Navigation
- GSLB Planning
- ADNS
- Metric Exchange Protocol
- GSLB Services
- GSLB Virtual Server
- Test GSLB
- DNS Delegation
- Geo Location Database
💡 = Recently Updated
GSLB Planning
GSLB is nothing more than DNS. GSLB is not in the data path. GSLB receives a DNS query and GSLB sends back an IP address, which is exactly how a DNS server works. However, GSLB can do some things that DNS servers can’t do:
- Don’t give out an IP address unless it is UP (monitoring)
- If active IP address is down, give out the passive IP address (active/passive)
- Give out the IP address that is closest to the user (proximity load balancing)
- Give out different IPs for internal vs external (DNS View)
GSLB is only useful if you have a single DNS name that could resolve to two or more IP addresses. If there’s only one IP address then use normal DNS instead.
Citrix Blog Post Global Server Load Balancing: Part 1 explains how DNS queries work and how GSLB fits in.
Citrix has a good DNS and GSLB Primer.
When configuring GSLB, don’t forget to ask “where is the data?”. For XenApp/XenDesktop, DFS multi-master replication of user profiles is not supported so configure “home” sites for users. More information at Citrix Blog Post XenDesktop, GSLB & DR – Everything you think you know is probably wrong!
GSLB can be enabled both externally and internally. For external GSLB, configure it on the DMZ NetScaler appliances and expose it to the Internet. For internal GSLB, configure it on internal NetScaler appliances. Note: Each NetScaler appliance only has one DNS table so if you try to use one NetScaler for both public and internal then be aware that external users can query for internal GSLB-enabled DNS names. As described by Phil Bossman in the comments, you can use a Responder policy to prevent external users from reading internal DNS names. 💡
add policy patset GSLB_INTERNAL bind policy patset GSLB_INTERNAL internalHostname.gslb.domain.com -index 1 add responder action DNS_Empty_Response respondwith DNS.NEW_RESPONSE add responder policy GSLB_DNS_Empty_Response "(!(CLIENT.IP.SRC.IN_SUBNET(10.0.0.0/8)||CLIENT.IP.SRC.IN_SUBNET(192.0.0.0/16)||CLIENT.IP.SRC.IN_SUBNET(172.0.0.0/12)) && DNS.REQ.QUESTION.DOMAIN.CONTAINS_ANY(\"GSLB_INTERNAL\"))" DNS_Empty_Response bind responder global GSLB_DNS_Empty_Response 100 END -type DNS_REQ_DEFAULT
For internal and external GSLB of the same DNS name on the same appliance, you can use DNS Policies and DNS Views to return different IP addresses depending on where users are connecting from. Citrix CTX130163 How to Configure a GSLB Setup for Internal and External Users Using the Same Host Name.
However, GSLB monitoring applies to the entire GSLB Service so it would take down both internal and external GSLB. If you need different GSLB monitoring for internal and external of the same DNS name, try CNAME:
- External citrix.company.com:
- Configure NetScaler GSLB for citrix.company.com.
- On public DNS, delegate citrix.company.com to the NetScaler DMZ ADNS services.
- Internal citrix.company.com:
- Configure NetScaler GSLB for citrixinternal.company.com or something like that.
- On internal DNS, create CNAME for citrix.company.com to citrixinternal.company.com
- On internal DNS, delegate citrixinternal.company.com to NetScaler internal ADNS services.
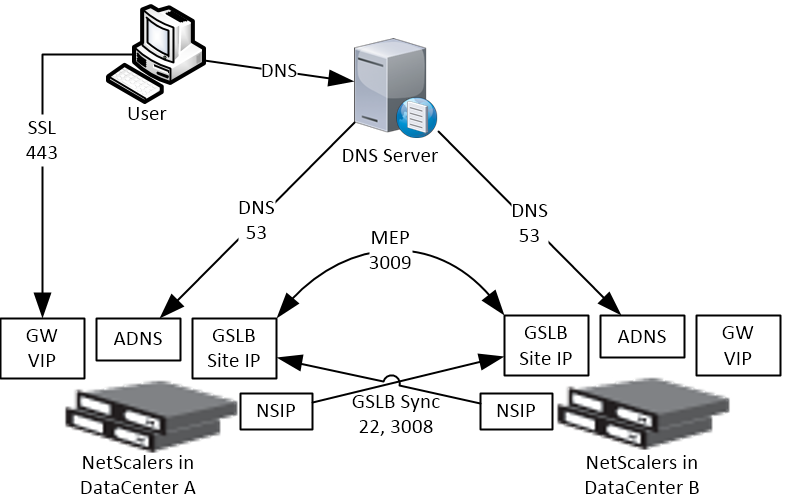
Some IP Addresses are needed on each NetScaler pair:
- ADNS IP: An IP that will listen for ADNS queries. For external, create a public IP for the ADNS IP and open UDP 53 so Internet-based DNS servers can access it. This can be an existing SNIP on the appliance.
- GSLB Site IP / MEP IP: A GSLB Site IP that will be used for NetScaler-to-NetScaler communication, which is called MEP or Metric Exchange Protocol. The IP for ADNS can also be used for MEP / GSLB Site.
- RPC Source IP: If running NetScaler 11.0 build 64 or newer then the GSLB Site IP can be anything and RPC traffic (MEP) can be sourced from the GSLB IP. For older NetScaler builds, RPC traffic is sourced from a SNIP, even if this is different than the GSLB Site IP. In older builds, it’s less confusing if you use a SNIP as the GSLB Site IP.
- Public IP: For external GSLB, create public IPs that are NAT’d to the GSLB Site IPs. The same public IP used for ADNS can also be used for MEP. MEP should be routed across the Internet so NetScaler can determine if the remote datacenter has Internet connectivity or not.
- MEP Port: Open port TCP 3009 between the two NetScaler GSLB Site IPs. Make sure only the NetScalers can access this port on the other NetScaler. Do not allow any other device on the Internet to access this port. This port is encrypted.
- GSLB Sync Ports: To use GSLB Configuration Sync, open ports TCP 22 and TCP 3008 from the NSIP (management IP) to the remote public IP that is NAT’d to the GSLB Site IP. The GSLB Sync command runs a script in BSD shell and thus NSIP is always the Source IP.
- DNS Queries: The purpose of GSLB is to resolve a DNS name to one of several potential IP addresses. These IP addresses are usually public IPs that are NAT’d to existing Load Balancing, SSL Offload, Content Switching, or NetScaler Gateway VIPs in each datacenter.
- IP Summary: In summary, for external GSLB, you will need a minimum of two public IPs in each datacenter:
- One public IP that is NAT’d to the IP that is used for ADNS and MEP (GSLB Site IP). You only need one IP for ADNS / MEP no matter how many GSLB names are configured. MEP (GSLB Site IP) can be a different IP, if desired.
- One public IP that is NAT’d to a Load Balancing, SSL Offload, Content Switching, or NetScaler Gateway VIP.
