Navigation
This article applies to Federated Authentication Service (FAS) versions 2411, 2402 LTSR, 2203 LTSR, 1912 LTSR, and all other versions 7.9 and newer.
- Change Log
- Overview
- Install/Upgrade FAS Service
- FAS Group Policy
- FAS Configuration
- StoreFront Configuration
- SAML Configuration:
- Active Directory Shadow Accounts
- Verify FAS
Change Log
- 2025 Jan 9 – updated Versions section for version 2203 CU6
- 2024 Dec 4 – updated Versions and Install sections for version 2411
- 2024 April 2 – added Force Authentication in NetScaler SAML Action
- 2024 March 6 – added Standard Edition instructions
- 2024 April 30 – updated Versions section for version 1912 LTSR CU9
- 2023 Aug 11 – added link to Deployment Guide: Multi-Domain FAS Architecture at Citrix Tech Zone.
- 2023 May 17 – added info from Can I enable other credential providers after installing Duo Authentication for Windows Logon? (h/t Barry Barclay)
Overview
Citrix Federated Authentication Service (FAS) enables users to log in to Citrix Gateway and Citrix StoreFront using SAML authentication.
With SAML, Citrix Gateway and StoreFront do not have access to the user’s password and thus cannot perform single sign-on to the VDA. FAS works around this limitation by using issuing certificates that can be used to logon to the VDA.
- StoreFront asks Citrix Federated Authentication Service (FAS) to use a Microsoft Certificate Authority to issue Smart Card certificates on behalf of users.
- The certificates are stored on the FAS server.
- The VDA requests the user’s certificate from FAS so it can complete the VDA Windows logon process.
FAS can be used for any authentication scenario where the user’s password is not provided.
Requirements:
- Microsoft Certification Authority (CA) in Enterprise mode.
- When configuring FAS, you tell it what CA server to use.
- You can build a new CA server just for FAS.
- You can install CA on the FAS server.
- Domain Controllers must have Domain Controller certificates. See CTX218941 FAS – Request not supported.
- The certificates on the Domain Controllers must support smart card authentication. Certificates created using the Microsoft CA certificate template named Domain Controller Authentication supports smart cards. Manually created Domain Controller certificates might not work. See CTX270737 for the Domain Controller certificate requirements.
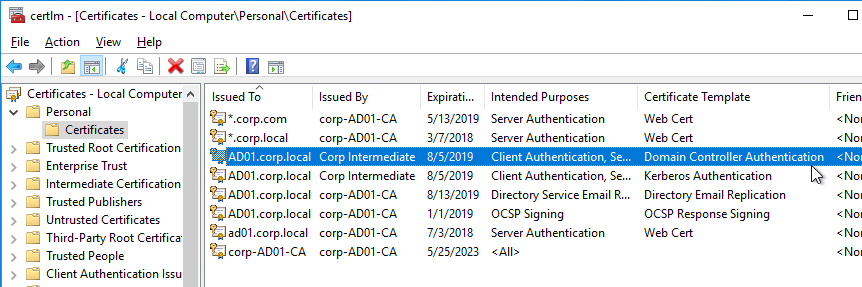
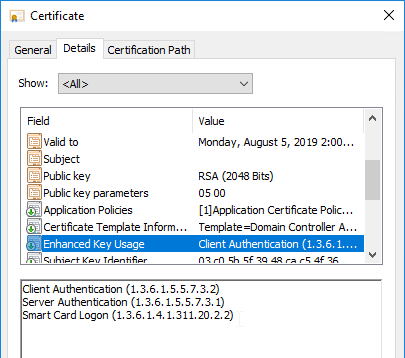
- The certificates on the Domain Controllers must support smart card authentication. Certificates created using the Microsoft CA certificate template named Domain Controller Authentication supports smart cards. Manually created Domain Controller certificates might not work. See CTX270737 for the Domain Controller certificate requirements.
- Citrix Virtual Apps and Desktops or XenApp/XenDesktop 7.9 or newer
- StoreFront 3.6 or newer
- Citrix Gateway.
- StoreFront 3.9 and newer also support SAML authentication natively without Citrix ADC.
- SAML in an nFactor (Authentication Virtual Server) configuration works in both browsers and Workspace app.
- For multiple domains, see Deployment Guide: Multi-Domain FAS Architecture at Citrix Tech Zone.
Configuration overview:
- Build one or more FAS servers.
- For security reasons, FAS should be its own server and not installed on a Delivery Controller.
- Upload Certificate Templates to Active Directory and configure a CA server to issue certificates using the new templates.
- Enterprise Admin permissions are needed to upload the Certificate Templates.
- One of the Certificate Templates is for Smart Card logon to Citrix VDA.
- The other two Certificate Templates are to authorize FAS as a certificate registration authority.
- The registration authority certificate does not renew automatically so be prepared to renew it manually every two years. See Renew registration authority certificates at Citrix Docs.
- Install the Citrix FAS group policy .admx template into PolicyDefinitions.
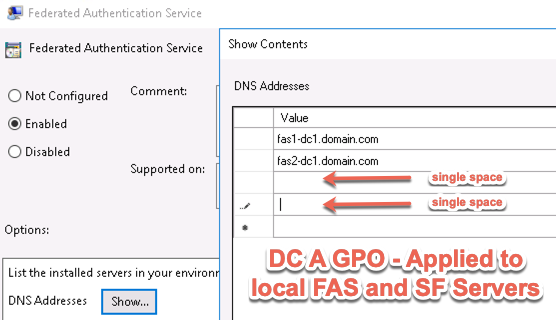
- Create a group policy object (GPO) and configure the GPO with the addresses of the FAS servers.
- The GPO must apply to FAS servers, StoreFront servers, and every VDA. It does not need to apply to Delivery Controllers, but there’s no harm in applying it to the Delivery Controllers.
- Authorize FAS to request certificates from a Microsoft CA server.
- Configure FAS Rules to permit StoreFront servers to request FAS to generate certificates for users and permit VDA machines to retrieve the certificates from FAS.
- Configure StoreFront to use FAS for VDA single sign-on.
Links:
- CTA Julian Mooren Citrix FAS – Notes from the Field
- CTP Wilco van Bragt Citrix Federated Authentication Service (FAS) Tips and Tricks
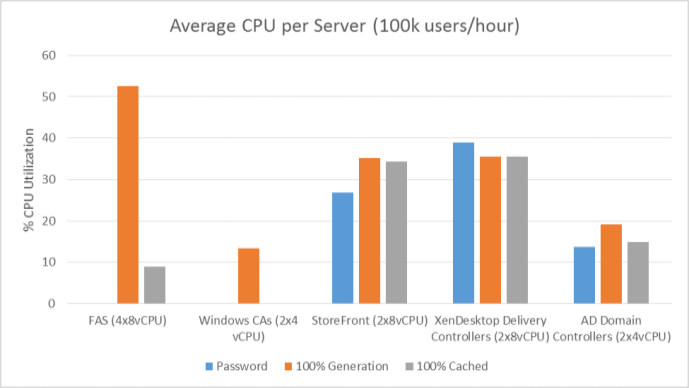
From Citrix CTX225721 Federated Authentication Service High Availability and Scalability: you can build multiple FAS servers. Enter all FAS server FQDNs in the Group Policy. StoreFront will then use a hashing algorithm on the username to select a FAS server.
- If you have less than 10K users, one FAS server with 4 vCPUs (2.5Ghz) should be sufficient.
- You will require a minimum of one FAS server (with 8 vCPUs) per 25,000 users if all users expect to be able to logon under cold start conditions (no keys or certificates cached) within 60-90 minutes.
- A single FAS server can handle greater than 50K users under warm start conditions (keys and certificates pre-cached)
- One reserve FAS server for every four FAS servers for “Day 1” cold start (Users get new keys/certificates) & disaster recovery scenarios
- Split the FAS Certificate Authority from Certificate Authority that performs other tasks for both security and scalability purposes.
Michael Shuster explains the Group Policy configuration for FAS in multiple datacenters at HowTo: Active-Active Multi-Datacenter Citrix FAS.
Also see the Citrix Federated Authentication Service Scalability whitepaper.
Federated Authentication Service Versions
The most recent Federated Authentication Service Current Release is version 2411.
- Download FAS 2411.
For LTSR versions of Citrix Virtual Apps and Desktops (CVAD) and StoreFront, install the version of FAS that comes with the CVAD LTSR version.
- FAS LTSR version 2402 CU2 is included in the Citrix Virtual Apps and Desktops 2402 LTSR CU2 ISO.
- FAS LTSR version 2203 CU6 is included in the Citrix Virtual Apps and Desktops 7 2203 LTSR CU6 ISO.
- FAS LTSR version 1912 CU9 is included in the Citrix Virtual Apps and Desktops 7 1912 LTSR CU9 ISO.
Install/Upgrade Federated Authentication Service
The service should be installed on a secure, standalone server that does not have any other Citrix components installed. The FAS server stores user authentication keys, and thus security is paramount.
- On the Federated Authentication Service server, go to the Citrix Virtual Apps and Desktops, or XenDesktop 7.9, or newer ISO, and run AutoSelect.exe. Or you can download the standalone installer and run that.
- In the lower half of the window, click Federated Authentication Service.
- In the Licensing Agreement page, select I have read, understand, and accept the terms of the license agreement, and click Next.
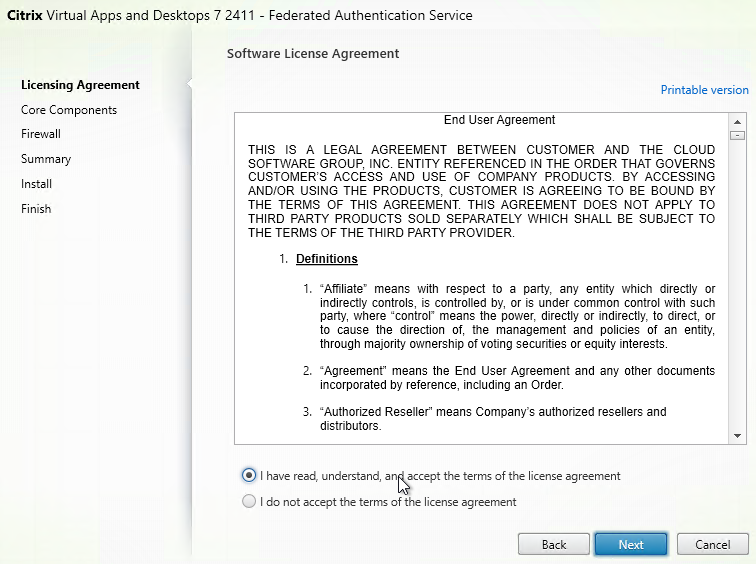
- In the Core Components page, click Next.
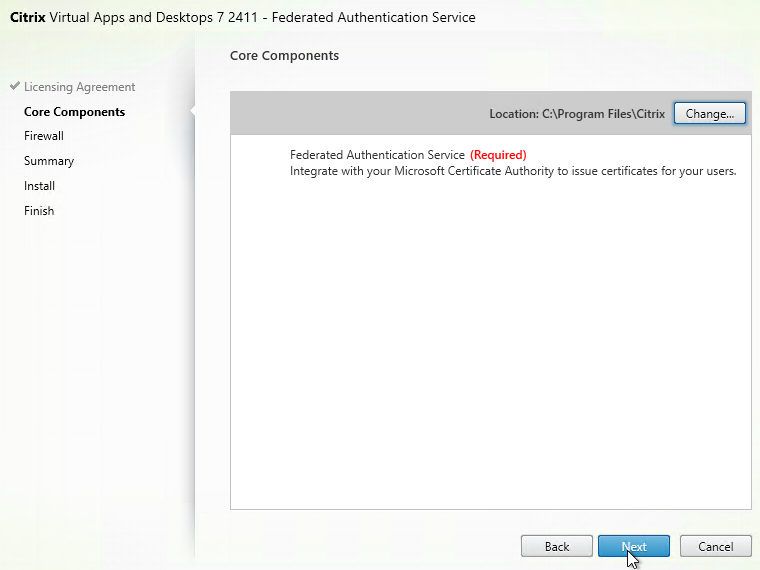
- In the Firewall page, click Next.
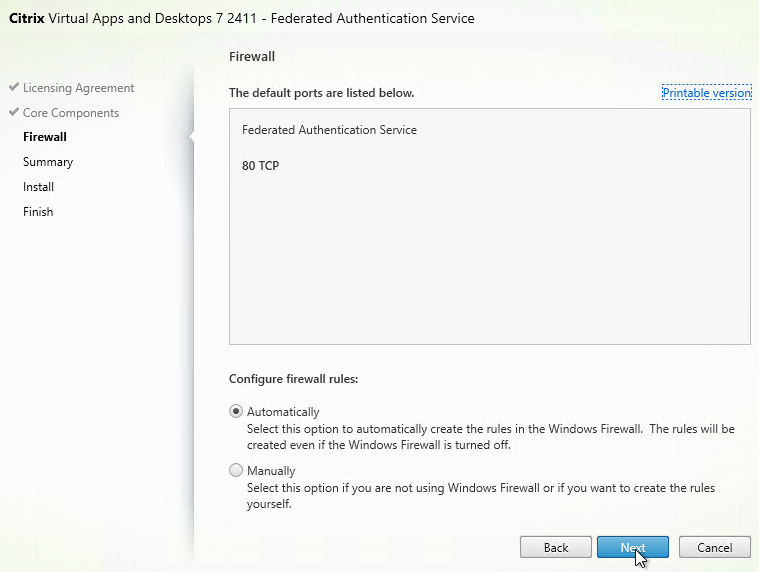
- In the Summary page, click Install.
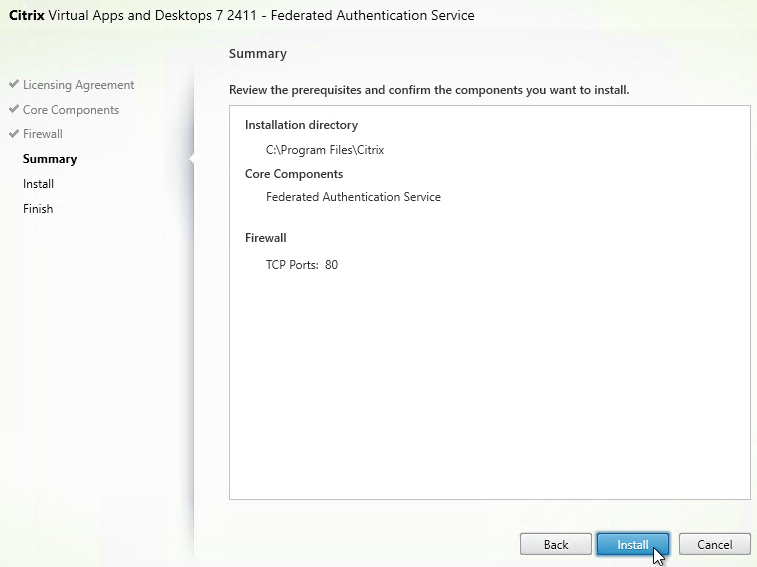
- The installer will probably ask for a restart.
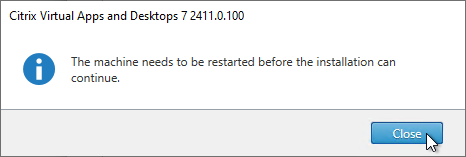
- After the reboot, and after logging in again, you might see a Locate ‘Citrix Virtual Apps and Desktops 7’ installation media window. Don’t click anything yet.
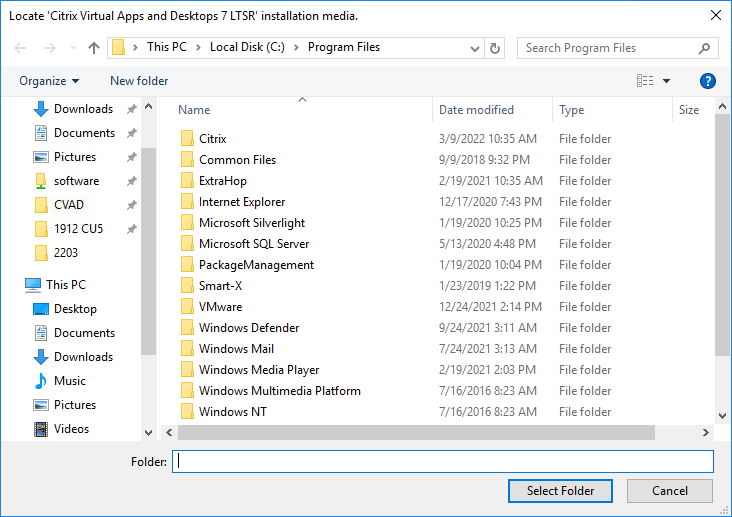
- Go to the Citrix_Virtual_Apps_and_Desktops_7_2411.iso file and mount it.
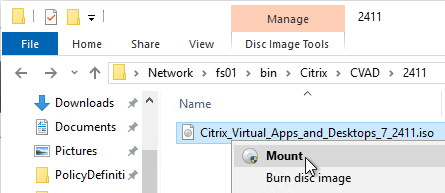
- Go back to the Locate ‘Citrix Virtual Apps and Desktops 7’ installation media window.
- On the left, expand This PC, and click the DVD Drive.
- Click Select Folder.
- After the reboot, and after logging in again, you might see a Locate ‘Citrix Virtual Apps and Desktops 7’ installation media window. Don’t click anything yet.
- Click Finish.
FAS Group Policy
Configure a Group Policy that instructs StoreFront servers and VDAs on how to locate the FAS servers.
- On the Federated Authentication Service server, browse to C:\Program Files\Citrix\Federated Authentication Service\PolicyDefinitions. Copy the files and folder.
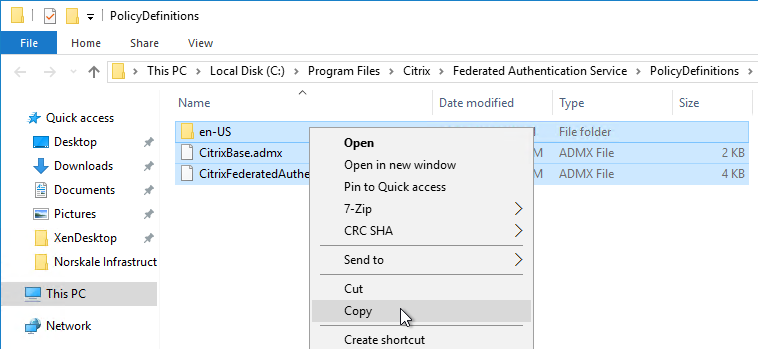
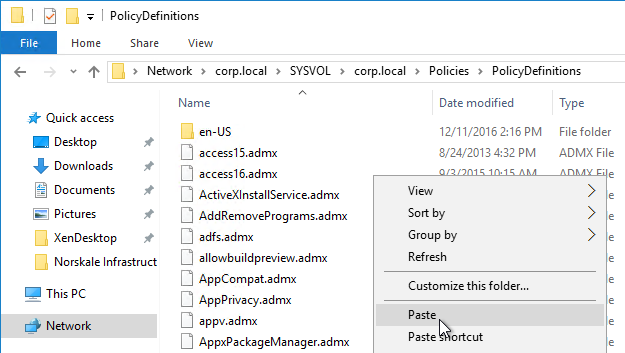
- Go to \\domain.com\SYSVOL\domain.com\Policies\PolicyDefinitions and paste the files and folder. If PolicyDefinitions doesn’t exist in SYSVOL, then copy them to C:\Windows\PolicyDefinitions instead.
- Edit a GPO that applies to all StoreFront servers, all Federated Authentication Service servers, and all VDAs.
- Navigate to Computer Configuration > Policies > Administrative Templates > Citrix Components > Authentication.
- Edit the setting Federated Authentication Service.
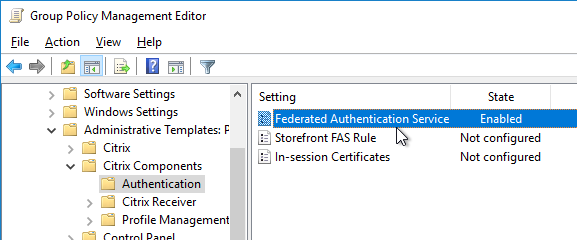
- Enable the setting and click Show.
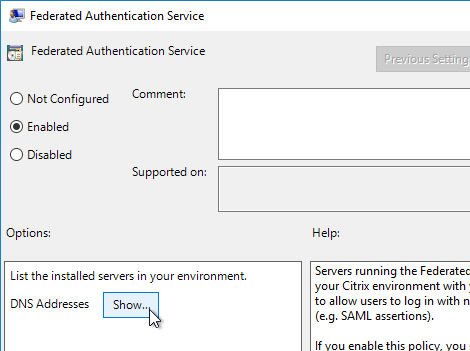
- Enter the FQDN of the Federated Authentication Service server. You can add more than one Federated Authentication Service server.
- Michael Shuster explains the Group Policy configuration for FAS in multiple datacenters at HowTo: Active-Active Multi-Datacenter Citrix FAS.
- Michael Shuster explains the Group Policy configuration for FAS in multiple datacenters at HowTo: Active-Active Multi-Datacenter Citrix FAS.
- Click OK twice.
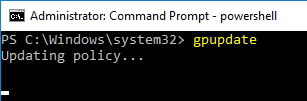
- On the Federated Authentication Service server, and VDAs, run gpupdate.
- On the FAS server, and on VDAs, look in the registry at HKLM\Software\Policies\Citrix\Authentication\UserCredentialService\Addresses. Make sure this key and value exists. The number one cause why FAS doesn’t work is because this key is missing from VDAs. The FAS Address GPO must apply to VDAs too.
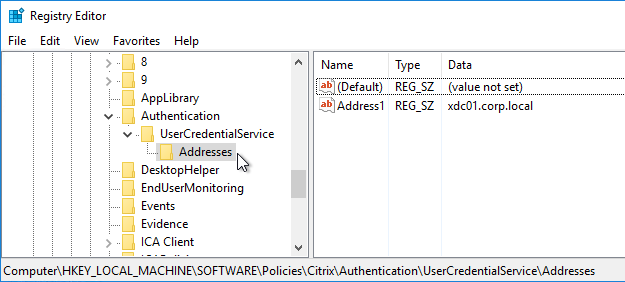
- If the VDAs and Users are in different domains, see CTX220497 Users from one AD Domain not able to get FAS user certificates from another trusted domain: add the Citrix StoreFront Servers, FAS server and VDA servers to the Windows Authorization Access Group in the users’ domain. Also see Deployment Guide: Multi-Domain FAS Architecture at Citrix Tech Zone.
-
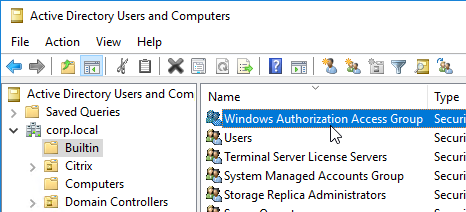
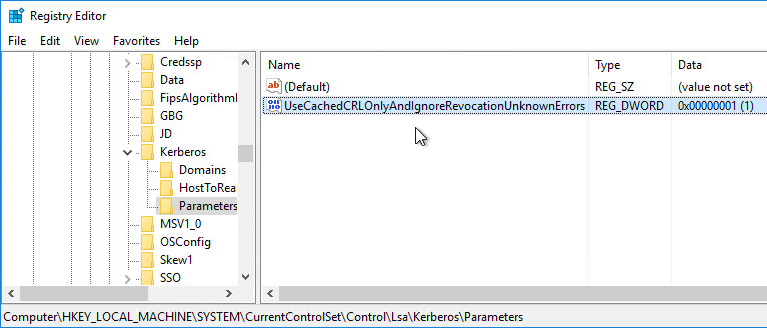
- By default, the VDAs will verify the certificates aren’t revoked by downloading the Certificate Revocation List. You can disable CRL checking by configuring HKEY_Local_Machine\System\CurrentControlSet\Control\LSA\Kerberos\Parameters\UseCachedCRLOnlyAndIgnoreRevocationUnknownErrors (DWORD) = 1 as detailed at CTX217150 Unable to login using the FAS Authentication – Getting Stuck on Please wait for local session manager.
- If your VDAs have third party credential providers (e.g., Duo), then it might interfere with FAS Single Sign-on.
- For Duo, see Can I enable other credential providers after installing Duo Authentication for Windows Logon? to whitelist the FAS credential provider, which is {81C8E4DC-B376-4D88-BCCD-BD0DD65BEE2B} CitrixMirrorCredentialProvider.
FAS 1909+ Configuration
If you prefer to script the FAS configuration, then see Citrix Blog Post Automating the Citrix Federated Authentication Service with PowerShell.
FAS 1909 and newer have a different configuration GUI than FAS 1906 and older.
Here are 1909 and newer GUI configuration instructions:
- Log into the FAS server as an Enterprise Administrator that can upload certificate templates to Active Directory.
- On the FAS server, from the Start Menu, run Citrix Federated Authentication Service as administrator. Make sure you run it elevated.
