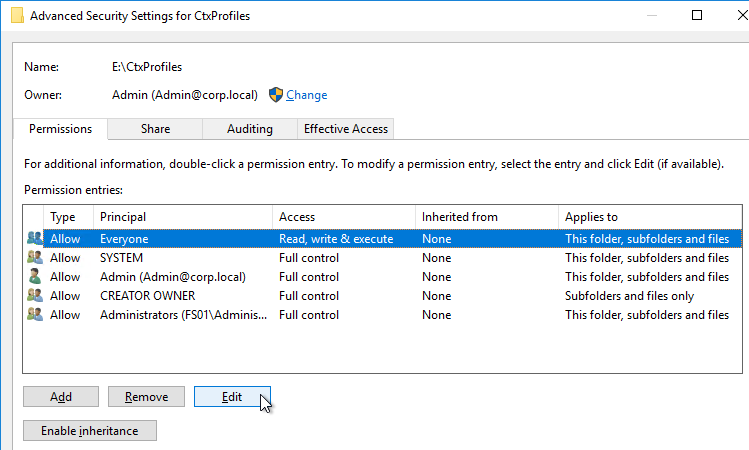
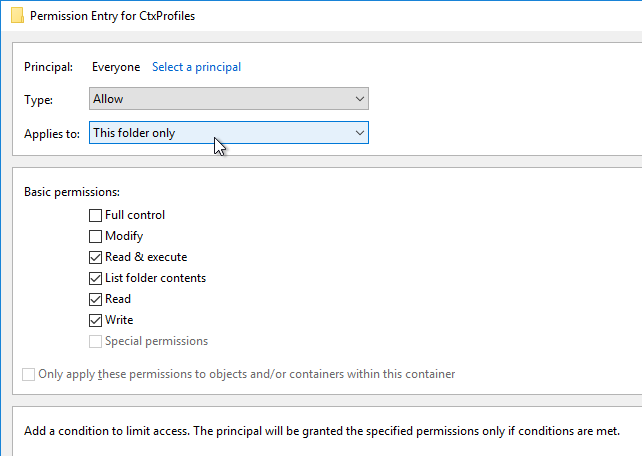
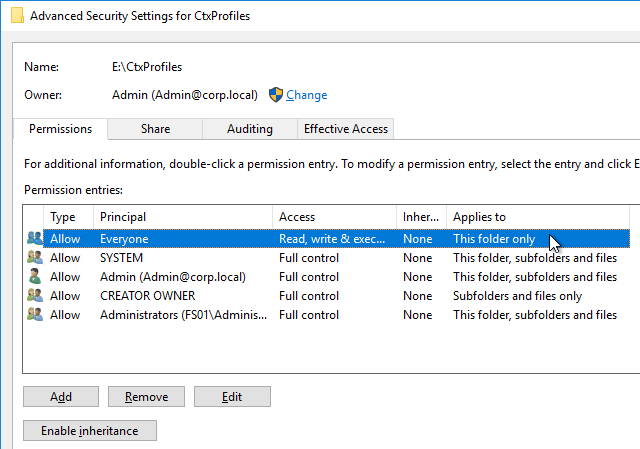
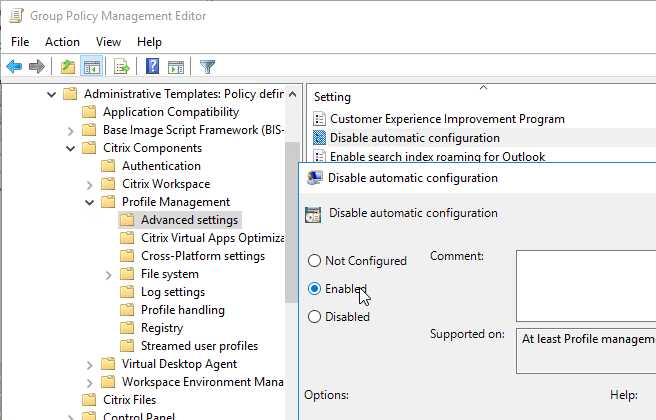
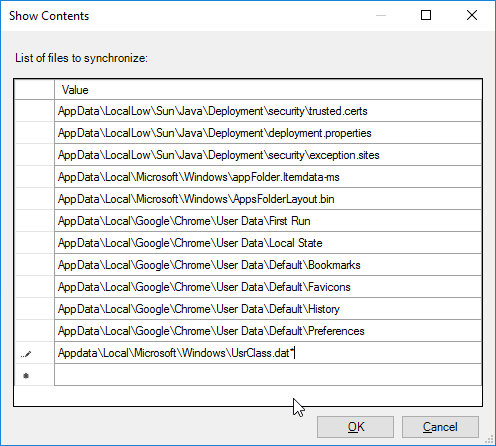
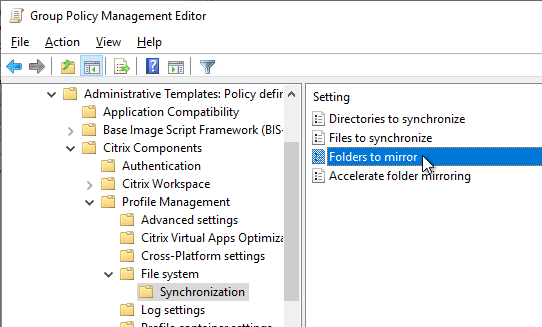
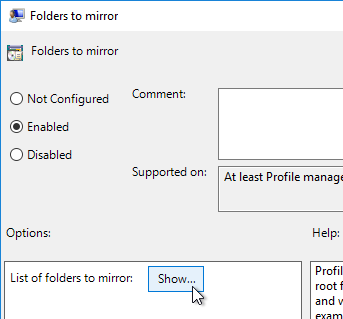
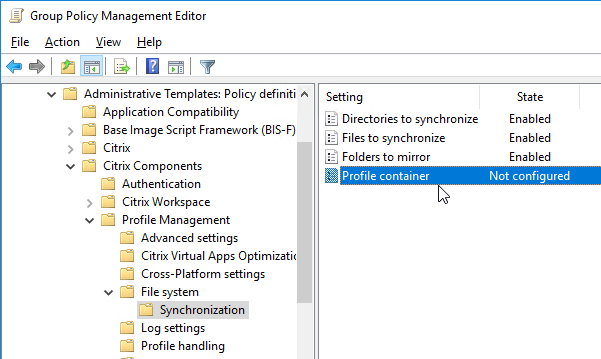
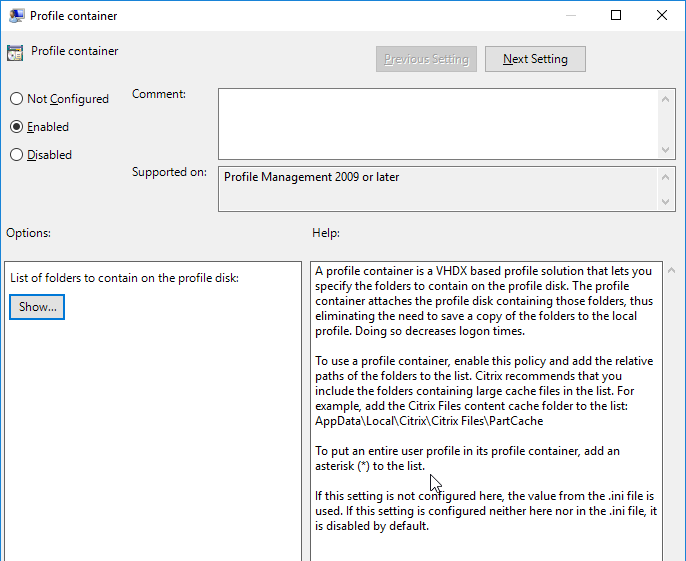
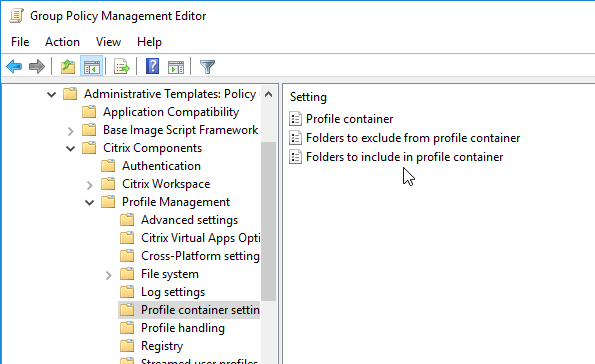
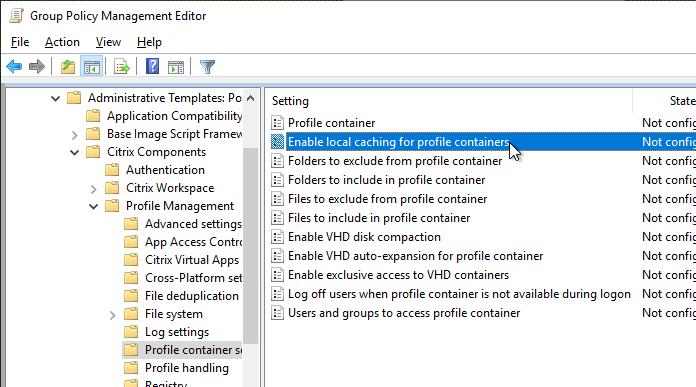
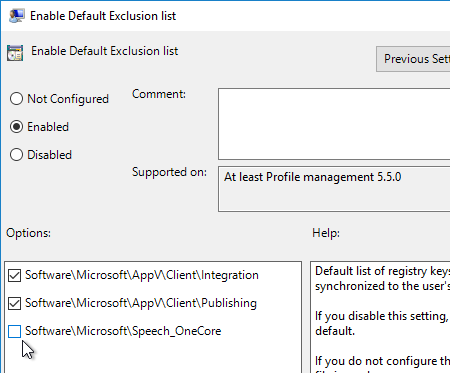
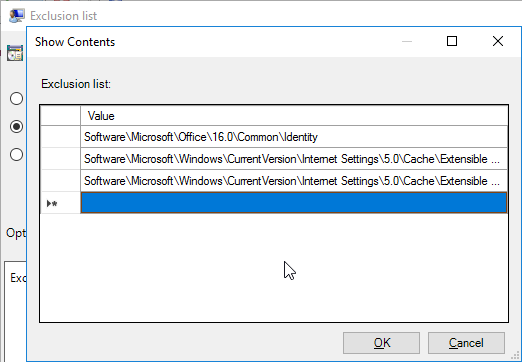
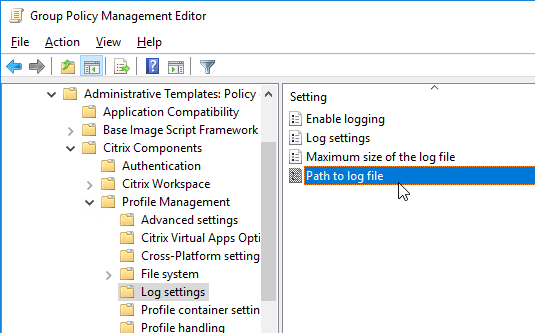
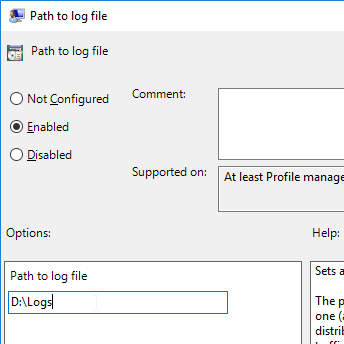
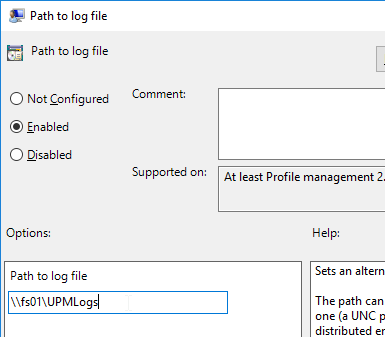
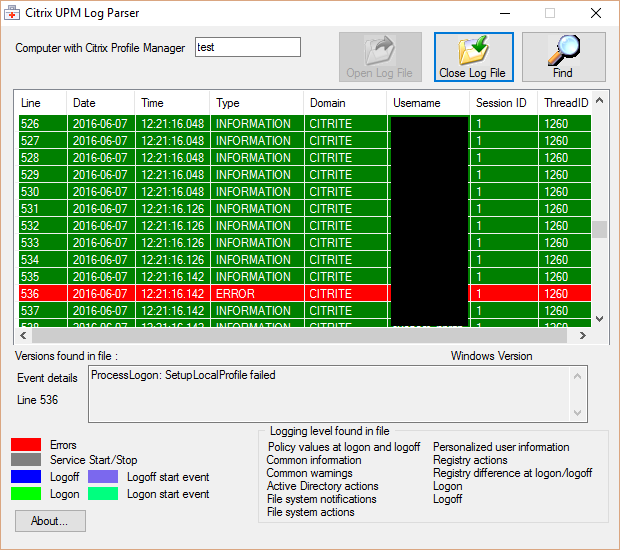
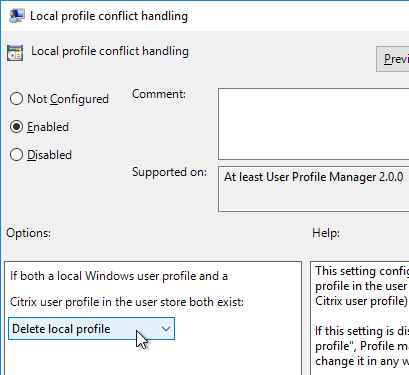
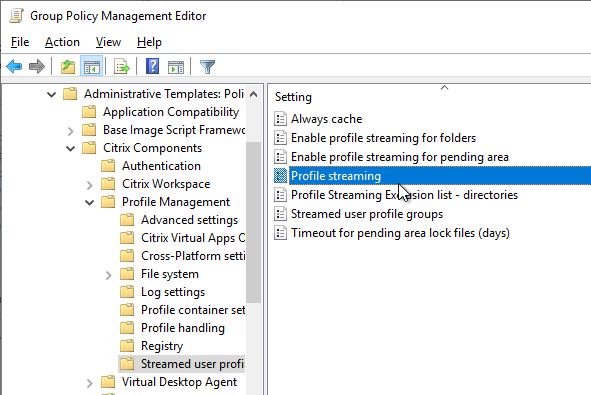
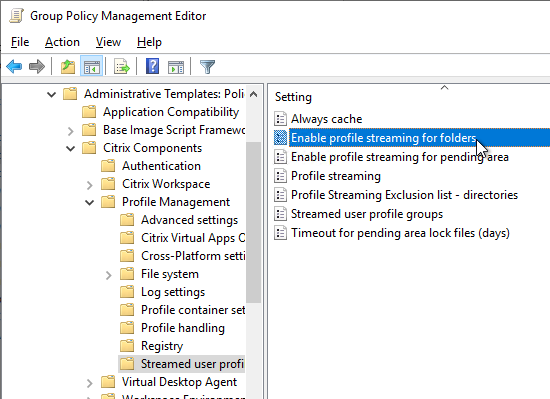
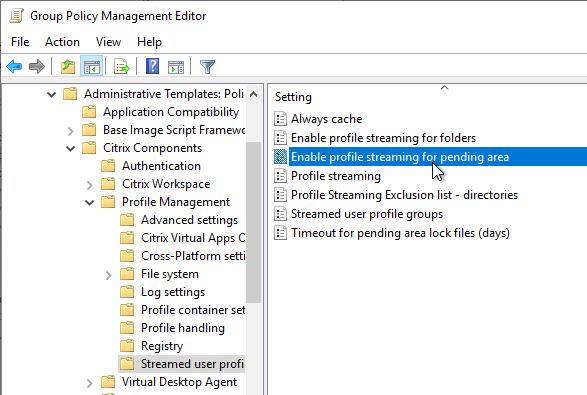
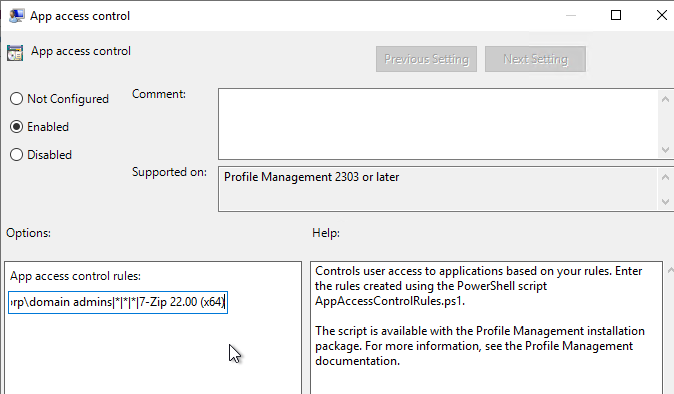
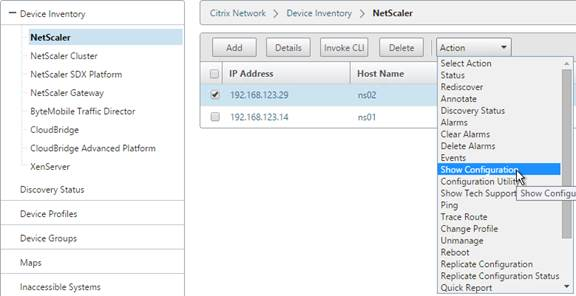
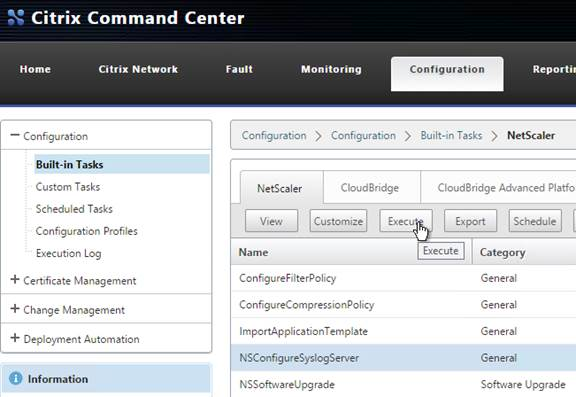
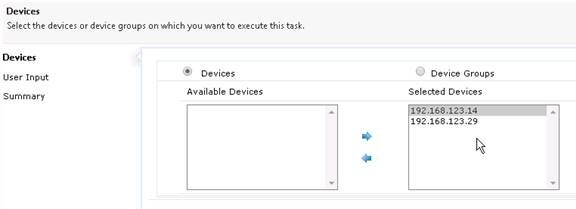
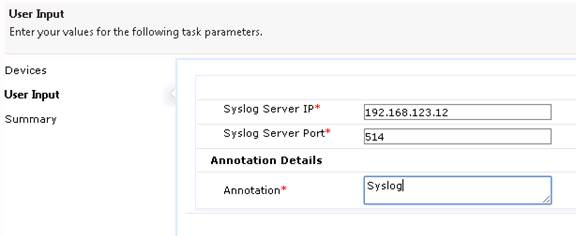
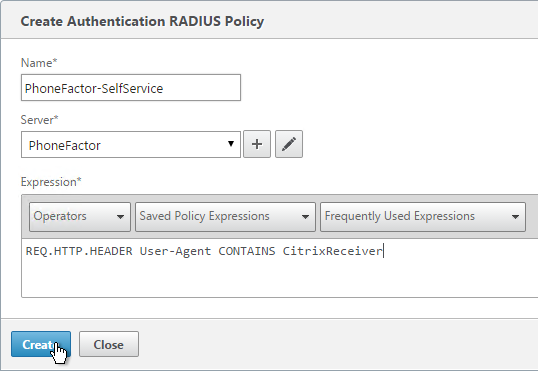
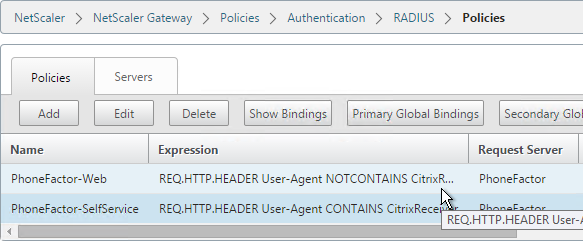
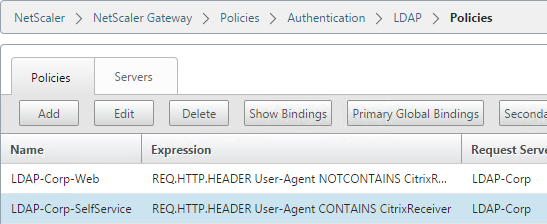
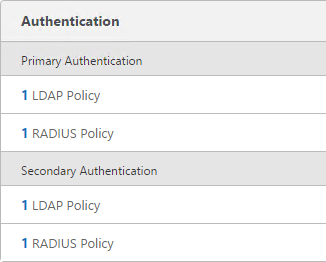
Navigation
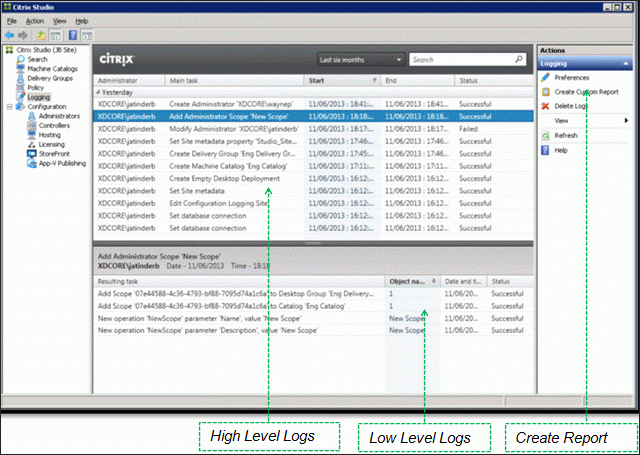
- Change Log
- Catalogs / Delivery Groups
- RDSH Application Testing
- Application Groups (CVAD and XenApp 7.9 and newer)
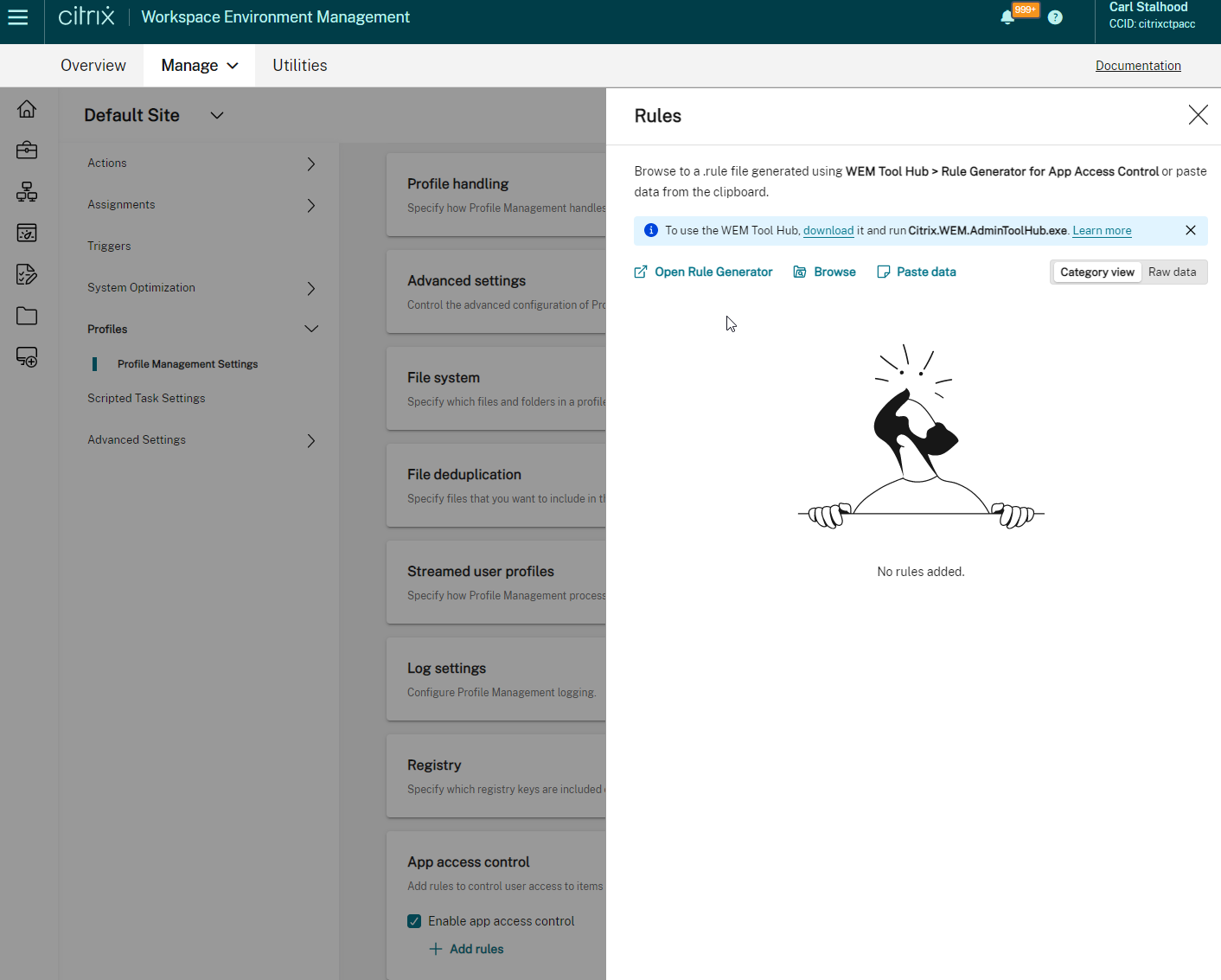
- Limit Icon Visibility based on AD Group Membership
- Published Content (CVAD and XenApp 7.11 and newer)
- Application Usage Limits
- Keywords for StoreFront
- Secure Browser
- App-V – hotfix, Citrix’s Share Method
- AppDisks
- Custom Published Desktop Icon
- Other Published App Tips – Chrome
- Hide Disabled Published Applications
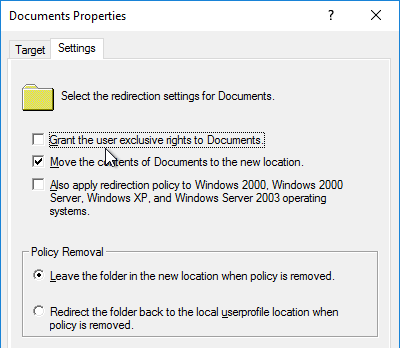
- Redirection:
- Browser Content Redirection (CVAD and XenApp 7.16 and newer)
- Bidirectional Content Redirection (CVAD and XenApp 7.13 and newer)
- Host to Client Redirection
- Local App Access (Reverse Seamless)
- Anonymous Apps
- Export/Import Published Applications
💡 = Recently Updated
Change Log
- 2023 Dec 22 – Bidirectional content redirection in CVAD 2311 is now configured using a JSON string
- 2023 Dec 22 – Publish packaged applications on single-session or shared desktop VDAs at Citrix Docs
- 2023 Oct 23 – Added link to Citrix CTX582697 Export apps setting and import by using PowerShell
- 2023 April 4 – Export/Import – added link to Citrix Docs PoC Guide: Automated Configuration Tool – On-Premises to On-Premises Migration
- 2022 May 17 – Export/Import – added link to CTP James Kindon Citrix Migration Scripts.
