Navigation
Overview
If you plan to use LDAP (Active Directory) for NetScaler Gateway or NetScaler management authentication, load balance the Domain Controllers that are used for authentication.
An alternative to load balancing is to configure NetScaler Gateway and NetScaler management authentication with multiple authentication policies, each pointing to a single Domain Controller. However, NetScaler will try each authentication policy until it finds one that works. If the user enters a wrong password and if you have three authentication policies pointing to different Domain Controllers in the same domain then three different failure attempts will be recorded thus causing premature account lockout. Use Load Balancing to avoid this behavior.
This page details LDAPS, aka Secure LDAP. This protocol requires certificates to be installed on the Domain Controllers. When a user’s password expires, Active Directory does not allow password changes over clear text LDAP so LDAPS must be used instead. Make sure you have certificates installed on your Domain Controllers. The easiest way to accomplish that is to deploy a Microsoft Certificate Authority. Once that’s done the Domain Controllers will request certificates automatically.
An ldaps monitor can be used to verify that the Domain Controller is functional. The ldaps monitor will login as an account, perform an LDAP query, and look for a successful response. The ldaps monitor uses a service account to login. Make sure the service account’s password does not expire. Domain User permissions are sufficient. Since this monitor is a Perl script, it uses NSIP as the source IP.
If you have Domain Controllers in multiple datacenters, you can create multiple load balancing Virtual Servers and cascade them so that the local Domain Controllers are used first, and if they’re not available, then the Virtual Server fails over to Domain Controllers in remote datacenters.
The Load Balancing Virtual Server for LDAPS can be TCP or SSL_TCP:
- If the protocol is TCP, then SSL-encrypted LDAP traffic is not terminated on the NetScaler, and is simply forwarded to the LDAP servers. If your LDAP client needs to verify the LDAP server certificate, then this Load Balancing configuration will not work, since each back-end LDAP server will have a different certificate.
- If your Load Balancing Virtual Server is protocol SSL_TCP, then a certificate must be installed on the NetScaler and bound to the Load Balancing Virtual Server. SSL is terminated at the NetScaler and re-encrypted before sending it to the destination Domain Controller. The primary benefit of NetScaler SSL termination is that your LDAP clients can verify the Virtual Server SSL certificate.
When NetScaler uses a local (same appliance) load balanced Virtual Server for LDAPS authentication, the traffic is sourced from the NetScaler SNIP (Subnet IP). When NetScaler uses a direct connection to a Domain Controller without going through a local Load Balancing Virtual Server, or if NetScaler uses a remote (different appliance) Load Balancing VIP, then the traffic is sourced from the NetScaler NSIP (NetScaler IP). Adjust firewall rules accordingly.
LDAPS Monitor
Note: Perl monitor uses NSIP as the source IP.
- In the NetScaler Configuration Utility, expand Traffic Management, expand Load Balancing, and click Monitors.
- On the right, click Add.
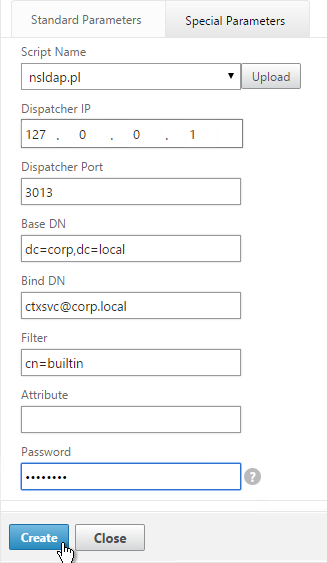
- Name the monitor ldaps-Corp or similar. The ldaps monitor logs into Active Directory, performs an LDAP query, and looks for a successful response. The monitor configuration has domain specific information, so if you have multiple Active Directory domains, then you will need multiple ldaps monitors. Include the domain name in the monitor name.
- Change the Type to LDAP.
- Scroll down and check the box next to Secure.
- Scroll back up and switch to the Special Parameters tab.
- On the Special Parameters tab, use the Script Name drop-down list to select the nsldap.pl file.
- In the Base DN field, enter your domain name in LDAP format (e.g. dc=company,dc=com)
- In the Bind DN field, enter the UPN login (e.g. ctxsvc@company.com) of a service account in the domain that can browse all objects. Any normal Domain User should be sufficient. Just make sure the password doesn’t expire.
- In the Filter field, enter cn=builtin. This limits the search results.
- In the Password field, enter the password for the service account. Make sure there is no semicolon in the password or the script will be unable to parse the parameters.
