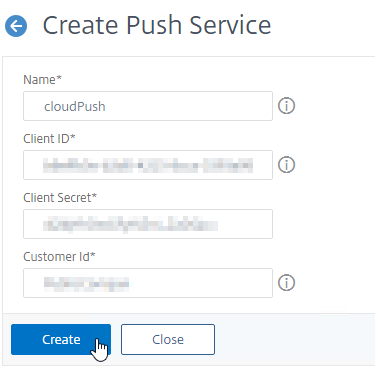
- In the Create Push Service page, do the following:
- Enter a name for the Push Service.
- Enter the Client ID and Client Secret that you downloaded when creating your API Client.
- Enter the Customer ID shown on the Create Client web page at cloud.com. Make sure there are no hidden characters or whitespace around the Customer ID.
- Click Create.
- On the top right, click the refresh icon until the Status changes to COMPLETE. If it won’t go past CCTOKEN, then make sure you entered the API Client info correctly, especially the Customer ID, which might have hidden characters around it.
LDAP Actions/Servers
Create three LDAP Actions (aka LDAP Servers):
- One LDAP Action for normal LDAP authentication against Active Directory
- One LDAP Action to set the OTP Active Directory attribute and register with push
- One LDAP Action to perform push authentication (in a dual-authentication flow)
Create normal LDAP Action
- Go to Security > AAA – Application Traffic > Policies > Authentication > Advanced Policies > Actions > LDAP.
- On the right, click Add.
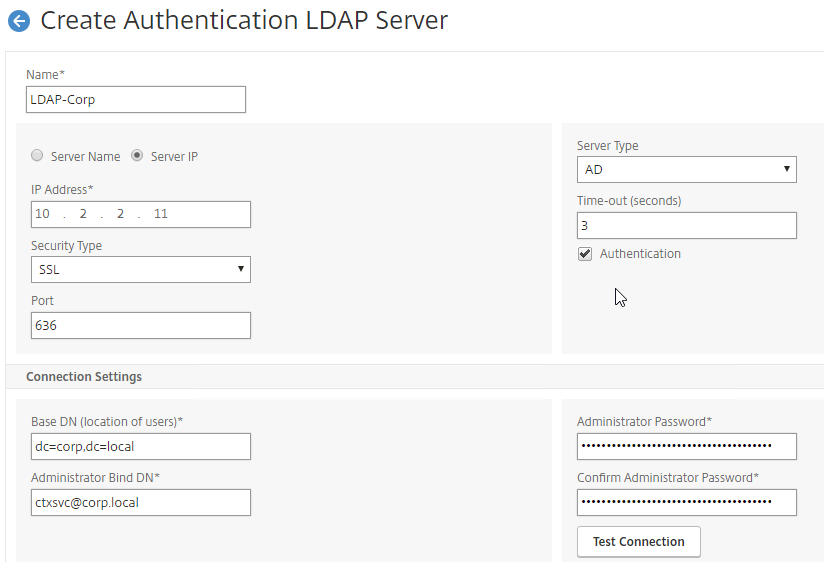
- Create a normal LDAP Server if you don’t have one already. This one has Authentication enabled. There are no special instructions for this LDAP Server.
Create LDAP Action for OTP Device Registration
Create the LDAP Action for OTP device registration that sets the OTP Active Directory attribute and registers with push:
- Create another LDAP Action.
- Name it according to this goal: used by the manageotp web site to set the OTP authenticator in Active Directory.
- On the right, uncheck the box next to Authentication.
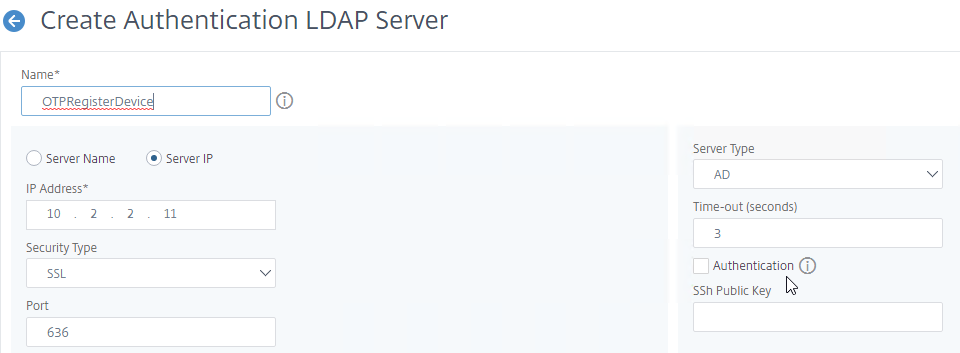
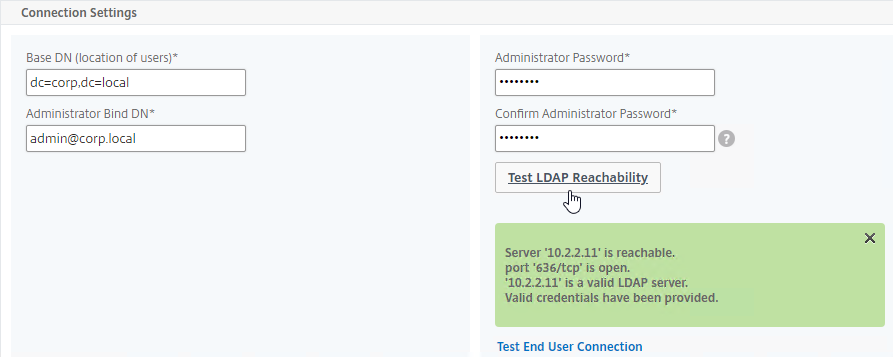
- Make sure the Administrator Bind DN has permissions to modify the OTP Secret Active Directory attribute for all users. A regular non-admin LDAP Bind account won’t work.
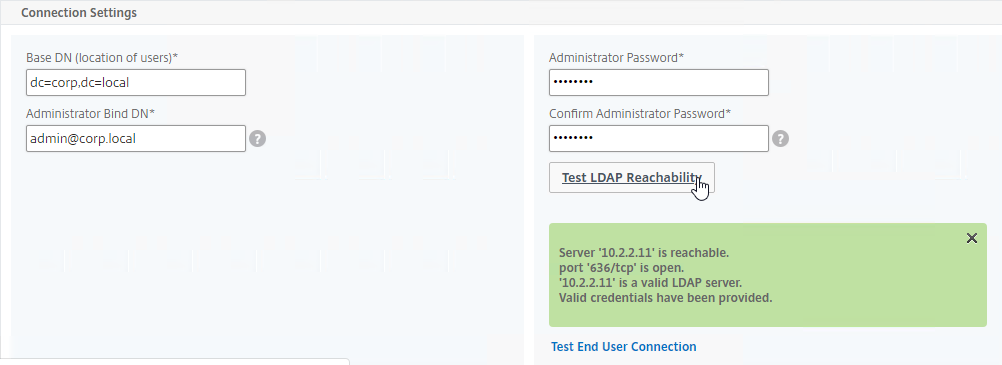
- If you cloned an existing LDAP Server, then make sure you re-enter the Administrator Password or the new LDAP Action won’t work.
- Click Test LDAP Reachability.
- Configure the Server Logon Name Attribute to match the one you configured in the normal authentication LDAP Server.
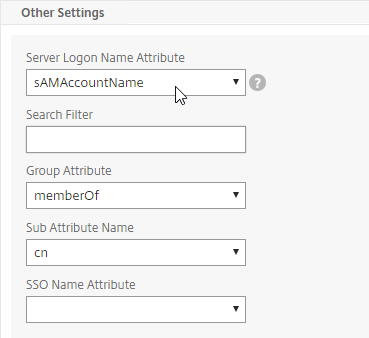
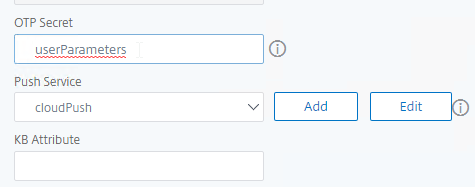
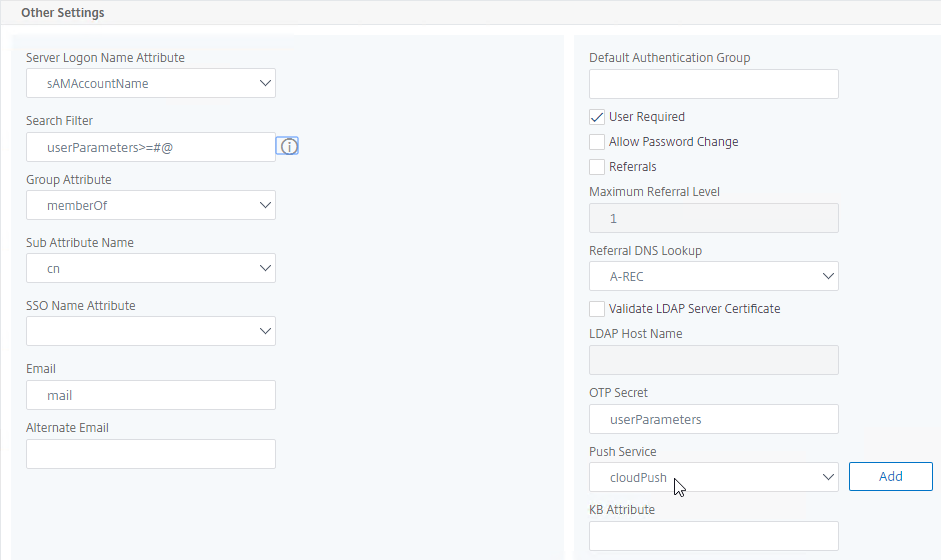
- In the Other Settings section, on the bottom right, find the OTP Secret field. Enter the name of the Active Directory attribute where Citrix ADC will store the user’s OTP secret. You can use the userParameters attribute if that attribute isn’t being used for anything else.
- userParameters is populated by Active Directory Users & Computers if you set anything on the RDS tabs (e.g. RDS Roaming Profile).
- Select the Push Service that you created earlier.
- Click Create when done.
Create LDAP Action for OTP Authentication
Create a LDAP Action that performs OTP push authentication or verifies the OTP Passcode. The only difference from the prior LDAP Action is the addition of an LDAP Search Filter.
- Create another LDAP Action.
- Give the LDAP Action a name.
- On the right, uncheck the box next to Authentication.
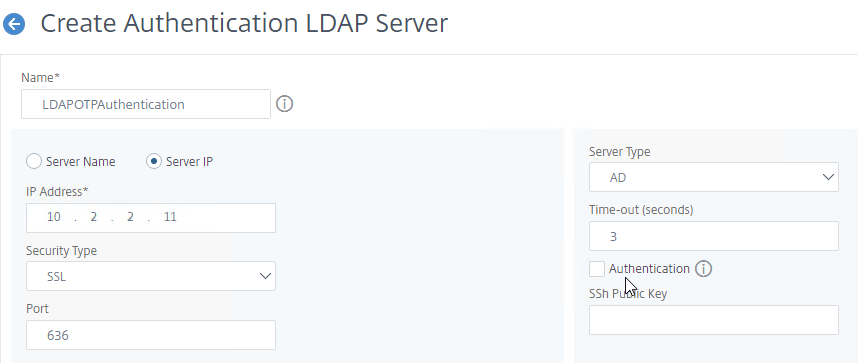
- Make sure the Administrator Bind DN has permissions to read the OTP Secret Active Directory attribute.
- If you cloned an existing LDAP Server, then make sure you re-enter the Administrator Password or the new LDAP Action won’t work.
- Click Test LDAP Reachability.
- In the Other Settings section, configure the Server Logon Name Attribute to match the one you configured in the normal authentication LDAP Server.
- In the Search Filter field, enter the text userParameters>=#@. This syntax ensures that only users with enrolled authenticators can login. See George Spiers NetScaler native OTP for more info.
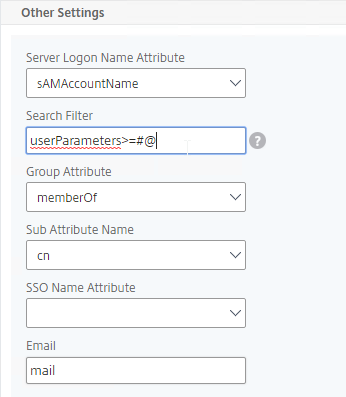
- In the Other Settings section, on the bottom right, find the OTP Secret field. Enter the name of the Active Directory attribute containing the user’s OTP secret.
- In the Push Service drop-down, select the Push Service that you already created.
- Click Create when done.
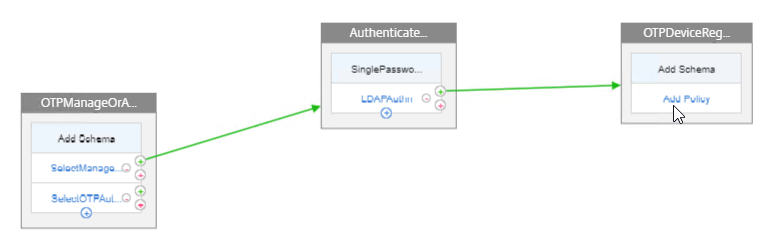
nFactor Visualizer
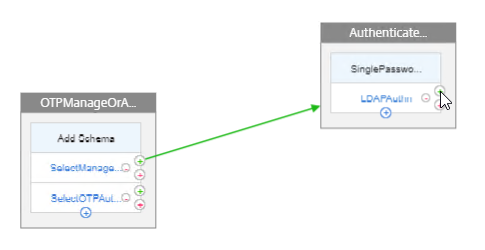
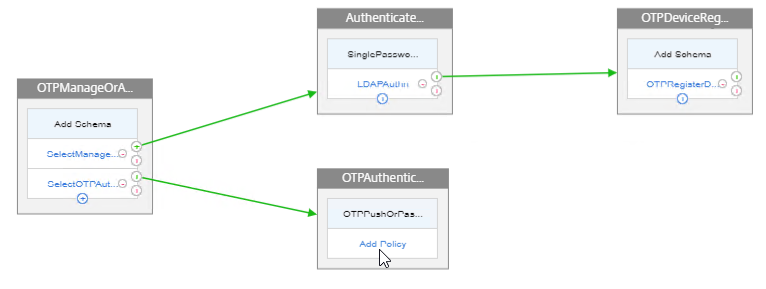
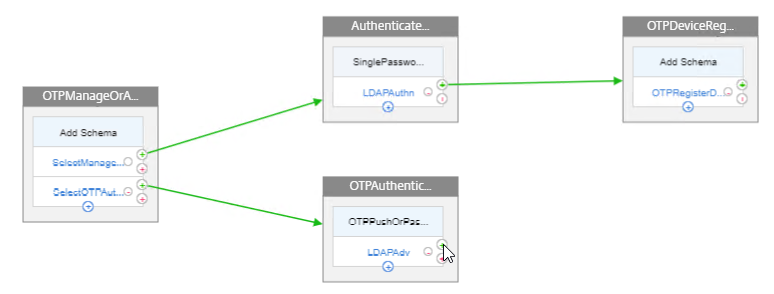
We will build a nFactor Flow that looks something like this:
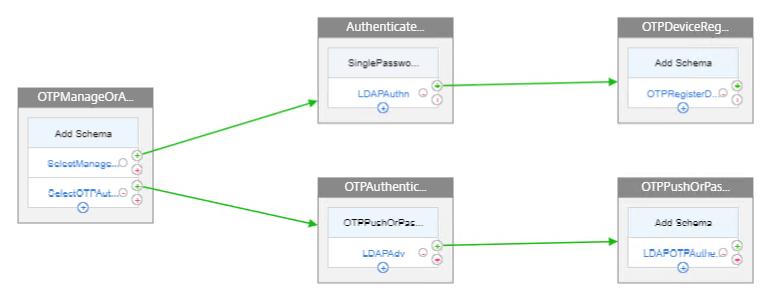
- First factor on the left chooses either OTP Device Registration or OTP Authentication. If user enters /manageotp, then nFactor Flow takes the top path. Otherwise, nFactor flow takes the bottom path.
- Login Schema is not needed for the first factor.
- Second factor for Manage OTP = Login Schema with Manage OTP flag and normal LDAP authentication before allowing users to add devices.
- Third factor is just an LDAP Policy configured with the OTP Active Directory attribute and Push Service. No Login Schema needed.
- Second factor for OTP Authentication = Login Schema with OTP Push (or OTP Passcode) and normal LDAP authentication.
- Third factor is just an LDAP Policy with the OTP Active Directory attribute and Push Service. No Login Schema needed.
nFactor Visualizer notes:
- nFactor Visualizer is not required. You can instead follow the older manual ADC 12.1 instructions.
- It doesn’t seem to be possible to rename any part of the flow once it’s created. To rename, you basically remove the entire flow and rebuild it.
- nFactor Visualizer does not support policy expressions for Login Schemas so the older ADC 12.1 instructions must be modified to support two different branches.
Create Flow and first factor that selects Manage or selects Authenticate
- In ADC 13, go to Security > AAA – Application Traffic > nFactor Visualizer > nFactor Flows. Or search the menu for nFactor.
- On the right, click Add.
- Click the blue plus icon to create a factor.
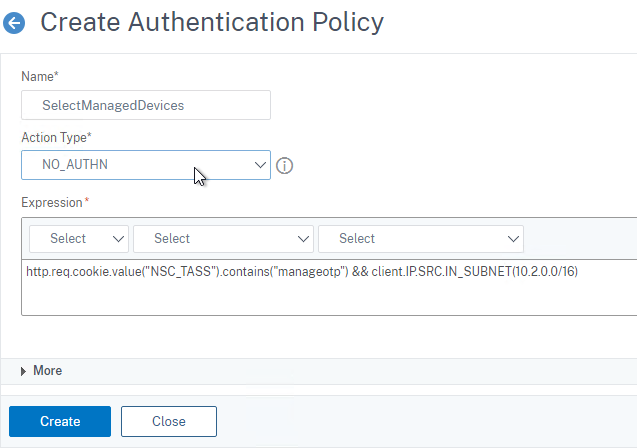
- Name the factor based on this goal: choose manageotp or authenticate based on whether the user entered /manageotp or not. The name of the first factor is also the name of the nFactor Flow.
- Click the blue Create button.
- The first factor does not need a Schema.
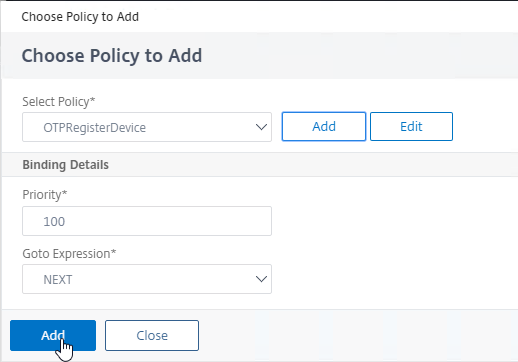
- In the first factor, click where it says Add Policy.

