This article applies to Citrix Gateway 13.0, Citrix Gateway 12.1, and NetScaler Gateway 12.0. Citrix ADC is the new name for NetScaler. Citrix Gateway is the new name for NetScaler Gateway.
Navigation
- Change Log
- RADIUS Overview
- Two-factor Policies Summary
- RADIUS Server/Action
- Advanced (nFactor) Two-factor Policies – for RADIUS and LDAP
- Classic Two-factor Policies – for RADIUS and LDAP
Change Log
- 2021 Mar 29 – added Advanced (nFactor) Two-factor Policies
- 2019 Jun 17 – Create RADIUS Server – change password encoding to mschapv2
RADIUS Overview
One method of two-factor authentication to Citrix Gateway is the RADIUS protocol with a two-factor authentication product (tokens) that has RADIUS enabled.
- Another common two-factor authentication method is SAML to an Identity Provider, like Azure Active Directory or Okta. SAML is detailed in the Federated Authentication Service article.
RADIUS Clients and Source IP – On your RADIUS servers, you’ll need to add the ADC appliances as RADIUS Clients. When ADC uses a local (same appliance) load balanced Virtual Server for RADIUS authentication, the traffic is sourced from the ADC SNIP (Subnet IP). When ADC uses a direct connection to a RADIUS Server without going through a load balancing Virtual Server, or uses a remote (different appliance) Load Balancing Virtual Server, the traffic is sourced from the ADC NSIP (ADC Management IP). Use the correct IP(s) when adding the ADC appliances as RADIUS Clients. And adjust firewall rules accordingly.
- For High Availability pairs, if you locally load balance RADIUS, then you only need to add the SNIP as a RADIUS Client, since the SNIP floats between the two appliances. However, if you are not locally load balancing RADIUS, then you’ll need to add the NSIP of both appliances as RADIUS Clients. Use the same RADIUS Secret for both appliances.
Links:
- For two-factor authentication using Azure Multi-factor Authentication, see Jason Samuel How to deploy Microsoft Azure MFA & AD Connect with Citrix NetScaler Gateway
- Citrix CTX125364 How to Configure Dual Authentication on NetScaler Gateway Enterprise Edition for Use with iPhone and iPad.
Some two-factor products (e.g. SMS Passcode) require you to hide the 2nd password field. Receiver 4.4 and newer supports hiding the 2nd field if you configure a Meta tag in index.html.
Two-factor Policies Summary
ADC has two methods of configuring multi-factor authentication:
- Citrix Gateway Virtual Server has bind points for Primary and Secondary authentication. This functionality is available in all ADC Editions and is detailed in this post.
- This is the older method of configuring authentication also known as Classic authentication policies. One challenge with Classic policies is that Citrix Workspace app requires the LDAP and RADIUS fields to be swapped.
- nFactor Authentication supports unlimited factors, but requires ADC Advanced Edition (formerly known as Enterprise Edition) or ADC Platinum Edition.
- nFactor is the newer authentication configuration method also known as Advanced authentication policies. With nFactor, there’s no need to swap the LDAP and RADIUS fields for Citrix Workspace app.
Workspace app authentication with a Classic Policy configuration looks like a Window that is very difficult to customize.
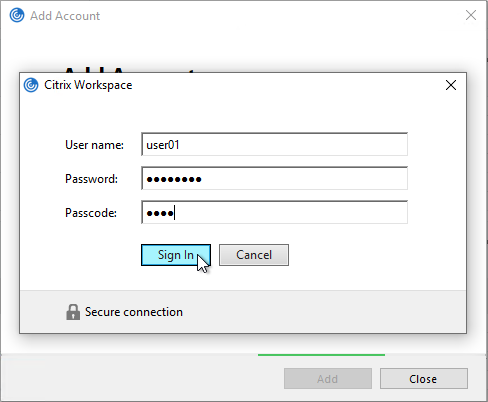
Workspace app authentication with an nFactor configuration looks like a webpage that is fully customizable.
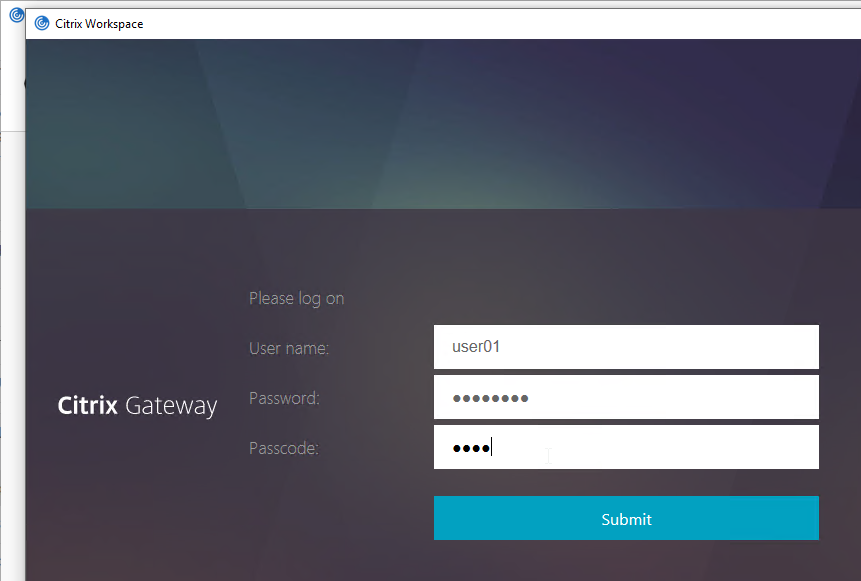
See the ADC menu page for additional authentication mechanisms supported by Citrix Gateway. Some require nFactor.
When configuring the Citrix Gateway Virtual Server, you can specify both a Primary authentication policy, and a Secondary authentication policy. Users are required to successfully authenticate against both policies before being authorized for Citrix Gateway.
For browser-based StoreFront, you need two authentication policies:
- Primary = LDAPS authentication policy pointing to Active Directory Domain Controllers.
- Secondary = RADIUS authentication policy pointing to RSA servers with RADIUS enabled.
For Citrix Workspace app, the classic authentication policies need to be swapped. There’s no need to swap them if doing nFactor (Advanced) policies.
- Primary = RADIUS authentication policy pointing to RSA servers with RADIUS enabled.
- Secondary = LDAPS authentication policy pointing to Active Directory Domain Controllers.
With Classic Authentication Policies, if you need to support two-factor authentication from both web browsers and Citrix Workspace app, then you’ll need at least four authentication policies as shown below.
Primary:
- Priority 90 = RADIUS policy. Expression = REQ.HTTP..HEADER User-Agent CONTAINS CitrixReceiver
- Priority 100 = LDAP policy. Expression = REQ.HTTP..HEADER User-Agent NOTCONTAINS CitrixReceiver
Secondary:
- Priority 90 = LDAP policy. Expression = REQ.HTTP..HEADER User-Agent CONTAINS CitrixReceiver
- Priority 100 = RADIUS policy. Expression = REQ.HTTP..HEADER User-Agent NOTCONTAINS CitrixReceiver
LDAP Server/Action
See the LDAP post for instructions to create an LDAP Server/Action. Only the LDAP server/action is needed. The Policies will be created later.
RADIUS Server/Action
Create a RADIUS Server/Action:
- On the left, expand Authentication, and click Dashboard.
- On the right, click Add.
- Change Choose Server Type to RADIUS.
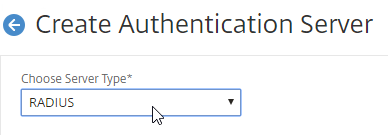
- Give the server a name.
- Specify the IP address of the RADIUS load balancing Virtual Server.
- Enter the secret key specified when you added the ADCs as RADIUS clients on the RADIUS server. Click Test RADIUS Reachability.
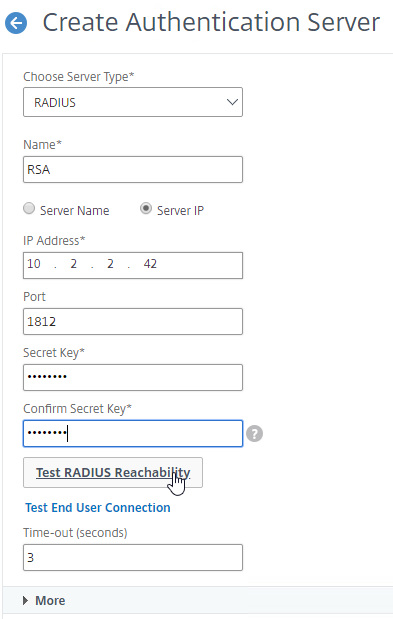
- Scroll down, and click More.
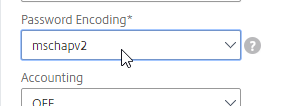
- Find the Password Encoding drop-down. Change it to mschapv2 if your RADIUS server supports it, c. Microsoft NPS requires mschapv2 to support changing expired Active Directory passwords. 💡
- If you want ADC to receive AAA Group information from RADIUS, see CTX222260 Radius Group Extraction from Windows Server 2008/2012 with NetScaler/CloudBridge.
- RADIUS attribute = 26 (Vendor-Specific)
- Vendor Code = 3845 (Citrix)
- Vendor-assigned attribute number = any number (e.g. 1). Configure RADIUS policy on ADC with same attribute number.
- Attribute value = Group Name
- Click Create.
add authentication radiusAction RSA -serverIP 10.2.2.210 -serverPort 1812 -authTimeout 60 -radKey Passw0rd -passEncoding mschapv2
Advanced Authentication (nFactor) Policies for LDAP and RADIUS
For the older Classic Authentication policies, jump ahead to the Classic Policies section.