- Click Create.
add lb monitor LDAP-Corp LDAP -scriptName nsldap.pl -dispatcherIP 127.0.0.1 -dispatcherPort 3013 -password Passw0rd -secure YES -baseDN "dc=corp,dc=local" -bindDN "corp\\ctxsvc" -filter cn=builtin
- If you have multiple domains, then create additional monitors: one for each domain.
Servers
- On the left, expand Traffic Management, expand Load Balancing, and click Servers.
- On the right, click Add.
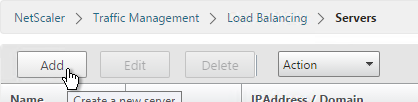
- Enter a descriptive server name, usually it matches the actual server name.
- Enter the IP address of the server.
- Enter comments to describe the server. Click Create.
add server AD01 10.2.2.11 add server AD01 10.2.2.12
- Continue adding Domain Controllers.
Service Groups
- On the left, expand Traffic Management, expand Load Balancing, and click Service Groups.
- On the right, click Add
.
- You will create one Service Group per datacenter. Enter a name reflecting the name of the data center. Also, you will create a set of service groups per Active Directory domain so include the domain name.
- Change the Protocol to SSL_TCP. Scroll down, and click Continue.
- On the left, in the Service Group Members section, click where it says No Service Group Member.
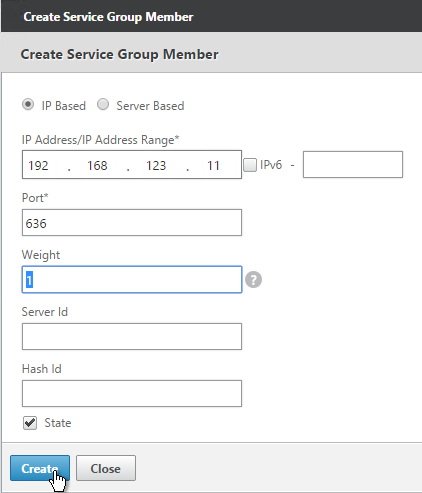
- If you did not create server objects then enter the IP address of a Domain Controller in this datacenter. If you previously created a server object then change the selection to Server Based, and select the server object. In the Port field, enter 636 (LDAPS).
- Note: Any Domain Controller you add to this list must have an SSL certificate installed. The easiest way to install SSL certificates on the Domain Controllers is with Active Directory Certificate Services since it installs the certificates automatically.
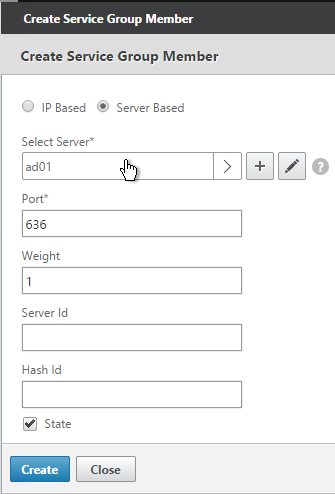
- To add more members, click where it says 1 Service Group Member, and then click Add. Click Close when done.
- On the right, in the Advanced Settings column, click Monitors.
- On the left, in the Monitors section, click where it says No Service Group to Monitor Binding.
- Click the arrow next to Click to select.
- Select your new LDAPS monitor and click Select.
- Click Bind.
- To verify the member is up, click in the Service Group Members section.

- Highlight a member, and click Monitor Details.
- It should say Probe successful. Click OK.
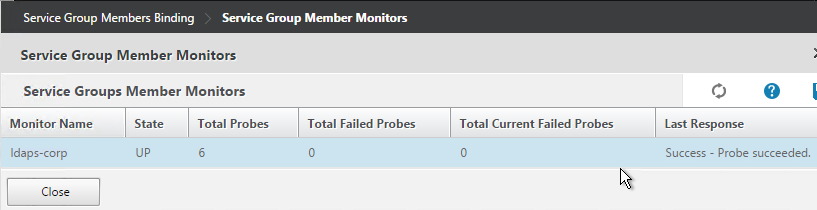
- If the monitor doesn’t work, use ldp.exe to verify the Domain Controller certificate.
- Click Done to finish creating the Service Group.
add serviceGroup svcgrp-LDAP-Corp SSL_TCP bind serviceGroup svcgrp-LDAP-Corp AD01 636 bind serviceGroup svcgrp-LDAP-Corp AD02 636 bind serviceGroup svcgrp-LDAP-Corp -monitorName LDAP-Corp
- The Service Group is displayed as UP. If not, click the refresh icon on the top right.
