Navigation
Overview
If you plan to use LDAP (Active Directory) for NetScaler Gateway or NetScaler management authentication, load balance the Domain Controllers that are used for authentication.
An alternative to load balancing is to configure NetScaler Gateway and NetScaler management authentication with multiple authentication policies, each pointing to a single Domain Controller. However, NetScaler will try each authentication policy until it finds one that works. If the user enters a wrong password and if you have three authentication policies pointing to different Domain Controllers in the same domain then three different failure attempts will be recorded thus causing premature account lockout. Use Load Balancing to avoid this behavior.
This page details LDAPS, aka Secure LDAP. This protocol requires certificates to be installed on the Domain Controllers. When a user’s password expires, Active Directory does not allow password changes over clear text LDAP so LDAPS must be used instead. Make sure you have certificates installed on your Domain Controllers. The easiest way to accomplish that is to deploy a Microsoft Certificate Authority. Once that’s done the Domain Controllers will request certificates automatically.
An ldaps monitor can be used to verify that the Domain Controller is functional. The ldaps monitor will login as an account, perform an LDAP query, and look for a successful response. The ldaps monitor uses a service account to login. Make sure the service account’s password does not expire. Domain User permissions are sufficient. Since this monitor is a Perl script, it uses NSIP as the source IP. You can use RNAT to override this as described in CTX217712 How to Force scriptable monitor to use SNIP in Netscaler in 10.5.
If you have Domain Controllers in multiple datacenters, you can create multiple load balancing Virtual Servers and cascade them so that the local Domain Controllers are used first, and if they’re not available, then the Virtual Server fails over to Domain Controllers in remote datacenters.
The Load Balancing Virtual Server for LDAPS can be TCP or SSL_TCP:
- If the protocol is TCP, then SSL-encrypted LDAP traffic is not terminated on the NetScaler, and is simply forwarded to the LDAP servers. If your LDAP client needs to verify the LDAP server certificate, then this Load Balancing configuration will not work, since each back-end LDAP server will have a different certificate.
- If your Load Balancing Virtual Server is protocol SSL_TCP, then a certificate must be installed on the NetScaler and bound to the Load Balancing Virtual Server. SSL is terminated at the NetScaler and re-encrypted before sending it to the destination Domain Controller. The primary benefit of NetScaler SSL termination is that your LDAP clients can verify the Virtual Server SSL certificate.
When NetScaler uses a local (same appliance) load balanced Virtual Server for LDAPS authentication, the traffic is sourced from the NetScaler SNIP (Subnet IP). When NetScaler uses a direct connection to a Domain Controller without going through a local Load Balancing Virtual Server, or if NetScaler uses a remote (different appliance) Load Balancing VIP, then the traffic is sourced from the NetScaler NSIP (NetScaler IP). Adjust firewall rules accordingly.
LDAPS Monitor
Note: Perl monitor uses NSIP as the source IP. You can use RNAT to override this as described in CTX217712 How to Force scriptable monitor to use SNIP in Netscaler in 10.5.
- In the NetScaler Configuration Utility, expand Traffic Management, expand Load Balancing, and click Monitors.
- On the right, click Add.
- Name the monitor ldaps-Corp or similar. The ldaps monitor logs into Active Directory, performs an LDAP query, and looks for a successful response. The monitor configuration has domain specific information so if you have multiple Active Directory domains, then you will need multiple ldaps monitors. Include the domain name in the monitor name.
- Change the Type to LDAP.
- Scroll down and check the box next to Secure.
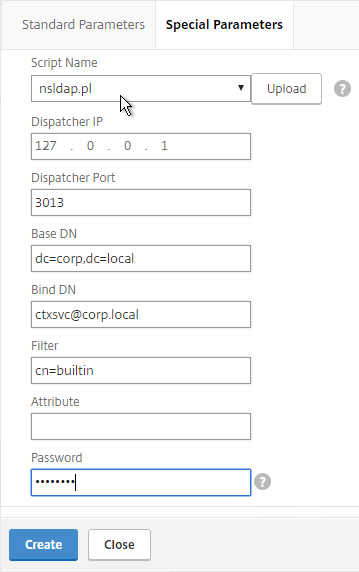
- Scroll back up and switch to the Special Parameters tab.
- On the Special Parameters tab, use the Script Name drop-down list to select the nsldap.pl file.
- In the Base DN field, enter your domain name in LDAP format (e.g. dc=company,dc=com)
- In the Bind DN field, enter the UPN login (e.g. ctxsvc@company.com) of a service account in the domain that can browse all objects. Any normal Domain User should be sufficient. Just make sure the password doesn’t expire.