- 2021 July 21 – Export/Import – added link to Steven Lemonier Export and Import On-Prem Citrix Site configuration
- 2019 Mar 6 – Published Content – added link to Citrix Github’s GUI-based Citrix Content Publishing Utility
- 2019 Feb 22 – App-V Single Admin – added link to CTP George Spiers Launching App-V applications published through Studio on the same VDA
- 2018 Oct 10 – Export/Import – added link to Kasper Johansen Citrix Published Apps Migration Script
RDSH Application Testing
Installing apps on Remote Desktop Session Host (Virtual Apps or XenApp) is more complicated than installing apps on a single-user operating system (virtual desktop). Here are some RDSH-specific considerations that must be tested before integrating a new application into RDSH. These considerations usually don’t apply to virtual desktops.
- Multi-user Capable – can the application run multiple times on the same machine by different users? Most applications don’t have a problem, but a few do, especially applications that put temporary files or other writable files in global locations. For example, the first user of an app could write temporary files to C:\Temp. The second user writes to the same location, overwriting the temp files needed by the first user. Test the app with multiple users running the app on the same RDSH machine.
- Lockdown to prevent one user from affecting another – What restrictions are needed to prevent one user from affecting another? For example, if an app’s configuration files are stored in a global location, you don’t want one user to edit the configuration file, and thus affect a different user. Test the app with multiple users running the app on the same RDSH machine.
- Permission Relaxations – what relaxations (e.g. NTFS) are needed to allow non-administrators and GPO locked-down users to run the application? Test the application as a non-administrator with GPO lock down policies applied.
- First Time Use – when a user launches an application the first time, the application should be automatically fully configured with default settings (e.g. back-end server connections). Use group policy to apply application settings. Automated FTU also helps with a user whose profile is reset. Test the RDSH app with a user that has a new (clean) profile.
- Roaming – users could connect to a different RDSH machine every day, and thus user settings need to roam across machines. Test running the app on one RDSH, make changes, then login to a different RDSH machine to ensure the changes are still there.
- Application Licensing – if an application requires licensing, can licensed and non-licensed users connect to the same machine? Can it be guaranteed that non-licensed users can’t run the application that requires licensing? Adobe Acrobat is an example of a challenging application because of the global .pdf file-type association, and the global PDF printer.
- Client Devices (USB, printers, COM ports) – the client device mapping capabilities on RDSH are not as extensive as virtual desktops. For example, generic USB wasn’t added until Windows Server 2012 R2. When the application prints, does it show printers from every user, instead of just the user running the app? Does the app need COM port mapping?
- Shared IP – does the app have any problems with multiple users sharing the same IP address? If so, you might have to configure RDS IP Virtualization.
- Fair Sharing of Hardware Resources– does the app sometimes consume a disproportionate amount of hardware resources? For example, can the app be used to launch a task that consumes 100% CPU for some time? One option is to put this app on its own Delivery Group. Or you can use Citrix Workspace Environment Manager to ensure fair sharing of hardware resources.
- Published Application – can the app run as a published application that doesn’t have Explorer running in the background? Does the app (e.g. Internet Explorer web apps) need RunOnce.exe /AlternateShellStartup to fully initialize before it will run correctly as a published application? Some apps work without issue in a published desktop, but don’t work properly as published applications. When testing a published app, test it with a user that has a new (clean) profile. Connecting to the published desktop once will cause Active Setup to run, changing the user’s profile, thus distorting the published app testing results.
- Integration Testing – when installing a new app on a RDSH server, don’t forget to test the other apps already on the RDSH server, because the new app might have broken the other apps. The more apps you put on an RDSH server, the longer it takes to perform integration testing.
Also see MSDN Remote Desktop Services programming guidelines.
Some of the issues in this list can be overcome by using an application virtualization tool (e.g. Microsoft App-V) that runs apps in isolated bubbles.
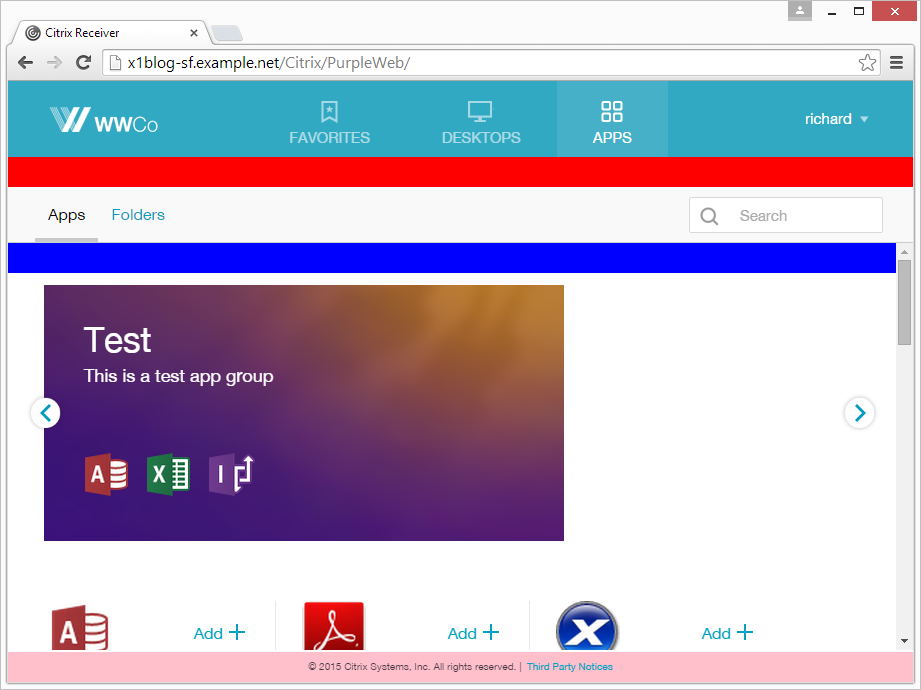
Application Groups
Citrix Blog Post Introducing Application Groups in XenApp and XenDesktop 7.9
Citrix Virtual Apps and Desktops and XenApp 7.9 and newer has an Application Group feature. This feature lets you group published apps together so you can more easily apply properties to every app in the group. Today, you can do the following:
- Control visibility of every app in the app group (Users page).
- Publish every app on the same Delivery Groups.
- Prevent or allow apps in different Application Groups from running in the same session.
- With one published app icon, test users launch from test Delivery Group, while production users launch from production Delivery Group.
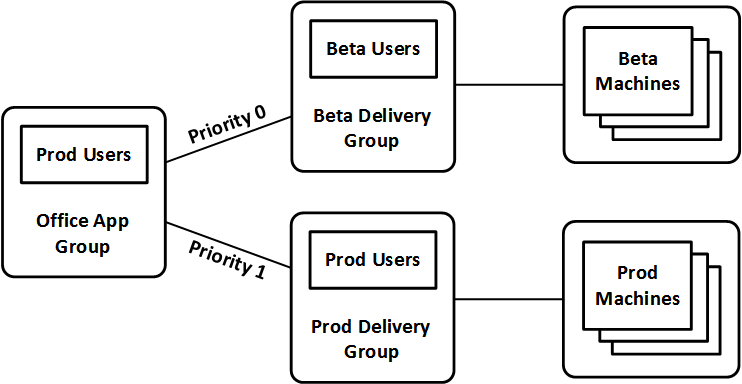
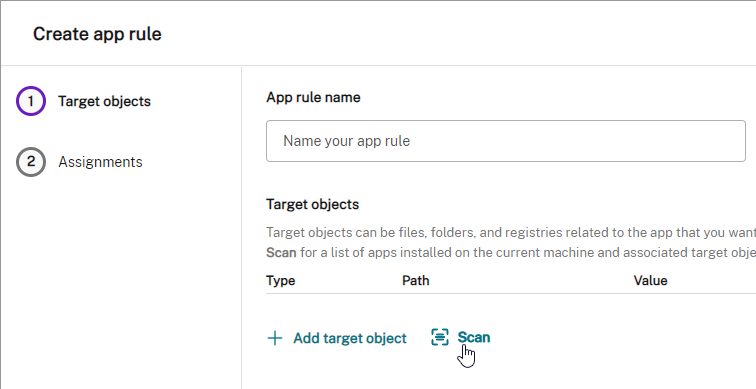
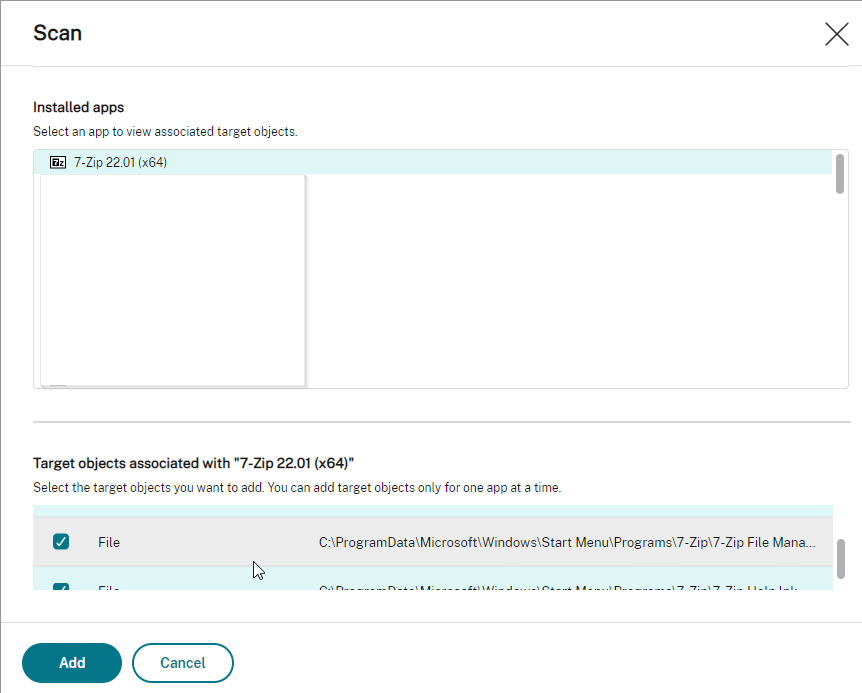
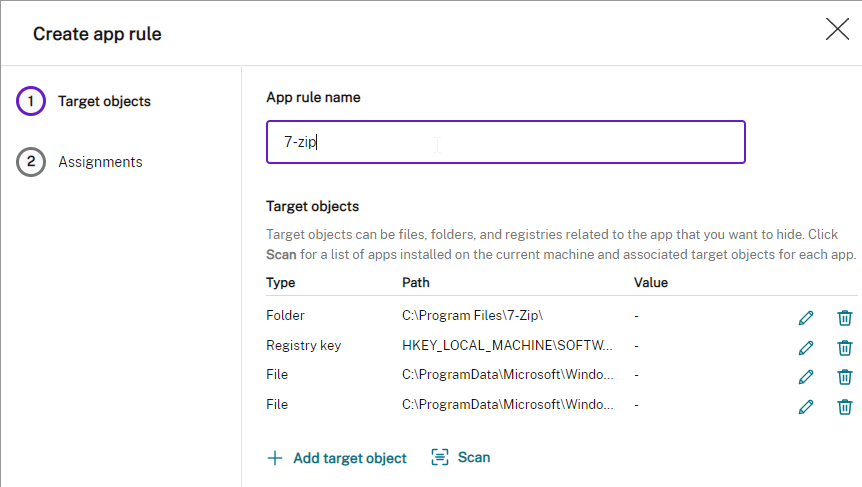
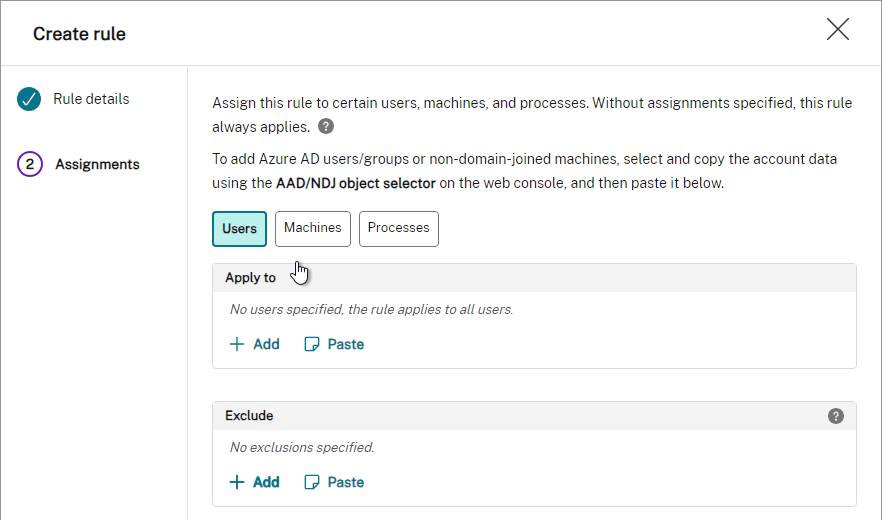
To create an Application Group:
- In Citrix Studio, right-click Applications, and click Create Application Group.

- In the Getting Started page, click Next.
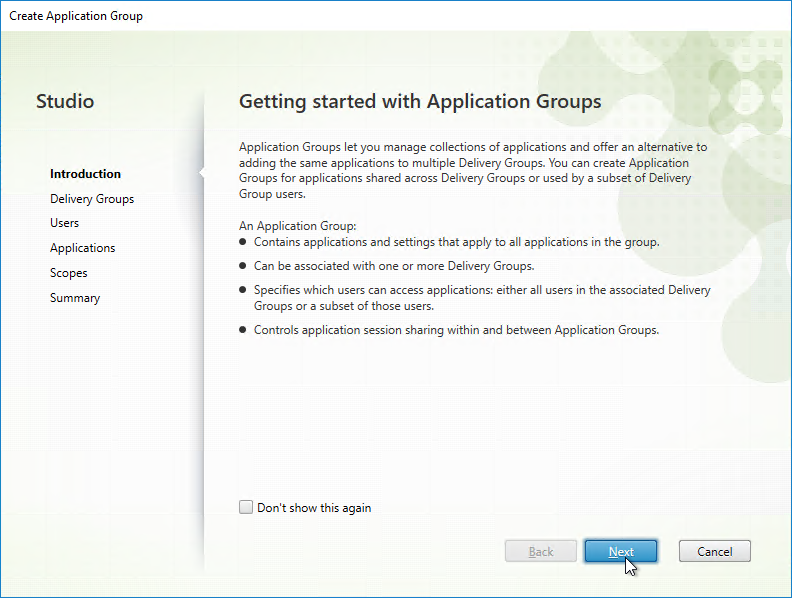
- In the Delivery Groups page, select the delivery groups you want these apps published from.
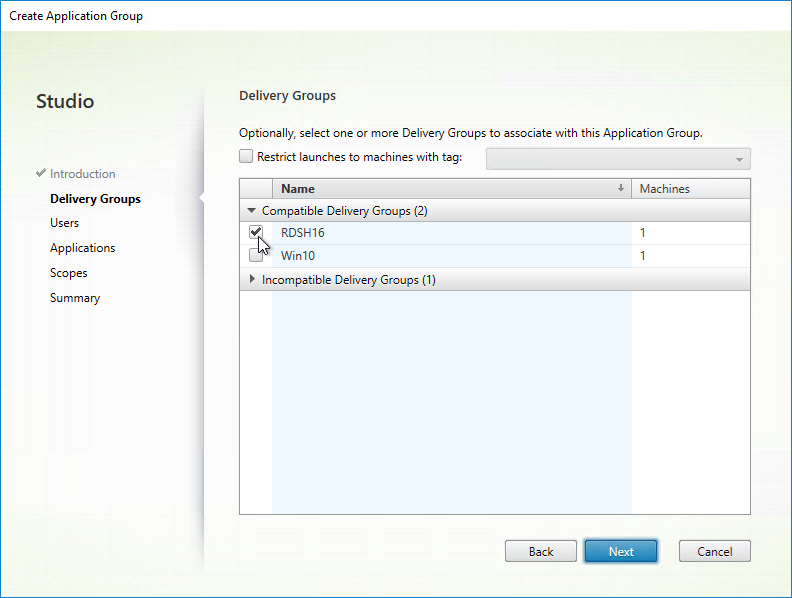
- In the Users page, select the users that can see the apps in this app group.
- Note: there are three levels of authorization. An app is only visible to a user if the user is assigned to all of the following:
- Delivery Group
- Application Group
- Individual Published Apps in the Application Group
- Click Next.
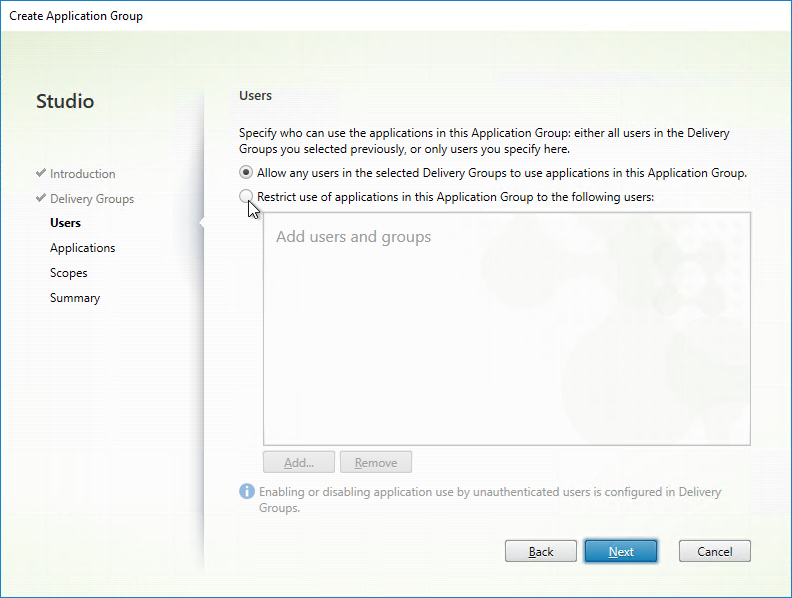
- In the Applications page, publish applications like normal. The Existing option lets you select an app that’s already been published to a different Application Group or Delivery Group. Click Next.