Create Advanced Authentication Policies:
- In the left menu, go to Security > AAA – Application Traffic > Policies > Authentication > Advanced Policies > Policy.
- On the right, click Add.
- In the Create Authentication Policy window:
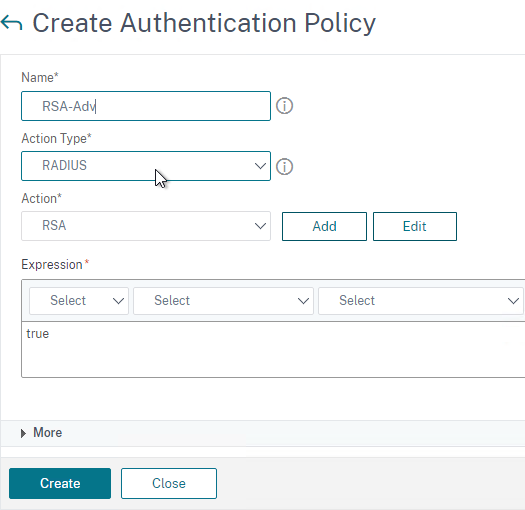
- Change the Action Type to RADIUS.
- Select your RADIUS Action.
- Give the policy a name.
- Expression = true.
- Click Create.
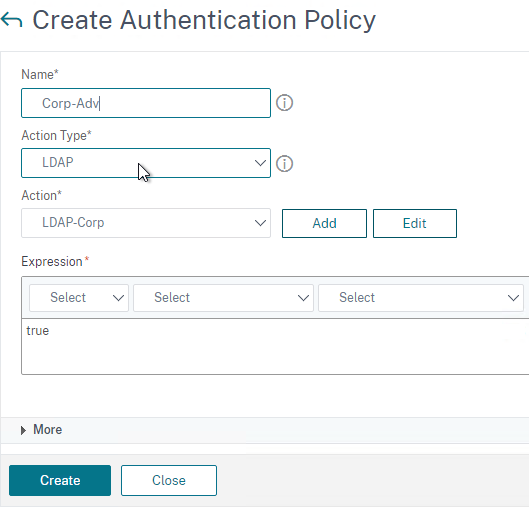
- Create another Authentication Policy.
- Set Action Type to LDAP.
- Select your LDAP Action/Server.
- Give the policy a name.
- Expression = true.
- Click Create.
Create a Policy Label for the second factor, which is typically the RADIUS policy. The first factor (LDAP) does not need a Policy Label.
- In the left menu, click Policy Label.
- On the right, click Add.
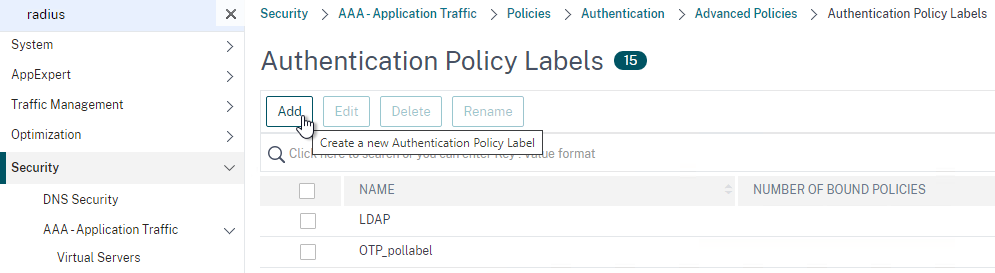
- Give the Policy Label a name.
- Leave Login Schema set to LSCHEMA_INT. The Login Schema in the first factor will collect both password and passcode in one form so there’s no need for the second factor to collect it again.
- Click Continue.
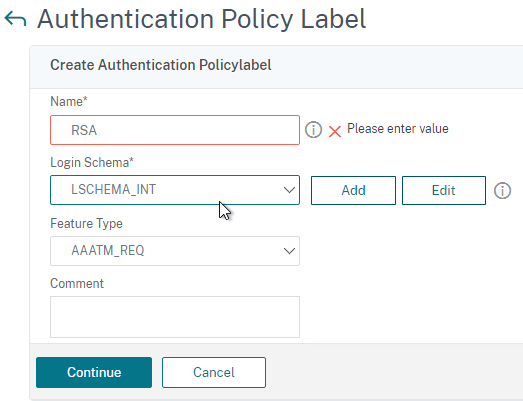
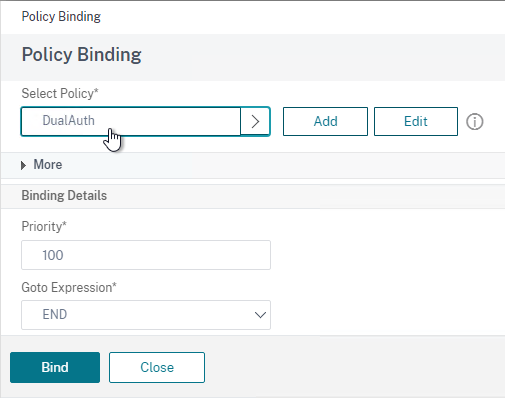
- In the Select Policy field, select your RADIUS policy.
- Click Bind at the bottom of the page.
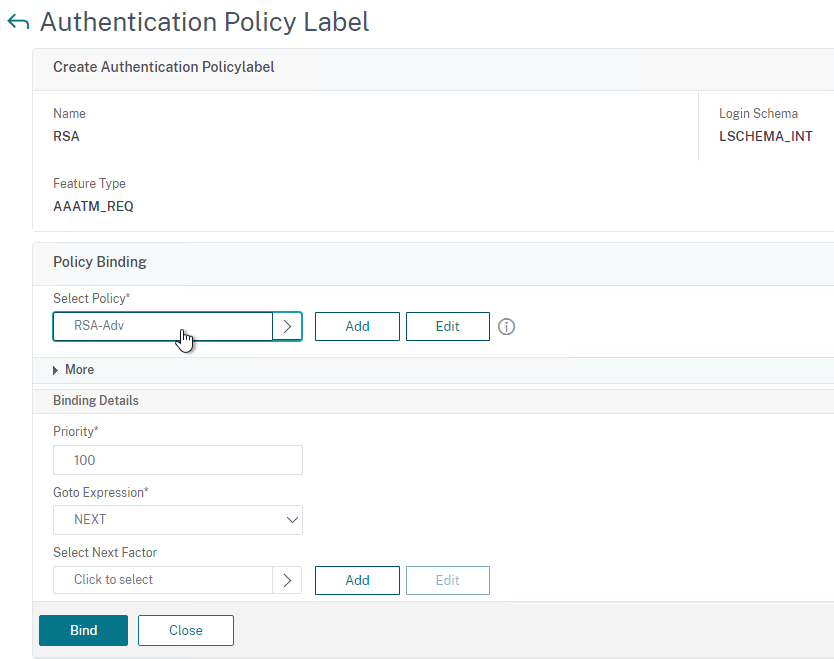
- Click Done to finish creating the Policy Label.

Create a Login Schema to collect the password and passcode on the same form.
- In the left menu, click Login Schema.
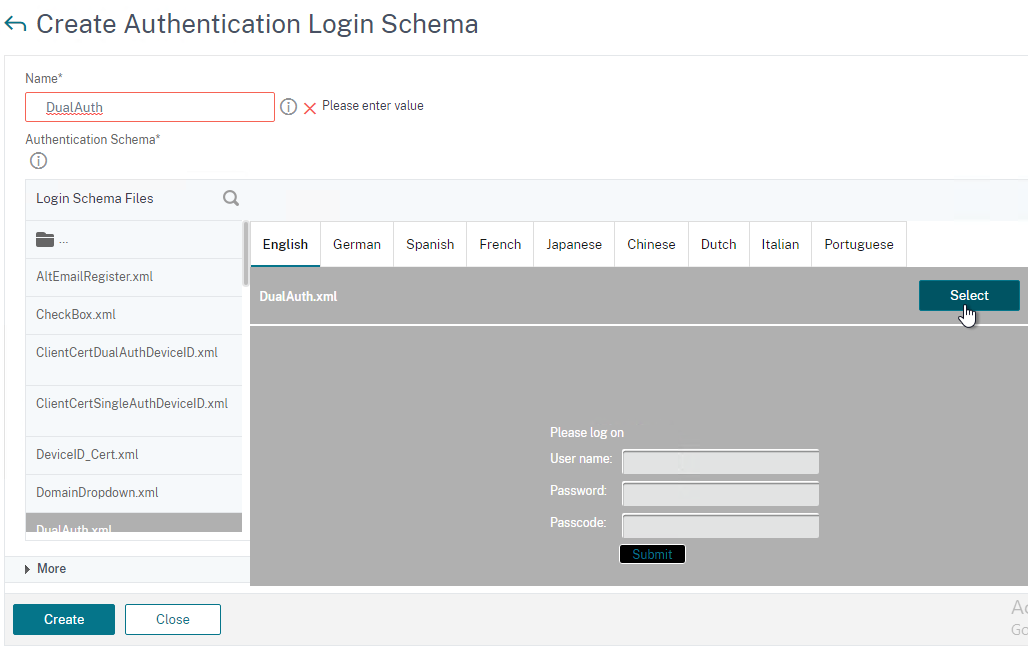
- On the right, switch to the tab named Profiles and then click Add.