- Add additional service groups for Domain Controllers in each data center.
Virtual Server
- Create or import a certificate that matches the FQDN that resolves to the new Load Balancing VIP for LDAPS.
- On the left, expand Traffic Management, expand Load Balancing, and click Virtual Servers.
- On the right, click Add.
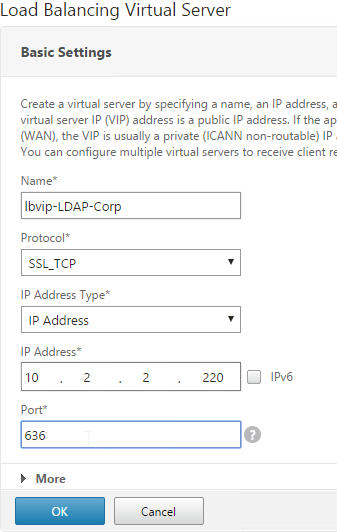
- Name it lbvip-LDAPS-Corp-HQ or similar. You will create one Virtual Server per datacenter so include the datacenter name. Also, each domain has a separate set of Virtual Servers so include the domain name.
- Change the Protocol drop-down to SSL_TCP.
- Enter a Virtual IP. This VIP cannot conflict with any other IP/Port already being used. You can use an existing VIP that is not already listening on TCP 636.
- Enter 636 as the Port. Click OK.
- On the left, in the Service Group section, click where it says No Load Balancing Virtual Server ServiceGroup Binding.
- Click the arrow next to Click to select.
- Select the previously created Service Group, and click Select.
- Click Bind.
- Click Continue.
- On the left, in the Certificates section, click where it says No Server Certificate.
- Click the arrow next to Click to select.
- Select a certificate that matches the FQDN that will resolve to this VIP. Click Select.
- Click Bind.
- Click Continue.
add lb vserver lbvip-LDAP-Corp SSL_TCP 10.2.2.210 636 -persistenceType NONE -cltTimeout 9000 bind lb vserver lbvip-LDAP-Corp svcgrp-LDAP-Corp
- If you haven’t enabled the Default SSL Profile, then perform other normal SSL configuration including: disable SSLv3, and bind a Modern Cipher Group.
bind ssl vserver MyvServer -certkeyName MyCert set ssl vserver MyvServer -ssl3 DISABLED -tls11 ENABLED -tls12 ENABLED unbind ssl vserver MyvServer -cipherName ALL bind ssl vserver MyvServer -cipherName Modern bind ssl vserver MyvServer -eccCurveName ALL
- Click Done to finish creating the Virtual Server.
- The new Virtual Server should show as Up.
- Create additional Virtual Servers for each datacenter. These additional Virtual Servers do not need a VIP so change the IP Address Type to Non Addressable. Only the first Virtual Server will be accessible.
add lb vserver lbvip-LDAP-Corp-Backup SSL_TCP 0.0.0.0 0
- Notice that the additional datacenter Virtual Servers show up with an IP Address of 0.0.0.0 and port of 0.
- After you are done creating a Virtual Server for each datacenter, right-click the primary datacenter’s Virtual Server, and click Edit.
- On the right, in the Advanced Settings column, click Protection.
- On the left, in the Protection section, change the Backup Virtual Server to one of the other datacenter Virtual Servers. If all of the services in this datacenter are DOWN, the backup Virtual Server will be used instead. You can cascade multiple Virtual Servers using this method. Click OK and Done.
set lb vserver lbvip-LDAP-Corp -backupVServer lbvip-LDAP-Corp-Backup
Clear Text LDAP
Citrix Command Center does not support Secure LDAP so you will need to do the following:
- Create a regular LDAP monitor that does not have the secure box checked.
- Create Service Groups of Protocol TCP and Port 389.
- Create a Load Balancing Virtual Server of Protocol TCP on port 389. Bind the Service Groups to it.
Next Steps
You may now use this Virtual IP in your LDAP authentication policies for NetScaler Gateway or NetScaler management login.
Hi Carl,
Quick question, can you configure have a NS Gateway VIP, that comes through a Tunnel, I.E Single Source IP, without Persistency, do you see any issues with have a Gateway configured without Persistency, so that the LB method is honoured , or would that break Authentication requests or launch requests, that you are aware of ?
Thanks,
Persistency from what to what? From clients to a single Gateway? Or from Gateway to multiple load balanced backend servers (e.g. LDAP)? LDAP load balancing doesn’t normally need persistence.