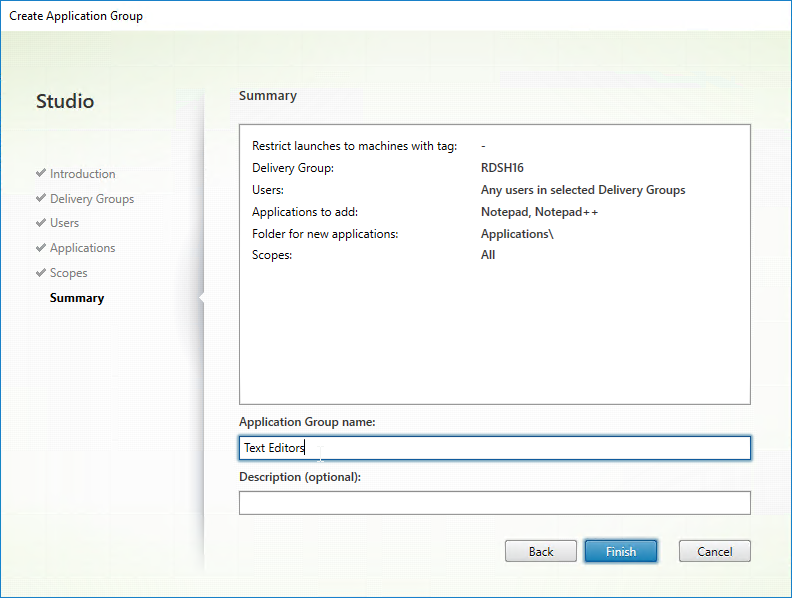
- In the Summary page, give the Application Group a name, and click Finish.
- In the Getting Started page, click Next.
- In the Applications node in Studio, there’s a new Application Groups section.
- If you highlight your Application Group, on the right is the list of apps in the group. You can edit each of these published apps like normal.
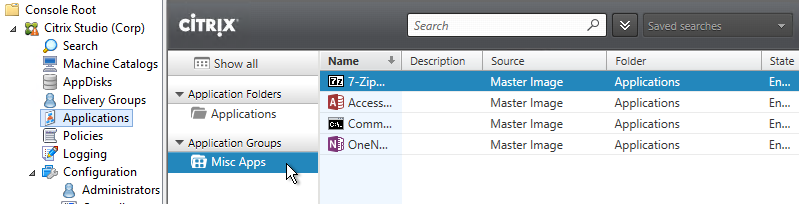
- You can drag applications into an Application Group.

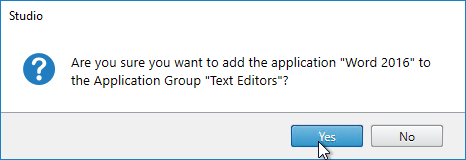
- However, this more of a copy than a move. To actually move the app exclusively into the Application Group, edit the individual app, and on the Groups page, remove all Delivery Groups (or other Application Groups). The app will instead inherit the Delivery Groups from the app group.
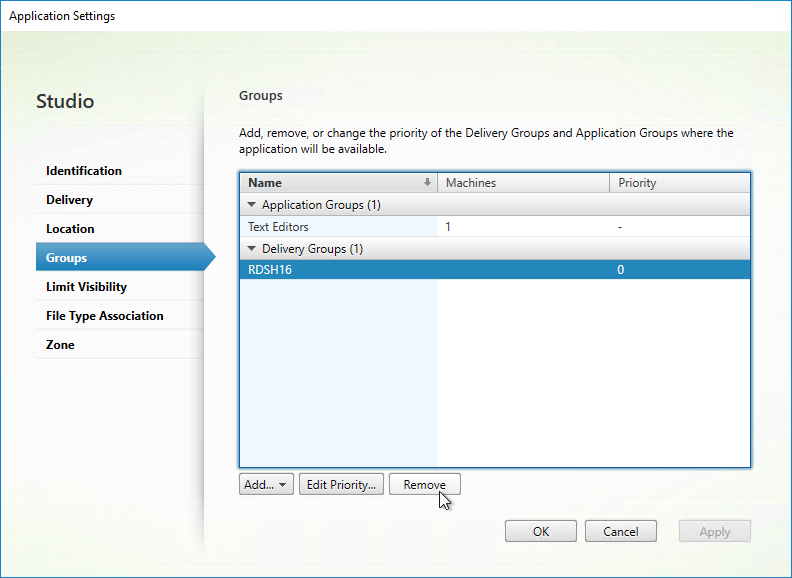
- If you edit the Application Group:
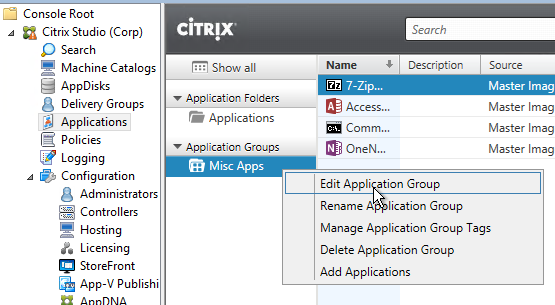
- The Settings page has an option for session sharing between Application Groups. Clearing this checkbox allows you to force applications in different Application Groups to run in different sessions.
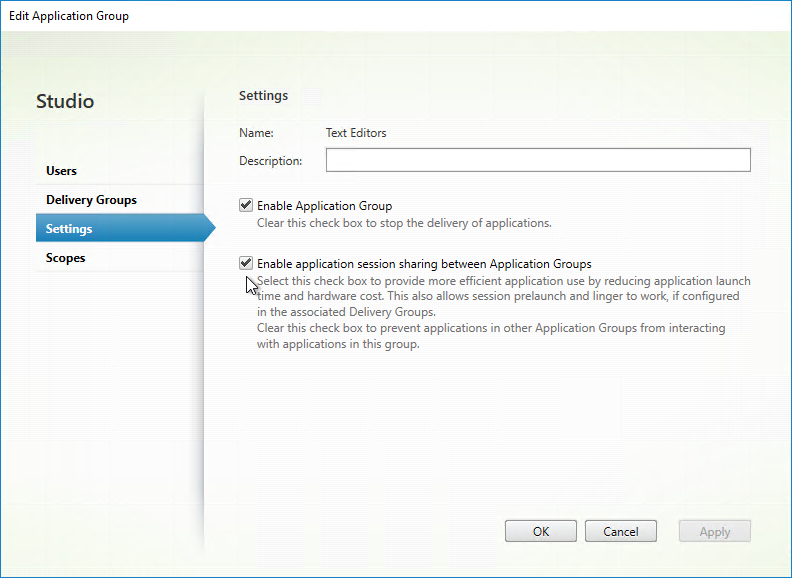
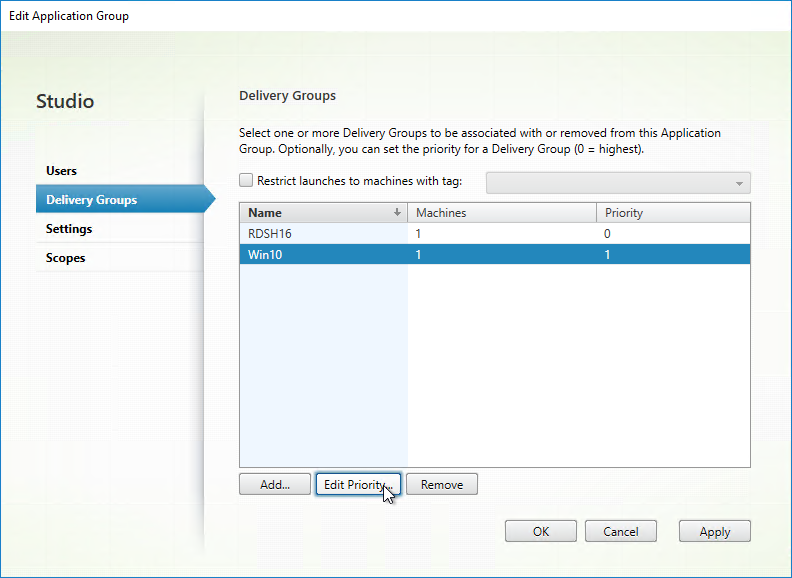
- The Delivery Groups tab lets you set Delivery Group priority. If priority is identical, then sessions are load balanced. If priorities are different, then sessions are launched on Delivery Groups in priority order.
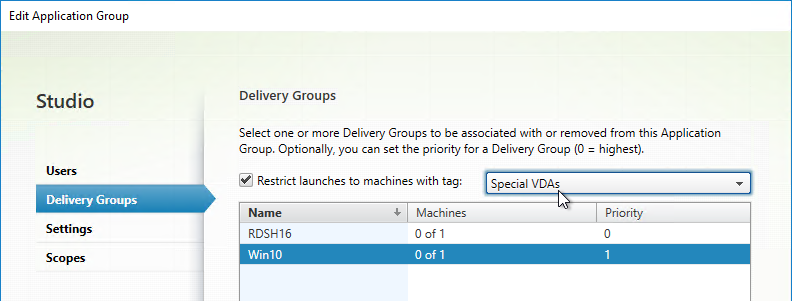
- The checkbox for Restrict launches to machines with tag lets you restrict the apps to only run on VDAs with the selected tag.
- In Citrix Virtual Apps and Desktops and XenApp/XenDesktop 7.13 and newer, you can use PowerShell to cause an Application Group to launch multiple app instances in separate sessions. Citrix Blog Post XenApp and XenDesktop 7.13: Launching an Application in Multiple Sessions.
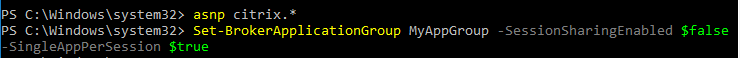
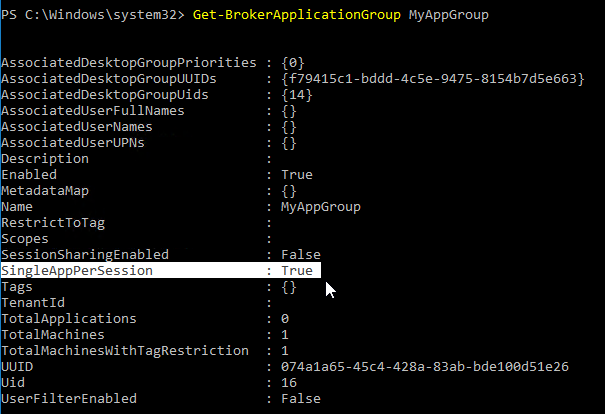
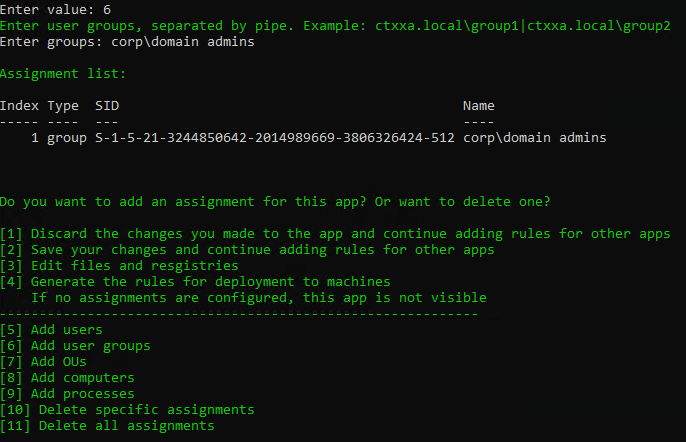
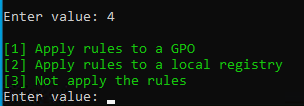
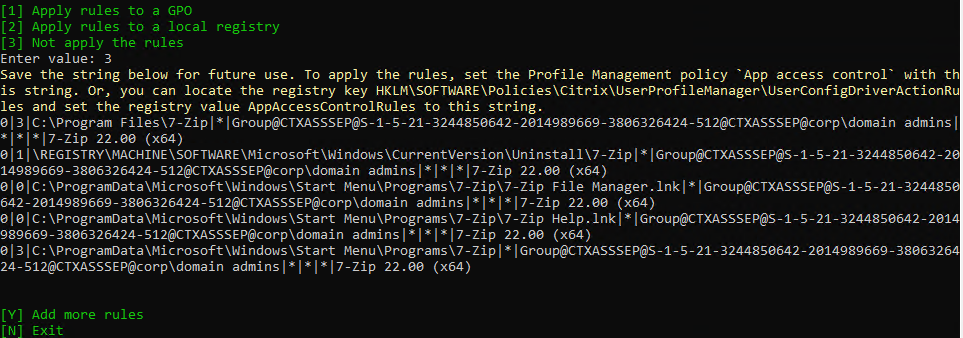
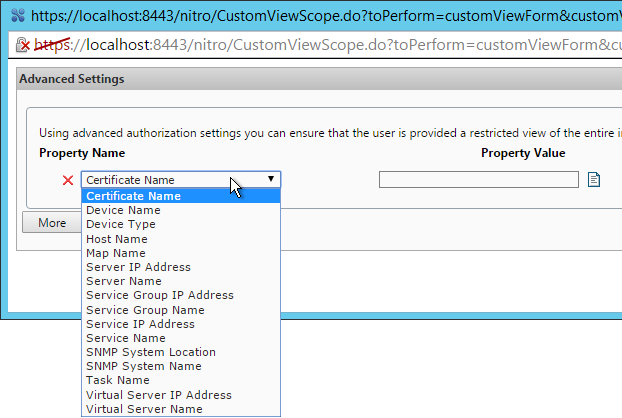
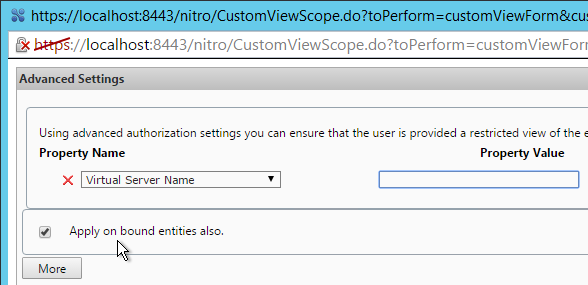
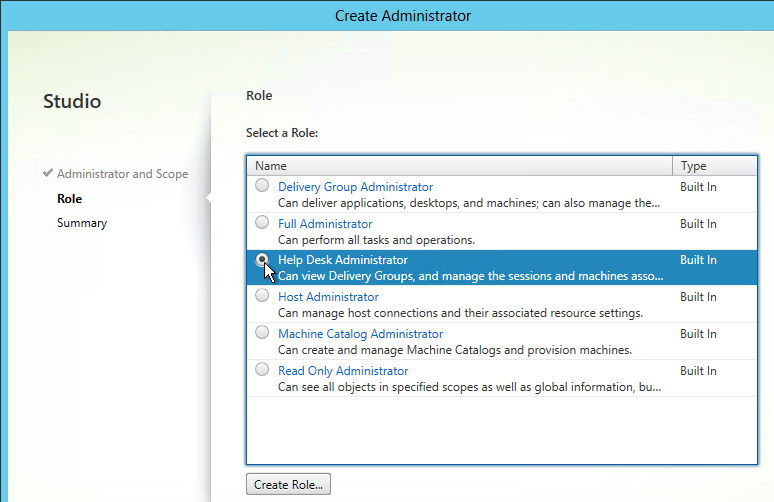
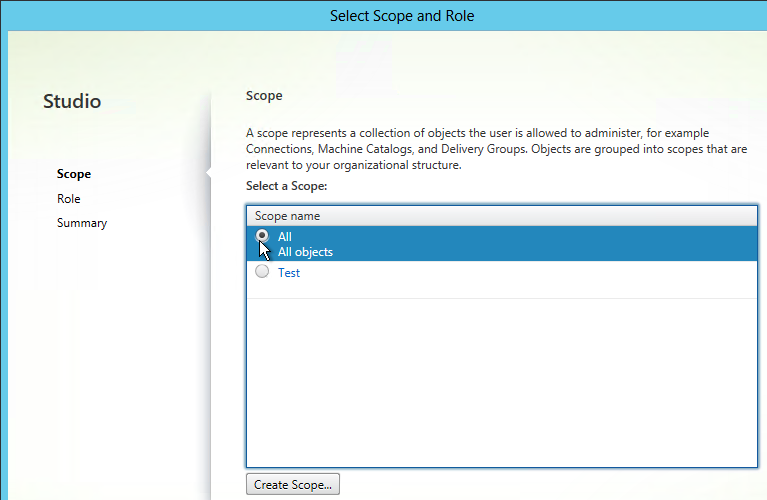
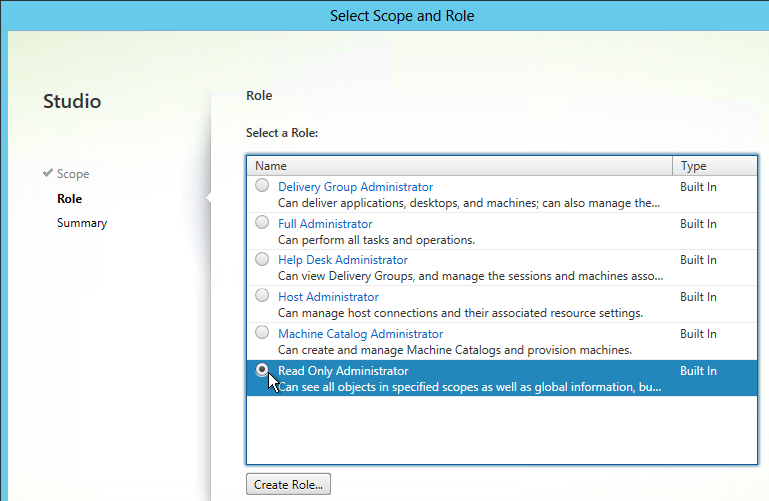
Limit Icon Visibility
For Published Applications, there are three levels of application authorization: Delivery Group, Application Groups, and Published App Limit Visibility. A published app icon is only visible if the user is added to all three levels.
- Delivery Group (Users page). If the user is not assigned to the Delivery Group, then the user won’t see any application or desktop icon published from that Delivery Group.
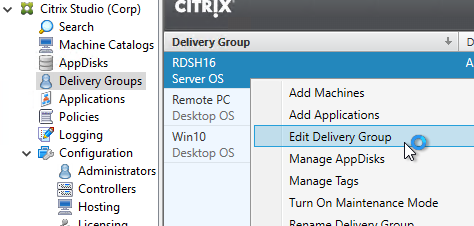
- Limit Visibility – You can use the published app’s Limit Visibility page to restrict an icon to a subset of Delivery Group users.
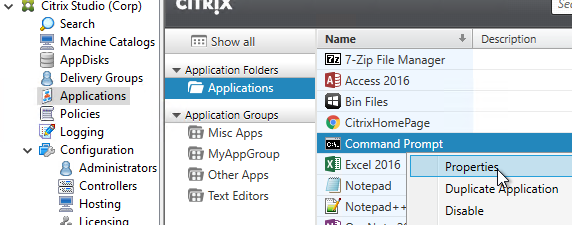
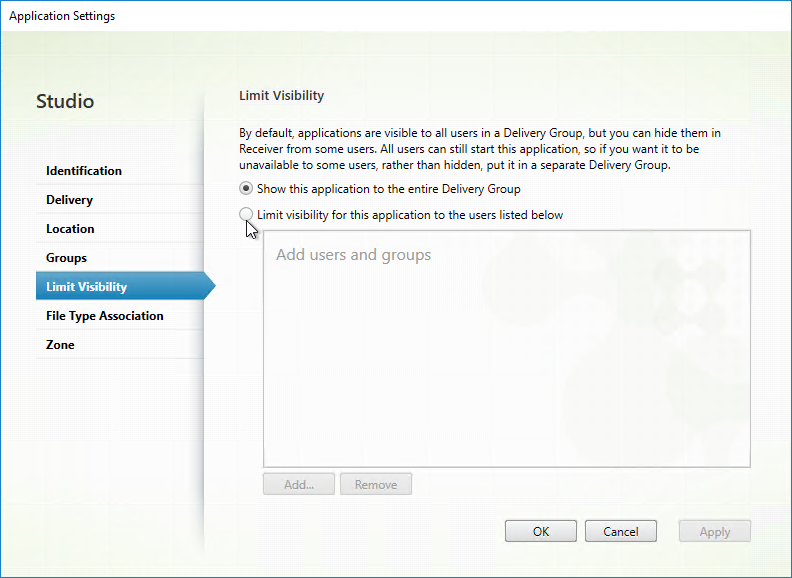
- In Citrix Virtual Apps and Desktops (CVAD) and XenApp/XenDesktop 7.9 and newer, you can use Application Groups to restrict access to published icons.
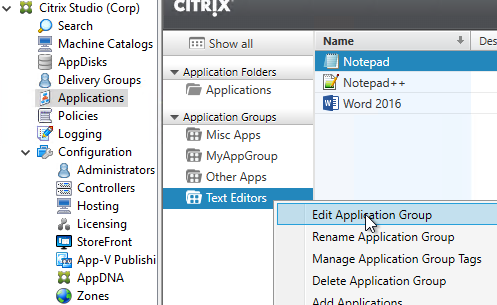
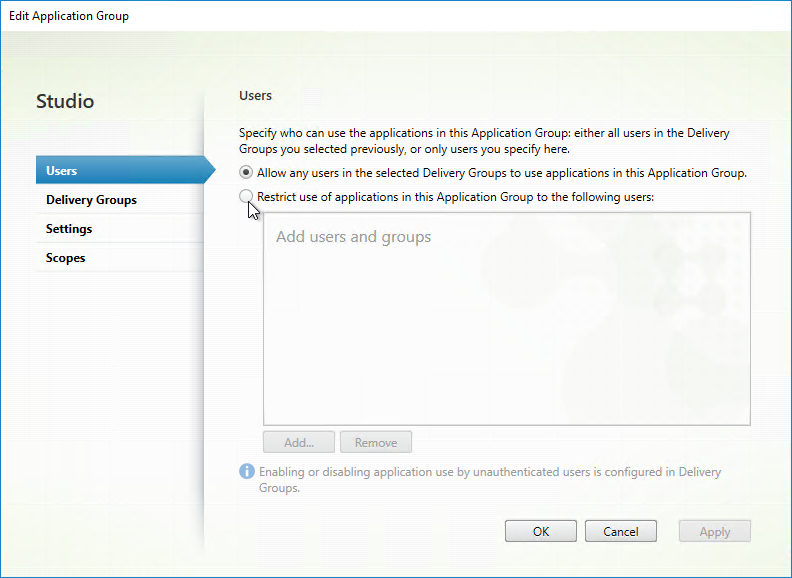
- App Icons won’t appear unless users are added to all three of the above locations.
Published Desktops have separate authorization configuration:
- Citrix Virtual Apps and Desktops (CVAD) and XenApp/XenDesktop 7.8 and newer have a Desktops page in Delivery Group properties where you can publish multiple desktops and restrict access to those individual published desktops.