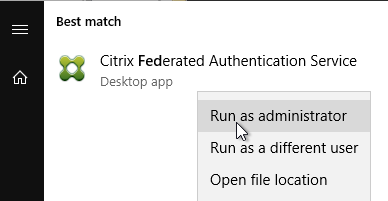
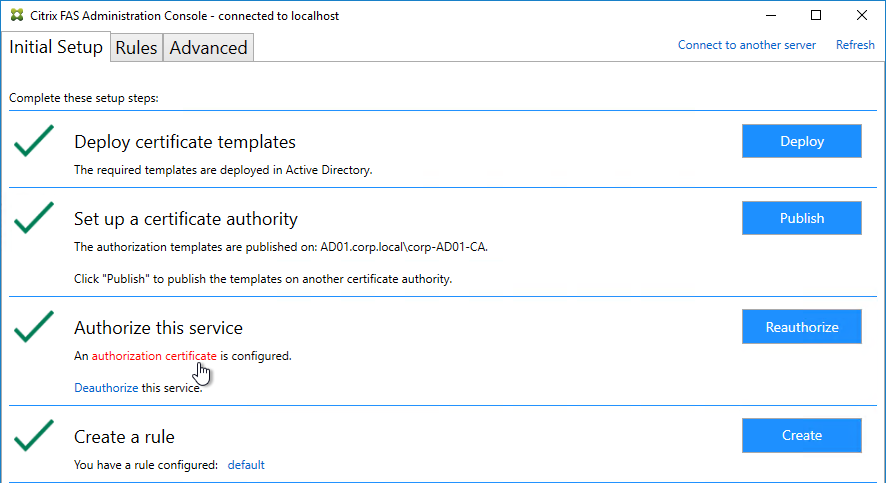
- In the tab named Initial Setup, in the row named Deploy certificate templates, click Deploy.
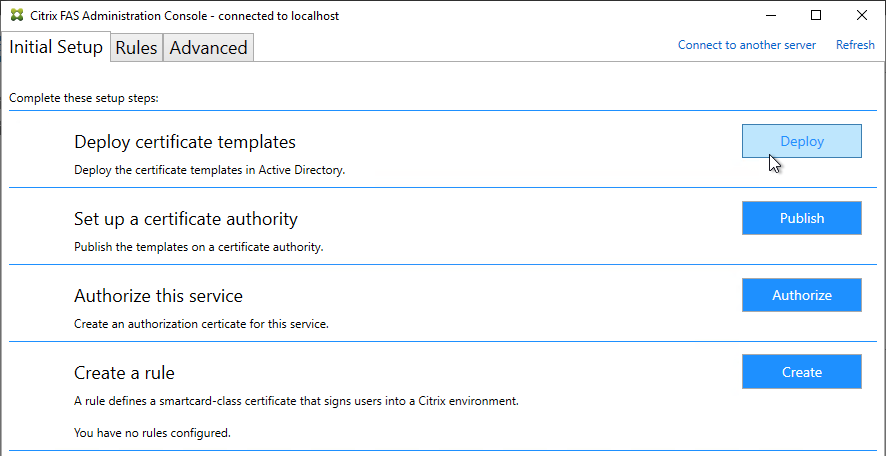
- Click OK to deploy the templates to Active Directory.
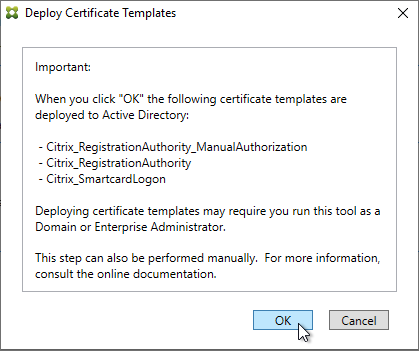
- In the row named Set up a certificate authority, click Publish.
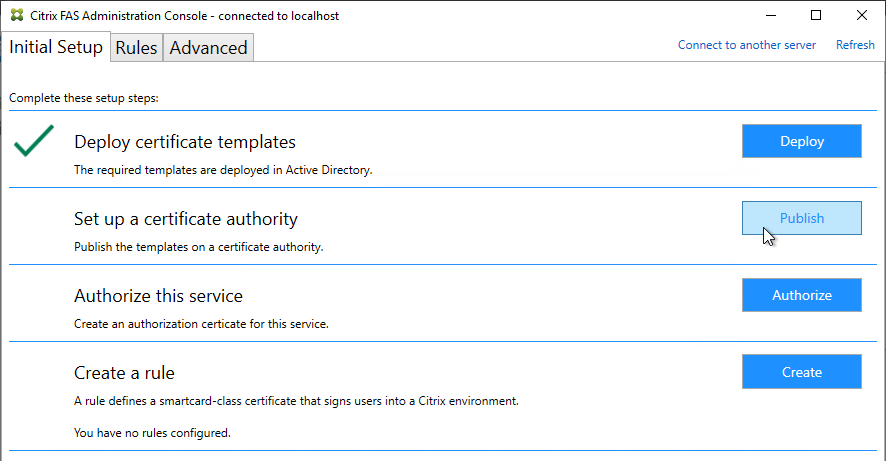
- Select an Enterprise Certificate Authority that will be issue the FAS certificates and click OK.
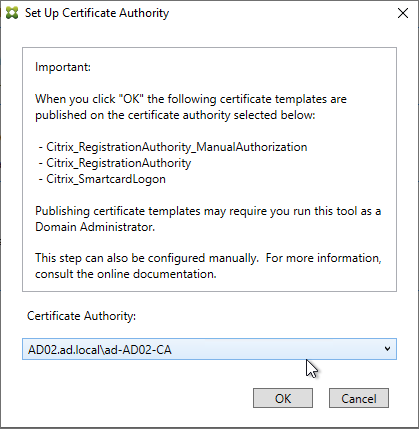
- In the row named Authorize this service, click Authorize.
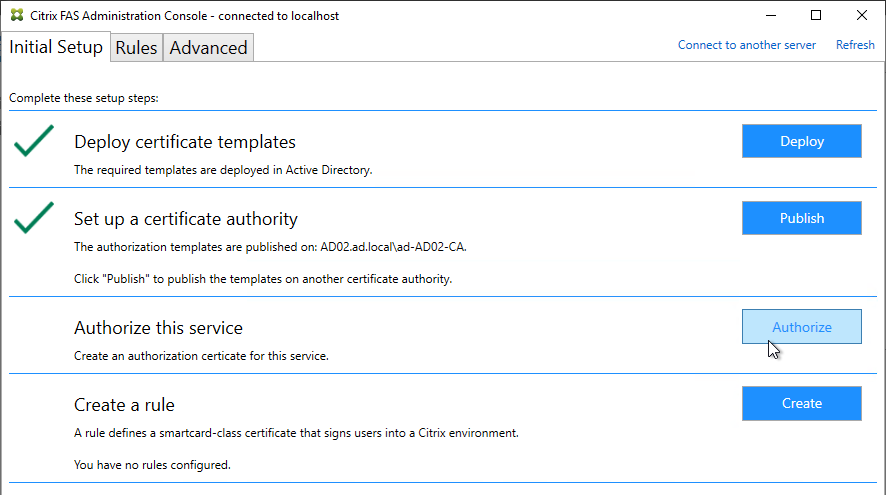
- Select a CA that will issue this FAS server a Registration Authority certificate. Later, you will need to open the Certificate Authority console on the chosen server. Click OK.
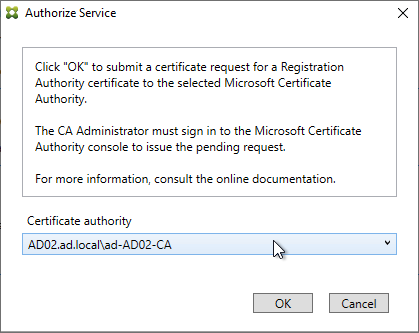
- The row named Authorize this service has a new icon indicating it is waiting on the registration authority certificate to be approved.
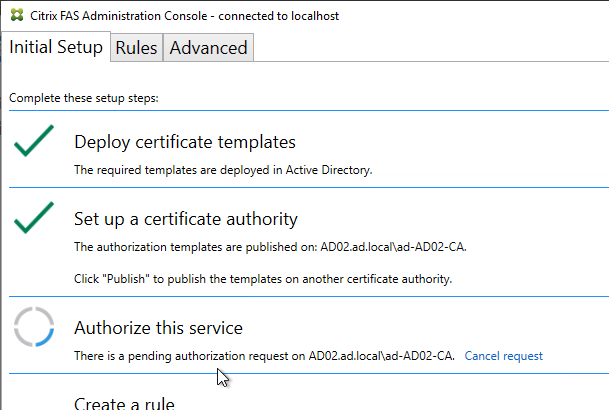
- Open the Certification Authority console and point it to the CA server. In the Pending Requests node, find the certificate request for the FAS server and Issue it.
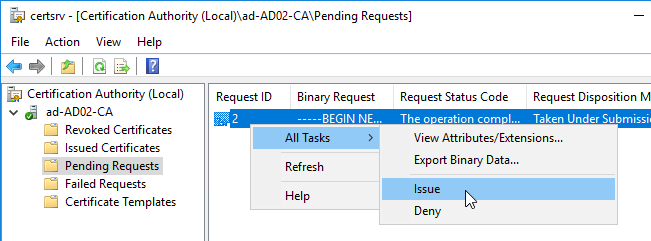
- Back in the FAS Administration Console, on the top right, click Refresh.
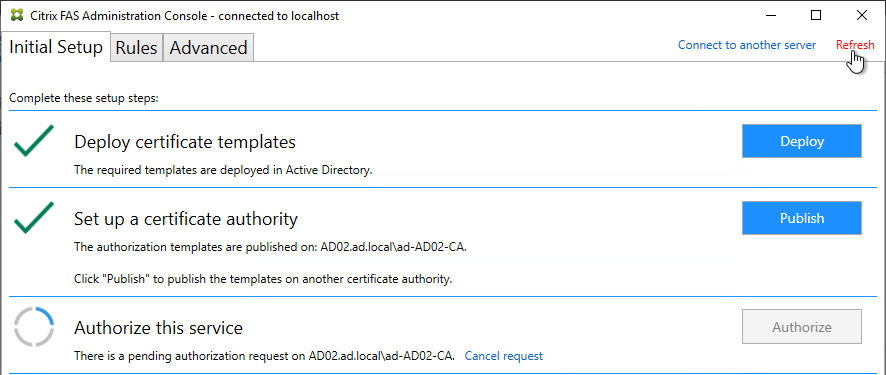
- The row named Authorize this service should now have a green check mark.
- In the row named Create a rule, click Create.
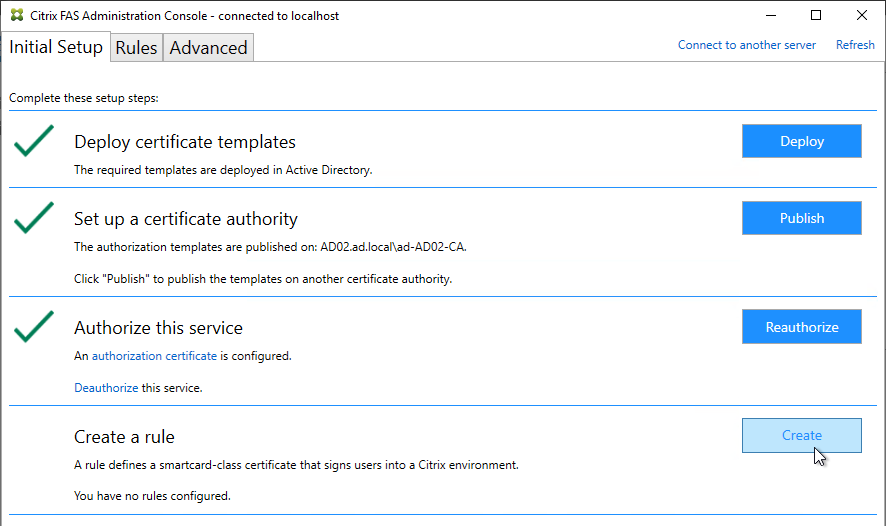
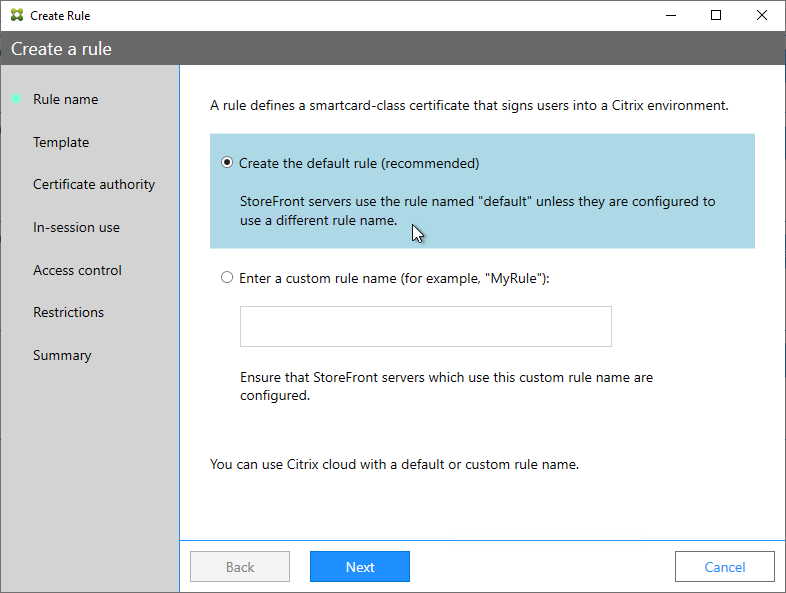
- In the Rule name page, leave it set to Create the default rule and click Next.
- In the Template page, click Next.
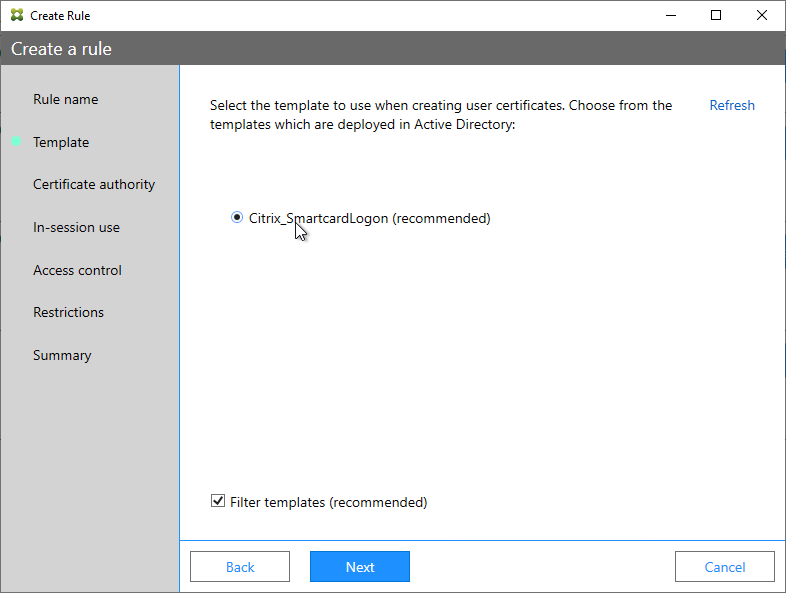
- In the Certificate authority page, select the CA that has the issuing templates configured and click Next. You can select more than one CA server.
- In the In-session use page, click Next.
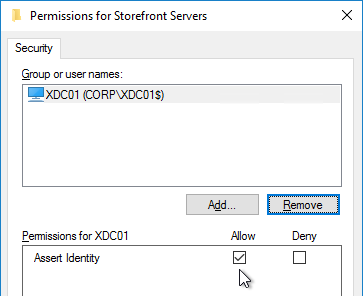
- In the Access control page, click the link to Manage StoreFront access permissions.
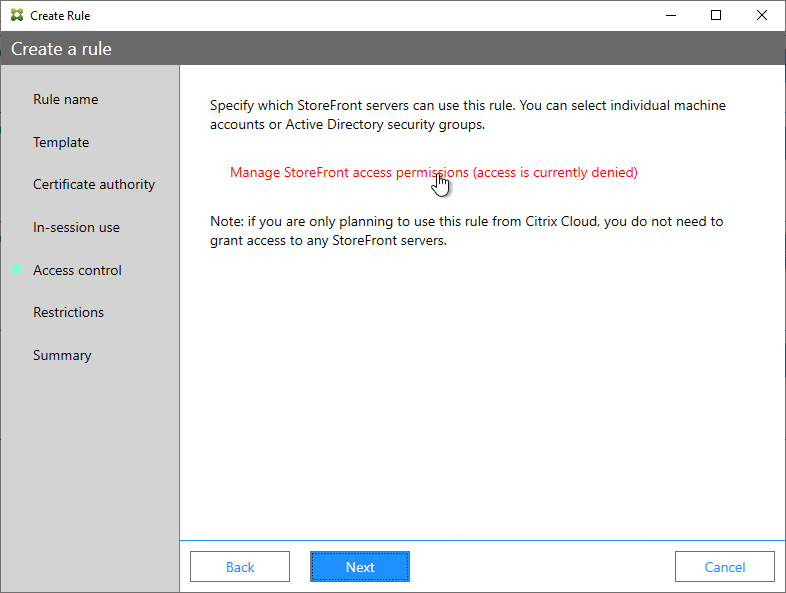
- In the Permission for StoreFront Servers page, add your StoreFront servers and give them the permission Assert Identity. Click OK.
- Back in the Create Rule wizard, click Next.
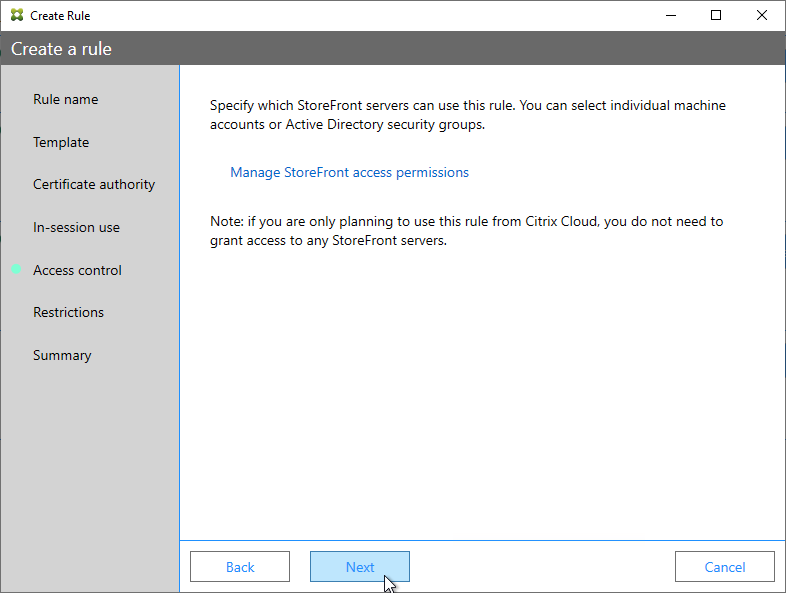
- In the Restrictions page, you can optionally reduce the VDAs that are authorized to use FAS. Click Next.
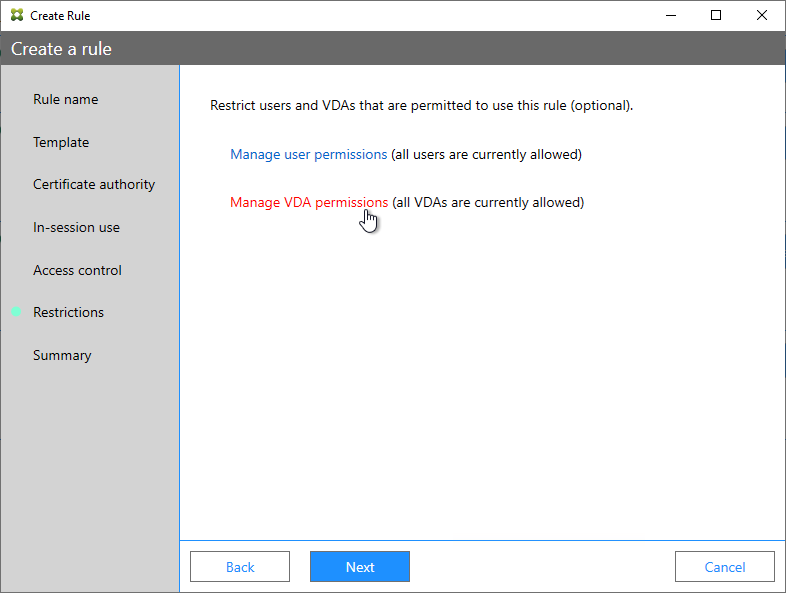
- In the Summary page, click Create.
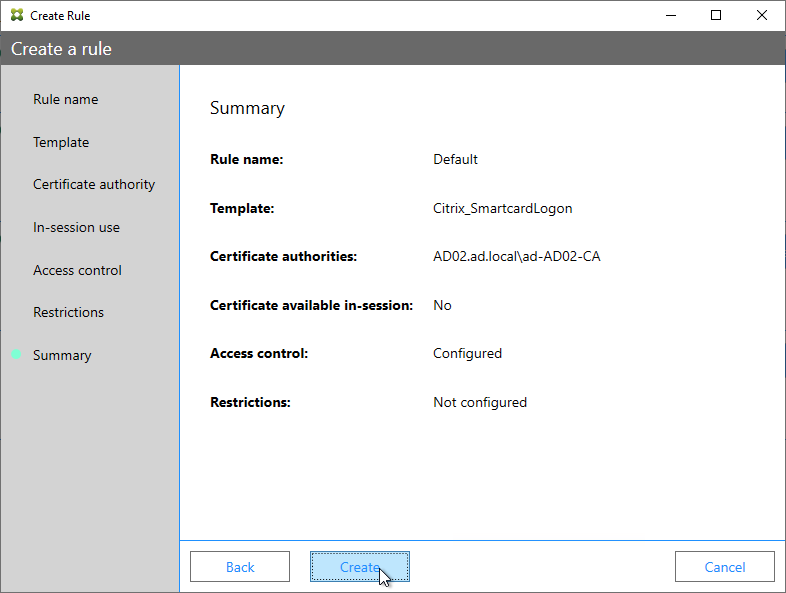
- The FAS Registration Authority certificate expires in two years. You’ll need to manually renew the FAS Registration Authority certificate before it expires. Put a notification on your calendar. For details, see Renew registration authority certificates at Citrix Docs.
- In the row named Authorize this service, you can click the link for authorization certificate to see when it expires. Before expiration, use the Reauthorize button on the right of the same row.
- In the row named Authorize this service, you can click the link for authorization certificate to see when it expires. Before expiration, use the Reauthorize button on the right of the same row.
- Jump ahead to Certificate Templates.
FAS 1906 and older Configuration
If you prefer to script the FAS configuration, then see Citrix Blog Post Automating the Citrix Federated Authentication Service with PowerShell.
Here are GUI configuration instructions for FAS 1906 and older:
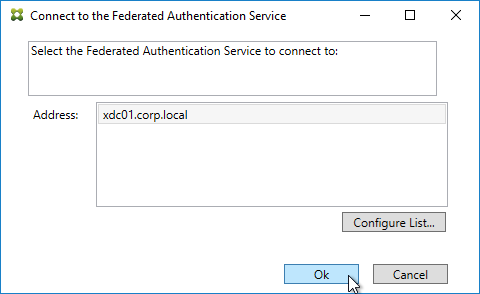
- Log into the FAS server as a Domain Administrator or Enterprise Administrator that can upload certificate templates to Active Directory.
- On the FAS server, from the Start Menu, run Citrix Federated Authentication Service as administrator. Make sure you run it elevated.

- The Federated Authentication Service FQDN should already be in the list (from group policy). Click OK.
- In Step 1: Deploy certificate templates, click Start.
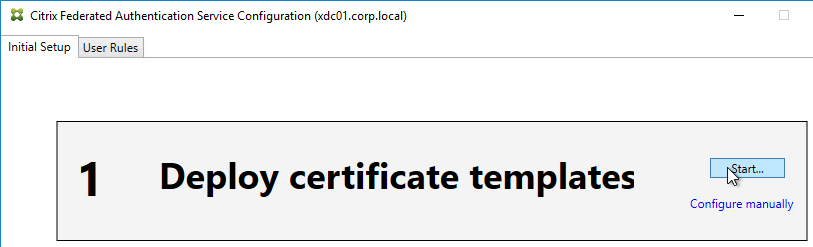
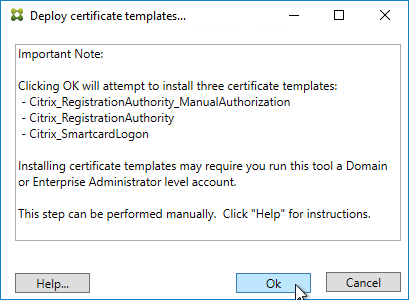
- Click OK to add certificate templates to Active Directory. Sufficient permission is required.
