Navigation
- Change Log
- GSLB Planning
- GSLB Wizard
- GSLB Infrastructure – one time setup
- GSLB Configuration – Repeatable Steps
💡 = Recently Updated
Change Log
- 2023 Mar 30 – GSLB vServer – added GSLB Service binding Order method of doing active/passive in 13.1 and newer
- 2021 Jan 29 – RPC nodes – added link to Citrix CTX292743 Configuration Sync, Propagation and MEP Propagation Might Fail After Upgrade to 13.0 64.x\12.1 61.x
- 2020 Feb 27 – updated link to Citrix Tech Zone Troubleshooting Citrix GSLB MEP Cheat Sheet
- 2019 Mar 6 – Geo Location Database – added link to Citrix Github Citrix-ADC-GSLB-GeoIP-Conversion-Tool
- 2019 Feb 12 – Metric Exchange Protocol – added link to CTX244517 Citrix ADC Troubleshooting GSLB MEP and Sync Cheat Sheet
- 2019 Feb 4 – DNS Delegation – added link to Citrix CTX241493 Citrix Response on DNS Flag Day
- 2019 Jan 30 – ADNS – added ADNS_TCP
- 2018 Dec 18 – updated screenshots for ADC 12.1
- Geo location database – added link to Retrieve location details from user IP address using geolocation database at Citrix Docs
- 2018 July 1 – Geo Location Database – added link to CTX235799 NetScaler data formats for Location Database Import
- 2018 Mar 12 – in Use Geo Locations section, added info from CTX232884 Policies with GSLB Wildcard Location expressions not getting a hit on build 11.1-53.11 and above
GSLB Planning
GSLB is nothing more than DNS. GSLB receives a DNS query, and then GSLB sends back an IP address, which is exactly how a DNS server works. The user then connects to the returned IP, which doesn’t even need to be on a NetScaler ADC.
GSLB can do some things that DNS servers can’t do:
- Don’t give out an IP address unless it is UP (monitoring)
- If the active IP address is down, then give out the passive IP address (active/passive) instead
- Give out the IP address that is closest to the user (proximity load balancing)
- Give out different IPs for internal users vs external users (DNS View)
GSLB is only useful if you have a single DNS name that could resolve to two or more IP addresses. If there’s only one IP address, then use normal DNS instead.
Citrix Blog Post Global Server Load Balancing: Part 1 explains how DNS queries work and how GSLB fits in.
Citrix has a good DNS and GSLB Primer.
When configuring GSLB, don’t forget to ask “where is the data?”. See Citrix Blog Post XenDesktop, GSLB & DR – Everything you think you know is probably wrong!
GSLB Configuration Overview
GSLB Configuration can be split between one-time steps for GSLB infrastructure, and repeatable steps for each GSLB-enabled DNS name.
One-time GSLB Infrastructure configuration
- Create ADNS listener on each ADC pair – DNS clients send DNS queries to the ADNS listeners. GSLB resolves a DNS query into an IP address, and returns the IP address in the DNS response.
- Create GSLB Sites (aka MEP Listener) – GSLB Sites usually correspond to different datacenters. GSLB Sites are also the IP address endpoints for Citrix ADC’s proprietary Metric Exchange Protocol (MEP), which is used by GSLB to transmit proximity, persistence, and monitoring information.
- Import Static Proximity Database – Citrix ADC includes a database that can be used to determine the geographical location of an IP address. Or you can subscribe to a geolocation service, and import its database.
- Delegate DNS sub-zone to ADC ADNS – in the original DNS zone, create a new sub-zone (e.g. gslb.company.com), and delegate the sub-zone to all ADNS listeners.
Repeatable GSLB Configuration for each DNS name:
- Create one or more GSLB Services per DNS name, and per IP address response – each GSLB Service corresponds to a single IP address that can be returned in response to a DNS Query.
- Optionally, bind a Monitor to each GSLB Service. Monitors determine if the GSLB Service is up or not.
- Create a GSLB Virtual Server per DNS name
- Bind a DNS name to the GSLB Virtual Server.
- For active/active – bind multiple GSLB Services to the GSLB Virtual Server, configure a load balancing method (e.g. proximity), and configure site persistence.
- For active/passive – bind the active GSLB Service. Create another GSLB Virtual Server with passive GSLB Service and configure as Backup Virtual Server.
- Alternatively, NetScaler ADC 13.1 and newer let you bind GSLB Services in priority order. See Citrix Docs for details.
- Create CNAME records for each delegated DNS name – in the main DNS zone, create a CNAME that maps the original DNS name to the delegated sub-zone. For example, CNAME citrix.company.com to citrix.gslb.company.com.
You will create separate GSLB Services, separate GSLB Virtual Servers, and separate CNAMEs for each DNS name. If you have a bunch of DNS names that you want to GSLB-enable, then you’ll repeat these steps for each GSLB-enabled DNS name.
Each datacenter has a separate ADNS listener IP address. DNS is delegated to all GSLB ADNS Listener IPs, and any one of them can respond to the DNS query. Thus, all ADC pairs participating in GSLB should have the same Per-DNS name configuration.
One ADC appliance for both public DNS/GSLB and internal DNS/GSLB?
GSLB can be enabled both publically and internally. For public GSLB, configure it on DMZ ADC appliances, and expose the DNS listener to the Internet. For internal GSLB, configure it on separate internal ADC appliances/instances, and create an internal DNS listener.
Each ADC appliance only has one DNS table, so if you try to use the same ADC for both public DNS and internal DNS, then be aware that external users can query for internal GSLB-enabled DNS names.
- As described by Phil Bossman in the comments, you can use a Responder policy to prevent external users from reading internal DNS names.
add policy patset GSLB_INTERNAL bind policy patset GSLB_INTERNAL internalHostname.gslb.domain.com -index 1 add responder action DNS_Empty_Response respondwith DNS.NEW_RESPONSE add responder policy GSLB_DNS_Empty_Response "(!(CLIENT.IP.SRC.IN_SUBNET(10.0.0.0/8)||CLIENT.IP.SRC.IN_SUBNET(192.0.0.0/16)||CLIENT.IP.SRC.IN_SUBNET(172.0.0.0/12)) && DNS.REQ.QUESTION.DOMAIN.CONTAINS_ANY(\"GSLB_INTERNAL\"))" DNS_Empty_Response bind responder global GSLB_DNS_Empty_Response 100 END -type DNS_REQ_DEFAULT
One appliance resolving a single DNS name differently for internal and public
Let’s say you have a single DNS name citrix.company.com. When somebody external resolves the name, it should resolve to a public IP. When somebody internal resolves the name, it should resolve to an internal IP.
For internal GSLB and external GSLB of the same DNS name on the same ADC appliance, you can use DNS Policies and DNS Views to return different IP addresses depending on where users are connecting from. See Citrix CTX130163 How to Configure a GSLB Setup for Internal and External Users Using the Same Host Name.
If the Internet circuit in the remote datacenter goes down, then this should affect public DNS, since you don’t want to give out a public IP that isn’t reachable. But do you also want an Internet outage to affect internal DNS? Probably not. In that case, you would need different GSLB monitoring configurations for internal DNS and external DNS. However, if you have only a single GSLB Virtual Server with DNS Views, then you can’t configure different monitoring configurations for each DNS View.
To work around this limitation, create two separate GSLB Virtual Servers with different monitoring configurations. Internal DNS uses a CNAME record to reach the GSLB Virtual Server configured for internal monitoring:
- External citrix.company.com:
- Configure ADC GSLB for citrix.company.com.
- On public DNS, delegate citrix.company.com to the ADC DMZ ADNS services.
- Internal citrix.company.com:
- Configure ADC GSLB for citrixinternal.company.com or something like that.
- On internal DNS, create CNAME for citrix.company.com to citrixinternal.company.com
- On internal DNS, delegate citrixinternal.company.com to ADC internal ADNS services.
Remote Internet Monitoring
For public DNS/GSLB, you don’t want to give out a remote public IP address if that remote public IP address is not reachable. That means the local ADC will need to somehow determine if the remote datacenter has Internet connectivity or not. Here are some methods of verifying the remote Internet connection:
- Route GSLB Metric Exchange Protocol (MEP) across the Internet. If MEP goes down, then all IP addresses associated with the remote GSLB Site are assumed to be down, and thus the local ADC will stop giving out those remote IP addresses.
- Bind explicit monitors to each GSLB Service, and ensure the monitoring is routed across the Internet.
GSLB IP Addresses
GSLB is separate from data traffic. The GSLB IP addresses are separate from the IP addresses needed for data.
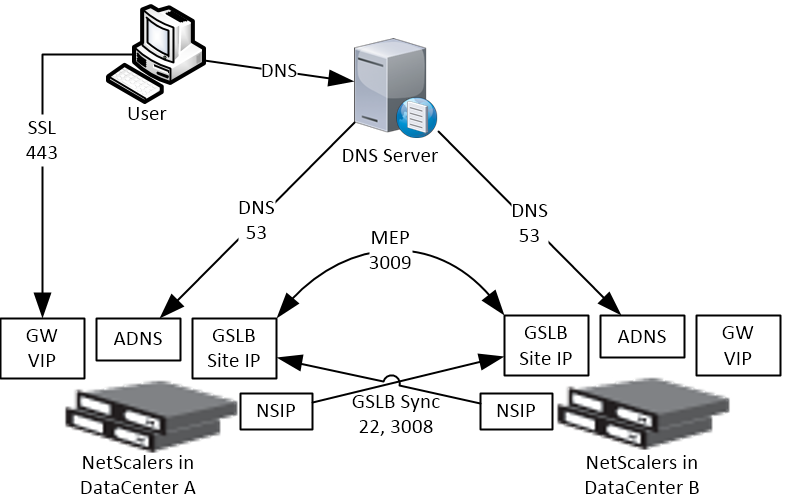
Some GSLB-specific IP Addresses are needed on each ADC pair:
- ADNS Listener IP: An ADC IP that listens for DNS queries.
- The ADNS listener IP is typically an existing SNIP on the appliance.
- For external DNS, create a public IP for the ADNS Listener IP, and open UDP 53 and TCP 53, so Internet-based DNS servers can access it.
- A single ADC appliance can have multiple ADNS listeners – typically one ADNS listener for public, and another ADNS listener for internal.
- GSLB Site IP / MEP listener IP: An ADC IP that will be used for ADC-to-ADC GSLB communication. This communication is called MEP or Metric Exchange Protocol. MEP transmits the following between GSLB-enabled ADC pairs: load balancing metrics, proximity, persistence, and monitoring.
- GSLB Sites – On ADC, you create GSLB Sites. GSLB Sites are the endpoints for the MEP communication. Each ADC pair is configured with the MEP endpoints for the local appliance pair, and all remote appliance pairs.
- TCP Ports – MEP uses port TCP 3009 or TCP 3011 between the ADC pairs. TCP 3009 is encrypted.
- The ADNS IP address can be used as the MEP endpoint IP.
- MEP endpoint can be any IP – The MEP endpoint IP address can be any IP address and does not need to be a SNIP or ADNS.
- One MEP IP per appliance – there can only be one MEP endpoint IP address on each ADC pair.
- Route MEP across Internet? – If you route MEP across the Internet, and if the MEP connection is interrupted, then Internet at one of the locations is probably not working. This is an easy way to determine if remote Internet is up or not. If you don’t route MEP across the Internet, then you’ll need to configure every remote-site GSLB Service with a monitor to ensure that the remote Internet is up.
- Public IPs for MEP Enpoints – if you route MEP across the Internet, then you’ll need public IPs for each publically-accessible MEP endpoint IP address.
- Public Port for MEP: Open port TCP 3009 between the MEP Public IPs. Make sure only the MEP IPs can access this port on the other ADC . Do not allow any other device on the Internet to access this port. Port 3009 is encrypted.
- GSLB Sync Ports: To use GSLB Configuration Sync, open ports TCP 22 and TCP 3008 (secure) from the NSIP (management IP) to the remote public MEP IP. The GSLB Sync command runs a script in BSD shell and thus NSIP is always the Source IP.
- In ADC 13.0 64.x and 12.1 build 61.x onwards, Secure is enabled by default. Citrix CTX292743 Configuration Sync, Propagation and MEP Propagation Might Fail After Upgrade to 13.0 64.x\12.1 61.x
- Public IP Summary: In summary, for public GSLB, if MEP and ADNS are listening on the same IP, then you need one new public IP that is NAT’d to the DMZ IP that is used for ADNS and MEP (GSLB Site IP).
- Each datacenter has a separate public IP.
- DNS is delegated to all public ADNS IP listeners.
GSLB Wizard
NetScaler 12 and Citrix ADC 12.1 and newer have a GSLB Wizard at Traffic Management > GSLB.
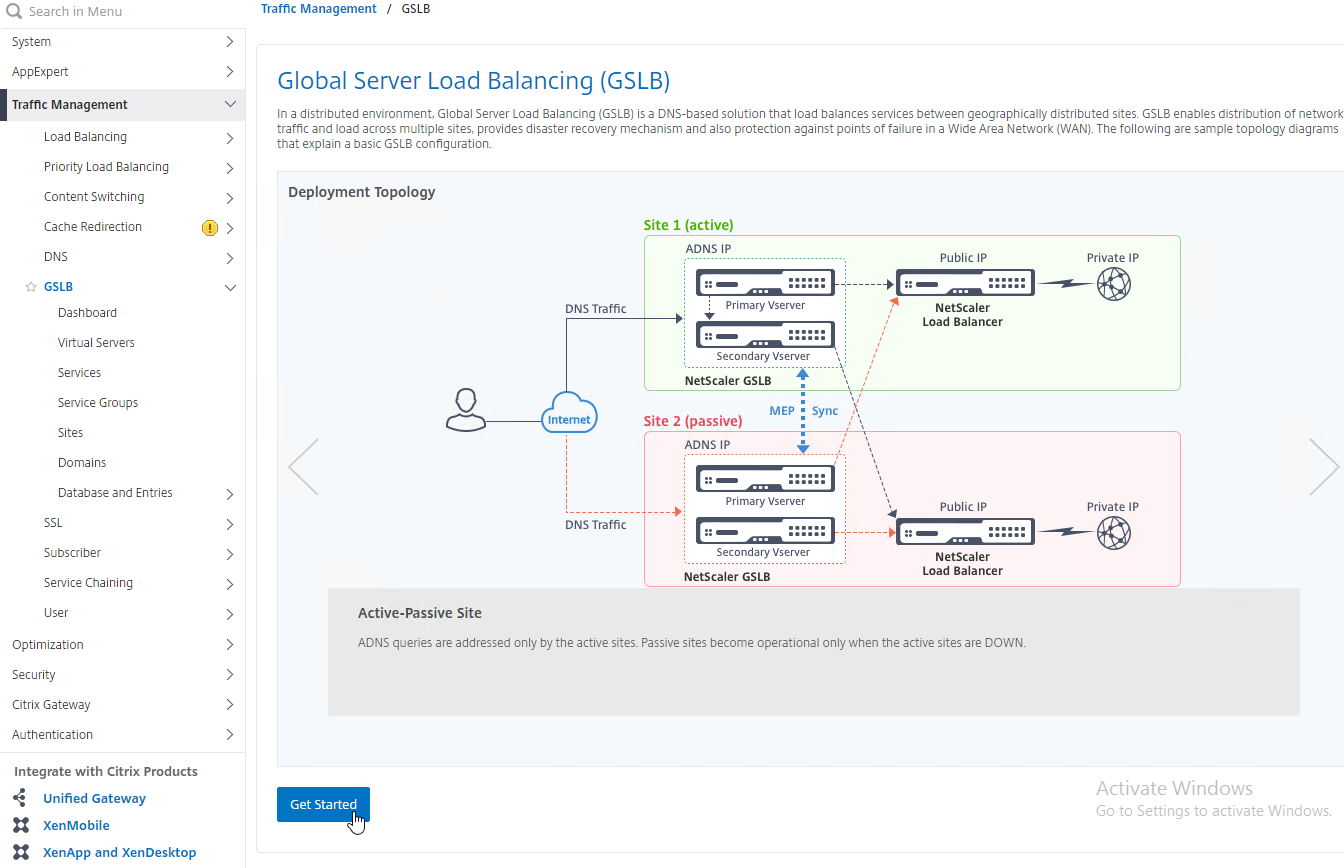
However, the wizard doesn’t really save any time or steps, so it won’t be documented here.
ADNS Listener
- At System > Network > IPs, identify a Citrix ADC-owned IP that you will use as the ADNS listener. This is typically a SNIP.
- Create a public IP for the ADNS Service IP and configure firewall rules. UDP 53 and TCP 53 need to be opened from the Internet to the public IP that NATs to the ADNS Listener IP address.
- On the left, expand Traffic Management > Load Balancing, and click Services.
- On the right, click Add.
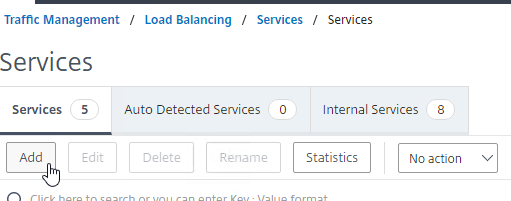
- In the Basic Settings section, do the following:
- Name the service ADNS or similar.
- In the IP Address field, enter an appliance SNIP.
- In the Protocol drop-down, select ADNS.
- Click OK.
- No other configuration is needed so scroll down and click Done to close the Load Balancing Service properties.
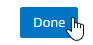
- In the Basic Settings section, do the following:
- Highlight the ADNS service you just added and then click Add to create another Service while copying some of the settings from the previously created Service.
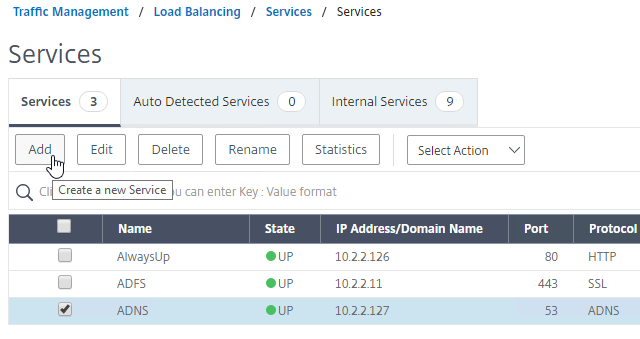
- Change the Service Name to ADNS_TCP or similar.
- Change the Protocol drop-down to ADNS_TCP.
- Click OK to close the Basic Settings section.
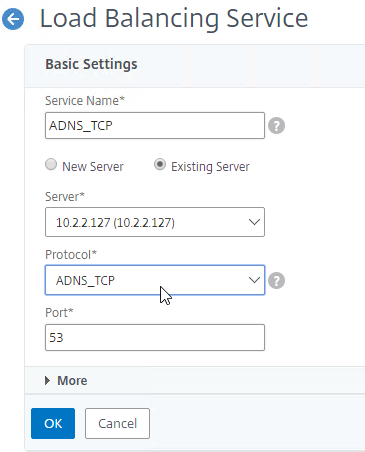
- No other configuration is needed so scroll down and click Done to close the Load Balancing Service properties.