- If you GSLB-enable multiple DNS names, each DNS name usually resolves to different IPs. This usually means that you will need additional public IPs NAT’d to additional VIPs.
ADNS
- Identify an NetScaler-owned IP that you will use for ADNS. This is typically a SNIP.
- Configure a public IP for the ANDS Service IP and configure firewall rules.
- On the left, expand Load Balancing and click Services.
- On the right, click Add.
- Name the service ADNS or similar.
- In the IP Address field, enter an appliance SNIP.
- In the Protocol field, select ADNS. Then click OK.
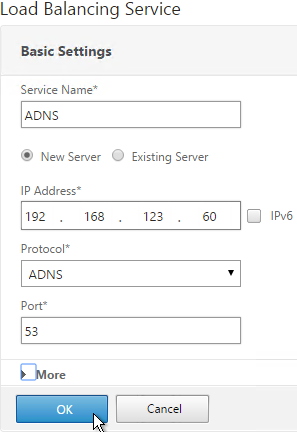
- Scroll down and click Done.
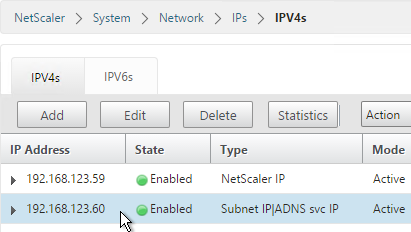
- On the left of the console, expand System, expand Network and then click IPs.

- On the right, you’ll see the SNIP as now being marked as the ADNS svc IP. If you don’t see this yet, click the Refresh icon.
- Repeat on the other appliance in the other datacenter.
Metric Exchange Protocol
- Select an IP to be the GSLB Site IP. In NetScaler 11.0 build 64 and newer, this can be any IP. In older builds, you can use the same SNIP and same public IP used for ADNS.
- Open the firewall rules for Metric Exchange Protocol.
- On the left, expand Traffic Management, right-click GSLB and enable the feature.
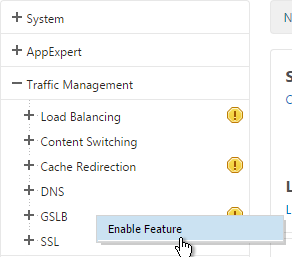
- Expand GSLB and click Sites.
- On the right, click Add.
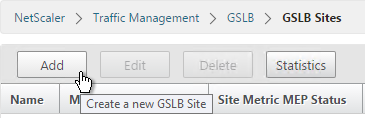
- Add the local site first. Enter a descriptive name and in the Site Type select LOCAL.
- In the Site IP Address field, enter an IP that this appliance will listen for MEP traffic. This IP must be in the default Traffic Domain. (Note: NetScaler 11.0 build 64 supports GSLB in Admin Partitions).
- For external GSLB, in the Public IP Address field, enter the public IP that is NAT’d to the GSLB Site IP. For internal GSLB, there’s no need to enter anything in the Public IP field. Click Create.
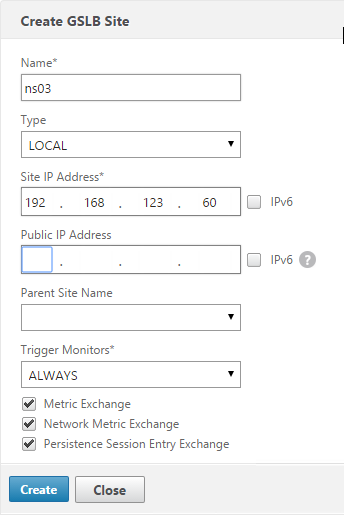
- Go back to System > Network > IPs and verify that the IP is now marked as a GSLB site IP. If you don’t see it yet, click the Refresh button.
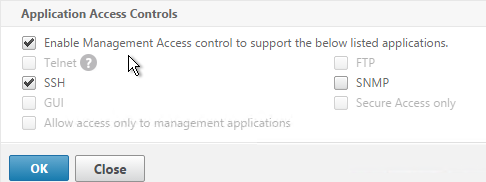
- If you want to use the GLSB Sync Config feature, then you’ll need to edit the GSLB site IP and enable Management Access.
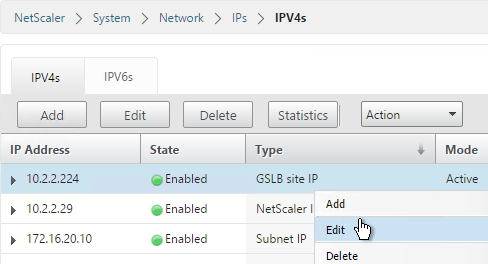
- When you enable Management Access on a dedicated GSLB site IP, SSH is already selected by default. That’s all you need.
- Go to the other appliance and also create the local GSLB site using its GSLB site IP and its public IP that is NAT’d to the GSLB site IP.
- In System > Network > IPs on the remote appliance, there should now be a GSLB site IP. This could be a SNIP. If GSLB Sync is desired, enable management access on that IP and ensure SSH is enabled.
- Now on each appliance add another GSLB Site, which will be the remote GSLB site.
- Enter a descriptive name and select REMOTE as the Site Type.
- Enter the other appliance’s actual GSLB Site IP as configured on the appliance. This IP does not need to be reachable.
- In the Public IP field, enter the public IP that is NAT’d to the GSLB Site IP on the other appliance. For MEP, TCP 3009 must be open to this IP from the local GSLB Site IP. For GSLB sync, TCP 22, and TCP 3008 must be open to this IP from the local NSIP. Click Create.
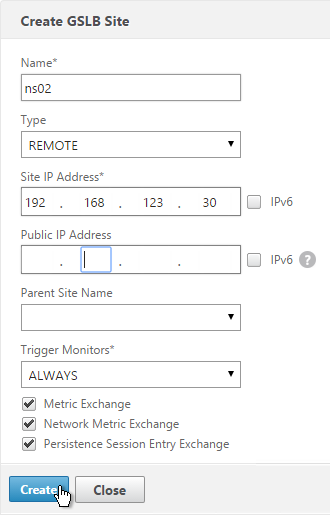
- Repeat on the other appliance.
- MEP will not function yet since the NetScalers are currently configured to communicate unencrypted on TCP 3011. To fix that, on the left, expand System, expand Network and click RPC.
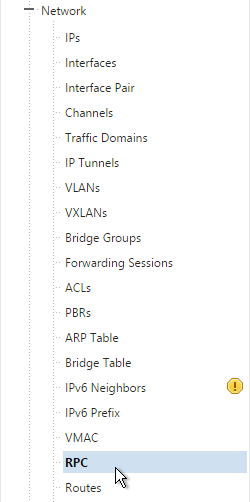
- On the right, edit the new RPC address (the other site’s GSLB Site IP) and click Open.
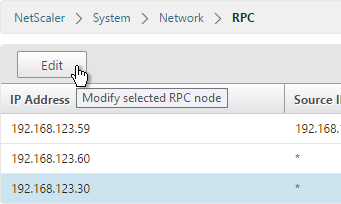
- On the bottom, check the box next to Secure.