- In the Choose Policy to Add page, click Add to create an authentication policy.
- Name this policy according to this goal: if this policy’s expression is true, then select the manageotp branch (instead of OTP authentication).
- For the Action Type drop-down, select NO_AUTHN. This policy is merely a decision point for the next factor so no actual authentication will occur at this time. The next factor is configured later.
- In the Expression box, enter something similar to the following. The IP subnet expression restricts the manageotp web page to only internal users.
http.req.cookie.value("NSC_TASS").eq("manageotp") && client.IP.SRC.IN_SUBNET(10.2.0.0/16) - In newer ADC 13, you might have to change the expression to eq /manageotp, or change it to contains manageotp. (source = Samuel LEGRAND Native OTP issues on Citrix ADC 13) 💡
http.req.cookie.value("NSC_TASS").eq("/manageotp") && client.IP.SRC.IN_SUBNET(10.2.0.0/16) http.req.cookie.value("NSC_TASS").contains("manageotp") && client.IP.SRC.IN_SUBNET(10.2.0.0/16) - Then click the blue Create button.
- Click the blue Add button to bind this policy to the factor.
- In the first factor, below the policy you just added, click the blue plus arrow to create another policy.
- In the Choose Policy to Add page, click Add to create another policy.
- Name the policy according to this goal: select the dual factor OTP authentication branch.
- For the Action Type drop-down, select NO_AUTHN. This is a decision point policy without authentication that leads to the next factor that does the actual authentication.
- In the Expression box, enter true to capture all OTP users that did not match the prior manageotp policy.
- Click the blue Create button.
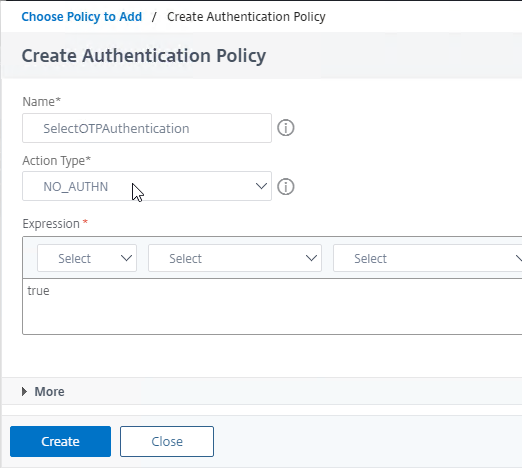
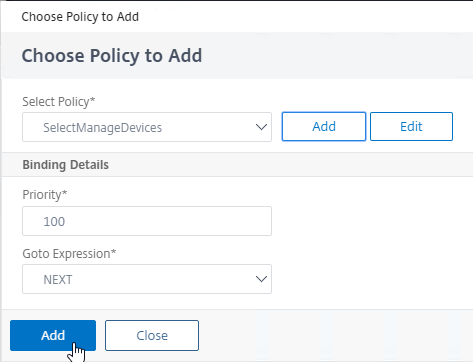
- Click Add to bind this policy to the first factor but after (higher priority number) than the manageotp policy.
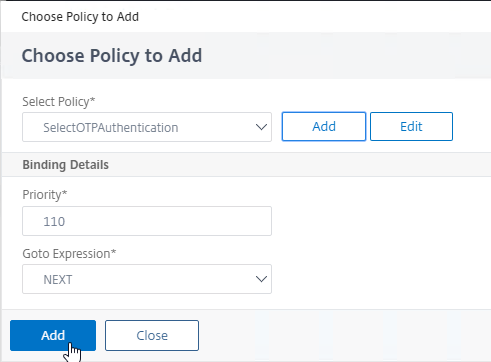
Create second factor for manageotp
- In the first factor, click the green plus icon to the right of the “SelectManageOTP” policy. If the “SelectManageOTP” policy is true, then this new factor will be evaluated.
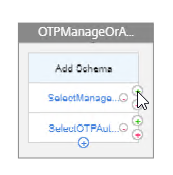
- Name this factor according to this goal: perform single-factor LDAP authentication before allowing access to the manageotp web page.
- Then click the blue Create button.
- In the second factor, click where it says Add Schema.
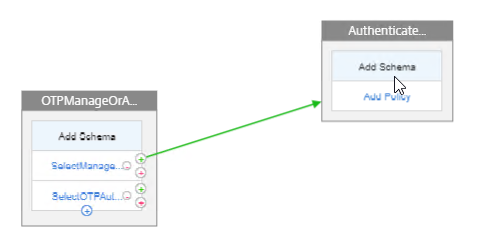
- In the Choose Schema page, click Add to create a Login Schema.
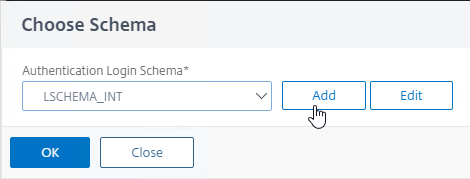
- Name the Login Schema according to this goal: ask user for one password that will be verified with LDAP (Active Directory) before showing the manageotp web page.
- In the Authentication Schema field, click the pencil icon.
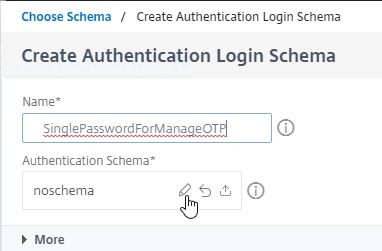
- The existing window expands to show the Login Schema Files. On the left, click the LoginSchema folder to see the files in that folder.
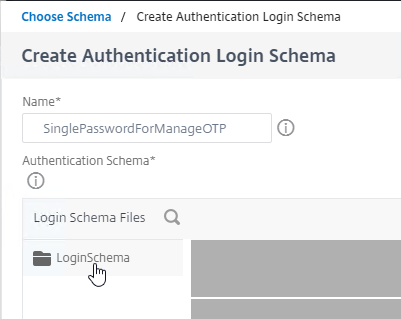
- In the list of files, click SingleAuthManageOTP.xml. This login schema asks for one password and has the special hidden credential to enable the manageotp web page.
- To actually select this file, on the top right, click the blue Select button. The Login Schema window will then collapse so that Login Schema Files are no longer shown.
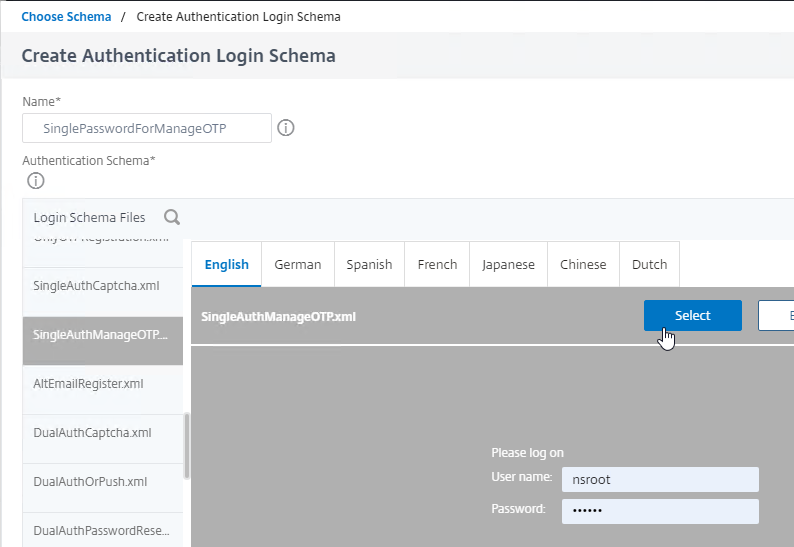
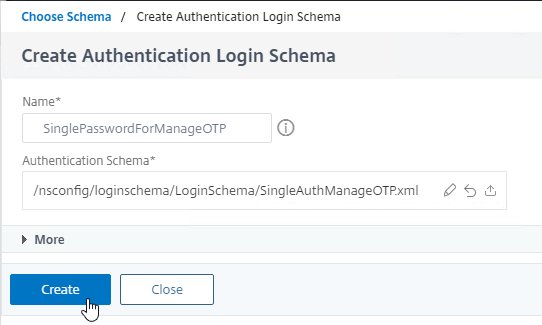
- Make sure the Authentication Schema field shows the Login Schema file that you selected.
- Then click the blue Create button.
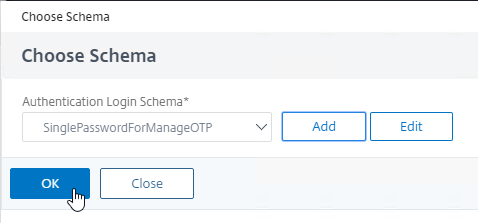
- Click OK to bind the Schema to the factor.
- In the second factor, below the Schema, click Add Policy.
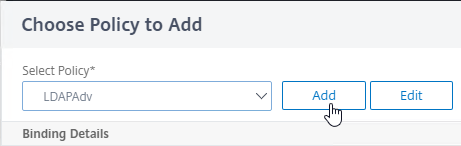
- In the Choose Policy to Add page, if you already have a normal Advanced Expression LDAP policy, then select it.
- Otherwise, click Add to create one.
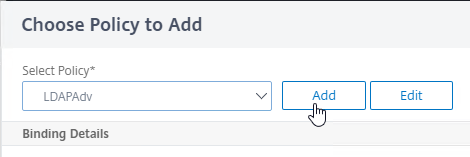
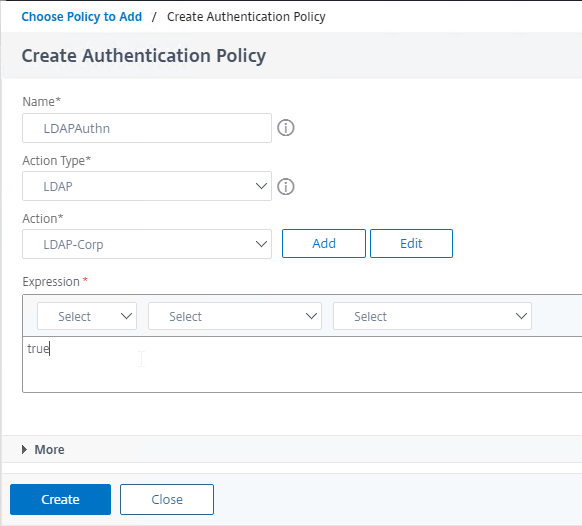
- Name this policy according to this goal: perform normal LDAP authentication against an Active Directory domain.
- In the Action Type drop-down, select LDAP.
- In the Action drop-down, select the LDAP Action/Server you created earlier that performs normal authentication.
- In the Expression box, enter true, which is an Advanced Expression.
- Click the blue Create button.
- Click Add to bind this LDAP Policy to the factor.
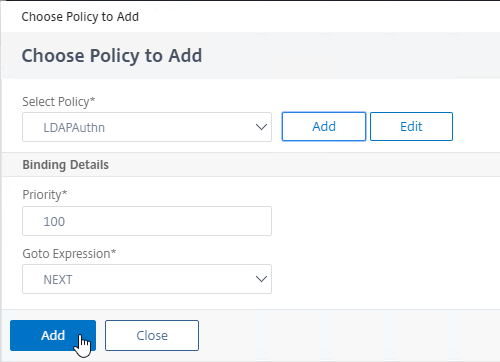
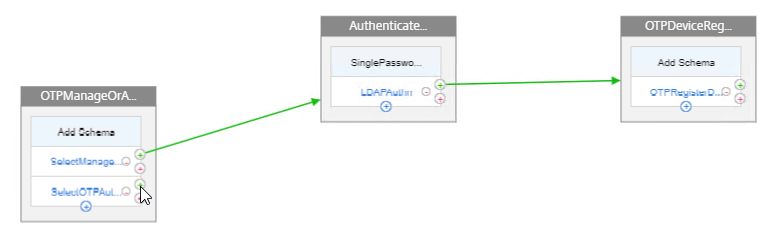
Create third factor that registers an OTP device with Active Directory and Push
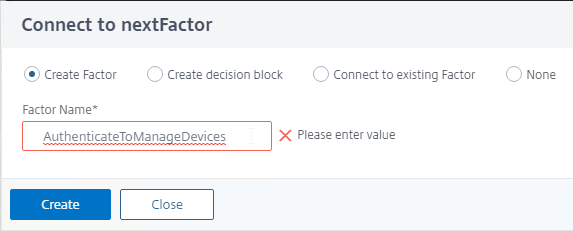
- In the second factor, click the green plus icon to create another factor. This new factor is only evaluated if the LDAP Policy is successful.
- Name the factor according to this goal: register the device with Active Directory and optionally Push.
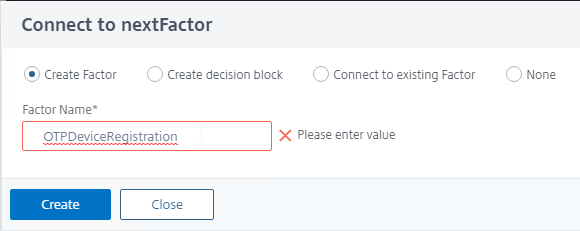
- This factor does not need any Schema.
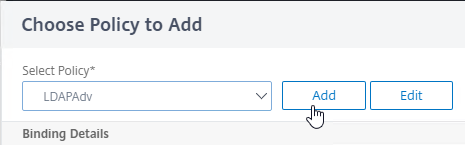
- In the third factor, click Add Policy
- In the Choose Policy to Add page, click Add to create a policy.
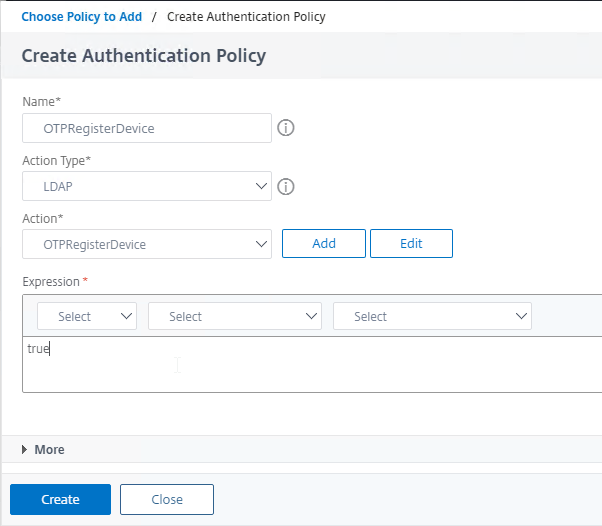
- Name the policy according to this goal: Register OTP devices using LDAP Action without authentication that has the OTP Secret Attribute specified.
- In the Action Type drop-down, select LDAP.
- In the Action drop-down, select the LDAP Action you created earlier that registers new devices. Make sure authentication is disabled in the LDAP Action, and make sure it has OTP Secret and optionally OTP Push configured.
- In the Expression field, enter true.
- Click the blue Create button.
- Click the blue Add button to bind this policy to the factor.
The Factors for manageotp are complete. Now we build the factors for authenticating using OTP.
Create a second factor for LDAP Authentication
- Go back to the first factor and click the green plus icon next to the OTP Authentication policy.
- Name the factor according to this goal: ask user for one password + push, or two passwords, and then perform LDAP authentication. OTP authentication is performed in the next factor (see below).
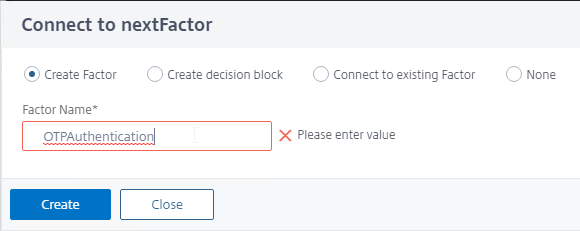
- In the second factor, click where it says Add Schema.
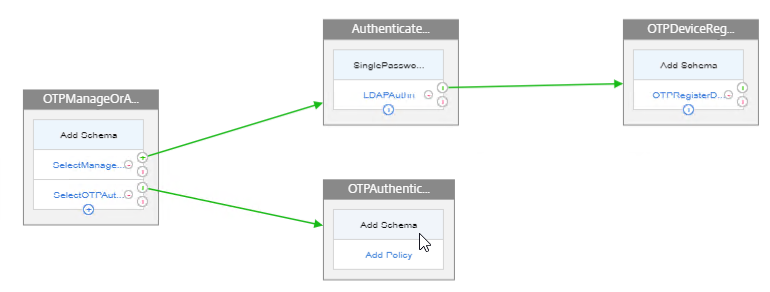
- In the Choose Schema window, click Add.
- Name the Login Schema according to this goal: ask for one password + OTP push, or ask for two passwords.
- In the Authentication Schema field, click the pencil icon.
- The window expands to show Login Schema Files. On the left, click the LoginSchema folder to see the files under it.
- On the left, click the DualAuthPushOrOTP.xml file.
- Or if you don’t want push, then click a normal two password schema like DualAuth.xml. You can modify the DualAuth.xml file to indicate to the user that the OTP Passcode is expected in the second field.
- Then on the top right click the blue Select button. This causes the Login Schema window to collapse and no longer show the Login Schema Files.
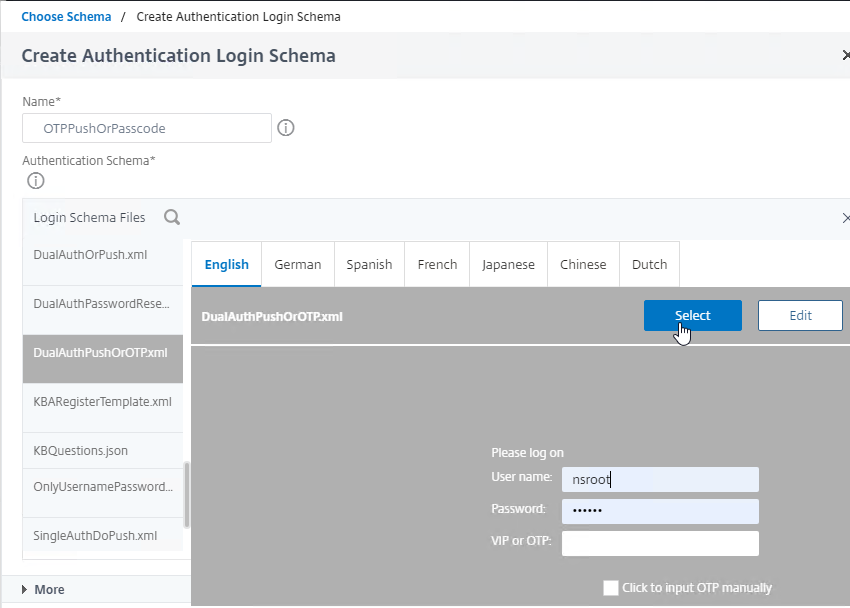
- In the Authentication Schema field, makes sure the correct file name is selected.
- Click More.
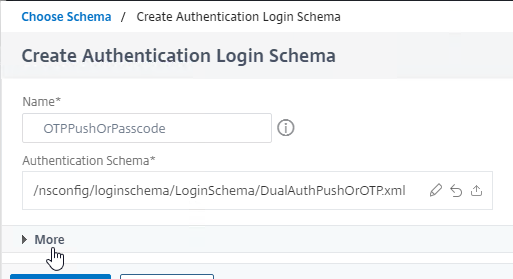
- At the bottom, in the Password Credential Index field, enter a 1 to save the first password into AAA Attribute 1, which we’ll use later in a Traffic Policy that performs Single Sign-on to StoreFront.
- Then click the blue Create button.
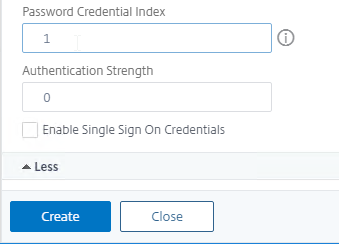
- Click OK to bind the Schema to the factor.
- In the second factor, below the schema, click where it says Add Policy.
- In the Select Policy drop-down, select your normal LDAP Active Directory authentication policy. This is the same one you used for the second factor in the manageotp branch.
- Click the blue Add button to bind this LDAP policy to the second factor.
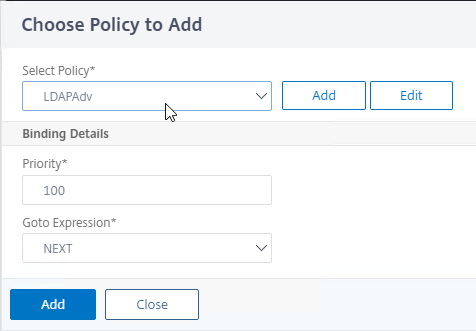
Create third factor to perform OTP authentication (Push or Passcode)
- In the second factor, click the green plus icon next to the LDAP Policy to create another factor.
- Name the factor according to this goal: perform OTP Push or Passcode authentication.
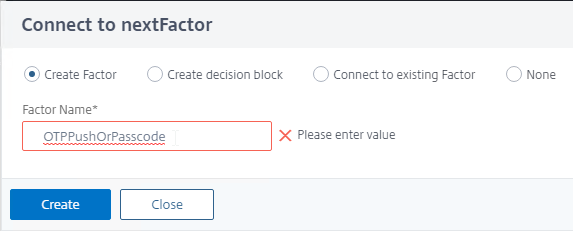
- Be aware that the nFactor Visualizer might swap your third factors.
- This third factor does not need a Login Schema.
- In the new third factor (probably the top one, follow the arrows), click where it says Add Policy.
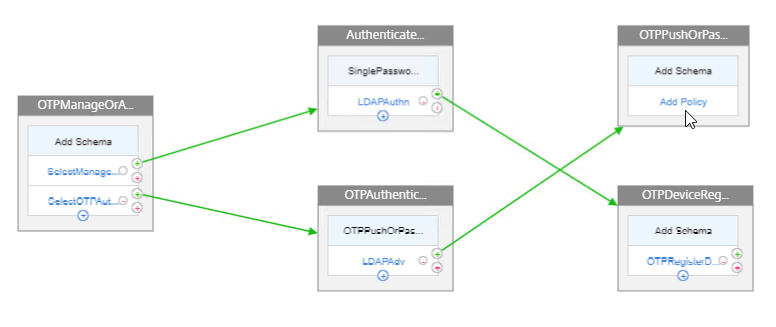
- In the Choose Policy to Add page, click Add to create a policy.
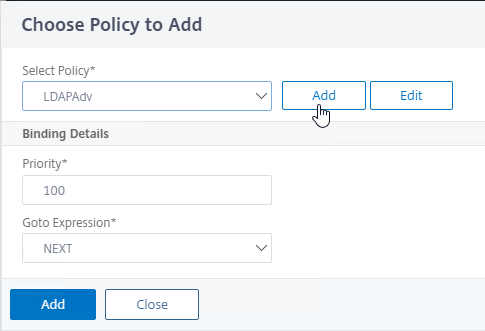
- Name this policy according to this goal: perform OTP Push or OTP Passcode authentication.
- In the Action Type drop-down, select LDAP.
- In the Action drop-down, select the LDAP action you created earlier that verifies the OTP push or passcode. This is the Action that has the LDAP Filter configured.
- In the Expression box, enter true.
- Click the blue Create button.
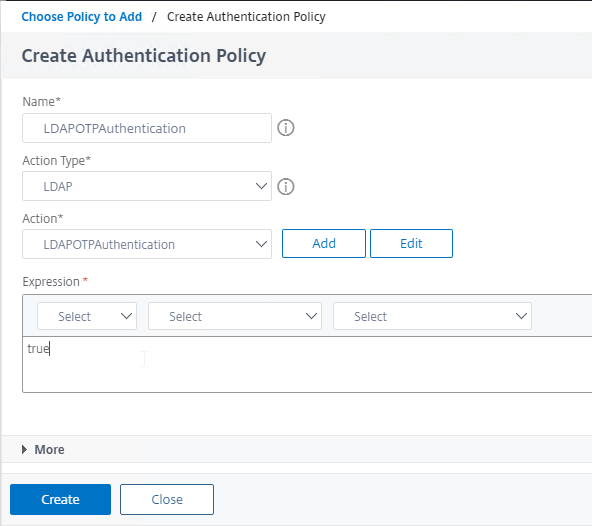
- Click the blue Add button to bind this policy to the third factor.
- Click the blue Done button to close the Flow.