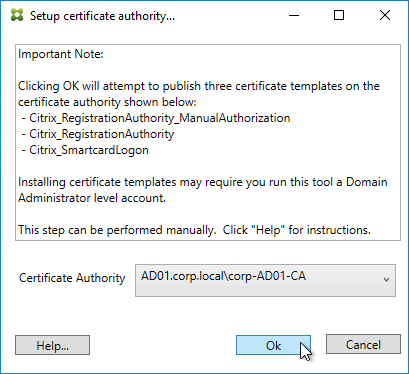
- In Step 2: Setup Certificate Authority, click Start.
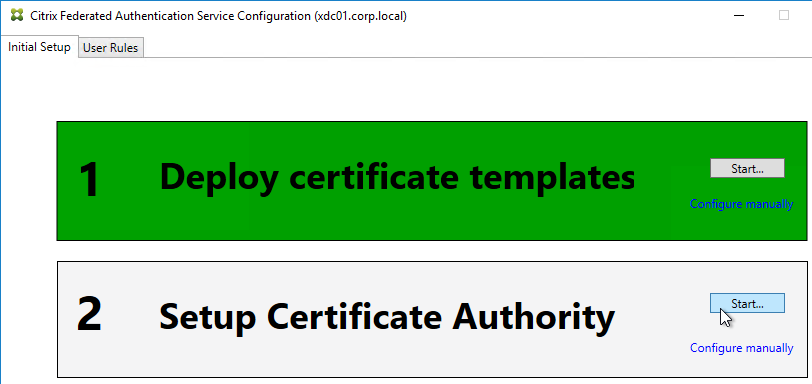
- Select a Certificate Authority to issue the certificates, and click Ok.
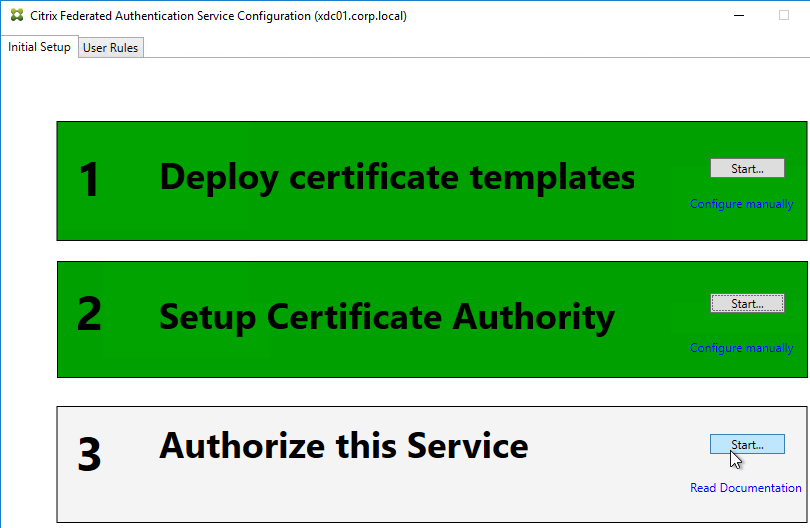
- In Step 3: Authorize this Service, click Start.
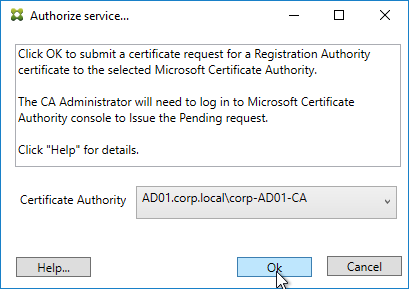
- Step 3 automatically submits an online request for the Registration Authority certificate to the CA and stores the non-exportable private key in the standard Microsoft Enhanced RSA and AES Cryptographic Provider.
- Alternatively, you can submit the certificate request manually, and store the private key in TPM or HSM as detailed at Federated Authentication Service private key protection at Citrix Docs. When running New-FasAuthorizationCertificateRequest, the -UseTPM switch is optional.
- Select the issuing Certificate Authority, and click OK.
- Authorize this Service only lets you select one Certificate Authority. If you want to load balance certificate requests against multiple Certificate Authorities, then see Set up multiple CA servers for use in FAS at Citrix Docs.
Set-FasCertificateDefinition -Name default_Definition -CertificateAuthorities @("ca1.corp.local\CA1.corp.local", "ca2.corp.local\ca2.corp.local")
- Authorize this Service only lets you select one Certificate Authority. If you want to load balance certificate requests against multiple Certificate Authorities, then see Set up multiple CA servers for use in FAS at Citrix Docs.
- Step 3 is now yellow.
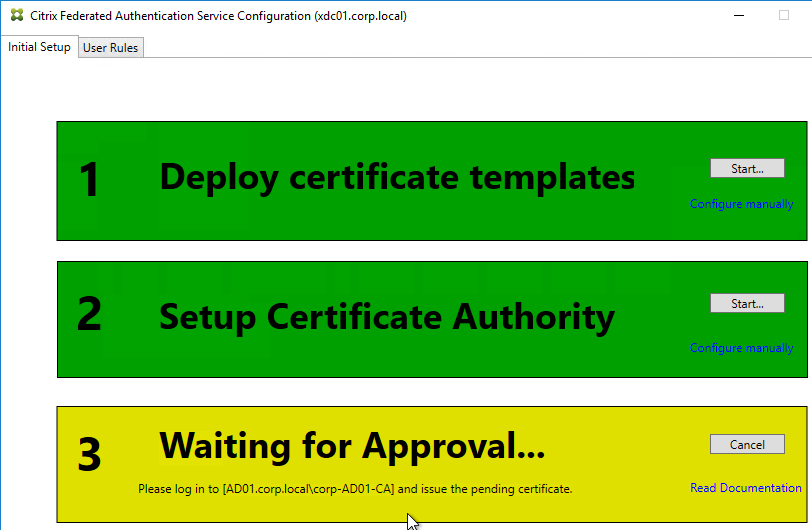
- On the Microsoft CA server, go to the Certification Authority Console > Pending Requests. Find the pending request, and Issue it.
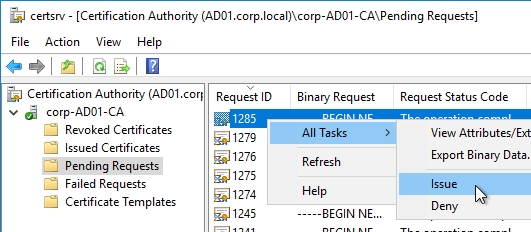
- In a minute or two, Federated Authentication Service will recognize the issued certificate and Step 3 will turn green.
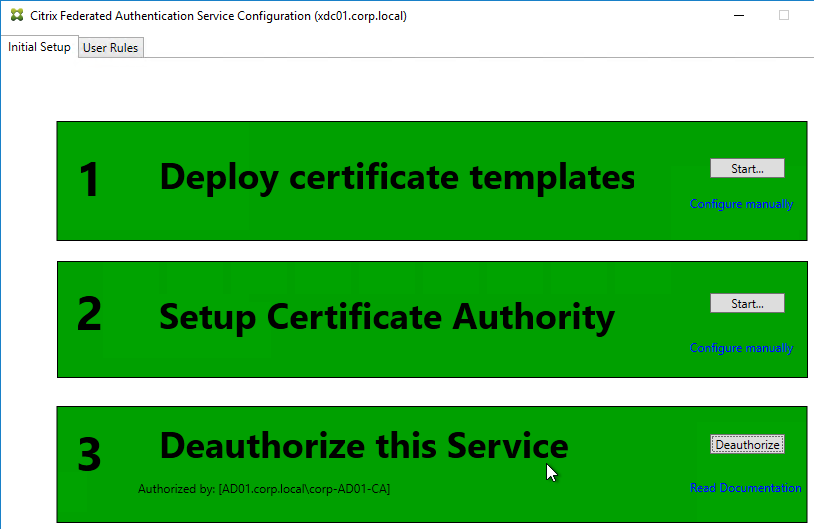
- After FAS authorization with the CA, in the FAS Configuration tool, switch to the User Rules tab.
- Use the Certificate Authority drop-down to select the issuing Certificate Authority.
- Use the Certificate Template drop-down to select the Citrix_SmartcardLogon template.
- Click Edit next to List of StoreFront servers that can use this rule.
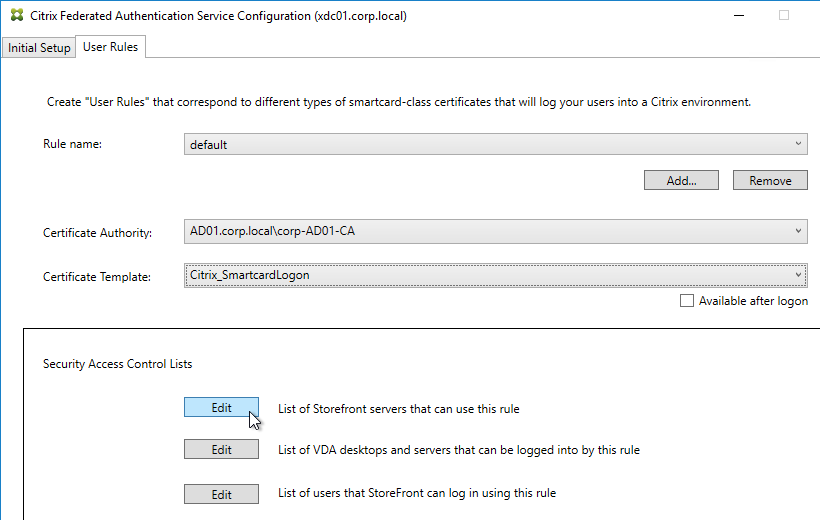
- Remove Domain Computers from the top half, and instead add your StoreFront servers. You could add an Active Directory security group instead of individual StoreFront servers.
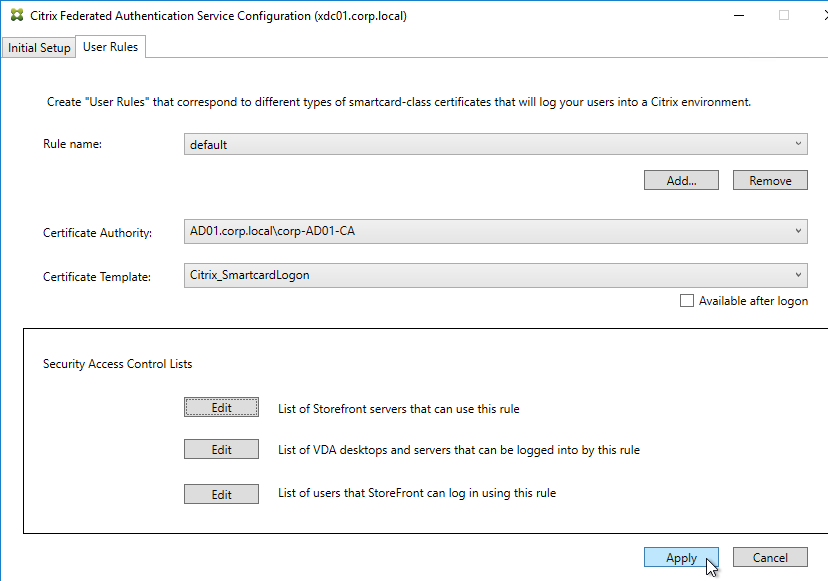
- On the bottom half, make sure Assert Identity is Allowed. Click OK.
- By default, all users and all VDAs are allowed. You can click the other two Edit boxes to change this.
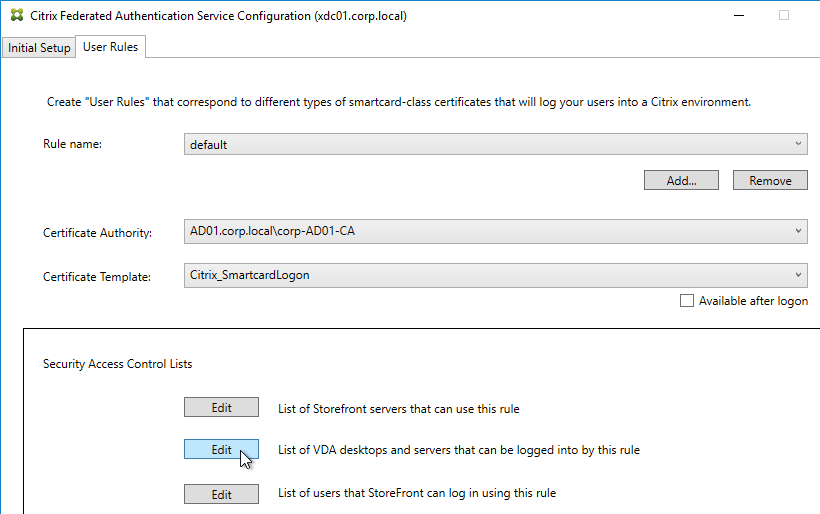
- When done, click Apply.
- Click OK when you see Rule updated successfully.
- The FAS Registration Authority certificate expires in two years. You’ll need to manually renew the FAS Registration Authority certificate before it expires. Put a notification on your calendar. For details, see Renew registration authority certificates at Citrix Docs.
- To see the expiration date of the authorization certificate, run the following PowerShell command after running
add-pssnapin Citrix.Authentication.FederatedAuthenticationService.V1:Get-FasAuthorizationCertificate -FullCertInfo -address myFASServer
- To see the expiration date of the authorization certificate, run the following PowerShell command after running
Certificate Templates
The deployed FAS Certificate Templates from older versions of FAS have Autoenroll enabled. Newer versions of FAS (e.g., 2203) no longer have Autoenroll enabled.
- Open the Certificate Templates console. One option is to open the Certification Authority console, right-click Certificate Templates, and then click Manage.
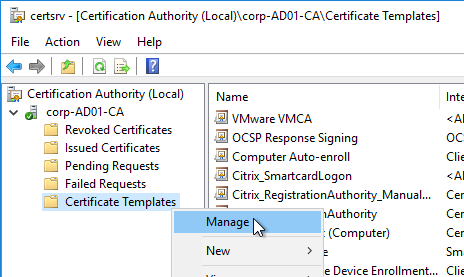
- There should be three templates with names starting with Citrix_. Open the properties on each one.
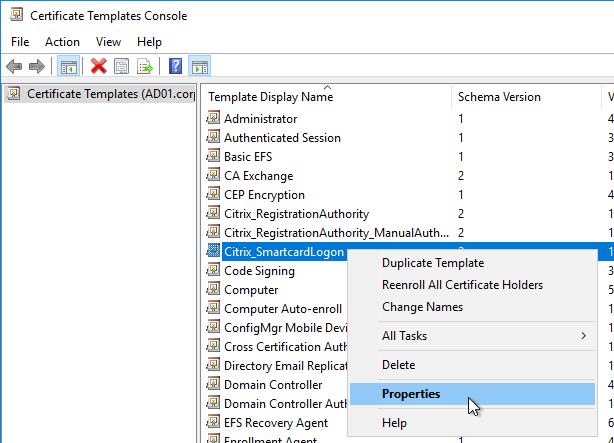
- On the Security tab, highlight each group assigned to the template.
- On the bottom half, uncheck the box in the Autoenroll row but leave Enroll checked. Perform this step for every group assigned to this template. Then click OK.
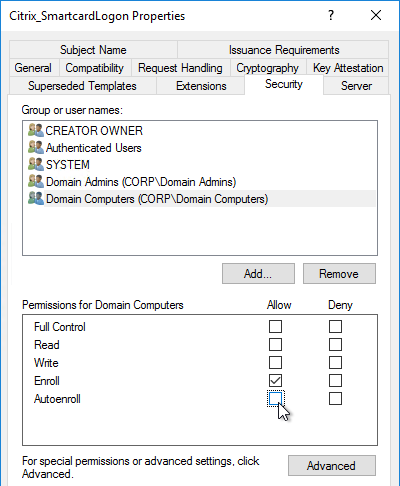
- Repeat disabling autoenroll for the other two templates.
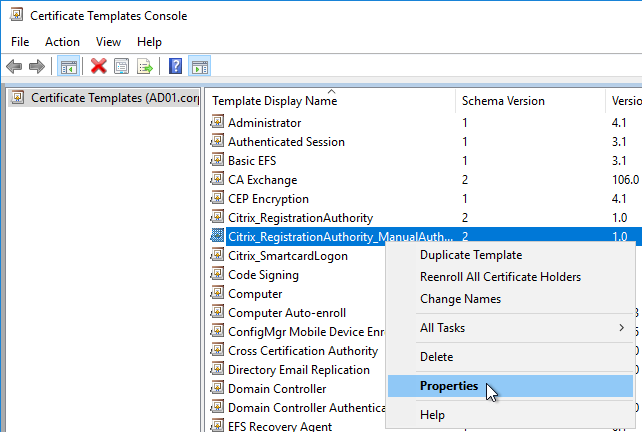
The Registration Authority certificate templates are permitted to all Domain Computers. You might want to change that.
- Open the Properties of one of the Citrix_RegistrationAuthority certificate templates.
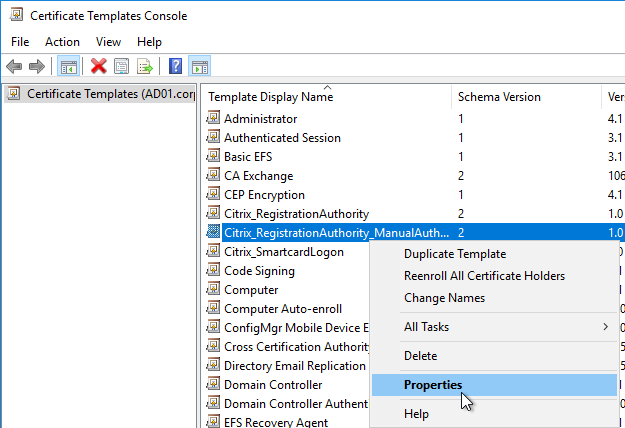
- On the Security tab, remove Domain Computers.
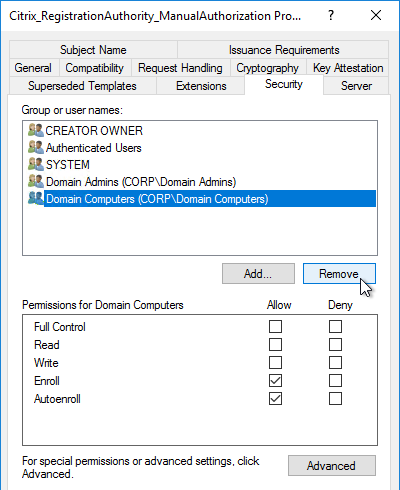
- Add your FAS servers and enable the Enroll permission.
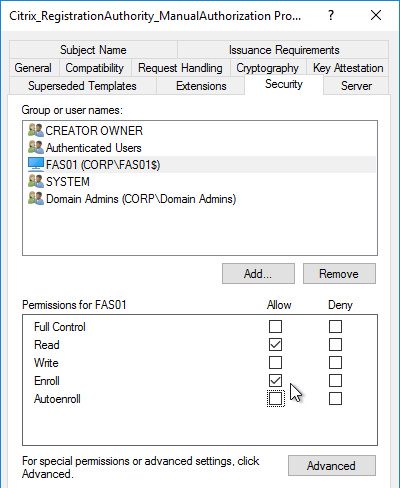
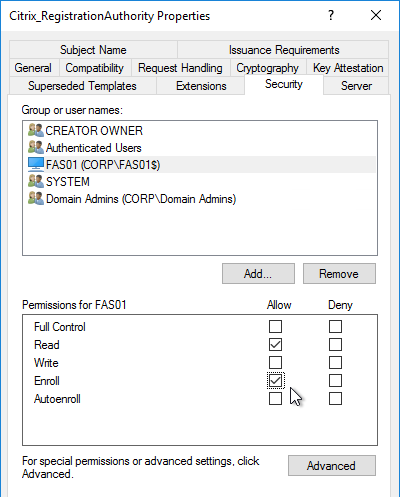
- Repeat for the other Registration Authority certificate.
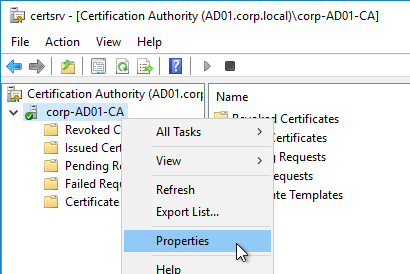
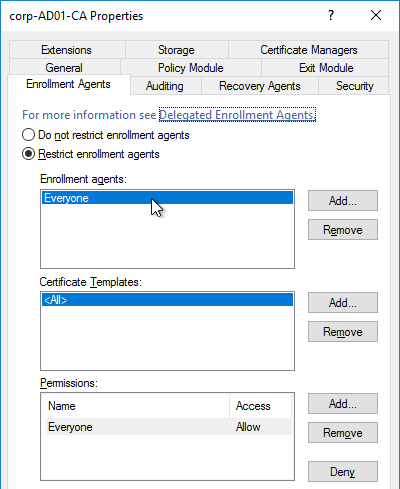
To further restrict who can be issued certificates, go to your Certificate Authority’s Properties and use the Enrollment Agents tab to restrict enrollment agents.
StoreFront Configuration
Once FAS is enabled on a StoreFront store, it applies to all connections through that store, including password-based authentications. One option is to create a new store just for FAS users.
- Check the registry at at HKLM\Software\Policies\Citrix\Authentication\UserCredentialService\Addresses to confirm that the group policy with FAS addresses has been applied to the StoreFront servers.
- On the StoreFront 3.6 or newer server, run the following elevated PowerShell command:
& "$Env:PROGRAMFILES\Citrix\Receiver StoreFront\Scripts\ImportModules.ps1"
- Run the following commands. Adjust the store name as required.
$StoreVirtualPath = "/Citrix/Store" $store = Get-STFStoreService -VirtualPath $StoreVirtualPath $auth = Get-STFAuthenticationService -StoreService $store Set-STFClaimsFactoryNames -AuthenticationService $auth -ClaimsFactoryName "FASClaimsFactory" Set-STFStoreLaunchOptions -StoreService $store -VdaLogonDataProvider "FASLogonDataProvider"
- If you have multiple StoreFront servers, Propagate Changes.
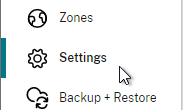
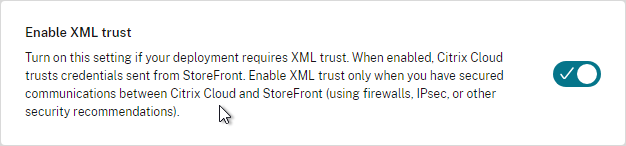
- In Web Studio (CVAD 2212 and newer), go to Settings and Enable XML Trust.
- Or on a Citrix Delivery Controller, run the following PowerShell command:
Set-BrokerSite -TrustRequestsSentToTheXmlServicePort $true
- Or on a Citrix Delivery Controller, run the following PowerShell command:
If you ever need to disable FAS on StoreFront, run the following commands. Adjust the store name as required.
$StoreVirtualPath = "/Citrix/Store" $store = Get-STFStoreService -VirtualPath $StoreVirtualPath $auth = Get-STFAuthenticationService -StoreService $store Set-STFClaimsFactoryNames -AuthenticationService $auth -ClaimsFactoryName "standardClaimsFactory" Set-STFStoreLaunchOptions -StoreService $store -VdaLogonDataProvider ""
SAML Configuration
SAML Flow
SAML flows like this:
- (Optional) User goes to the web application aka Service Provider (e.g. Citrix Gateway).
- The Service Provider (SP) redirects the user’s browser to the Identity Provider’s (IdP) SAML Single Sign-on (SSO) URL and includes an authentication request in the Redirect. The IdP SSO URL might be different for each Service Provider.
- The Authentication Request from the Service Provider includes a Service Provider Entity ID. The IdP matches the SP Entity ID with an entry in its database so it knows which SP is making the authentication request. The Entity ID must match on both the SP and the IdP.
- If the Authentication Request is signed by the Service Provider’s certificate private key, then the IdP will verify the signature using the Service Provider’s certificate public key. In this scenario, the Service Provider’s certificate (without private key) must be loaded into the IdP.
- The user authenticates to the IdP, typically using Multi-factor Authentication.
- If the user was redirected from the SP, then the IdP already knows which SP to authenticate with.
- If the user went directly to the IdP, then the user typically needs to click an icon representing the web application (Service Provider).
- IdP generates a SAML Assertion containing the user’s userPrincipalName or email address.
- Configure the IdP to include the user’s UPN or email address in the NameID field of the assertion. SAMAccountName won’t work with Citrix FAS.
- The SAML Assertion also includes the Service Provider’s Entity ID. The ID in the Assertion must match the ID configured on the SP.
- IdP signs the SAML Assertion using an IdP certificate private key.
- IdP has a configuration for the SP that includes a SAML Assertion Consumer Service (ACS) URL. IdP redirects the user’s browser to the SP’s ACS URL and POST’s the SAML Assertion.