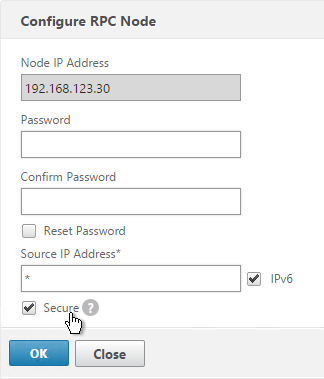
- In NetScaler 11.0 build 64 or newer, if your GSLB Site IP is not a SNIP then you’ll need to change the RPC Node to use the local GSLB Site IP as the source IP. Uncheck IPv6 first. Then enter the local GSLB Site IP. Click OK when done.
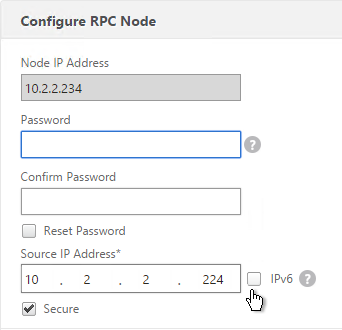
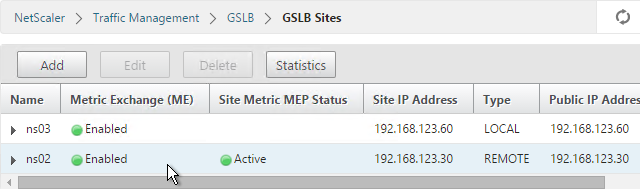
- Do the same thing on the other appliance.
- If you go back to GSLB > Sites, you should see it as active.
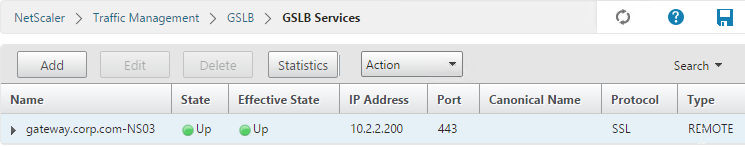
GSLB Services
GSLB Services represent the IP addresses that are returned in DNS Responses. DNS Query = DNS name. DNS Response = IP address.
GSLB should be configured identically on both NetScalers. Since you have no control over which NetScaler will receive the DNS query, you must ensure that both NetScalers are giving out the same DNS responses.
Create the same GSLB Services on both NetScalers:
- Start on the appliance in the primary data center. This appliance should already have a traffic Virtual Server (NetScaler Gateway, Load Balancing, or Content Switching) for the DNS name that you are trying to GSLB enable.
- On the left, expand Traffic Management > GSLB and click Services.
- On the right, click Add.
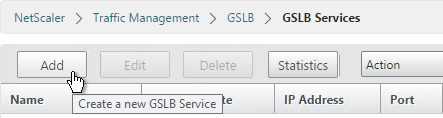
- The service name should be similar to the DNS name that you are trying to GSLB. Include the site name in the service name.
- Select the LOCAL Site.
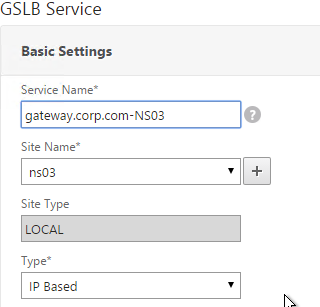
- On the bottom part, select Virtual Servers and then select a Virtual Server that is already defined on this appliance. It should automatically fill in the other fields. If you see a message asking if you wish to create a service object, click Yes.
- Scroll up and make sure the Service Type is SSL. It’s annoying that NetScaler doesn’t set this drop-down correctly.
- The Public IP field contains the actual IP Address that the GSLB ADNS service will hand out. Make sure this Public IP is user accessible. It doesn’t even need to be a NetScaler owned IP.
- Scroll down and click OK.
- If the GSLB Service IP is a VIP on the local appliance, then GSLB will simply use the state of the local traffic Virtual Server (Load Balancing, Content Switching, or Gateway). If the GSLB Service IP is a VIP on a remote appliance, then GSLB will use MEP to ask the other appliance for the state of the remote traffic Virtual Server. In both cases, there’s no need to bind a monitor to the GSLB Service.
- However, you can also bind monitors directly to the GSLB Service. Here are some reasons for doing so:
- If the GSLB Service IP is a NetScaler-owned traffic VIP, but the monitors bound the traffic Virtual Server are not the same ones you want to use for GSLB. When you bind monitors to the GSLB Services, the monitors bound to the traffic Virtual Server are ignored.
- If the GSLB Service IP is in a non-default Traffic Domain, then you will need to attach a monitor since GSLB cannot determine the state of Virtual Servers in non-default Traffic Domains.
- If the GSLB Service IP is not hosted on a NetScaler, then only GSLB Service monitors can determine if the Service IP is up or not.
- If you intend to do GSLB active/active and if you need site persistence then you can configure your GSLB Services to use Connection Proxy or HTTP Redirect. See Citrix Blog Post Troubleshooting GSLB Persistence with Fiddler for more details.
- Click Done.
- On the other datacenter NetScaler, create a GSLB Service.
- Select the REMOTE site that is hosting the service.
- Since the service is on a different appliance and not this one, you won’t be able to select it using the Virtual Servers option. Instead, select New Server.
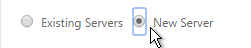
- For the Server IP, enter the actual VIP configured on the other appliance. This local NetScaler will use GSLB MEP to communicate with the remote NetScaler to find a traffic Virtual Server with this VIP. The remote NetScaler respond if the remote traffic Virtual Server is up or not. The remote Server IP configured here does not need to be directly reachable by this local appliance. If the Server IP is not owned by either NetScaler, then you will need to bind monitors to your GSLB Service.
- In the Public IP field, enter the IP address that will be handed out to clients. This is the IP address that users will use to connect to the service. For Public DNS, you enter a Public IP that is usually NAT’d to the traffic VIP. For internal DNS, the Public IP and the Server IP are usually the same.
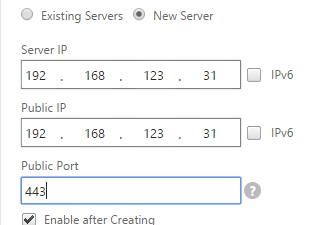
- Scroll up and change the Service Type to match the Virtual Server defined on the other appliance..
- Click OK.
- Just like the other appliance, you can also configure Site Persistence and GSLB Service Monitors. Click Done when done.
- Create more GSLB Services, one for each traffic VIP. GSLB is useless if there’s only one IP address to return. You should have multiple IP addresses (VIPs) through which a web service (e.g. NetScaler Gateway) can be accessed. Each of these VIPs is typically in different datacenters, or on different Internet circuits. The mapping between DNS name and IP addresses is configured in the GSLB vServer, as detailed in the next section.