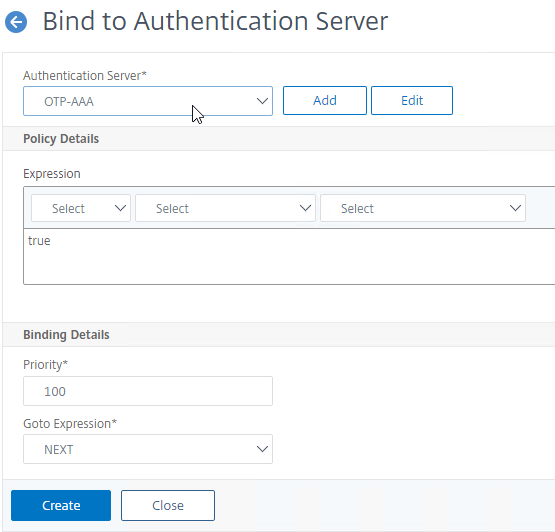
Bind nFactor Flow to AAA Virtual Server
- In the nFactor Flows menu node, highlight the nFactor Flow and click the button labelled Bind to Authentication Server.
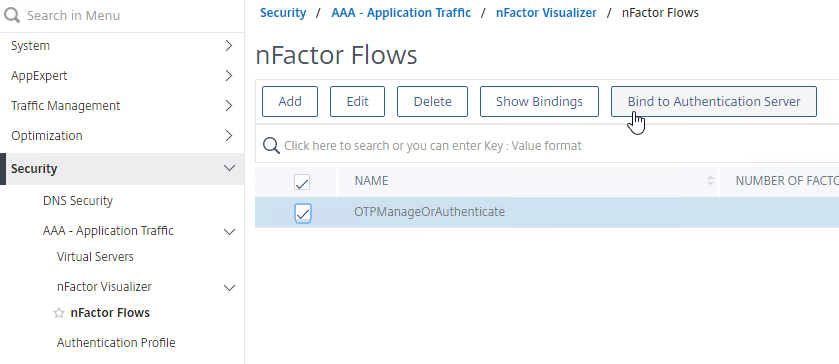
- In the Authentication Server drop-down, select the AAA vServer you created earlier.
- Everything else should already be filled in so just click the blue Create button.
Maximum Number of Registered OTP Devices
ADC 13 lets you restrict the number of OTP devices each user can register:
- In the ADC menu, go to Security > AAA – Application Traffic.
- On the right, click Change authentication AAA OTP Parameter.