- The ACS URL on Citrix Gateway ends in /cgi/samlauth
- SP uses the IdP certificate’s public key to verify the signature on the SAML Assertion.
- The IdP’s certificate (without private key) is installed on the Citrix ADC so it can verify the Assertion’s signature.
- SP extracts the user’s userPrincipalName from the Assertion and uses the UPN for Single Sign-on to StoreFront and the rest of the Citrix components.
- Note that the SP does not have access to the user’s password and thus that’s why we need Citrix FAS to generate certificates for each user.
Configure the SAML IdP
You typically start the configuration on the Identity Provider (IdP). Every IdP has unique instructions. Search Google for your IdP and Citrix ADC and you might find a IdP-specific guide. After IdP configuration, you download the IdP’s certificate and copy the IdP’s SSO URL so you can configure them on Citrix ADC.
- Azure Active Directory IdP – See the next section. Also see:
- Marius Sandbu Setting up Citrix SSO with Windows 10 and Azure AD Join
- ADFS IdP – jump to the ADFS as IdP section. Also see:
- George Spiers ADFS authentication to StoreFront using NetScaler, SAML and Citrix Federated Authentication Service
- Dennis Radstake SAML authentication for Citrix XenDesktop and XenApp.
- Citrix Blog Post ADFS v3 on Windows Server 2012 R2 with NetScaler.
Azure AD as SAML IdP
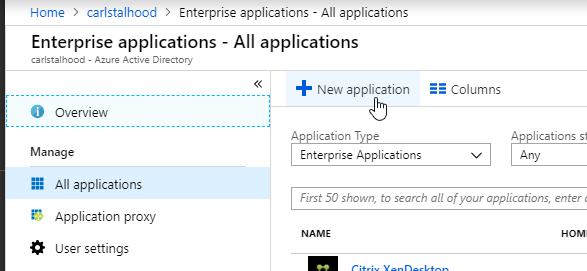
- In Azure Portal, go to Azure Active Directory.
- On the left, click Enterprise applications.
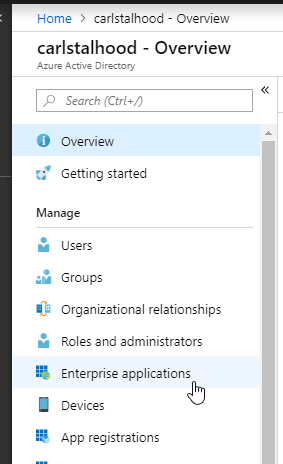
- In the new blade that appears, on the All applications page, on the right, click New application.
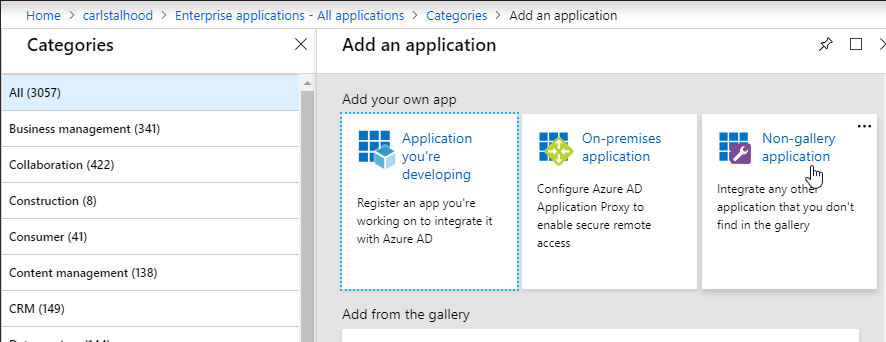
- In the All Categories view of the gallery, on the top right, click Non-gallery application.
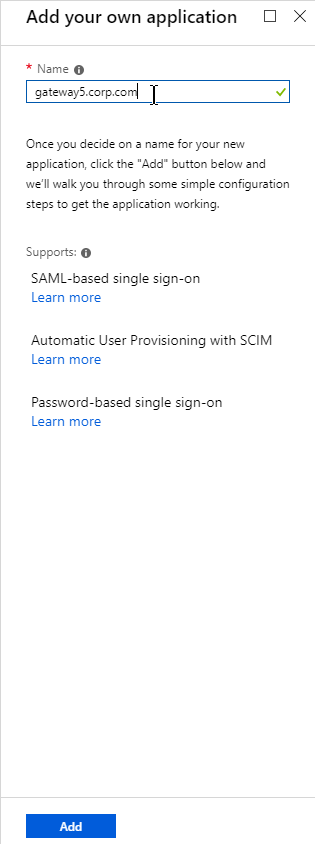
- Give the application a descriptive name. Azure AD shows this name in the myapps portal. Click Add.
- After the application is created, on the left, in the Manage section, click Single sign-on.
- On the right, click the big button for SAML.
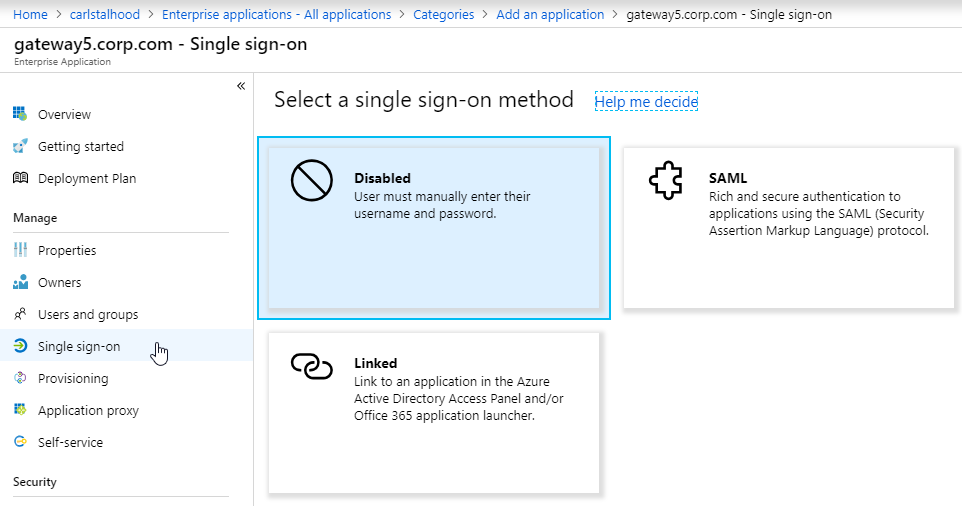
- In section 1 labelled Basic SAML Configuration, click the pencil icon.
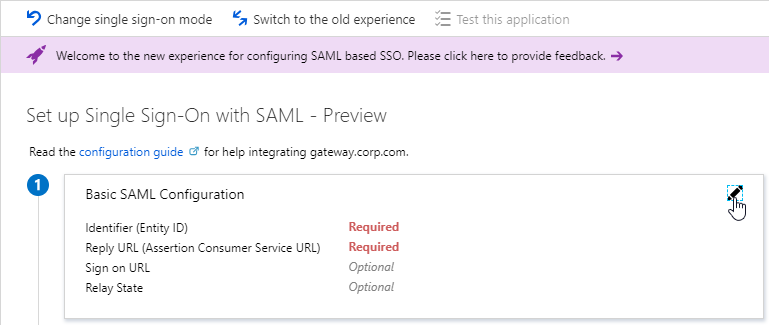
- In the Identifier (Entity ID) field, enter an identifier in URI format. Usually it matches the FQDN of the Citrix Gateway and can be entered in https://gateway.corp.com format. You’ll later need to specify the exact same Identifier on the Citrix ADC.
- In the Reply URL (Assertion Consumer Service URL) field, enter a URL similar to https://mygateway.company.com/cgi/samlauth. The path must be /cgi/samlauth. The scheme should be https. And the FQDN is your Citrix Gateway’s FQDN.
- Click Save. Then you might have to click the x on the top right to make it go away.
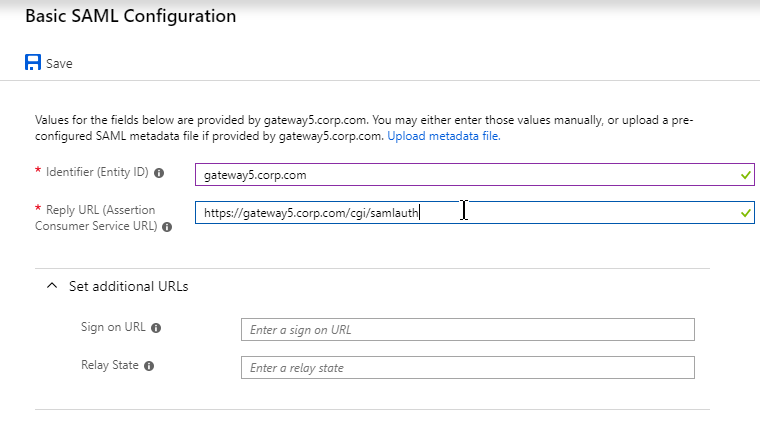
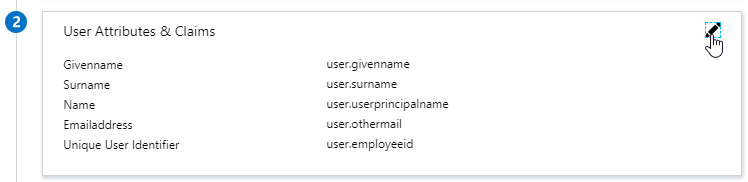
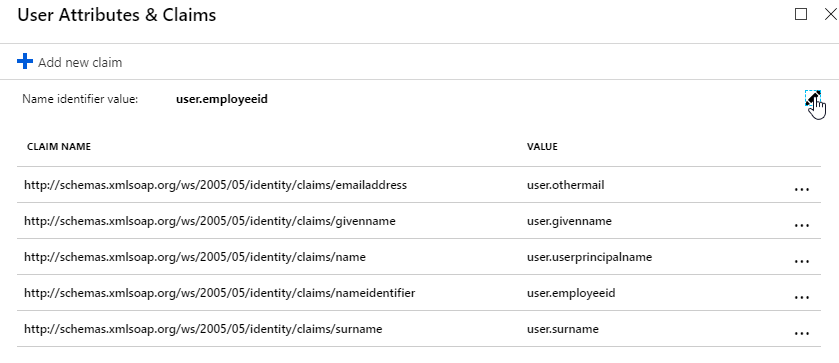
- In section 2 labelled User Attributes & Claims, notice that it defaults to sending the userprincipalname. You can click the pencil to change the attribute used for the Name identifier value. Whatever value you send will need to match the userPrincipalNames of local Active Directory accounts (aka shadow accounts).
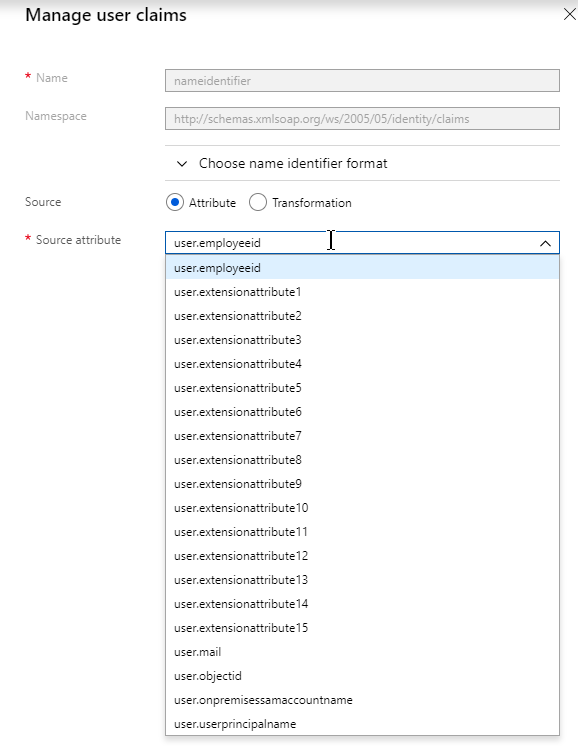
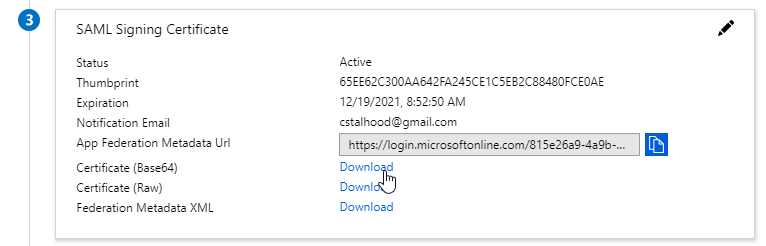
- In section 3 labelled SAML Signing Certificate, click the Download link in the Certificate (Base64) line.
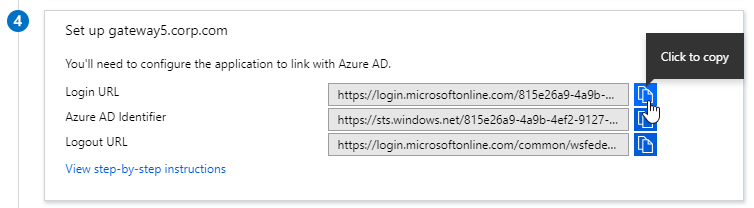
- Citrix ADC 12.1 and newer support SAML metadata so feel free to copy the App Federation Metadata Url field.
- If you are running NetScaler 12.0 or older, then you will need to copy the Login URL field from section 4 labelled Set up gateway5.corp.com
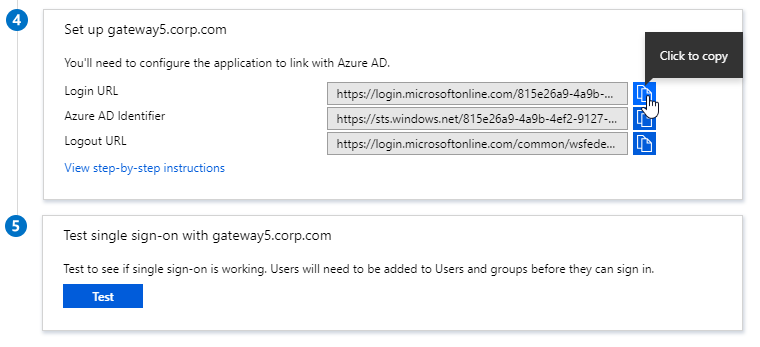
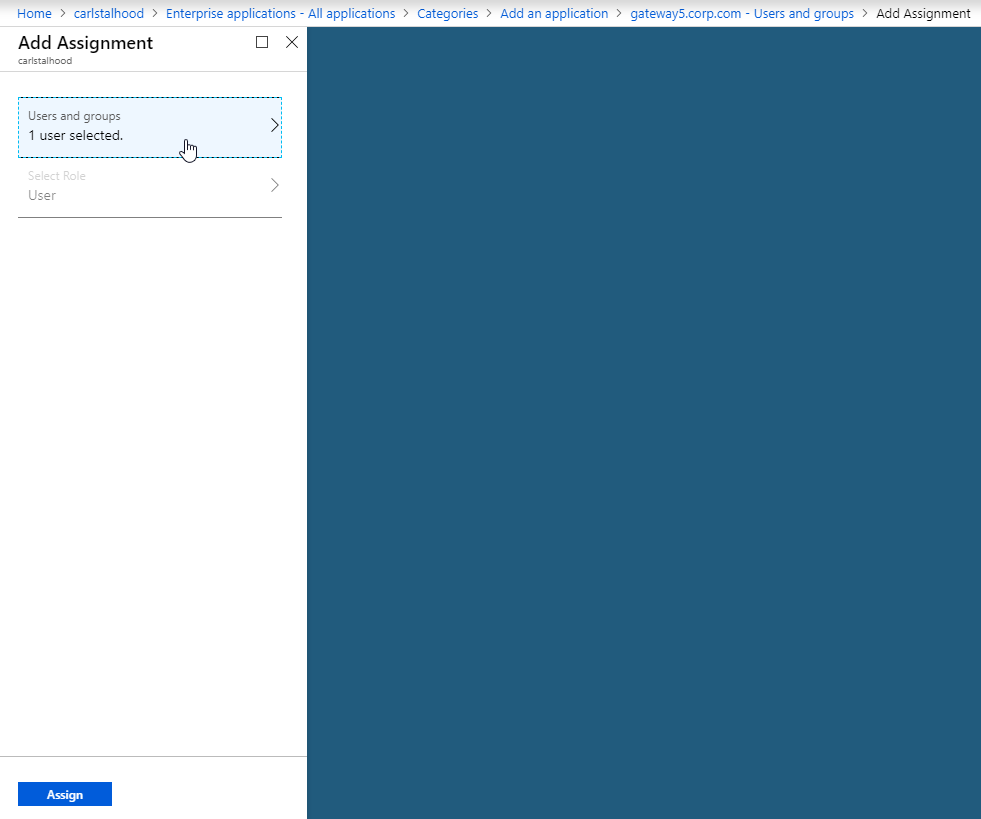
- On the left, under Manage, click Users and groups.
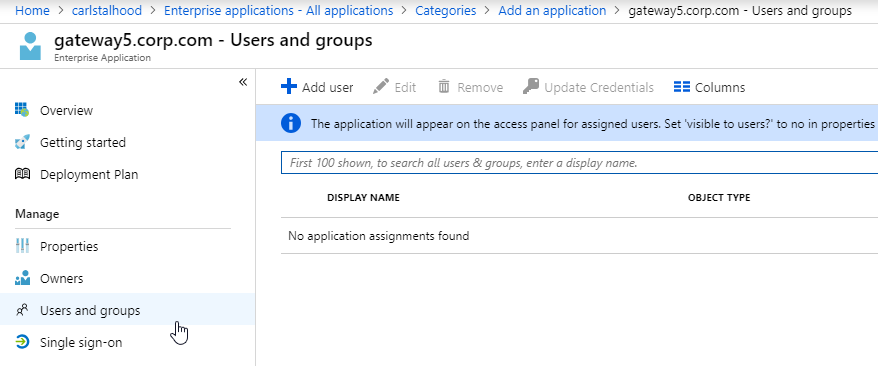
- Use the normal process to assign Azure AD users and groups to this application. Click Assign.
- Jump to the section named Citrix ADC SAML Configuration.
ADFS as SAML IdP
The screenshots in this section use ADFS as an example IdP. Your IdP will be different.
- In your SAML IdP, create a Relying Party Trust (aka service provider trust) or new Application.
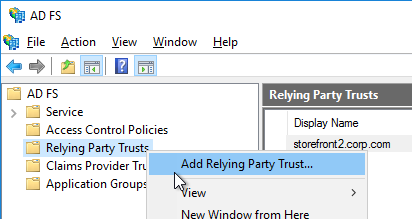
- Since we’re configuring the IdP before we configure Citrix ADC and thus don’t have access to the SP metadata, select the option to Enter data about the relying party manually.
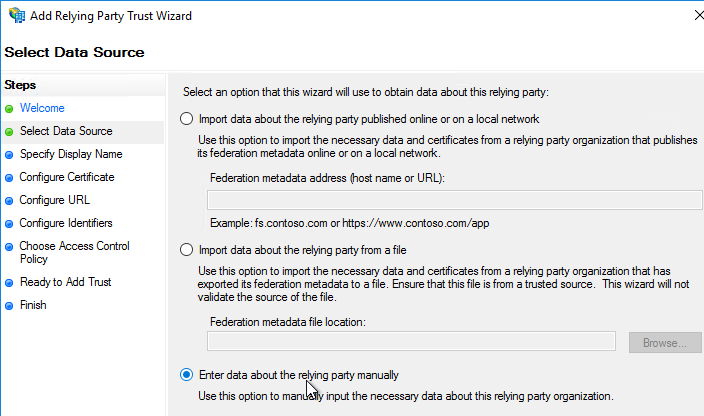
- For the Assertion Consumer Service URL (aka relying party service URL), enter the URL to your Citrix Gateway with /cgi/samlauth appended to the end (e.g. https://gateway.corp.com/cgi/samlauth)
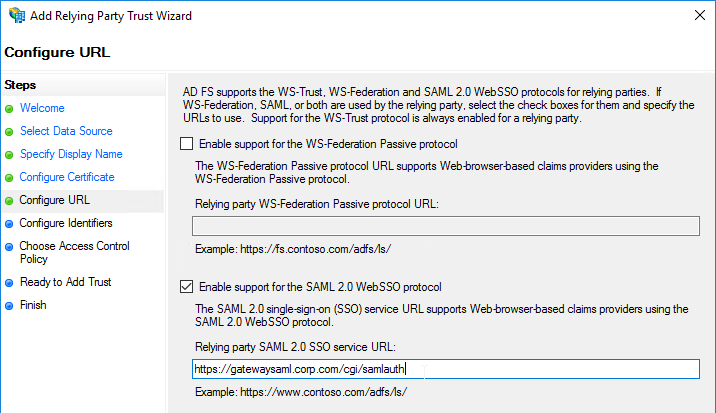
- Enter a Relying party trust identifier in URI format. You must specify the same identifier (Issuer Name) on the Citrix ADC as detailed in the next section.
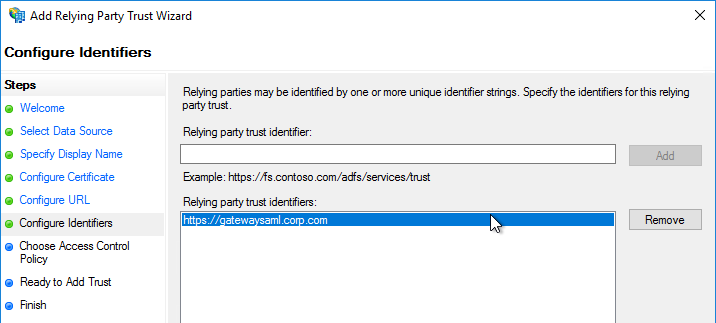
- Configure the SAML IdP to send email address or User-Principal-name as Name ID. Citrix ADC receives the Name ID and sends it to StoreFront. StoreFront will look in Active Directory for an account with userPrincipalName that matches the Name ID.
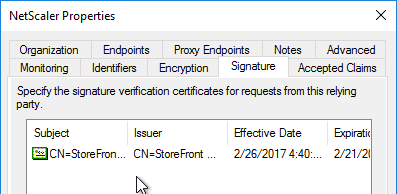
- Citrix ADC will sign the authentication requests it sends to the IdP. On the Citrix ADC, you will soon configure the Citrix ADC SAML SP signing certificate with private key that signs the authentication requests that are sent to the IdP. In your SAML IdP, import the same Citrix ADC SAML SP signing certificate but without the private key.
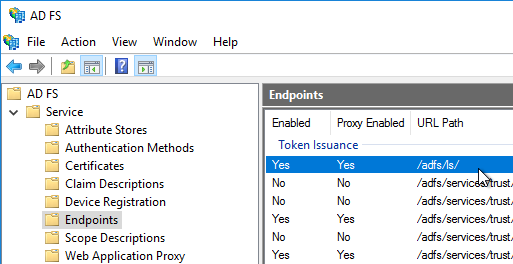
- Copy the SAML authentication URL (aka Token Issuance URL) from your SAML IdP. You’ll need to enter this same URL on your Citrix ADC later.
- Export the IdP Token-signing certificate from your SAML IdP. The IdP could be ADFS, Okta, Ping, etc.
Citrix ADC SAML Configuration
SAML Server/Action
- Instructions for Citrix ADC 13.0, Citrix ADC 12.1, NetScaler 12.0, and NetScaler 11.1 are essentially the same.
- Citrix ADC 12.1 and newer support SAML Metadata while older versions of NetScaler do not support SAML Metadata.
- NetScaler 11 is very similar, except Certificates are in a different place in the NetScaler menu tree.
- Workspace app support – If you bind a SAML Authentication Policy directly to the Gateway Virtual Server (no nFactor/AAA), then Workspace app and Gateway VPN plug-in won’t work. To support SAML with Workspace app and Gateway VPN plug-in, configure nFactor (Authentication Virtual Server with Authentication Profile) instead of directly on the Gateway Virtual Server.