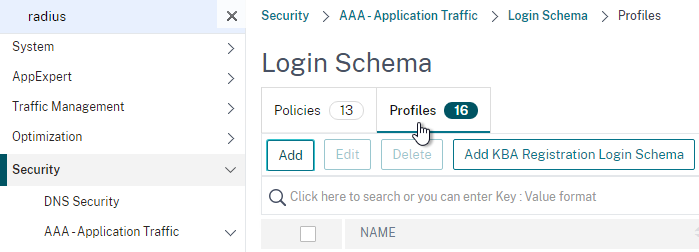
- Give the Login Schema a name (e.g. DualAuth).
- Click the pencil icon and then open the LoginSchema folder.
- Click the DualAuth.xml file on the left. On the right, make sure you click the blue Select button. It’s too easy to miss this step.
- See my nFactor article for some info on how to customize the Login Schema.
- Then click Create.
- On the right, switch to the tab named Policies.
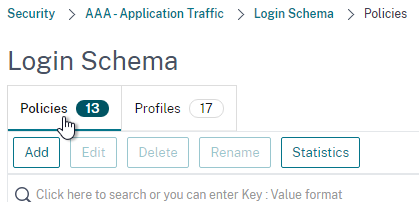
- Give the Login Schema Policy a name.
- Select the Login Schema Profile you just created.
- Set the Rule field to true.
- Click Create.
Create an Authentication (AAA) Virtual Server to link the factors together.
- In the left menu, under AAA – Application Traffic, click Virtual Servers.
- On the right, click Add.
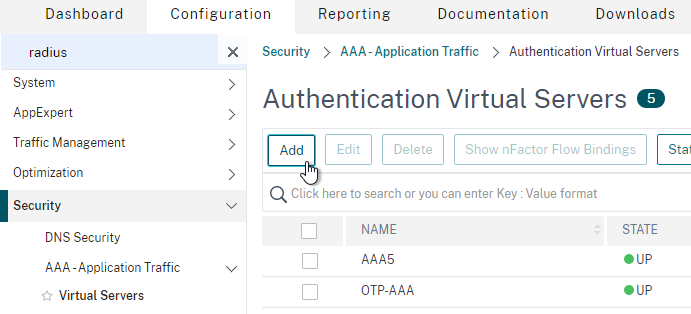
- Change the IP Address Type to Non Addressable.
- Give the AAA vServer a name and then click OK.
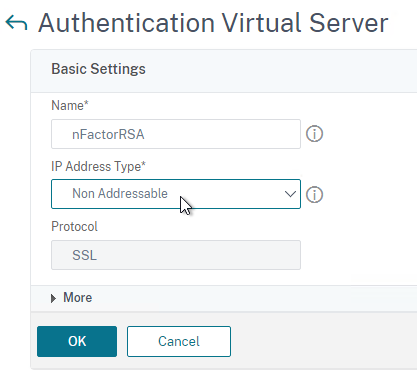
- In the Certificate section, you can optionally bind a certificate. It doesn’t matter what certificate you choose (typically the Gateway cert). The only thing this certificate binding does is make the AAA vServer show as UP instead of DOWN. Otherwise it has no effect on functionality. Click Continue.
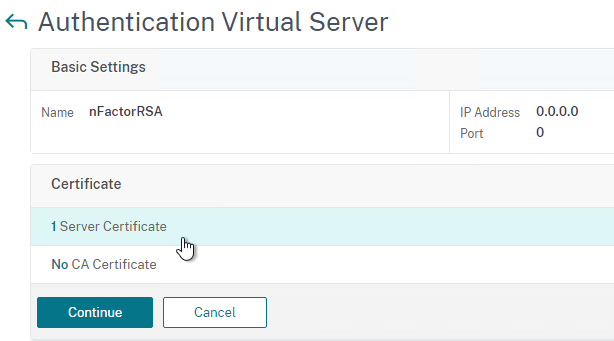
- In the Advanced Authentication Policies section, click where it says No Authentication Policy.
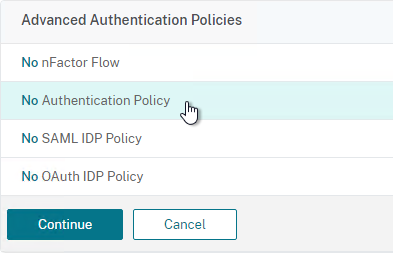
- In the Select Policy field at the top of the window, select the LDAP policy.
- Near the bottom, in the Select Next Factor field, click where it says Click to select.
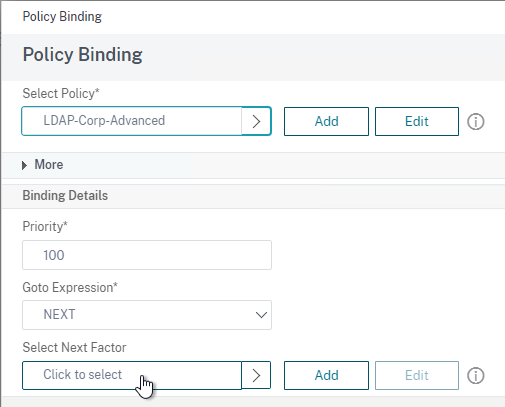
- Select your RADIUS Policy Label and then click Bind. After LDAP is done, nFactor will then move to your RADIUS Policy Label.
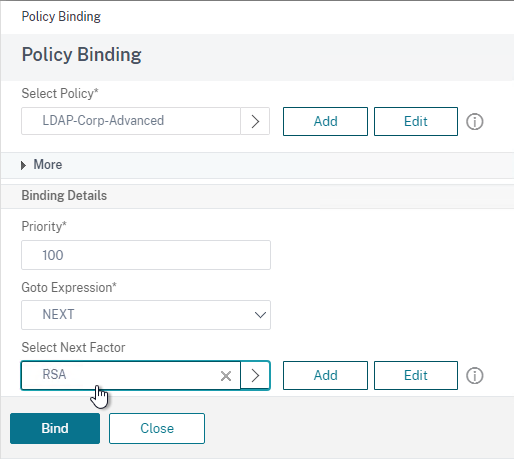
- Click Continue.
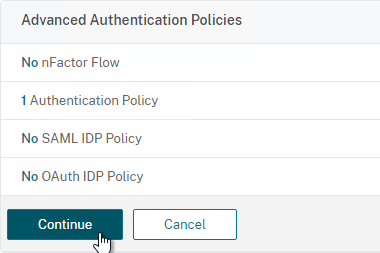
- On the right, in the Advanced Settings column, click Login Schemas.
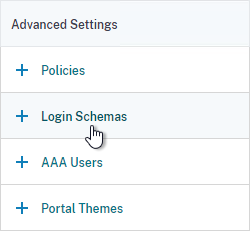
- On the bottom left, click where it says No Login Schema.
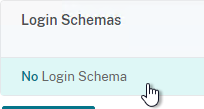
- Select the DualAuth Login Schema you created earlier and then click Bind.
- Click Done at the bottom of the page.
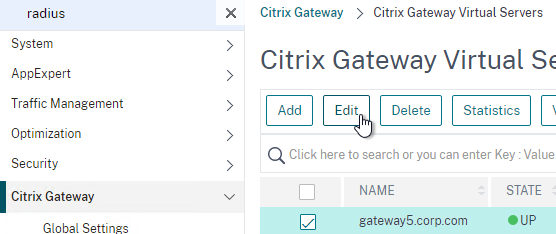
Link the AAA vServer to your Gateway vServer:
- In the left menu, expand Citrix Gateway and then click Virtual Servers.
- On the right, edit your Gateway vServer.
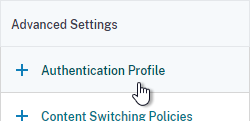
- On the right, in the Advanced Settings column, click Authentication Profile.
- On the bottom left, in the Authentication Profile section, click the Add button.
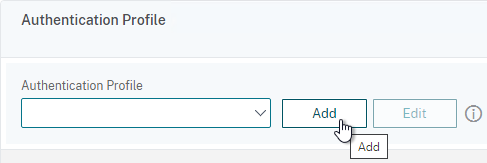
- Select the AAA vServer you created earlier.
- Give the Profile a name and then click Create.
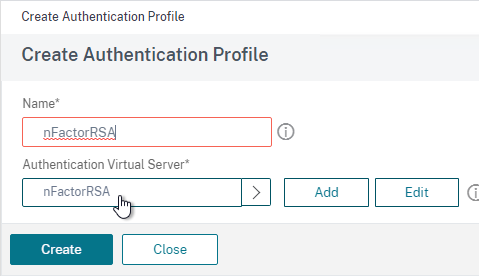
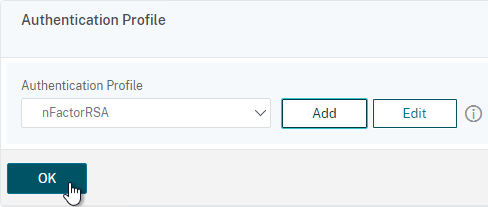
- Back in the Gateway vServer, make sure you click OK in the Authentication Profile section. If you forget to click OK then the Authentication Profile won’t be bound.