- Enter the number of devices each user can register and then click OK.

- When the user attempts to register more than the max number of devices, the error message is not user friendly.

- But you can see the actual error by grepping /var/log/ns.log for otp. which might show <Max permitted otp devices reached>.

Traffic Policy for Single Sign-on to StoreFront
Create Traffic Profile
- On the left, go to Citrix Gateway > Policies > Traffic.
- On the right, switch to the tab named Traffic Profiles, and click Add.
- Name the Traffic Profile according to this goal: use the AAA attribute 1 as password when doing Single Sign-on to StoreFront.
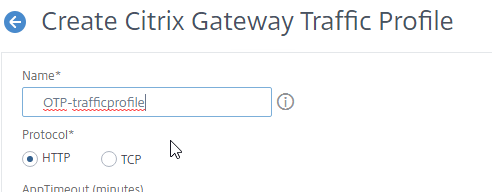
- Scroll down.
- In the SSO Password Expression box, enter the following which uses the Login Schema Password Attribute specified earlier.
AAA.USER.ATTRIBUTE(1)
- Click the blue Create button.
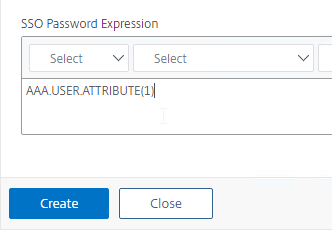
Create Traffic Policy
- On the right, switch to the tab named Traffic Policies, and click Add.
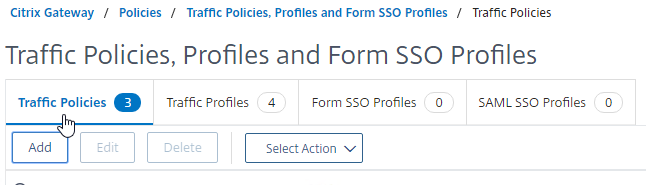
- In the Request Profile field, select the Traffic Profile you just created.
- Name the Traffic Policy.
- In the Expression box, enter true (Advanced Syntax).
- If your Citrix Gateway Virtual Server allows full VPN, change the expression to the following. Source = Julien Mooren at NetScaler – Native OTP is breaking SSL VPN.
http.req.method.eq(post)||http.req.method.eq(get) && false
- If your Citrix Gateway Virtual Server allows full VPN, change the expression to the following. Source = Julien Mooren at NetScaler – Native OTP is breaking SSL VPN.
- Click the blue Create button.
Citrix Gateway, Traffic Policy, and Authentication Profile