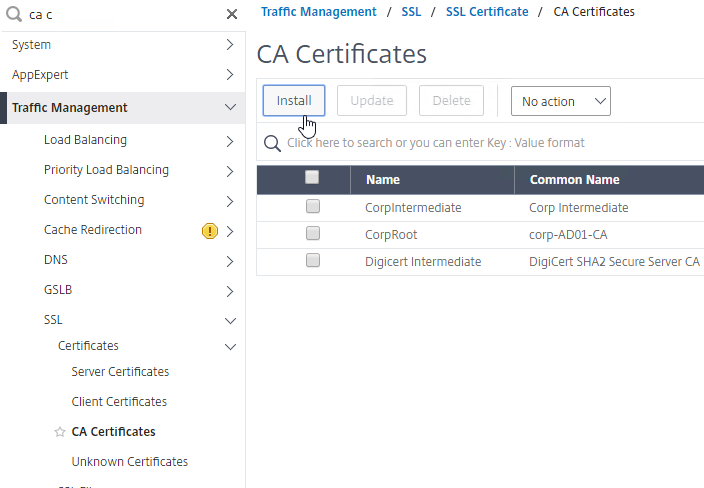
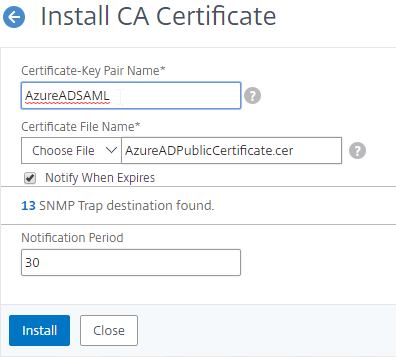
- IdP Signing Certificate – On Citrix ADC, if you are not importing IdP metadata, then manually import the IdP SAML token-signing certificate (without private key) under Traffic Management > SSL > Certificates > CA Certificates. Citrix ADC uses this certificate to verify the signature of the SAML assertion from the IdP.
Note: when you later create the SAML Action on Citrix ADC, there’s a place to add a SAML certificate. Unfortunately, the SAML Action is trying to import the wrong type of certificate since it wants the private key, which you don’t have access to. If you import the certificate here under CA Certificates, then there’s no prompt for private key.
- SAML IdP certificates are shown in the Unknown Certificates node.
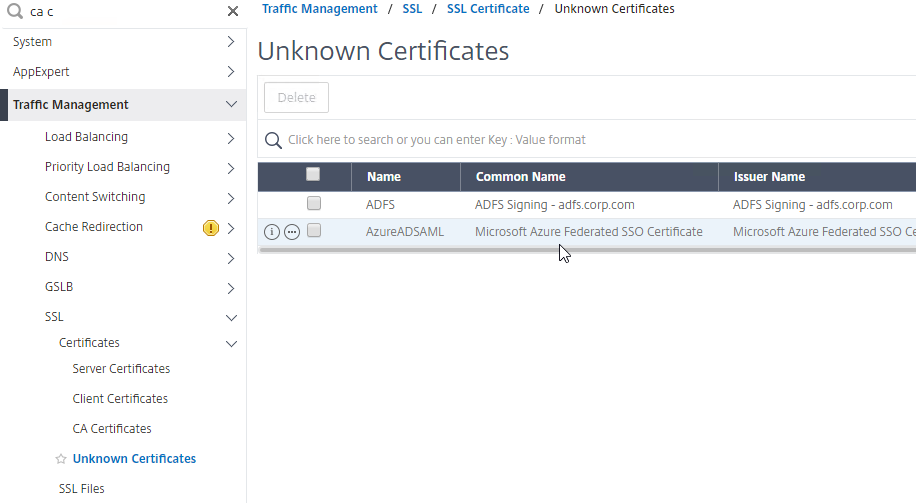
- SAML IdP certificates are shown in the Unknown Certificates node.
- If you want ADC to sign the authentication requests it sends to the IdP, then do the following:
- Move up two nodes to Server Certificates and Import or create a SP SAML signing certificate with private key. This can be the same certificate used on Citrix Gateway. Or a more common practice is to create a self-signed certificate.
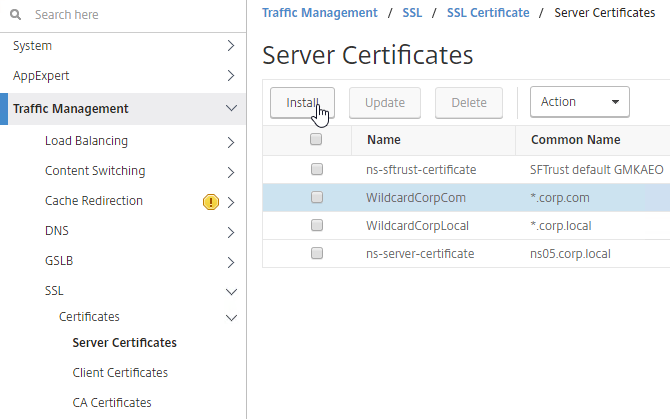
- You’ll also need to import this SAML SP signing certificate (without private key) to your SAML IdP so it can verify the SAML authentication request signature from the Citrix ADC.
- Move up two nodes to Server Certificates and Import or create a SP SAML signing certificate with private key. This can be the same certificate used on Citrix Gateway. Or a more common practice is to create a self-signed certificate.
- Go to Citrix Gateway > Policies > Authentication > SAML. The quickest way to get here is to enter SAML in the search box on top of the menu.
- On the right, switch to the tab labelled Servers, and click Add.
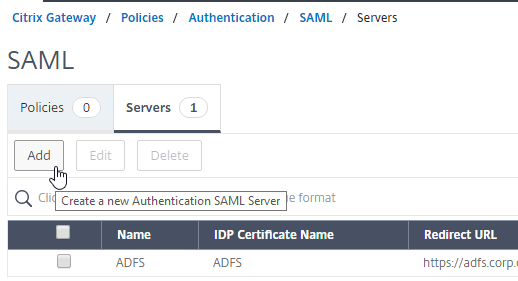
- In the Name field, give the SAML Action a name that indicates the IdP’s name.
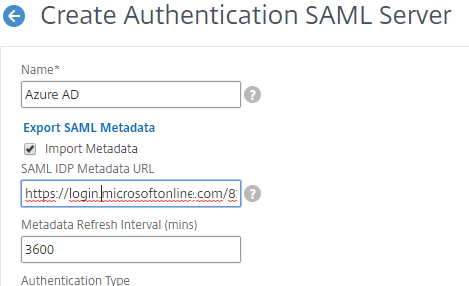
- If your Citrix ADC is 12.1 or newer, then get the SAML Metadata URL (or file) from the IdP.
- In the SAML Server on Citrix ADC, in the SAML IDP Metadata URL field, paste in the URL. ADC should be able to extract the IdP’s certificate from the Metadata URL.
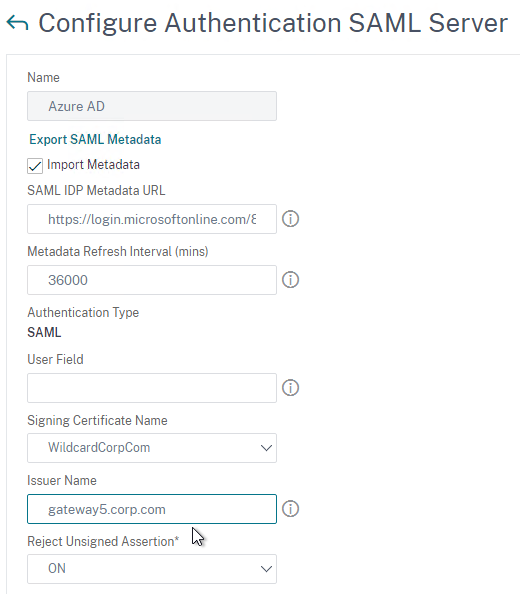
- In the Issuer Name field, enter the ID that the SAML IdP is expecting for the Relying Party. This Issuer Name must match the name you configured on the IdP’s Relying Party (Service Provider) Trust. Azure AD calls this the Identifier or Entity ID.
- Near the bottom, configure a Relay State Rule to prevent session hijack. It should check the Relay State field to make sure it matches the URL that users using to reach the Gateway Virtual Server. Make sure you include the forward slash at the end of the URL. Sample expression below. Pattern set is also possible. See CTX316577 for details. To avoid relay state “does not match” error, make sure users enter the Gateway URL instead of using a bookmark. 💡
AAA.LOGIN.RELAYSTATE.EQ("https://gateway5.corp.com/")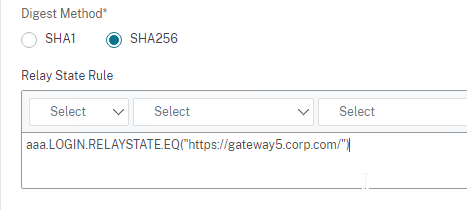
- Scroll down and click More.
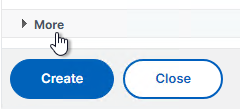
- You can optionally check Force Authentication to prevent users from doing SAML authentication using cached credentials. This prompts for MFA every time the user accesses Citrix Gateway.
- Scroll down and click Create.
- Edit the SAML Server again.
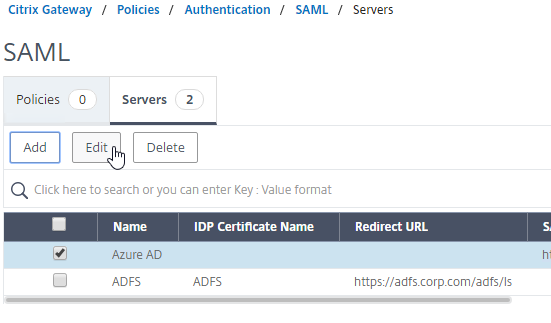
- If you uncheck the box next to Import Metadata, you can see the fields that it filled in for you. Unfortunately, other fields must be configured manually as detailed soon.
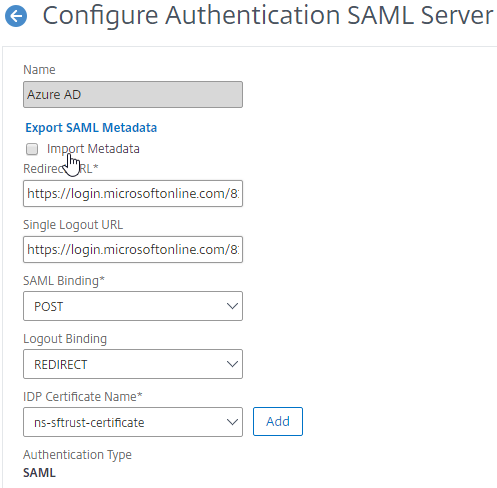
- In the SAML Server on Citrix ADC, in the SAML IDP Metadata URL field, paste in the URL. ADC should be able to extract the IdP’s certificate from the Metadata URL.
- Configure the SAML Server based on the data provided by your IdP. If you imported Metadata, then some of the fields might already be populated.
- For IDP Certificate Name, select the SAML IdP’s certificate that was exported from the SAML IdP and imported to Citrix ADC. Citrix ADC will use this IdP certificate to verify SAML assertions from the IdP.
Note: the Add button here does not work correctly. Instead, if you need to import the SAML IDP certificate, then do it at the CA Certificates node as detailed earlier in this section.
- For Redirect URL, enter the URL to the SAML IdP’s authentication page. Citrix Gateway will redirect users to this URL. For ADFS, enter your ADFS URL appended with /adfs/ls (e.g. https://adfs.corp.com/adfs/ls). For other IdP’s, get the URL from your IdP.
- For User Field, enter the name of the SAML Claim from the IdP that contains the value that matches the userPrincipalName of your local Active Directory users (aka shadow accounts). This defaults to the NameID field, but you might have to use a different claim, like emailaddress.
- In the Issuer Name field, enter the ID that the SAML IdP is expecting for the Relying Party. This Issuer Name must match the name you configured on the IdP’s Relying Party (Service Provider) Trust. Azure AD calls this the Identifier or Entity ID.

- Near the bottom, configure a Relay State Rule to prevent session hijack. It should check the Relay State field to make sure it matches the URL that users using to reach the Gateway Virtual Server. Make sure you include the forward slash at the end of the URL. Sample expression below. Pattern set is also possible. See CTX316577 for details. 💡

- Optionally, for Signing Certificate Name, select the SAML SP certificate (with private key) that Citrix ADC will use to sign authentication requests to the IdP. This same certificate (without private key) must be imported to the IdP, so the IdP can verify the authentication request signature. This field usually isn’t needed by most IdPs.
- Scroll down and click More.
- Citrix ADC defaults to SHA1. You might have to change the Signature Algorithm and Digest Method to SHA256.
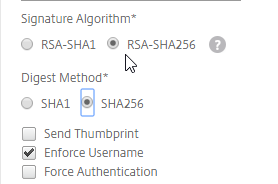
- Review the other settings as needed by your IdP. Click Create when done.
- For IDP Certificate Name, select the SAML IdP’s certificate that was exported from the SAML IdP and imported to Citrix ADC. Citrix ADC will use this IdP certificate to verify SAML assertions from the IdP.
SAML Policy – Advanced (nFactor) Method
Workspace app and Gateway Plugin (i.e. VPN plugin) require nFactor (Advanced Authentication Policies) to support SAML authentication.
Licensing – nFactor requires NetScaler ADC Advanced Edition or NetScaler ADC Premium Edition. The newest builds of NetScaler ADC 13 have added nFactor support for NetScaler ADC Standard Edition, but the configuration of an Authentication Virtual Server is not directly accessible from the main menu. If you only have Standard Edition, then do the following to get to the Authentication Virtual Server:
- Go to Citrix Gateway > Virtual Servers and edit one.
- On the right, add the Authentication Profile section.
- On the left, in the Authentication Profile section, click Add to create an Authentication Profile.
- In the Authentication Virtual Server row, click Add to create an Authentication Virtual Server.
- The rest of the nFactor configuration is similar to what’s detailed below.
If you prefer to configure the older Classic Method, which doesn’t work with Workspace app, then skip to the Classic Method.
Do the following to create an Advanced Authentication Policy, an Authentication Virtual Server, and bind it to the Gateway Virtual Server:
- In the left menu, expand Security, expand AAA – Application Traffic, expand Policies, expand Authentication, expand Advanced Policies, and then click Policy.
- On the right, click the button labelled Add.
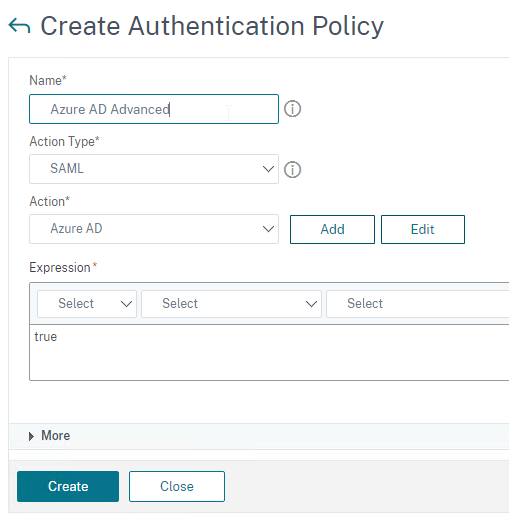
- Change the drop-down for Action Type to SAML.
- Change the drop-down for Action to the SAML Action you created earlier.
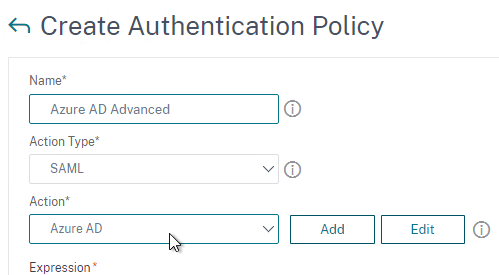
- In the box labelled Expression, enter true.
- Give the policy a name and click Create.
- Change the drop-down for Action Type to SAML.
- In the left menu, expand Security, expand AAA – Application Traffic and then click Virtual Servers.
- On the right, click the button labelled Add.
- Change the drop-down named IP Address Type to Non Addressable and then click OK.
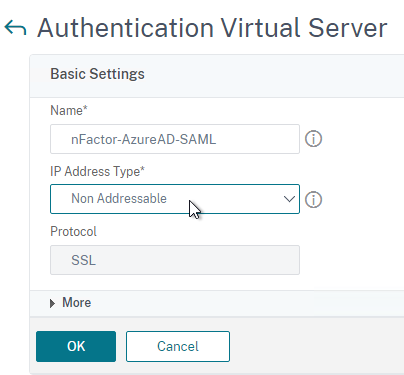
- Change the drop-down named IP Address Type to Non Addressable and then click OK.
- You can optionally bind a Server Certificate. If you don’t bind a certificate, then the AAA vServer will be down but it will still work. It doesn’t matter what certificate you choose. Click Continue when done.
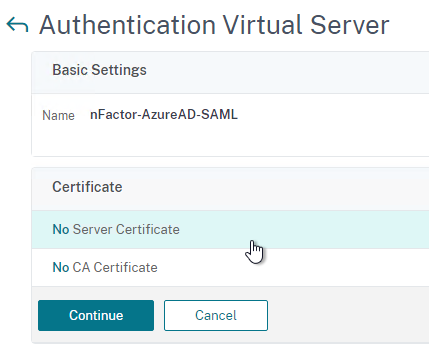
- On the left, in the section named Advanced Authentication Policies, click the row that says No Authentication Policy.
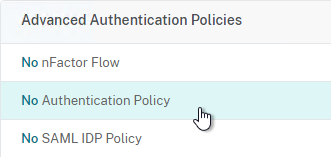
- Click where it says Click to select.
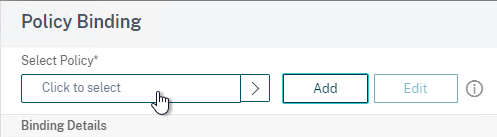
- Click the small circle to the left of the SAML Policy that you created earlier. Then click the blue button labelled Select at the top of the screen.
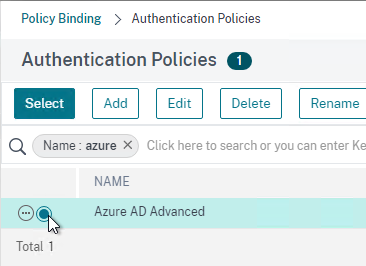
- There’s no need to configure Select Next Factor unless you want to bind an LDAP Policy with Authentication Disabled so you can extract groups from Active Directory and use those groups for Gateway authorization. This configuration procedure is detailed in the next section.
- Click the blue button labelled Bind at the bottom of the window.
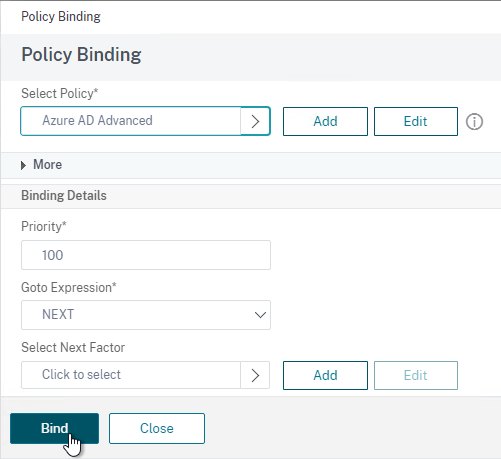
- Click where it says Click to select.
- Click Continue,
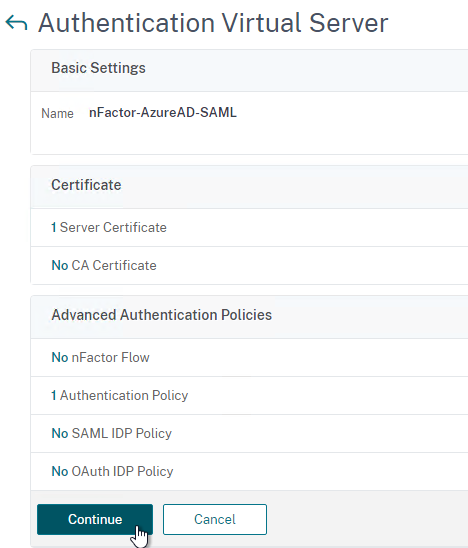
- At the bottom of the page, click Done to finish creating the AAA vServer.
- In the left menu, expand Citrix Gateway and click Virtual Servers.
- On the right, edit your existing Gateway Virtual Server.
- On the right side of the screen, in the Advanced Settings column, click Authentication Profile.
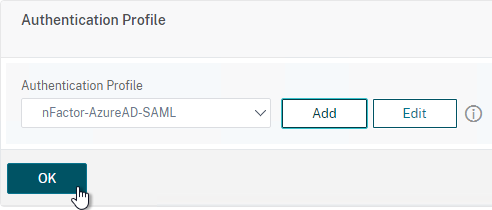
- On the left side of the screen, find the Authentication Profile section and then click the button labelled Add.
- Click where it says Click to Select and then select your AAA vServer.
- Give the Authentication Profile a name and then click the blue button named Create.
- Make sure you click the blue OK button before you click Done. If you don’t click OK then your changes won’t be saved.
Here are some sample CLI commands for this nFactor SAML configuration.
# SAML Actions # ------------ add authentication samlAction "Azure AD" -samlIdPCertName AzureADSAML -samlSigningCertName WildcardCorpCom -samlRedirectUrl "https://login.microsoftonline.com/815e26a9-4a9b/saml2" -samlIssuerName gateway5.corp.com -Attribute1 emailaddress -logoutURL "https://login.microsoftonline.com/815e26a9/saml2" -logoutBinding REDIRECT -relaystateRule "aaa.LOGIN.RELAYSTATE.EQ(\"https://gateway5.corp.com/\")" # SAML Authentication Policies # ---------------------------- add authentication samlPolicy "Azure AD" ns_true "Azure AD" # Advanced Authentication Policies # -------------------------------- add authentication Policy "Azure AD Advanced" -rule true -action "Azure AD" # Authentication Virtual Servers # ------------------------------ add authentication vserver nFactor-AzureAD-SAML SSL 0.0.0.0 bind authentication vserver nFactor-AzureAD-SAML -policy "Azure AD Advanced" -priority 100 -gotoPriorityExpression NEXT # Authentication Profiles # ----------------------- add authentication authnProfile nFactor-AzureAD-SAML -authnVsName nFactor-AzureAD-SAML # Citrix Gateway Virtual Servers # ------------------------------ set vpn vserver gateway5.corp.com -authnProfile nFactor-AzureAD-SAML
SAML nFactor LDAP Group Extraction
If you use AAA Groups with Citrix Gateway, then be aware that SAML usually does not provide the user’s group membership. Instead, configure a LDAP Policy to get the user’s groups from Active Directory so the groups can be later used by Citrix Gateway.
If you don’t need LDAP Group Extraction, then skip ahead to the StoreFront section.
Do the following to configure LDAP Group Extraction.
- Create a new LDAP Action.
- Use the Search in Menu to find LDAP then pick any of the results.

- Check the box next to an existing LDAP policy and click Add to copy its configuration. Or create a new one.
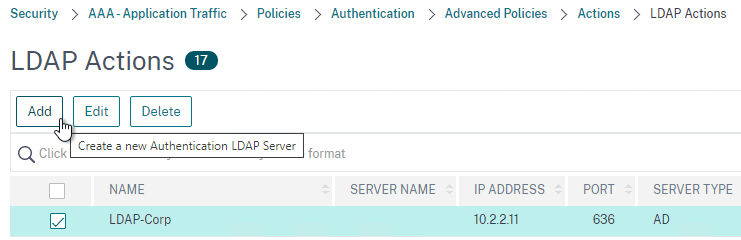
- Change the name of the LDAP Action.
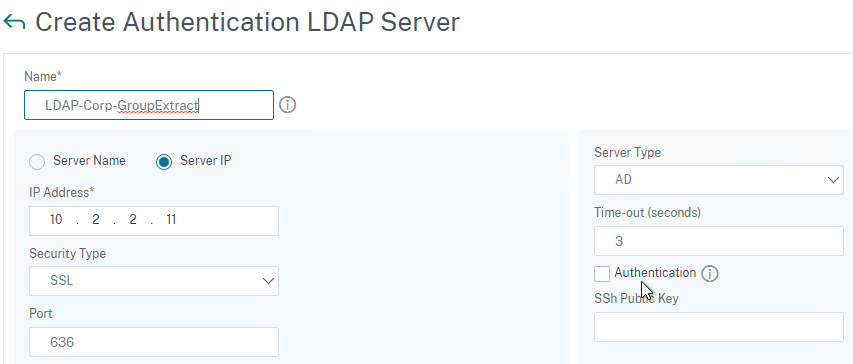
- On the top right, uncheck the box next to Authentication.
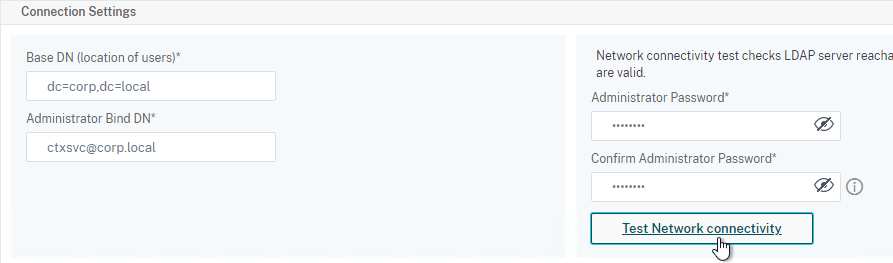
- Scroll down a bit and in the right side re-enter the Administrator Password. Copying an existing LDAP Action does not copy the Bind password.
- Scroll down to the Other Settings section.
- On the left, change Server Logon Name Attribute to –<< New >>–.
- Enter userPrincipalName. The UPN is extracted from the SAML Assertion.