GSLB Virtual Server
The GSLB Virtual Server is the entity that the DNS name is bound to. GSLB vServer then gives out the IP address of one of the GSLB Services that is bound to it.
Configure the GSLB vServer identically on both appliances:
- On the left, expand Traffic Management > GLSB, and click Virtual Servers.
- On the right, click Add.
- Give the GSLB vServer a descriptive name. For active/active, you can name it the same as your DNS name. For active/passive, you will create two GSLB Virtual Servers, one for each datacenter, so include Active or Passive in the Virtual Server name.
- Click OK.
- If you intend to bind multiple GSLB Services to this GSLB vServer, then you can optionally check the box for Send all “active” service IPs. By default, GSLB only gives out one IP per DNS query. This checkbox always returns all IPs, but the IPs are ordered based on the GSLB Load Balancing Method and/or GSLB Persistence.
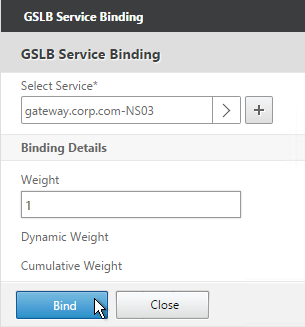
- On the right, in the Advanced Settings column, click Service.
- On the left, click where it says No GSLB Virtual Server to GSLBService Binding.
- Click the arrow next to Click to select.
- Check the box next to an existing GSLB Service and click Select. If your GSLB is active/passive then only bind one service.
- If your GSLB is active/active then bind multiple GSLB Services. Also, you’d probably need to configure GSLB persistence (Source IP or cookies).
- Click Bind.
- On the right, in the Advanced Settings column, click Domains.
- On the left, click where it says No GSLB Virtual Server Domain Binding.
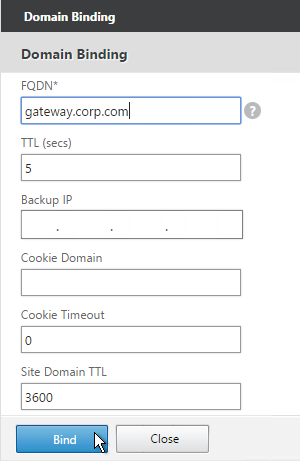
- Enter the FQDN that GSLB will resolve.
- If this GSLB is active/passive, there are two options:
- Use the Backup IP field to specify the IP address that will be handed out if the primary NetScaler is inaccessible or if the VIP on the primary appliance is marked down for any reason.
- Or, create a second GSLB Virtual Server that has the passive GSLB service bound to it. Don’t bind a Domain to the second GSLB Virtual Server. Then edit the Active GSLB Virtual Server and use the Backup Virtual Server section to select the second GSLB Virtual Server.
- Click Bind.
- If this is active/active GSLB, you can edit the Method section to enable Static Proximity. This assumes the Geo Location database has already been installed on the appliance.
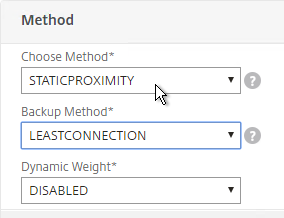
- Also for active/active, if you don’t want to use Cookie-based persistence, then you can use the Persistence section to configure Source IP persistence.
- Click Done.
- If you are configuring active/passive using the backup GSLB Virtual Server method, create a second GSLB Virtual Server that has the passive GSLB service bound to it. Don’t bind a Domain to the second GSLB Virtual Server. Then edit the Active GSLB Virtual Server and use the Backup Virtual Server section to select the second GSLB Virtual Server.
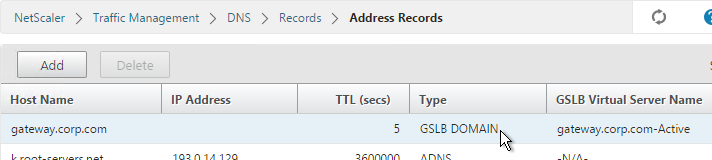
- On the left, if you expand Traffic Management > DNS, expand Records and click Address Records, you’ll see a new DNS record for the GSLB domain you just configured. Notice it is marked as GSLB DOMAIN.
- Configure identical GSLB Virtual Servers on the other NetScaler appliance. Both NetScalers must be configured identically.
- You can also synchronize the GSLB configuration with the remote appliance by going to Traffic Management > GSLB.
- On the right, click Synchronize configuration on remote sites.
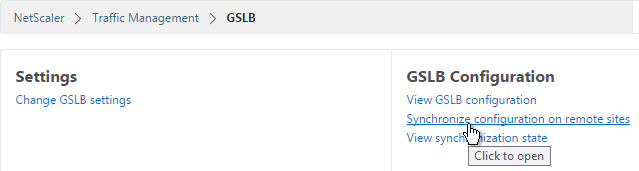
- Use the check boxes on the top, if desired. It’s usually a good idea to Preview the changes before applying them. Then click OK to begin synchronization.
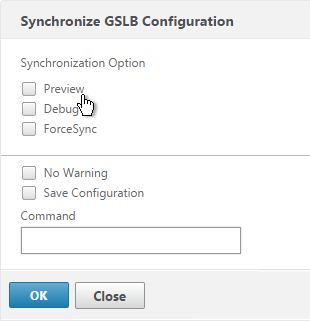
Some notes regarding GSLB Sync:
- It’s probably more reliable to do it from the CLI by running sync gslb config and one of the config options (e.g. -preview).
- GSLB Sync runs as a script on the BSD shell and thus always uses the NSIP as the source IP.
- GSLB Sync connects to the remote GSLB Site IP on TCP 3008 (if RPC is Secure) and TCP 22.
Test GSLB
- To test GSLB, simply point nslookup to the ADNS services and submit a DNS query for one of the DNS names bound to a GSLB vServer. Run the query multiple times to make sure you’re getting the response you expect.
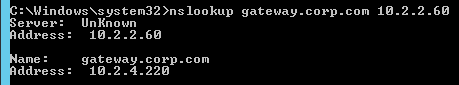
- Both NetScaler ADNS services should be giving the same response.
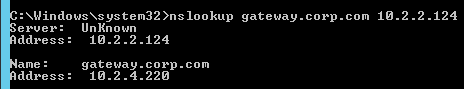
- To simulate a failure, disable the traffic Virtual Server.
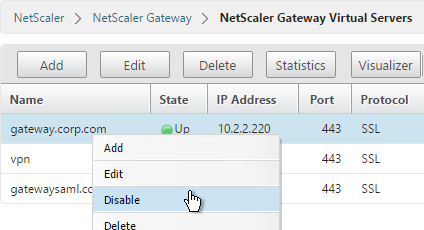
- Then the responses should change. Verify on both ADNS services.