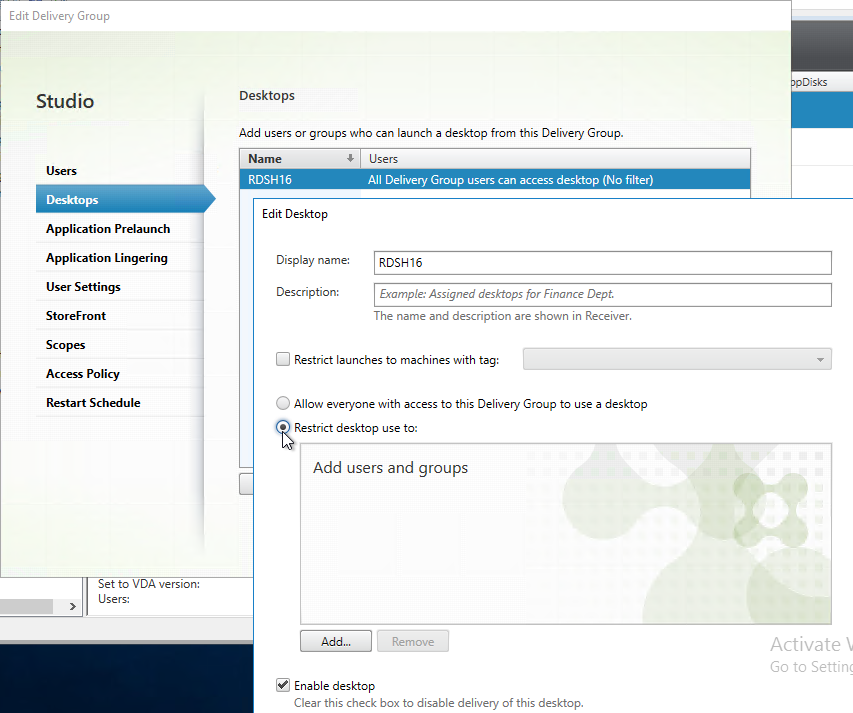
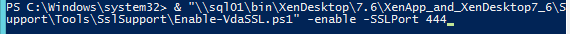
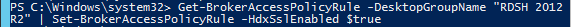
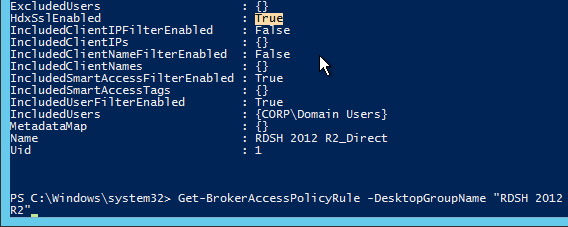
- In XenApp/XenDesktop prior to version 7.8, if a desktop is published from the Delivery Group, by default, every user assigned to the Delivery Group can see the icon. You can use the PowerShell command
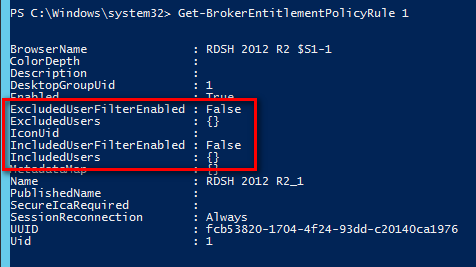
Set-BrokerEntitlementPolicyRuleto limit the desktop icon to a subset of the users assigned to the Delivery Group.- Run
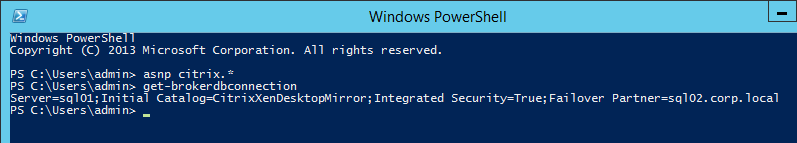
asnp citrix.* - Run
Get-BrokerEntitlementPolicyRuleto see the published desktops. - Then run
Set-BrokerEntitlementPolicyRuleto set the IncludedUsers or ExcludedUsers filters.
- Run
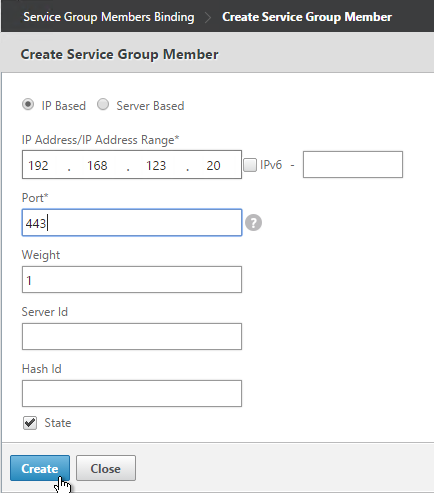
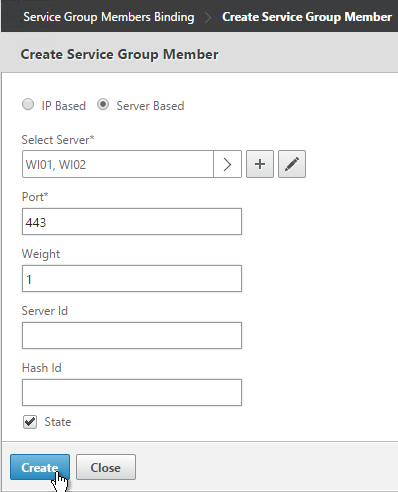
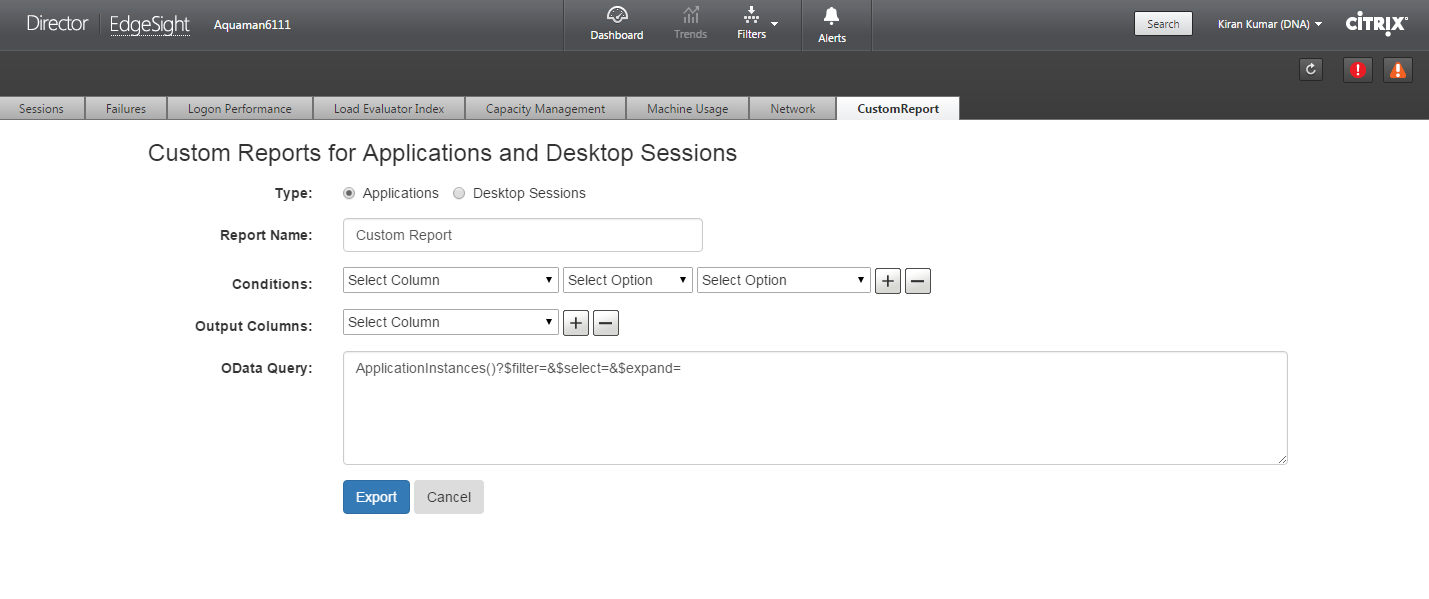
Published Content
Citrix Virtual Apps and Desktops (CVAD) and XenApp 7.11 and newer have Published Content where you can publish URLs that are opened in the user’s local browser. You can also publish UNC paths, which are opened with local Explorer or local application.
It’s not possible to publish content using Citrix Studio. Instead, use PowerShell.
- Citrix Github has a GUI-based Citrix Content Publishing Utility.
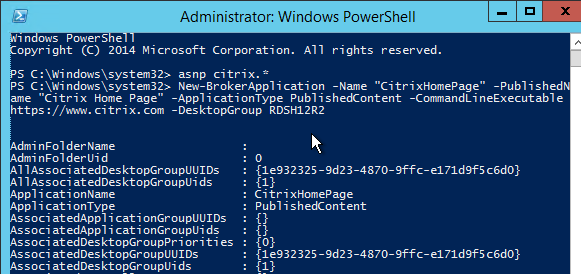
The New-BrokerApplication cmdlet requires you to specify a Delivery Group which must have at least one registered machine in it. However, the published content does not actually launch from the Delivery Group since the URLs and/or UNCs open locally.
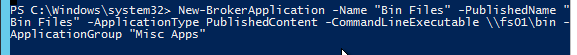
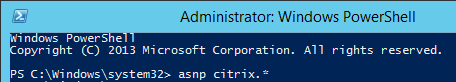
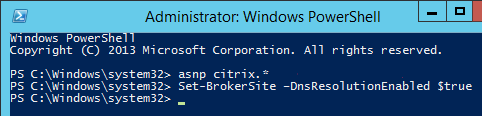
First run asnp citrix.*
Then run New-BrokerApplication -ApplicationType PublishedContent. Here is a sample PowerShell command:
New-BrokerApplication -Name "CitrixHomePage" -PublishedName "Citrix Home Page" -ApplicationType PublishedContent -CommandLineExecutable https://www.citrix.com -DesktopGroup RDSH12R2
Instead of publishing to a Delivery Group, you can publish to an Application Group by using the -ApplicationGroup switch. The Application Group must have Delivery Group(s) assigned to it.
Once the Published Content is created, you can see it in Citrix Studio. You can also edit it from Citrix Studio, including Limit Visibility and Groups (to move it to an Application Group).
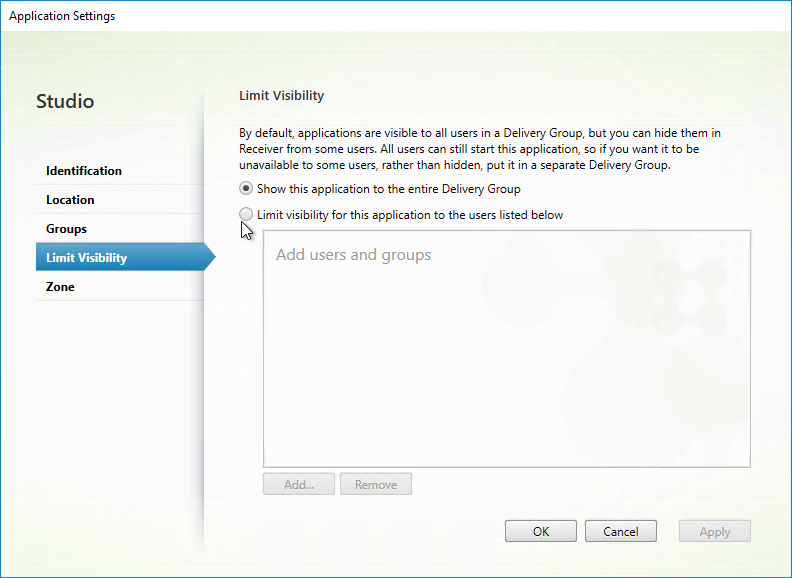
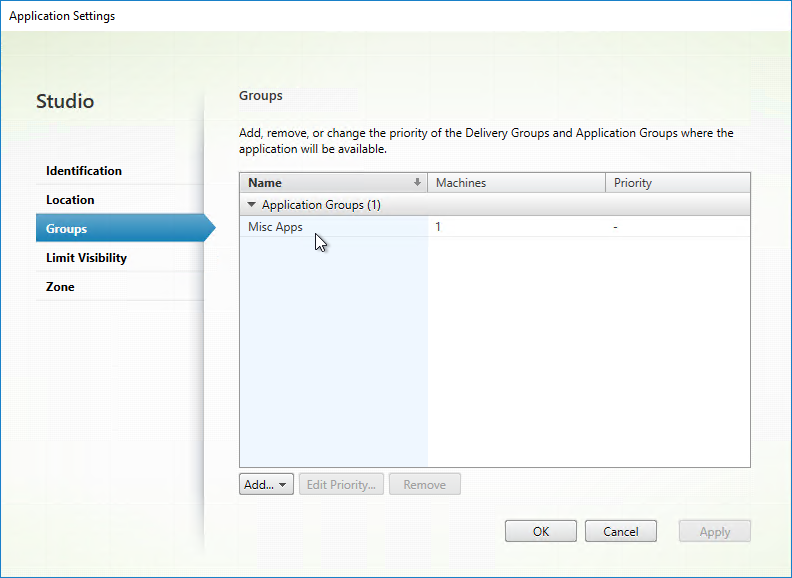
Published Content can be placed in Application Groups, which supports properties to restrict access to the shortcut.
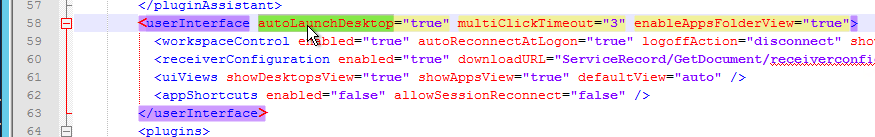
It does not appear to be possible to set the icon from Studio, but you can do it using PowerShell. See Citrix Blog Post @XDtipster – Changing Delivery Group Icons Revisited (XD7) for instructions to convert an icon to a base64 string, and import to Citrix Virtual Apps or XenApp using New-BrokerIcon -EnCodedIconData "Base64 String". Then you can link the icon to the Published Content using Set-BrokerApplication "App Name" -IconUid.
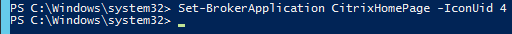
In StoreFront 3.7, you can click the icon and URLs will open in a new browser tab.

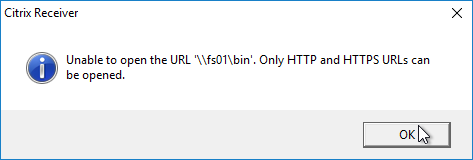
HTTP/HTTPS Published Content should open in Receiver. Other URLs (e.g. file:// or UNC path) will probably show an error message.
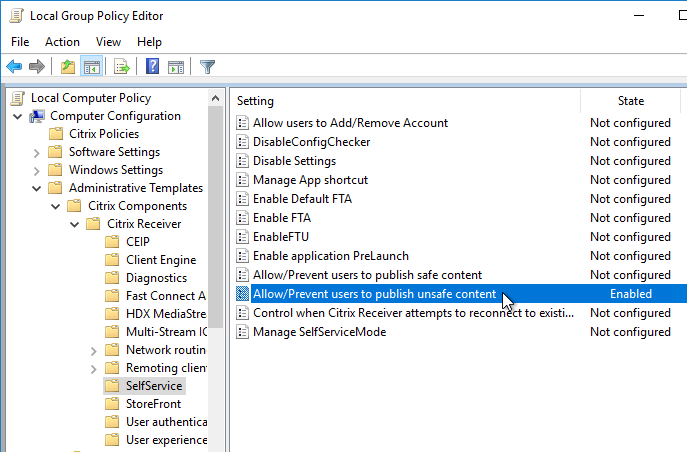
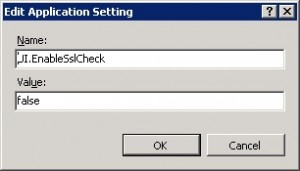
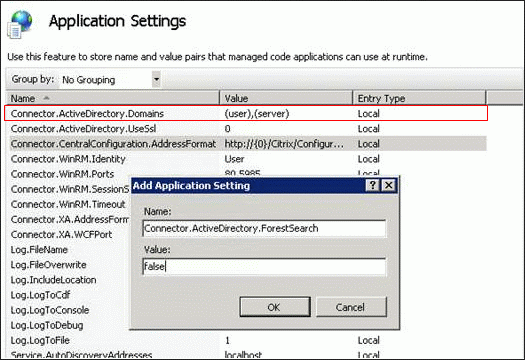
You can override this restriction by enabling the group policy setting Allow/Prevent users to publish unsafe content at Computer Configuration | Policies | Administrative Templates | Citrix Components | Citrix Receiver | SelfService. This assumes you’ve installed the Receiver .admx files. (h/t David Prows at CUGC forums).
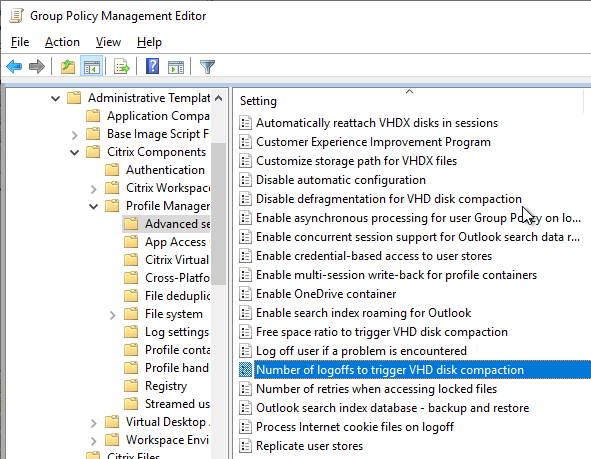
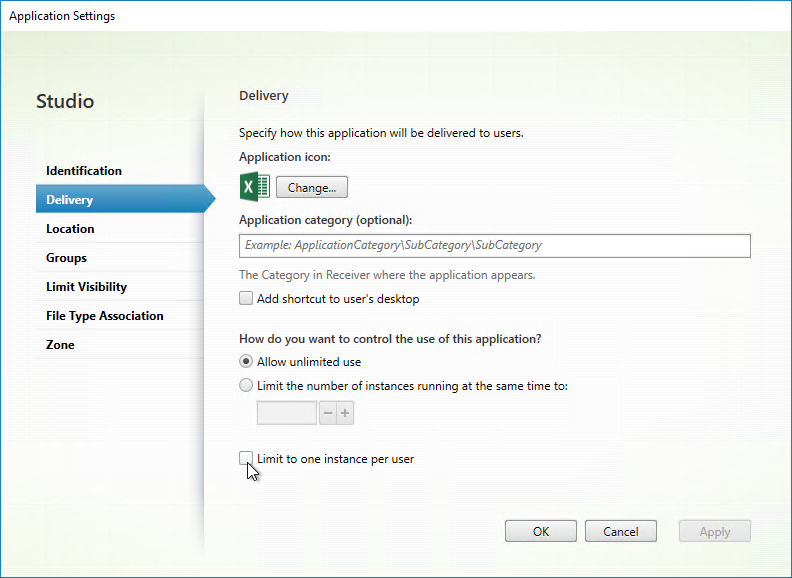
Application Usage Limits
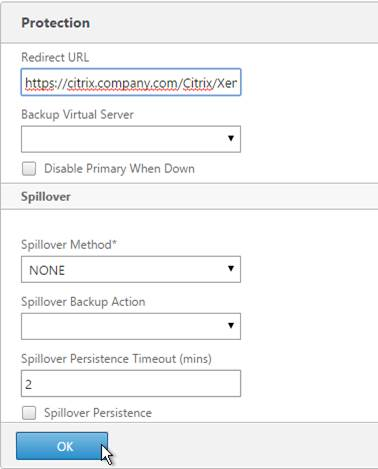
In Citrix Virtual Apps and Desktops (CVAD) and XenApp/XenDesktop 7.7 or newer, if you edit an application’s Properties, on the Delivery page, you can restrict the number of concurrent instances of the application. You can also Limit to one instance per user.
Citrix Virtual Apps and Desktops (CVAD) 1808 and newer support limiting the number of application instances per machine. This setting is configured using PowerShell. See Configure application limits at Citrix Docs.
asnp citrix.* Set-BrokerApplication MyApplication -MaxPerMachineInstances 2
To revert to unlimited per-machine instances of the published application, set MaxPerMachineInstances to 0.
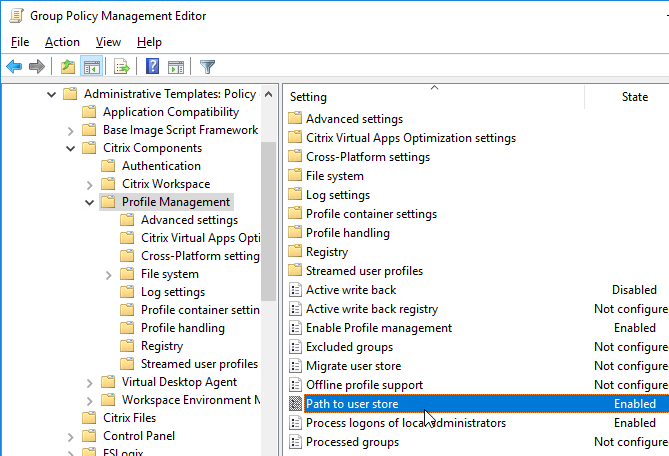
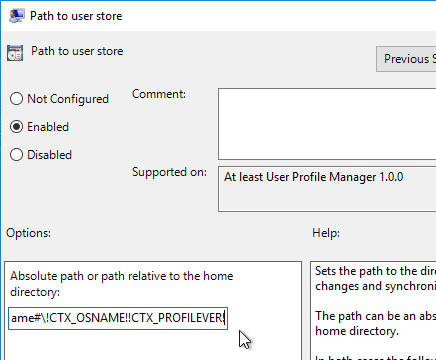
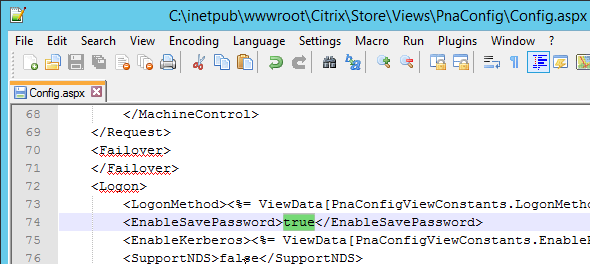
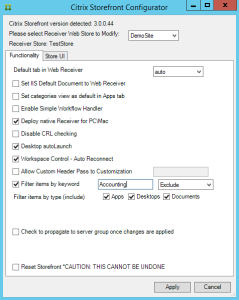
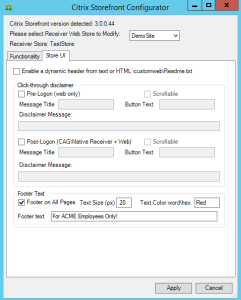
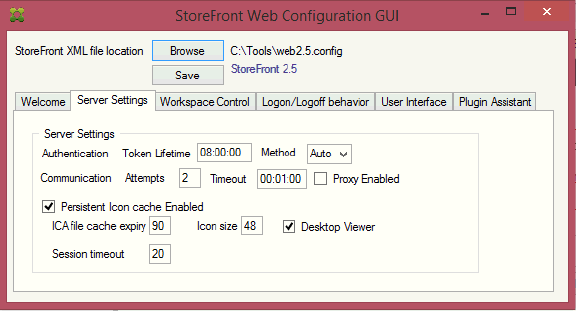
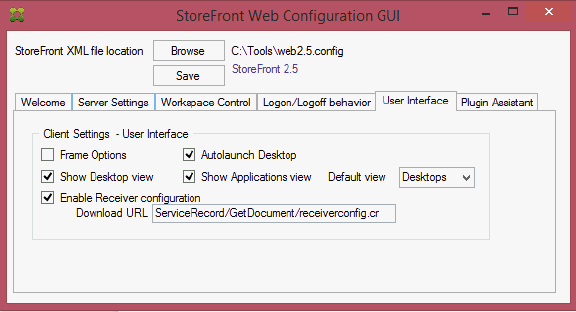
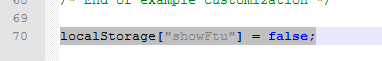
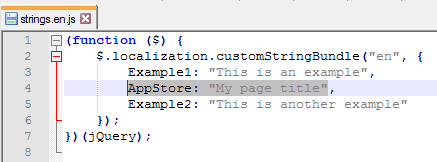
Keywords for StoreFront
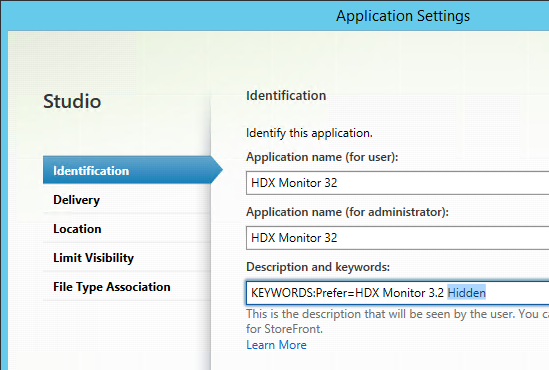
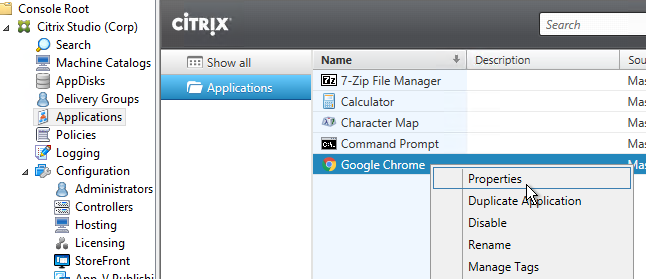
In a published application’s Properties, on the Identification page, in the Description and keywords field, you can enter KEYWORDS to control how the app behaves when displayed by StoreFront.