Edit an existing Citrix Gateway Virtual Server
- Go to Citrix Gateway > Virtual Servers.
- Edit an existing Gateway vServer. If you don’t have one, see the other Citrix Gateway topics on this site.
Bind the Traffic Policy
- While editing a Gateway Virtual Server, scroll down to the Policies section, and click the plus icon.
- Change the Choose Policy drop-down to Traffic, and then click the blue Continue button.
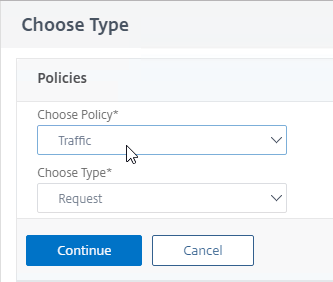
- In the Policy Binding section, click Click to select.
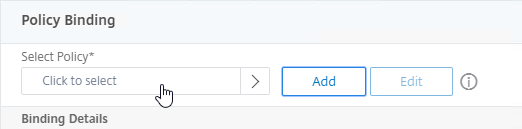
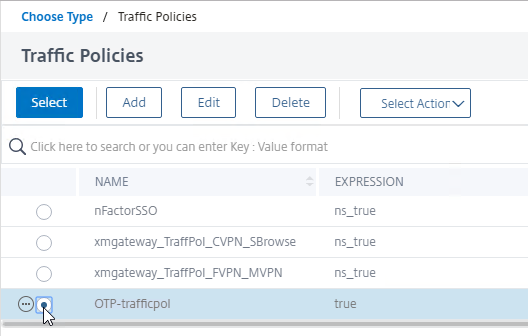
- Click the radio button next to the Traffic Policy you created earlier, and then click the blue Select button at the top of the page.
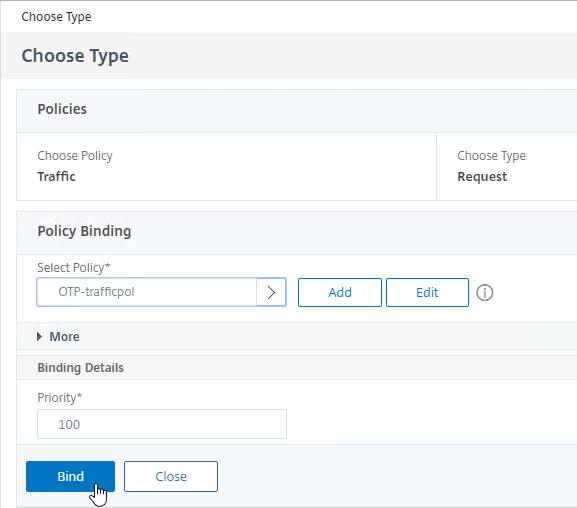
- Click the blue Bind button.
Create Authentication Profile
Create and bind an Authentication Profile to link the Gateway Virtual Server to the AAA Virtual Server:
- While editing a Gateway Virtual Server, on the right, in the Advanced Settings column, click Authentication Profile.
- On the left, scroll down to the Authentication Profile section.
- Click Add to create one.
- Authentication Profile links the Citrix Gateway vServer with the OTP AAA vServer, so name it accordingly.
- In the Authentication Virtual Server section, click Click to select.
- Click the radio button next to the OTP AAA vServer, and then click the blue Select button at the top of the page.
- Click the blue Create button.
- Scroll down again to the Authentication Profile section, and click the blue OK button. Your selection isn’t saved until you click OK.
- The Portal Theme bound to the Gateway Virtual Server should be X1, RfWebUI, or a derivative.
Update Content Switching Expression for Unified Gateway
If your Citrix Gateway Virtual Server is behind a Unified Gateway (Content Switching Virtual Server), then you must update the Content Switching Expression to include the manageotp paths.
- In the Citrix ADC GUI, navigate to Configuration> Traffic Management > Content Switching > Policies.
- On the right, select the Unified Gateway Content Switching Policy, and then click Edit.
- Append the following expression under the Expression area, and then click OK.
|| HTTP.REQ.URL.CONTAINS("/manageotp")
Manageotp User Experience
To access the manageotp web page:
- Point your browser to https://mygateway.corp.com/manageotp or similar. Add /manageotp to the end of your Gateway URL.

- Notice it’s only single-factor authentication. Login using normal LDAP credentials.

- Click Add Device.

- Enter a device name, and click Go.

- For OTP Push, on your phone, install the Citrix SSO app if it’s not already installed. Then launch it.
- Switch to the Password Tokens tab and tap Add New Token.

- Tap Scan QR Code.

- Then scan the QRCode shown in your browser.
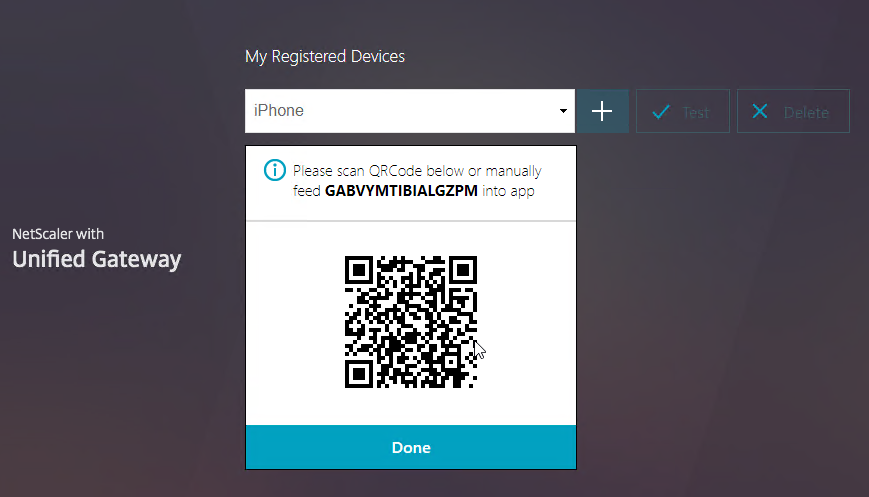
- You should see the Device Name. Tap Save.

- Switch to the Password Tokens tab and tap Add New Token.
- If OTP Passcode, launch the Google Authenticator application on your phone. Click the plus icon in Google Authenticator, and scan the QRCode that is shown on the screen.
- Citrix SSO app also supports passcode.
- Christian in the comments indicated that Microsoft Authenticator also works. Click on plus sign -> other (Google,…).
- If you configured OTP Push, then you won’t see a Test button. To display the Test button, simply refresh your browser page.

- Click Test.

- Enter the passcode shown in your Authenticator, and click Go.

- Citrix SSO app shows the passcode on the main Password Tokens view.

- Citrix SSO app shows the passcode on the main Password Tokens view.
- When done, on the top right, click your name and Log Off.

- The OTP registration info is stored in the Active Directory attribute. If users need to re-register, then help desk might need permission to clear this Active Directory attribute.

Perform OTP Authentication
- If you access your Gateway URL normally, you’ll be prompted for either one password or two passwords. If one password, then enter your normal LDAP credentials and Citrix Gateway will send a push notification to your phone. If two passwords, then enter the OTP passcode in the second field.

- The push notification is shown on the phone’s lock screen. Tap it to open the Citrix SSO app.

- Tap Allow to allow the authentication request.

- Tap OK when prompted with Logon Success.

- After Gateway authentication, Gateway should Single Sign-on into StoreFront with no additional password prompts.