- In the Filter field, enter cn=builtin. This limits the search results.
- In the Password field, enter the password for the service account. Make sure there is no semicolon in the password or the script will be unable to parse the parameters.
- Click Create.
add lb monitor LDAP-Corp LDAP -scriptName nsldap.pl -dispatcherIP 127.0.0.1 -dispatcherPort 3013 -password Passw0rd -secure YES -baseDN "dc=corp,dc=local" -bindDN "corp\\ctxsvc" -filter cn=builtin
- If you have multiple domains then create additional monitors: one for each domain.
Servers
- On the left, expand Traffic Management, expand Load Balancing, and click Servers.
- On the right, click Add.
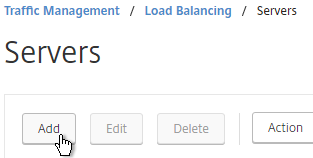
- Enter a descriptive server name, usually it matches the actual server name.
- Enter the IP address of the server.
- Enter comments to describe the server. Click Create.
add server AD01 10.2.2.11 add server AD01 10.2.2.12
- Continue adding Domain Controllers.
Service Groups
- On the left, expand Traffic Management, expand Load Balancing, and click Service Groups.
- On the right click Add
.
- You will create one Service Group per datacenter. Enter a name reflecting the name of the data center. Also, you will create a set of service groups per Active Directory domain so include the domain name.
- Change the Protocol to SSL_TCP. Scroll down and click OK.
- On the left, in the Service Group Members section, click where it says No Service Group Member.
- If you did not create server objects, then enter the IP address of a Domain Controller in this datacenter. If you previously created a server object, then change the selection to Server Based, and select the server object. In the Port field, enter 636 (LDAPS).
- Note: Any Domain Controller you add to this list must have an SSL certificate installed. The easiest way to install SSL certificates on the Domain Controllers is with Active Directory Certificate Services since it installs the certificates automatically.
- Click Create.
- Click OK.
- On the right, in the Advanced Settings column, click Monitors.
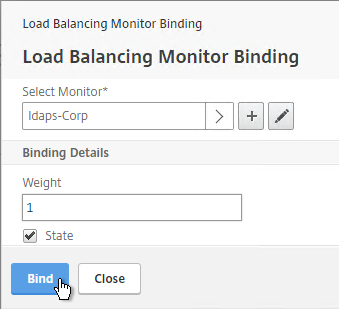
- On the left, in the Monitors section, click where it says No Service Group to Monitor Binding.
- Click the arrow next to Click to select.
- Select your new LDAPS monitor and click Select.
- Click Bind.
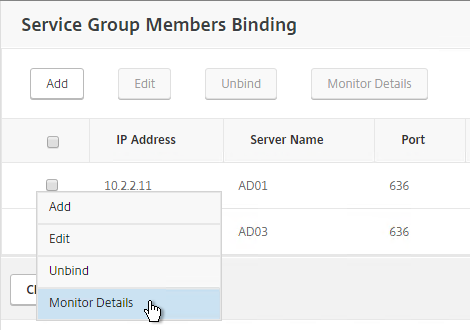
- To verify the member is up, click in the Service Group Members section.

- Click the ellipsis next to a member and click Monitor Details.
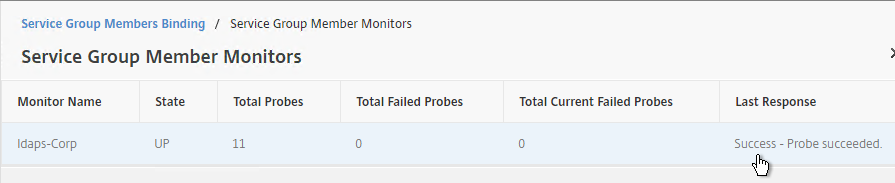
- It should say Success – Probe succeeded. Click Close.
- If the monitor doesn’t work, use ldp.exe to verify the Domain Controller certificate.
- Click Close and Done to finish creating the Service Group.
add serviceGroup svcgrp-LDAP-Corp SSL_TCP bind serviceGroup svcgrp-LDAP-Corp AD01 636 bind serviceGroup svcgrp-LDAP-Corp AD02 636 bind serviceGroup svcgrp-LDAP-Corp -monitorName LDAP-Corp
- Add additional service groups for Domain Controllers in each data center.
Virtual Server
- Create or import a certificate that matches the FQDN that resolves to the new Load Balancing VIP for LDAPS.