- Enter KEYWORDS:Mandatory or KEYWORDS:Auto to cause the application to automatically be subscribed or favorited in Citrix Receiver.
- In StoreFront 3.0 and newer, the user can go to the Apps tab, click an App’s Details button, and mark the app as a Favorite.
- In the older StoreFront interface, users subscribe to applications by clicking the plus icon to add the application to the middle of the screen.
- Mandatory means the app can’t be removed from Favorites or unsubscribed.
- Auto means the app is automatically favorited or subscribed, and can be un-favorited or unsubscribed by the user.
- Enter KEYWORDS:Featured to make the application show up in the Featured list.
- You can separate multiple keywords with a space. KEYWORDS:Mandatory Featured.
- See the StoreFront 3.7 Keywords documentation at Citrix Docs for more information.
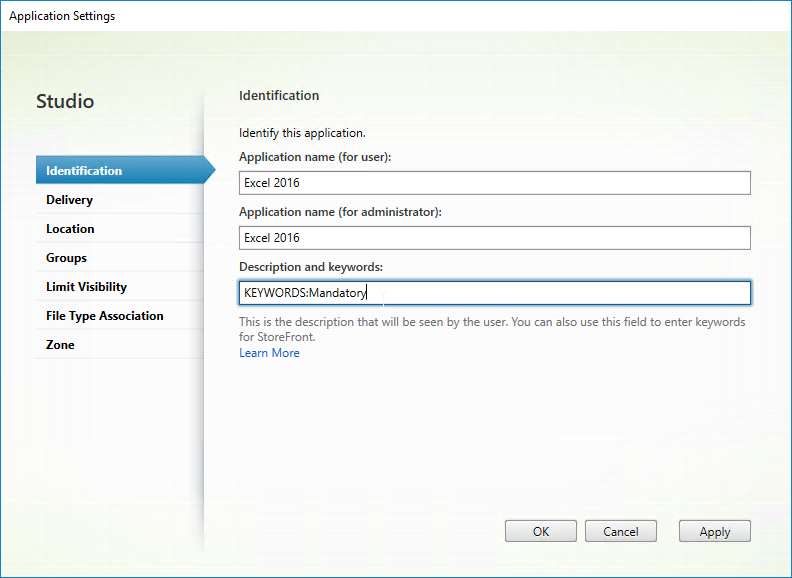
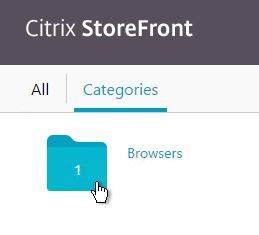
Users will have a better experience with StoreFront if applications are published into folders. The folder name is specified in the Delivery page in the Category field. Note: Add shortcut to user’s desktop works in newer versions of Receiver assuming the app is marked as a Favorite.
Secure Browser
Citrix has a deployment guide for publishing a browser from XenApp. Here’s an overview of the configuration:
- Install Chrome on an RDSH VDA.
- In Studio, publish IE and/or Chrome in Kiosk Mode to anonymous users.
- Create a different published app for each website.
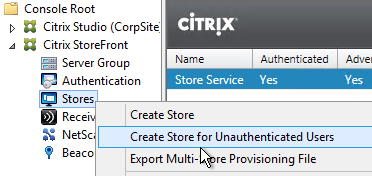
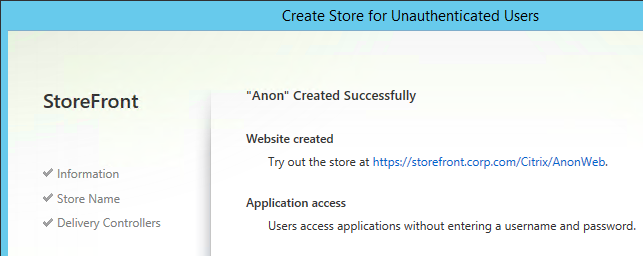
- In StoreFront, create a Store for Unauthenticated Users.
- In StoreFront, enable Receiver for HTML5.
- In StoreFront, enable web links so you can link to the published browser from a different website.
When a user launches the published browser, the HTML5 client opens the published app in a local browser tab. The published browser runs in kiosk mode so that the published browser’s user interface is hidden. It looks like the website is running on the local browser but actually it’s running from a published browser.
App-V
App-V GPO ADMX templates
The latest GPO ADMX templates for App-V can be downloaded from Microsoft Desktop Optimization Pack Group Policy Administrative Templates.
App-V and Logon Times
Links:
- Microsoft App-V Team Blog: Support Tip: Mandatory user profiles and App-V integration with Configuration Manager – configure SCCM to run a logon script to republish App-V packages at every logon.
- Måns Hurtigh: Integrate Application Virtualization with Citrix Provisioning Services – pre-load App-V apps in master image, then run startup script on Target Devices to update App-V cache
App-V Dual Admin
In Dual Admin mode, you configure Citrix Studio to connect to App-V Management Server(s) and Publishing Server(s).
See Citrix Blog Post Load Balancing Microsoft App-V Servers with a Citrix Virtual Apps deployment for supported App-V server load balancing configurations.
- Connecting to Management Servers using a load balancing VIP is not supported.
- Use DNS Round Robin instead. Or use Citrix PowerShell to specify multiple Management Servers.
- You can connect to Publishing Servers load balanced through a VIP, but Studio will show an error. Just ignore it.
App-V Single Admin
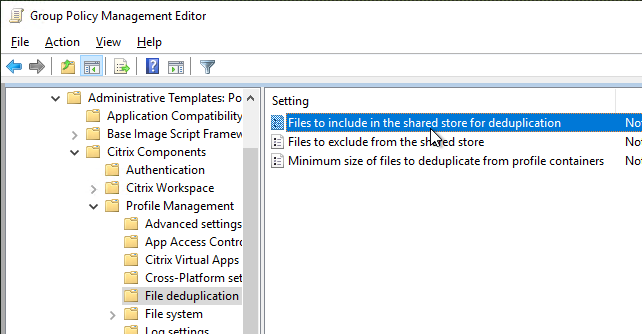
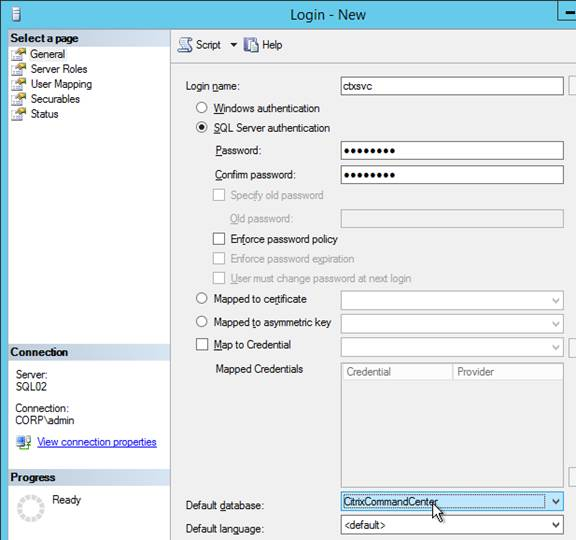
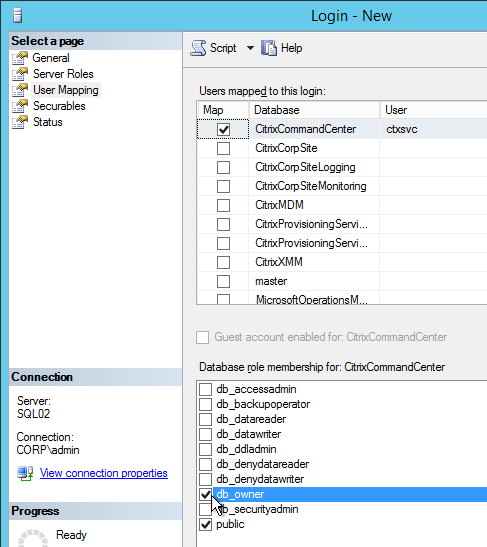
Citrix Virtual Apps and Desktops (CVAD) and XenApp 7.8 no longer requires App-V management infrastructure and can instead pull the App-V packages directly from an SMB share as detailed at App Packages at Citrix Docs.
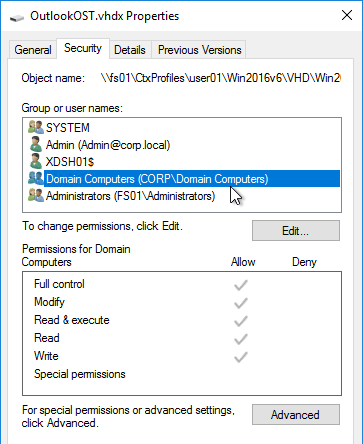
The computer accounts for Delivery Controllers and VDAs must have read access to the share. An easy method is to add Domain Computers. See CTX221296 Citrix App-V Integration Minimum Permission Requirements.
In CVAD 2311 or newer, in Web Studio, go to App Packages to add App-V packages. See Publish packaged applications on single-session or shared desktop VDAs at Citrix Docs.
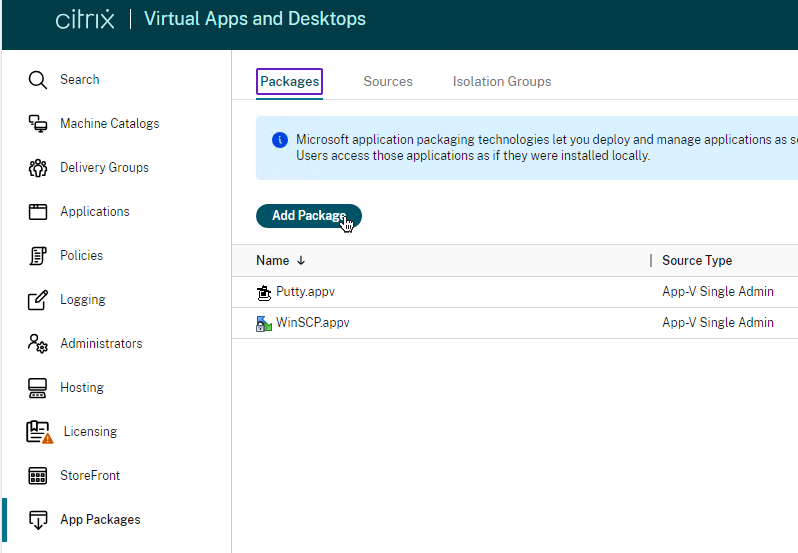
In older Citrix Studio, go to Configuration > Hosting, right-click App-V Publishing, click Add Packages, and browse to the .appv file.
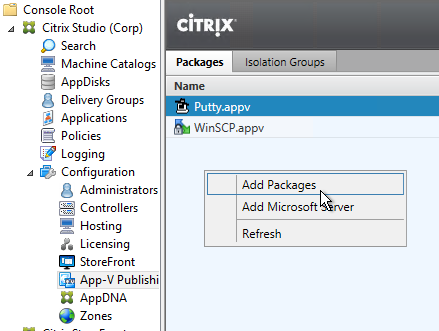
Citrix Virtual Apps and Desktops (CVAD) and XenApp 7.11 adds an Isolation Groups tab.
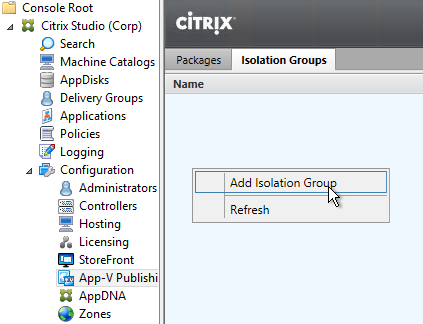
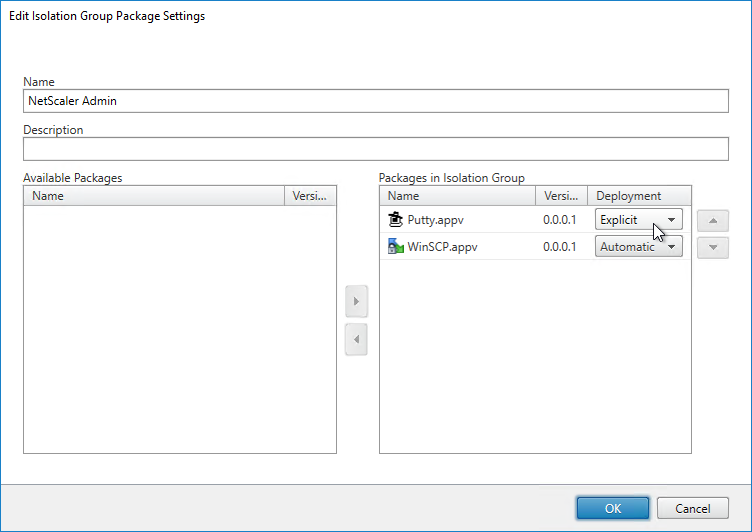
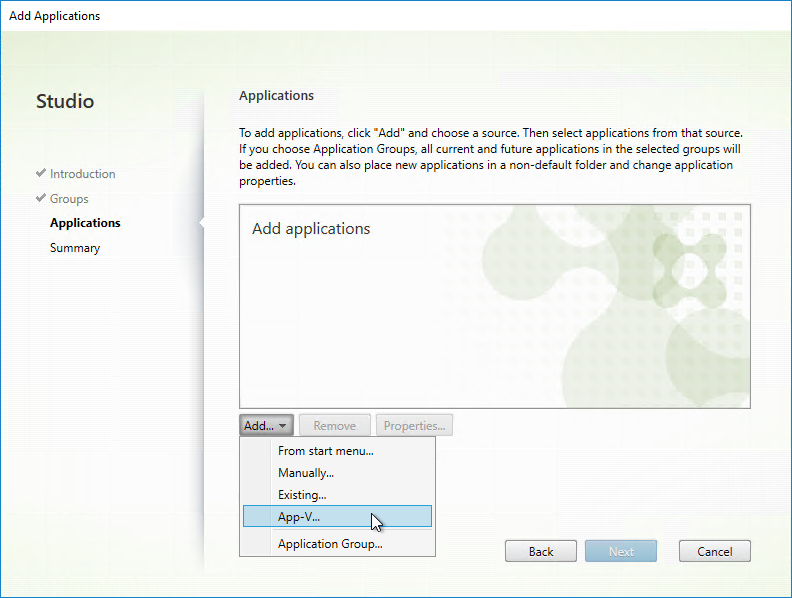
Once App-V packages are added to Citrix Studio, you can publish an app, and select App-V from the drop-down.
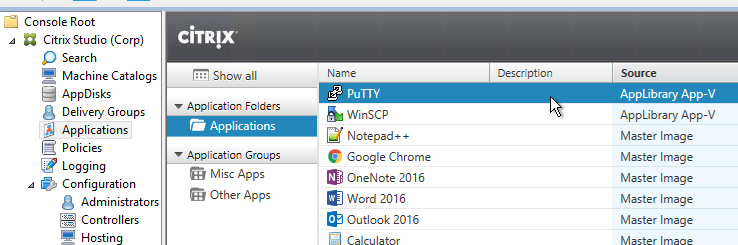
The App-V apps show up as AppLibrary App-V and support the same options as other published applications.
Make sure the App-V Components are installed on your VDA. It’s not checked by default in 7.12 and newer.
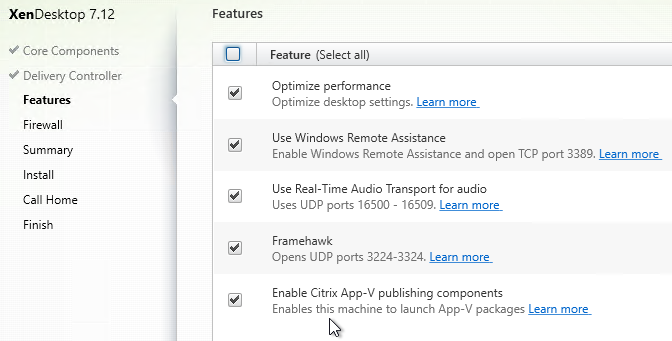
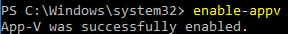
On your VDA Windows 10/2016 or newer, in PowerShell, run Enable-Appv. For older OS, install the App-V client.
There appears to be some limitations to the package share method as detailed by Joe Robinson at Citrix Discussions:
- No File Type Associations
- No Custom Deployment Config Files (no scripts)
- No Category for published App-V apps
Joe Robinson provided a script to force the App-V client to sync before launching the user’s App-V application.
If you run Citrix Workspace app inside a VDA machine and attempt to launch an App-V published app, it will launch from a different VDA session instead of the VDA session you’re already connected to.
- This problem has been fixed in Workspace App 1912 Cumulative Update 3 💡
- Or, change the published app’s command line executable and configure Prefer or vPrefer. This might not work in CVAD 2003 and newer. More info at CTP George Spiers Launching App-V applications published through Studio on the same VDA.
Launch App Inside App-V Bubble
From Citrix Blog Post Process Launching in an App-V V5 Virtual Environment:
- On any executable, add the
/appvve:<PackageID>_<VersionID>of the package in which one would like the executable to run - If the App-V process is already running then use the
/appvpid:<ProcessId>to inject into a running App-V virtual environment - If you want something more permanent, you can set the
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\AppV\Client\RunVirtual\<YourApplicationName>with a default REG_SZ key that has the executable name in it.
Also see Microsoft Knowledgebase article How to launch processes inside the App-V 5.0 virtualized environment.
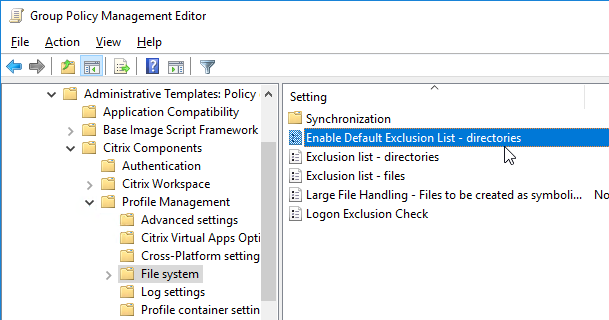
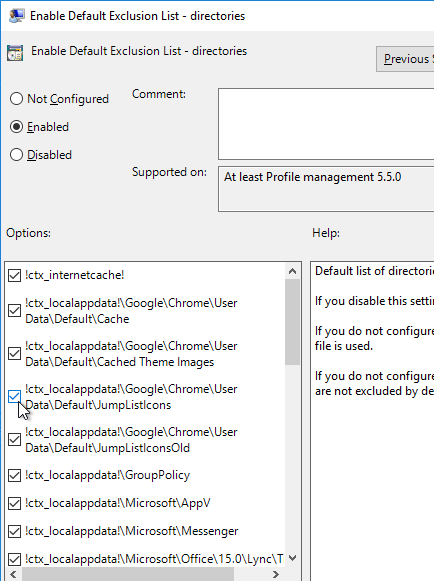
AppDisks
See https://www.carlstalhood.com/appdisks/
Change Published Desktop Icon
Citrix Blog Post Changing Delivery Group Icons Revisited (XD7) has instructions on how to use PowerShell to import a Base-64 icon and then link it to the published desktop.
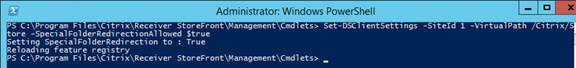
StoreFront overrides custom desktop icons. Run the following PowerShell commands to restore custom desktop icons: (h/t CTP Sam Jacobs)
& 'C:\Program Files\Citrix\Receiver StoreFront\Scripts\ImportModules.ps1' $store = Get-STFStoreService /Citrix/Store Set-STFStoreService -StoreService $store -SubstituteDesktopImage $false -Confirm:$false
Other Published App Tips
CTX209199 Published 64 bit Aps Can’t Be Started With %ProgramFiles% in Command Line If It’s Not the first Application to Start: You can try the following methods to address this issue:
- Use the absolute path to publish the application.
2. Use %ProgramW6432% for 64-bit applications instead of %ProgramFiles%.
Google Chrome
Links detailing installation, configuration, roaming profiles, and publishing.
- Dennis Span Google Chrome on Citrix deep-dive.
- Måns Hurtigh Configure Google Chrome In A Multi-User Environment
CTX132057 Google Chrome Becomes Unresponsive when Started as Published Application: add the parameters --allow-no-sandbox-job --disable-gpu in the published app command line. According to Dennis Span, this is no longer needed in Chrome 58 and newer.