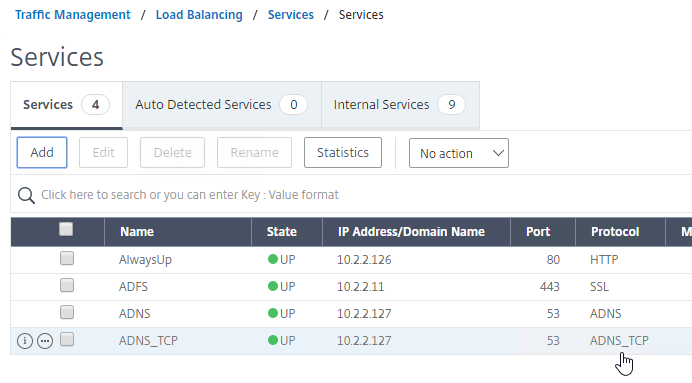
- You should have two ADNS services on the same IP address: one for ADNS, and one for ADNS_TCP.
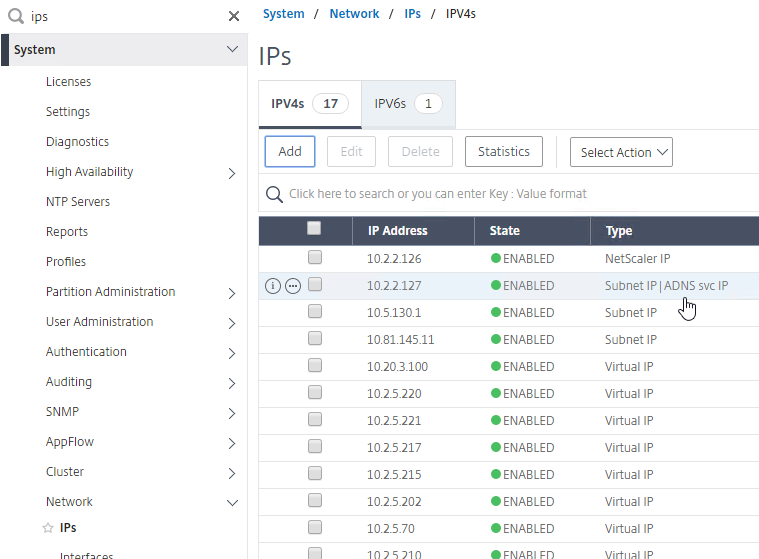
- On the left of the console in the menu, expand System, expand Network, and then click IPs.
- On the right, you’ll see the SNIP is now marked as the ADNS svc IP.
- Repeat the ADNS configuration on the other appliance pair in the other datacenter. Except the other appliance will use its own SNIP as the ADNS Service listener IP address.
- Your ADC appliances are now DNS servers.
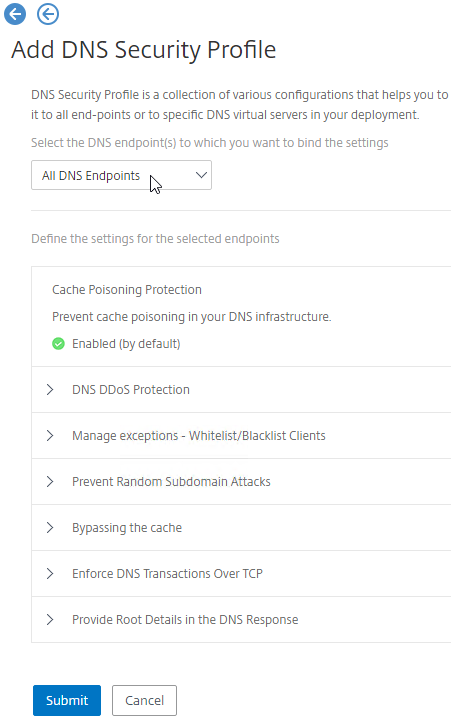
DNS Security
- Citrix ADC includes DNS Security Options, at Security > DNS Security, which can protect your ADNS service.
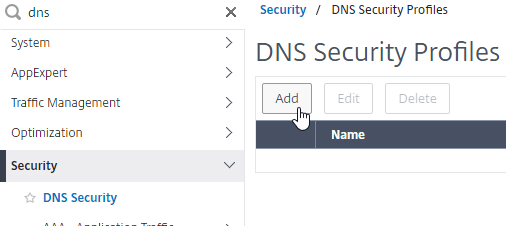
- To protect ADNS, set the Profile to All DNS Endpoints.
Metric Exchange Protocol
This section details MEP configuration between two GSLB Sites. See Citrix Docs for larger Parent-Child Topology Deployment Using the MEP Protocol.
GSLB Sites
- The local GSLB Site IP can be any IP, including the same SNIP that you used for ADNS.
- Open the firewall rules for Metric Exchange Protocol. The GSLB Site IP on this appliance pair uses TCP 3009 to communicate with the GSLB Site IP on the other appliance pair.
- On the left, expand Traffic Management, right-click GSLB, and enable the feature.
- Expand GSLB, and click Sites.
- On the right, click Add.
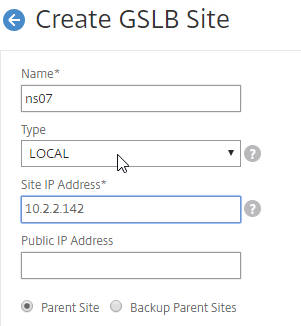
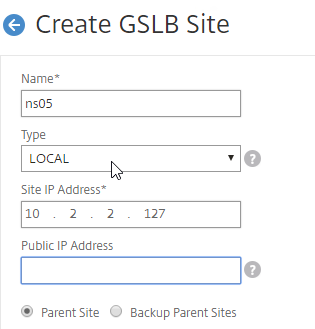
- In the Create GSLB Site page, do the following:
- We’re adding the local site first. Enter a descriptive name for the local site.
- In the Site Type drop-down, select LOCAL.
- In the Site IP Address field, enter an IP that this appliance will listen for MEP traffic. This is typically a SNIP and can the same as your ADNS IP.
- For Internet-routed GSLB MEP, in the Public IP Address field, enter the public IP that is NAT’d to the GSLB Site IP.
- For internal GSLB MEP, there is no need to enter anything in the Public IP field.
- Scroll down, and click Create, to close the Create GSLB Site page.
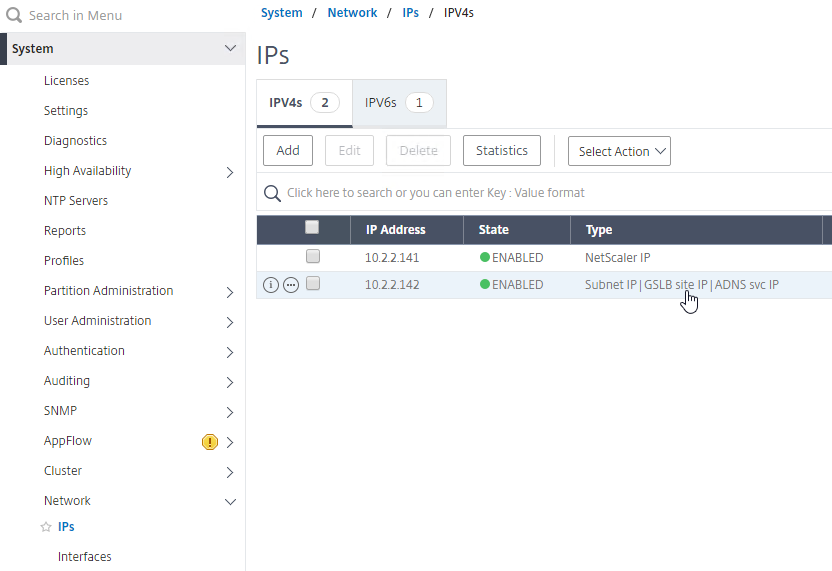
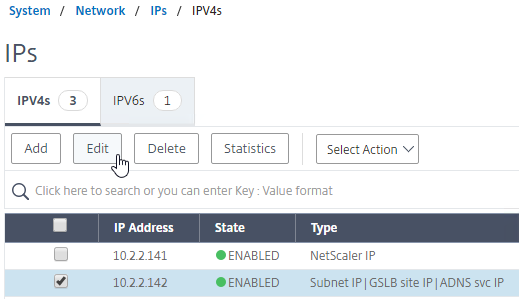
- Go back to System > Network > IPs, and notice that the IP is now marked as a GSLB site IP.
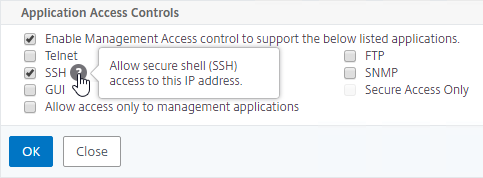
- If you want to use the GSLB Sync Config feature, then you’ll need to edit the GSLB site IP, and enable Management Access.
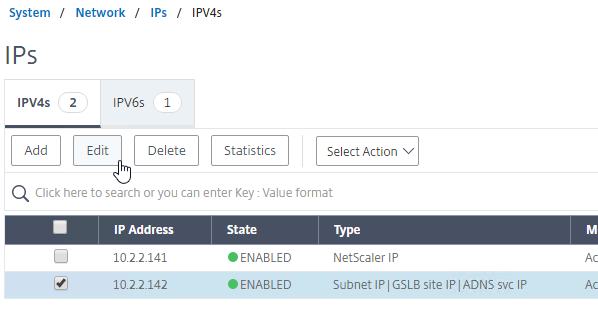
- Scroll down, and enable Management Access. SSH is all you need.
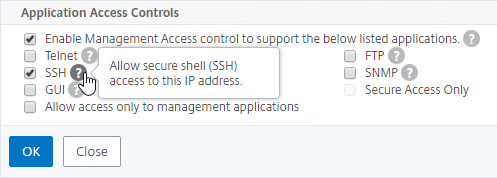
- Scroll down, and enable Management Access. SSH is all you need.
- Go to the other appliance pair, and also create the Local GSLB site using its GSLB site IP, and its public IP that is NAT’d to the GSLB site IP.
- In System > Network > IPs on the remote appliance, there should now be a GSLB site IP. If GSLB Sync is desired, enable management access on that IP and ensure SSH is enabled.
- Now on each appliance, add another GSLB Site, which will be the Remote GSLB site.
- In the Create GSLB Site page, do the following:
- Enter a descriptive name for the remote site.
- Select REMOTE as the Type.
- Enter the other appliance’s actual GSLB Site IP as configured on the appliance. This IP does not need to be reachable.
- In the Public IP Address field, enter the public IP that is NAT’d to the GSLB Site IP on the other appliance. For MEP, TCP 3009 must be open from the local GSLB Site IP, to the remote public Site IP. For GSLB sync, TCP 22, and TCP 3008, must be open from the local NSIP, to the remote public Site IP.
- Click Create.
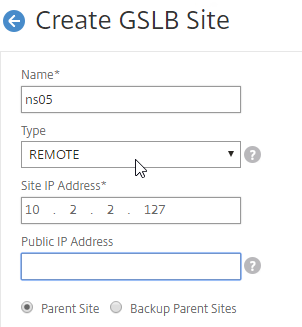
- Repeat on the other appliance.
RPC
MEP defaults to unencrypted on TCP 3011. To fix that:
- On the left, expand System, expand Network, and click RPC.
- On the right, right-click the new RPC address (the other site’s GSLB Site IP), and click Edit.
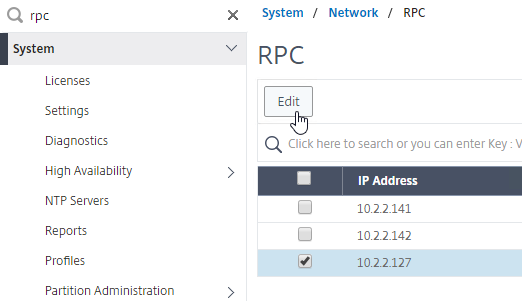
- On the bottom, check the box next to Secure. In ADC 13.0 64.x and 12.1 build 61.x onwards, Secure is enabled by default. (source = Citrix CTX292743 Configuration Sync, Propagation and MEP Propagation Might Fail After Upgrade to 13.0 64.x\12.1 61.x)
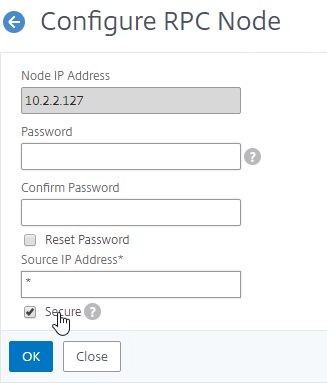
- If your local GSLB Site IP is not a SNIP, then you’ll need to change the RPC Node to use the local GSLB Site IP as the source IP. In the Source IP Address field, enter the local GSLB Site IP.
- Click OK when done.
- Do the same thing on the other appliance.
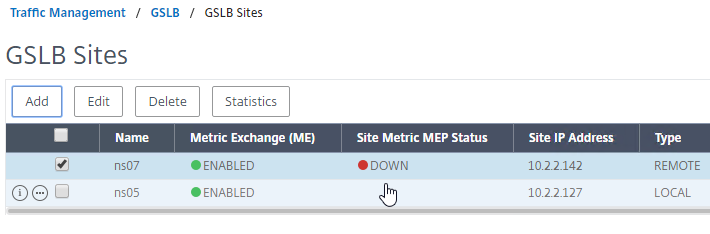
- If you go back to GSLB > Sites, you should see it as active.
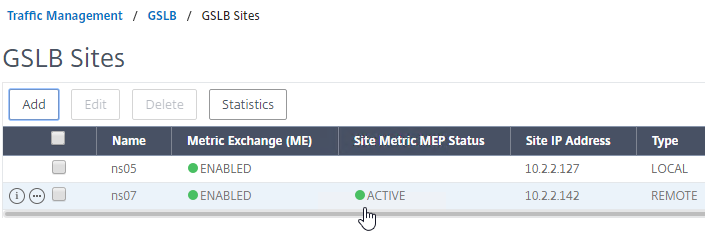
See Citrix Tech Zone Troubleshooting Citrix GSLB MEP Cheat Sheet
If your MEP connection between GSLB Sites flaps, it might be useful to introduce a delay before remote GSLB Services are marked as Down.
- You can do this at Traffic Management > GSLB > Dashboard.
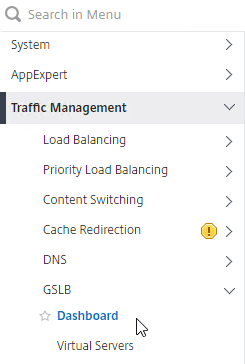
- On the right, click Change GSLB settings.
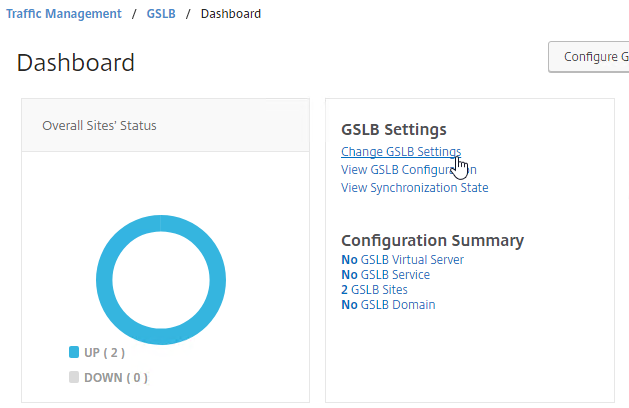
- In the GSLB Service State Delay Time (secs) field, enter a delay before the GSLB Services are marked as down when MEP goes down.
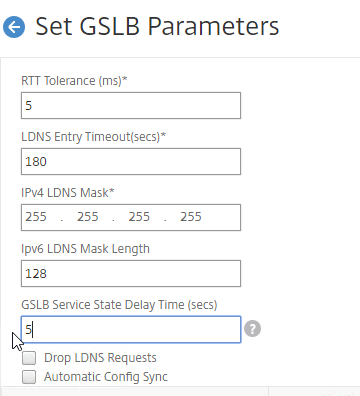
set gslb parameter -GSLBSvcStateDelayTime 15
Static Proximity Geo Location Database
If you want to use DNS Policies, or Static Proximity GSLB Load Balancing, or Responders based on user’s location, import a geo location database.
Citrix ADC has a built-in database at /var/netscaler/inbuilt_db/ that you can use. Or you can download a database. Common free databases are:
- GeoLite Legacy – http://dev.maxmind.com/geoip/legacy/geolite/
- IP2Location Lite – http://lite.ip2location.com/
For IP2Location, see the blog post Add IP2Location Database as NetScaler’s Location File for instructions on how to import.
CTX235799 NetScaler data formats for Location Database Import
Citrix Github has a Citrix-ADC-GSLB-GeoIP-Conversion-Tool that can convert Maxmind GeoIP City database to Citrix ADC (NetScaler) format.
Import the Built-in Geo database:
- In the Citrix ADC GUI, on the left, expand Traffic Management, expand GSLB, expand Database and Entries, and click Static Databases.
- On the right, click Add.
- Change the Import From selection to File.
- Click Choose File.
- Browse to /var/netscaler/inbuilt_db/. To browse to the directory, select var, and then click Open.
- Repeat for each directory until you reach /var/netscaler/inbuilt_db.
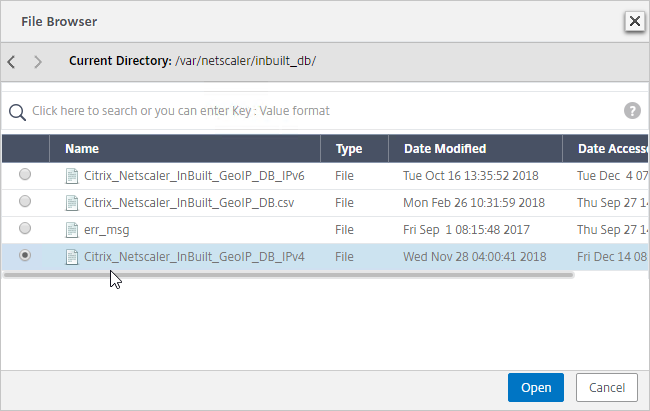
- In ADC 12.1, you can select the file named Citrix_Netscaler_InBuild_GeoIP_DB_IPv4. In NetScaler 12.0, select the only file shown. Then click Open.
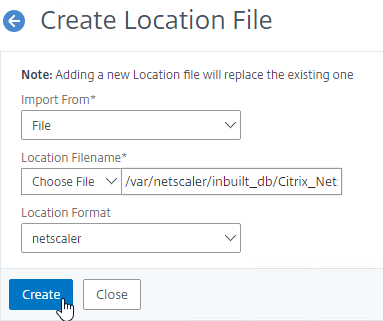
- In the Location Format field, if using the built-in database, select netscaler, and click Create.
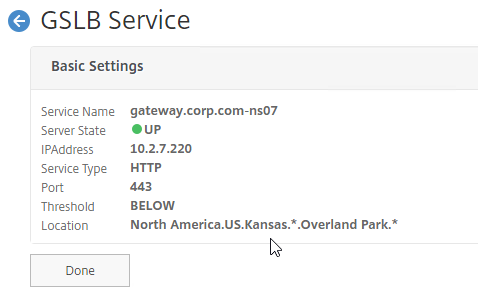
- After you later create a GSLB Service, when you open the GSLB Service, the public IP will be translated to a location based on the contents of the static proximity database.
Private IP Blocks
Geo Location databases only contain entries for Public IPs. For Private IPs, do the following:
- On the left, expand Traffic Management, expand GSLB, expand Database and Entries, and click Custom Entries.
- On the right, click Add.
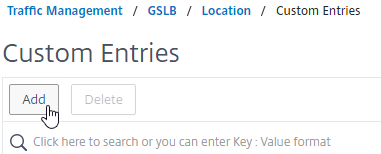
- Enter a range of IP addresses for a particular location.
- Enter a Location Name in Geo Location format, which is typically six location words separated by periods. You can look in the static proximity database for examples.
- Make sure you enter coordinates. Google can find you coordinates for cities.
- Click Create.
- Continue creating Custom Entries for other private IP blocks.
Use Geo Locations
You can use the Geo locations in a DNS Policy, static proximity GSLB Load Balancing, Responders, and Rewrites:
Prior to Citrix ADC 12.1 build 50, the only option in policy expressions is to match a known location.
- The main expression is CLIENT.IP.SRC.MATCHES_LOCATION(“North America.US.*.*.*.*”))
- Citrix Knowledgebase article CTX130701 – How to Block Access to a Website Using a Location Database Based on User’s Country
- In newer versions of Citrix ADC, Location expressions (e.g. CLIENT.IP.SRC.MATCHES_LOCATION(“North America.US.*.*.*.*”)) must be exact matches. You can re-enable wildcards matching by running
set locationParameter -matchWildcardtoany YESfrom the CLI. Source = CTX232884 Policies with GSLB Wildcard Location expressions not getting a hit on build 11.1-53.11 and above
- In newer versions of Citrix ADC, Location expressions (e.g. CLIENT.IP.SRC.MATCHES_LOCATION(“North America.US.*.*.*.*”)) must be exact matches. You can re-enable wildcards matching by running
- Neil Spellings blog post – Using Netscaler HTTP callouts for real-time GeoIP and anonymous proxy detection
- Citrix Docs – Overriding Static Proximity Behavior by Configuring Preferred Locations
Citrix ADC 12.1 build 50 and newer lets you extract the user’s location and use it in policy expressions.
- The main expression is CLIENT.IP.SRC.LOCATION
add audit messageaction msg1 DEBUG "\"Request Location: \"+CLIENT.IP.SRC.LOCATION"add rewrite action rewrite_act insert_http_header "User_location" CLIENT.IP.SRC.LOCATION
- For details, see Retrieve location details from user IP address using geolocation database at Citrix Docs.
GSLB Services
GSLB Services represent the IP addresses that are returned in DNS Responses. The IP addresses represented by GSLB Services do not need to be hosted on a Citrix ADC, but Citrix ADC-owned IP addresses (e.g. load balancing VIPs) have additional GSLB Site Persistence options (e.g. cookie-based persistence).
- Each potential IP address in a DNS response is a separate GSLB Service.
- GSLB Services are associated with GSLB Sites.
- GSLB Service configuration is identical for active/active and active/passive. GSLB Virtual Server configuration defines active/active or active/passive, not GSLB Services.
GSLB should be configured identically on all Citrix ADC pairs that are responding to DNS queries. Since you have no control over which Citrix ADC will receive the DNS query, you must ensure that both Citrix ADC pairs are giving out the same DNS responses.
To create a GSLB Service:
- On the left, expand Traffic Management > GSLB, and click Services.
- On the right, click Add.
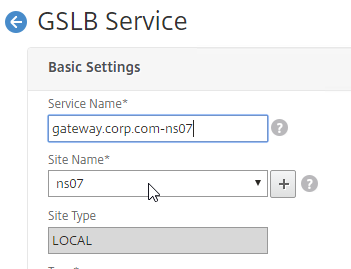
- The service name should be similar to the DNS name that you are trying to GSLB. Include the site name in the service name.
- Select one of the GSLB Sites. The IP address you’re configuring in this GSLB Service should be geographically located in the selected GSLB Site.
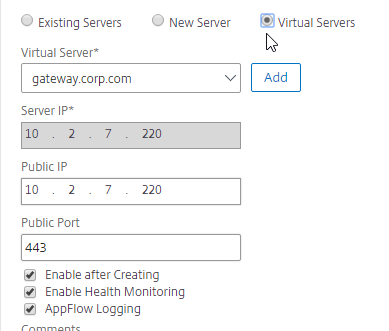
- On the bottom part, if the IP address is owned by this Citrix ADC, then select Virtual Servers, and select a Virtual Server that is already defined on this appliance. It should automatically fill in the other fields. This option is only available when creating a GSLB Service in the Local GSLB Site.
- If the IP address is not owned by this Citrix ADC, then change the selection to New Server, and enter the remote IP address in the Server IP field.
- The Server IP field is the IP address that Citrix ADC will monitor for reachability.
- If the remote IP is owned by a different Citrix ADC that is reachable by MEP, then enter the actual VIP configured on that remote Citrix ADC. The Server IP does not need to match what is returned to the DNS Query.
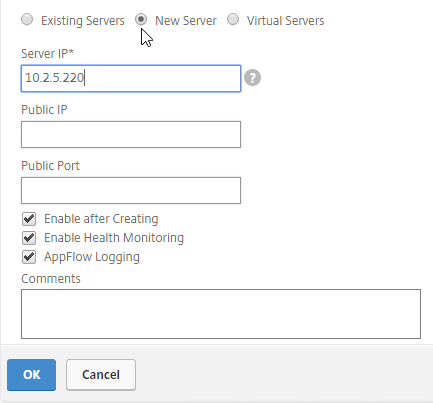
- In the Public IP field, enter the IP address that will be returned to the DNS Query. If you leave Public IP blank, then Citrix ADC will copy the Server IP to the Public IP field. For Public GSLB, the Public IP field is usually a Public IP address. For internal GSLB, the Public IP field is usually an internal IP, and probably matches the Server IP.
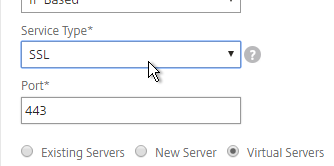
- Scroll up, and make sure the Service Type is SSL. It’s annoying that Citrix ADC doesn’t set this drop-down correctly.
- Scroll down, and click OK, to close the Basic Settings section.
- GSLB Service Monitoring – on the right, in the Advanced Settings column, you can click Monitors to bind a monitor to this GSLB Service. Review the following notes before you bind a monitor.
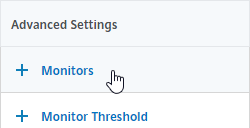
- Local Citrix ADC VIP – If the GSLB Service IP is a VIP on the local appliance, then GSLB will simply use the state of the local traffic Virtual Server (Load Balancing, Content Switching, or Gateway). There’s no need to bind a monitor to the GSLB Service.
- Remote Citrix ADC VIP – If the GSLB Service IP is a VIP on a remote appliance, then GSLB will use MEP to ask the other appliance for the state of the remote traffic Virtual Server. In both cases. There’s no need to bind a monitor to the GSLB Service.
- GSLB Monitor overrides other Monitoring methods – If you bind a monitor to the GSLB Service, then MEP and local Virtual Server state are ignored (overridden).
- Here are some reasons for binding a monitor to the GSLB Service:
- IP is not on a Citrix ADC– If the GSLB Service IP is not hosted on a Citrix ADC, then only a monitor can determine if the Service IP is up or not.
- Monitor remote Internet – For Public DNS, if MEP is not routed through the Internet, then you need some method of determining if the remote Internet circuit is up or not. In that case, you’ll need to bind monitors directly to the GSLB Service. The route of the Monitor should go across the Internet. Or you can ping the Internet router in the remote datacenter to make sure it’s reachable.
- Traffic Domains – If the GSLB Service IP is in a non-default Traffic Domain, then you will need to attach a monitor, since GSLB cannot determine the state of Virtual Servers in non-default Traffic Domains.
- TCP monitor – for TCP services (not UDP), a simple TCP monitor is probably all you need. The TCP monitor tries to connect to the GSLB Service Public IP address using the SNIP of the local appliance. Make sure firewall on both sides allows this connection.
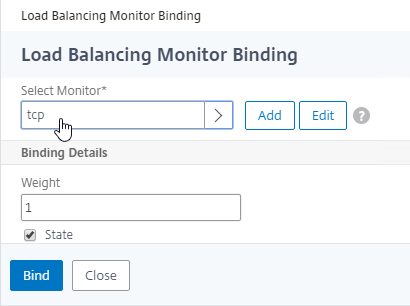
- Active/Active Site Persistence – If you intend to do GSLB active/active, and if you need site persistence, then on the right you can add Site Persistence and enable Connection Proxy or HTTP Redirect. See Citrix Blog Post Troubleshooting GSLB Persistence with Fiddler for more details. This only works with GSLB Service IPs that match Virtual Server VIPs on Citrix ADC appliances reachable through MEP.
- Scroll down, and click Done, to finish creating the GSLB Service.
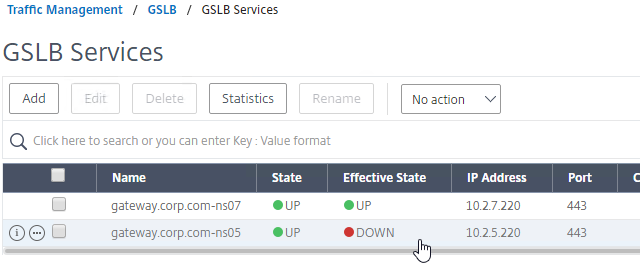
- Create additional GSLB Services for each IP address that will be returned to a DNS query. There should be at least two for each DNS name.
- When creating a GSLB Service, select the correct Site, and make sure Service Type = SSL.
- The State will probably be down until the other ADC is configured.
Manually Synchronize GSLB Configuration
Copy the GSLB Service Configuration to the remote Citrix ADC pair. You can either repeat the GUI steps listed above. Or you can do the following:
- On the left, expand Traffic Management, expand GSLB, and click Dashboard.
- On the right, click View GSLB Configuration.
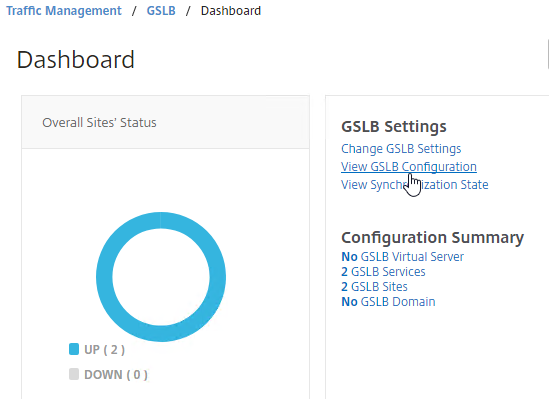
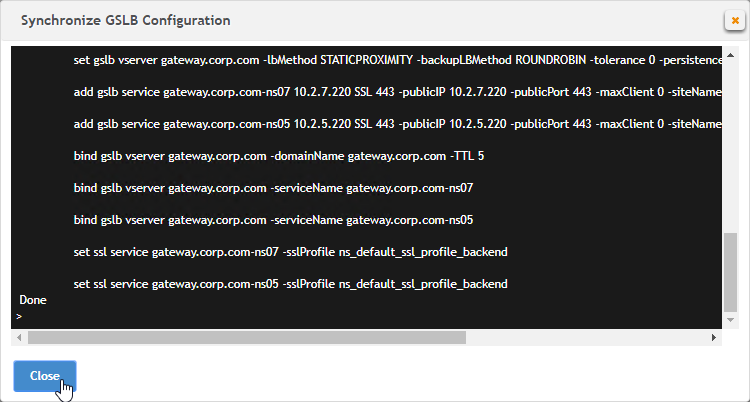
- This shows you all of the CLI commands for GSLB. Look for add gslb service commands. You can copy them, and run them (SSH) on other Citrix ADC pairs that are participating in GSLB.
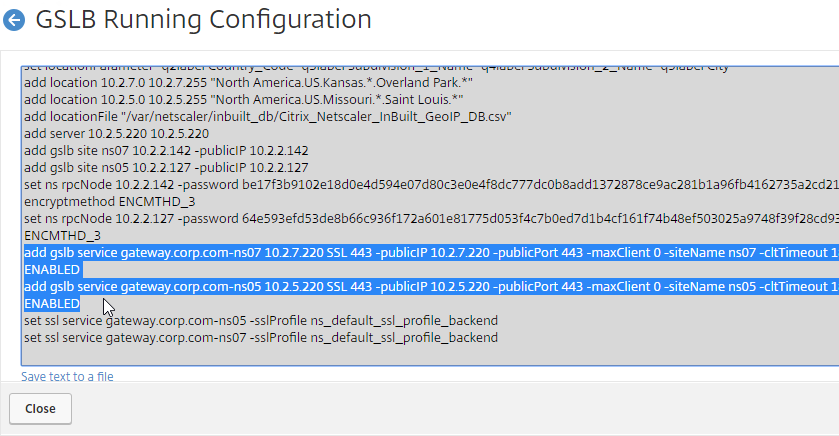
GSLB Virtual Server
GSLB Virtual Server is the entity that links a DNS name with GSLB Services.
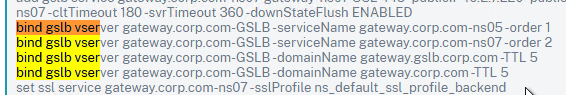
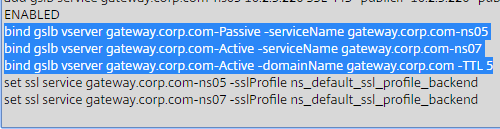
For Active/Passive GSLB in NetScaler ADC 13.1 or newer, GSLB Services can be bound in priority order. GSLB will give out the IP address of the lowest order GSLB Service. If that GSLB Service is down, then GSLB will give out the IP address of the next order GSLB Service.
- Create a GSLB Virtual Server.
- Bind the active GSLB Service but set the Order to 1.
- Bind the passive GSLB Service but set the Order to 2.
- Bind a DNS name to the GSLB Virtual Server.
- Repeat the GSLB Virtual Server configuration on other Citrix ADC pairs participating in GSLB.
- Delegate the DNS name to Citrix ADC ADNS.
For Active/Passive GSLB, the Active GSLB Virtual Server will give out a single IP address if that IP address up. If the GSLB Service is down, then it will fail over to a Backup GSLB Virtual Server that gives out a different IP address.
- Create a GSLB Virtual Server for the Passive IP address.
- Bind the Passive GSLB Service to the Passive GSLB Virtual Server.
- Create another GSLB Virtual Server for the Active IP address.
- Bind the Active GSLB Service to the Active GSLB Virtual Server.
- Configure Backup Virtual Server pointing to the Passive GSLB Virtual Server.
- Bind a DNS name to the Active GSLB Virtual Server.
- Repeat the GSLB Virtual Server configuration on other Citrix ADC pairs participating in GSLB.
- Delegate the DNS name to Citrix ADC ADNS.
For Active/Active GSLB, a single GSLB Virtual Server gives out multiple IP addresses based on load balancing method and site persistence.
- Create one GSLB Virtual Server.
- Bind two or more GSLB Services to the Virtual Server.
- Configure the GSLB Virtual Server Load Balancing Method – e.g., Proximity
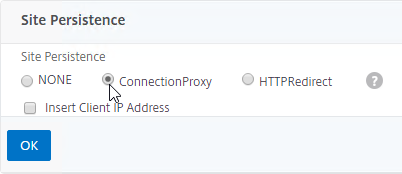
- Configure Site Persistence:
- Source IP persistence is configured on the GSLB Virtual Server.
- Cookie Persistence is configured on the GSLB Services.
- Bind a DNS name to the GSLB Virtual Server.
- Repeat the GSLB Virtual Server configuration on other Citrix ADC pairs participating in GSLB.
- Delegate the DNS name to Citrix ADC ADNS.
Configure Active/Passive GSLB in NetScaler ADC 13.1 and newer
- On the left, expand Traffic Management, expand GSLB, and click Virtual Servers.
- On the right, click Add.
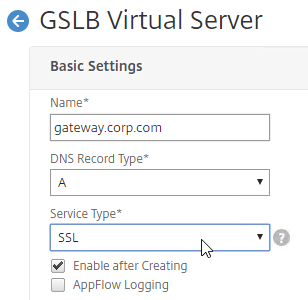
- In the Basic Settings section, do the following:
- Give the GSLB Virtual Server a descriptive name.
- Set the Service Type to SSL to match the GSLB Sevices you intend to bind.
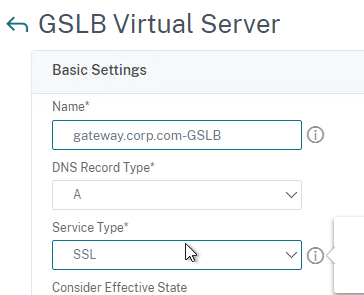
add gslb vserver <gslb_vserver_name> SSL
- Click OK to close the Basic Settings section.