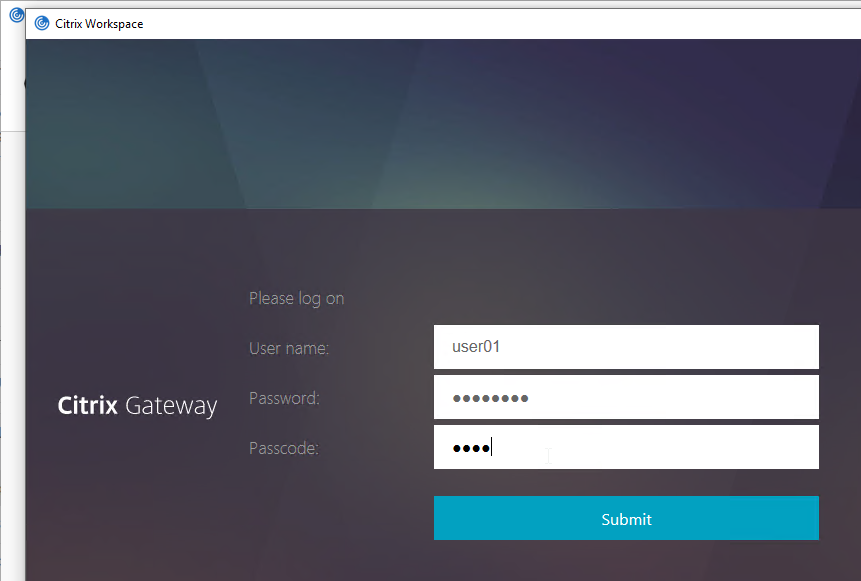
If you point your Workspace app to the Gateway that has nFactor configured, the authentication window will look like a web page.
Classic Authentication Policies for LDAP and RADIUS
For Advanced Authentication (nFactor) policies, jump back to the Advanced Policies section.
- Go to Citrix Gateway > Policies > Authentication > RADIUS.
- On the right, in the Policies tab, click Add.
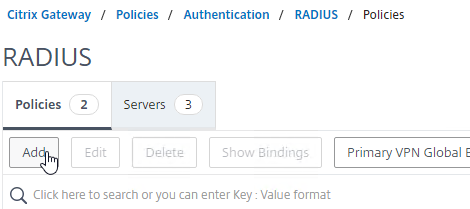
- In the Create Authentication RADIUS Policy page:
- Name the policy RSA-ReceiverSelfService or similar.
- Select the RADIUS server created earlier.
- Enter an expression. You will need two policies with different expressions. The expression for Receiver Self-Service is REQ.HTTP.HEADER User-Agent CONTAINS CitrixReceiver.
Note: Citrix Gateway 12.1 does not natively support binding of Advanced Authentication Policies so you’ll have to create them as Basic Policies (classic expressions). You can only bind Advanced Authentication Policies using nFactor.
- Click Create.
- If you see a warning about deprecation, click OK, and ignore it.
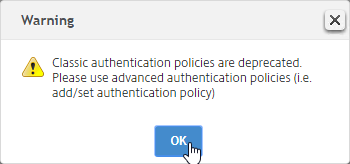
- Create another RADIUS policy to match the ones shown below. Both RADIUS policies are configured with the same RADIUS server. The only difference between them is the expression (CONTAINS vs NOTCONTAINS):
Name Expression Server RSA-ReceiverSelfService REQ.HTTP.HEADER User-Agent CONTAINS CitrixReceiver RSA RSA-ReceiverForWeb REQ.HTTP.HEADER User-Agent NOTCONTAINS CitrixReceiver RSA 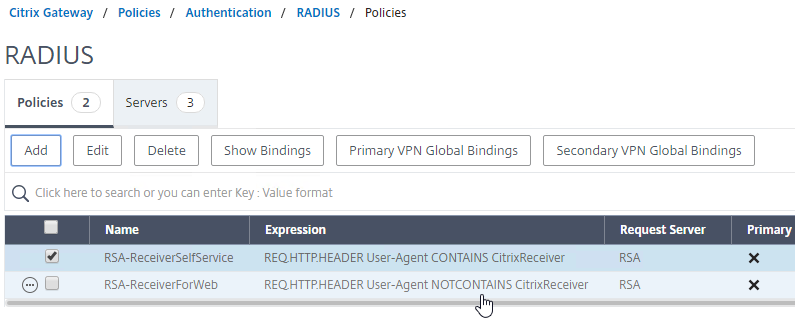
- Go to the Citrix Gateway\Policies\Authentication\LDAP node.
- On the Policies tab, create two policies with the expressions shown below. Both LDAP policies are configured with the same LDAP server. The only difference between them is the expression (CONTAINS vs NOTCONTAINS).
Name Expression Server LDAP-Corp-ReceiverSelfService REQ.HTTP.HEADER User-Agent CONTAINS CitrixReceiver LDAP-Corp LDAP-Corp-ReceiverForWeb REQ.HTTP.HEADER User-Agent NOTCONTAINS CitrixReceiver LDAP-Corp 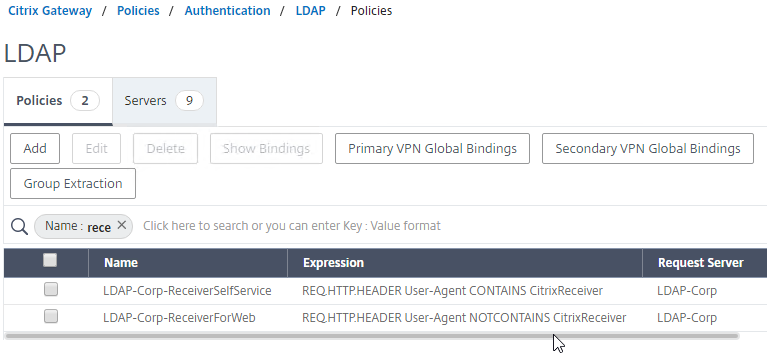
add authentication radiusPolicy RSA-ReceiverForWeb "REQ.HTTP.HEADER User-Agent NOTCONTAINS CitrixReceiver" RSA add authentication radiusPolicy RSA-ReceiverSelfService "REQ.HTTP.HEADER User-Agent CONTAINS CitrixReceiver" RSA add authentication ldapPolicy Corp-Gateway-ReceiverForWeb "REQ.HTTP.HEADER User-Agent NOTCONTAINS CitrixReceiver" Corp-Gateway add authentication ldapPolicy Corp-Gateway-ReceiverSelfService "REQ.HTTP.HEADER User-Agent CONTAINS CitrixReceiver" Corp-Gateway
Bind Two-factor Policies to Gateway
- When you create or edit a Citrix Gateway Virtual Server, bind the Basic Authentication Policies as shown in the following table. Priority doesn’t matter because they are mutually exclusive.
Policy Name Type Bind Point LDAP-Corp-ReceiverForWeb LDAP Primary RSA-ReceiverSelfService RADIUS Primary LDAP-Corp-ReceiverSelfService LDAP Secondary RSA-ReceiverForWeb RADIUS Secondary 

bind vpn vserver gateway.corp.com -policy Corp-Gateway-ReceiverForWeb -priority 100 bind vpn vserver gateway.corp.com -policy RSA-ReceiverSelfService -priority 110 bind vpn vserver gateway.corp.com -policy RSA-ReceiverForWeb -priority 100 -secondary bind vpn vserver gateway.corp.com -policy Corp-Gateway-ReceiverSelfService -priority 110 -secondary
- The Session Policy/Profile for Receiver Self-Service needs to be adjusted to indicate which authentication field contains the Active Directory password. On the Client Experience tab is Credential Index. This needs to be changed to SECONDARY. Leave the session policy for Web Browsers set to Primary.
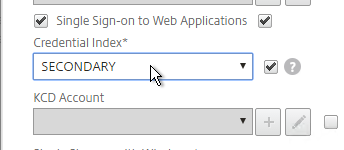
set vpn sessionAction "Receiver Self-Service" -ssoCredential SECONDARY
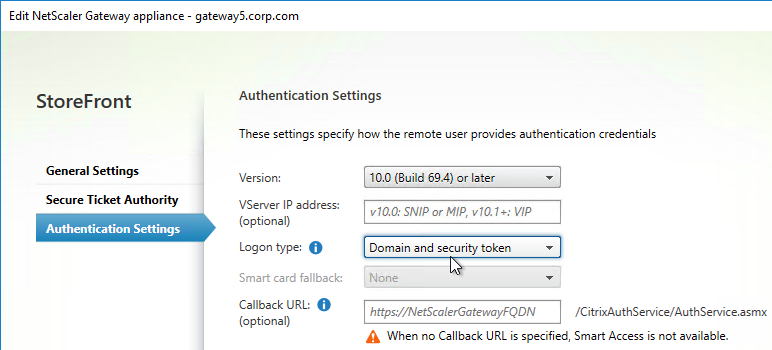
- On the StoreFront server, when creating the Citrix Gateway object, on the Authentication Settings page, change the Logon type to Domain and security token. This instructs Receiver / Workspace app to properly handle two-factor authentication. If you change this setting after Receiver / Workspace app has already performed discovery, then users might have to remove the Account from Receiver / Workspace app and re-add it.
Hi Carl,
Is there have any idea to allow only specific security group of the user to have 2FA only, other users not the security group will be login by providing Username and Password only.
nFactor authentication can do it. First factor gets groups from LDAP. Second factor depends on group membership.
Thanks Carl for the idea, I believe following link is what you means. “https://support.citrix.com/article/CTX220793”. Possible some configuration guide?
Hi, I would like to start using the Microsoft Authenticator app for MFA on the NetScaler Gateway Virtual Server. Do I still need an NPS server for this? I read somewhere that support for this will expire and it will not be developed further?
Can it now also be done in a different, simpler way? What are the options? SAML with Azure AD, Azure MFA Cloud Service in ADC? Do I also need a FAS server?
Thank you very much for the response!
Either RADIUS to NPS, or SAML to Azure AD. SAML is more user friendly.
If you do SAML then you need FAS to eliminate the second login at the VDA machine.
Thank you Carl. Radius to NPS is therefore still a way that can be applied. Also on a new setup?
Yes, RADIUS to NPS with Azure AD MFA is still an option. https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-mfa-nps-extension
Hi,
I am implementing a 2F authentication on a Citrix Gateway/Netscaler version 13.1..