CLI Commands
Here’s a complete OTP nFactor Flow (Visualizer) CLI configuration (except encrypted passwords):
# AAA Global Settings # ------------------- enable ns feature AAA set aaa otpparameter -maxOTPDevices 1 # Push Service # ------------ add authentication pushService cloudPush -namespace "https://mfa.cloud.com/" -clientID b6effb5e-b2d3125 -clientSecret 152c84647b -encrypted -encryptmethod ENCMTHD_3 -CustomerID MyCompan -trustService "https://trust.citrixworkspacesapi.net/" # LDAP Actions # ------------ add authentication ldapAction LDAP-Corp -serverIP 10.2.2.11 -serverPort 636 -ldapBase "dc=corp,dc=local" -ldapBindDn ctxsvc@corp.local -ldapBindDnPassword a368c -encrypted -encryptmethod ENCMTHD_3 -ldapLoginName sAMAccountName -groupAttrName memberOf -subAttributeName cn -secType SSL -passwdChange ENABLED -nestedGroupExtraction ON -groupNameIdentifier sAMAccountName -groupSearchAttribute memberOf -groupSearchSubAttribute CN add authentication ldapAction OTPRegisterDevice -serverIP 10.2.2.11 -serverPort 636 -ldapBase "dc=corp,dc=local" -ldapBindDn admin@corp.local -ldapBindDnPassword 1f952a81 -encrypted -encryptmethod ENCMTHD_3 -ldapLoginName sAMAccountName -groupAttrName memberOf -subAttributeName cn -secType SSL -authentication DISABLED -pushService cloudPush -OTPSecret userParameters add authentication ldapAction LDAPOTPAuthentication -serverIP 10.2.2.11 -serverPort 636 -ldapBase "dc=corp,dc=local" -ldapBindDn admin@corp.local -ldapBindDnPassword 4319b4d7 -encrypted -encryptmethod ENCMTHD_3 -ldapLoginName sAMAccountName -searchFilter "userParameters>=#@" -groupAttrName memberOf -subAttributeName cn -secType SSL -authentication DISABLED -pushService cloudPush -OTPSecret userParameters # Advanced Authentication Policies # -------------------------------- add authentication Policy _OTP-AAA_OTPManageOrAuthenticate__root_0 -rule true -action NO_AUTHN add authentication Policy SelectManageDevices -rule "http.req.cookie.value(\"NSC_TASS\").contains(\"manageotp\") && client.IP.SRC.IN_SUBNET(10.2.0.0/16)" -action NO_AUTHN add authentication Policy SelectOTPAuthentication -rule true -action NO_AUTHN add authentication Policy LDAPAdv -rule true -action LDAP-Corp add authentication Policy OTPRegisterDevice -rule true -action OTPRegisterDevice add authentication Policy LDAPOTPAuthentication -rule true -action LDAPOTPAuthentication # Login Schemas # ------------- add authentication loginSchema SinglePasswordForManageOTP -authenticationSchema "/nsconfig/loginschema/LoginSchema/SingleAuthManageOTP.xml" add authentication loginSchema OTPPushOrPasscode -authenticationSchema "/nsconfig/loginschema/LoginSchema/DualAuthPushOrOTP.xml" -passwordCredentialIndex 1 # Authentication Policy Labels # ---------------------------- add authentication policylabel OTPManageOrAuthenticate__root -loginSchema LSCHEMA_INT bind authentication policylabel OTPManageOrAuthenticate__root -policyName SelectManageDevices -priority 100 -gotoPriorityExpression NEXT -nextFactor AuthenticateToManageDevices__OTPManageOrAuthenticate bind authentication policylabel OTPManageOrAuthenticate__root -policyName SelectOTPAuthentication -priority 110 -gotoPriorityExpression NEXT -nextFactor OTPAuthentication__OTPManageOrAuthenticate add authentication policylabel AuthenticateToManageDevices__OTPManageOrAuthenticate -loginSchema SinglePasswordForManageOTP bind authentication policylabel AuthenticateToManageDevices__OTPManageOrAuthenticate -policyName LDAPAdv -priority 100 -gotoPriorityExpression NEXT -nextFactor OTPDeviceRegistration__OTPManageOrAuthenticate add authentication policylabel OTPAuthentication__OTPManageOrAuthenticate -loginSchema OTPPushOrPasscode bind authentication policylabel OTPAuthentication__OTPManageOrAuthenticate -policyName LDAPAdv -priority 100 -gotoPriorityExpression NEXT -nextFactor OTPPushOrPasscode__OTPManageOrAuthenticate add authentication policylabel OTPDeviceRegistration__OTPManageOrAuthenticate -loginSchema LSCHEMA_INT bind authentication policylabel OTPDeviceRegistration__OTPManageOrAuthenticate -policyName OTPRegisterDevice -priority 100 -gotoPriorityExpression NEXT add authentication policylabel OTPPushOrPasscode__OTPManageOrAuthenticate -loginSchema LSCHEMA_INT bind authentication policylabel OTPPushOrPasscode__OTPManageOrAuthenticate -policyName LDAPOTPAuthentication -priority 100 -gotoPriorityExpression NEXT # Authentication Virtual Servers # ------------------------------ add authentication vserver OTP-AAA SSL 0.0.0.0 bind authentication vserver OTP-AAA -policy _OTP-AAA_OTPManageOrAuthenticate__root_0 -priority 100 -nextFactor OTPManageOrAuthenticate__root -gotoPriorityExpression NEXT # Authentication Profiles # ----------------------- add authentication authnProfile OTP-AAA -authnVsName OTP-AAA # NetScaler Gateway Session Profiles # ---------------------------------- add vpn sessionAction AC_OS_10.2.4.120 -transparentInterception OFF -defaultAuthorizationAction ALLOW -SSO ON -icaProxy ON -wihome "https://xdc01.corp.local/Citrix/StoreWeb" -ClientChoices OFF -ntDomain corp.local -clientlessVpnMode OFF -storefronturl "https://xdc01.corp.local" add vpn sessionAction AC_WB_10.2.4.120 -transparentInterception OFF -defaultAuthorizationAction ALLOW -SSO ON -icaProxy ON -wihome "https://xdc01.corp.local/Citrix/StoreWeb" -ClientChoices OFF -ntDomain corp.local -clientlessVpnMode OFF # NetScaler Gateway Session Policies # ---------------------------------- add vpn sessionPolicy PL_OS_10.2.4.120 "REQ.HTTP.HEADER User-Agent CONTAINS CitrixReceiver" AC_OS_10.2.4.120 add vpn sessionPolicy PL_WB_10.2.4.120 "REQ.HTTP.HEADER User-Agent NOTCONTAINS CitrixReceiver && REQ.HTTP.HEADER Referer EXISTS" AC_WB_10.2.4.120 # NetScaler Gateway Global Settings # --------------------------------- enable ns feature SSLVPN # NetScaler Gateway Virtual Servers # --------------------------------- add vpn vserver gateway2 SSL 10.2.4.220 443 -Listenpolicy NONE -tcpProfileName nstcp_default_XA_XD_profile -deploymentType ICA_STOREFRONT -authnProfile OTP-AAA -vserverFqdn gateway3.corp.com bind vpn vserver gateway2 -portaltheme RfWebUI bind vpn vserver gateway2 -policy LDAP-Corp -priority 100 bind vpn vserver gateway2 -policy PL_OS_10.2.4.120 -priority 100 bind vpn vserver gateway2 -policy PL_WB_10.2.4.120 -priority 100 # SSL Virtual Servers # ------------------- bind ssl vserver gateway2 -certkeyName WildcardCorpCom.cer_CERT_KEY bind ssl vserver gateway2 -eccCurveName P_256 bind ssl vserver gateway2 -eccCurveName P_384 bind ssl vserver gateway2 -eccCurveName P_224 bind ssl vserver gateway2 -eccCurveName P_521 bind ssl vserver OTP-AAA -certkeyName WildcardCorpCom.cer_CERT_KEY bind ssl vserver OTP-AAA -eccCurveName P_256 bind ssl vserver OTP-AAA -eccCurveName P_384 bind ssl vserver OTP-AAA -eccCurveName P_224 bind ssl vserver OTP-AAA -eccCurveName P_521
Hi Carl,
It would be very useful to see steps for configuring the manageotp and otp authentication websitse for more than one domain.
I have already made many connections via native OTP to the ADC. Always on a gateway server, but now for the first time on a content switch and I have a problem there. The setup and authentication with a smartphone and the OTP via MS Authenticator works, but when redirecting to the backend I get the error message “Target URL not found for redirection” after login. We haven’t found a solution to this problem yet. Apparently the cookie for “NSC_TASS” is not written and is now missing or maybe something else. Can anyone help here?
Does your Content Switch have a policy based on URL paths? Or is it based on hostname?
it is based on hostname
Hi Carl
I need put a page EULA before of nfactor flow.
I have the OTP flow working with correct access to manageotp and policy autheticated running ok. But when I bind login schema EULA in server AAA and policy with expression http.REQ.URL.CONTAINS(“/nf/auth/doAuthentication.do”) is bind in Authenticad policies, the OTP flow is broken
If you have an idea ?
Thanks
Hi Carl,
Аny ideas on how to add authentication by membership in AD group to this scheme with the AAA-OTP?
Something like this: https://support.citrix.com/article/CTX111079/how-to-restrict-access-to-netscaler-gateway-for-only-members-of-one-active-directory-group
Thanks in advance!
Are you asking about LDAP Search Filter?
yes, but it’s not clear where it can be bind for it to work (
There’s an LDAP policy for authentication. And there’s another one for OTP. I would probably add the Search Filter to the authentication LDAP Policy/Server.
Added search filter to the “LDAP_OTP_set_no_auth” action. Works as expected.
Thanks!
Hi @Carl!
Thanks for this detailed instructions but I think you forgot to mention about how domain admins group administrators will get userParameters changed considering domain admins are a part of protected accounts and they are not as easy as to normal delegation to users.
I have been trying to solve this for the last few weeks but unable to.
Tried AdminSDHolder permissions to add ldap admin service account to have read/write userParamaters but effective access still shows ldap admin account does not have write userParameters.
I tried talking to Citrix but they said it is Active Directory Microsoft related.
I have not raised it with Microsoft yet but since nobody is suggesting any solution here I might have to.
If this was addressed before to you Carl, is there any solutions to that?
Cheers, Mark
Hi,
did you find solution for this?
Thanks
Hi
I can not register the device with the CITRIX SSO
I’m getting an error
Blogs I have run through the app I get the following errors
Got push registration response code: 400
Failed to get push information. Error message: Bad Request
Hi Carl
I follow your post on ADC 13.1.12.51 and i can’t see any QR code when i want to manage my device (add one) on /manageotp.
So i can’t scan it from my phone (google authenticator).
i see all ldap action are working and if a device is registered on AD attributes (from old ADC v 12) i can see this one, but i can’t add other… because i can see any QR code.
Hi Carl,
now i am using content switch to Citrix virtual apps gateway and Exchange owa, it works well.
could i bind OTP AAA to Exchange LB, or to my content switch? many thanks.
Only one AAA or Gateway can be bound to a Content Switch. One or the other, but not both.
You can bind nFactor to the Gateway and then configure your LB to use Gateway for authentication.
Hi Carl,
Could you give more ideas or detail for this, we wanna use otp with owa login pages. Thanks.
You could load balance OWA through ADC and then add Authentication vServer to the load balancing configuration.
Is otp works with citrix sso plugin android phone !?
Very helpful post! One thing though I’ve been trying to figure out based on this is the default OTP nFactor Flow listed has an issue if you have the “Allow Password Change” is on your LDAP Authentication Action when on the Dual Factor Login. From my testing this appears to be then only a Single-Factor check which then allows the user to update the password without it checking the OTP. Then when it completes even though it successfully updates the password it displays an Error (Please log on :: The server met an error. Please try again or contact your administrator. (Go Back)) as I believe it loses the OTP value you previously had submitted.
Is it possible to check for the OTP to be Valid before the LDAP User Authentication to then handle the “Allow Password Change” properly?
Of course, if this is the case then between your ManageOTP and your OTPAuthentication you would need to use different LDAP Actions so that users could not simply go to manageotp and then have a method for getting around a second Factor for handling password expiration/must change situations.
Also, do you have a way of adding “Cancel” buttons so the “manageotp” {Expression::http.req.cookie.value(“NSC_TASS”).contains(“manageotp”)} can be cleared when a user accidentally goes to the wrong URL and then can not get back to being a standard OTPAuthentication Login Form without being forced to log into the ManageOTP?
I found I have to have a Policy/Action ahead of time to perform the Policy/Action LDAP with “Authentication” disabled. That checks for the user’s security group membership of whether they have the Citrix Remote Access and then if so it continues on to the OTP Factor Check. If the OTP Factor Check is TRUE then it continues onto the Policy/Action that has “Authentication” enabled and the “Allow Password Change” enabled. This ensures the OTP was valid and then handles allowing the user to update their Password after verifying the old password was valid. Annoyingly, this does cause another LDAP Search/Query which seems wasteful.
The solution works mostly, except an outstanding problem is that it produces the ugly response of.
Please log on
The server met an error. Please try again or contact your administrator.
Options: “Go Back”
The user is able to use the “Go Back” and then sign back in with their updated password and OTP. But it would be really helpful to have some way of changing this response to be more user friendly and/or update it to just use the new credentials to pass through to StoreFront.
Also, I still would like to know if anybody has a way to setup a “Cancel” that clears cookies so the http.req.cookie.value(“NSC_TASS”).contains(“manageotp”) is also cleared.
You could use searchFilter “memberOf=” in the LDAP profile to only return the set of users with remote access. Then you don’t have to check for group membership.
Hi Carl – Cheers for the guide. I am running NS 13.1 17..42nc and I am getting the following when attempting to register a new device for OTP.
Mar 14 20:49:10 acs-ctx-ns-001 [611]: (0-57) receive_ldap_user_search_event: Number of entires in LDAP server response = 1
Mar 14 20:49:10 acs-ctx-ns-001 [611]: (0-57) receive_ldap_user_search_event: [0]: Object = 0x805415840
Mar 14 20:49:10 acs-ctx-ns-001 [611]: (0-57) check_for_domain_dns: Extracted attribute, name: objectClass, value: top,person,organizationalPerson,user
Mar 14 20:49:10 acs-ctx-ns-001 [611]: (0-57) check_for_domain_dns: Did not find objectClass of type domainDNS
Mar 14 20:49:10 acs-ctx-ns-001 [611]: (0-57) receive_ldap_user_search_event: Updated usrobj for user chris.gregson
Mar 14 20:49:10 acs-ctx-ns-001 [611]: (0-57) extract_ldap_attribute: retrieved pwdLastSet value 130861313413969376 for some.user, length is 18
Mar 14 20:49:10 acs-ctx-ns-001 [611]: (0-57) receive_ldap_user_search_event: Failed to extract attribute, name: userParameters,