Hi Carl,
In response to your question, it would be Persistency from a Client to a GSLB Gateway Active/Active across Sites.
The Client being Users coming through a VPN Tunnel, the Tunnel creating a Single Source IP, as opposed to multiple IPs from Internet Users.
The Netscaler’s are in a Double Hop scenario DMZ/Internal, but that persistency is different, and probably not related.
I was looking at turning off Persistency because I feel that the client connections all coming from the VPN tunnel , seen as a single IP would cause persistency to override the LB method, so if 1000 users logon from that site in the morning for example, persistency would cause a huge imbalance across sites GSLB sites/Netscaler.
Now I know Cookie Persistency method is another option, but this would rely on all the clients being able to accept cookies and have browsers to support this correctly, which we cant govern in this case.
So we were thinking if we Set Persistency to none, the primary and only method would be Least Connection.
The Concern here is what can break if we do this, is persistency required to do the whole Authentication to Launch process, Or would there be a scenario where it breaks, as packets are distributed across sites/gslb Servers.
Thanks,
Many web servers store session information on a single server, not all servers. StoreFront is an example of this and requires persistency.
Once the Citrix session is launched, it’s a long-lived TCP connection, which means there’s no need for persistency. It’s only the short-lived HTTP connections that need persistency.
Is there a standard or best practice for the monitoring probe service account
I’m running on 11.1_51.12, and I have a weird issue; The Gateway appears to work without issues with the load balanced secure LDAP vserver, but when attempting to connect using LDP.exe, I keep getting
ld = ldap_sslinit(“ldap.domain.com”, 636, 1);
Error 81 = ldap_set_option(hLdap, LDAP_OPT_PROTOCOL_VERSION, 3);
Error 81 = ldap_connect(hLdap, NULL);
Server error:
Error : Fail to connect to ldap.domain.com.
I fail to see where this is going wrong. I tried to disable TLS1.1 and 1.2 on the backend service, but this only resulted in bringing down the ldap authentication all together?
Any Idea where I should look? I need to offer secure LDAP to a software tooling that needs to enumerate all objects in the AD for merge in a CMDB
You created the LB vServer on port 636 using SSL_TCP protocol with a valid certificate that matches ldap.domain.com?
Correct. The certificate is based on a private CA, has several subject alt names, amongst which LDAP.domain.com, LDAPS.domain.com and the IPv4 address of both the DMZ and LAN VIP.
The CA is added to the trusted rootca store of the server performing the ldp.exe test.
I can access all four Domaincontrollers directly using ldaps. The monitors tell me the test is successful. Using the Standard 389 port, the loadbalancer works fine, so i have to assume the problem is indeed in the ssl part on the Netscaler.
Please check the key length in the certificate used. I had same issue having 4k key. Usage of 2k key fixed the issue.
HI Carl,
I have done the required load balancing configuration for LDAPS 636, bound the server certificate the VIP, monitoring is also working. VIP is UP. Now When I am trying to connect on VIP port 636 by using ldp.exe its giving me error
ld = ldap_open(“10.0.0.10”, 636);
Error : Fail to connect to 10.0.0.10
I am not in respective domain from where I am testing it. Can you tell me where would be the issue?
Thanks in advance.
Did you use the FQDN so it matches the certificate?
Yes. I have used FQDN however its giving below output.
ld = ldap_open(“community.example.com”, 636);
Established connection to community.example.com.
Retrieving base DSA information…
Server error:
Error: ldap_parse_result failed: No result present in message
Getting 0 entries:
Hi Carl
I have resolved it by disabling TLS1.2 on services.
Thanks
Hi Carl, we are replacing the existing DC certificates and domain CA certificates with new one’s. Can u help me out with Plan of Action to import the new certificates in storefront and netscalar to avoid complication and issues.
What are the precautions need to be before replacing the certificate.
Thanks
M Murali Krishna
Are you revoking the old certs? If not, then the old certs will continue to work until you replace them.
I always use public certs for anything client-facing so I don’t have to worry about CRLs or trusted Roots. Otherwise, make sure your clients trust the root and have access to the CRL location.
StoreFront = IIS, so just change the binding like normal.
NetScaler, you can change the files the existing certKey is using, or add a new certKey and swap out the bindings.
Hey, Carl! I noticed some odd behavior and wanted to get your take on it.
I have a DMZ-facing, one-armed instance, and an internal-facing, one-armed instance. The internal instance has an LB vsrv front-ending four ADDC’s per the steps you’ve presented here – servers, monitors, TCP 636 service group bindings, etc.