- On the left, expand Traffic Management, expand Load Balancing, and click Virtual Servers.
- On the right, click Add.
- Name it LDAPS-Corp-HQ-LB or similar. You will create one Virtual Server per datacenter so include the datacenter name. Also, each domain has a separate set of Virtual Servers so include the domain name.
- Change the Protocol drop-down to SSL_TCP.
- Enter a Virtual IP. This VIP cannot conflict with any other IP + Port already being used. You can use an existing VIP that is not already listening on TCP 636.
- Enter 636 as the Port. Click OK.
- On the left, in the Service Group section, click where it says No Load Balancing Virtual Server ServiceGroup Binding.
- Click the arrow next to Click to select.
- Select the previously created Service Group and click Select.
- Click Bind.
- Click Continue.
- On the left, in the Certificates section, click where it says No Server Certificate.
- Click the arrow next to Click to select.
- Select a certificate that matches the FQDN that will resolve to this VIP. Click Select.
- Click Bind.
- Click Continue.
add lb vserver lbvip-LDAP-Corp SSL_TCP 10.2.2.210 636 -persistenceType NONE -cltTimeout 9000 bind lb vserver lbvip-LDAP-Corp svcgrp-LDAP-Corp
- If you haven’t enabled the Default SSL Profile, then perform other normal SSL configuration including: disable SSLv3, and bind a Modern Cipher Group.
bind ssl vserver MyvServer -certkeyName MyCert set ssl vserver MyvServer -ssl3 DISABLED -tls11 ENABLED -tls12 ENABLED unbind ssl vserver MyvServer -cipherName ALL bind ssl vserver MyvServer -cipherName Modern bind ssl vserver MyvServer -eccCurveName ALL
- Click Done to finish creating the Virtual Server.
- The new Virtual Server should show as Up.

- Create additional Virtual Servers for each datacenter. These additional Virtual Servers do not need a VIP so change the IP Address Type to Non Addressable. Only the first Virtual Server will be directly accessible.
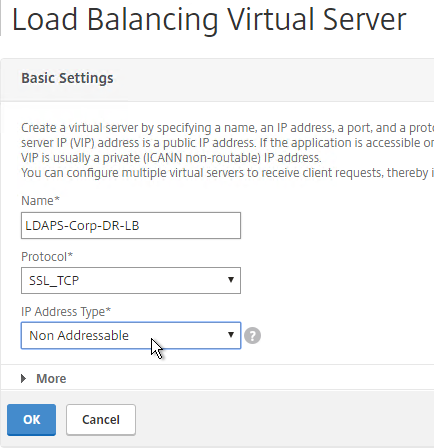
add lb vserver lbvip-LDAP-Corp-Backup SSL_TCP 0.0.0.0 0
- Notice that the additional datacenter Virtual Servers show up with an IP Address of 0.0.0.0 and port of 0.
- After you are done creating a Virtual Server for each datacenter, click the ellipsis next to the primary datacenter’s Virtual Server and click Edit.
- On the right, in the Advanced Settings column, click Protection.
- On the left, in the Protection section, change the Backup Virtual Server to one of the other datacenter Virtual Servers. If all of the services in this datacenter are DOWN, the backup Virtual Server will be used instead. You can cascade multiple Virtual Servers using this method. Click OK and Done.
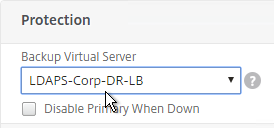
set lb vserver lbvip-LDAP-Corp -backupVServer lbvip-LDAP-Corp-Backup
Next Steps
You may now use this Virtual IP in your LDAP authentication policies for NetScaler Gateway or NetScaler management login.
Hey Carl! Really like this write up, and we’ve had an NS VIP for LDAPS authentication in place for years without issue. Recently, we began using the Active Directory “Protected Users” group for certain users, and we find that they can’t authenticate with the NS VIP any longer. I believe this is because the VIP only load balances 636 for LDAPS, and Protected Users require Kerberos. Have you run into this yet? Any thoughts on the best way to deliver both LDAPS (with cert) as well as Kerberos auth? Is it replacing the existing VIP with a new one with >1 port, or just adding new VIPs for TCP/UDP 88?
Thanks!