Mar 14 20:49:10 acs-ctx-ns-001 [611]: (0-57) extract_ldap_attribute: retrieved mail value some.email@domain.com for some.user, length is 34
Seems it is failing to extract the attribute ‘UserParameters’. I’ve checked all of the LDAP actions and they all test successfully and syntax seems correct.
If I check the UserParameters attribute in AD it is unset.
Consequently the Citrix SSO app fails to add the token.
Any ideas?
Many thanks
Does your bind account have permissions to read and modify this attribute? A normal Domain User does not have permission. You can try a domain admin to confirm.
I wonder if you see that when no device has been registered. Any other errors later in the log?
I am also getting the same issue
it is able to read the attribute if i put one there manually and seems to be able to delete it aswell but its just writing to it for some reason i can see anything in the logs at the moment with out that says why
Hi yuljk.
Where did you find those logs in Netcaler?
I am trying to troubleshoot
Cheers.
Dumb question:
is the userParameters attribute not used for the TSProperty settings for the Terminal Server? Or is this just a relict from old versions?
https://docs.microsoft.com/en-us/openspecs/windows_protocols/ms-tsts/15f8b01d-900d-4f89-a3fa-1681e55f383d
Old versions, yes. It’s a convenient attribute already in the schema that supports the data type and length required for OTP. If you are using userParameters then you should find a different attribute.
Great guide, works like a charm for me. Only I have two questions/concerns:
1. How can I change the page title: ‘Netscaler AAA’. Binding a portal theme doesn’t work. Editing tm1index.html doesn’t work either.
2. This doesn’t seem to work with Workspace App (Using 2112). Is it possible to make it work with Workspace App? I’m not sure what I’m doing wrong. I don’t use any classic authentication policies.
In your portal theme, have you added the Login Page section and edited the title in there?
Alternatively, when creating the Authentication Schema in the nFactor Flow, you can ‘edit’ before ‘selecting’ the XML.
Hope this helps.
Would anyone be able to tell me what I need to change to remove the “Delete” button from the OTP registration page? We do not want users to be able to remove their own devices, but I can not find how to remove it.
Thanks
Hi Truh Seeker,
Did you manage to make the configuration to prevent users from removing the enrolled device? I also need to do this and I have not been able to make it work
Hello Carl, I followed your steps and everything working when I enter the passcode manually, the push never works. when I try to login for the puhs, I get the following error
server not expecting curent user input. please try again or contact your administartor but when i enter the passcode manually, i login fine.
I alread have the push selected in the LDAP NO AuTH policy and it is status is COMPLETE
please advise.
Anybody got the manageotp URL working on ADC NS13.0 82.41.nc? When I browse to manageotp, it goes to logon/LogonPoint/tmindex.html and asks for username and password. When I enter valid username and password, the message in the debug logs is “username not found”. The same LDAP policy works with my other Citrix gateway and authentication server.
I can see this Citrix ADC OTP still is the poor man’s nFactor authentication. This is OK for small environments. For large environments, must have something like Azure MFA or Okta.
Everything working for me, BUT the logon session seems to timeout. Normally when I would go to launch an app in a timeout out session it would prompt me to log back on. This doesn’t. It just says ‘The resource is unavailable currently’. I have to remove and re-add the site to get it working again. Even trying to use ‘sign in’ doesn’t seem to get me back in successfully.
Hi Carl,
Is it possible to extend the wait time for the push to be approved? , currently is 30 sec.
Thanks,
Moshe
Hello Carl,
While loggin into Citrix either from normal login url or from manageotp url users get ntp sync error while login.
Without any changes in Citrix and AD environment and but we change the mobile devices of users and register the new device then user able to login into Citrix vdi.
Is there any way to find out the root cause, because if we face the similar issues again then it is not possible to change the mobile device every time.
If you run “date” from the BSD shell, do you see the correct time and time zone?
Yes it’s shown correct date and time on ADC.
This issue observed on some of the devices once we change the mobile device we are able to login without any issue.
I have a question on the MANAGEOTP access we have it setup on a test and works fine. external access to the manageotp but we have limited to e a member of a AD group and the userparameters has to meet a requirement to login to register a device. my question is we have multiple tenents so limiting to ip is not going to work and I can seem to access the maangeotp internally. so the way we currently go external access is this ok or is there a better way for us to secure access to get users to register devices? we were going to remove users from the AD that allows access to login to OTP management once a device is registered. but just wondering if there is a better way to make it more secure with out a 3 party. as the whole idea of us using Citrix OTP is it no extra cost.
OK, For everyone else that might pulling his/her hair out on this one, indeed the Citrix SSO App does DOESNOT support SNI at this point in time. Please Citrix go fix! At this point each vserver/secret combination consumes one IP address … The Push Service kicks the App and hitting OK passes me one, though now I get a Cannot Complete Request message, so diving further into this …
ok, got everything to work. If you, like me, prefer UPN as logon name, of course use userPrincipalName as SSO name attribute where applicable AND in the traffic policy you have to explicitly set ‘Single Sign-on’ to ‘ON’ and make sure there is no default domain (otherwise that could be postfixed to your logon name and of course that won’t work…
Does anyone have a self service web solution to manage the 1st enrollment and setup secret questions/answers or set of backup codes (that can be used for account recovery)… Thanks!
Its in NetScaler 13 =) Would be handy if there was also something for OTP (re)enrollment if you are successfully authenticated by secret questions and password .. so that 1st forced enrollment with SSPR also requires OTP device registration …
Hi, I also had the issue with “Cannot Complete Request” message on 64.35. Did you try it already with 67.39 ?
still the same with 67.39 🙁
Not sure if it’s related to your problem, but citrix disabled some weaker authentication methods, below setting should fix it. I do advice to change your setup in the near future.
Link: https://support.citrix.com/article/CTX281592
Fix: Citrix Gateway -> Policies -> Traffic -> Traffic Profiles -> Single Sign-on = ON
The third attempt was successful, I did it all again. But I use the Microsoft Authenticator App, with which it works, also with SSO = on.
Turn on SSO in the Traffic Profile also didn’t help 🙁
Hi Carl and others,
Sorry to bother, but I am stuck at something that did work in the previous OTP (without Push service). Whenever I scan the QR code with Citrix SSO app on iOS, I get this error in the app: “Notification registration failed. Citrix SSO was unable to register for push notification” and my hence AD attribute is not written (I use extensionAttribute15, unencrypted). I also tried adding the key manually in the app, but same result. There are no related events in the /var/log/ns.log. I also used a dedicated external IP, since Citrix SSO and SNI seem to not work together. I am getting out of options, so if someone can shed a light heer, would be very great!
Thanks!
Ronald
Hi Ronald,
Dit you ever sort this out?
I’m on the same page here…
If I remove the push service within the Device registration server, the app registers within my AD. And I can login with user/pass and manual enter OTP.
if I remove the device registration enable push service, then I get the same error as you do.
Push service seems enabled (complete)
can you shine a little light on my issue? 🙂
Thanks in advance!
Best regards,
Herwin
Hi Carl,
Just finished the setup, but I found that I can register a device just fine, but when trying to login with the dual factor the SSO App does not pop up nor does it work when I put the OTP in manually. I get prompted with “Try again after some time ..”. I know for sure I can access mfa.cloud.com etc, the status of the auth Push Service is also complete .. No clue what goes wrong. Are there some logs I can check?
Thanks!
Ronald
Hi all,
Checked the ns.log:
Sep 11 11:34:22 10.0.2.160 09/11/2020:09:34:22 GMT sys-ctx-ns1301 0-PPE-0 : default SSLVPN Message 2561 0 : “ns_aaa_login_handler: Login request is not expected to be encrypted”
Sep 11 11:34:22 10.0.2.160 09/11/2020:09:34:22 GMT sys-ctx-ns1301 0-PPE-0 : default SSLVPN Message 2562 0 : “LOGIN: CGI/LOGIN: Continuing auth for user @ at factor OTPAuthentication__OTPManageOrAuthenticate with login schema OTPPushOrPasscode”
Sep 11 11:34:22 10.0.2.160 09/11/2020:09:34:22 GMT sys-ctx-ns1301 0-PPE-0 : default SSLVPN Message 2563 0 : “AAAD API: aaad_authenticate_req: sending login req to aaad for <@>, factor , auth type 65, trans id 3884”
Sep 11 11:34:22 10.0.2.160 09/11/2020:09:34:22 GMT sys-ctx-ns1301 0-PPE-0 : default AAA Message 2564 0 : “(0-29) send_authenticate_pdu: Sending Preamble”
Sep 11 11:34:22 10.0.2.160 09/11/2020:09:34:22 GMT sys-ctx-ns1301 0-PPE-0 : default AAA Message 2565 0 : “sslvpn_aaad_login_handler : (0-29): sslvpn_aaad_login_handler: Reply Received, status from aaad: 3, aaad flags 1000”
Sep 11 11:34:22 10.0.2.160 09/11/2020:09:34:22 GMT sys-ctx-ns1301 0-PPE-0 : default AAATM Message 2566 0 : “AAAD RESP: received resp,user: <@>, factor: , trans id 3884, pcb trans id 3884, q_flags 1342210052”
Sep 11 11:34:22 10.0.2.160 09/11/2020:09:34:22 GMT sys-ctx-ns1301 0-PPE-0 : default AAA LOGIN_FAILED 2567 0 : User @ – Client_ip 10.0.1.72 – Failure_reason “External authentication server denied access” – Browser Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.83 Safari/537.36
Any ideas? Where/how/why external access denied?
Grtz,
Ronald
did you find what this ” Reply Received, status from aaad: 3, aaad flags 1000″ means? Why you had access denied? I have a dyployment and some users sometimes faced this error ..
Hi, don’t know if my previous one makes it or not, but you need a DNS Name Server that is not showing DOWN and you need Premium Edition .. The the push service shows up in the web ui .. took me way too long. Cheers!
Hi Carl,
I just tried to follow your article, I downloaded the ns13_64.35 bits, added an enterprise license, enabled all necessary features, but when I search for ‘push’ I get zero hits. When I go to the ‘Action’ submenu, in the right pane it says ‘No Push Service’, but when I click it, nohting happens. On the left in the menu itself I cannot see the Push Service either.
Am I missing something? Saw this before?
Thanks as always for sharing your stuff =)
BR,
Ronald
Hi Carl,
Thank you again for another wonderfull post (Thumbs up!!)
I’m learning netscaler this way :p
So I’m running my Citrix gateway and I would like to get push OTP.
Maybe I’m missing something, all is working great when entering otp manually, when I want to use push. never gonna happen.
Error in ns.log Push: No devices are registered to send Push Request to cloud for Username
Also when entering credentials and password, and press enter, it directly returns to login.
I have setup my OTP push service, that’s fine, (says ompleted.)
Also verified I’m running platinum edition 🙂 and I’m running NetScaler NS13.0: Build 61.48.nc
Can you point me in the right direction?
I did not use the userParameters (i’m using RDS profile so that’s taken) I’m using the department parameter.
Best Regards,
Herwin Duinkerken
Hi Carl, where is OPT secret stored in Active directly by default ? Is it in userParameters attribute ?
If so, can you change the location of it ? I’d appreciate it if you could answer the question.
It’s stored in whatever attribute you specify in your LDAP Policy/Server. There’s a field called OTP Secret.
Hi Carl
Thank you so much for your quick response! I understand.
Hi Carl, do you know if is it possible to set an email policy as authentication factor?
I need to change the OTP sended to user’s device with OTP sended by user’s e-mail. This because the customer doesn’t want to enroll users personal devices.
Thank you.
Citrix SSPR has Email as an authentication factor. https://carlstalhood.com/self-service-password-reset-citrix-adc/
Thank you Carl. Do you think is it possible to modify the OTP authentication with e-mail authentication ?
Should be necessary to fill the filed the userParameter with a token …
I tried in my lab environment, starting with a Native OTP auth schema but I can’t to invoke the mail send.
Do you have any tips?
Thank you
There are some users who are deleted from AD. But their mobile authentication APP still showing the code. How to check which users have registered their device for OTP? And how to remove users from Netscaler OTP whose AD profile is deleted
If the user doesn’t exist in AD and there’s no OTP secret in AD, then the user won’t be able to login.
Hi Carl, I have a situation in which MAx OTP allowed = 1, I go to /manage OTP and delete secret. It show successufully deleted but when I add the new device it says that I reached maximum device. From AD never secret will be deleted. OTP user data is crypted with the same certificate before user register device for the first time. AD is not balanced during test to make easy replication/persistent aspects. Where do you thing I could keep going on the analysis? Many thanks
Hi, Sorry for my last comment . I found my error. The script was just looking for Notepad(86x) and not Notepad(64x), thanks for your work.
Hi Carl , thanks again for this huge article. I have a question regarding the Wilcard certificate from your domain. Is it a simple Web certificate request from IIS and your local authority ? or is it with additionnal OID for authentification ?
Thanks
Just a regular wildcard certificate should be fine.
Thanks Carl , it work well. I’ve make a mistake by binding the certificate with the shell activated.
Solution is working now.
I have just a little concern about manage OTP page. The filter by “&& client.IP.SRC.IN_SUBNET(192.168.1.0/24)” isn’t working in my case.