First factor LDAP
Second factor Raidus server.
When authenticating on the client wab interface, I have NPS Event 6273 Reason Code 16, “Authentication failed due to a user credentials mismatch.
Any idea ?
Regards,
Is ADC sending the user’s Active Directory password to NPS?
The ADC should not send the Active Directory password the NPS.
I have installed Authlite in the NPS for the OTP.
The ADC should send the OTP to the NPS.
Hello Carl,
How I can configure with nfactor dualauth schema to send user’s password to NPS? I think for dualauth schema somehow the password and passcode are combined.
Thank you for your assistance in advance!
Hello – I have been tasked with finding a reliable MFA solution. Duo looks like a good option, do you have any recommendations? Using on prem LDAP.
Duo is very popular RADIUS option. Use their nFactor configuration instructions.
Thanks, Duo looks good to me. Mgmt showing interest in Azure and Google. I can’t find solid documentation, but it looks like with Azure you need an Azure AD? And I don’t see much about integrating Google MFA into Netscaler.
The two common authentication methods are RADIUS and SAML. Many Identity Providers have both options. SAML is more user friendly than RADIUS but SAML requires additional infrastructure (e.g. Citrix FAS) to facilitate Single Sign-on to the VDAs. RADIUS doesn’t have that requirement.
Azure AD is a Identity Provicer.
Google Authenticator is not an Identity Provider. Many Identity Providers support using Google Authenticator to perform authentication to the Identity Provider.
Thank you for your help.
Last question! Forgot about Netscaler Native OTP. Any experience with that? Looks like it will do what we want. Setup seems complex, and end user registration involves more steps then I would like to see. Might work though…
You get what you pay for. 🙂
I hear you! Made that mistake one too many times.
I need to add multiple domains drop down on Citrix ADC logon page. We are using RADIUS MFA as 2FA. I configured StoreFront server with multiple domains. But not been able to do over Citrix ADC configurations.
I recommend doing it in nFactor so it also works with Workspace app – https://support.citrix.com/article/CTX201760
Does nFactor works with Radius 2FA?
Of course.
Thanks for providing the Citrix article CTX201760.
I began to work on the steps provided in this article, but at step 7, it says to ‘Add Policy’. I have a policy under;
Security> AAA – Application Traffic> Policies> Authentication> Basic Policies> LDAP.
But when I tried to pull this policy to apply under nFactor Flows, its not loading the LDAP policy to apply.
Do I need to create another authentication policy for LDAP? If yes, what should be the ‘Expression’ under Expression Editor?
Thanks
The expression should be something like this but put in your actual domain name that’s in your drop-down.
HTTP.REQ.BODY(500).AFTER_STR(“domain=”).CONTAINS(“AAATM.COM”)
All the configurations are set as defined in the Citrix article. But the Citrix Gateway page is still not showing the drop-down menu.
I just saved the ADC configurations and bounced it too.
Hello Carl
I have a question regarding the CEM (Citrix EndPoint Management) and this method of authentication. I want to deploy radius+ldap, so i assume that i would need the same policies but for the secure hub client. could you assist on what that would look like regarding the expressions.
Hi Carl,
Thanks for the great article and explanation.
We recently upgraded to ADC 13 and have been using MFA authentication for both Web and Receiver for multiple years allready. We have been using classic policies and have not had any issues up untill we updated our NS to version 13.
The web auth is still working flawlessly, however the Receiver auth is not working as we expected. Actually we are nt able to logon anymore and keep getting prompted with Login screens, requesting to put in our Username, PW and Passcode.
Below the primary and secondary auth policies.
PRIMARY LDAP
90 LDAP_LOCAL_Browser REQ.HTTP.HEADER User-Agent NOTCONTAINS CitrixReceiver LOCAL_LDAP
100 LDAP_PRODUCTION_Web REQ.HTTP.HEADER User-Agent NOTCONTAINS CitrixReceiver LDAP_PRODUCTION
PRIMARY RADIUS
90 Receiver_GemaltoCloud_Receiver REQ.HTTP.HEADER User-Agent CONTAINS CitrixReceiver Gemalto
SECPNDARY LDAP
80 LDAP_LOCAL_Receiver REQ.HTTP.HEADER User-Agent CONTAINS CitrixReceiver LOCAL_LDAP
90 LDAP_PRODUCTION_Receiver REQ.HTTP.HEADER User-Agent CONTAINS CitrixReceiver LDAP_PRODUCTION
SECONDARY RADIUS
100 Browser_GemaltoCloud_Browser REQ.HTTP.HEADER User-Agent NOTCONTAINS CitrixReceiver Gemalto
We have at least 4 and I have the impression the order is also correct. only difference we have is that we have mulitple LDAP policies. Could this be the reason the prompt to auth keeps coming back? Strange thing is that this was working correctly in the past. Any tips/advice on what we might be doing worng here?
Thanks
I wonder if it needs a Traffic Policy to enable SSON to StoreFront.
Have you tried switching to nFactor (AAA vServer)?
We have a traffic profile, but it only states ‘Single Sign-on’ > ‘On’
Nothing else is configured.
We have not yet tried to switch to nFactor but will probably look into it somewhere beginning next month
Hi Carl,. Just had quick advise would need,
1.ldap auth 2. Radius (NPS mfa)
authenticate in Mobile,.
Is any configuration we missed to get only single pop up approval message for mobile??
Configured 3 netscaler ip(vip, primary, secondary) as radius client in NPS
because of this we r getting 2times auth pop up notification for mobile??
Are you testing internally instead of externally? Does the mobile device have access to the Internal Beacon and the StoreFront Base URL? For accurate testing, make sure Internal Beacon and the StoreFront Base URL are not accessible from the mobile device.
We don’t have access for internal beacon or storefront base url in mobile device. Yes carl! I am testing internally, because still public gateway url records are not created in public DNS, Does still we require to make records for public DNS? even if we are using GSLB ADNS for Records?
Workspace app connects to Gateway to download the provisioning file. Then Workspace app reads the internal beacon from the provisioning file and tries to connect to it. If successful, then Workspace app connects to the StoreFront base URL in the provisioning file and StoreFront will ask for authentication even though you’ve already been authenticated at Gateway. If you do your testing externally, then internal beacon won’t be reachable and all communication will go through Gateway, which only authenticates once.
Even with externally also we are getting multiple times authenticate for Mobile,
In StoreFront Console > Manage NetScaler Gateways, edit the Gateway. On the Authentication tab, is it set to Domain and security token?
In Citrix Gateway > Session Policy, do you have one that sets Credential Index as Secondary for Workspace app?
Yes carl! In StoreFront Console > Manage NetScaler Gateways, edit the Gateway. On the Authentication tab, is it set to Domain and security token?–Yes
In Citrix Gateway > Session Policy, do you have one that sets Credential Index as Secondary for Workspace app?– Yes still we are receiving two times authentication
Hello Carl, thanks for the article which was very good.However I got a strange behavior. indeed when I used classic policies (first LDAP secondary RADIUS) everything is working perfectly (on receiver and web). If I switch to advanced policies when I use single auth with LDAP it works but when i switch to dual policy LDAPs and Radius then I got the error “cannot complete your request” and the event viewer on the storefront displays event viewer 7 and 10… I have look all over internet but cannot find any answer on how to fix this…
I wonder if it’s because the wrong password is being sent to StoreFront. If you edit the Login Schema and click More, there’s a checkbox for Single Sign On Credentials. Another option is to store the LDAP password in an AAA Attribute and use it later in a Traffic Policy.
Thanks Carl however i don’t have advanced license… so i cannot check the Single Sign On Credentials… can you please explain me how to store the AAA Attribute ?
Thanks
My nFactor article has some info on it but I don’t think you’ll be able to configure it in Standard Edition. Search the article for “attribute”. https://www.carlstalhood.com/nfactor-authentication-citrix-gateway-13/
Hi Carl, you are absolutely right. In the standard release of ADC I cannot set any value on password attribute of my login schema… I will open a case on Citrix support because in my opinion even on standard license I should be able to use dual authentication as I used to do it with classic policies.
Hi Carl, still regarding my password issue, do you know if there is any solution on how to use dual authentication with advanced policy ? At the moment our customer got Citrix Gateway Advanced VPX license. Is it possible to add the Citrix ADC advanced on my gateway (mix the two license in fact) ?
Thanks
Hi Anthony, did you manage to solve this? I am facing the same issue right now on 13.1. It seems that Citrix overlooked standard license customers that are using two factor auth.
Hi Carl,
I tried to switch first and second factor so that first factor is RADIUS and then LDAP as second factor.
So I created a Policy Label für LDAP (instead of RADIUS) with the Login Schema “LSCHEMA_INT”.
In the Authentication Policy from the AAA vServer, I selected the RADIUS Policy as first factor and LDAP Policy as Next Factor.
Now I can see that RADIUS authentication is checked first (as desired) but the RADIUS authentication always fails. I can verify that my RADIUS passcode is correct.
Any idea what I missed?
Thanks in advance!
Hong
Did you also modify the Login Schema to flip passwd and passwd1? There’s also a DualAuth_Flipped.xml file.
No because I don’t want to switch the login fields username/pass/token.
But I just entered password and token in the “Flipped” order and it worked!
So question is, how can I use DualAuth.xml correctly with RADIUS as first factor?
In the XML file, flip the passwd and passwd1 identifiers. Whichever field is passwd is evaluated before passwd1 is evaluated. The fields are displayed in the correct order but passwd is processed before passwd1.
No, flipping the passwd and passwd1 identifiers didn’t change anything.
The fields are displayed in correct order but I have to enter the token in the password field and the password in the token field to have a successful login.