- On the left, click where it says No GSLB Virtual Server to GSLB Service Binding.
- Click where it says Click to select.
- Check the box next to the active GSLB Service and click Select.
- In the Order box, enter 1. Click Bind.
- Click where it says Click to select.
- To add another GSLB Service Binding, on the left, click where it says 1 GSLB Virtual Server to GSLB Service Binding.
- Click Add Binding.
- Click where it says Click to select.
- Check the box next to a passive GSLB Service and then click Select at the top of the page.
- In the Order box, enter 2 so that this GSLB Service is only used if all Order 1 GSLB Services are down. Click Bind.
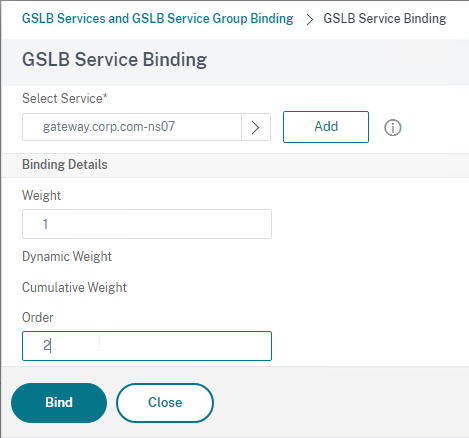
- Click Add Binding.
- Click OK to close the GSLB Services and GSLB Service Group Binding section.
- On the left, click where it says No GSLB Virtual Server Domain Binding.
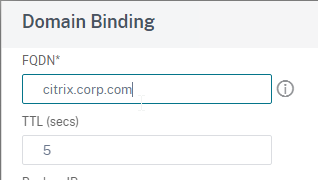
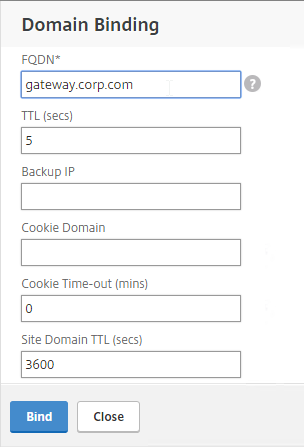
- Enter the FQDN that this GSLB Virtual Server will resolve.
- Click Bind.
- If you are doing CNAME (e.g., citrix.corp.com CNAME to citrix.gslb.corp.com, then add domain bindings for both the main FQDN and the CNAME FQDN. Click Close when done.
- Click OK to close the GSLB Virtual Server Domain Binding section.
- Click OK to close the ADNS Service section.
- With GSLB Services assigned to different Order numbers, it is not necessary to configure Backup Virtual Server.
- If you bound multiple GSLB Services to a single Order number, then you might want to adjust Method and Persistence.
- Click Done to finish creating the GSLB Virtual Server.