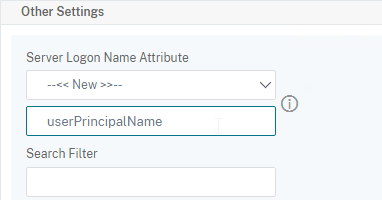
- Scroll down and click Create.
- Use the Search in Menu to find LDAP then pick any of the results.
- On the left, go to Security > AAA – Application Traffic > Policies > Authentication > Advanced Policies > Policy and click Add to create a new Policy.
- Change Action Type to LDAP.
- Expression = true.
- Click Create.
- On the left, go to Security > AAA – Application Traffic > Policies > Authentication > Advanced Policies > Policy Label. On the right, click Add.
- Give the Policy Label a name and click Continue. The Login Schema should be LSCHEMA_INT.
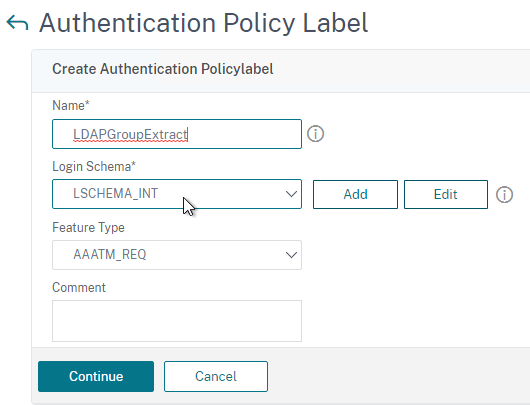
- Select your LDAP Group Extract policy and then on the bottom click Bind.
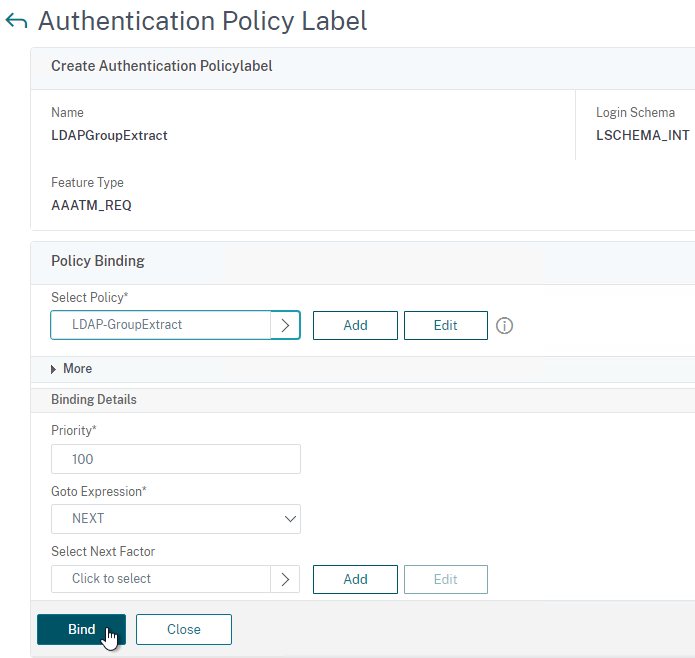
- Click Done to close the Policy Label.
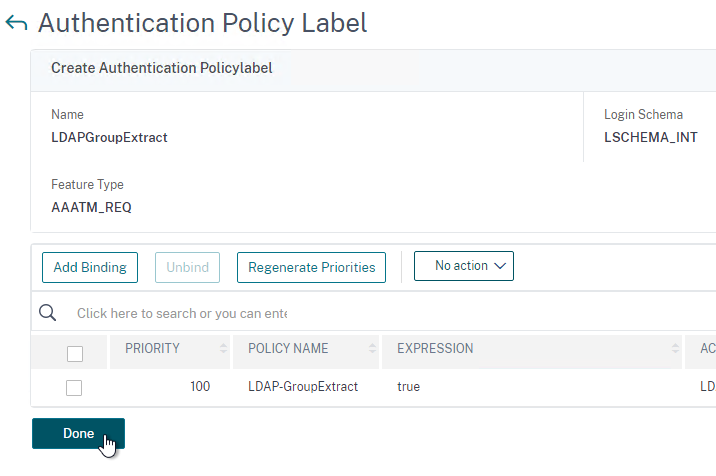
- Give the Policy Label a name and click Continue. The Login Schema should be LSCHEMA_INT.
- On the left, go to Security > AAA – Application Traffic > Virtual Servers. On the right, edit your SAML AAA vServer.
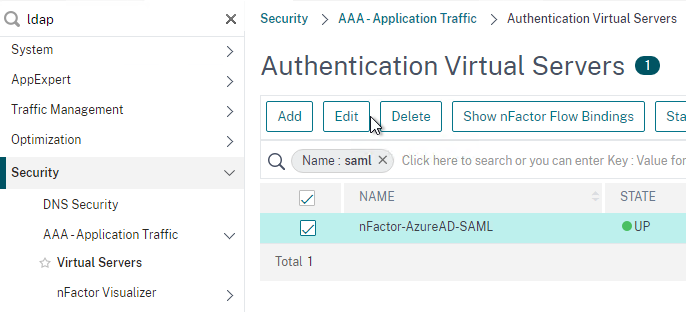
- Click where it says 1 Authentication Policy.
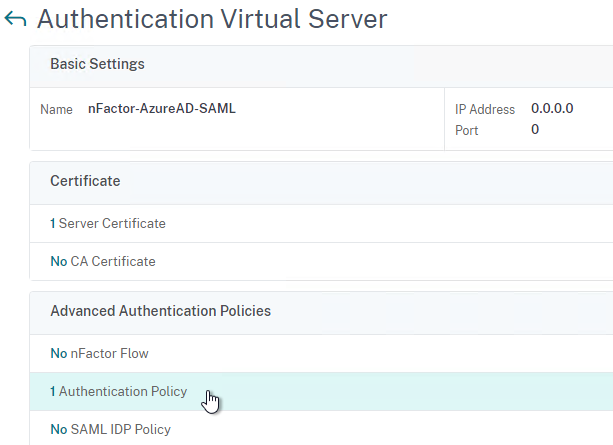
- Right-click the Authentication Policy and then click Edit Binding.
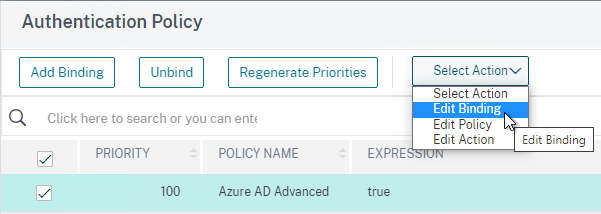
- In the Select Next Factor field, click where it says Click to select.
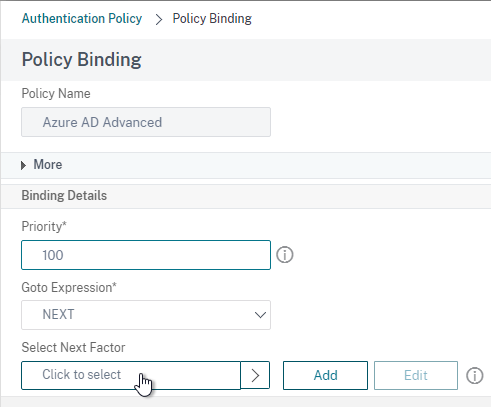
- Select your LDAP Group Extract Policy Label and then click Bind.
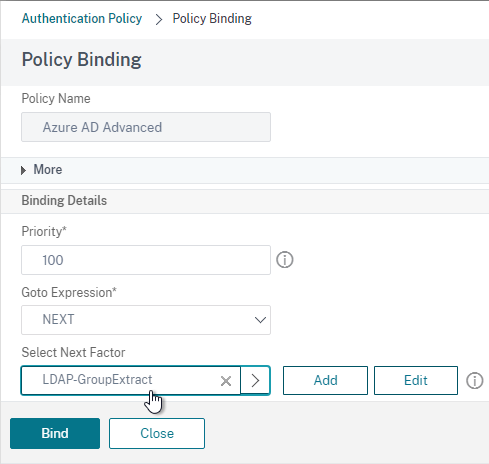
- Click where it says 1 Authentication Policy.
- Skip ahead to the StoreFront section.
Here are some sample CLI commands for this nFactor SAML LDAP Group Extract configuration.
# LDAP Actions # ------------ add authentication ldapAction LDAP-GroupExtract -serverIP 10.2.2.11 -serverPort 636 -ldapBase "dc=corp,dc=local" -ldapBindDn ctxsvc@corp.local -ldapBindDnPassword ****** -ldapLoginName userPrincipalName -groupAttrName memberOf -subAttributeName cn -secType SSL -authentication DISABLED # LDAP Policies # ------------- add authentication ldapPolicy LDAP-Corp ns_true LDAP-Corp # Authentication Policy Labels # ---------------------------- add authentication policylabel LDAP-GroupExtract -loginSchema LSCHEMA_INT bind authentication policylabel LDAP-GroupExtract -policyName LDAP-GroupExtract -priority 100 -gotoPriorityExpression NEXT # Authentication Virtual Servers # ------------------------------ bind authentication vserver nFactor-AzureAD-SAML -policy "Azure AD Advanced" -priority 100 -nextFactor LDAP-GroupExtract -gotoPriorityExpression NEXT
Configure StoreFront for SAML Citrix Gateway
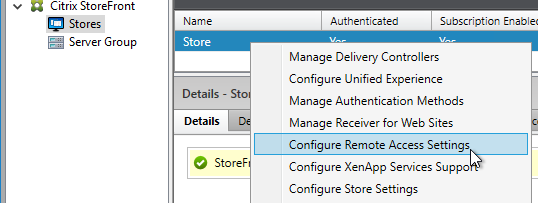
- In StoreFront 3.6 or newer, in the StoreFront Console, go to Stores, right-click the store, and click Manage Authentication Methods.
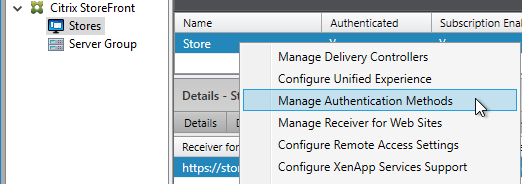
- Make sure Pass-through from Citrix Gateway is selected.
- Click the bottom gear icon on the right, and click Configure Delegated Authentication.
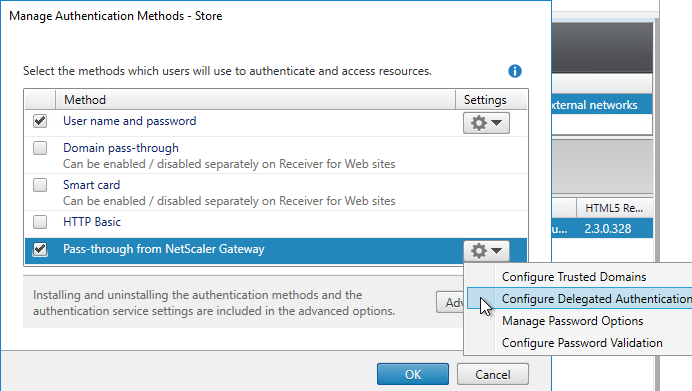
- Check the box next to Fully delegate credential validation to Citrix Gateway and click OK twice.
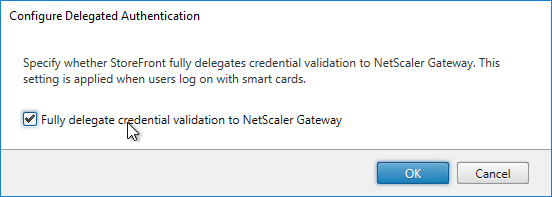
- In StoreFront, add a Citrix Gateway object that matches the FQDN of the Citrix Gateway Virtual Server that has SAML enabled.
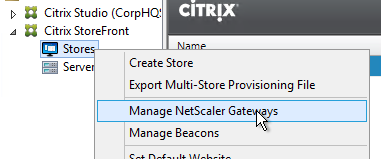
- On the Authentication Settings page, make sure you configure a Callback URL. It won’t work without it.
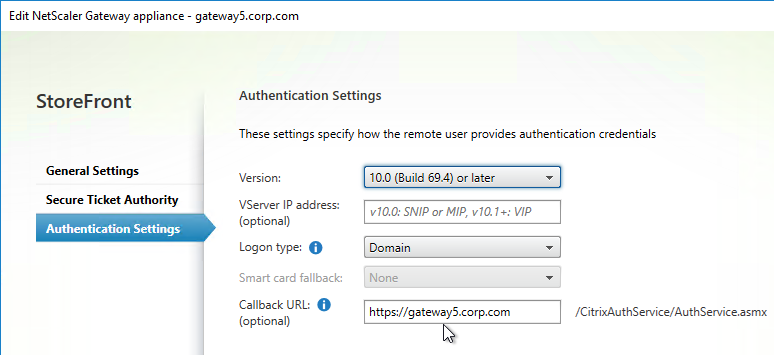
- Then assign (Configure Remote Access Settings) the Gateway to your Store.
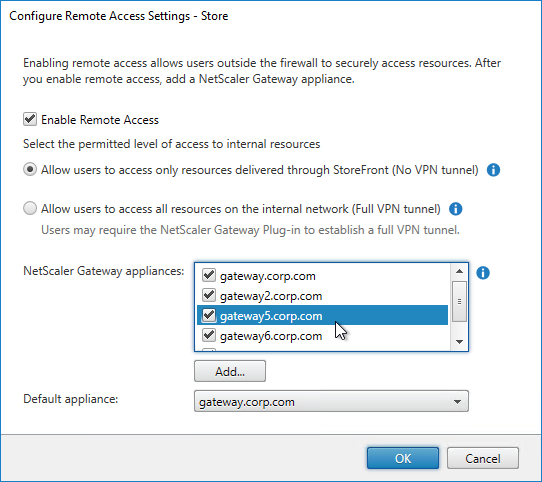
- Next step: create Active Directory Shadow Accounts
Native SAML on StoreFront without Citrix ADC
StoreFront 3.9 and newer have native support for SAML Authentication without Citrix ADC. Notes:
- SAML overrides Explicit and Pass-through authentication.
- SAML in StoreFront without Citrix ADC seems to work in Workspace app and Receiver Self-Service for Windows.
For an example configuration using StoreFront PowerShell commands and SAML metadata, see CTX232042 Configure StoreFront with OKTA.
To configure native SAML in StoreFront 3.9 or newer:
- Export the signing certificate from your SAML IdP. The IdP could be ADFS, Okta, Ping Identity, etc.
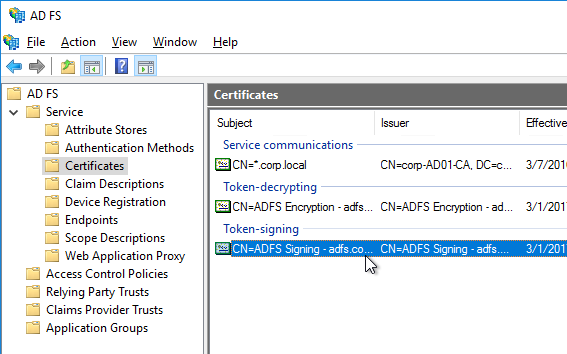
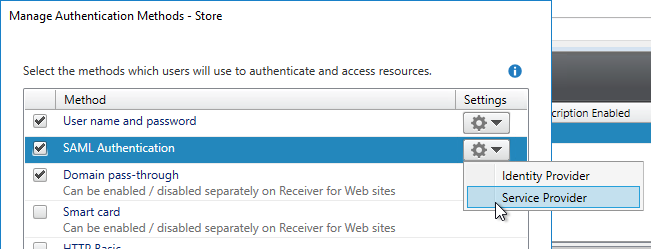
- In StoreFront 3.9 or newer console, right-click a Store, and click Manage Authentication Methods.
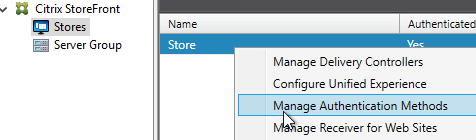
- Check the box next to SAML Authentication. If you don’t see this option (because you upgraded from an older version), click the Advanced button on the bottom of the window, and install the authentication method.
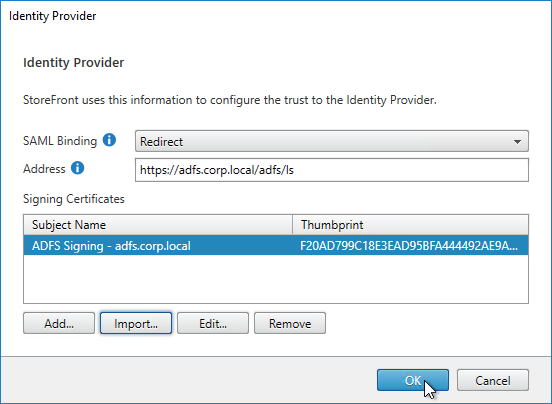
- On the right, click the gear icon for SAML, and click Identity Provider.
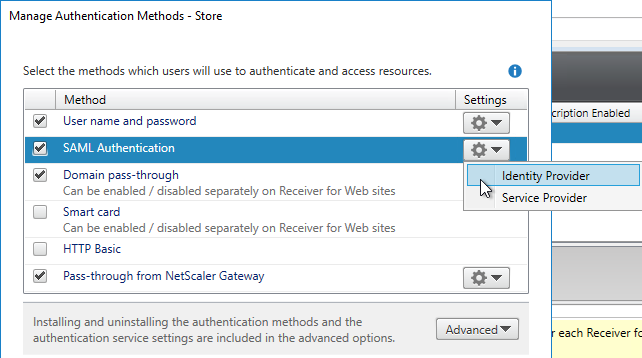
- Change the SAML Binding to the method your IdP expects.
- Enter the IdP token issuance endpoint URL. For example, in ADFS, the path is /adfs/ls.
- Click Import.
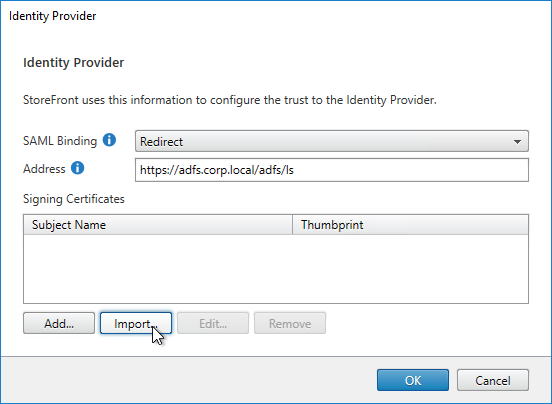
- Browse to the signing certificate exported from your IdP, and click Open.
- Then click OK to close the Identity Provider window.
- On the right, in the SAML Authentication row, click the gear icon, and then click Service Provider.
- Click the first Browse button.
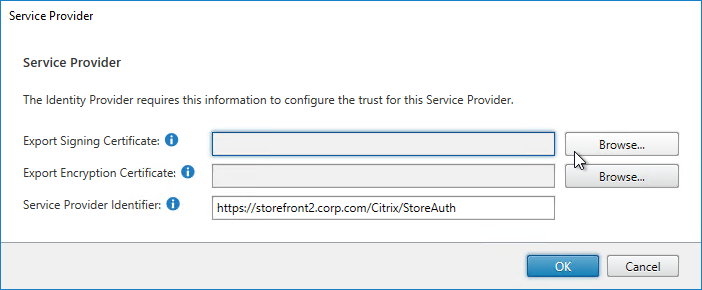
- Give the Signing certificate a name, and save it somewhere.
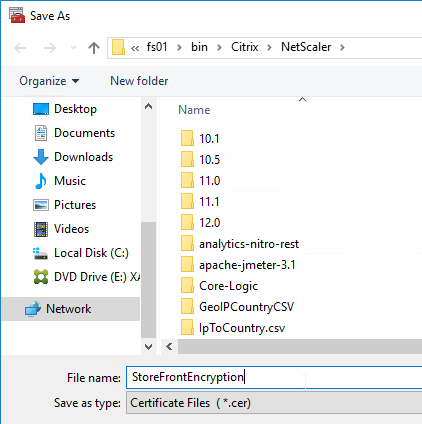
- Click the second Browse button.
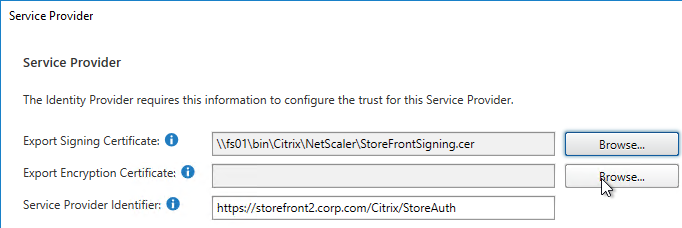
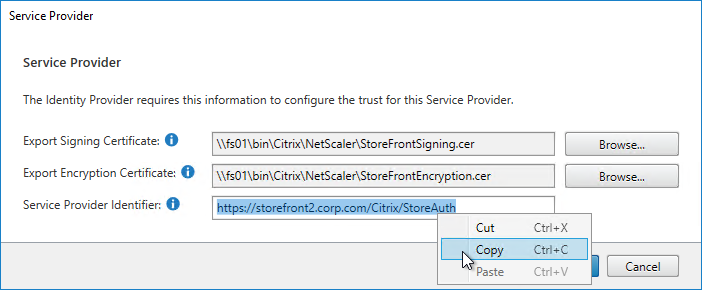
- Give the Encryption certificate a name, and save it somewhere.
- Copy the Service Provider Identifier. Or you can change it to your desired value. Then click OK.
- In your IdP (e.g. ADFS), create a Relying Party Trust.
- Import the Encryption certificate that you exported from StoreFront.
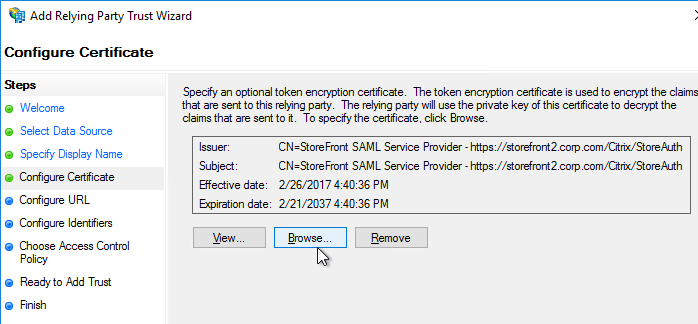
- Enable SAML 2.0.
- For the Assertion Consumer Service (ACS) path, enter something similar to https://storefront.corp.com/Citrix/StoreAuth/SamlForms/AssertionConsumerService. The hostname portion of the URL is equivalent to your StoreFront Base URL. /Citrix/StoreAuth matches your Store name with Auth on the end. The rest of the path must be /SamlForms/AssertionConsumerService. You can get this ACS value by looking in the SAML metadata at the bottom of https://<storefront host>/Citrix/StoreAuth/SamlForms/ServiceProvider/Metadata.
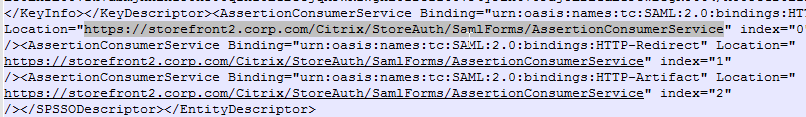
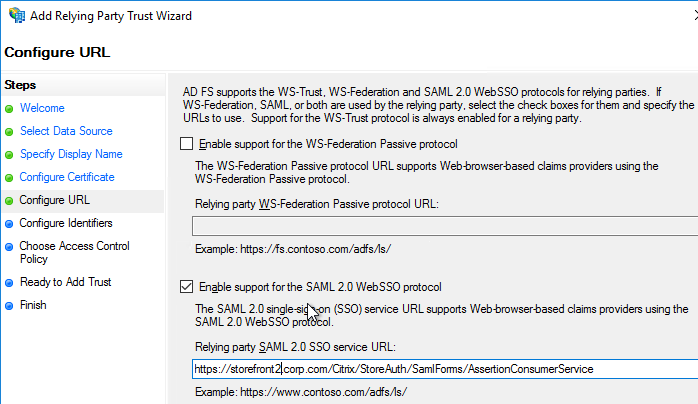
- For the Relying party trust identifier, enter the identifier you copied from the Service Provider window in StoreFront.