After modifying the Login Schema, in the ADC GUI, go to the Login Schema Profiles node, edit the Login Schema, and re-select the Login Schema file. You must do that every time you modify the file.
I always create a new XML, upload it to /flash/nsconfig/loginschema and select the new XML in the Login Schema Profile 😉
Hi Carl, thank you for your help, the Login Schema never change to have the password field and the pin field, do I have to do something else?
Hello,
I was following your guide to enable 2 factor autherntication with radius, but when I got to step 6 the test fails.
If I do ping test using the NSIP of the VPX it works OK:
>ping -c 5 -i 1 -s 56 -S 172.18.3.17 -n 192.168.11.99
PING 192.168.11.99 (192.168.11.99) from 172.18.3.17: 56 data bytes
64 bytes from 192.168.11.99: icmp_seq=0 ttl=62 time=1.567 ms
64 bytes from 192.168.11.99: icmp_seq=1 ttl=62 time=1.029 ms
64 bytes from 192.168.11.99: icmp_seq=2 ttl=62 time=1.049 ms
64 bytes from 192.168.11.99: icmp_seq=3 ttl=62 time=1.553 ms
64 bytes from 192.168.11.99: icmp_seq=4 ttl=62 time=1.125 ms
— 192.168.11.99 ping statistics —
5 packets transmitted, 5 packets received, 0.0% packet loss
round-trip min/avg/max/stddev = 1.029/1.265/1.567/0.243 ms
Done
But when I press “Test RADIUS Reachability” it says:
Server ‘192.168.11.99’ is reachable.
Either ‘192.168.11.99’ is not a valid Radius server
‘1812/udp’ is not a valid Radius authentication port or Radius client is not configured properly in the Radius server.
What can I check to make it work?
Thanks in advance,
Christian M
The test button uses NSIP to do a RADIUS authentication request to your RADIUS server (or VIP) and expects a response. I’m guessing the NSIP didn’t get a response.
Hello Carl,
Thanks for your reply, I checked with the people that manage the RADIUS Server, and they don’t see any connection attempt from the VPX, Is there a file or troubleshooting I can do to verify access? besides ping that clearly works from the VPX’s NSIP.
Regards,
Christian M.
I usually ignore the testing button since it uses NSIP when I typically use load balancing that uses the SNIP. Create a RADIUS authentication policy and bind it to your Gateway or AAA. When doing authentication, use “cat /tmp/aaad.debug” to see what is happening.
You can also do “nstcpdump.sh port 1812” to see the RADIUS traffic.
Do I need to have a SNIP in the same subnet as the NSIP for it to work?
Regards,
Christian M.
No. If you are load balancing RADIUS through a local VIP, then any SNIP that can reach the RADIUS server is fine.
Thank you for your help Carl,
In tandem with our networking team we checked the communication from VPX was working and trying to connect to the RADIUS server, but the port 1812 was enabled for TCP and not UDP in the Firewall. (by mistake i guess)
Once the port was correctly configured everything worked.
Maybe you can add some tips on troubleshooting for people like me that are just getting into VPX and its configurations?
Thanks again,
Christian M.
Carl, we started implementing OKTA as Radius authentication .. followed all the steps so web version works just fine but receiver self service i see it authenticates to Okta but returns back with invalid username or password error in workspace, any thoughts
Are you doing nFactor? Or are you doing classic authentication?
Are you doing two password fields, one for LDAP and one for RADIUS? If so, and if doing classic authentication, then you need to swap the fields.
Carl do you have a post where you show how to configure netscaler for OKTA radius with nfactor ? trying to setup a wyse terminal in the company wiht OKTA and nfactor is the only thing i can think of to make it work with email address for OKTA verify and SAMaccount for LDAP.
Does Wyse support nFactor?
The 9.0 version does I think.
I’m trying to test all that and see how to make OKTA work for Wyse factor or not.
Right now we are trying to get off RSA
Hi Carl,
Do you know if it is possible to extract e.g. the AD attribute ‘mobile’ and send it as the username in the RADIUS request?
Hi Carl,
Thanks for all the work you do.
We use RADIUS with the Azure MFA NPS Extension, and it works. If the user’s default Azure MFA method is Authenticator Notifications, the user will just get a spinning circle after entering AD credentials. We’d like to present a screen using nFactor that tells a user “Please approve the notification in your Authenticator app”.
I’ve tried fiddling around with login schema XML’s, but when I apply a login schema to the RADIUS factor, it won’t send the notification. Do you have any ideas?
I’m not aware of any way to do that. That’s one of the limitations of RADIUS as compared to SAML.
Hi Carl, Thank you for the document I was wondering if its possible once you have the 2 factor up and running if you can then apply this to only certain users? And allow some users to log in via a single policy?
You can configure it using nFactor. https://www.carlstalhood.com/nfactor-authentication-citrix-gateway-13/
Thanks, Is there another way of doing this if you don’t have the license to set up nFactor? Like setting up a separate storefront?
Separate StoreFront usually means separate URL. You can easily setup multiple Gateways with separate URLs and use LDAP Search Filter to restrict who can use each Gateway.
Okay, but can you then set one gateways to use 2fa and another gateway to use single factor?
Just bind different policies to each Gateway.
Sorry to come back to this. But is it possible to do this on the same Gateway without nfactor?
Gateway only prompts for one password or two passwords for all users that connect to that Gateway. It’s not possible to choose different number of password fields for different users without nFactor.
If your MFA Product can do both Active Directory and the second factor at the same time with only one password field, then you can have different authentication policies for MFA vs AD-only. However, Gateway won’t have the user’s AD groups yet so you can’t use AD groups to select the authentication policy. But other factors like FQDN or Source IP can be used. You can cascade multiple authentication policies and Gateway will try each one until it works, but that will cause failed logons for the ones the user is not entitled to use.
Hi Carl, we are running Netscaler 12.1. Remote Gateway Authentication Radius with LDAP. Noticed the monitor was Down and verified the Radius server ip port udp/1812 and just to make sure edit the conf re entering the secret key. Any pointers for bringing this Up would be greatly appreciated. Thank you
Does it show you receiving a result code? I usually add Result Code 3 to the monitor.
Or, it’s easier to change the monitor to ping.
Hi Carl. We are trying to setup RADIUS Authentication with MFA (NPS MFA Extension) and facing some issues. The error at NPS Server:
NPS Extension for Azure MFA: NPS Extension for Azure MFA only performs Secondary Auth for Radius requests in AccessAccept State. Request received for User xxxxxxx with response state AccessReject, ignoring request.
We have 4 policies like your documentation.
Policy Name Type Bind Point
LDAP-Corp-ReceiverForWeb LDAP Primary
RSA-ReceiverSelfService RADIUS Primary
LDAP-Corp-ReceiverSelfService LDAP Secondary
RSA-ReceiverForWeb RADIUS Secondary
With NPS, you usually don’t need both LDAP and RADIUS, just RADIUS is sufficient. ADC asks the user for AD password and sends it to NPS. NPS authenticates AD, then the Azure MFA plugin uses the user’s default MFA method to perform MFA. After both are complete, NPS returns success. You don’t need both LDAP and RADIUS when doing NPS because NPS does AD authentication for you unless you turned off AD authentication on the NPS server.
Generic high level question, can a Netscalar gateway be configured to use primary auth via a on prem ldap/ad and secondary mfa auth via a radius agent (on prem or cloud like a DUO or Okta’a Radius Agent App)?
Of course. I configure this frequently.
thanks Carl, perhaps i missed it but can you please link to any docs you may have which walk through this setup? thanks in advance.
Some of the RADIUS products do both AD and MFA with one password field. In other words, users enter only the AD password and the RADIUS server then does MFA after the RADIUS server verifies AD credentials. In this case, just configure the RADIUS policy/server and bind to the Gateway. No LDAP needed.
Other products require two password fields: one for LDAP, and the second for MFA passcode. Duo has the ability to hide the second password field for web browsers but shows it for Workspace app (if not doing nFactor). Here’s a sample guide for Duo – https://duo.com/docs/citrix-netscaler-alt . If no nFactor, then you might have to swap the password fields as detailed in this article.
Hello Carl,
Thanks for the article as it helped me a lot. I had integrated Azure MFA with NPS extension and bind the RADIUS policies only as you mentioned above. I have 2 RADIUS policies under primary for receiver and web. Receiver authentication and application launch works just fine, but strangely, the Web browser access doesnt work. Authentication happens over web browser and I can get to the storefront apps, but I am unable to launch any apps and it doesnt show any error as well. Tried multiple browsers, but still same problem. Do you happen to see such issue before?
Hi Carl,
I have followed this article to the letter to get MFA authentication working with our 3rd Party OTP product and most of the configuration is working. We stumbled across an issue whereby users connecting via the Workspace app could not reset their AD password when it had expired. To fix the issue I have now re-ordered our authentication policy bindings so that LDAP is the Primary authentication policy and Radius is the secondary authentication policy. Users can now reset their AD passwords when they expire when connecting either by Web browser or with a Citrix workspace app connection from any device (IOS, Android, windows etc). I am unsure why in the article it says that users connecting via the workspace app (where User-Agent string contains CitrixReceiver) have to have RADIUS as the primary authentication policy as this doesn’t appear to work for us ?
Best regards
Gary
Thank you for this article. It seems to me that MFA using MS Authenticator and NPS will work with all editions of VPX, including the “free” version (express?). Am I correct?
Free doesn’t include Gateway so probably not. If you use Classic authentication policies with Gateway, then any licensed ADC will work. AAA, Advanced Authentication policies, and nFactor are only in ADC Advanced/Enterprise edition.