- On the left, if you expand Traffic Management > DNS, expand Records, and click Address Records…
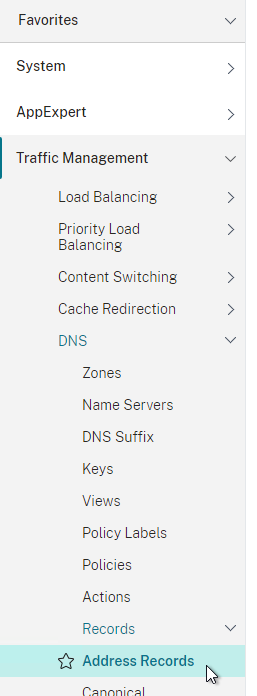
- You’ll see a new DNS record for the GSLB domain you just configured. Notice it is marked as GSLB DOMAIN, and has a default TTL of 5 seconds. You can also see which GSLB Virtual Server it is bound to.
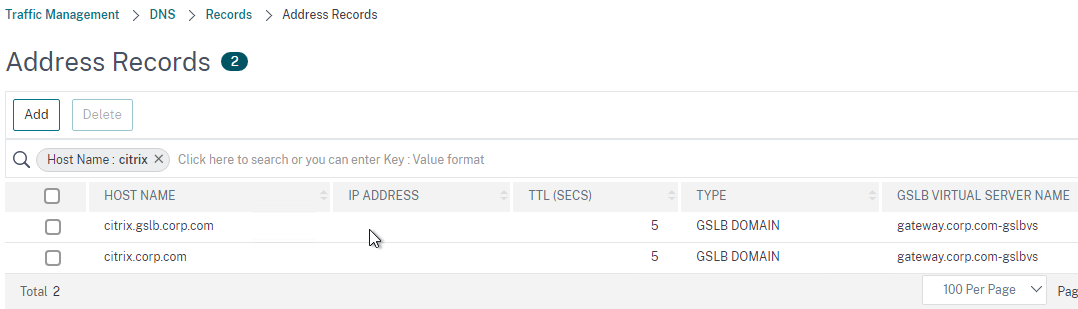
- Configure an identical GSLB Virtual Server on the other NetScaler ADC appliance pair. Both NetScaler ADC pairs must be configured identically. You can use Traffic Management > GSLB > Dashboard > View GSLB Configuration to copy the add/set/bind gslb vserver commands from this appliance to other NetScaler ADC appliances.
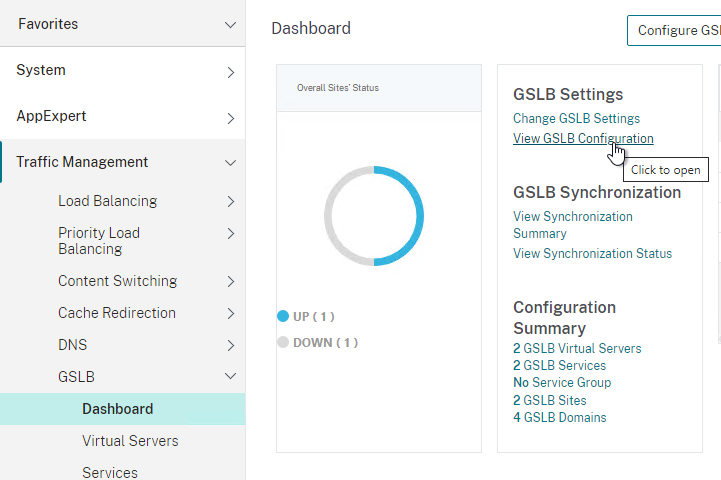
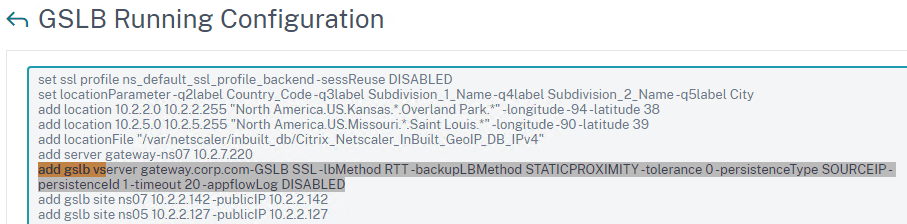
Configure Active/Passive GSLB in NetScaler ADC 13.0 and older
Passive Virtual Server
- On the left, expand Traffic Management, expand GSLB, and click Virtual Servers.
- On the right, click Add.
- In the Basic Settings section, do the following:
- Give the Passive GSLB Virtual Server a descriptive name.
- Set the Service Type to SSL to match the GSLB Services that you will bind to this Virtual Server.
- Click OK to close the Basic Settings section.
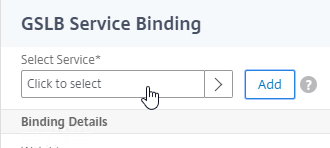
- On the left, click where it says No GSLB Virtual Server to GSLB Service Binding.

- Click where it says Click to select.
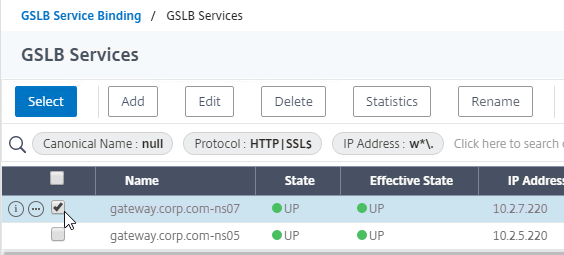
- Check the box next to an existing Passive GSLB Service, and then click the blue Select button at the top of the screen.
- Click Bind.
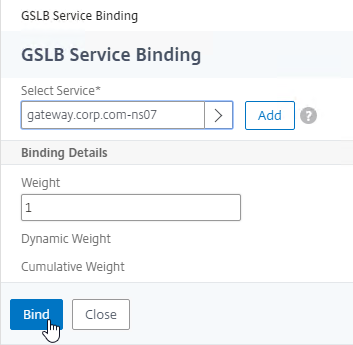
- Click where it says Click to select.
- Click OK to close the GSLB Virtual Server GSLB Service Binding section.
- Click OK to close the GSLB Virtual Server Domain Binding section. The DNS name is bound to the Active Virtual Server, not the Passive Virtual Sever.
- Click OK to close the ADNS Service section.
- Click Done to finish creating the Passive GSLB Virtual Server.

Active Virtual Server
- On the left, expand Traffic Management, expand GSLB, and click Virtual Servers.
- On the right, click Add.
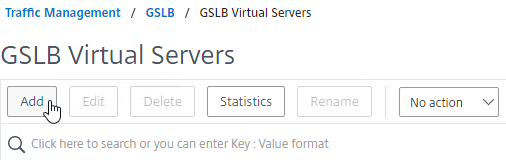
- In the Basic Settings section, do the following:
- Give the Active GSLB Virtual Server a descriptive name.
- Set the Service Type to SSL to match the GSLB Services that you will bind to this Virtual Server.
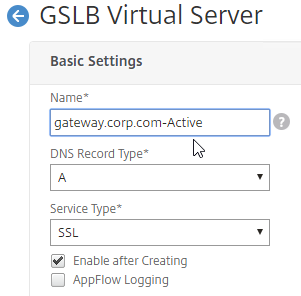
- Click OK to close the Basic Settings section.
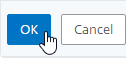
- On the left, click where it says No GSLB Virtual Server to GSLB Service Binding.

- Click where it says Click to select.
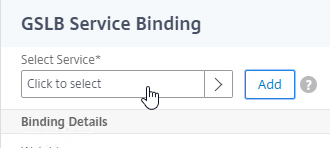
- Check the box next to an existing Active GSLB Service, and click Select.
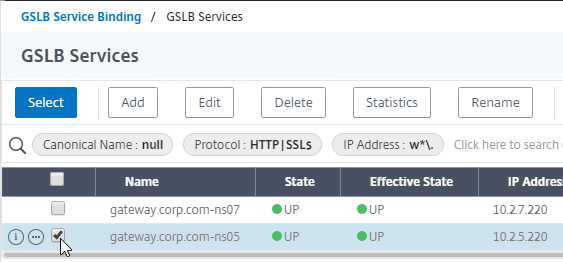
- Click Bind.
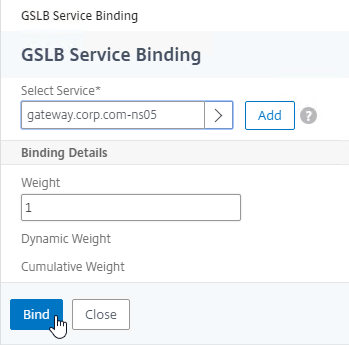
- Click where it says Click to select.
- Click OK to close the GSLB Virtual Server GSLB Service Binding section.
- On the left, click where it says No GSLB Virtual Server Domain Binding.
- In the Domain Binding page, do the following:
- Enter the FQDN that GSLB will resolve.
- Click Bind.
- Click OK to close the GSLB Virtual Server Domain Binding section.
- Click OK to close the ADNS Service section.
- On the right, in the Advanced Settings section, click Backup Virtual Server to add it to the left.
- On the left, in the Backup Virtual Server section, select the Passive GSLB Virtual Server, and click OK.
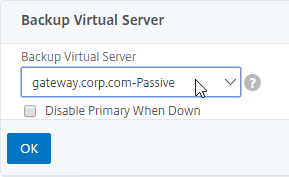
- Click Done when done creating the Active GSLB Virtual Server.

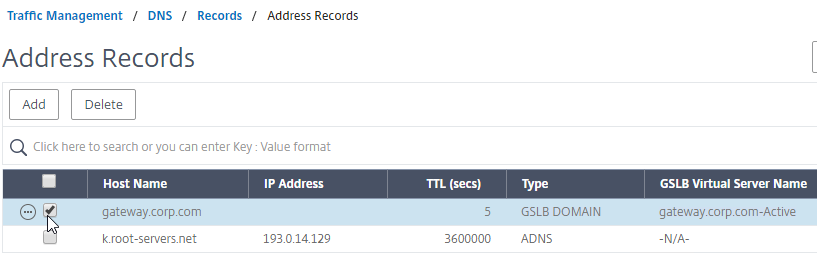
- On the left, if you expand Traffic Management > DNS, expand Records, and click Address Records…
- On the right, you’ll see a new DNS record for the GSLB domain you just configured. Notice the Type is GSLB DOMAIN, and has a default TTL of 5 seconds. You can also see which GSLB Virtual Server it is bound to.
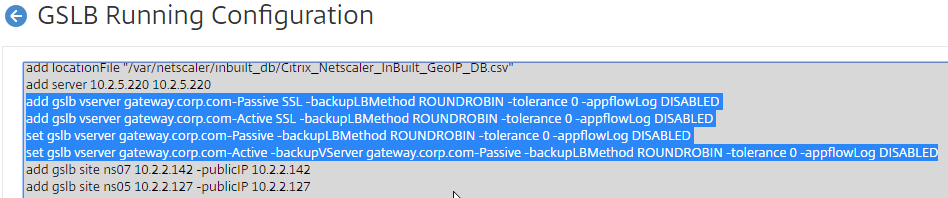
- Configure identical GSLB Virtual Servers on the other Citrix ADC appliance pair. Both Citrix ADC pairs must be configured identically. You can use Traffic Management > GSLB > Dashboard > View GSLB Configuration to copy the add/set/bind gslb vserver commands from this appliance to other Citrix ADC appliances.
Configure Active/Active GSLB
- On the left, expand Traffic Management, expand GSLB, and click Virtual Servers.
- On the right, click Add.
- In the Basic Settings section, do the following:
- Give the GSLB Virtual Server a descriptive name.
- Set the Service Type to SSL to match the GSLB Sevices you intend to bind.
- You can optionally check the box for Send all “active” service IPs in response (MIR). By default, GSLB only gives out one IP address per DNS query. This checkbox always returns all IPs, but the IPs are ordered based on the GSLB Load Balancing Method and/or GSLB Persistence.
- A new DNS feature called ECS will contain the actual DNS client IP. This dramatically improves the accuracy of determining a user’s location. Without this setting, GSLB can only see the IP address of the user’s configured DNS server instead of the real client IP. Check the box next to Respond with ECS option to enable ECS for site persistence.
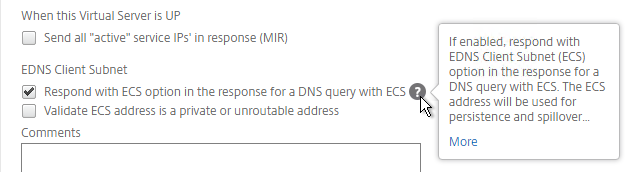
set gslb vserver <gslb_vserver> -ECS ENABLED
- Click OK to close the Basic Settings section.

- On the left, click where it says No GSLB Virtual Server to GSLB Service Binding.

- Click where it says Click to select.

- Check the boxes next to multiple existing GSLB Services, and click Select.
- Click Bind.
- Click where it says Click to select.
- Click OK to close the GSLB Virtual Server GSLB Service Binding section.
- On the left, click where it says No GSLB Virtual Server Domain Binding.
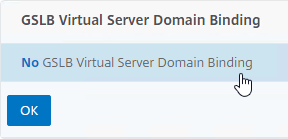
- Enter the FQDN that this GSLB Virtual Server will resolve.
- Click Bind.
- Click OK to close the GSLB Virtual Server Domain Binding section.
- Click OK to close the ADNS Service section.
- On the left, in the Method section, click the pencil icon.
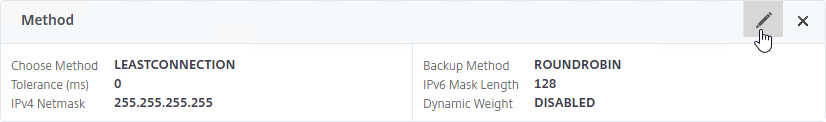
- For poximity load balancing, change the Choose Method drop-down to RTT with STATICPROXIMITY as backup.
- RTT = Round Trip Time. Each ADC appliance sends a ping to the user’s DNS server. Whichever ADC appliance gets the fastest response determines the site of the GSLB Service. RTT requires that ADC be able to ping anything on the Internet so adjust firewall rules accordingly.
- STATICPROXIMITY requires that the Geo Location database has already been installed on the appliance.
- Click OK to close the Method section.
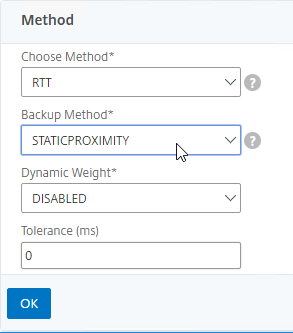
- For poximity load balancing, change the Choose Method drop-down to RTT with STATICPROXIMITY as backup.
- On the right, in the Advanced Settings column, click Persistence to add it to the left.
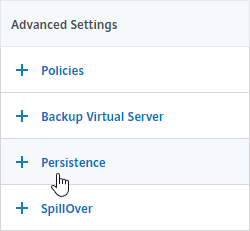
- On the left, at the bottom of the page in the Persistence section, change the Persistence drop-down to Source IP.
- Enter a Persistence Id.
- The Persistence ID signifies the persistence table that each ADC pair shares across the MEP connection.
- Each active/active GSLB Virtual Server should have a different Persistence ID (different persistence table).
- When you configure the same GSLB Virtual Server on each Citrix ADC pair, specify the same Persistence ID so every Citrix ADC has the same persistence information for this particular GSLB Virtual Server.
- In the Time-out field, enter the Persistence Time-out. This is typically the same or longer than the webpage timeout.
- Click OK to close the Persistence section.
- Click Done to finish creating the GSLB Virtual Server.

- On the left, if you expand Traffic Management > DNS, expand Records, and click Address Records…
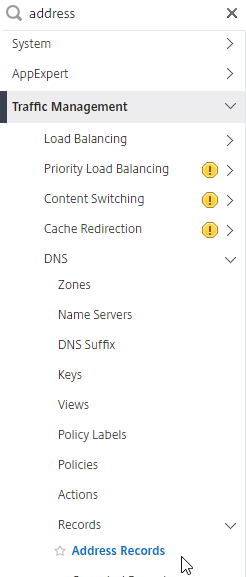
- You’ll see a new DNS record for the GSLB domain you just configured. Notice it is marked as GSLB DOMAIN, and has a default TTL of 5 seconds. You can also see which GSLB Virtual Server it is bound to.
- Configure an identical GSLB Virtual Server on the other Citrix ADC appliance pair. Both Citrix ADC pairs must be configured identically. You can use Traffic Management > GSLB > Dashboard > View GSLB Configuration to copy the add/set/bind gslb vserver commands from this appliance to other Citrix ADC appliances.
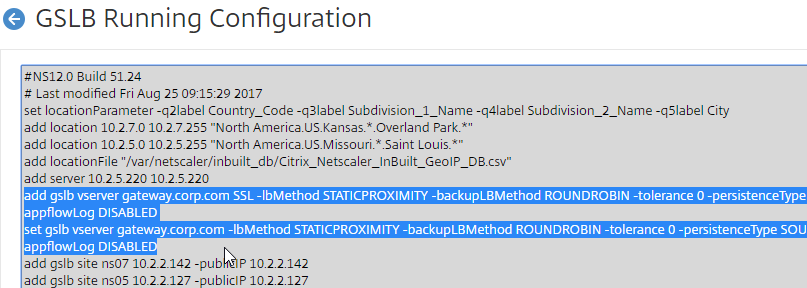
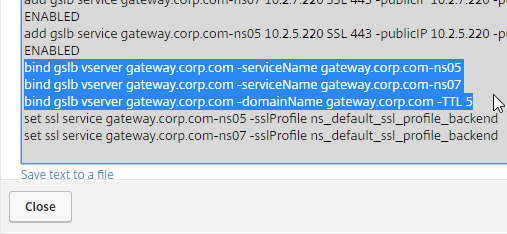
GSLB Configuration Synchronization Script
Manual GSLB Synchronization
- The synchronization script requires SSH to be enabled on your GSLB Site IPs.
- Ports TCP 3008, TCP 3010, and TCP 22 must be opened from the local NSIP to the remote GSLB Site IP. The source IP is NSIP, not SNIP.
- To manually run the script that syncs GSLB configuration from one GSLB Site to another, on the left, expand Traffic Management, expand GSLB, and click Dashboard.