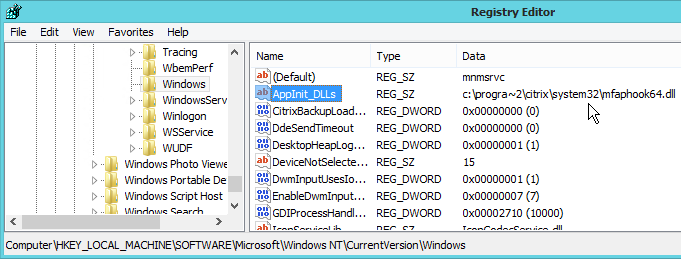
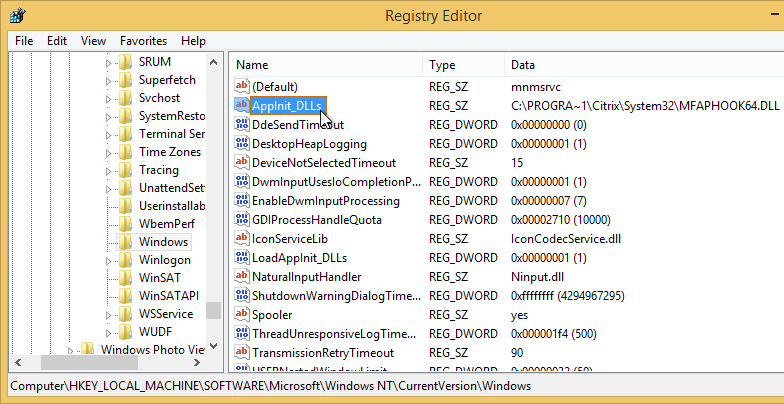
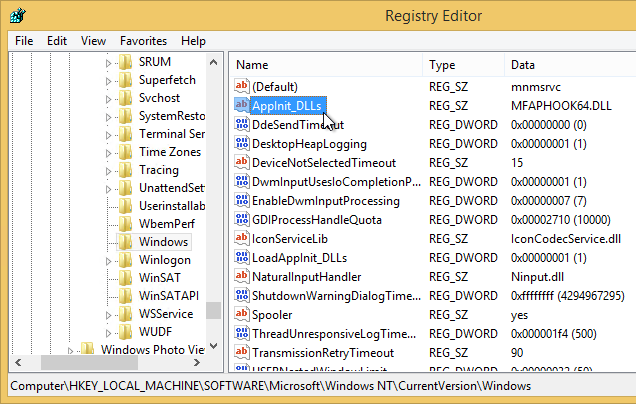
CTX205876 Non-published Google Chrome browser on XenApp server, called and launched from any published app, is seen in black/grey screen: The command line parameter has to be added to registry shell open command for the Chrome browser:
- In Regedit, navigate to HKEY_CLASSES_ROOT\http\shell\open\command
- Edit the Default value as follows:
"C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --allow-no-sandbox-job --disable-gpu -- "%1"
Disable Application and Hide It
- In Studio, you can disable a published application by right-clicking it, and clicking Disable.
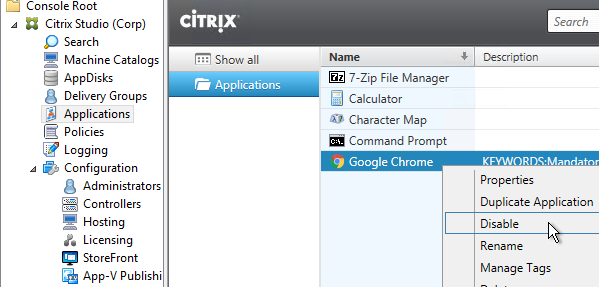
- In older versions of XenApp/XenDesktop, when you disable the application, it leaves the application visible but it is grayed out thus preventing users from launching it. In 7.8, the disabled app is automatically hidden (no longer shown in the apps list).
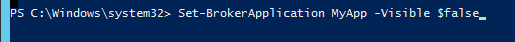
- If desired, you can hide or unhide the disabled application icon by running a PowerShell command:
asnp citrix.* Set-BrokerApplication MyApp -Visible $false
- When you re-enable the application, Visibility is automatically set back to true.
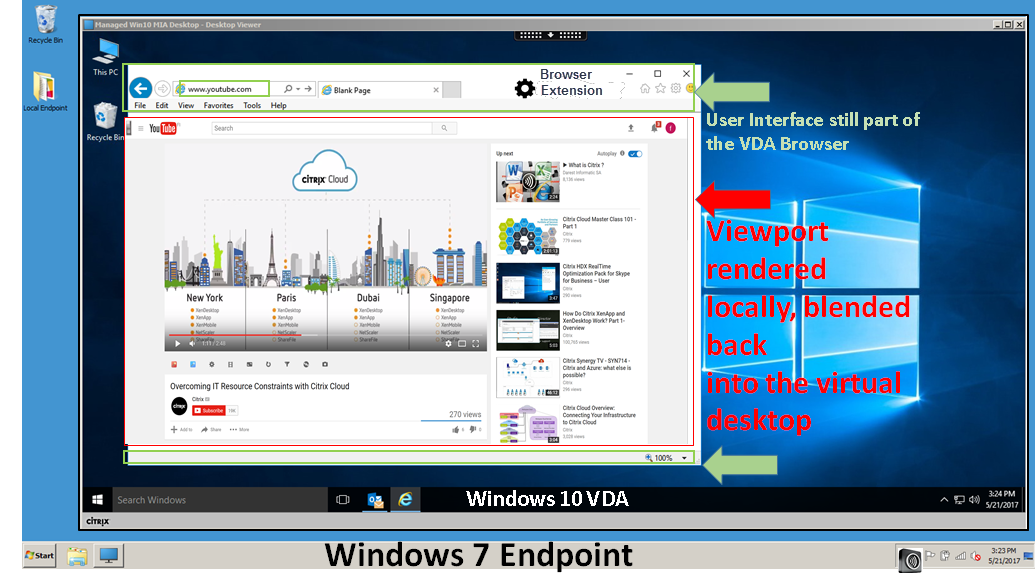
Browser Content Redirection
Browser Content Redirection prevents the rendering of whitelisted webpages on the VDA side, and instead renders them on the client side. Only the browser viewport is redirected. The intent of this feature is to redirect HTML5 Video (e.g .youtube).
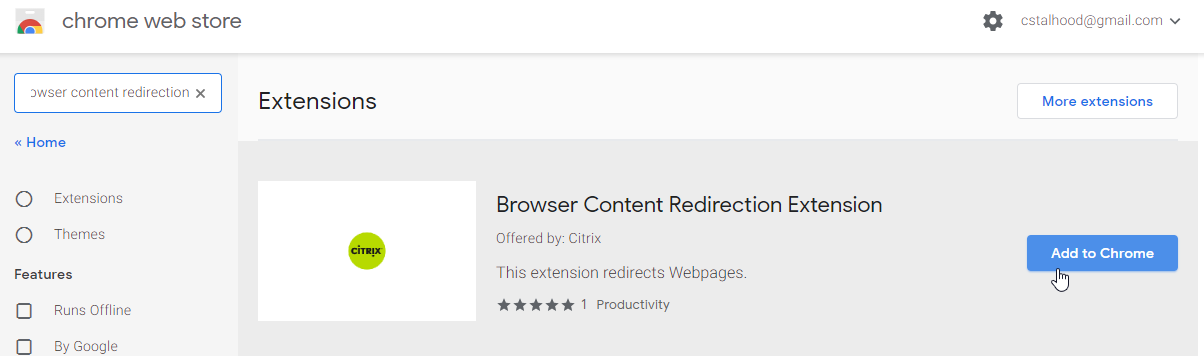
Browser Content Redirection requirements:
- Citrix Virtual Apps and Desktops (CVAD) or XenApp/XenDesktop 7.16 and newer
- Receiver 4.10 or newer
- Chrome support is available in Citrix Virtual Apps and Desktops (CVAD) 1808 and newer
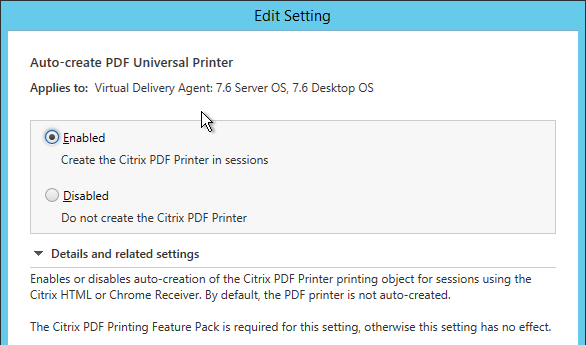
- In the VDA, install the Chrome Browser Extension named Browser Content Redirection Extension. You can use Google Chrome Group Policy templates to force installation of the extension. See Browser content redirection Chrome extension at Citrix Docs.
- You do not need any client software other than Workspace app 1809 or newer. The client-side rendering engine is included in Workspace app 1809 and newer.
- HDX Browser Content Redirection feature will not work with Citrix Workspace app for Windows 1912 LTSR due to removal of the embedded browser from LTSR versions. But it does work in Workspace app 2006.
- In the VDA, install the Chrome Browser Extension named Browser Content Redirection Extension. You can use Google Chrome Group Policy templates to force installation of the extension. See Browser content redirection Chrome extension at Citrix Docs.
- Internet Explorer 11– IE 11 on both the VDA, and on the client.
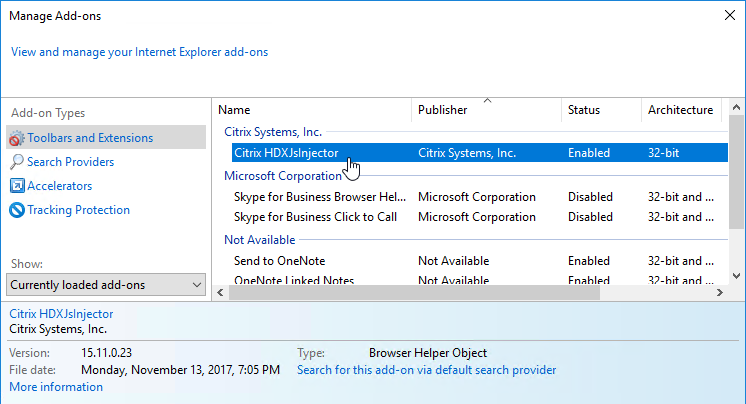
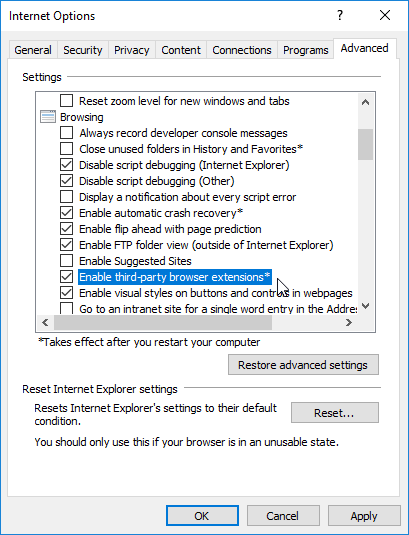
- On the VDA, Enhanced Protected Mode must be disabled under Internet Explorer: Internet Options > Advanced
- On the VDA, an IE 11 Browser Helper Object (BHO) named Citrix HDXJsInjector facilitates the redirection.
- In Internet Explorer > Tools > Internet Options > Advanced > Browsing, ensure that Enable third-party browser extensions is checked. Source = Content Browser Redirection at Citrix Discussions.
- Internet access from Client – By default, the client (Receiver) tries to fetch the redirected content. If client is not able to fetch, then the content falls back to server rendering.
- You can enable server fetch / client render by configuring Browser Content Redirection Proxy settings.
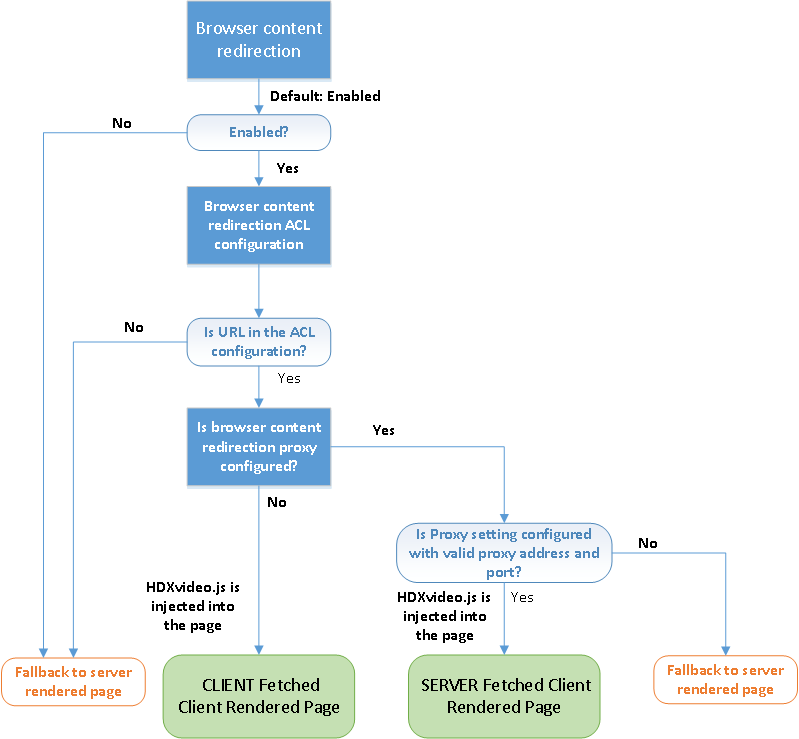
- See Citrix Blog Post HTML5 Multimedia Redirection: State of the Union Part II for technical details on Server Side Fetching.
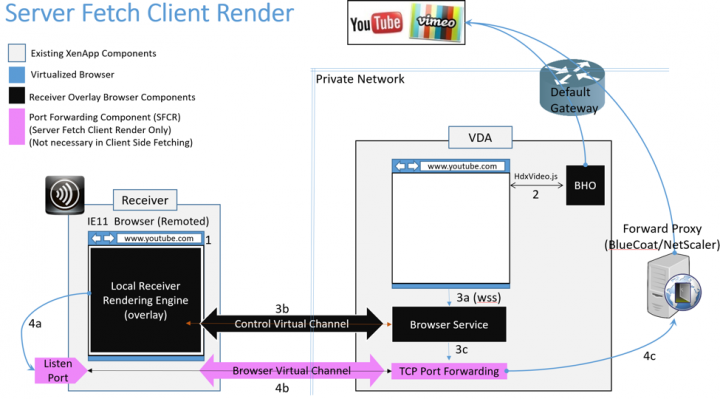
- You can enable server fetch / client render by configuring Browser Content Redirection Proxy settings.
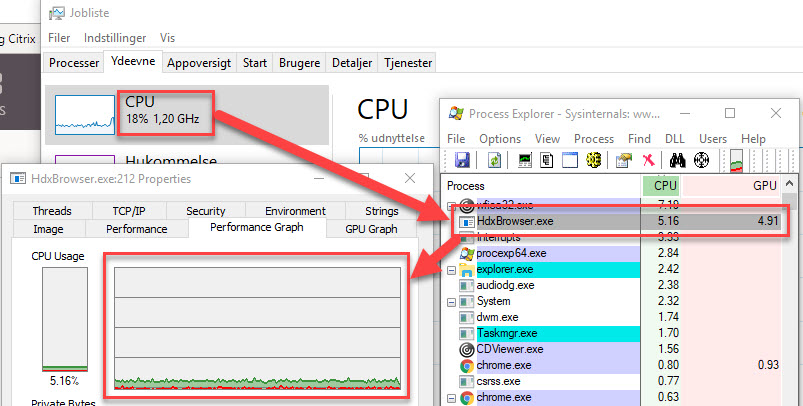
- When redirection is working, the client machine has a HdxBrowser.exe process.
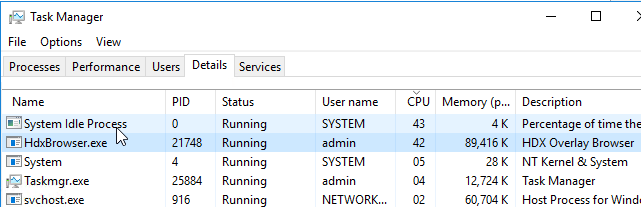
- See Kasper Johansen Citrix Xenapp And Desktop 7.16 Browser Content Redirection for some videos of this feature.
- Kasper and Rasmus detail client-side registry keys to enable HdxBrowser.exe to use client-side GPU. These keys/values might already be configured in Receiver 4.11 and newer.
- HKEY_LOCAL_MACHINE\Software\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_GPU_RENDERING
- HdxBrowser.exe (DWORD) = 1
- HKEY_LOCAL_MACHINE\Software\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_BROWSER_EMULATION
- HDXBrowser.exe (DWORD) = 11000 (Decimal)
- HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_GPU_RENDERING
- HdxBrowser.exe (DWORD) = 1
- HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_BROWSER_EMULATION
- HDXBrowser.exe (DWORD) = 11000 (Decimal)
- HKEY_LOCAL_MACHINE\Software\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_GPU_RENDERING
- Rasmus Raun-Nielsen at Browser Content Redirection?! at LinkedIn has some CPU analysis, including client-side GPU.
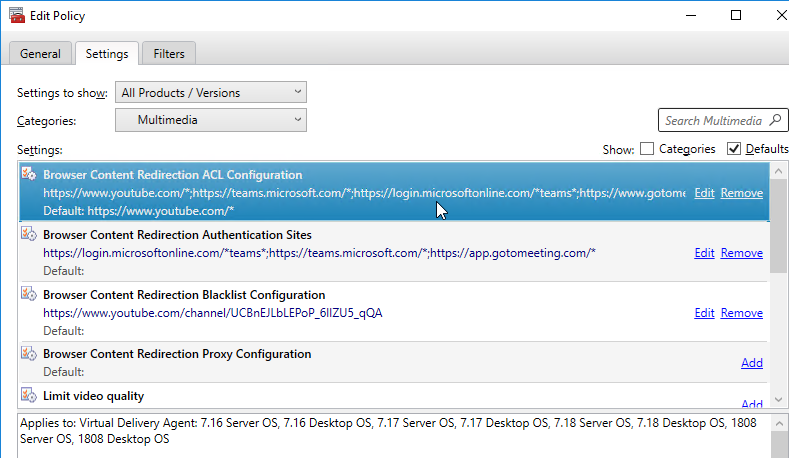
Browser Content Redirection is configured using Citrix Policies, in the User half, under the Multimedia category.
Browser Content Redirection is enabled by default, but only for the specified whitelist URLs (ACL Configuration). Note that wildcards can be used in the path, but not in the DNS name. To configure Microsoft Teams and GoToMeeting, see CTX238236 Browser Content Redirection: whitelisting websites.
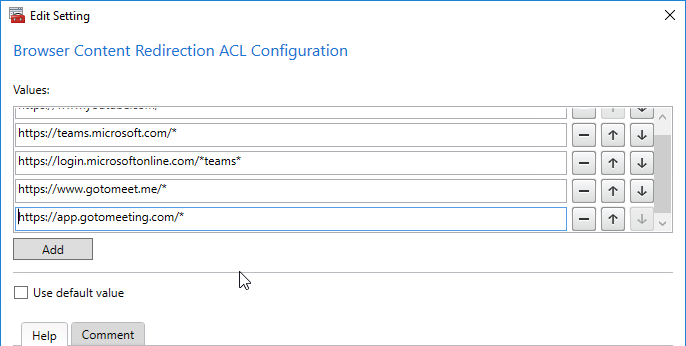
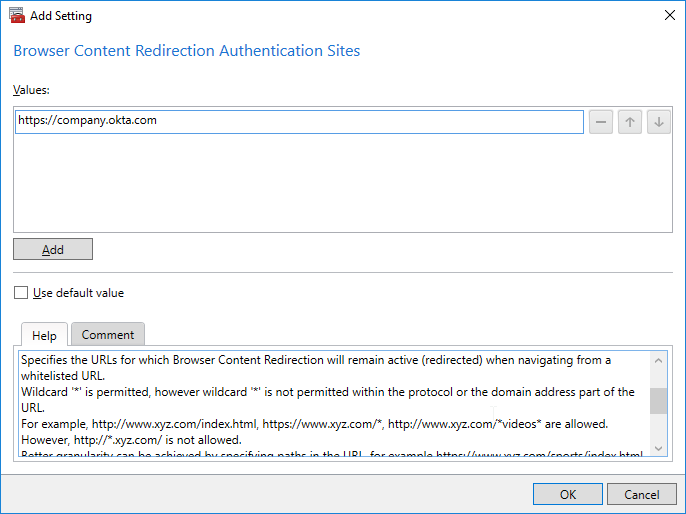
Citrix Virtual Apps and Desktops (CVAD) and XenDesktop 7.18 and newer have a setting named Browser Content Redirection Authentication Sites. Add URLs that are redirected from the main ACL URL. To configure Microsoft Teams and GoToMeeting, see CTX238236 Browser Content Redirection: whitelisting websites. Also see See CTX230052 How to Troubleshoot Browser Content Redirection.
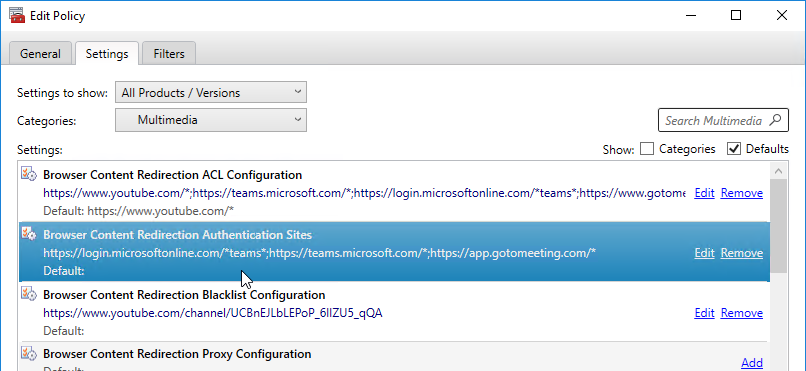
Citrix Virtual Apps and Desktops (CVAD) and XenDesktop 7.17 and newer have a Blacklist setting. Any address added here will not be redirected to the client. You typically configure this setting to override the ACL setting (e.g. ACL setting has a generic URL, but the Blacklist has a more specific URL)
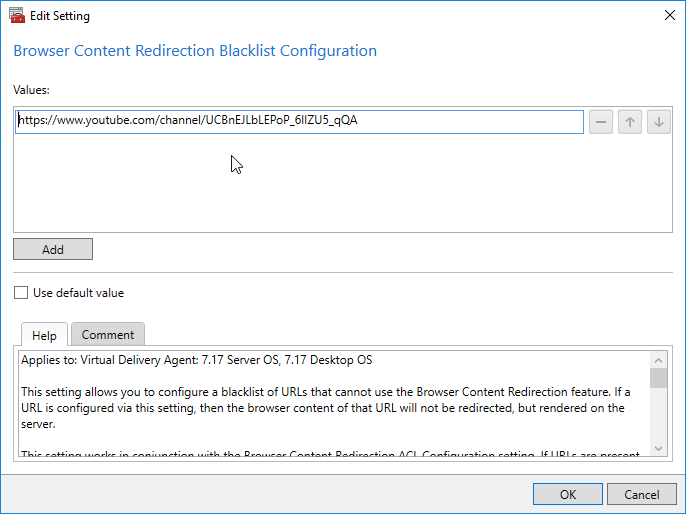
7.18 adds a Browser Content Redirection Authentication Sites setting. Configure a list of URLs that sites redirected via Browser Content Redirection can use to authenticate a user. E.g. iDP URLs.