I’m on 12.1.x using the free version and Gateway for ICA proxy works just fine. Are you referring to the Unified Gateway?
I have upgraded from 11.x which I believe did in fact include full Gateway functionality. Might this by why it works for me on 12?
Hi Carl, I successfully implemented such config with Radius last year because the SAML did not work with the IOS receiver as Apple does not support the browser in the Citrix Workspace app for authentication. https://support.citrix.com/article/CTX267031
I dont know if there is any other method than those 2 (separate gateway and full VPN) you might have found? I’m back to the old way of authentication because of IOS devices…
thanks and good job for great articles!
Hi Carl, Does Netscalar 12.1 supports RSA REST API? I understand it works with Nitro APi, wanted to know if RSA REST API is supported?
Carl,
We are working on deploying Dup with our Citrix Gateway and Storefront servers and have it pretty much working through web and receiver. We are also working to deploy to external Dell Wyse clients and running into minor issue. User logs in with AD credentials and receives Duo push and approves. Once user launches a desktop you are told password has expired and needs to be re-entered. If you enter in your AD password you receive and approve second Duo push and desktop launches. Can you assist in helping get rid of the second AD password prompt?
Right now we are using 2 RADIUS policies on the Citrix Gateway that point to the Duo Auth server. One for receiver and one for web.
Hi Carl,
thx for your tutorial. i have a strange Problem. Web Site Login runs well.
Ldap password in the first passwordfield and token password leave blank for authentication on the second screen.
But on receiver login i have to enter the ldap Password in token passwordfield. were can change this?
best regards
Roger
Did you swap the fields as detailed in this article? You should have four authentication policies: two LDAP, two RADIUS.
Hi, Carl. thy for your reply.
Yes i swaped these fields and i have 4 Policies.
Hi Roger, I’m not sure if this will help you but we had the same issue in our environment. For us, it turns out we didn’t do the part in Carl’s instructions under “Bind Two-Factor Policy to Gateway”. After setting the correct authentication index for the Mobile policy following those instructions, and disabling authentication on our LDAP policy (we just allow RADIUS/NPS to take care of authentication) our “passcode token” field disappeared in Receiver and “password2” field disappeared for web.
Hi
We have this completely set up for Web Browsers using Google Authenticator (this requires that the userprinciapal name to be input in the user field) but when I try and set up the Wyse terminals to use Google Authenticator I can see (looking at aaad.debug) them authenticating via Radius and LDAP successfully but the Wyse terminal beeps and says incorrect authentication.
I have tried forcing it to send both the sAMAccountname and the userPrincipalname with no change in behavour.
We have set up RSA correctly for users with a hard token (different virtual server and this uses samaccountname) and the Wyse terminal correctly logs in.
So I am thinking there is a problem with the Storefront accepting userprincipalname but everything I have tried has not worked.
Thanks
Tom
Do the Wyse terminals require the password fields to be swapped like Receiver/Workspace does?
Hi
Sorry for the late response
Yes and I have done this following your guide for the normal Radius setup (just pointing the radius server at the Google Auth server we have running in house)
When I run cat /tmp/aaad.debug I can see both authentication (first Radius and then LDAP) – the Wyse terminal then beeps and says incorrect login
I have run this through both Citrix support and Dell Wyse support both of which gave up 🙂
As I said it works via a https page and the Wyse terminal works when we use the normal RSA tokens – the only difference between the RSA and the Google Auth is that RSA uses Samaccount name and Google uses UserPrincipalName
Thanks
Tom
Hi Carl,
By default Netscalar gateway ask for username, Password and Password2 in the same login page. Is there a way to configure it to ask for Username and Password in one page and Password2 in the next page.
Say, I have LDAP as primary authentication and RADIUS as secondary authentication (i am entering an RSA passcode and contacting RSA radius server to get authenticated). So what i want is to enter username and LDAP password on the first page and just RSA passcode on the second page. is there a way to break up the Netscalar login page to allow this ?
Thanks!
nFactor can do that, yes. https://www.carlstalhood.com/nfactor-authentication-for-netscaler-gateway-12/
thanks for the quick response. Apart from nFactor is there any other way to achieve this? I just wanted to confirm nFactor is the only way to do this.
Duo RADIUS sends a RADIUS challenge instead of requiring the user to enter a passcode on the first page. I’m not sure if RSA supports something similar. Otherwise, nFactor is the best option.
Hi Carl,
Is there a way to set radius besides using the Netscaler Gateway option. Right now I have virtual servers under “load balancing” and I’ll like to set the Radius authentication under this option.
Thank you!
You can add a AAA (Authentication) vServer and bind it to the LB vServer. NetScaler will prompt the user to authenticate before allowing access to the website.
Thanks, I’ll try that. Is possible to add MFA on top of the LB vServers as well?
Sure. Your AAA Virtual Server supports any authentication. nFactor is very flexible.
Hi Anuvab
We managed this by creating 2 rewrite actions and binding to 2 rewrite policies one for Web and one for Receiver to hide the “Password 2” field. Apply both to the AG and the result is users get username and password on 1st page and RADIUS on 2nd page.
If possibible, please send us an example. We have the same issue.
Just wanted to give a shout and say Thank You for the time you put into these articles. We’ve been battling a migration to new 7.15 environment with doubleNAT DMZ and 2FA, and your insights have been crucial along the way. We routinely refer to you as “Our Guy Carl Who Knows Everything About Citrix…” Keep up the great work!
Hello Carl, thanks you for the loads of information.
We are using Netscaler with Radius for 2 factor authentication.
When connecting from browser, ldap and token is required.
In the native Citrix Workspace, the sms token is only asked after creating the account. Next time I can login without the token. The device seems to stay validated. Is there a timeout so that next time a user logs on, sms token is asked again ?
If the Internal Beacon is reachable, then Workspace will connect directly to StoreFront, which doesn’t require MFA. If Internal Beacon is not reachable, then Workspace uses the Gateway authentication settings configured in StoreFront Console > Manage NetScaler Gateways > Edit > Authentication. It should be set to Domain + Token.
That’s what I expected too! When I’m connecting from WAN with Workspace App, the first time I need to create an account. I’m asked for loginname, password and after the a new field for sms token is presented.. Login works fine!.When I then logoff Citrix Workspace, or reboot my laptop and login into the Workspace App, online loginname and password is asked. The sms token is never asked again. My apps are presented and I start the apps without problems. I would like the sms token in Workspace App to expire e.g. within one hour or half an hour. So next time I login to the Workspace App there will also be a sms token required.
Thanks for commenting!
This is an awesome article. I’m quite new to Netscaler and with your help I managed to set up LDAP and Radius authentication. From netscaler point of view everything looks fine. Radius monitor authenticates successfully. LDAP without Radius works perfectly. But I’m not able to login with LDAP & Radius because my token seems to be in new-pin mode. The window to set a new pin/passcode doesn’t come up. aaad.debug shows successful LDAP auth but rejected Radius auth. Any idea what I’m doing wrong? Thanks
Is it possible to configure sms passcode via radius and storefront but without use of the netscaler?
StoreFront does not have native support for RADIUS.
But StoreFront does have some support for SAML.
Hi Carl,
somehow i cannot reply to your previous answer.
My netscaler is just connected to the RADIUS Server, so no directly Active Directory connection at all. Is there a way to just use the successful RADIUS Login to connect to the store ?
So without any further passthrough or login?
Regards,
Sanchez
Ultimately the user will need to log into a VDA machine, which requires Active Directory authentication. StoreFront needs Active Directory username to determine which icons the user is entitled to see.
How to authenticate netscaler management tasks with radius or ldap or cisco ise
I have some management authentication instructions at https://www.carlstalhood.com/system-configuration-citrix-adc-13/#auth
Hi Carl
Is there a way to have 2 RADIUS authentication bound to the same Virtual Server and direct the user to the correct one based on AD group membership?
The use case for this would be when having 2 MFA providers.
Thanks
With nFactor, yes. nFactor can extract LDAP group membership and then user group membership to choose the next factor.
Hi,
some other products can do that as well, for example OpenOTP can send a RADIUS challenge for additional factors, send a push Push message to mobile for Approve/Deny 2FA, request U2F/FIDO2 if the client supports it etc. etc.
These can all be configured per authentication client, user or user LDAP group.
Hi Carl,
Can you please help in swapping password and RSA token fields in gateway login page. If we change the credential index to secondary will it work?.
Just put RADIUS in primary and LDAP in secondary. Users will then be prompted for RADIUS first and LDAP second so you’ll have to edit your Portal Theme labels correctly. You can also swap the fields on the Portal Theme but that requires hacking the HTML code.
Thanks Carl. I already changed RADIUS as the primary authentication and LDAP as secondary. But client is interested in seeing it in the login portal also.
Is there any citrix blog talks about editing the html page for changing it. Unfortunately not found one.
Depends on the theme. For non-RFWEBUI (e.g. X1), you can modify the gateway_login_form_view.js file to swap the password fields. Then use the normal process to change the labels.
Hi Carl,
Thanks for your quick assistance. I am able to swap the Password & Password 2 fields successfully.
You are the champion 🙂
Hi Carl, thank you for your outstanding site. I need help with our unique configuration. We have two factor (RSA and AD) but not from one screen. Users prompted for RSA ID and token and after successful authentication redirected to Citrix Web Interface for AD password. I am trying to migrate the same to StoreFront but cannot find the correct settings. I found this https://support.citrix.com/article/CTX237625 but as usual with Citrix documentation they seem to be missing something. Any advice is greatly appreciated. Thanks
If you want StoreFront to do the second authentication, they try this – https://support.citrix.com/article/CTX200066
Hi Carl,
Thanks for your response.