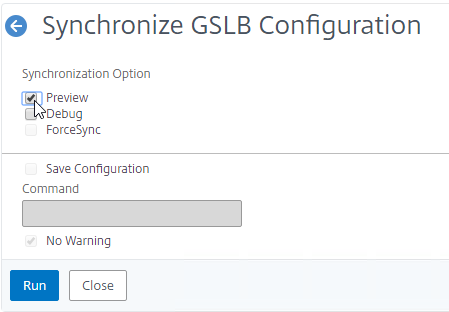
- On the right, click the button labelled Auto Synchronization GSLB.
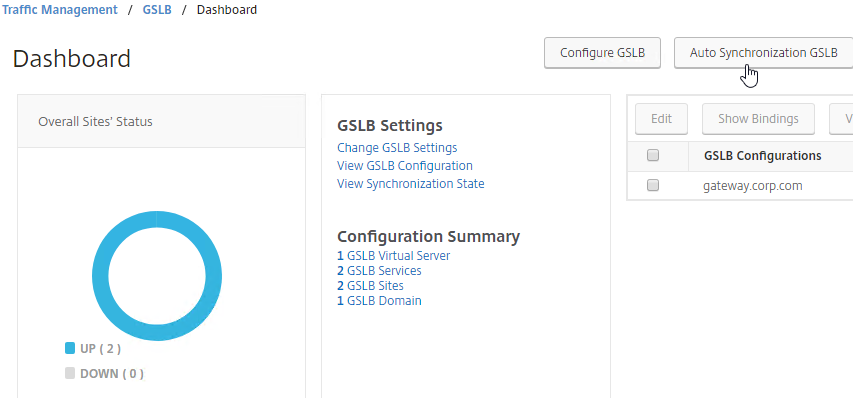
- Use the check boxes on the top, if desired. It’s usually a good idea to Preview the changes before applying them.
- Then click Run to begin synchronization.
- Click Close.
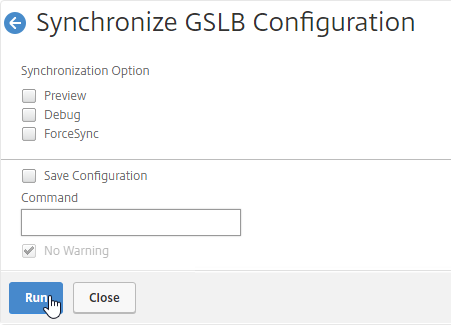
- You can Run it again without previewing it. It seems to take several seconds to complete.
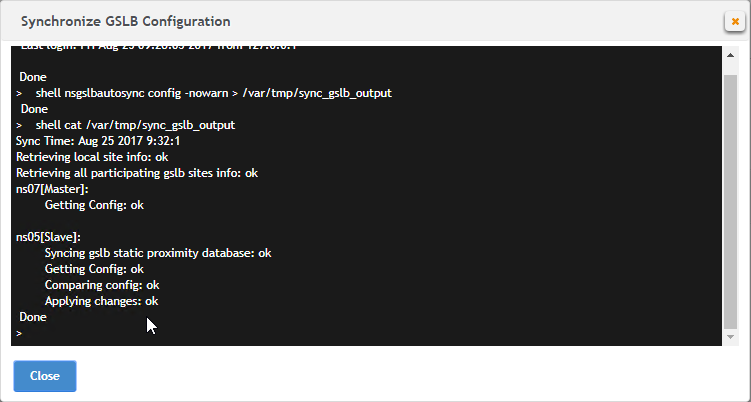
Automatic GSLB Synchronization
- There is an automatic GSLB Configuration Sync feature, which automatically syncs the GSLB config every 15 seconds. To enable it on the master appliance, go to Traffic Management > GSLB > Dashboard. On the right, click Change GSLB settings.
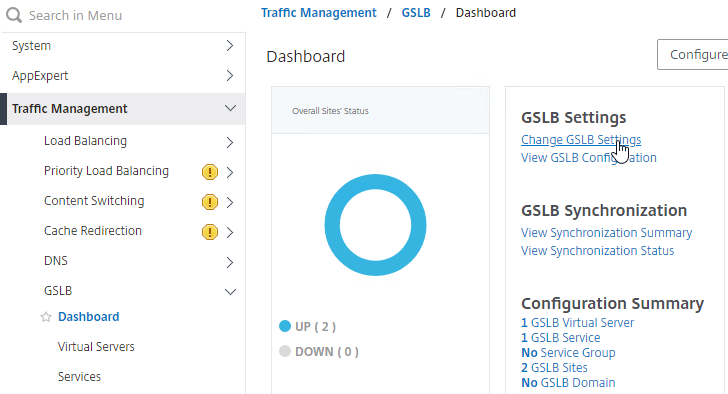
- Check the box next to Automatic Config Sync. Only enable this on the one appliance where you are configuring GSLB, and want that GSLB config synced to other appliance.
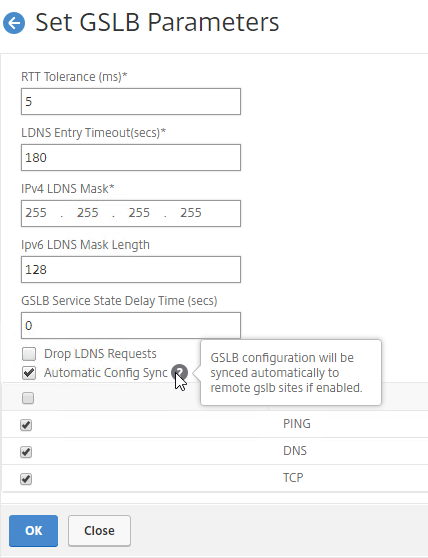
- The automatic sync log can be found at /var/netscaler/gslb/periodic_sync.log.
Some notes regarding GSLB Sync:
- When syncing GSLB Services, it tries to create Load Balancing Server objects on the remote appliance. If the GSLB Service IP matches an existing Load Balancing Server object, then the GSLB sync will fail. Check the Sync logs for details. You’ll have to delete the conflicting Load Balancing Server object before GSLB Sync works correctly.
- GSLB Sync runs as a script on the BSD shell and thus always uses the NSIP as the source IP.
- GSLB Sync connects to the remote GSLB Site IP on TCP 3008 (if RPC is Secure) and TCP 22.
Test GSLB
- You can test GSLB DNS name resolution from the GUI by going to Traffic Management > GSLB > Dashboard, and on the right, click the button labelled Test GSLB.

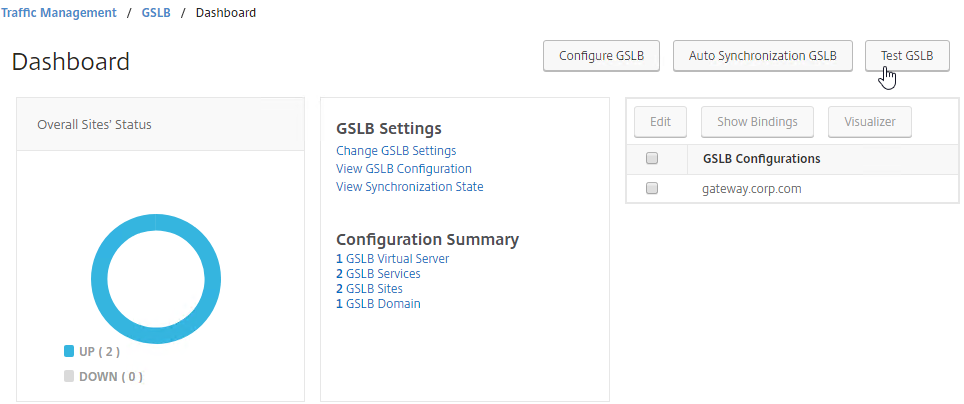
- Select a GSLB Domain Name.
- Select an ADNS Service IP to test it from, and click Test.
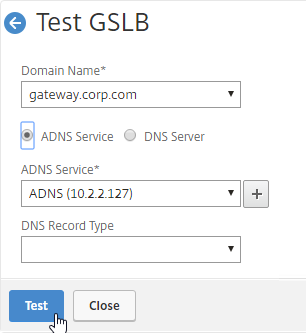
- The test performs a dig against the ADNS IP. Verify that the response contains the IP address you expected.
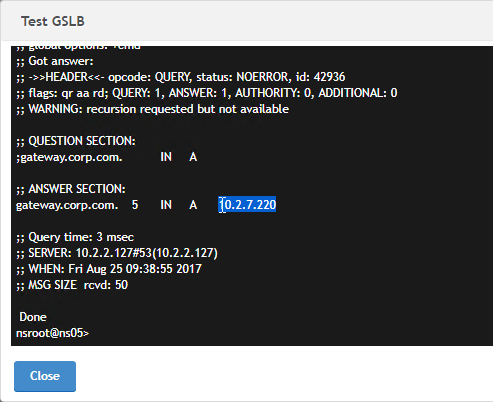
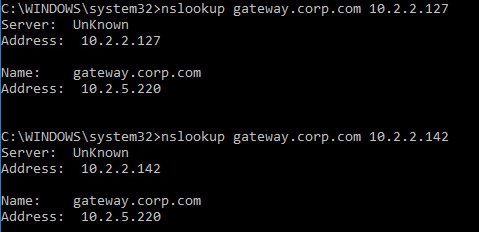
- Another method of testing GSLB is to simply point nslookup to the ADNS services and submit a DNS query for one of the DNS names bound to a GSLB vServer. Run the query multiple times to make sure you’re getting the response you expect.
- The syntax is “nslookup <DNS_name> <ADNS_IP>”. The second argument specifies the DNS server that you send the DNS Query to.
- The Citrix ADC ADNS services at both GSLB sites should be giving the same response.
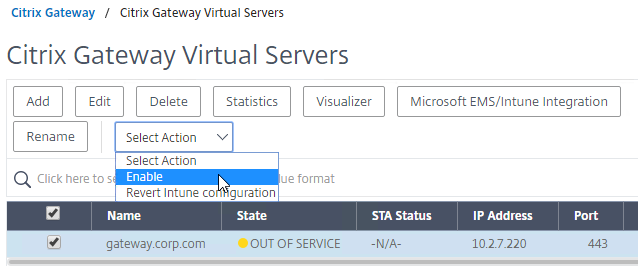
- To simulate a failure, if the GSLB Service IP is a Citrix ADC Load Balancing, Content Switching, or Citrix Gateway IP, you can disable the Virtual Server.
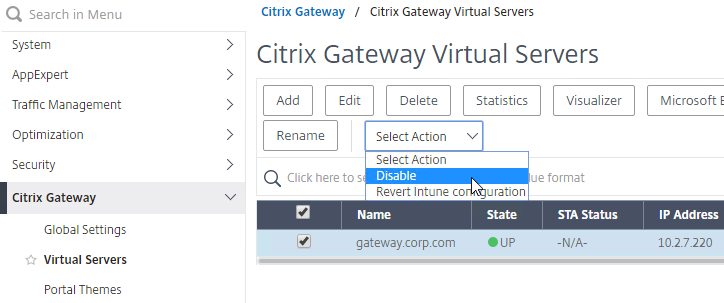
- Then the responses should change. Verify on both ADNS services.
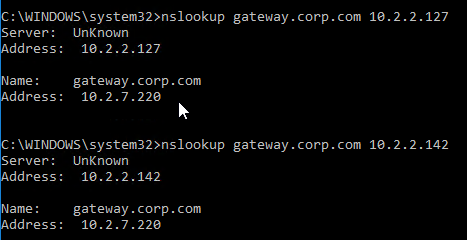
- Re-enable the Virtual Server, and the responses should return to normal.

DNS Delegation
If you are enabling GSLB for the domain gateway.corp.com, you’ll need to create a delegation at the server that is hosting the corp.com DNS zone. For public GSLB, you need to edit the public DNS zone for corp.com.
DNS Delegation instructions will vary depending on what product is hosting the public DNS zone. This section details Microsoft DNS, but it should be similar in BIND or web-based DNS products.
There are two ways to delegate GSLB-enabled DNS names to Citrix ADC ADNS:
- Delegate the individual record – For example, delegate gateway.corp.com.
- Delegate an entire subzone – For example, delegate the subzone gslb.corp.com. Then create a CNAME record in the parent DNS zone for gateway.corp.com that is aliased to gateway.gslb.corp.com. For additional delegations, simply create more CNAME records.
- The incoming DNS query to the ADNS listener is for gateway.gslb.corp.com and not gateway.corp.com. You’ll need to bind gateway.gslb.corp.com to your GSLB Virtual Server. You can bind multiple FQDNs to a single GSLB Virtual Server.
A delegation consists of the following DNS records:
- A records (host records) that resolve to each Citrix ADC ADNS IP address. If you have two ADC pairs participating in GSLB, then you’ll need one A record for each ADC pair.
- The A record names are typically something like ns1.corp.com and ns2.corp.com, just like you would name any other DNS server.
- You only create the A records once. The A records for ADNS services can be used by multiple delegations.
- These A records for ADNS are sometimes called glue records.
- NS records for each delegation. The NS records point to the A records that resolve to the ADC ADNS IP addresses. If you have two ADC ADNS IP addresses, then you need two NS records for each delegation.
- When delegating individual records, you create separate NS records for each delegation. If you have two ADNS listeners, then you need two NS records for each delegation.
- When delegating a subzone, you only need NS records for the subzone. To GSLB-enable a DNS name, you create a CNAME that aliases to a record under the subzone.
Delegate an individual DNS record
- Run DNS Manager.
- First, create Host Records pointing to the ADNS services running on the Citrix ADC pairs in each data center. These host records for ADNS are used for all GSLB delegations no matter how many GSLB delegations you need to create. These are sometimes called glue records.
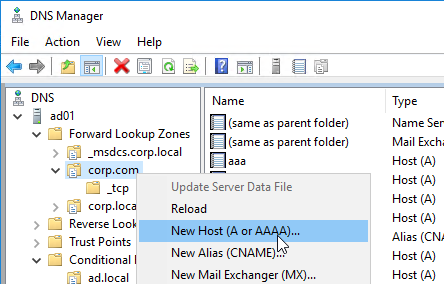
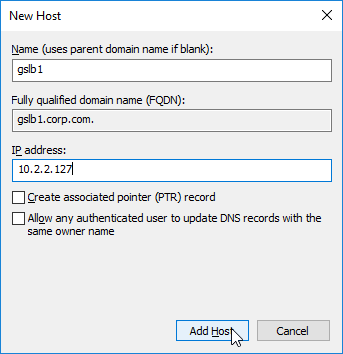
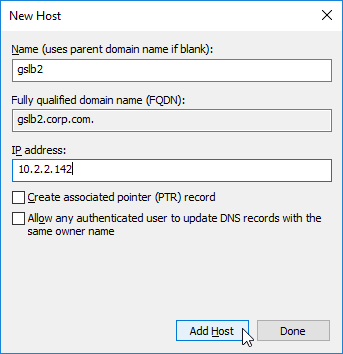
- The first Host record is gslb1, (or similar) and should point to the ADNS service (Public IP) on one of the Citrix ADC appliances.
- The second Host record is gslb2, and should point to the ADNS Service (public IP) on the other Citrix ADC appliance.
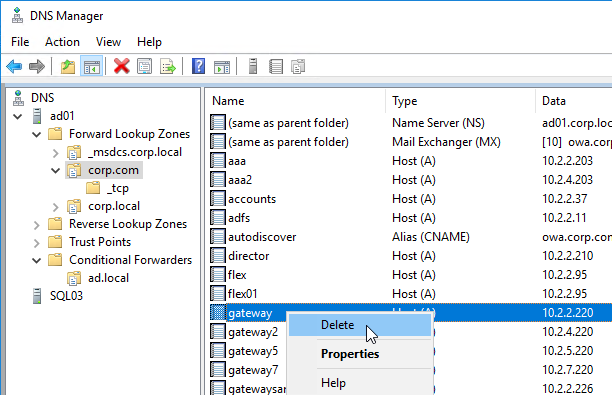
- If you currently have a host record for the service that you are delegating to GSLB (e.g. gateway.corp.com), delete it.
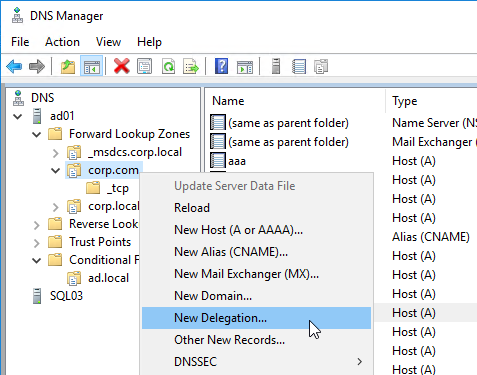
- Right-click the parent DNS zone, and click New Delegation.
- In the Welcome to the New Delegation Wizard page, click Next.
- In the Delegated Domain Name page, enter the left part of the DNS record that you are delegating (e.g. gateway for gateway.corp.com). Click Next.
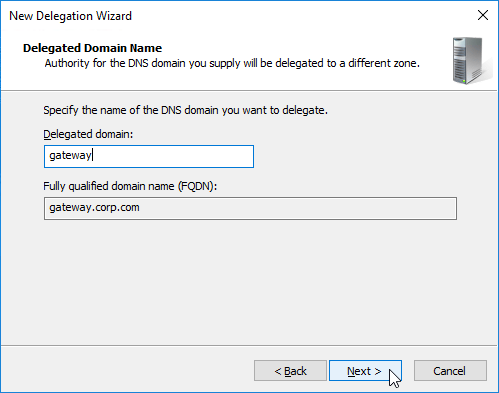
- In the Name Servers page, click Add.
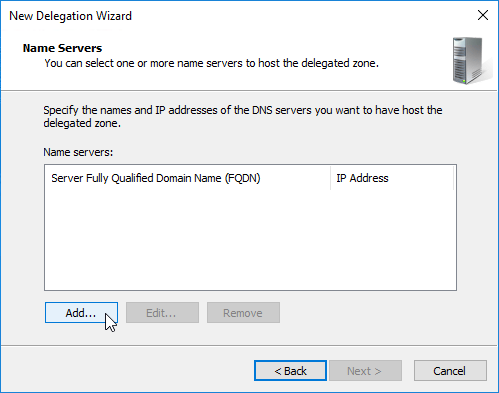
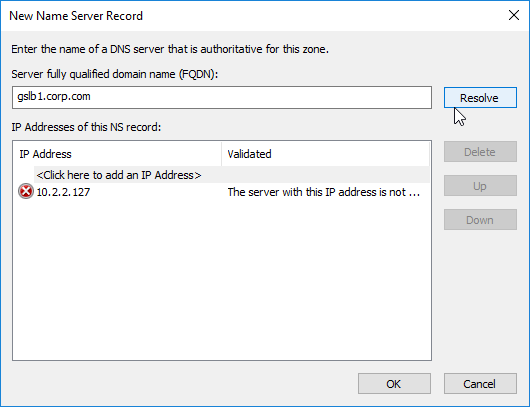
- This is where you specify gslb1.corp.com and gslb2.corp.com as delegated name servers. Enter gslb1.corp.com, and click Resolve. Then click OK. If you see a message about the server not being authoritative for the zone, ignore the message. Note: you only add one name server at a time.
- Then click Add to add the other GSLB ADNS server.
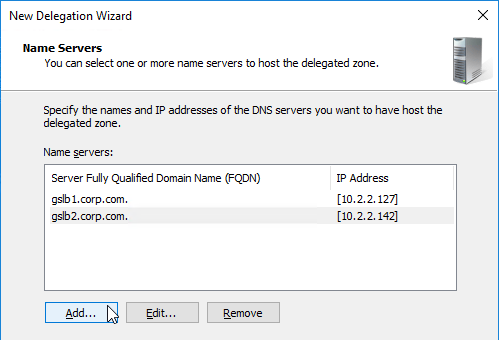
- Once both ADNS servers are added to the list, click Next.
- In the Completing the New Delegation Wizard page, click Finish.
- The delegation is shown in the DNS Manager console.
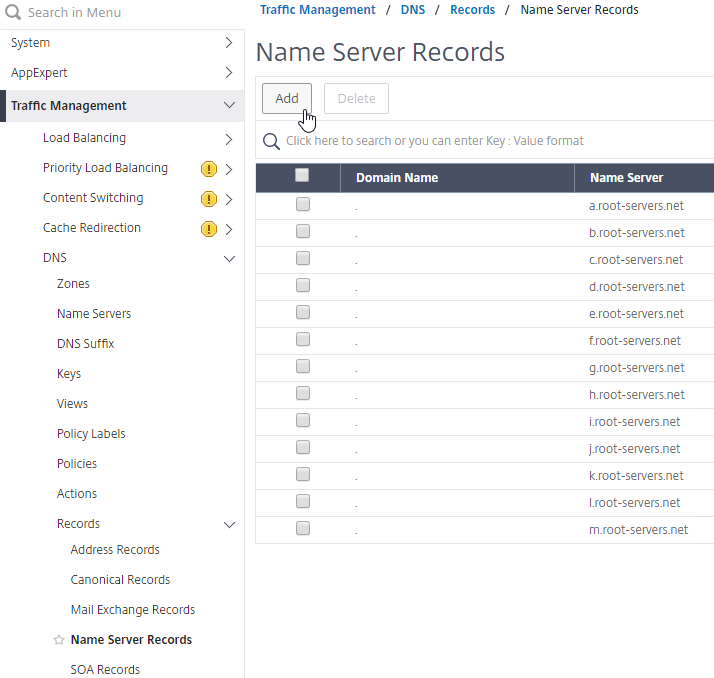
- For proper delegation, the Name Server records should also be added to Citrix ADC. (source = Citrix CTX241493 Citrix Response on DNS Flag Day)
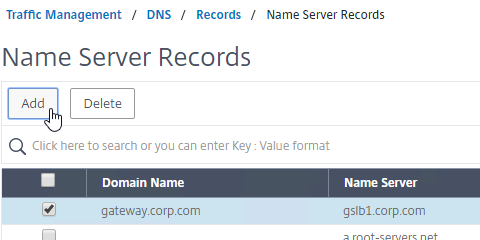
- On the GSLB Citrix ADC appliances, expand Traffic Management, expand DNS, expand Records, and click Name Server Records.
- On the right, click Add.
- In the Domain Name field, enter the name of the delegated DNS name (e.g. gateway.corp.com).
- In the Name Server field, leave it set to –<< New >>–, and enter one of the FQDNs for your GSLB ADNS services. This is one of the glue records you created earlier.
- Click Create.
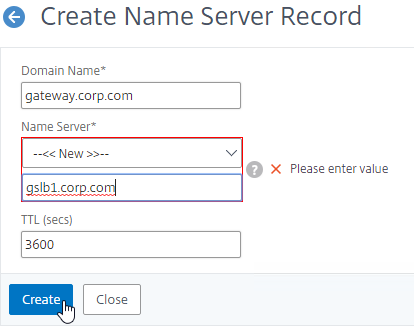
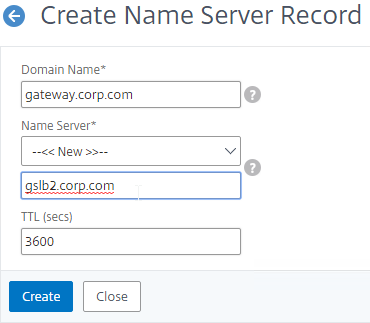
- Add another Name Server Record for the same domain name. But this time, enter the second GSLB ADNS FQDN. Repeat this process until all GSLB ADNS FQDNs are specified.
- Also add an SOA record for the delegation. If you are delegating individual records, then you will need an SOA for each record. If you are delegating a subzone, you only need an SOA record for the subzone.
- On the left, in the menu, go to Traffic Management > DNS > Records > SOA Records.
- On the right, click Add.
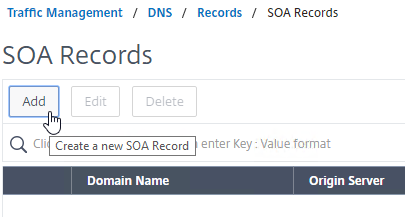
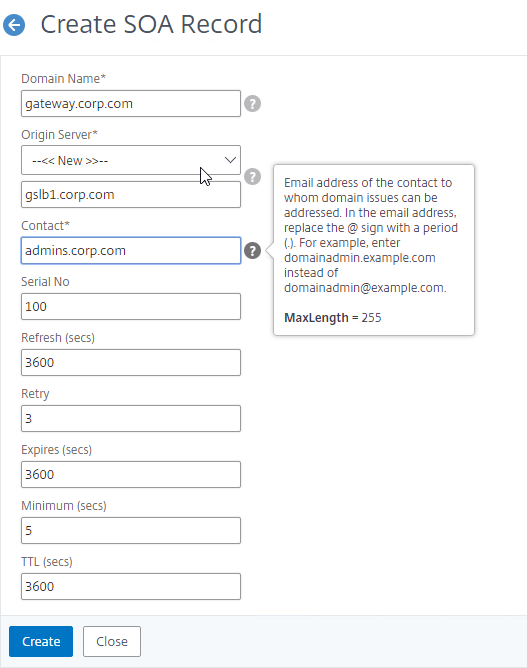
- In the Domain Name field, enter the FQDN that you delegated to NetScaler. This can be an individual record, or a sub-zone.
- In the Origin Server field, leave it set to –<< New >> — and then enter the FQDN that resolves to one of your ADNS listeners. It doesn’t matter which one you enter.
- In the Contact field, enter an email address that is publicly viewable. Replace the @ symbol with a period.
- Click Create.
- Repeat this on the other ADCs that are participating in GSLB for this delegated DNS name.
- On the left, in the menu, go to Traffic Management > DNS > Records > SOA Records.
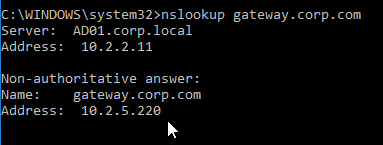
- If you run nslookup against your Microsoft DNS server, it will respond with Non-authoritative answer. That’s because it got the response from Citrix ADC, and not from the original DNS server that you send the request to.
Delegate a Sub-zone
- Run DNS Manager.
- First, create Host Records pointing to the ADNS services running on the Citrix ADC pairs in each data center. These are sometimes called glue records.