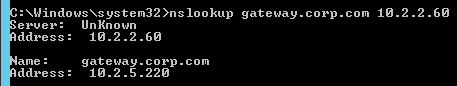
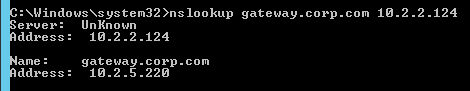
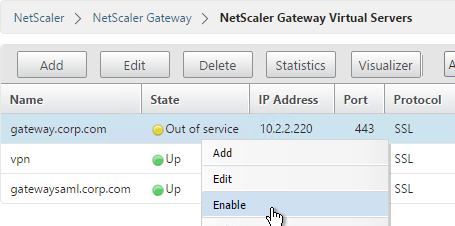
- Re-enable the traffic Virtual Server, and the responses should return to normal.


DNS Delegation
If you are enabling GSLB for the domain gateway.corp.com, you’ll need to create a delegation at the server that is hosting the corp.com DNS zone. For public GSLB, you need to edit the public DNS zone for corp.com.
DNS Delegation instructions will vary depending on what product host’s the public DNS zone. This section details Microsoft DNS, but it should be similar in BIND or web-based DNS products.
There are two ways to delegate GSLB-enabled DNS names to NetScaler ADNS:
- Delegate the individual record. For example, delegate gateway.corp.com to the two NetScaler ADNS services (gslb1.corp.com and gslb2.corp.com).
- Delegate an entire subzone. For example, delegate the subzone gslb.corp.com to the two NetScaler ADNS services. Then create a CNAME record in the parent DNS zone for gateway.corp.com that is aliased to gateway.gslb.corp.com. When DNS queries make it to NetScaler, they will be for gateway.gslb.corp.com and thus gateway.gslb.corp.com needs to be bound to the GSLB Virtual Server instead of gateway.corp.com. For additional delegations, simply create more CNAME records.
This section covers the first method – delegating an individual DNS record:
- Run DNS Manager.
- First, create Host Records pointing to the ADNS services running on the NetScalers in each data center. These host records for ADNS are used for all GSLB delegations no matter how many GSLB delegations you need to create.
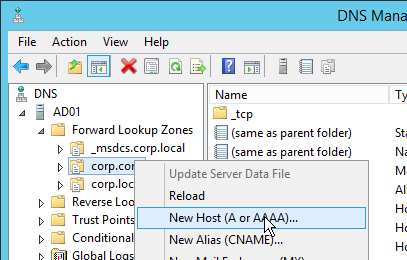
- The first Host record is gslb1 (or similar) and should point to the ADNS service (Public IP) on one of the NetScaler appliances.
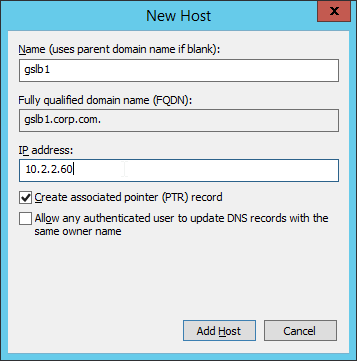
- The second Host record is gslb2 and should point to the ADNS Service (public IP) on the other NetScaler appliance.
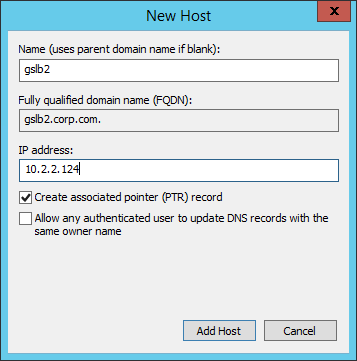
- If you currently have a host record for the service that you are delegating to GSLB (gateway.corp.com), delete it.
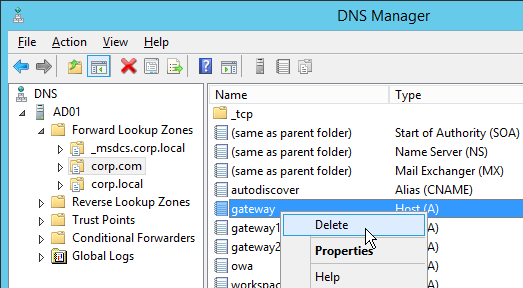
- Right-click the parent DNS zone and click New Delegation.
- In the Welcome to the New Delegation Wizard page, click Next.
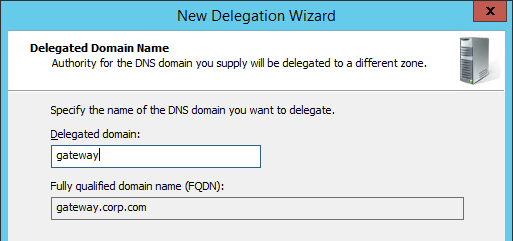
- In the Delegated Domain Name page, enter the left part of the DNS record that you are delegating (e.g. gateway). Click Next.
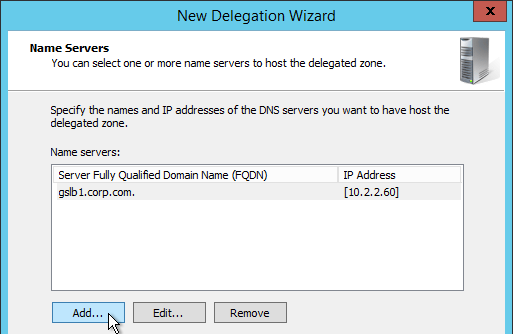
- In the Name Servers page, click Add.
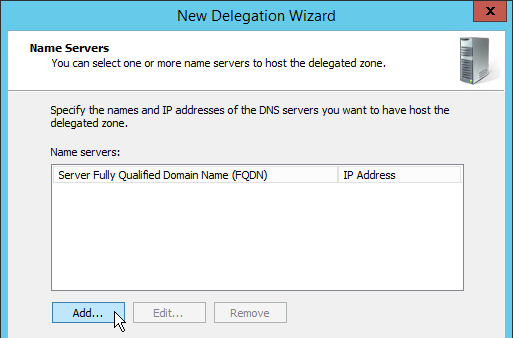
- This is where you specify gslb1.corp.com and gslb2.corp.com. Enter gslb1.corp.com and click Resolve. Then click OK. If you see a message about the server not being authoritative for the zone, ignore the message.
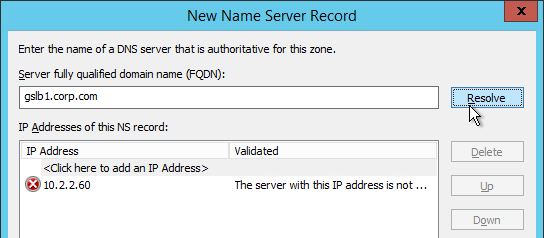
- Then click Add to add the other GSLB ADNS server.
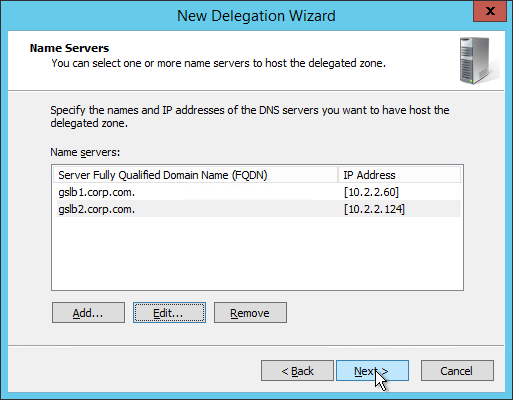
- Once both ADNS servers are added to the list, click Next.