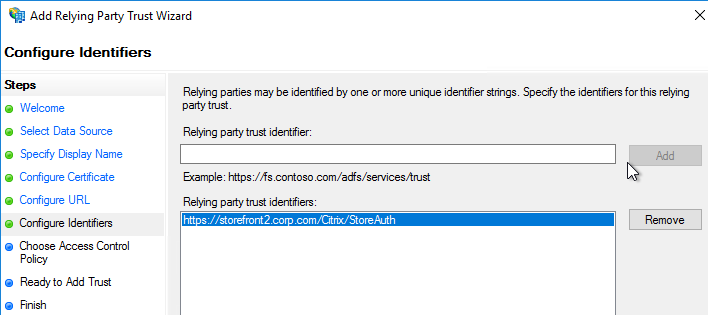
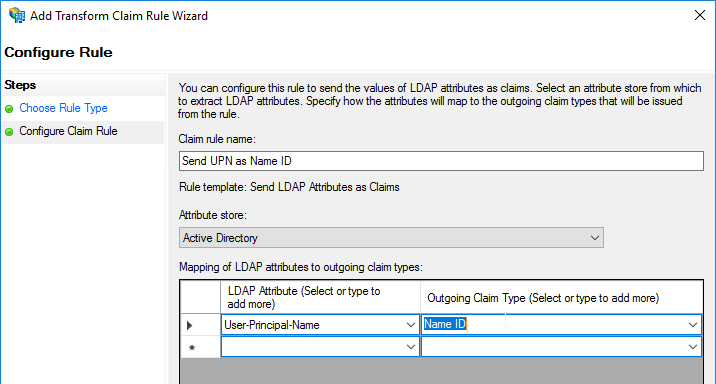
- Configure the Claim Rules to send the user’s email address or userPrincipalName as Name ID.
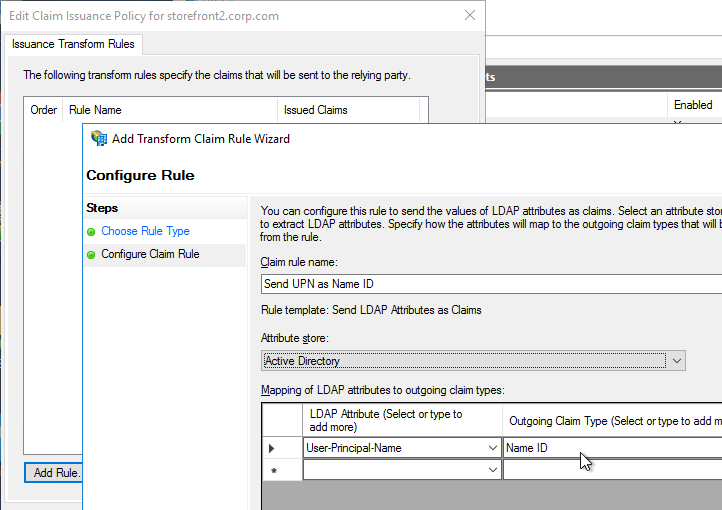
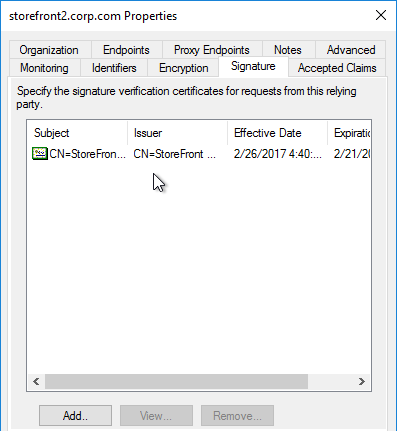
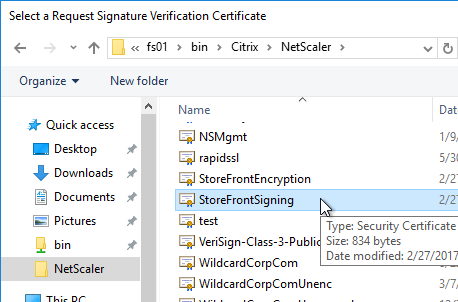
- Edit the Relying Party Trust. Import the Signing certificate that you exported from StoreFront.
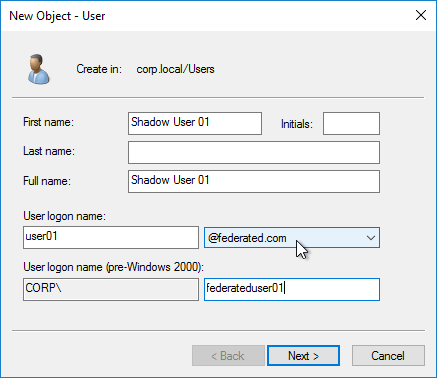
- Create Active Directory Shadow Accounts. Federated users must be userPrincipalName mapped to local Active Directory accounts.
- If you point your browser to https://<storefront-host>/Citrix/<storename>Auth/SamlTest, it should perform a SAML Login, and then show you the assertion that was returned from the IdP. See Citrix CTX220639 How to configure SAML Authentication-Test Configuration.
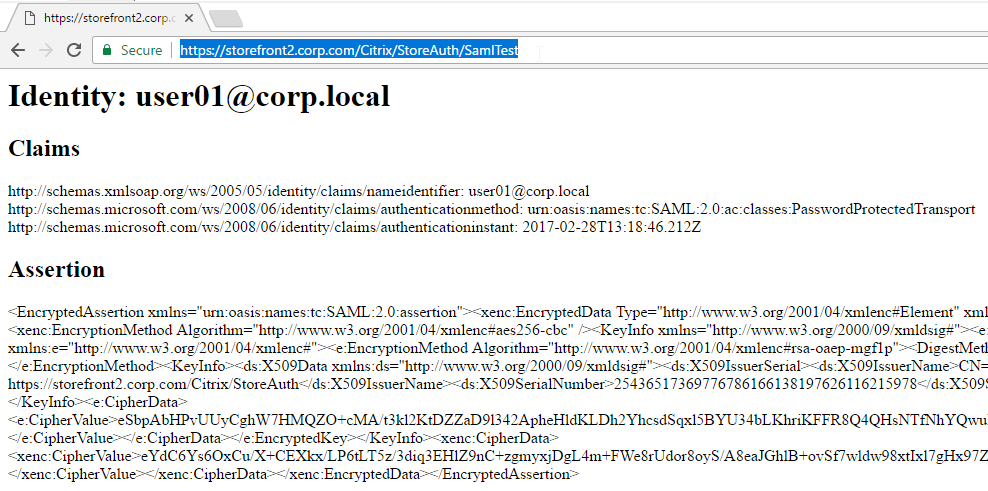
- See Citrix CTX220682 Storefront SAML Troubleshooting Guide for event logs, SAML Metadata, Active Directory account mapping, Trust XML, etc.
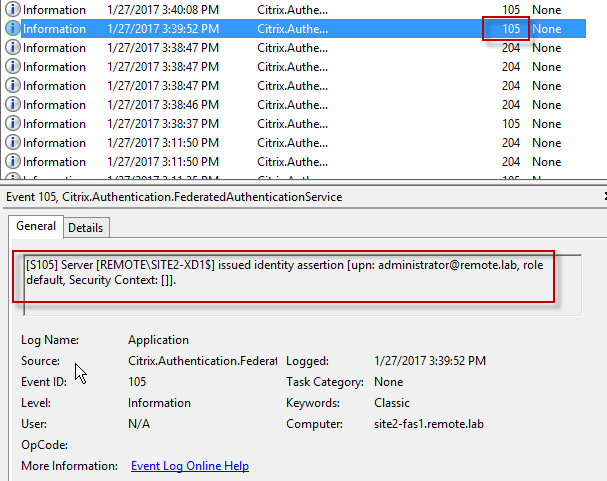
- When you go to your Receiver for Web page, it should automatically redirect you to your IdP. After authentication, it should redirect you back to StoreFront and show you your icons.
- ADFS also works in Receiver 4.6 and newer, and Workspace app.
- When you logoff, it won’t let you log on again unless you close your browser and reopen it.
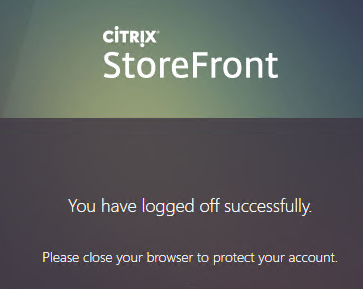
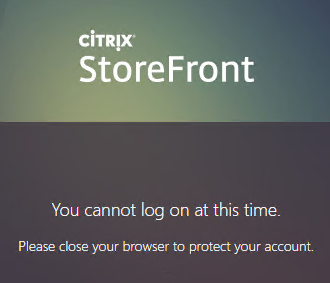
- To fix this problem, see CTP Sacha Thomet StoreFront – Allow relogin without browser close. Edit the file C:\inetpub\wwwroot\Citrix\StoreWeb\custom\script.js, and add the following line:
CTXS.allowReloginWithoutBrowserClose = true
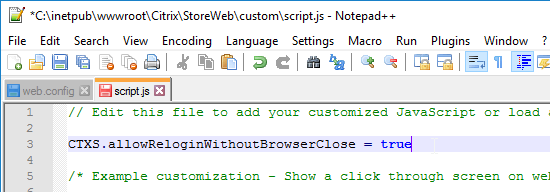
- Now when you logoff, you’re given an option to log on again.

Active Directory Shadow Accounts
To login to Windows (Citrix VDA), every user must have an Active Directory account in a domain trusted by the VDA. For Federated Users, you typically need to create shadow accounts for each Federated user in your local Active Directory. These Shadow accounts need a userPrincipalName that matches the SAML attribute (usually email address) provided by the SAML IdP.
If the email address provided by the SAML IdP does not match the UPN suffix for your domain, then do the following:
- Open Active Directory Domains and Trust.
- Right-click the top left node (not a domain node), and click Properties.
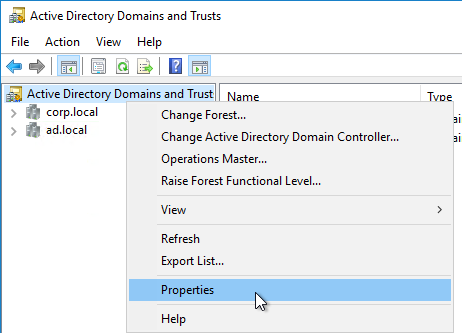
- In the UPN Suffixes tab, add a UPN suffix that matches the email suffix provided by the SAML IdP.
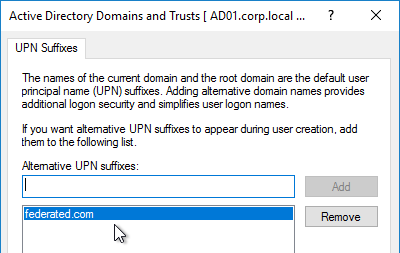
- When creating a shadow account in your Active Directory, the new UPN suffix is available in the drop-down list. Note that the pre-Windows 2000 logon name can’t conflict with any other user in the domain.
- The password for these Shadow accounts can be any random complex password since the Federated users never need the Shadow account’s password.

- If the shadow account is already created, edit the account, and on the Account tab, use the drop-down to select the new UPN suffix.
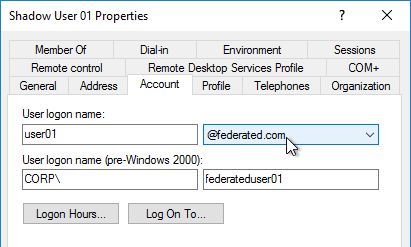
- Create a shadow account for every federated user. There are third party Identity Management tools that can automate this. Or get an export from the IdP and use PowerShell scripting to create the acccounts.
Verify FAS
When FAS is enabled on StoreFront, every user that logs into StoreFront (local or remote) causes a user certificate to be created on the FAS server. You can see these user certificates by running the following PowerShell commands:
Add-PSSnapin Citrix.Authentication.FederatedAuthenticationService.V1 Get-FasUserCertificate -address fas01.corp.local
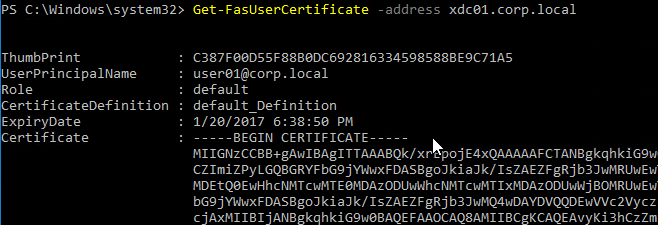
Citrix uses these certificates to logon to the VDA as the user. No password needed.
With Citrix Federated Authentication Service (SAML) I can permit to external users (another domain) open automatically your desktop?without open browser….at windows logon? thanks
SAML is a web-based authentication method. The newest versions of Workspace app and Gateway support SAML without needing to open a browser.
Thanks for the reply! Do you know some link with this information? when you say “newest versions of Workspace app and Gateway” it’s mean xendesktop 1808? Netscaler VPX 12?
ADC 12.1 and Workspace app 1809. https://www.citrix.com/content/dam/citrix/en_us/documents/data-sheet/citrix-workspace-app-feature-matrix.pdf
Thanks !
So.. I need only to configure SAML with the latest version adc 12.1 and 1809 to permit to users launch desktop automatically… Cool !
With email discovery.
I’ll go to read your web documents
Workspace app won’t launch icons automatically. One option is to create a shortcut to SelfService.exe /qlaunch Mydesktop and put the shortcut in the Startup folder. It should then prompt the user for SAML credentials.
Thanks a lot Carl you are the best
I need to install and configure 1809 and adm 12.1 and later test the auto launch
Thanks
Hi Carl,
Will SAML authentication directly to Storefront work with an external non-ADFS SAML provider?
It might. But I’ve seen some that don’t work native to StoreFront, but work fine with Gateway.
Carl, can you elaborate on that? I am seeing an issue with PingFederate as a SAML IdP trying to post the SAML assertion response back to the SAML SP (Storefront), but getting stuck at the SAML ACS URL, with “Completing authentication” showing on the screen.
Greg, did you ever find a solution to this? I am running into same issue ‘completeing authentication’ on the ACS URL after authenticating against PING
awesome Carl!
Maybe you can help me on my particular issue – I am a Netscaler guy but not so much a Storefront/Xenapp guy.
We have a Access setup with 2f auth (first user/pass – second radius), and we need to get radius removed – So I configured SAML instead on our test and enabled the Trust for delegation on the Netscaler Pass through auth. Logon to SF works fine but when starting an ica session I need to authenticate.
I learned that SF does not have a password and so it cant authenticate towards a backend server – only solutions I found is FAS (which i am no keen to implement – you remember I am a Netscaler guy) or transporting the password in the claim – which doesnt sound right at all…Is there any other way?
One more:
If I do SAML directly on the SF (without NS at all) – I guess SSO wont work either when launching the ica session, right? Again the Storefront doesnt have a PW, or is it done different when using SAML on the SF? So do I always need FAS if I want single sign on to the ica session when using SAML no matter where I do the SAML auth (NS or SF)?
Cheers
Alex
Windows supports two methods of authentication – password, or certificate. If no password, then certificate is the only other option. FAS generates certificates for users and uses the certificates for authentication. Every major broker does SAML this way.
If shadow accounts were in a different forest (with limited CFT), would you recommend the CA be in the User or DDC\VDA forest?
Thank you,
The Citrix_SmartcardLogon template builds the Subject Name from AD information. I assume the CA needs to able to get that user info from AD.
Hi Carl,
Does Storefront support IdP initiated single sign-on (SAML)?
Thanks
I don’t see why not. StoreFront has some native SAML functionality, but I find NetScaler as SAML SP to be much more capable.
Hello Carl.
This page is really helpful in setting up Citrix farm with FAS, very detailed. Thanks!
When we use our IdP and Storefront as SP, we are getting certificate validation error. I have installed all signing certificates in both SP and IDP.
“The security token failed validation.
System.IdentityModel.Tokens.EncryptedTokenDecryptionFailedException, System.IdentityModel, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089
ID4022: The key needed to decrypt the encrypted security token could not be resolved. Ensure that the SecurityTokenResolver is populated with the required key.
at System.IdentityModel.Tokens.Saml2SecurityTokenHandler.CreatePlaintextReaderFromEncryptedData(XmlDictionaryReader reader, SecurityTokenResolver serviceTokenResolver, SecurityTokenSerializer keyInfoSerializer, Collection`1 clauses, EncryptingCredentials& encryptingCredentials)
at System.IdentityModel.Tokens.Saml2SecurityTokenHandler.ReadAssertion(XmlReader reader)
at System.IdentityModel.Tokens.Saml2SecurityTokenHandler.ReadToken(XmlReader reader)
at System.IdentityModel.Tokens.SecurityTokenHandlerCollection.ReadToken(XmlReader reader)
at Citrix.DeliveryServices.Authentication.Saml20.SamlExtensions.GetSecurityToken(String assertion, SecurityTokenHandlerCollection securityTokenHandlers)
at Citrix.DeliveryServices.Authentication.Saml20.SamlManager.ProcessSamlResponse(String base64EncodedResponse, Boolean compressed)”
Please help!
You can decode the SAML Assertion to verify that the certificate used to sign the assertion matches the one you installed on StoreFront.
Otherwise, I find configuring SAML on NetScaler to be much more capable than configuring it natively on StoreFront.
Thanks Carl for the quick response.
We will check that out and revert for any queries.
Hello Carl,
We are still investigating SAML flow with Citrix Farm along with our IdP.
Is it possible to perform Kerberos constrained delegation to storefront 3.x server?
Thanks in advance.
Delivery Controllers and VDAs do not support Kerberos delegation. 6.5 does, but 7.x does not.
StoreFront can send username without password to Delivery Controller if Trust XML is enabled in the farm. However, once Receiver connects to VDA, StoreFront and Delivery Controller don’t have a password to give the VDA, and thus you need FAS to perform SSON to the VDA.
Thanks Carl for the quick response.
We have setup FAS environment to perform SSON from Storefront to Delivery controller to VDA.
We are looking at performing constrained delegation from our IdP to Storefront since user logs without password . Is it possible to enable constrained delegation to Storefront?
User logs in to our IdP with certificate or token and should be able to perform SSON to Storefront and to VDA through Delivery controller using FAS
Pass-through Authentication is essentially Negotiate authentication.
What is doing the KCD?
Hi Lima what did you find was the issue with this error. I am receiving the exact error?
Hello Carl
I have completed all the steps but I can not complete your request when I login through the Citrix web site.Storefront even ID:Citrix Receiver For Web
A CitrixAGBasic Login request has failed.
Citrix.DeliveryServicesClients.Authentication.AG.AGAuthenticatorException, Citrix.DeliveryServicesClients.Authentication, Version=3.12.0.0, Culture=neutral, PublicKeyToken=null
Authenticate encountered an exception.
at Citrix.DeliveryServicesClients.Authentication.AG.AGAuthenticator.Authenticate(HttpRequestBase clientRequest, Boolean& passwordSupplied)
at Citrix.Web.AuthControllers.Controllers.GatewayAuthController.Login()
System.Net.WebException, System, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089
The remote server returned an error: (403) Forbidden.
Url: https://127.0.0.1/Citrix/TestAuth/CitrixAGBasic/Authenticate
ExceptionStatus: ProtocolError
ResponseStatus: Forbidden
at System.Net.HttpWebRequest.GetResponse()
at Citrix.DeliveryServicesClients.Utilities.HttpHelpers.ReceiveResponse(HttpWebRequest req)
at Citrix.DeliveryServicesClients.Authentication.TokenIssuingClient.RequestToken(String url, RequestToken requestToken, String primaryToken, String languages, CookieContainer cookieContainer, IEnumerable`1 acceptedResponseTypes, IDictionary`2 additionalHeaders)
at Citrix.DeliveryServicesClients.Authentication.AG.AGAuthenticator.Authenticate(HttpRequestBase clientRequest, Boolean& passwordSupplied)
Another ID:Citrix Authentication Service
CitrixAGBasic single sign-on failed because the credentials failed verification with reason: Failed.
The credentials supplied were;
user: selahattin.yildirim
domain:
ID : Citrix Domain Service
The following error occurred during an authentication attempt for user: xx.local\selahattin.yildirim with realm:
System.ArgumentOutOfRangeException, mscorlib, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089
Specified argument was out of the range of valid values.
at Citrix.DeliveryServices.Authentication.Kerberos.Native.Authenticator.Authenticate(String userPrincipalName, String clientRealm)
at Citrix.DeliveryServices.Authentication.Kerberos.KerberosAuthenticator.Authenticate(String userPrincipalName, String clientRealm)
at Citrix.DeliveryServices.Kerberos.Delegated.Server.DelegatedKerberosAuthenticator.Authenticate(String userPrincipalName, String clientRealm)
I would appreciate your help
Best Regards
It looks like NetScaler is not sending the userPrincipalName to StoreFront. Or you’re not getting the userPrincipalName (or email address) from your SAML iDP.
Hi carl,
Thank you very much for your help.I look Netscaler Session Policy and ı see single sign on configured. and then uncheck single sign on so it problem solved.
Best Regards
Hello Carl,
We would like use an Enterprise CA that is hosted in our trusted domain with two-way relashionship, but the FAS server cannot hit the CA using its console or powershell Get-FASMsCertificateAuthority.
On our local domain, we have Storefront, FAS, Controllers and VDAs.
On the trusted domain, we have the Enterprise CA and the corporate users.
Do you know if there are a way to specify our Enterprise CA to the FAS?
i’m planning to have a set with Netscaler VPX(From Azure
Marketplace) in ICA Proxy Mode with 2-factor authentication
configured via Azure MFA (Cloud based).
Does this setup require FAS server for VDA single sign on to
happen?
Is it because of limitation with ICA proxy mode. Can I have
VPX with FULL VPN mode and have VDA single sign on without
FAS?
Hi Carl,
I’m planning to have an environment with a Netscaler VPX (ICA proxy – azure market place) with 2 -factor auth configured with Azure MFA(cloud based) . Will I be prompted for credentials when pass through to VDA happens .Do I need to have a FAS set up to have VDA single sign on. ?
Is there a limitation wrt to ICA proxy with MFA ? If I use a full VPN mode can i eliminate FAS?
If NetScaler collects the user’s AD password and sends it to StoreFront then there is no need for FAS or dual login.
Thanks Carl.
Hi Carl –
I have OKTA/SAML integrated per https://support.citrix.com/article/CTX232042 (with FAS installed). An SP initiated session works fine… I hit the SF URL, it redirects to OKTA, auth is successful and then kicks it back to Storefront. I can see apps and launch them with no issue. However, when I try and launch from OKTA (IdP initiated), I get directed the the /StoreAuth/SamlForms/AssertionConsumerService URL that is configured in OKTA, but I get an IIS runtime error. There is a corresponding event (ID 1309) for ASP.NET – Event message: An unhandled exception has occurred.
Any ideas? There’s not a lot out there and Citrix support is SLOW at helping me with this…
Thanks!
I usually prefer to do SAML on NetScaler instead of directly to StoreFront. NetScaler has greater SAML compatibility than direct to StoreFront, which was designed mostly for ADFS.
I agree, but unfortunately at this time, we’re not using Netscaler. Our company uses F5 and I followed a great article on setting up F5/OKTA/Storefront.. Using the SF URL directly, works great with OKTA. But anything via OKTA directly I hit that IIS runtime error page. If I use the OKTA chicklet or if I go through F5 virtual server (which has SP/IdP configured for Citrix), I get that runtime error. Only seems to work via SP-initiated sessions.
Also, funny thing is – if I go through OKTA and hit that IIS runtime error page (https://storefront.domain.com/Citrix/StoreAuth/SamlForms/AssertionConsumerService) and then click the address bar and press enter – resending the request myself – I get the ‘Completing authentication… ‘ window. It doesn’t go any further, but it doesn’t error out. And still the only error I ever see is the ASP.NET error when this happens.. no security fails or anything else I have been able to find yet.
Hello,
We’re you able to find a resolution?
Found part of an answer. Needed to have defaultRedirect (web.config) set to /Citrix/STOREWeb of the /Citrix/STOREAuth
Event Log still shows the ASP.NET error each time still.
Hi Carl, do you know if the FAS mechanism will work with our own hosted Storefront via the Netscaler gateway service offered with Workspace suite?
Can we configure a citrix FAS and netscaler as SP and okta or pingfedrate as a idp
Of course. Have you tried it?
Hi Carl, i have now a problem that storefront cannot proceed request. Event id 2 and 10. “cannot identify authentication domain” (translated from german). ADFS 2.0 on WS 2008R2, NS 12. 56.20nc. Maybe you have some idea? Thanks
From NetScaler? If so, is NetScaler sending the domain name when it shouldn’t be?
Is ADFS sending back the user’s UPN? Can StoreFront find a user account in AD that matches the UPN?
Yes, from NS. No, it sends no domain name, in session profile is no sso domain configured. In ADFS i have a claim rule: UPN as LDAP attribute and email as outgoing claim type. At domain where SF is shadow account configured.
If saml attribute is mail, then it looks like this:
samluser01@domain.de
If we take NameID, then it works fine) And looks like this:
samluser01@domain.de
hey guys,
does saml authentication require a specific version or license? only enterprise and platinum and version 12 of netscaler?
You should be able to bind a SAML Policy directly to the Gateway vServer, which means it should work in all Editions. However, if you do nFactor (AAA vServer), then you need Enterprise.
While installing FAS on step 3, I approved the certificate on the CA. Then the status changed to “Status: The supplied chain does not contain a self-signed certificate”.
Any ideas?
Is the CA root an offline root? Is the CA root distributed to the FAS server? Is the CA root CRL accessible?