- The first Host record is gslb1 (or similar), and should point to the ADNS service (Public IP) on one of the Citrix ADC appliances.

- The second Host record is gslb2, and should point to the ADNS Service (public IP) on the other Citrix ADC appliance.

- The first Host record is gslb1 (or similar), and should point to the ADNS service (Public IP) on one of the Citrix ADC appliances.
- Right-click the parent DNS zone, and click New Delegation.

- In the Welcome to the New Delegation Wizard page, click Next.

- In the Delegated Domain Name page, enter the left part of the DNS sub-zone that you are delegating (e.g. gslb for gslb.corp.com). Click Next.
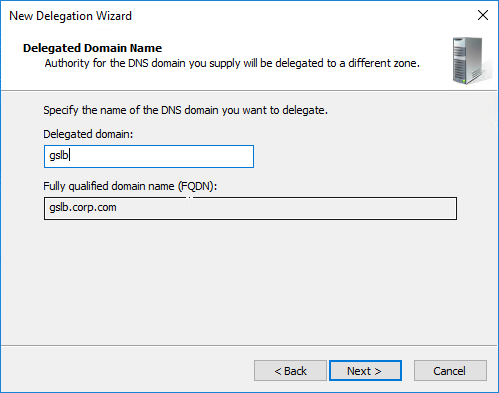
- In the Name Servers page, click Add.

- This is where you specify gslb1.corp.com and gslb2.corp.com. Enter gslb1.corp.com, and click Resolve. Then click OK. If you see a message about the server not being authoritative for the zone, ignore the message. Note: you only add one name server at a time.

- Then click Add to add the other GSLB ADNS server.

- Once both ADNS servers are added to the list, click Next.

- In the Completing the New Delegation Wizard page, click Finish.
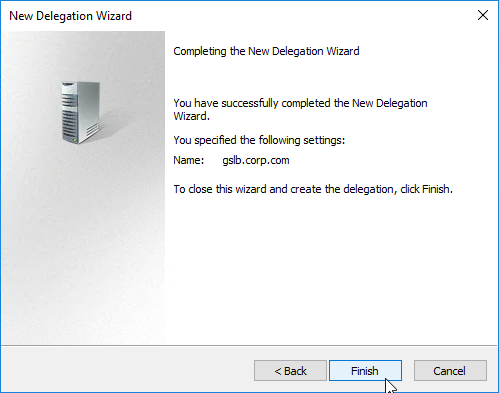
- The sub-zone delegation is shown in the DNS Manager console.
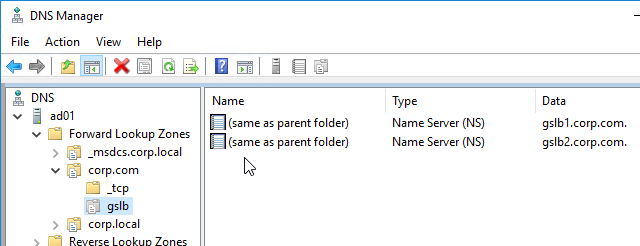
- For proper delegation, the Name Server records should also be added to Citrix ADC. (source = Citrix CTX241493 Citrix Response on DNS Flag Day)
- On the GSLB Citrix ADC appliances, expand Traffic Management, expand DNS, expand Records, and click Name Server Records.
- On the right, click Add.
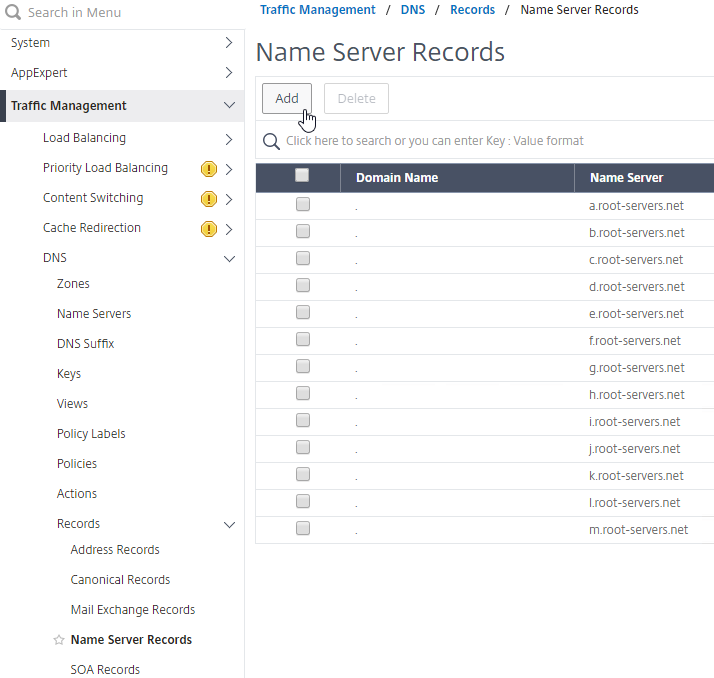
- In the Domain Name field, enter the name of the delegated sub-domain (e.g. gslb.corp.com).
- In the Name Server field, leave it set to –<< New >>–, and enter one of the FQDNs for your GSLB ADNS services. This is one of the glue records you created earlier.
- Click Create.
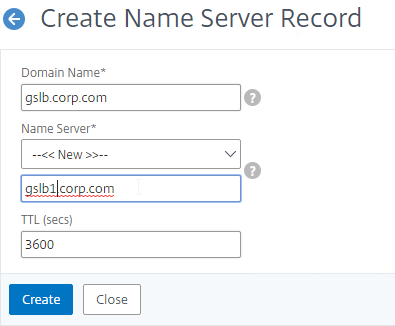
- Add another Name Server Record for the same domain name. But this time, enter the second GSLB ADNS FQDN.
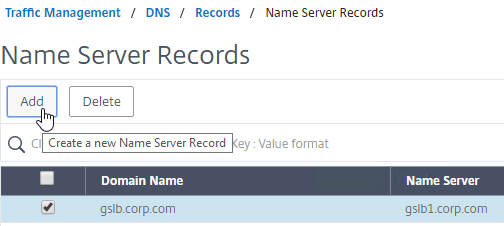
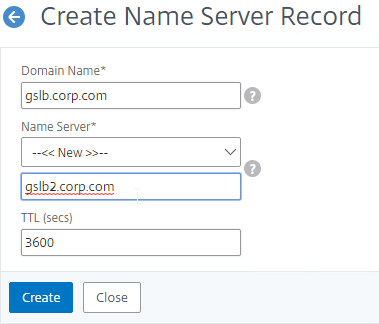
- Repeat this process until all GSLB ADNS FQDNs are specified.
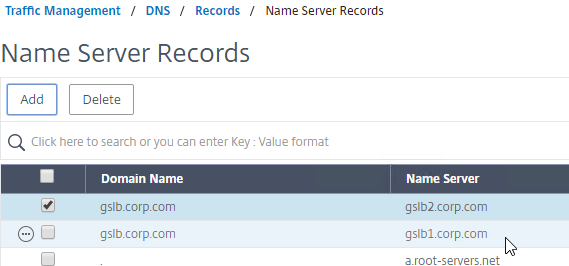
- Also add an SOA record for the delegation. If you are delegating individual records, then you will need an SOA for each record. If you are delegating a subzone, you only need an SOA record for the subzone.
- On the left, in the menu, go to Traffic Management > DNS > Records > SOA Records.

- On the right, click Add.