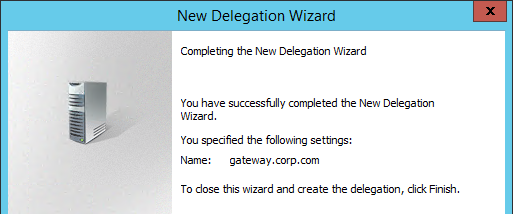
- In the Completing the New Delegation Wizard page, click Finish.
- If you run nslookup against your Microsoft DNS server, it will respond with Non-authoritative answer. That’s because it got the response from NetScaler and not from itself.
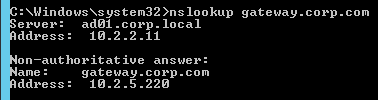
That’s all there is to it. Your NetScalers are now DNS servers. For active/passive, the NetScalers will hand out the public IP address of the primary data center. When the primary data center is not accessible, GSLB will hand out the GSLB Service IP bound to the Backup GSLB vServer.
Geo Location Database
If you want to use DNS Policies or Static Proximity GSLB Load Balancing or Responders based on user’s location, import a geo location database.
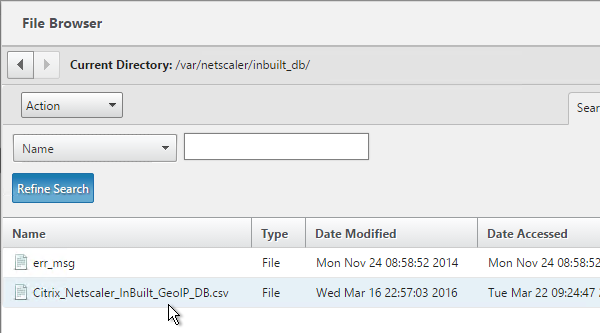
NetScaler 11 has a built-in database at /var/netscaler/inbuilt_db/ that you can use. Or you can download a database. Common free databases are:
- GeoLite Legacy – http://dev.maxmind.com/geoip/legacy/geolite/
- IP2Location Lite – http://lite.ip2location.com/
For IP2Location, see the blog post Add IP2Location Database as NetScaler’s Location File for instructions on how to import.
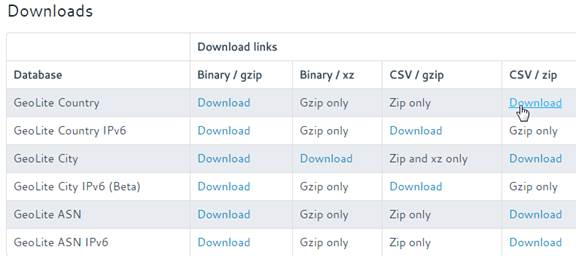
To Download GeoLite Legacy:
- Download the GeoLite Country database CSV from http://dev.maxmind.com/geoip/legacy/geolite/.
- Note: GeoLite City is actually two files that must be merged as detailed at Citrix Blog Post GeoLite City as NetScaler location database. GeoLite Country doesn’t need any preparation.
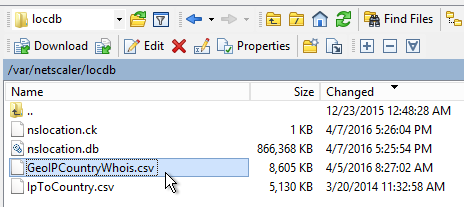
- Upload the extracted database (.csv file) to the NetScaler appliance at /var/netscaler/locdb.
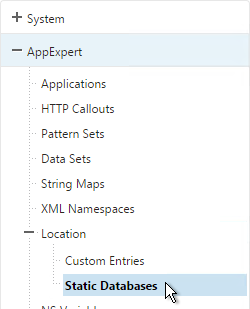
To import the Geo database (including the built-in database):
- In the NetScaler GUI, on the left, expand AppExpert, expand Location and click Static Database (IPv4).
- On the right, click Add.
- Change the Import From selection to File.
- Click Browse.
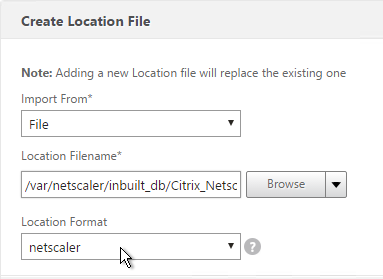
- For the built-in database, browse to /var/netscaler/inbuilt_db/ and open Citrix_NetScaler_InBuild_GeoIP_DB.csv.
- Or browse to the Geo Location database file you uploaded and open it.
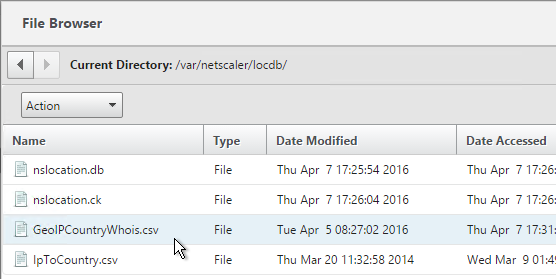
- In the Location Format field, if using the built-in database, select netscaler.
- If using GeoLite Country, select geoip-country.
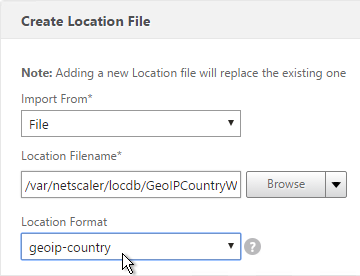
- Click Create.
- When you open a GSLB Service, the public IP will be translated to a location.
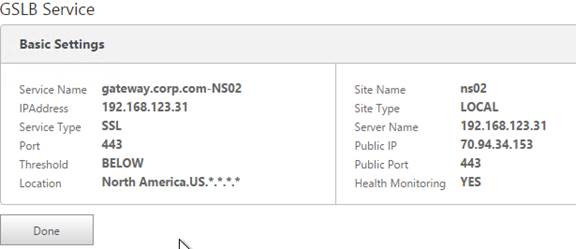
You can use the Geo locations in a DNS Policy, static proximity GSLB Load Balancing, or Responders:
- Citrix Knowledgebase article CTX130701 – How to Block Access to a Website Using a Location Database Based on User’s Country
- Neil Spellings blog post – Using Netscaler HTTP callouts for real-time GeoIP and anonymous proxy detection
- Citrix Docs.citrix.com – Overriding Static Proximity Behavior by Configuring Preferred Locations
Hi Karl,
I’ve small query on GeoIP database, If GeoIP database is configure on the Netscaler but GSLB is NOT configured on the Netscalers
In that case, does Netscalers still use this GeoIP database to determine any specific IP range mentioned in the database?
appreciate if you could advise
I think it shows the Geo location of LB Servers. You can use Geo location in your policy expressions.