I am having a lot of issues with setting up the LDAPS monitor and have been forced to resort to just TCP which I would prefer not to use. Version is Citrix ADC NS13.0: Build 64.35.nc,
I have done the following to eliminate environmental causes on the DCs
Tested the Firewall 636 ports are open on both DCs
Tested the LDAPS connection using a Powershell script and also ldp.exe and both succeed
Test-LDAP -ComputerName “DC1”
Test-LDAP -ComputerName “DC2”
Computer : DC1
ComputerFQDN : DC1.domain.com
GlobalCatalogLDAP : True
GlobalCatalogLDAPS : True
LDAP : True
LDAPS : True
AvailablePorts : 389,636,3268,3269
Chosen SSL_TCP as the service type for LDAP services that are being load balanced but the LDAPS monitor never returns success.
A basic auth policy action which connects to the same 2 DCs succeeds with SSL and 636 selected and a AAA vServer that uses this LDAP auth action also works. Its the monitoring of LDAPS that seems problematic when TCP is not used. Any tips to debug this further?
The LDAP monitor is a Perl script so it comes from the NSIP.
You can try the debug script – https://support.citrix.com/article/CTX227727
Great article Carl, In an environment where few windows servers present which are hosting dns, ldap, ldaps, RPC and Kerberos services. How can all these service be achieved by creating a single vip in netscaler.
If I create a single vip with any protocol & any port & put the backend servers to windows servers – Then I will be missing out features such as dns security, waf etc.
So what is your suggestion on loadbalancing dns, ldap, ldaps, RPC and Kerberos services….
Hi Carl, we are utilizing LDAP VIP’s through our our organization for various applications that need LDAP authentication or even DNS and other AD services Global catalog, etc.. We have multiple locations globally. In most of these locations we have a netscaler. So we have local LDAP VIP’s setup on these netscalers. But we would like to use GSLB on the netscaler to Load balance LDAP to 1 VIP and have it globally load balanced across the netscalers. Is there any special considerations to accomplish this?
Thanks.
GSLB is just DNS so it shouldn’t be a problem.
Hello Carl,
I created this LDAP Load balancer (without certs) – so just with 389port. Without gateway.
Is that possible to use this LDAP load balancer for a normal domain authentication requests?
Same like this – if I want to create a new VM which will be member of a domain, can I use this LDAP LB address (IP of load balancer) for this joining procedure on new VM?
It is not working for me.
Is DNS LB required for this? Sorry for my “stupid question”.
Windows doesn’t use LDAP when joining a domain. I think it uses RPC and Kerberos.
Hi Carl! Great page… A few things:
1.) I thought AD LDAPS didn’t like wildcards configured on the backend servers? So if we have an LDAPS configured on the server shouldn’t it be the CA certficate from the domain controller? In an AD environment WildcardLDAPS certificate won’t work.
LDAPS (Lightweight Directory Access Protocol) does not support wildcards.
Active Directory does not support wildcards.
2.) If we have deployed in an internal certificate on all our domain servers to configure LDAPS. We will need to CA Root certificate on the netscaler, correct?
3.) don’t we have to use the name and not ip? because it doesn’t have the ip in the SAN?
Domain Controllers will only choose a non-wildcard cert for the LDAPS listener.
Some LDAP Clients (e.g. NetScaler Gateway) don’t validate the certificate. Some LDAP Clients (e.g. Linux machines) do validate the certificate. If you need valid certificates, then you’ll need to provision a valid certificate. You might be right that LDAPS with certificate validation won’t accept wildcards.
Carl, If I am setting persistence, should it be by Source IP, or by SSL Session?
Probably Source IP. SSL Session tends to change when SSL is renegotiated.
I usually just use TCP instead of SSL_TCP so I don’t have to bind the certificate, or have to update the certificate in the future. Is there any benefit of using SSL_TCP though?
If NetScaler is your LDAP client, then no. But if you have Linux/UNIX machines using the LDAP LB VIP, then yes, so they can verify the certificate.
great article, thanks Carl
My questions is about step 15: “Select a certificate that matches the FQDN that will resolve to this VIP.”
In my scenario, our local domain is acme.local, there is a CA installed, I’m using single FQDN for Receiver and our external FQDN will be e.g. accesss.domain.com (with a split DNS zone internally for this purpose) for which I have a 3rd party purchased cert.
Which certificate must be used on the LDAPS VIP? Install my root and server certs for the Domain controllers on the netscaler or use the 3rd party one, but have that cert also on the DC’s for SSL_TCP? I’m a bit confused. Thanks for helping !
It’s a different FQDN. And it’s internal only. It’s the same as setting you a new load balancing VIP. It has nothing to do with Gateway other than Gateway will use it to perform LDAP queries.
Offloading LDAP SSL to NetScaler is optional. Another option is TCP protocol instead of SSL_TCP protocol.