- In the Domain Name field, enter the FQDN that you delegated to NetScaler. This can be an individual record, or a sub-zone.
- In the Origin Server field, leave it set to –<< New >> — and then enter the FQDN that resolves to one of your ADNS listeners. It doesn’t matter which one you enter.
- In the Contact field, enter an email address that is publicly viewable. Replace the @ symbol with a period.
- Click Create.
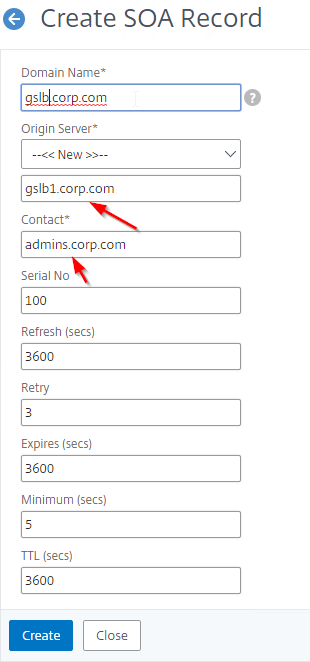
- Repeat this on the other ADCs that are participating in GSLB for this delegated DNS name.
- On the left, in the menu, go to Traffic Management > DNS > Records > SOA Records.
Each GSLB-enabled DNS name must be CNAME’d to GSLB:
- In Citrix ADC, go to Traffic Management > GSLB > Virtual Servers, and edit your GSLB Virtual Server.
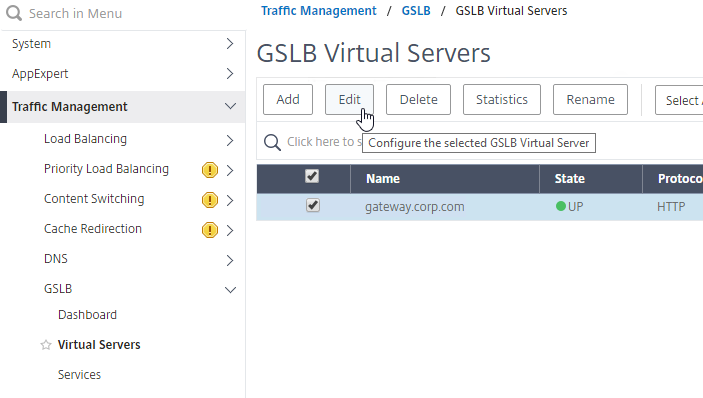
- On the left, click in the GSLB Virtual Server Domain Binding section.
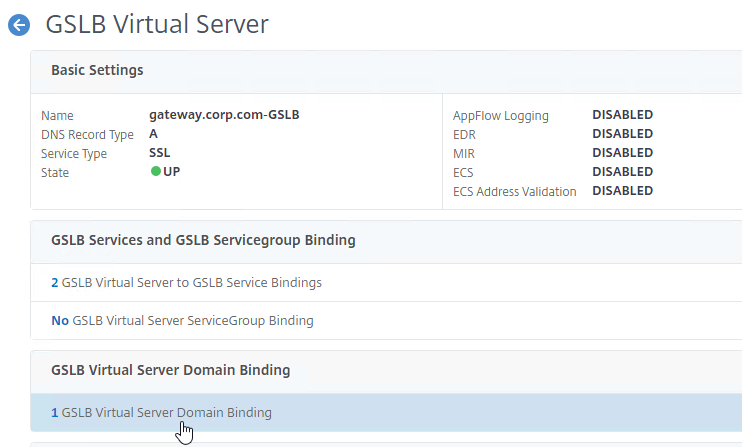
- Click Add Binding.
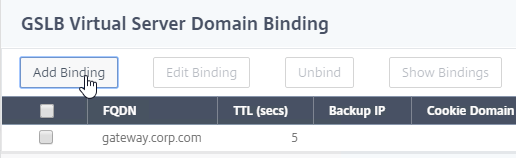
- Add a domain binding for the CNAME’d DNS name. For example, if the original DNS name is gateway.corp.com, then enter gateway.gslb.corp.com. gslb.corp.com matches the sub-zone that you delegated to Citrix ADC. Click OK.
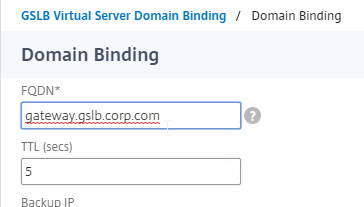
- Repeat the Domain Binding on the other Citrix ADC appliances.
- In DNS Manager, if you currently have a host record for the service that you are delegating to GSLB (gateway.corp.com), delete it.
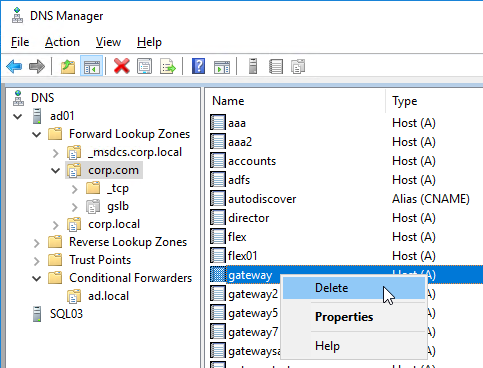
- Right-click the DNS zone, and click New Alias (CNAME).
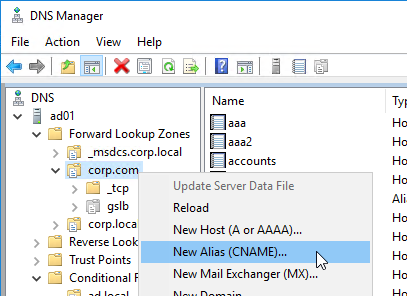
- In the Alias name field, enter the left part of the original DNS name. For gateway.corp.com, enter gateway.
- In the Fully qualified domain name (FQDN) for target host field, enter the CNAME’d DNS name that is delegated to Citrix ADC. For example, if you delegated gslb.corp.com to Citrix ADC, then enter gateway.gslb.corp.com. The GSLB Virtual Server must be configured to match this longer DNS name.
- Click OK.
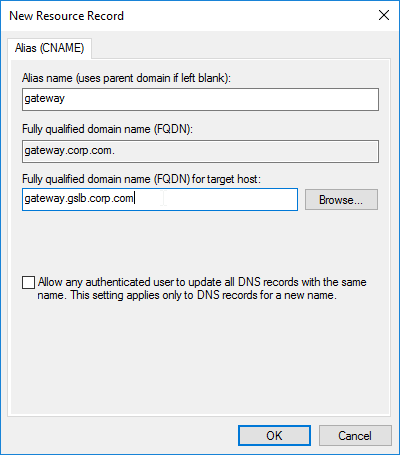
- If you run nslookup for the delegated DNS name, it will first CNAME to the longer name, and then respond with the IP address returned by Citrix ADC GSLB.
- You can repeat these steps to delegate (CNAME) additional DNS names to Citrix ADC GSLB.
Hi Carl,
Thanks for the article. It helped me a lot to understand some crucial points when configuring GSLB but I did not fully get one thing so far. It’s that what SNIP is mentioned in the following sentence “The TCP monitor tries to connect to the GSLB Service Public IP address using the SNIP of the local appliance.” ? Is it “GSLB Site IP address” of the local Citrix ADC?
SNIP. ADC looks in its routing table for the next hop to the destination address. ADC then chooses a SNIP that is on the same subnet as the next hop router and uses that SNIP as the Source IP.
You can run “nstcpdump.sh host” to confirm the source IP.
Hi, Carls, i have a question,I’m trying to make an upgrate for a netscaler versión 10.5 , and wend i try to run this command “create system backup CRM_Cluster -level full” , i have this error, ERROR: Operation not supported in Cluster, what could be the cause of the error?. thanks you.
Looks like no backup for clusters. https://support.citrix.com/article/CTX223257
should, please see this referenceplease look this referencce, https://docs.citrix.com/en-us/citrix-adc/current-release/clustering/backup-and-restore-of-cluster-setup.html , thanks again.
This is really nice, Carl,
How do I integrate Google 2-factor MFA Authenticator at the GLSB, level?
GSLB is just DNS. It doesn’t do HTTP so there’s no way for GSLB to ask for credentials.
Once GSLB returns an IP address to your DNS query, then the browser connects to the IP address, which is usually a Load Balancing Virtual Server or a Citrix Gateway Virtual Server.
How can one integrate google MFA with Citrix Netscaler?
Either through SAML or RADIUS.
Are you asking about Citrix Gateway? Or are you asking about AAA Virtual Server? Or are you asking about management authentication to the NetScaler?
We want all domain users coming externally authenticate with Google Authenticator,
management authentication to the NetScaler
I highly doubt that management authentication (to get to the NetScaler configuration GUI) is reachable from the outside without first launching a VPN. I’m guessing what you really want is to add OTP to your Citrix Gateway.
Where are your user accounts stored? If they are only in local active directory, then see https://www.carlstalhood.com/netscaler-gateway-12-native-one-time-passwords-otp/
If the user accounts are in a cloud Identity Provider, then you typically use SAML. See https://www.carlstalhood.com/citrix-federated-authentication-service-saml/
Users are local on Active Directory,
Hi Carl,
Hopefully you can help me understand this a bit better. I have GSLB configured and working internally, but now I need to get it working externally.
I’m not sure how to do this yet or its going over my head. Our external DNS is Network Solutions which points to our external IP for the domain name.
We have two sites with external access in, but only one site has accepted traffic. Now that we have GSLB enabled on the internal network for the two sites across a VPN connection how can I provide the same from the outside so that if site A goes down our external URL is still accessible via SITE B using Network Solutions as our DNS provider?
Expose your ADNS services to the Internet on Public IPs.
Create GSLB Services that have Public IPs that can reach the website. Repeat on other ADC.
Create a GSLB vServer with the external FQDN. Repeat on other ADC.
In public DNS, delete the existing A record and replace it with two NS records pointing to two new A records that resolve to the public IPs for your ADNS services.
Hi Carl,
What if in GSLB Service i would like to monitor the WAN Link IP instead of any virtual server(s). What PROTOCOL & PORT should i use? Though it is working if i use TCP & PORT 1 in my case but i would like to know the best practice. Thanks.
Rgds,
Willis
You want to monitor a router’s IP? Ping is an option.
Its necesary to enable recursion on principal DNS?
The client machines certainly need to use a recursive DNS server. But you don’t normally configure your clients to use your ADC ADNS as DNS servers so you don’t need recursion on the ADC.
thanks for your answer, but the recursion should be enable on the public DNS? and if that is necessary, what vulnerability occurs using DNS bind
Hi Carl, i’ve got a production GSLB implementaion where the DNS server has an autoritive zone eg: corp.com and subzone gslb.corp.com which delegated to to the ADC.
On the ADC a GSLB domain http://www.gslb.corp.com is configured. Is it possible to implement DNSSEC in the current implementation?where the keys should be made?
Is there any documentaion which coves this senario?
Here is some documentation. https://docs.citrix.com/en-us/citrix-adc/13/dns/dnssec/config-dnssec-gslb-domain-name.html
Hi Carl,
Great article. I am familiar with the Netscaler setup and GSLB with an on prem DNS server with delegation. But unsure how I can achieve the same with an internet DNS server. Do I just create multiple A records with the external ADNS IPs?
Thanks
That’s the first step. Then you create NS records for the delegation that point to the A records for ADNS.
Hi Carl,
If i have an active/passive(backup) datacenter and i want to configure site persistence for StoreFront, how do i do that?
which means i don’t want users to encounter the issues of “Cannot complete your request” i.e. if datacenter from passive moves to active
The persistence settings described below for Duke’s post should work for you. It is interesting that this issue is reported often. I myself have battled with this problem often and have been working with Citrix support on it for many of our customers. I think Citrix needs to do a better job of getting the GSLB to work out of the box, along with a best practice wizard that is updated with each Citrix ADC release. I read Duke’s post and he mentioned his company is using total uptime (at totaluptime.com) to do GSLB. I know exactly what he is talking about. Our company is also using that and setting up GSLB with Total Uptime is as easy as 1, 2, 3. We have clients who are load balancing Citrix ADC across regions using total uptime and it is ironic how simple and flawless it is compared to Citrix’s own GSLB configuration. No issues at all with persistence, as in total uptime is just a simple check box to tick to persist to one data center or another. Literally takes 5 – 10 minutes to configure GSLB in total uptime to front the Citrix gateway running on an ADC, whether you are active / active or active / passive. The instructions and step by step tutorial on this page is impressive, but in the year 2020 to have to go through all these steps manually for the Citrix ADC is just too primitive. There are so many tools that Citrix can use to automate this setup with a couple of clicks, as Total Uptime has done, there is no excuse (Ansible comes to mind). Don’t get me wrong, Citrix ADC is an amazing product and one of the best products Citrix has going for them, but the GSLB configuration is shameful for the year 2020.
The “cannot complete your request” is an extremely common message that occurs in StoreFront (even without GSLB). In my experience, this is often an issue with cookies in the web browser. Clearing out the browser configuration to start clean or using a private browser session will work. I am interested in this topic and would love to hear feedback on how you all have gotten this work.
Hey Marco,
We are in the process of testing the persistence configuration recommended by Carl below and we will provide feedback. Thumbs up for Total Uptime. I am glad other people are using it for GSLB. My recommendation? Use Citrix ADC for internal load balancing and use Total Uptime for GSLB. Will save you a great deal of time and effort. In our case, our company branch requires us to use GSLB on the Netscaler, while the parent company is able to use Total Uptime for GSLB. If your company already has a public cloud presence and you are clear to use a pure cloud solution, do yourself a favor and use Total Uptime for GSLB, while keeping regular internal load balancing on the Citrix ADC.
The way we resolved ‘Cannot complete your request” messages is by ensuring Citrix Gateway URLs are accessed using in private browser mode across sites, no matter if active active or active passive. There are plenty of problems with clients caching this information in the web browser. Accessing the gateway URL in browser private mode ensures the next session will be nice and clean. Still you need to mind the persistence settings in the GSLB services and storefront. If you do not do in private browsing mode you will still get cannot complete your request messages (though not as often), even if you have the persistence settings correct for GSLB. In fact, even without GSLB, your users will occasionally get the cannot complete your request message when you are regularly load balancing storefront with the ADC. Private browsing mode is the only solution we have found that completely makes the cannot complete your request message go away for good.
Has anybody been able to get this to work successfully active-active with published applications via storefront over Citrix Gateway? I’ve been working in the configuration of two data centers one in New York and the other one in California. And while the active-active configuration works we often see messages in the browser of cannot complete your request. The browser must be refreshed a few times for the application to lunch. Does active active work at all opening applications via ICA or is active-active purely for web technologies only? Thank you.
Which persistence type? Connection Proxy? Or Source IP? If Connection Proxy, try disabling Source IP.
Thank you for the response. Our team has tried multiple configurations including connection proxy and source IP. The result is the same. Often we see the message cannot complete your request. I will have one of the guys on my team recheck the configuration and ensure connection proxy is selected, while keeping source IP turned off. Does this configuration work at all (active active) with ICA traffic? I found a couple of posts on Reddit from 2 years ago or so that claim the GSLB active active configuration is problematic with ICA traffic and not reliable on the Citrix ADC. Our parent company is using GSLB via total uptime (a cloud service from total uptime.com) which front ends two Netscalers at the same data centers (same data center location, different vaults) and their GSLB works flawlessly. I know this is not a direct comparison given that in their configuration GSLB is working on total uptime cloud service and not on the Citrix ADC, but they did spend only 5 minutes setting that up on it works flawlessly and we’re still experiencing problems with cannot complete your request. Our configuration is a single Netscaler VPX at each data center running on CentOS KVM. 2 Citrix storefront servers at each datacenter in their datacenter specific server group. Our environment is up and running and users are able to get to their applications from both data centers. However we get many help desk tickets about can not complete your request messages in storefront via the Citrix Gateway. The workaround is to refresh theathe browser afa times until the application can be launched.
Cannot complete your request is a StoreFront HTTP error, not an ICA error. ICA is long-lived TCP connection so once connected persistence shouldn’t matter.
Okay thank you for your response. So you believe this problem to be persistence related? Are you able to provide the location of the persistent settings for GSLB and I will have my team check in their next shift? We have been having this issue now for about a year and our director of IT wants this issue resolved. We also have opened several support cases with Citrix and it has been escalated internally but the problem persists.
In each GSLB service, enable Site Persistence with Connection Proxy. I’m assuming that each ADC can connect to the Gateway on the other ADCs.
In the GSLB vServer, disable Persistence.
Ok. Thank you. I will have my guys recheck that configuration on their next shift. I appreciate your prompt response. I will check all those settings including the storefront persistent settings. I will update this post with findings and or results just so that it can help other people having similar problems.
Also check each of your StoreFront LB vServers and make sure persistence is set to Source IP.
Guys this is an update, we implemented this on Friday and last week and there has been no change. We still get tickets with pictures of cannot complete your request in storefront. Users perform a few refreshes of the site and then they are able to launch the applications. We are going to do another test with this. We are going to point the session polices of the Netscaler to a single Storefront server. We are going to point at the web server IP address directly without using the load balancer to test if the problem occurs without the VIP. I will post back any updates from this. Thank you.
Hi Carl, just wondering whether you know if running GSLB with mixed ADC versions a) works and b) is supported. I’m thinking here of a two site GSLB running 12.0 with a 13.0 VPX – at least until I can upgrade the 12.0 to 13 that is.. 🙂
Cheers,
Rod
I believe it is supported for MEP. There are new GSLB sync features in newer ADC so I’m not sure if that’s impacted.
Hi Carl,
Great article! Have you ever configured the Backup Parent feature and gotten it to work? I find Citrix’s documentation to be a little lacking in that area. I have found this: https://docs.citrix.com/en-us/netscaler/11-1/gslb/gslb-deployment-types/parent-child-topology-deployment.html. An example would be Site A has 1 parent with 2 child sites. Site B has 1 parent with 2 child sites. If site B parent crashes, those 2 child sites would then use Site A as a parent. Per the documentation it looks as simple as configuring Site A as the backup parent to Site B on the config and then the child sites pull that information via MEP. I can’t seem to get the MEP connections to actually work to Site A when I take Site B offline. Any GSLB VIP that points to anything at Site B goes red and stays offline. Thoughts?
IS it a SNIP or VIP that us used to source the traffic when connection is proxied?
I believe it is SNIP. You can use nstcpdump.sh to confirm.
Hi Carl,
Thanks for sharing your knowledge and experience.
I’m have a GSLB (Active/Active) in my DC’s and one of the GSLB ViPs is resolving to vpn.mysite.com. At the moment it’s doing it on a Round Robin bases. I’d like to be able to check number of VPN connections and load balance to the site which has a lower number of active connections. (VPN is terminated on a back-end appliacen; not NetScaler)
What I have done is configured a LOAD monitor, used the corresponding OID and ran a SNMP get request (using the monitor) to check the number of VPN connections. Till this stage it is working perfectly fine and I can see the servers load in ‘stat gslb vserver mygslbvip’ output. But I don’t know how to make the VIP to load balance based on it. It keeps using Round Robin.
This is the partial output of ‘show gslb vserver mygslbvip’ command:
…
Configured Method: CUSTOMLOAD
Current Method: Round Robin Reason: All load monitors are active
…
service 1:…
service 2:…
Warning: Service will be skipped in LB as it has reached threshold
Regards,
This is fixed now and working perfectly fine. 🙂
Any chance you could outline what you did to resolve this? I’m about to attempt something similar (GSLB+customload) and would love to know what you did in case I run across the same issue.
Thanks Carl,
I have already setup GSLB with your article and it is working fine . However on same netscaler I created another LB for different URL.
When I am trying to create GSLB Sites , it says local Site is already present, So if that mean I can’t setup GSLB for another URL that I have setup.?
I am using another Subnet IP as ADNS for new URL. As I already created ADNS service for new URL setup.
You can create multiple GSLB Services in the same GSLB Site.
I didn’t get it. You mean to say I need to use just one ADNS for another GSLB setup? I need not to create another site?
You only need one GSLB Site per appliance.
Each DNS name is a separate GSLB Virtual Server.
Each GSLB Virtual Server has multiple GSLB Services (IP addresses) bound to it.
These GSLB Service are linked to a GSLB Site. Whichever appliance contains the GSLB Server (VIP) is the GSLB Site you should choose. You can create multiple GSLB Services and select the same GSLB Site for each of them.
Hi Carl,
Very helpful article!
Instead of using DNS delegation, I used AD DNS Conditional Forwarders by pointing gateway.corp.com to both nodes ADC ADNS.
This DNS zone “corp.com” is managed externally, so I wanted to bring a specific record for internal use.
My testing shows no issues for GSLB integrated with AD DNS Conditional Forwarders.
Is there any drown back by using Conditional Forwarders instead of DNS delegation?
Thank you,
Vladi
Would also like to know the answer to this, Conditional Forwarders Versus DNS Delegation for GSLB ?
Very nice and helpful article, thank you very much Carl…..
Hi Carl,
Thanks for your Article, iam configuring active/passive 2 sites, but iam having some troubles, in the step configuring active virtual server, i cannot choose the passive server (configured in the standby site), do i need to add a passive server in active site?.
MEP is active between 2 sites, and service also up
GSLB should be configured identically in all nodes participating in the DNS delegation.
Create the Passive vServer first. Then you can select it when creating the Active vServer.
Thanks for your reply, i am a newbie in this major. So i have to create both active vserver and passive server at each sites, or just create passive vserver in passive site and create active vserver in active site then choose the passive server as the backup server is already created in the passive site. Thank you very much
On every NetScaler that has ADNS services, create both the Passive vServer and the Active vServer.
Hi Carl ,
If i have an Active-Active setup and i would like manually to send all the traffic to the one only Datacenter Netscaler , what is the best way to do it , without disconnect the possible active users ? Is there any smooth way to isolate the one Netcaler for maintenance ?
BR
Prodromos
It depends on the kind of connection. If long-lived TCP connection (e.g. ICA), then changing DNS (i.e GSLB) won’t affect the existing connections. Short-lived connections that query DNS frequently (e.g. HTTP) will switch over once you change the GSLB configuration.
Thanks Carl ,
I was thinking of disable the GSLB LOCAL services to the Netscaler i want to maintenance .
An action like this would stop the new users to login and use this netscaler (GSLB would send the traffic to the other one) ? And when the already active connected users disconnect to start the maintenance ?
Thanks again for your time
Makis
Carl,
I’m a bit fuzzy on how to setup the CNAMEs in an Active-Passive configuration.
If I have the following…
GSLB Active Virtual Server – test.abc.com
GSLB Backup Virtual Server – testbackup.abc.com
FQDN – test.gslb.abc.com
CNAME – test.abc.com with Canonical Name test.gslb.abc.com
CNAME – testbackup.abc.com with Canonical Name test.gslb.abc.com ??? is this correct
You don’t need the backup DNS name unless you want to explicitly connect to backup even if the active vServer is up. Your Active vServer will apply the prod DNS name to the backup vServer if the Active vServer is down.
Can we configure a different remote site IP for MEP, and different remote site IP for GSLB sync?
Thank you for such a great article. I have successfully configured Active-Active GSLB using this article. However, the site doesn’t work on Apple devices or Safari.
What do you think could possibly be causing this?
My DNS configuration is as such:
Akamai->Imperva Web Application Firewall->Netscaler.
Are you saying the Apple can’t resolve the DNS name?
Hi Carl
I have a problem in the configuration of active / active gslb, for applications that have a configuration file that refers to a gslb domain, in this case the result is that data centers are crossed, and this situation is not desired. What we need to implement is an active / active gslb where requests always remain in the same data center and I can also put persistence in balanced services.
Can you give me recommendations for this implementation?
Thank you
Probably depends on the app. One option is to create separate DNS names for each data center but configure each DNS name as active/passive and configure different users/endpoints with different DNS names. Another option is to configure the app to perform a redirect to a data center-specific DNS name after the user’s identity has been determined.