Registry keys for Browser Content Redirection are detailed at Browser content redirection policy settings at Citrix Docs.
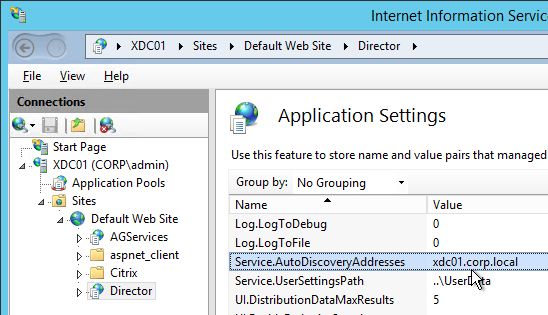
Bidirectional Content Redirection
You can redirect URLs from client to a published browser, or from VDA to the client. See Bidirectional content redirection policy settings at Citrix Docs for requirements and limitations.
- Make sure Local App Access is not enabled on the VDAs.
- Make sure a browser is published. Chrome and Edge require Workspace app 2106 and newer connecting to VDA 2106 and newer.
- Edit a GPO that applies to VDA users.
- Go to User Config | Policies | Citrix Policies and edit a Citrix Policy.
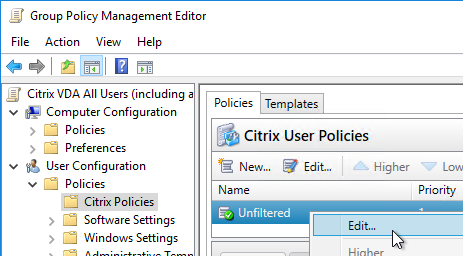
- Find the setting Allow Bidirectional Content Redirection and enable it (Allowed).
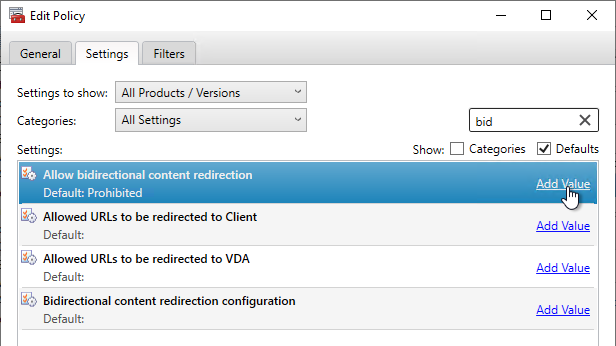
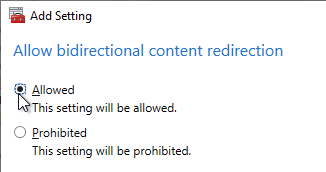
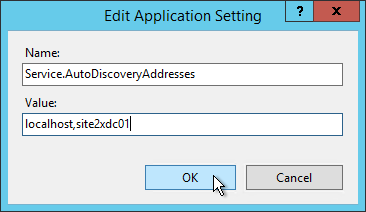
- In CVAD 2311 and newer, use the setting Bidirectional content redirection configuration to insert a JSON string containing the list of URLs to redirect from client or VDA. The older setting for Allowed URLs has been deprecated. See Bidirectional content redirection at Citrix Docs.
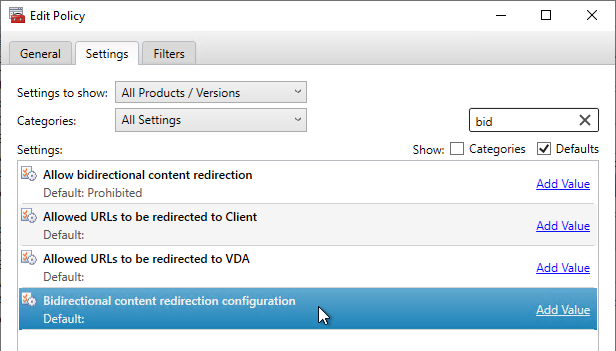
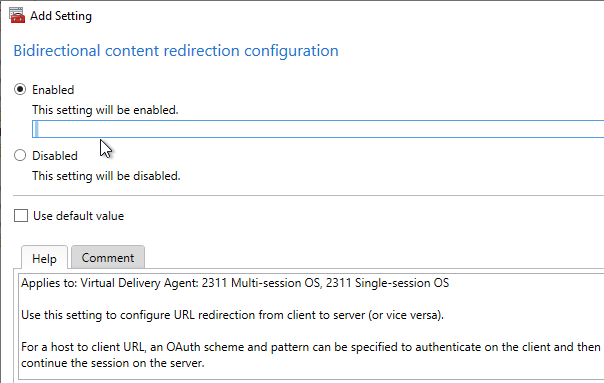
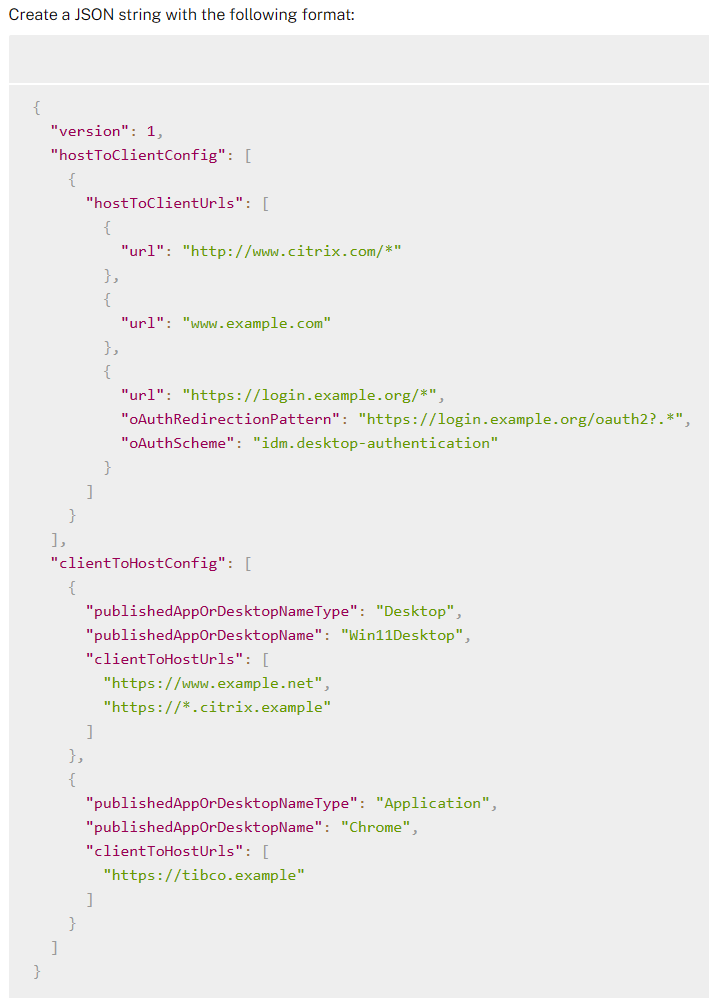
- Prior to CVAD 2311, also configure the Allowed URLs policy settings (VDA to client, or client to VDA) to indicate which URLs should be redirected in either direction.
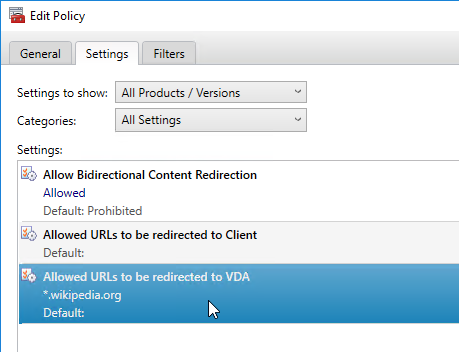
- VDA 2206 adds support for wildcards in the Allowed URLs to be redirected to Client policy setting, but not from Client to VDA.
- VDA 2206 adds support for custom protocols other than HTTP and HTTPS in the Allowed URLs to be redirected to Client policy setting. These custom protocols don’t work from Edge/Chrome.
- More details at Citrix Docs.
- In CVAD 2311 and newer, it is no longer necessary to configure Bidirectional Content Redirection on the client side. For older CVAD:
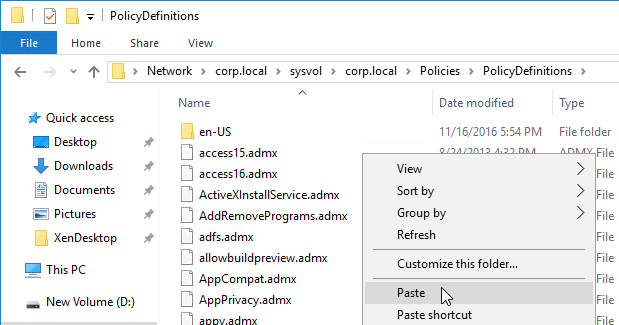
- Copy the receiver.admx file from Receiver 4.7 or newer to PolicyDefinitions (SYSVOL or C:\Windows\PolicyDefinitions).
- Edit a GPO that applies to client devices (endpoints).
- Go to User Configuration | Policies | Administrative Templates | Citrix Workspace | User experience.
- Double-click the setting Bidirectional Content Redirection.
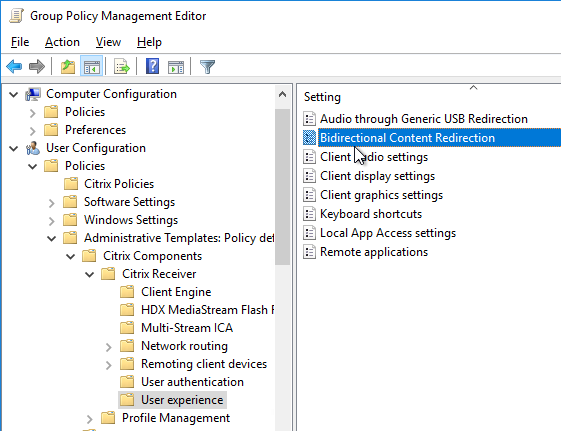
- Enable the setting.
- In the Published Application field, enter the name of the Internet Explorer published application.
- In the Allowed URLs fields, configure the URLs you want to redirect in either direction.
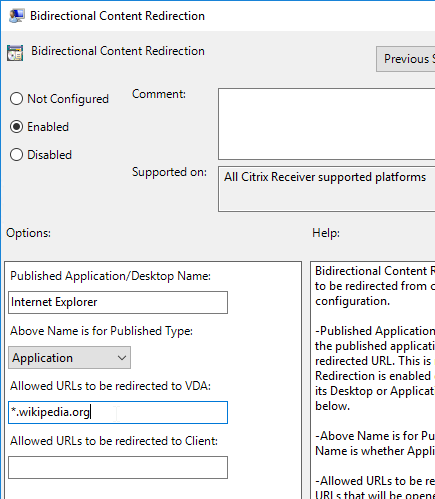
- On the VDA, run one or more the following commands to register the browser add-on. Chrome and Edge require Workspace app 2106 and newer connecting to VDA 2106 and newer.
"C:\Program Files (x86)\Citrix\System32\VDARedirector.exe" /regIE "C:\Program Files (x86)\Citrix\System32\VDARedirector.exe" /regChrome "C:\Program Files (x86)\Citrix\System32\VDARedirector.exe" /regEdge "C:\Program Files (x86)\Citrix\System32\VDARedirector.exe" /regall
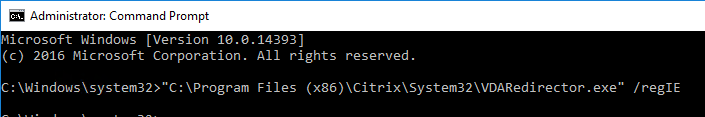
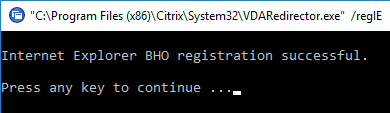
- CTX232277 Unable to Logoff When Bidirectional Content Redirection is Configured says that the following registry value should be configured on the VDA. If you already have LogoffCheckSysModules, then add the below processes names to the existing value.
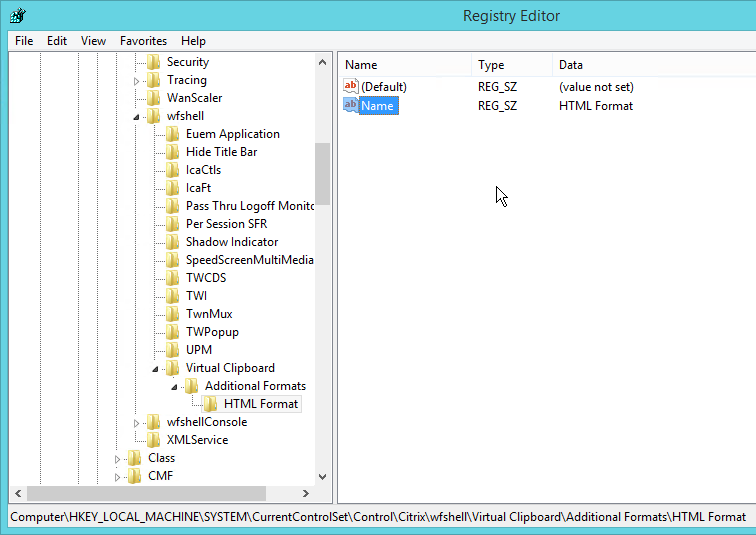
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Citrix\wfshell\TWI- LogoffCheckSysModules (REG_SZ) = wfcrun32.exe,Concentr.exe,SelfServicePlugin.exe,redirector.exe
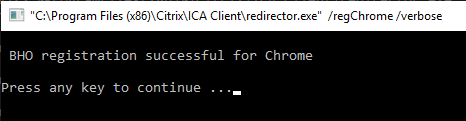
- In Workspace app 2106 and newer connecting to VDA 2106 and newer, do the following to enable redirection for Chrome and/or Edge:
"%ProgramFiles(x86)%\Citrix\ICA Client\redirector.exe" /regChrome /verbose
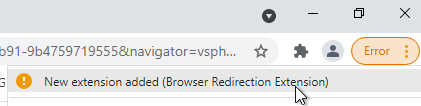
- Chrome might display an Error indicating New extension added.
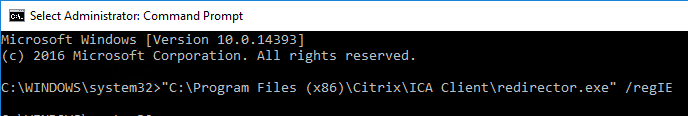
- For Internet Explorer, do the following:
"C:\Program Files (x86)\Citrix\ICA Client\redirector.exe" /regIE
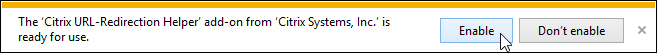
- When you run Internet Explorer on the VDA or client device, you’ll be prompted to enable the add-on. You can configure a GPO to enable this add-on automatically. Redirection won’t work unless the add-on is enabled.
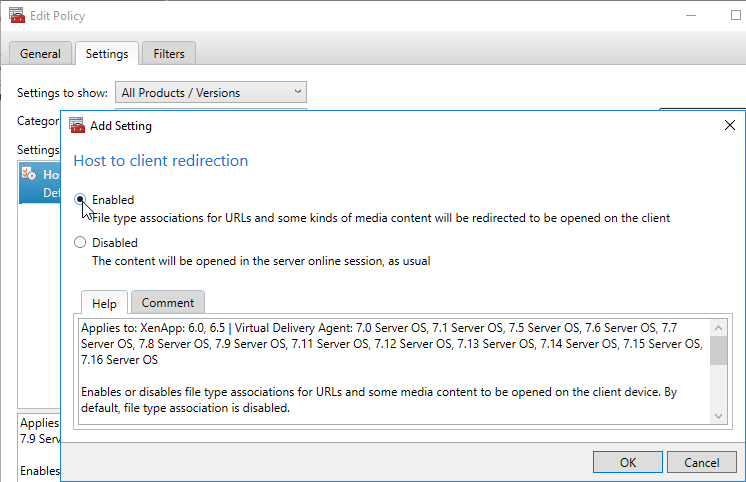
Host to client Redirection
This feature causes Citrix VDA to redirect http links in applications to the client machine, so they are opened using the client’s browser. The feature is disabled by default.
James Rankin at Using host-to-client redirection in Citrix XenApp explains the feature in detail, including:
- Limitations of the feature
- Registry values to control the URL Schemes that can be redirect to the client
- Group Policy and XML file to handle the File Type Associations in Windows 2012 and newer
Local App Access
Some applications are not suitable for centralization and instead should run on endpoint devices. These applications include: phone software, applications needing peripherals, etc. Citrix Local App Access lets you access these endpoint-installed applications from inside a published desktop. This is sometimes called Reverse Seamless.
Local App Access has three modes of functionality:
- User-managed local applications. Any shortcuts in the endpoint’s local Start Menu and local Desktop are made available from inside the published desktop.
- Administrator-managed local applications. Use Studio to publish a local application, which is created as a shortcut inside the published desktop. When the shortcut is launched, it is actually running from the endpoint device (reverse seamless) instead of the centralized desktop. If you enable administrator-managed local applications then user-managed local applications are disabled.
- URL Redirection. Administrators define some URLs that should be opened in a local endpoint browser instead of a VDA browser, and then display the local browser inside the published desktop (reverse seamless).
- An alternative to URL Redirection is Bidirectional Content Redirection. Citrix recommends Bidirectional over Local App Access URL Redirection.
Local App Access requires Platinum Licensing.
Do the following to configure Local App Access:
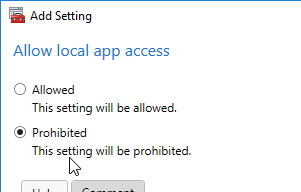
- In a Citrix Policy that applies to the VDAs, enable the Allow local app access policy setting. It’s in the Computer Half.
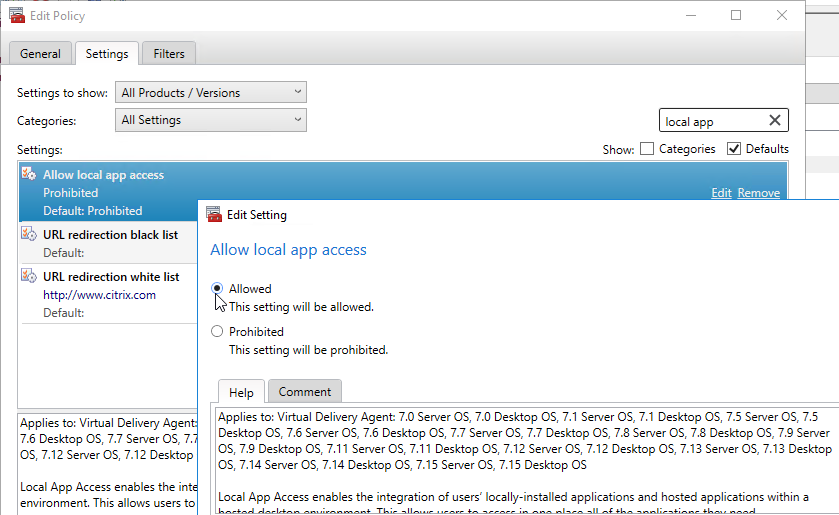
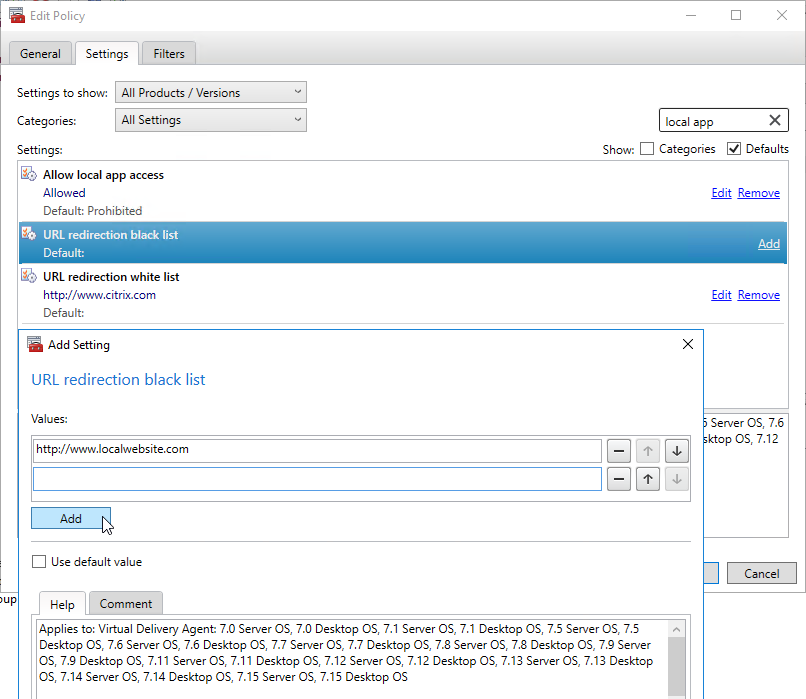
- The URL redirection black list setting lets you define a list of URLs that should be opened on the endpoint’s browser instead of the VDA browser. Alternatively, you can instead configure Bidirectional Content Redirection.
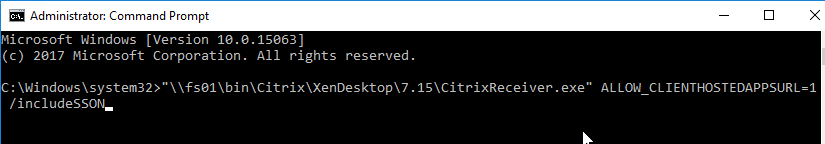
- On the Endpoints, install Receiver using the ALLOW_CLIENTHOSTEDAPPSURL=1 switch. Feel to add /includeSSON too. Run the installer from an elevated (Administrator) command prompt. This switch automatically enables both Local App Access and URL Redirection. Note: the URL Redirection code does not install on VDAs so URL Redirection might not work if your endpoint has VDA software for Remote PC.