Can you help me please what would be the configuration changes that I need to do in storefront and Netscaler 12.1? Already unchecked single sign-on to web applications under clients experience in Netscaler.
In storefront already did the trial an error config but to no avail still the cannot complete error persist. Thanks Carl.
Regards,
John
To configure StoreFront to not require an AD password, see https://www.carlstalhood.com/citrix-federated-authentication-service-saml/#storefrontsamlgateway. When the user launches an icon, the VDA will prompt the user for the AD password.
If you want to eliminate the AD password, then you’ll also need to implement Citrix FAS.
If you want StoreFront to ask for the user’s AD password, see https://support.citrix.com/article/CTX200066
Hi Carl,
I followed the above article it is very useful, but after providing radius token it goes back to ” Can not complete Request” and if i remove radius and use LDAP authentication works fine and application launches fine
Are you doing both LDAP and RADIUS? Or just RADIUS (without LDAP)?
Hi Carl,
Thanks for this article.
I got ‘cannot complete request error’ too while doing radius authentication.
I’m using only Radius(without LDAP).
Tried to gather logs also via aaad.debug and got the below message error.
I was able to authenticate successfully based on the logs.
error message:
process_radius 0-71: extracted group string :(null)
Hope you could help me on this. Thanks Carl!
Regards,
John
Are users entering their AD password into the RADIUS field? If not, then it’s not possible to do Single Sign-on from NetScaler to StoreFront and you’d have to make some changes to StoreFront.
Hi Carl,
im having trouble with the “cannot complete your request” error too.
I followed your guide to configure RADIUS authentication.
The aaadebug shows me that the authentication is successful and ends with “sending accept to kernel for: user@domain”.
In the windows Event-Viewer, i get the Event ID´s 7 and 10.
I want to delegate the whole authentication to the netscaler, which is connected with a RADIUS Server in a different domain.
Do you got any tips to solve this issue?
Regards,
Sanchez
Does NetScaler have access to the user’s Active Directory password? If not, then you’ll need to follow the instructions in the FAS article, especially related to configuring StoreFront to delegate authentication to NetScaler. https://www.carlstalhood.com/citrix-federated-authentication-service-saml/
I assume it has access to the user’s Active Directory username.
Another option is to configure StoreFront to prompt the user for Active Directory credentials. https://support.citrix.com/article/CTX200066
Hi Carl,
Just wondering if you can help me. I need to do the following with my NetScaler 12.1 appliance:
1. Use a single SSL VPN endpoint to provide MFA via Azure MFA server (Azure MFA will handle both Windows and Radius auth)
2. Apply different session policies based on AD user group, logic is If user is member of Group A, apply session policy with Split Tunneling off if user is member of Group B, apply session policy with Split Tunneling on.
3. Access to SSL VPN is provided by the NetScaler Gateway client only
Are you able to advise what is the best way to achieve this?
Your help would be much appreciated.
Thanks
Which particular step do you need guidance on?
If Azure MFA Server, enable the LDAP listener, and configure NetScaler to use LDAP so it can get the user’s groups. It’s more difficult with RADIUS.
Once you have groups, then the rest is standard.
Hi Carl,
Thanks for the prompt response. I’ve configured the NetScaler Gateway to use Radius as it’s primary authentication and Azure MFA Server. This works great. Where I’m struggling is to understand the process I need to go through to get the NetScaler to grab the AD Groups so I can use them for Session policy assignment.
Configuration I have used is based on this article http://download.microsoft.com/download/1/A/4/1A482764-4A63-45C2-A5EC-2B673ACCDD12/Citrix_NS_Azure_MFA_RADIUS.docx
Regards.
The MFA Server has an option to listen using LDAP instead of RADIUS. Then you configure NetScaler to talk to MFA Server using LDAP instead of RADIUS. I think MFA Server will send back the user’s groups using LDAP.
Unable to hide the passcode field in receiver / workspace client under NetScaler 12.1 where it was working fine using the well documented rewrite policy under NetScaler 12.0.
Does anyone have any information on how to achieve the same under NetScaler 12.1?
You’re doing this with the X1 theme? What procedure? I recently followed Duo’s procedure and I couldn’t get it to work until I failed over over my HA pair. Something was cached.
Changing the logon type to “Domain and security token” is valid for ReceiverSelfService only or ReceiverforWeb as well?
Just for ReceiverSelfService. It controls the authentication settings in the provisioning file, which is read by ReceiverSelfService.
Thanks Carl. I have load balanced Defender servers on the NetScaler. I gave the the SNIP to Defender guys to create an agent (client). Am I doing it right?
What should be the username and password for Defender while creating the Monitor?
For RADIUS monitor, you want a username that has a static password. Or, set your RADIUS monitor to look for result code 3, which means that RADIUS rejected the authentication request. However, rejected requests usually fill up the logs on the RADIUS server.
Hi Carl, I have configured 2 factor authentication on our NetScaler for LDAPS and RADIUS. Login appears successful through the receiver however I get ‘cannot complete your request’.
This is a new config?
Did you change the Session Profile for Receiver to set Credential Index = Secondary?
So can an NS be configured to support 2 step authentication ala having an SMS code sent to a mobile device instead of using an event-driven token or an OAUT app like google authenticator. Looking for the experience to be…
– user logs in with username and password
– RADIUS triggers an MFA request by way of SMS to users mobile
– NS throws a prompt to enter the SMS code… login successful….
As it stands when you enable the RADIUS auth it adds the code field to the login screen as a third box, at that point we havent yet got the code !
Any suggestions ? or is this not possible…. If anyone knows this you will Carl !!
Only asking this as we use Microsoft Multi Factor Authentication server for MFA, recently deprecated the phone calls option in preference for SMS (which works really well on our MS web based apps)
NS integrates to it for RADIUS without issue but the order of events seems to not work…..
Yes. But you’d have to hide the second password field so RADIUS is still attempted. It’s much easier to hide in X1 theme than RfWebUI theme. Duo has instructions to hide the second field – https://duo.com/docs/citrix_netscaler-alt#modify-the-sign-in-page
In my Environment it seems not to work with NetScaler 12.1 48.13.nc.. I see the policy hits, but the 2nd password field is still showing up.
Do i need to configure someting different with Netscaler 12.1?
I appear to have the same issue running NetScaler 12.1 although I am only really concerned with hiding the passcode field in the receiver client. This was previously working under NetScaler 12.0 using the well documented X-Citrix-AM-GatewayAuthType = SMS rewrite action
What I had to do was remove the secondary authentication (which only adds a PIN box) and change primary authentication to RADIUS at which point you see username and PIN on the one screen and no prompts for another PIN.
If you have a single authentication server (e.g. NPS plus Azure MFA) that can do both authentication steps, then that’s the easiest configuration for NetScaler. However, users might not be able to change their expired AD passwords.
Hello Carl
I have a Netscaler 12 VPX 1000 Enterprise license and would like to make 2 factor Auth against the storefront.
I always get the error code 4020.
Can you help me?
You setup a NetScaler Gateway?
What kind of 2-factor? RADIUS?
Did you try aaad.debug? https://support.citrix.com/article/CTX114999
I am using NetScaler Gateway 12.0-57.19 and I am also having this same problem. I use a NetScaler in Azure, with MFA authentication.The problem is only with iPhone, where it always asks for “Token” in the configuration. For Citrix Receiver in Windows everything is ok.
What RADIUS auth does netscaler support? Is there like a validated list?
Hi Carl,
In your screenshot below Authentication there are no Advanced and Basic policies.Are the screenshots really from v12 ?
Because Citrix is going to deprecate Basic policies how to do it with Advanced ones ? I created two advanced policies (LOCAL, LDAP) bind them to an authentication server with respectively 100 and 110 priority value (both have NEXT set up). Unfortunately I can see only one password field. If I move to Basic an create Primary and Secondary I can see two password fields. Does it mean Citrix plays tricks on me showing Deprecation warning message ?
They seem to be encouraging nFactor. You can bind Advanced Authentication Policies to a AAA vServer, and then use an Authentication Profile to link it to a Gateway vServer. This requires NetScaler Enterprise Edition. It would certainly be easier if I can bind nFactor and Advanced Authentication Policies directly to Gateway.
Thank you very much. Seems a new adventure is calling me now … Adventure with Authentication profiles …
Hi Carl,
We need to transition to duo from rsa for our 2 factor auth. Using the same url, is there an easy way to transition using the same gateway url?
thanks,
Zach
Carl,
Is there a way of using the netscaler virtual server IP address to send to the radius server? Ultimately the NISP is sent. I need to have dedicated policies and profile on our Radius service which can be triggered by the the actual individual virtual servers IP addresses and not the NISP or SNIP
You should be able to create a Net Profile that specifies the VIP, then bind the Net Profile to the Load Balancing Virtual Server.
we tested with “domain and sedurity token” and domain only. we also added the provided meta tag.
with domain only and the meta tag it is working for us. but we have then the 3rd field in the browser.
if i add the rewrite policy to hide this in browser the receiver stopped working. 🙁
it is so frustrating.
Hi Carl, as always a realy helpful article. But something working wrong on my site. I configured all as you write above. Login from Web works fine by entering Username and Password, leaving Password2 empty. (Radius is challange/response) On iOS and Android also all is working fine. But on Windows Receiver (tested with 4.9 and 4.7) I have to enter the Password in the Password2 fiel. 🙁 Login is working fine after that.
Do you know what I have configured wrong on my Netscaler?
Best regards
Beat
I wish NetScaler had an easy method of hiding the second password field.
In StoreFront, did you set it to Domain only?
On NetScaler, did you add the Meta tag to hide it? https://support.citrix.com/article/CTX205907