GSLB vServers and Services certainly support persistence but the duration is usually only for the one session.
Thanks Carl
I have tried to apply static proximity and dns policies but it does not work for me to maintain the data center when applications call other globally balanced applications.
I found this article:
https://docs.citrix.com/en-us/netscaler/12/global-server-load-balancing/how-to/manage-client-connections.html
But I have not made it work. You have additional exceptions to this topic.
Thank you
Hi Carl,
Thanks for this.
I have a question, for the firewall policy can we can stick with port 3011 only and not 3009 if our ADC is behind the firewall?We just need to ensure that Private IP will be NAT’d to the public IP addresses?
3009 is encrypted while 3011 is not.
Thanks so much Carl for the response. Appreciate it. 🙂
So you are saying that it is much better to use port 3009 instead of 3011 because it is encrypted?
What would be the use case if we use encrypted port(3009)? I’ve read your article about this port and I’m just confused. What I understand in your post is that we will used port 3009 if we route the MEP across the internet.
So it means if we will be using public IP’s for MEP am I correct?
if we will use private IP for MEP then we will just NAT’d the public IP addresses to private MEP IP addresses on the firewall so in this case port 3011 will suffice.Let me know if my understanding is correct or not. Thanks
Your article really helps me on my ADC deployments.
keep it up Carl! 🙂
Edit the RPC nodes and check the Secure box. That changes it to 3009.
Routing MEP across the Internet is optional.
Carl,
Are GLSB and AAA compatible when using services with different authentication requirements that use a single DNS name? I don’t see a way how to switch the content because GSLB only supports DNS based expressions and we have to inspect the HTTP packet to determine if the traffic is destined for Outlook Web Access or ActiveSync. I believe separate DNS names for each service may be the only option. Any thoughts?
Carl,
Have you ever seen an Exchange 2016 GSLB deployment with AAA authentication enabled? Works for OWA only, but if OWA and ActiveSync are both required externally there is no way to use content switching to switch the traffic to separate virtual servers with different traffic policies bound to meet the different authentication requirements for each service. (OWA uses FBA, AS uses 401) I suspect this won’t work unless we use different DNS names for each service but support has not confirmed this yet. Just curious if you had ever seen this config and/or if my suspicion is accurate. Appreciate the work on the site!
We are presently stuck on a Netscaler GSLB deployment for Microsoft Exchange 2016 involving pre-authentication using AAA authentication and traffic policies. OWA and ActiveSync are a requirement to be published externally but I believe that the GSLB and AAA features are incompatible with this product based on the authentication requirements for each Exchange service. OWA uses FBA while ActiveSync uses 401. These are configured in separate traffic policies which can’t be bound to the same LB vServer, which is where our problem is. We need to use content switching to switch the traffic between the OWA and ActiveSync virtual servers, but we can’t use URL expressions on a Content Switch that is tied to a GSLB virtual server. Have you ever seen a config like this? I highly suspect that this won’t work without separating DNS names for each service (OWA and AS) but Citrix support has yet to confirm. GSLB Selection is out as it uses DNS based expressions, not URL. Not after instructions, but if you have any thoughts on this I’d greatly appreciate some expert insight on this one. Thanks for the site info by the way, Citrix leaves much to be desired on the documentation front….
Hi Carl, have you ever delegate a subdomain from NetScaler to a Windows DNS?
I was following https://support.citrix.com/article/CTX135580, I do get back the NS Records from the nslookup search but it does not resolve the server IP address.
In my scenario I need to answer some DNS Queries with the NetScaler ADNS Service (those services are running on GSLB) but for other sub-domains I just need to forward the DNS Query to a Windows DNS Server. However when I´m not able to get any DNS response from the sub-domains that I forward. Do you have any ideas on this regard?
Did you create the CNAMEs?
Did you configure the GSLB vServers to match the alias name, not the original name?
See https://carlstalhood.com/global-server-load-balancing-gslb-netscaler-12/#delegatesubzone
I have error when accessing throgh GSLB on Storefront “Your logon has expired. Please log on again to continue”
I can access correctly on both NS through VIP with SSON. Something not right on GSLB config, any idea?
Persistence is enabled on either the GSLB Services (Connection Proxy) or GSLB vServer?
Hi Carl
When we create GSLB service and its for netscaler gateway, does it takes all the SSL settings underlying from the VServer created under netscaler gateway or do we have to reconfigure the SSL settings? I.e. ciphers, dh params. I do not have a default ssl profile bounded globally.
I’ve checked with Citrix engineer and he mentioned that configuration of ssl ciphers to be on the Vserver of NSG however i just checked via ssllabs.com it appears that ciphers that i have not defined are appearing there and which i suspect its not configured on the SSL settings of the GSLB service (tagged to the vserver).
GSLB is DNS, not SSL.
GSLB Service uses back-end SSL settings to monitor whatever IP address you entered. It is not front-end because GSLB is DNS.
Hi Carl
That’s what i initially though so that GSLB is DNS. But when i did a check recently, my NSG VIP bounded custom SSL cipher groups were not showing as to what i had configured.
Hi Carl,
Amazing guide. Thank you.
Currently I am very close to having this working and ‘Test GSLB’ is returning a correct single address depending on the status of the sites.
However, when performing an nslookup externally against the ADNS listeners (or when doing a plain nslookup with no DNS server specified) I receive the message…
“No internal type for both IPv4 and IPv6 Addresses (A+AAAA) records available for ******.******.co.uk.”
Do you know what might be causing this?
For nslookup on Windows, you type in “server x.x.x.x” where x.x.x.x is the IP address of your ADNS service. Make sure UDP 53 is open between nslookup and the ADNS service.
Hi Carl,
Thanks for the reply 🙂
This is the syntax I was using but have just double checked and I am receiving the same response. When requesting resolution for http://www.google.com I receive a correct answer from the ADNS listener. I only get the previous error when looking for my GSLB name.
Maybe you have a proxy device or firewall that is intercepting the DNS request? You shouldn’t be able to resolve non-GSLB names from the ADNS service.
Thank you for the tip! Turns out because I am using a Guest WiFi network for testing it was intercepting all DNS requests made from my testing laptop. I tethered the laptop to my phone and now get a valid response when performing an nslookup directly against the ADNS service.
However, when I perform an nslookup against Google DNS I now just receive…
Name: xxxxx.xxxx.co.uk
Do you have any other pearls of wisdom? 🙂
ADNS service is not recursive, by design. It’s usually not needed in a typical GSLB configuration. If you think you need recursion, then see https://support.citrix.com/article/CTX118189
Hi Carl,
Thank you for the link. I dont think having the ADNS be recursive is required for us either.
I am not getting an IP when looking up the GSLB name against public DNS. It just provides the response in my previous reply. Confirms the Name and that is all.
I have noticed our external web-based DNS provider has added their own SOA record alongside the name server records we have added pointing to our ADNS services. This SOA cannot be changed and refers to some of their own servers. Does this sound right? I can confirm our ADNS services are the only name servers listed under this subdomain though.
Thank you
Carl. Can you please expand on this section “One appliance resolving a single DNS name differently for internal and public”
To work around this limitation, create two separate GSLB Virtual Servers with different monitoring configurations. Internal DNS uses a CNAME record to reach the GSLB Virtual Server configured for internal monitoring:
The monitor is at the GSLB service level, however, you cannot create 2 services with the same port and service type. You get this message “Service exists with the same port and service type”.
Thanks as always!
Can you do it with GSLB Service Groups?
Yes I can. Thanks. Is there a way to make a GSLB VS dependent on another. Or even better, make a LLB Service group dependent on each other. I am in a situation where I want all the VIPs to fail if one of them fails. However, I get stuck where both service groups are down because they are monitoring each other. Thanks again.
Hi Carl,
I have a “design” question. I have 2 datacenters seperate by a layer 2 link. Site A is considered the active site and B the passive site. Internet redundancy is provided by 2 seperate providers. The provider routers are also split over the 2 datacenters. (HSRP). Site A is considered the active and can load balance between the 2 proividers. How many clusters do i need in this case for GLSB? Can I do it with1 pair or do i need 2 pairs?
Thank you.
Frederik
Are you asking specifically about ADC and not asking about CVAD?
Stretching a pair of ADC nodes increases the risk for split brain where both nodes try to be active at the same time if they lose connectivity to each other. Pairs are also active/passive where only one node is live. My preference is separate HA nodes in each datacenter, which allows me to have active VIPs in both datacenters.
Hi Carl, I’m configuring a SSL service with GSLB connection proxy site persistence. How do I know which is the expiration time of the cookie? Thanks!
Mónica
I believe GSLB session persistence cookies don’t have an expiration date/time, meaning they expire at the end of the browser session.
Hello Carl
I have a quick question regarding active/Active GSLB. My scenario as below:
I have two datacenters (A and B) with GSLB configured between them of them with optimal gateway routing. I have to sites configured in each datacenter and they are Storefront is grouped between both datacenters. Everything working great as long as both ADC are online in DCA and DCB.
When i disable vServer in DCA, the traffic get redirected to the DCB and users are able to login. they are able to launch applications in this DCB but not in the DCA anymore. Currently only the NS is down but the full infrastructure are up and running.
Should the NetScaler redirect the traffic over the site to site VPN? OR it will only be able to access the resources in DCB ONLY till NS in DCA is back online?
what if I have specific applications published in DCA and not published in DCB?
I need to be able to launch the application in DCA even if the NS is offline. Will this be possible?
Thanks
Sam
Are you able to see the icons in DCB? Then you get an error when you launch an icon? Does DCB Gateway have all STAs configured? Does DCB have firewall access to all VDAs in DCA?
Hey carl, i have a question. if i have implemented GSLB for internal and external, plus a single FQDN, what should i put in for the wiAddress for my session policies? I’m hitting someone unknown DNS issue whereby failing over the GSLB active-passive would cause the ADC within to somehow unable to resolve the FQDN in my session policy, and it’s stuck at Loading Apps (keep circling) only workaround was specifying a https://ip address/xxx instead across both ADC session policy for XA/XD. However i have tested nslookup on internal network and also via internet, the IP addresses returned are all correct. Secondly, would specifying an ip address in the wiAddress be of any issue if there isn’t any workaround?
I usually enter IP Address instead of DNS name.
Is it possible to configure a GSLB (active/passive) with a HA VPX pair in each datacenter?
Yep. That’s what I detail in this article.
Hi Carl,
In my testing it seems GSLB also functions correctly just by adding the Netscaler itself as a local name server (Traffic Management / DNS / Name Servers), instead of creating ADNS services. In such cases, GSLB VSs end up with no ADNS services listed but it doesn’t seem to impact functionality.
Is there a down-side of configuring it this way?
Cheers.
The goal is for external DNS servers to be able to ask NetScaler to resolve GSLB-enabled DNS names. Does your method accomplish that?
I only tested internally, but yes, it did resolve as expected. If I use ADNS Services it is a lot quicker to resolve, which I can’t explain.
Internally, via Windows DNS, it doesn’t seem to matter that the Netscaler is not authoritative (ie. it works the same with or without SOA records).
GSLB also works when ADC is a DNS Proxy. ADC will check GSLB for DNS records first. If none found, then ADC asks the external DNS servers for records.
Thanks, I just thought it wouldn’t respond unless it was authoritative for a zone/record.
Hey Carl, We have an issue with DNS Proxy. DNS is returning A records without any issues. Its that its sending NXDOMAIN for ANY query. I checked Citrix documentation and it says “For the NetScaler to return these records when it responds to the ANY query, all records corresponding to a GSLB domain must be configured on the NetScaler.” But when I try to create a test url lined to a GSLB domain i get the following error: “Operation not permitted on a GSLB-configured domain”
Any idea?
Hi Carl,
Nice article. I am trying to design a Highly available infrastructure and would like to get your opinion if the below scenario works for me or not?
I am having a GSLB Domain between two US GSLB Active-Passive Sites. I need to create another GSLB Domain between Germany and US region(existing GSLB Domain) so that in the event of German DC failure I need to connect to the Active US site.
Let me know your thoughts.
Two DNS names? So you need a single VIP to respond to both DNS names? Just make sure the certificate matches both DNS names.
Thanks Carl for your response.
Hi Carl
First of all a big thanks. With help from your articles I was able to successfully deliver my first GSLB Project.
We used GSLB to distribute load between two sites from internet so External GSLB was configured.
Now I was trying to configure Internal GSLB. As recommended instead of relying on DNS Views I wanted to configure a separate ADNS for Internal. I have two issues here
First Netscalar does not allow to configure a duplicate GSLB Service with Internal IP as “Public IP”. Secondly if a create an additional ADNS Service it automatically gets binded with all existing GSLB vServers.
Need expert thoughts here.
Expert opinion is separate NetScalers for internal and external. 🙂
Hi
I am trying to use same Netscalar for Internal and External . However I am unable to Create two GSLB Services with same Server IP.
I want to create two Services where “Public IP Fields” are different so that IP Addresses returned are different.
Hi Carl,
your articles are too informative and helpful for me
I will need your help on a specific issue please
Currently I have an Active-Active standalone NetScaler configuration with Azure Load Balancer and load balancing working fine .But when I logon on one NetScaler redirects me for authentication to another and so on (loop).
If disable one Netscaler Gateway Virtual Server from two (no mater which one) the logon process and delivery through storefront working fine. Netscalers have exactly the same configuration excepts VIP and NSIP of course.
What do you think?
Thanks in advance
Is this GSLB? Or is this Azure LB? In either case, is persistence configured?
Thank you for prompt answer
Is Azure LB
I have configured only Netscaler Gateway Virtual Server on both appliances ( not load balancing on Traffic Management)
Do you believe that no configured persistence is the problem?
Can you give me some advices on how to configure peristence ?
Client ip persistence is configured on the Azure load balancer, not NetScaler.
Thank you very much Carl
i totally dismissed this configuration now everything is up and running
By the way, i have one more question
I am trying to install additional DDC, SF but when i finished the roles installation (DDC,SF) on target server
and opening Citrix studio for some reason the site is already there and i cant find way to add Delivery Controller to existing site.
Can you also assist me on this ?
Are you running Studio on a remote machine? If so, open a new MMC and add the Studio plug-in and point it to the new Controller. Or maybe delete “%appdata%\Microsoft\MMC\StudioSF”
Thank you for the prompt reply
Is Azure external LB
i have configured only Netscaler Gateway Virtual Server on both apliances(no load balancing through traffic management)
Do you believe that the not configured persistence is the problem?
Can you give me some advices on how to configure persistence ?
I am running Studio on the server where DDC and SF roles installed
And i cant find way to add delivery controller on exisitng site because the site appeared on studio automatically and showing only the primary created DDC
No problem with adding storefront to existing server group
I’ve been reading your articles about Horizon and Netscaler and it’s really been saving my job! This is my first crack at GSLB.
we plan on deploying a highly available active/active Horizon deployment with both internal and external access using “horizon.domain.com” as our access point. our users would be directed to the proper horizon cluster based on IP proximity.
I’m working on setting up GLSB and Horizon LB on 2 HA Pairs of SDX appliances at separate sites. At each site, I have already configured 2 LB VPX (one internal and one external) and a GSLB VPX. I would like to have the GSLB VPX read the state of the Virtual servers on the LB VPX to be able to provide the proper cluster in the event of a failure.
Do I need to deploy MEP on the LB appliances as well?
Yep. You can do parent-child MEP. Or you can mesh the MEP between all appliances.
Hi Carl,
Right now I am deploying GSLB between DC and DR size by follow your guide. But I had met an issue related to effective state of service on DC site. State always down, although I had bind service to vServer. Any ideal for troubleshoot this case?
Did you bind a monitor to your GSLB Service? https://support.citrix.com/article/CTX125846
Did you bind a monitor to your GSLB Service? https://support.citrix.com/article/CTX125846
Hi Carl
Using GSLB to distribute users between Netscaler Gateways – everything working as expected, but only on HTTPS.
I am trying to get http>https redirect to work (as we would with a Netscaler Gateway w/o GSLB: when users enter http://NSGW_address they’ll get redirected to https://NSGW_address).
Tried many combinatons of LB vservers with responder policy, redirect URL, etc. but no success so far – it either doesn’t work, or I am not allowed to configure it in Netscaler (resource exists, not allowed, etc.).
I thought I found the solution here: https://support.citrix.com/article/CTX130152, but it seems to assume that GSLB will serve functional services for both HTTP and HTTPS, which is not the case, when we just need to get to the Netscaler Gateway.
Do you have an idea on how to get it to work ?
Thanks
Jacob
Hmm…I may have been chasing ghosts here – it seems that http redirect will work without any special considerations regarding GSLB.
I set it up in my homelab:
SSL GSLB vserver
HTTP LB vserver in down state with https redirect URL
– and it works: will respond to both http and http requests and http is redirected to https.
This thread confirmed that it didn’t require any special config:
https://discussions.citrix.com/topic/335265-http-to-https-redirect-when-using-gslb/
hi Carl, great article. A question relating to GSLB service configuration, is possible with lb metod “static proximity” set a default site, if there is’t a pxoimity match on the db ?
I think the default behavior is to revert to Round Robin. Maybe you can add custom entries to the Static Database. Or use DNS Policies to choose a preferred location. https://docs.citrix.com/ko-kr/netscaler/11-1/gslb/override-static-proxim-by-using-preferred-locations.html
Hi Carl –
Great article. A question relating to GSLB service configuration. The article/documentation says;
“Remote NetScaler VIP – If the GSLB Service IP is a VIP on a remote appliance, then GSLB will use MEP to ask the other appliance for the state of the remote traffic Virtual Server. In both cases. There’s no need to bind a monitor to the GSLB Service.”
So, if the GSLB Service references a Virtual server on different physical Netscalers (not those configured for GSLB), do you have to configure MEP between them?
Regards,
James
If you don’t want to bind a monitor to the GSLB Service, then yes.
Hi Carl –
I see, thank you for the reply.
My view would be to bind a suitable monitor in order to keep a clear division between GSLB configured devices and regular L4-7 loadbalancer devices (even if they are Netscalers). Would you agree?
Regards,
James
For Public GSLB, you usually want to monitor Internet connectivity on the other side. MEP can only do that if MEP is routed across the Internet.
In some cases, services need to reside in a data center where there is no NetScaler performing local load balancing. In such a case, create a placeholder site, and disable MEP so that no data exchange is attempted, then associate the service with the placeholder site.
Carl,
If we have a netscaler pair for internal and external configured for GSLB, is it best to configure them as individual GSLB setups. Both internal and external clients are connecting to same back end infrastructure via content switching VIPs, Goal is for both internal and external clients to be failed over and avoid a situtaiton wher internal hasn’t failed over, but external has.
I try to do separate, but there’s no requirement to do so.
With separate, external DNS Resolvers can’t resolve internal DNS names.
With separate, you can have different failover policies for external vs internal. If Internet goes down, you want external to fail over, but not necessarily internal.
Hi Carl,
Thank for you post, it is very useful for me. I follow this, but the GSLB site status always down. Do you have any suggesstion?
It’s usually firewall. Check the firewall logs for port 3009 or 3011. You can also run “nstcpdump.sh port 3009” on each NetScaler to see the traffic.
HI Carl, it is so nice to see you reply. I also run the “start new trace” function in the diagnostic part. I can see the 2 nodes exchange their information on the port 3009 or 3011, but the site status still down.
Do the RPC nodes have the same password? Is it a complex password? Try a simple password.
Thank you Carl,
It is because I did not bind a node to node group in my cluster. The problem is resolved.
This is a really good Article, steps by steps
WOW, Carl, this is a stunning article.