I cannot acces to the page with the condition activated.
If you have an idea ? 🙂
Same problem here at a new deployment of ADC 13.1
w/o IP.SRC filter it works, but not with IP.SRC filter activated
What a post!!
I’m newie in this topic; and I’m searching and learning about the OTP advantages; and I have certain doubts, so if you can helpme I really appreciated..
1) In the Login Schema Policy, if I change the subnet parameters for something like just “manageotp”, that’s would allow me that any user can access via browser to /manageotp page…
2) If I configure the push notifications as a DualOPT but my NS haven´t access to internet, the Gateway service will use the google authenticator or will send error?
3) And the last one for the pilot :D; if the client has his NS in a subnet and looks access from his NAT public IP address, the OTP will works normally as in intranet or is only limited to work on intranet.
Thank very much for any comments that you make can do.
Granting unlimited access to /manageotp is dangerous because /manageotp only requires single factor authentication.
Without push, users will need to enter the passcode.
Are you asking if OTP will work if exposed (NAT) to the Internet? Certainly. If push, then ADC will push to cloud, which pushes to user’s phone. If not push, then user will have to enter passcode that is displayed in the OTP app.
I understand, thank you very much for the replies.
be safe!! greetings
Hi Carl,
thank you for sharing the config details. In the past I already configured that solution for a customer successfully. Now I’m sitting on a new configuration for a different customer and I get an error when I try to register an Device.
I double/tripple checked the configuration today. I’m able to register the device with the OTPedit App with the bound service account to the LDAP action. Once I enrolled the device with the OTPedit tool, I can logon with that user and the bounded device.
The only thing that is not working is the device enrollment via /manageotp after successfull logging in. The message is: Failed to add ‘devicename’
Once I added an device via the OTPedit Tool, and I log on to the /manageotp website I can see that device registered and I can also successfull test it.
The ADC Build is: NS13.0.52.24.nc
Do you have any ideas?
best regards
I have the same problem as “Olu”
Followed your guide to configure my OTP on NetScaler with Premium license but after configuration when i try to access the url https://mygateway.local/manageotp it automatically redirect me to https://mygateway.local/logon/LogonPoint/index.html and when i put in the user credentials it sends me to the storefront login page after i authenticate. I am not given the option to register a device. Please help.
Never mind i was to quick :-), i can now add a device but when i want to add it i get a error: “Failed to add”, the time is correct and the netscaler has internet access.
Hi Sander
I am having a same problem of yours. how did you fixed it? the https://mygateway.local/manageotp page was working for sometime and it stopped working and redirecting to login page.
Hi Carl,
Great article again, thanks a lot. I’ve got everything working for our primary domain, but now i also want this to work on the domains where we have a forest domain trust to (from the primary domain where storefront etc. is running). I already have all the LDAP policies to the different domains. We want to use only one URL for our customers, and don’t want to bind every LDAP policy to the server (there’s is a limitation of 32 ldap policies, we have around 40)
I’ve read something about policy labels and that we need to use UPN and extract the domain to use towards storefront. Can you (or maybe one of your followers) put me in the right direction on how to achieve this? I’m a bit stuck on how to extract the domain from the users UPN. Hope you can help.
Hi Carl,
thank you for your valuable work!
I’ve successfully configured OTP auth but now i need to add a second LDAP domain. How i can accomplished this? I’m already using Upn as login name.
Do i need to bind a new nfactor flow to AAA vserver or can i add more policy/action to existing nfactor flow?
Thank you for your thoughts.
Stefano
You should be able to bind multiple LDAP Policies/Servers, one for each domain. ADC will loop through each one until the UPN matches.
Works like a charm 🙂
Thank you.
Hi Carl,
Followed your guide to configure my OTP on NetScaler with Premium license but after configuration when i try to access the url https://mygateway.local/manageotp it automatically redirect me to https://mygateway.local/logon/LogonPoint/index.html and when i put in the user credentials it sends me to the storefront login page after i authenticate. I am not given the option to register a device. Please help.
Thanks
Olu
Hi Carl,
Could you please help with the above question ? by the way i am a big fan and your page have been of great help since i found it.
Regards,
Olu
Hi Olu
Did you able to fix this issue? am facing same problem and looking for solution.
Yes, it was a misconfiguration for me. I had to use the Commands to set it up and i was able to reach the manageOTP page to register a device. But i am still having one issue and would appreciate it if @Carl Could help out.
After the complete setup, I was able to reach the manageotp device registration page and after registering a device it doesn’t seem to persist. if i access the url with the same user i don’t see the previously enrolled device. please help.
Thanks in advance.
Same problem here, device registered doesnt persist..
I have this issue as well. I have triple checked the config and it appears correct. Put domain admin creds in LDAP to make sure I wasn’t denied access. Still no luck. Also, I was able to get it working in the past. When I look at the AD attribute, it is empty.
Any news to this problem? We were able to configure push in the past, then we disabled it. Now when we tried to activate it again, device will not persist and Citrix SSO says was unable to register for push notificatoin. Everything check multiple times… any ideas?
Thanks,
Adam
Hi Carl, awesome work! Never would get OTP up and running without your support…
I wonder what happened to OTP Encryption if I have to regular replace the Encryption Certificate. May I use a cert from internal CA with extended lifetime?
Regards, Armin
Hi Carl,
Thank you, everything is working, except one thing. When the userparameter field is empty on a user, it can’t login at url/manageotp, when i manually put something (like the number 1) in the field, it’s working. They can register their device and this will overwrite the field. I can’t figure out if i’m doing something wrong, do you have an idea where to look?
Hi,
I successfully deployed OTP, however have 2 comments.
1. When push method is selected in LDAP Actions – OTP device is not being entered into UserParameters.
2. With enabled encryption of OTP device in UserParameters, first thing is to change search UserParameters string in LDAP Action. However after change it is not possible by user to remove by himself OTP device. I believe without encryption it was possible.
Any advice?
here are the logs
CTXADC [1334]: (0-219) ns_ldap_register_encrypted_otp: Failed to bas64 deocde OTP data, processing it as plain text
CTXADC [1334]: (0-219) unsigned int aaad_base64decode(char*, unsigned int, char*, unsigned int): Base64 Decode: Failed to decode string…
CTXADC [1334]: (0-219) receive_ldap_user_search_event: noauth, preparing to update otp in attribute for , devicelen 10, devicename __u31_234, devicetag len 0, devivetag ^C
CTXADC [1334]: (0-219) aaad_json_read_otp_attribute_value: Failed to bas64 deocde OTP data, processing it as plain text
CTXADC [1334]: (0-219) unsigned int aaad_base64decode(char*, unsigned int, char*, unsigned int): Base64 Decode: Failed to decode string…
Hi,
After latest 13.0 47.24 firmware update, my OTP encryption stopped working. Did anybody notice the same? I have constantly failed to add device. When disabling encryption of OTP device, it works correctly.
Hi Carl,
If you wanted turn off OTP for certain external IP Addresses, is this still the best method.
https://discussions.citrix.com/topic/382037-disable-two-factor-authentication-from-certain-sourceip/
Hi Carl,
Thanks for a great article. Could you confirm two things:
1. Push notification is only available with the Citrix SSO APP?
2. Before implementing the native OTP solution, the workspace app would ask for the username and password. The last username that logged in was remembered. Like the image on this page: https://discussions.citrix.com/topic/390720-citrix-4x-constantly-prompting-to-login
Now with OTP configured, it pops up the gateway GUI like the image in the overview under Workspace app 1809. Is that by design or can it be changed? The users like that they don’t have to type their username every time.
Regards,
Blair
1. That’s correct.
2. nFactor behaves differently than non-nFactor in that nFactor requires displaying a Web View. Another option is to use a browser to login, and many browsers have password managers.
Thanks heaps Carl.
Great post, got native OTP working on a Netscaler Enterprise. My only problem is IOS devices with the Workspace App, these are unable to login after enabling OTP on the portal
Hi Carl,
Thank You.For a single domain it works great but I am struggling implementing it on a single Ctrix Gateway server with multiple domains and the OTP using Nfactor as the users want to use domain\username .Any recommendations as I tried the domain dropdown as a first factor but have issue with the expressions and OTP as a second factor between the different domains ?
Hi Carl,
Thanks very much for the great post. I have similar issue with deploying native OTP and multiple domains. Is it simple that adding more server & policy per domain?
Hi,
Thanks for this! Push notifications are all working well. However with the pushService enabled on the OTPRegisterDevice LDAP action, we can only register Citrix SSO apps as devices. We add it, refresh the page, and the device is there, with the LDAP attribute updated.
If we attempt to use another app (e.g. Google or Microsoft Authenticator), or just click Go/continue, the LDAP attribute isn’t updated, and the device isn’t added.
Changing the pushService on OTPRegisterDevice to blank allows us to add other apps and log in with the OTP code manually, even using the SSO app via manual code. However now the push notifications don’t work.
Is this an expected limitation, or is there a workaround to this, to allow both Citrix SSO app push notifications, and adding non-Citrix-SSO-apps?
@Ben: did you found a solution?
I am also looking for a solution for this… what if besides CitrixSSO App the customer would want to give the users flexibility to use other authenticator apps ? Any help regarding this one would be awesome!
Hi Carl
if we using SSO on citrix adc what license do we buy.?
is it possible to standard Edition..?
Thank you carl.
All AAA vServer features, including nFactor, require Advanced Edition (aka Enterprise Edition).
Citrix Gateway can SSON to StoreFront without needing AAA license.
Feedback to version 13. Cool but unfortunately not much useful for me.
I was so hopeful to see “Push Notification” but…
We have Enterprise edition and it has Native OTP, but Push OTP is available only for Platinum edition.
IT is difficult for us to go through approval process for license upgrade just for that. Now I will have to roll out OTP without Push notification. It will seems like half backed feature for our end user, since everyone expects Push OTP these days.
I have designed and implemented (for now in Lab) ManageOtp, SelfService Password Reset with OTP.
Original user access enroll into OTP with single factor (if no device registered), but later (when we have registered device) user will need OTP to access it. If device lost, our support desk will clear attribute filed and let user login with single password to enroll new device. It all works fine.
Also I was so happy to see nFlow visualization, until I checked it out.
It took quite complicated nFlow to make my design work. I was hopping that new nFlow visualization will be able to pick it up.
But no. I had to re-do everything using nFlow visualization. Why? At the end it should be same commands. Why it can not just create flows based on already created policies? I spent few weeks building and testing it, now I have to re-do it to be able to visualize it?
In short two greatest features in Release 13, and I can not use them …
Carl, on this statement “Manageotp is difficult to secure – The manageotp website is usually only protected by single factor authentication so external access must be blocked.” – Gateway can be configured to ask for 2 factors when manageotp is accessed externally.
We are updating mainline docs as well to mention this explicitly. Essentially, otp management is presented through nFactor. That means, it could be made as stringent as required.
What alternative multi-factor would you recommend for protection of manageotp? I wonder if email factor would work.
The same actions you use for SSPR should work in this flow aswell.
Thank you for the testing. Are you using a windows plugin or MAC CitrixSSO to do the test?
One more question, when I made a change to the login schema, it only affect web browser login, but not affect plugin login display, right?
I tried Windows VPN plug-in and it handled nFactor correctly.
Amazing quick post!
Actually I have tested these new features in Gateway 13. Including push notification, registered device limit, nFactor visualizer, almost everything is working good. But also, I got some problems here:
1. After I downloaded the latest Windows Gateway Plugin, and connect to my gateway, there is an script error shown “jQuery is undefined” on the plugin. (https://discussions.citrix.com/topic/403232-windows-gateway-plug-in-error-jquery-is-undefined/)
2. The Gateway 13 release note also noticed that new Windows plugin support hostname/FQDN DNS split tunnel. Since my Windows plugin doesn’t work properly, I am not sure whether this is the same feature that CitrixSSO(MAC) supports.(There is a input box for “domains” on CitrixSSO(MAC) when you add a new gateway connection to the plugin)
3. The push notification is only functioning when you are using web browser, i wish it also could support the plugin…..
I just tried push notification in the Gateway 13 VPN Client and it works fine.
dear
i did all steps and is not send push notification only login with OTP