Where is part 2 to GSLB, how to configure (citrix blog).
Hi Carl , Can we us Netscaler as GEO DNS server for work load outside of it?
Of course. You just need to configure monitoring of the GSLB Services. However, site cookie persistence won’t work since HTTP traffic isn’t going through a NetScaler.
Hi Carl, what are your thoughts on using DNS proxy instead of ADNS for GSLB? I am thinking it would be ok for internal, but for external am wondering if it would be secure enough? Especially if the GSLB domain used was that of an existing AD domain and DNS zone that internal servers use & have records present. Would these records be accessible for querying on the outside? I’d like to make sure they are not.
DNS Proxy just forwards DNS requests to your DNS servers. DNS record availability is based on whatever records you have on the DNS servers.
Thanks for your reply Carl. I am no security expert, but based on the DNS forwarding and availability of whatever records are present, it sounds like the answer is yes – to an External user being able to query all records from the outside. Therefore it sounds like it’s not secure or a good idea to use DNS Proxy with External GSLB? Is that a fair assumption?
You can use DNS Policies (NetScaler or Microsoft) to control availability of records from various client IP addresses.
Just read there is a default limit of 255 concurrent DNS requests on a client connection. These requests being ones the NetScaler has forwarded to the name servers. This limit exists to help protect the name servers if a hostile client attempts a DDos attack by sending a flood of DNS requests:
https://docs.citrix.com/en-us/netscaler/10-5/ns-tmg-wrapper-10-con/ns-tmg-dns-gen-wrapper-10-con/ns-tmg-dns-config-ns-prxy-srvr-con.html
This is good to know but looking more secure to go with ADNS when doing External GSLB.
I always delegate individual DNS names to ADNS instead of doing DNS Proxy. But I have seen DNS Proxy at some customers.
Hi Carl , I have a question around GSLB Sync. Can we make NSIP Sync with DMZ IP address(Private Natted IP address) of GSLB site IP rather Public IP address? Since it is an information sharing i ,thought it doesn’t necessarily go through Public path. Please let me know.
Hi Carl,
my customer have now, 2 MPX8200, with this balance server in Front-end environment.
Thi MPX are configure in HA active/standby.
Now the customer want to create a little site for D.R.
For the remote site, have buy 2 licence of VPX .
Is possible create un GSLB , mixing fisical and virtual balancer?
In the event that we wanted to create two Virtual Domain in MPX and of course do the same in VPX, we have problems?
The MPX are over dimensioned, the traffic is currently very little, but in case you must also balance the backend is sure to be greater but if traffic will intra balancer and not from the outside.
Thanks in advance
Gino
Yes, GSLB MEP works across different NetScaler models.
Hi Carl
Is it possible to configure a GSLB virtual server to only supply internal addresses? I setup multiple vServers most for internal IPs. Others for external use, load balancing external DNS vips. Others that provide internal IPs for internal users and Public IP for external users (DNS views)
Is is possible to have a view that is only internal? DNS view internal returns internal IP, but externally (nothing)
Thanks in advance
~Phil B
Maybe you can create a DNS Policy for the internal names with a Drop action. The policy would allow internal DNS servers but drop all others.
Or, my preference is to have separate NetScaler appliances for internal vs external.
This may start a bigger question/discussion, but while thinking about this more… cant the Netscaler be delagated to multiple sub domains. Would it be just as simple to have some vServer domains responding to multiple sub domains
External DNS delagate to gslb.domain.com
Hostname -> CNAME to hostname.gslb.domain.com
Internal DNS delegate to gslb-internal.domain.com
Hostname -> CNAME to hostname.gslb-internal.domain.com
Just thinking… Your thoughts?
Also I’m not an expert on security as it relates to DNS, but Is this even a real world problem? Kind of “security by obscurity”.
Of course. But if you point nslookup to your ADNS IP and enter the internal DNS name, it will respond.
Carl,
I appreciate your responses. I wanted to follow up with you on what I ended up going with, as it might help others I worked with my team and we ended up using a Responder Policy along with a Pattern Set to manage future internal GSLB.
So… the responder will match any non-internal IP and a list of FQDNs that are internal (pattern set). the repsonder will then respond with an emply DNS response (EDR). Similar to a request for a non-existing name. A DROP action “would” work, but force the client to time out because no response is given, as well as possibly “leak” that something may be there and we’re simply not giving it out.
add policy patset GSLB_INTERNAL
bind policy patset GSLB_INTERNAL internalHostname.gslb.domain.com -index 1
add responder action DNS_Empty_Response respondwith DNS.NEW_RESPONSE
add responder policy GSLB_DNS_Empty_Response “(!(CLIENT.IP.SRC.IN_SUBNET(10.0.0.0/8)||CLIENT.IP.SRC.IN_SUBNET(192.0.0.0/16)||CLIENT.IP.SRC.IN_SUBNET(172.0.0.0/12)) && DNS.REQ.QUESTION.DOMAIN.CONTAINS_ANY(\”GSLB_INTERNAL\”))” DNS_Empty_Response
bind responder global GSLB_DNS_Empty_Response 100 END -type DNS_REQ_DEFAULT
HI Carl/Phil,
You might want to update your GSBL policy. You currently have CLIENT.IP.SRC.IN_SUBNET(192.0.0.0/16) listed but I believe you meant to have CLIENT.IP.SRC.IN_SUBNET(192.168.0.0/16) instead.
This might be a security issue for people implementing your responder policy.
Carl-
Question: I set up GSLB for Active/Passive sites. I realized after the fact, I entered the subnet as a /24 on my passive site and should have entered a /23. Is there a way to change this direct route to reflect a /23 without rebuilding GSLB? THe route is a Direct route so I am unable to remove it from the GUI and unable to run a “remove route” from CLI.
Thank you for any help you can provide-
Micah
Direct routes come from SNIPs. You’d have to unbind the SNIP from VLAN. Then delete the SNIP and re-add it.
Hi Carl, I have never configured GSLB before and just did it using your article. It is perfect!
Can you give me a hint please with this minor issue:
I am trying to GSLB 2 NetScaler Gateways and when I disable Virtual Server on my first NetScaler and trying to access my URL (https://gate.mysite.com) it just redirects me to https://10.10.10.12/vpn/index.html (which is my second NetScaler Virtual Server IP) Do you know why this could happen?
I haven’t configured DNS delegation yet, but that shouldn’t cause the issue.
Thank you.
Can you use your Browser’s developer tools to trace the HTTP traffic to see where the redirect is coming from?
Do you have a Responder on your Gateway?
Otherwise, I’ve never seen it redirect to an IP before.
Thank you Carl for the response.
Hi Carl – This is really awesome and great documents in your website. Thanks for the help with such detailed information which is not available straight elsewhere.