CA root is an offline root CA. CA certificate is installed on FAS Server in trusted root certificate authorities. The CRL URL in the root CA certificate is not reachable by the FAS Server. Is it necessary that the FAS Server can reach the CRL?
Hey Carl, the issue is solved!
FAS cannot validate ECDSA root certificates. I had to rebuild the entire offline root CA with (SHA512)RSA as the signature algorithm and the issue was gone. I wrote Citrix to update their documentation.
Best regards,
Michael
Hi Carl, thank you for your post, it is very helpful. We have this error: Http/1.1 Internal Server Error 43549 when we are redirected back to NS after auth.
We have NS as SP, ADFS as IdP and Oracle OAM as IdP Proxy – it is customer requierement.
Thanks for any help.
I think that usually means that NetScaler can’t communicate with the StoreFront server.
Hi Carl, thank you for the quick answer. I have tested SF communication before SAML and it worked. I become this error when i am redirected to https://nsgw.domain.com/cgi/samlauth after successful login at adfs. I have NS 12.0 installed.
SAML is the only authentication method?
Is this Unified Gateway instead of a normal NetScaler Gateway?
SAML is the only auth method. i am using normal GW, not Unified Gateway
Anything interesting in aaad.debug or /var/log/ns.log?
i dont see any events neither in ns.log nor in the aaa.debug. While redirecting there happens nothing in log
Took you too long to come up with your password. Do it over, but faster – it will work.
Hello,
We are in this configuration :
– iDP is keycloak
– XenApp 7.15 & Federation Service is 7.15
– Netscaler
In Active Directory, the UPN is different from the email domain.
We are not able to authenticated any user. If we create a “shadow acocunt” that has the same UPN as the email adress of the “real” user then we can authenticate with the “real” user password but we see in the store that it is actually the shadow user that are log in. So there is no application available..
In keycloak, as NameID, we use ’email’.
When we look at the SAML assertion in Firefox we see that the client return the email adress.
What is wrong? How can we be connected with the “real” user and not the Shadow one?
Thanks in advance for your help!
Hello,
Here is a solution. We use a custom attribut of the user object, for example extensionAttribute10, that contains the UPN of the user (user@domain). In the keycloack “User Federation – mapper” we mapped the email attribut to extensionAttribute10. Now, we can authenticated and launch applications.
🙂
Trying to figure out ADFS on the NetScaler with SAML. I have the Base64 exports from our CA servers for both the signing and encryption certificate. When I install the certs on my NetScaler (12.0 56.20) they appear in the ‘Unknown Certificates’ area and I can assign the Encryption cert (IDP) but when selecting the Signing certificate I get an ‘Invalid Certificate’ error.
Are you referring to the SAML Action (Server) on NetScaler? You can select the iDP certificate, which came from ADFS? But the signing cert, which needs a private key, doesn’t work?
correct, the SAML Action (Server) on the NetScaler. Do I need the private key for the Signing Cert? I don’t think that was provided.
The idea is that NetScaler is signing the SAML request, and thus it needs a private key to do that. Then you give your public key to the iDP so it can verify the signature. This can be a self-signed certificate, or your Gateway/AAA certificate.
Similar Issue here:
The signing cert that was provided to me from the iDP provider (ADFS in this case) when installed on the Netscaler comes up under “Unknown Certs”. The signing cert does not have a private key available.
I am getting an error of “Malformed Assertion sent to Netscaler; Please contact your system administrator.
Hi Carl,
we have tested SAML + Citrix FAS via Gateway using a single domain and it works, but Is SAML + Citrix FAS really works via Gateway using multi-domain environment? Search most of the article but not found related to FAS in multi-domain. Do you have any idea is it possible, you help is appreciated.
Thanks
As long as the user’s email address matches a UPN in one of StoreFront’s trusted domains, I don’t see why it wouldn’t work.
Thank you for your quick reply, Carl.
Yes, In our testing environment, we have set the user’s email address as UPN for SAML login and any domain trust has configured on Storefront server and set up two-way trust enabled.
When we tried accessing the gateway URL using Domain A user account (UPN), gateway redirects to SAML page and getting authenticated there, redirects back to storefront webpage and we are able to successfully launch the applications. In similar way, We tried accessing the gateway URL using a test user account (UPN) from Domain B, the gateway redirects to SAML page and getting authenticated there, redirects back to storefront webpage and we are getting an error “Cannot complete your request”.
Would you please share some article to clear the error message and launch the applications.
What error are you seeing in StoreFront Server > Event Viewer > Applications and Services > Citrix Delivery Services?
Are your multiple domains in separate forests?
Carl, I’ve discovered that with the VDA version 7.15 the Single Sign-on no longer works I’ve also seen some users reporting it in this discussion thread: Stefanos Evangelou & Udo
And there is also a thread on this issue on the Citrix discussion forums: https://discussions.citrix.com/topic/389163-715-vda-upgrade-password-not-passing-through/
I’ve made a reproduction for this issue in my demo lab and fixed it with a workaround for VDA version 7.15:
https://robertsteeghs.wordpress.com/2018/03/05/xenapp-vda-7-15-cu1-breaks-single-sign-on-with-citrix-fas/
I’ve also tested with VDA version 7.17 and this one works without any problem.
Would “gpupdate /force” fix it?
Hi,
I’m implementing FAS configuration using Google and/or F5 as an iDP. I have two issues. First one is that when entering powershell command to test FAS funtionality I don’t get any response
PS C:\Windows\system32> Add-PSSnapin Citrix.Authentication.FederatedAuthenticationService.V1
PS C:\Windows\system32> Get-FasUserCertificate -address HWEHC-F5APM2.hcwtestsaas.local
PS C:\Windows\system32>
Second issue is that when I try to enter iDP address (Google as iDP) in StoreFront configuration I get error “An error occured while saving your changes”. I have noticed that when I remove ?-mark from the address URL StoreFront accepts the address, but obviously that won’t work because address is then wrong.
https://accounts.google.com/o/saml2/idp?idpid=C01zs9bxz
I usually am not able to get SAML to work natively with StoreFront (no NetScaler), so I instead add a NetScaler Gateway to do the SAML Auth.
Hi Carl, NetScaler has a function to generate xml Metadata SAML for IdP. But if i have an xml file from Idp can i import it to NS? I haven’t found it…
NetScaler doesn’t support metadata import or export.
Thank you for the answer. NetScaler seems to have export of his own xml metadata:NS Gateway->Policies->Auth->SAML->Servers->Generate Metadata.
But it is unfortunately not possible to import metadata xml file from IdP… or?
Hi Carl
Awesome work.
We have setup a Citrix Cloud + Azure platform and have configured the NS to authenticate to Azure AD via SAML. To make this work we deployed Citrix FAS servers. Getting a session inside or outside the organisation via web browser works fine.
I am having trouble making Citrix Receiver on domain joined PCs work, it is failing to display the session. The VDA keeps dropping the connections with an event ID 1017 Connection Id 16 from :50671 to port 2598 was unexpectedly closed during its SSL handshake phase.
I realised the VDA might be expecting a certificate, so I created another store, but this is also failing.
Any ideas?
Internal Receiver is bypassing NetScaler Gateway. Is that what you want?
Do you have SSL enabled on your Delivery Groups? You usually don’t need to do that.
Carl
Ideally no, as we want to LB the StoreFront via NS. Having said this, I have used local host entry on the PC with Receiver to bypass the NS LB and I still get the 1017 error. We do not have SSL enable on DG.
I disabled FAS for the second Store I created, but I am still unable to launch a session.
Hello,
Thanks for your article.
We are using RedHat Keycloak as Idp and 7.15 LTSR as FAS.
The logon process seems to work but the user cannot acces to any ressources.
In the Storefront there is this error :
A CitrixAGBasic Login request has failed.
Citrix.DeliveryServicesClients.Authentication.AG.AGAuthenticatorException, Citrix.DeliveryServicesClients.Authentication, Version=3.12.0.0, Culture=neutral, PublicKeyToken=null
Authenticate encountered an exception.
at Citrix.DeliveryServicesClients.Authentication.AG.AGAuthenticator.Authenticate(HttpRequestBase clientRequest, Boolean& passwordSupplied)
at Citrix.Web.AuthControllers.Controllers.GatewayAuthController.Login()
System.Net.WebException, System, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b774e089
The remote server returned an error: (403) Forbidden.
Url: http://127.0.0.1/Citrix/Auth/CitrixAGBasic/Authenticate
ExceptionStatus: ProtocolError
ResponseStatus: Forbidden
at System.Net.HttpWebRequest.GetResponse()
at Citrix.DeliveryServicesClients.Utilities.HttpHelpers.ReceiveResponse(HttpWebRequest req)
at Citrix.DeliveryServicesClients.Authentication.TokenIssuingClient.RequestToken(String url, RequestToken requestToken, String primaryToken, String languages, CookieContainer cookieContainer, IEnumerable`1 acceptedResponseTypes, IDictionary`2 additionalHeaders)
at Citrix.DeliveryServicesClients.Authentication.AG.AGAuthenticator.Authenticate(HttpRequestBase clientRequest, Boolean& passwordSupplied)
Any idea??
thanks
There should be another event that shows the real error. Maybe on a different StoreFront server?
The iDP sent back the user’s email address? NetScaler Gateway extracted the email address and sent it to StoreFront? StoreFront is able to find a matching AD account using the user’s email address as UPN? NetScaler is not sending any domain name? FAS is enabled on StoreFront? StoreFront is configured to fully delegate authentication to NetScaler Gateway? Callback URL is configured in StoreFront? Any errors on the FAS server?
We have FAS setup with a netscaler gateway as mentioned above. We have some users that get the “cannot complete your request” After they put in their creds to the ADFS server. It appears to be failing before Storefront. We do see some errors in SF and on the fed auth servers about accounts being disabled [S102} but the accounts and the shadow accounts are all enabled. If the user tries a few times in short succession it lets them in. Any ideas?.
My suspicion is that Citrix Support would need to examine CDF traces to determine the cause of the intermittent issue.
Were you ever able to get this resolved? Any indication of what the problem was? We are seeing the exact same behavior (also seeing Kerberos TGT rejections on the DCs.) Thanks!
Hi Carl,
Thank you for all the useful info you’ve provided on this site. I’m interested in using this for my environment, currently we’re using ldap auth. Since implementing FAS requires modifying storefront and vda to accept saml and certificate auth, will this affect ldap auth or will these new settings simply get ignore if its not being used? In other words, if i create two different auth policy on the Netscaler (ldap and saml) can the two auth methods co-exist on the same storefront and VDA?
Thanks!
Once FAS is enabled on a StoreFront server, it will create certificates for every user of that StoreFront server. I typically create separate Stores for each FAS and non-FAS.
Hi Carl,
Can I create two separate stores on one Storefront server – one FAS enabled and one NON-FAS or will enabling FAS affect all stores on the server?
Thanks
I think it is per-store.
Hi Carl
I want to integrate Netscaler SAML authentication with Azure AD, i have 3 customer each one of them has Azure AD.
Can i create SAML authentication policy for each customer with SAML idp server ? pls note i have only one netscaler here.
Each customer has his own citrix Farm at the backend.
If users go to the iDP first, then you might be able to bind multiple SAML SP policies to the NetScaler Gateway.
However, if the user goes to NetScaler Gateway first, then NetScaler might not know which iDP to redirect the user to.
Thank you for your answer, how can i do that in the way the users go to the iDP first ?
In Azure AD, create the NetScaler Gateway SP application. Users go to the Azure AD portal and there should be an icon for NetScaler gateway.
Hi Carl
Can you please send me citrix document which shows me how o create Netscaler SP in Azure AD .
Thank you in advance
Best Regards
Basem
https://stealthpuppy.com/netscaler-azure-ad-conditional-access/ has info on how to add an App to Azure AD.
I plan to use PingFederate services (with SAML Browsing) to authenticate my users during the netscaler access process. Is the FAS required in this case ? what will happen if i don’t install FAS ? the VDA logon won’t be SSO passtrough ? Will i get a prompt to reenter a username/pwd on the XA/XD workloads ?
Without FAS, the VDA will prompt the user to enter username and password. This is the password for the shadow account, not the iDP account.
Hi Carl, in Step 11 under ‘FAS Group Policy’ section, I think you need to add FAS, VDA and SF servers from Domain B to Windows Authentication Group in Domain A as per CTX220497….. not Domain B.
Which brings the obvious question – how can step 11 be accomplished without a 2 way trust in place? If 2 way trust is needed, why bother eith FAS then?
Kind regards
Quazi
Thanks for pointing that out. It should be updated now.
I suspect the multiple domains in this case pertains to the shadow accounts being in a different domain than the Citrix machines.
Hello Carl,
I have the following environment:
1) Domain A, where our office users reside. This domain only has the local user workstations which run Citrix Receiver with SSO configured. Domain A also has ADFS v4 (WIndows Server 2016) which is used as SAML IDP. We need to have users logging in to domain A to be able to SSO to our XenDesktop 7.15 LTSR VDAs which are deployed in domain B (see below).
2) Domain B, where we have a XenDesktop 7.x delivery site, with 7.12 delivery controllers, 7.15 LTSR storefront servers and 7.15 LTSR VDA. We also have separate Citrix FAS server configured (latest version from VDA LTSR 7.15 binaries) and working with domain B PKI infrastructure (WIndows Server certificate services enterprise root CA). We have Netscaler VPX 10.5 configured with Netscaler Gateway, which is used as SAML SP.
The issue is the following:
==========================
When a user logs on to their local machine in domain A, they open a Web browser and point to the URL of Netscaler Gateway. They are automatically logged on to Netscaler Gateway via SAML and the the Storefront page is shown where the user can click on a published desktop. When the desktop is being launched, it gets all the way to the VDA machine, where the Windows Server LogonUI is shown but user does not get automatically logged on, screen stops at VDA logon. It seems that the necessary user certificates are not automatically populated, even though there are no errors in the FAS server. Even if we populate the user certificates via Powershell, the logon still stops on the VDA LogonUI screen.
I have checked event logs on DDC, VDA, Storefront, FAS and PKI servers without any apparent sign. Any ideas on what else I could be checking?
Thank you Carl for the great article on Citrix Federated Authentication Service!
Hi Carl,
Is there any way to integrate Netscaler with multiple Azure AD account, My scenario is using only one VIP with multiple saml policy for external Auth, group A has its own SAMl policy and their own Citrix ( Storefront, Delivery controoler, VDA ..) and group B has the same as group A, is there any way to tell the netscaler which saml to use for authentication if the user come from Group A, or Group B ?
Thank you in advance.
Kindest Regards
Basem Shalabi
Maybe if iDP initiated since I don’t think Citrix has an easy way to allow users to choose an iDP without using multiple FQDNs. Then maybe you would need Default Syntax Session Policies with expressions like http.REQ.USER.LOGIN_NAME.SET_TEXT_MODE(IGNORECASE).CONTAINS(“myupnsuffix.com”) to select the correct Session Policy for each iDP.
Thank you Carl, i did not find that expression from the expression drop down list , Can i add this expression at the SAML policy level ?
Thank you.
Default Syntax for Session Policies requires NetScaler 12. The expression would only work after a login has been performed, not before.
You could use HTTP.REQ.URL.HOSTNAME.EQ(“idp1.myurl.com”) to select a SAML Policy based on a unique FQDN. This implies that the certificate matches multiple FQDNs. And assumes Default Syntax Authentication Policies (nFactor) instead of Classic Expression.
I’m having issues when accessing storefront from a IDP. I get “cannot complete request”. From the event log on Storefront I get two errors:
Access is denied. Contact your system administrator.
Citrix.DeliveryServices.Security.Claims.Specializations.Fas.MissingUpnException
Followed by:
A CitrixAGBasic Login request has failed.
The remote server returned an error: (403) Forbidden.
Url: https://127.0.0.1/Citrix/samlAuth/CitrixAGBasic/Authenticate
I belive that the SSO from netscaler to storefront is the problem. I have checked my session policies multiple times. There is a CS(content switch) in front of the Netscaler vserver.
One of your StoreFront servers should have an event indicating an issue with the Callback URL.
Or, in StoreFront Console, go to Stores. in the middle, right-click your store. Click Manage Receiver for Web sites > Configure > Advanced. The third line is “loopback”. Change the drop-down from On to OnUsingHttp.
In case anybody else is having the same issue:
Mine was caused by me copying an existing session policy with SSO domain filled from before. I had to enable the field and clear it’s contents, then save. To have Netscaler SSO to Storefront.
Hi Carl
I made FAS working and was able to startup published desktop and apps (WS 2016, XA 7.15). But now it stopped and I get the message “wrong username or password” at the login (blue background of WS 2016, NOT a blue screen).
I verified FAS and see the certs with the PS command.
Any hint where I can look into?
Thanks
Udo
Solved it by removing the cert on FAS and revoke it on the CA. thx 🙂
So I still get this error when starting published applications. NO problems when starting the published desktop.
Any hint?
I have to add… now also the publ. desktop has the problem again. That’s really weird.
So I found out that 2 of 3 VDA have this problem. When I connect to the first, everything is working fine all the time (publ app and desktop). VDA 2 and 3 showing this error every login.
So I double-checked the FAS rule and the list of VDA includes all 3 VDA and rule is set to apply. I removed VDA 2 and 3 and re-added them but still no success.
They are in the correct OU that gets the GPO that enables FAS? Check HKLM\Software\Policies\Citrix and somewhere under there is the FAS address.
Argghhh – you made my day! The GPO was not linked to the correct OU. I worked with FAS earlier this year and only adjusted the server name but not the linked OU.
Thanks a lot!
Udo
Didn’t hold that long… I can start published apps but with the desktop I’m getting the same error again.
Any hint?
Carl,
I was wondering in you knew if it was possible to store the FAS RA private key on and HSM and still store the smart card logon keys on the FAS server? If so, could you point me in the right direction of configuring this? Based on my research, its seems you have an all or nothing option on where to store private keys (FAS, TPM, or HSM). Thanks in advance
From Citrix: “You configure FAS to use HSM before getting the RA certificate, then change the config again to not use HSM.” See Example 2 at https://docs.citrix.com/en-us/xenapp-and-xendesktop/7-15-ltsr/secure/federated-authentication-service/fas-config-manage/fas-private-key-protection.html.
Thank you for all this information, it has been very usefull.
Do you happen to know how i can set the ‘Fully delegate credential validation to NetScaler Gateway’ option with powershell?
I ask because i have a storefront deployment with multiple iis sites so i can not use the console.
I figured it out, maybe usefull for someone else:
set-STFCitrixAGBasicOptions -AuthenticationService $auth -CredentialValidationMode Auto
Thanks for the hard work Carl,
Im having trouble wrapping my head around something. After I configure FAS and users are being logged into the VDA with certificates, when users access other service providers (within the VDA), such as office 365, or gmail, is SSO available? Is that where the Group policy setting “In-Session Certificates” comes in? We us Shibboleth as our idp.
Password is not available. If you need password for SSON, then it won’t work. But Kerberos should work fine (e.g. ADFS with Integrated Windows Authentication).
Thanks, one follow up question. Is FAS technically a requirement for SAML? Could I not just configure the Netscaler to be a service provider using the method described at the following link? https://support.citrix.com/article/CTX200271 .
With the understanding that Kerberos is still needed for SSO within the VDA.
FAS is needed if you want to SSON to the VDA. Otherwise, the VDA will ask the user to login to the domain with username and password.
Hi Carl,
An update: I checked old logs and it looks like the SP-init SLO never worked properly. I don’t see any instance where the NetScaler has sent a SAML SLO to PingFederate. Other then specifying the “Single Logout URL” in the NetScaler config, is there something else we need to do to enable SLO from StoreFront?
We tried to follow the aforementioned Citrix doc (https://support.citrix.com/article/CTX200392), but its unclear where to bind the TM action/policy. Can you provide some guidance and/or links to docs on how to do that with NeScaler 11.1 and StoreFront 3.9?
Your help is much appreciated!
Thanks,
Jim
Hi Carl,
We are trying to configure SLO between NetScaler 11.1 and PingFederate. What wasn’t clear in Citrix documentation was what SLO endpoint to use on the NetScaler. I did find a Citrix support doc (https://support.citrix.com/article/CTX200392) that indicated a URL of: netscaler.com/cgi/tmlogout
Is that the correct URL? That support doc discusses SP-init SLO…does the NetScaler support IdP-init SLO? In our testing the SP-init SLO seems to work fine, but when we send a SAML SLO assertion to that same endpoint we don’t get a response…and the user’s session isn’t terminated in StoreFront.
Thanks,
Jim.
Hi Carl,
I’m planning to upgrade XenApp with latest version 7.14.1, also would like to upgrade SAML with latest one, Is there any upgrade docs for SAML?
Thanks,
AJ
You mean FAS? It’s just an in-place upgrade. No new features.
Thanks for the quick reply Carl.
Yes It’s FAS. Do I need to make any changes/upgrade on CA (Certificate Authority) server as well? Would you please help me upgrade sequence for XenApp 7.12 to 7.14.1?
This is what I’m planning: VDA -> Delivery Controller -> StoreFront
Thanks,
AJ
See https://www.carlstalhood.com/xenappxendesktop-upgrades/#7xupgradeoverview
Karl, I also ran the Verify FAS procedure above and FAS is generating certs. Can I assume if I am getting “The UserID or Password is incorrect” message, then the generated cert is not correct? Thanks.
Yes the GPO is applied.
Hi Carl
Thank you for article. i have configured Citrix FAS for citrix authentication. netscaler has configured with Azure AD idp . When i am trying to start Application i am keep getting windows Login Prompt. all delivery agent servers able to communicate with FAS and domain controllers, but the is no problem in application start for different VDAs which is located in different network segment.
Would you please advise
Thank you.
Karl, I get this message when I launch an app. I get a windows sign in screen with “The user name or password is incorrect”. I have looked for events on the S.F., FAS, and DC servers. Any ideas where to look? Thanks
There is a GPO that specifies the address of the FAS servers. Did you apply this GPO to the VDAs?
Carl,
So we cannot use Receiver for Windows with a FAS implementation?
Best Regards,
Chris
Is there a possibility to have two FAS servers ? build a loadbalanced FAS, just like any other component is HA in my Citrix,
Thanks,
Hi Carl
Can you use a Standalone CA (i.e., not an Active Directory integrated CA) in using FAS, as long as you add the cert of your standalone CA to the Trusted Roots store on your VDAs/Storefront servers?
Thanks
The Enterprise CA is needed to issue certificates for each user and link them to Active Directory users.
Hi Carl,
I am totally new to ADFS and would like to learn and get a better understanding of how it can be used for enabling users from Domain A (client domain) to be able to launch a XenApp or XenDesktop session in Domain B (resouce domain) the two domans do not trust each other. Both domains are in the same organization all be it they live in two separate network subnets with a firewall. Can I acheive this using the steps you have shown?
Thanks!
Yes. If internal only, then StoreFront has native support for ADFS and FAS.
Note: you must create accounts in Domain B for each of your users. The passwords don’t matter. The Domain B users are for authorization and identity mapping. What SAML does is avoid you having to synchronize passwords between the domains. And when you delete a user from Domain A, it can no longer be used to login to Domain B.
Thanks Carl for your quick reply. I take it I will first need to configure ADFS services on both domains before I proceed with the Citrix configuration steps? If so would you be able to suggest any good blog/guides for configuring ADFS.
You only need ADFS at the Identity Provider (where passwords are submitted).
So I need only need to configure ADFS in the resource domain. Or is it the client domain which is where the identity and passwords will be provided from? I can’t seem to get my head round this one 🙂
ADFS handles authentication (iDP).
Can we use GlobalSign CA not Microsoft CA with FAS?
I doubt it.
Can it automatically generate smart card certificates for windows interactive AD authentication? And can FAS tell it to generate those certs?
thank you Carl. I am not sure to be honest, we are using this: https://www.globalsign.com/en-hk/company/news-events/news-archive/082113-auto-enrollment-gateway-provides-automated-certificate-lifecycle-management/
Hi Carl,
After logging in ADFS opens with an error page. In eventlog:
Encountered error during federation passive request.
Additional Data
Protocol Name:
Relying Party:
Exception details:
Microsoft.IdentityServer.RequestFailedException: MSIS7065: There are no registered protocol handlers on path /adfs/ls to process the incoming request.
at Microsoft.IdentityServer.Web.PassiveProtocolListener.OnGetContext(WrappedHttpListenerContext context)
I can open /adfs/ls/idpinitiatedsignon.aspx and I see my relying parties. When selecting NetScaler Gateway I get Http/1.1 Service Unavailable
Any idea what this could be?
Thanks
Hi Mark,
have you been able to fix this issue with MSIS7065? I am facing exactly the same problem..
Thank you for your reply
This is a great article Carl. Question after i do the SAML authentication I can see the desktop and published apps. When i launch the application i get the desktop logon screen before federated authentication i was able to launch the app. Can you point me in the right direction.
Never mind i figured it out. My cert had some issues. Now all is good. Thank you.