One thing I noticed in Wireshark was that once I got this set up and working is that the NetScaler uses both its NSIP and a SNIP to talk to the LDAPS environment seemingly at the same time. Two SYN’s, two SYN ACK’s, two ACK’s, two Client Hellos, etc., down the whole probe, right up to the point of it terminating and trying again 5 seconds later.
I only noticed this because when I tried a similar set up on my DMZ-facing node, the service group wouldn’t come online. Same build (different ADDC’s), but it wouldn’t start. So I fired up Wireshark and noticed that A.) it was trying to probe using both NSIP and SNIP at the same time, and B.) that it was all SYN’s, no responses.
Firewall, perhaps, but in an attempt to “fix” it coming out two interfaces, I set up a quick PBR that defined the management default gateway for any traffic sourced from the NSIP to DST port TCP 636. This got the service group online, but now the Wireshark trace is full of Retransmit and Out-of-Sequence messages – I guess because now whatever it’s doing it’s doing twice out off the same interface?
Any insights here? I fixed the service but created a mess in the wire trace by “fixing” it using two interfaces, so I’m wondering if maybe that’s by design. D:
Thanks as always!
Hi Josh, I have the very same issue. I beleive this a bug, I reported it to Citrix va the CTA channel.
does the netscaler detect multiple connections, just wondering since we are exposing AD, if there are any checks to see if anyone is trying to hit the server in a hack attempt..
You can add rate limiting. And for AAA policies you can set Maxim Login Attempts.
Joe, I hope you’re not making your LDAP/S server publicly available, that’s just asking for trouble… Assuming only the NetScaler needs to talk to the LDAP/S VIP, you can always use a local random address (1.1.1.2) that will never get routed to the NetScaler to make the LDAP VIP non-addressable with the relevant local ADNS records.
If your talking about websites/NetScaler Gateway using the LDAP as a form of authentication, set up a form of 2 factor and use that as the first authentication method instead of LDAP, that way it will just lock out the 2 factor account and not the AD account (and yes, you can even set the browser based NetScaler gateway to do the 2nd factor first though it requires some rewrite rules or modifications of the jscript files).
Great post Carl!
It also works with openLDAP! I use an open LDAP Master – Master configuration. The only difference is in the config Monitior in the Bind DN, you have to enter the Principal: cn = users, ou = people, o = Company (and not user@people.company)
But I have another problem. I’m using an own PKI. The configuration works via SSL 636 and 389. The LDAP server using a certificate server01.example.com. For the Virtual Server I have a certificate ldap.example.com. The connection between VS and ldap server (front to back) is SSL_TCP 636. The VIP configured on SSL_TCP 636 and ldap.example.com certificate is bound. Still, I get on the VIP the certificate from Server01.example.com! After the DNS ldap.example.com points to the VIP, but I get the certificate server01.example.com, deny multiple applications to access LDAP.
Where do I set a NetScaler that he should use only the bound Certificate on VIP. SSL redirekt I have already tried, there is no difference.
The default config on a NetScaler is USNIP. Is that still enabled?
Do a WireShark on the LDAP client to see what’s happening.
Hi Carl, your guides are awesome. Just one question regarding the certificate for vip…. what type of certificate should it be? Webserver or Domain Controller ?
A regular Webserver cert will work on the vServer.
On DCs, you install DC certs.
Great post Carl! I have an interesting issue after following this guide. The monitor, and even LDP.exe queries to the DCs on port 636 fail. however, after configuring the vip, and using a standard ping monitor, my LDP queries to the vip are successful?
You have certificates on your domain controllers? If TCP protocol, certificate is handled by the domain controller. If SSL_TCP, certificate is handled by NetScaler. LDP.exe requires the the certificate to match the entered FQDN.
Correct, there are certs are on the DCs. SSL_TCP on both the service group and VIP. Cert bound to VIP. I can authenticate through the VIP… I just cant get the monitor to work. I’m on the latest version, NS11.0 64.34, and it appears they have ldaps functionality in the nsldap.pl script now.
See http://support.citrix.com/article/CTX205578. You might need to disable TLS 1.2 on the monitors.
Carl, trying to step through the monitor setup above and in my netscaler (11.0 62.10.nc) the secure option is unselectable. Any ideas?
Same problem in build 64? Did you select the nsldap.pl file as the script and not some other file?
Yes sir, correct script. Not sure about the FW update to 64, will have to work on it after a week off next week. Thanks for your feedback.
I just checked my 11.0 build 64 and the Secure option is definitely selectable.