I have a question on GSLB, Is this possible to use the same public IP used for NetScaler Gateway VIP to enable the GSLB configuration. We are having 2 public IPs (one per DC site) and NATed to NetScaler GW VIP of respective DCs. I just wanted to know if it is possible to use the same Public IP again (NATed to SNIP configured for ADNS service) as the ports are different. I am yet to discuss with my networking team if they can enable 1 Pubic IP NATed to few Internal IPs with different ports. I wanted to take your great views as it will help to circumvent multiple public IP requirements.
On a firewall you can configure Port Address Translation instead of Network Address Translation. But the IPs on the NetScaler are still separate.
Thanks and much appreciated for that Carl
Thanks Carl,
That’s where the problem is. I already have a Storefront monitor bound to Storefront Vserver. I can’t have multiple monitors bound to a Vserver?
Regards
You can definitely bind multiple monitors to a vServer. Try it. By default, if any one of the monitors is down then the vSever goes down.
Thanks Carl, for the reply. I really need to set up Storefront LB Vserver to monitor the delivery controllers (which are set up as a service and LB vip on the same netscaler) so that if either of the delivery controller service or vip goes down then storefront LB vserver should show down as well. in this case the GSLB will point to Passive DC.
Regards
Create a new monitor that contains the VIP of your Delivery Controller VIP. Bind this monitor to your StoreFront LB vServer. Monitors can have IP addresses in them.
Hi Carl,
My GSLB is pointing to 2 storefront vips in 2 different DCs in active passive mode. The storefront servers then point to a VIP on the Netscaler for delivery controllers. Is it possible that if the delivery controller at one site is down the GSLB points to other DC.
Are you asking if the delivery controller is down then “StoreFront” points to the other DC?
You can easily setup an active/passive LB vServer. You already have the active LB vServer. Create a new LB vServer that is non-addressable and points to the other datacenter. Then open the Active LB vServer, add the Protection section, and select your passive LB vServer.
Hi Carl, Do you have a config example for active/passive GSLB load balancing for NS v11. Appreciate if you could point to the right direction Please.
Isn’t that the subject of this page? Or are you looking for CLI commands?
Thanks Carl for very useful information. I have a question on GSLB. What will hapopen if the MEP on tcp 3009 goes down between 2 netscalers in 2 different DCs. Will the GSLB stop working or only GSLB services for remote site will not be accessible. Also in your above example how the dns resolution will work. Will the dns server always send the first IP address back to client DNS request or will it round robin.
If MEP goes down, and if you don’t have monitors attached to GSLB services, then the remote GSLB services will go down and the local ADNS will stop giving out those IPs.
The delegating DNS servers will delegate to all NetScaler ADNS services. One of them is chosen at random.
GSLB can be configured to return multiple IPs for a GSLB vServer. The order of the list depends on the load balancing algorithm.
Carl, do you know if its possible to do double hop config to GSLB?
I’m not sure what that means. Are you referring to the GSLB Service monitors? Or do you mean MEP? You can bind monitors to the GSLB Services to monitor almost anything.
NetScaler Gateway in a Double-Hop DMZ: https://docs.citrix.com/en-us/netscaler-gateway/10-5/ng-deployment-wrapper-con/ng-deploy-double-hop-con.html
My question is if it would be possible to have the second hop gateways running GSLB. I know this might be a pretty unique use case, but in a secure production environment, it could be a solution to secure
multiple non-internet connected plants for a worldwide deployment.
Are you asking if the 1st Gateway can use GSLB to resolve a DNS name for the 2nd Gateway’s IP? For double-hop, I usually direct ICA traffic to the 2nd Gateway in the same datacenter. Are you wanting that if the 2nd Gateway is down in the local datacenter then GSLB fails over to the 2nd Gateway in a different datacenter? I don’t see why that wouldn’t work.
Or are you simply asking if GSLB service can run on the 2nd Gateway? It can run on every appliance if you want. It’s just DNS.
Hi, Carl! Looooove your stuff! Budding NS architect here with two questions:
1. What is the functional difference between defining a Backup IP in the GSLB Vsrv, and creating and defining a Backup Virtual Server for it? Is there an advantage to one strategy over the other, or is one simply a hold-over from earlier versions of the software? Most docs and help guides I’ve seen simply offer the two options as equals without going into any detail. The only thing I’ve come up with so far is defining separate virtual servers allows you to create and bind separate services that could use slightly different parameters, but I’m not entirely sure why you’d do that.
2. When doing GSLB for a CSW configuration, how do you cleanly ensure the health of the CSW VIP (which is always UP unless you get into RHI state settings) actually reflects the health of the content it front-ends? And, related, is there a way to only fail over part of a CSW structure, or can you only GSLB fail over the entire name space?
Thanks so much for all your work! I rely on it ~a lot~! 🙂
1. Frankly, I don’t know the difference. I used to do Backup IP but all citrix.com documentation refers to two vServers so I switched to that method instead.
2. HTTP data is not included in DNS (GSLB) requests. So you’ll have the situation of the user connecting to the “wrong” site. In that case, the “wrong” site needs to either do a proxy or do a redirect. Both have their pros and cons. For proxy, you setup the LB VIP in active/passive. For redirect, you configure a Redirect URL if the LB services are down.
Yea, the Primary/Secondary virtual server structure made the most sense to my brain, but I just wasn’t sure whether I was shooting myself in the foot down the road by going one route or the other.
And that raises an interesting point to me on #2. I’ve been looking at GSLB as a black/white kind of setup, where I’ve either truly enabled our services to fail across sites using *just* GSLB, or I’ve not. But really, there’s an in-between of sorts: GSLB to fail over the entire name space in the event of a real calamity, but also the use of backup virtual servers and the like at different levels of the structure as needed. I guess I worried that mixing the two strategies was overly confusing, but I’m not sure how you’d get around some scenarios without doing it. 😮
Hello Carl, you said “NetScaler 11.0 build 64 supports GSLB in Admin Partitions so this might a workaround for single-appliance deployments.” but GSLB settings is not present in the admin partition after adding a partition. Did I miss anything? Thanks.
Hi Didier, I could have sworn I read that in the release notes. Maybe wishful thinking? I adjusted the text accordingly and added a workaround for same public/internal DNS name on one appliance. https://docs.citrix.com/en-us/netscaler/11/system/admin-partition/admin-partition-config-types.html shows the new partition features in 11.0 build 64.
Thank you very much for this Carl. I was hung up with DNS Delegation until I came across your post. I was wondering though, which methods you use for a true active/passive GSLB. I do not want my DR site’s IP to resolve unless the main one is completely down.
The GSLB vServer config is straightforward. However, the hard part is configuring the monitors so it fails over when you want it to and doesn’t when you don’t want it to. A common scenario is to failover when main site Internet is down and routing MEP through the Internet should handle that scenario.
I found that LEASTRESPONSETIME worked the best for me after some experimentation on the GSLB Virtual Server’s. This was after looking over some more granular details on the load balancing methods algorithms used which I found here in great detail. https://kb.wisconsin.edu/images/group9/13201/NS-Load_Balance_Methods.pdf