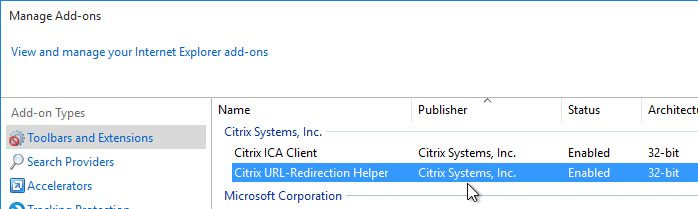
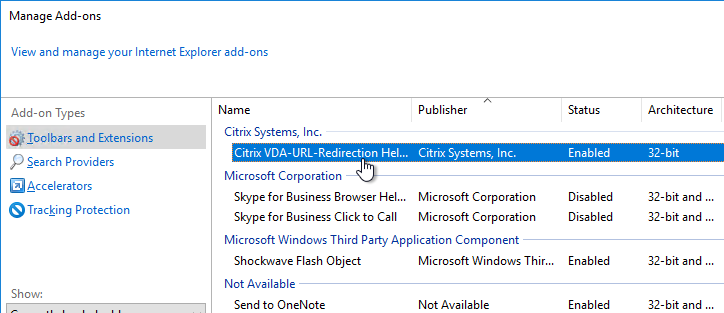
- After installation of Receiver, launch Internet Explorer. You should see a prompt to enable the Citrix URL-Redirection Helper add-on.
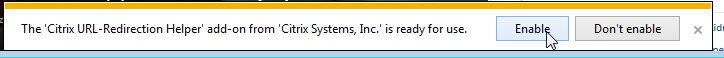
- You can also go to Tools > Manage Add-ons to verify the Browser Helper Object.
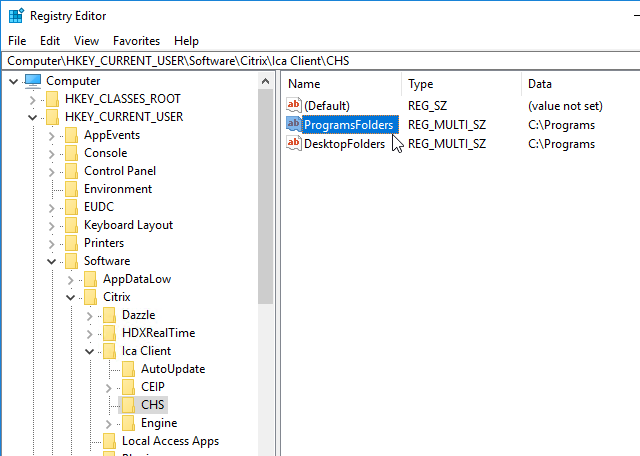
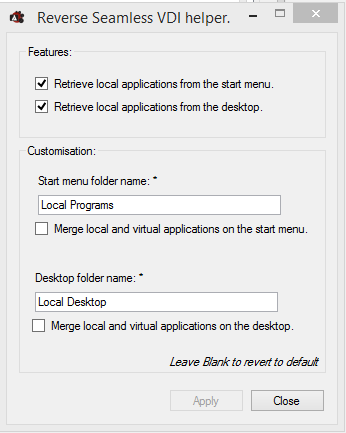
- By default, Local App Access redirects the endpoint’s Start Menu and Desktop. You can control which folders are redirected by editing the endpoint’s registry at HKCU\Software\Citrix\ICA Client\CHS. You might have to create the CHS key. Create the Multi-String Values named ProgramsFolders and DesktopFolders, and point them to folders containing shortcuts that you want to make available from inside the published desktop.
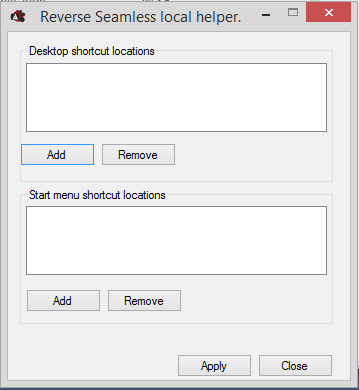
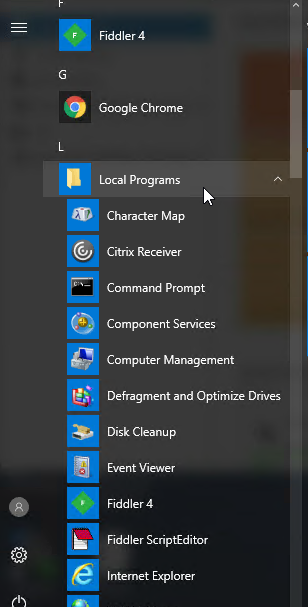
- When you connect to a published desktop, by default, there will be a Local Programs folder in the Start Menu containing shortcuts to programs on the endpoint’s Start Menu. These are user-managed shortcuts. Note: Windows 8 and newer only supports one level of Start Menu folders. This means that all local shortcuts are placed into the single Local Programs folder without any subfolders.
- On the VDA Desktop there will be a Local Desktop folder containing shortcuts from the endpoint’s desktop. These are user-managed shortcuts.
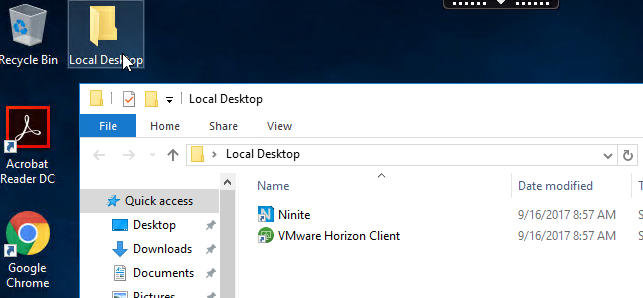
- Note: the following doesn’t seem to work in LTSR 7.15. The VDA seems to overwrite these registry values.
- The Local Desktop and Local Programs folders on the VDA can be renamed by editing the VDA’s registry at HKCU\Software\Citrix\Local Access Apps. You might have to create the Local App Access registry key. Create String values ProgramsCHSFolderName and DesktopCHSFolderName as detailed at Citrix Docs.
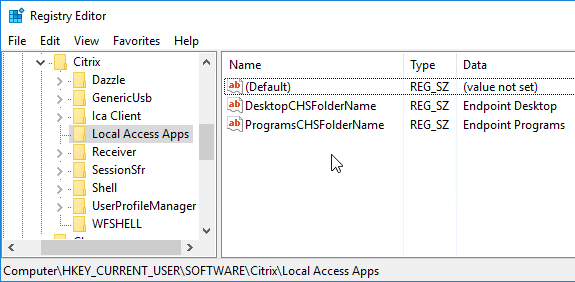
- The Local Desktop and Local Programs folders on the VDA can be renamed by editing the VDA’s registry at HKCU\Software\Citrix\Local Access Apps. You might have to create the Local App Access registry key. Create String values ProgramsCHSFolderName and DesktopCHSFolderName as detailed at Citrix Docs.
- To enable administrator-managed local applications, login to a machine that has Citrix Studio installed, and edit the registry. Go to HKLM\Software\Wow6432Node\Citrix\DesktopStudio, and create the DWORD value named ClientHostedAppsEnabled, and set it to 1.
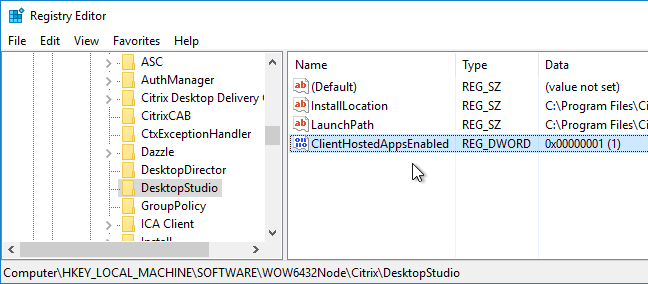
- When you open Studio, and right-click the Applications node, there is a new entry Add Local App Access Application.

- In the Getting Started with Local Access Applications page, click Next.
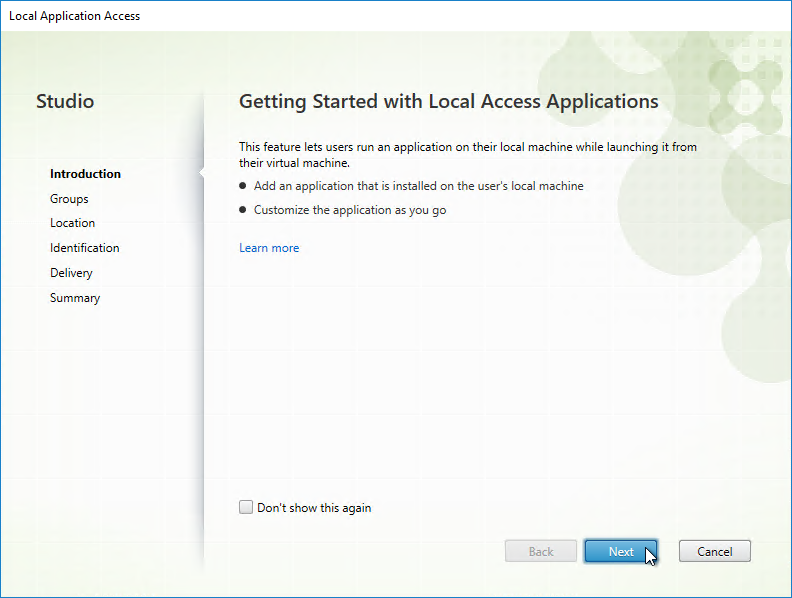
- In the Groups page, select the Delivery Group or Application Group whose published desktop will receive the shortcut, and click Next.
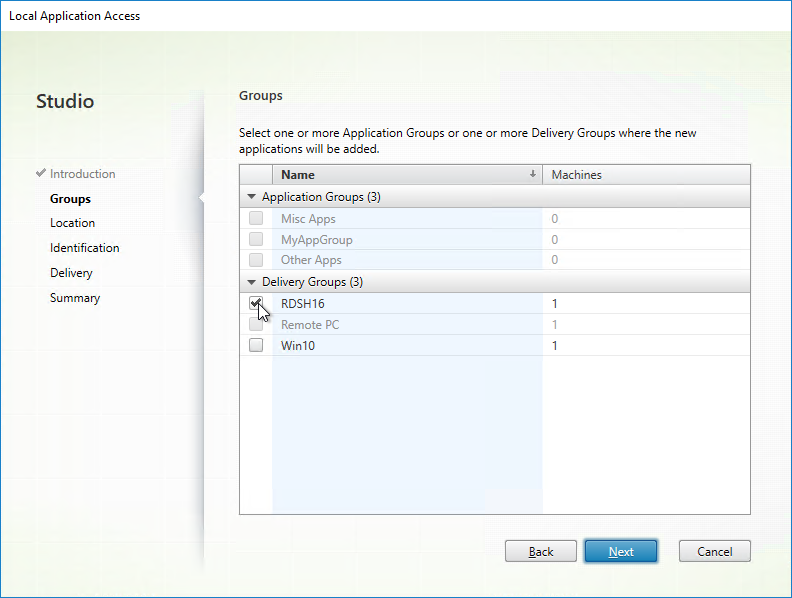
- In the Location page, enter the path to the executable. This is the path on the endpoint. Also enter a Working Directory. You can get this information from the properties of the shortcut on the endpoint device. Click Next.
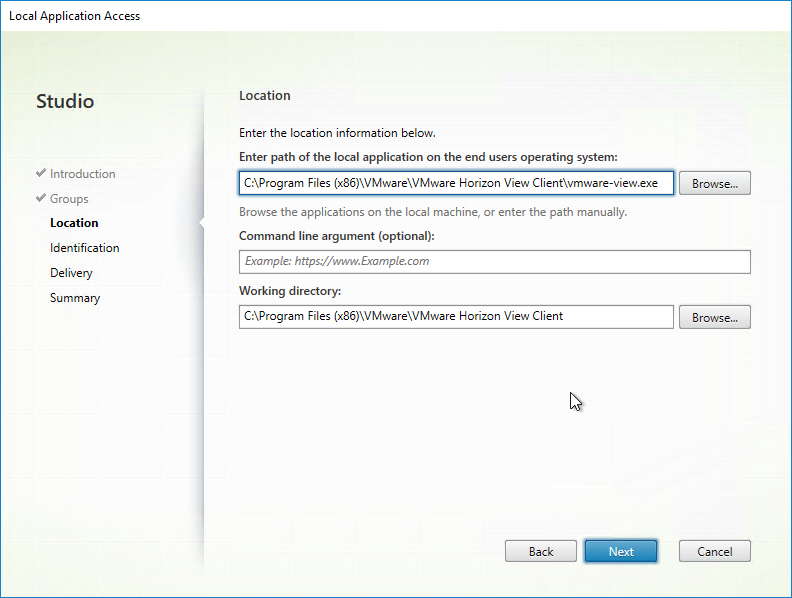
- In the Identification page, enter a name for the shortcut, and click Next.
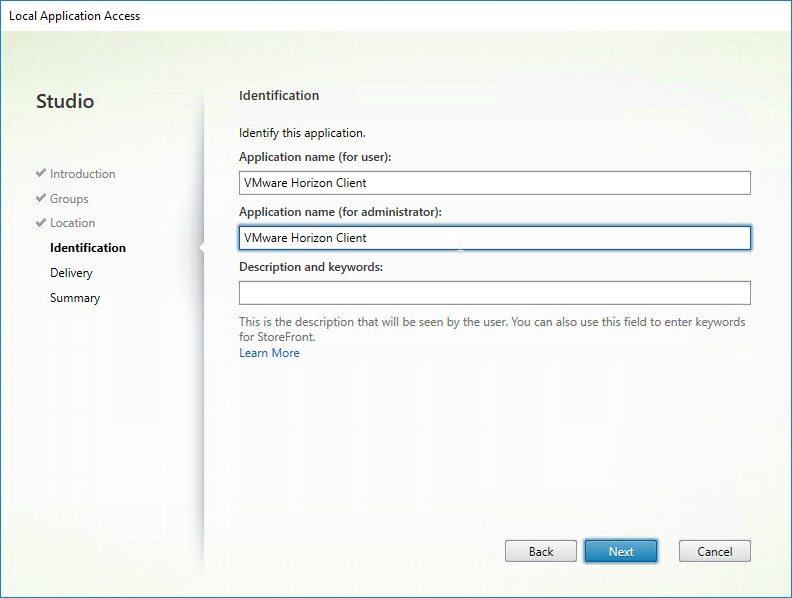
- In the Delivery page, these options work as expected. Click Next.
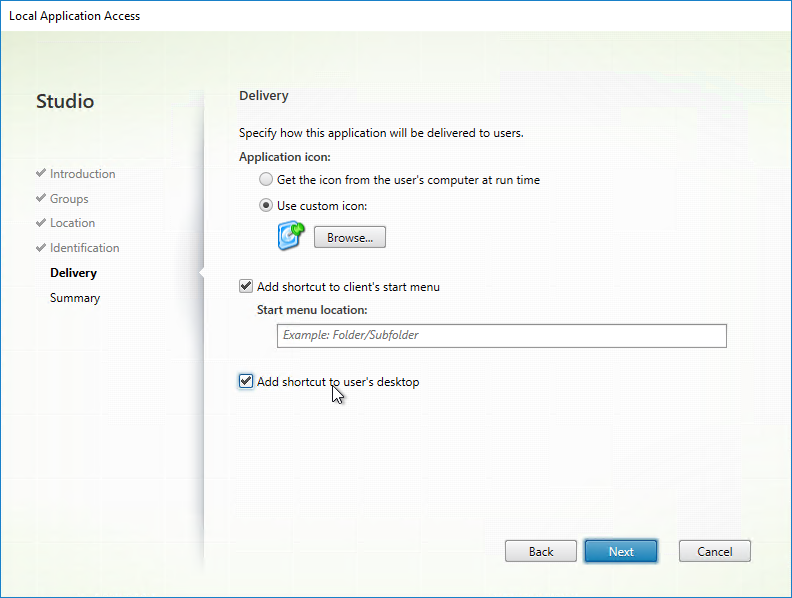
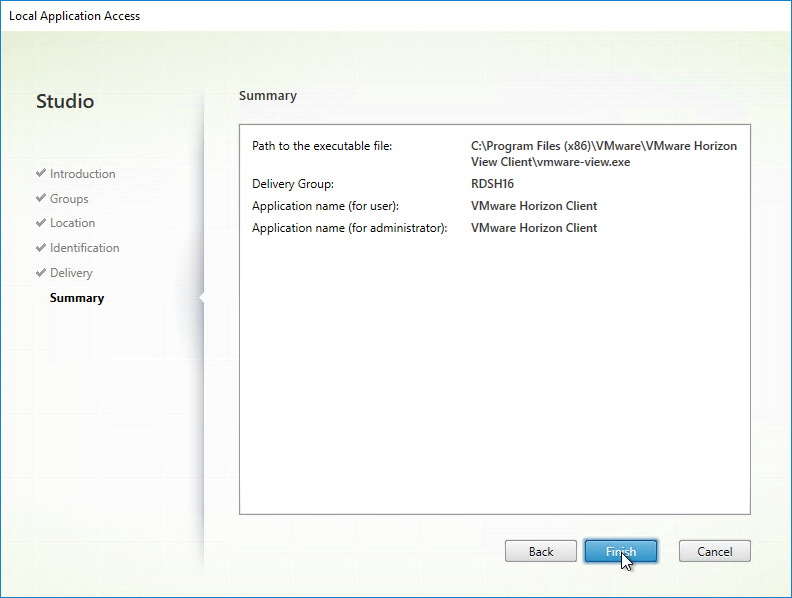
- In the Summary page, click Finish.
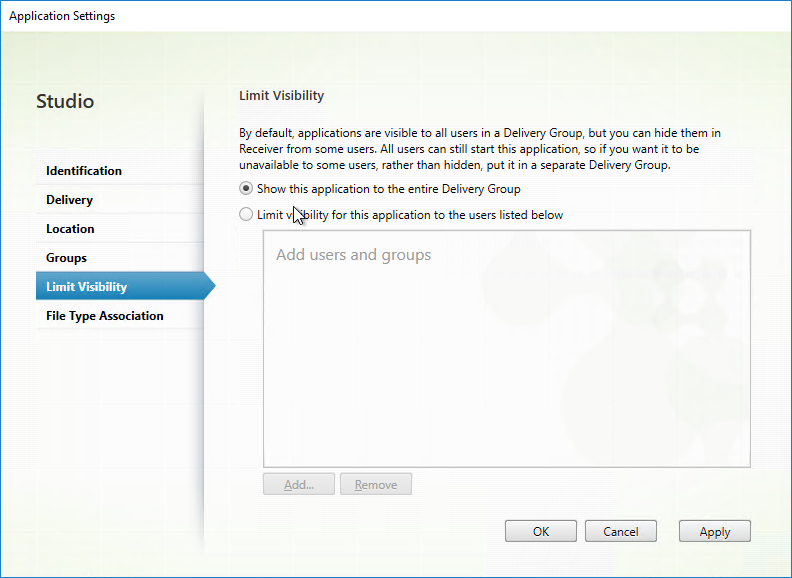
- If you open the Properties of the Local App, there’s a Limit Visibility page.
- In the Getting Started with Local Access Applications page, click Next.
- When you login to the desktop, you’ll see the administrator-managed local application. If any administrator-managed Client Hosted Applications are delivered to the user, then the default Local Programs and Local Desktop folders no longer appear.

- To enable URL Redirection, login to the VDA, and run
"C:\Program Files (x86)\Citrix\System32\VDARedirector.exe" /regall. This registers the browser helpers.
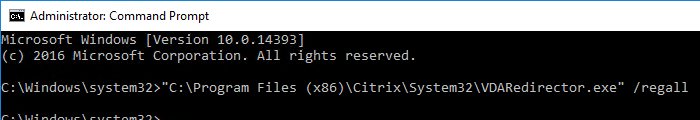
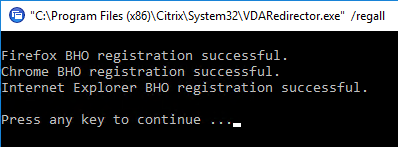
- In Internet Explorer, if you go to Tools > Manage Add-ons, you’ll see the Citrix VDA-URL-Redirection Helper add-on.
- From inside the published desktop, if you go to a website on the blacklist, the VDA browser will close and a local browser will open in Reverse Seamless mode. If you then go to a website that is not on the blacklist, the local browser will close and the VDA browser will open again.
Citrix TV – Local App Access in XenDesktop 7
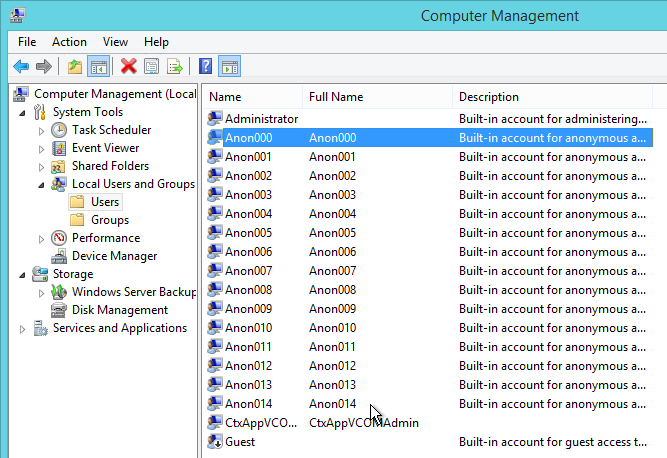
Anonymous Apps
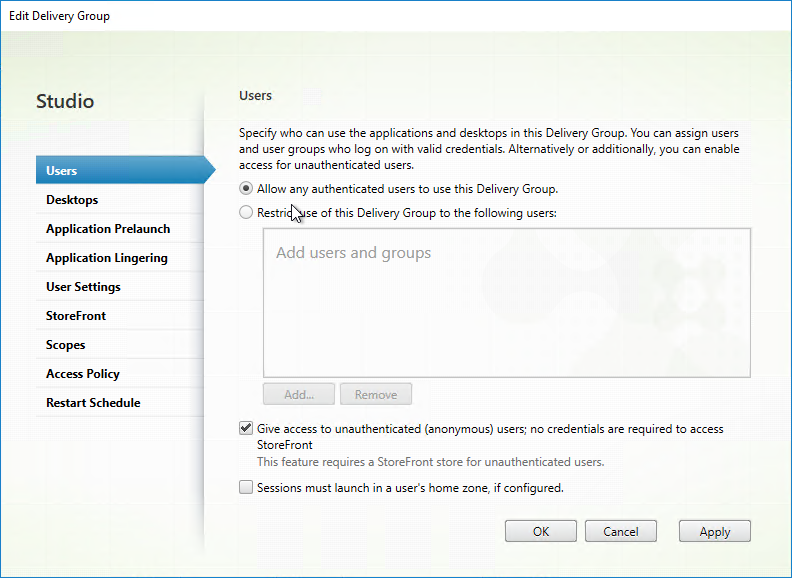
Citrix Virtual Apps and Desktops (CVAD) and XenApp 7.6 and newer supports publishing apps to anonymous users. Edit the Delivery Group, and on the Users page, check the box next to Give access to unauthenticated (anonymous) users.
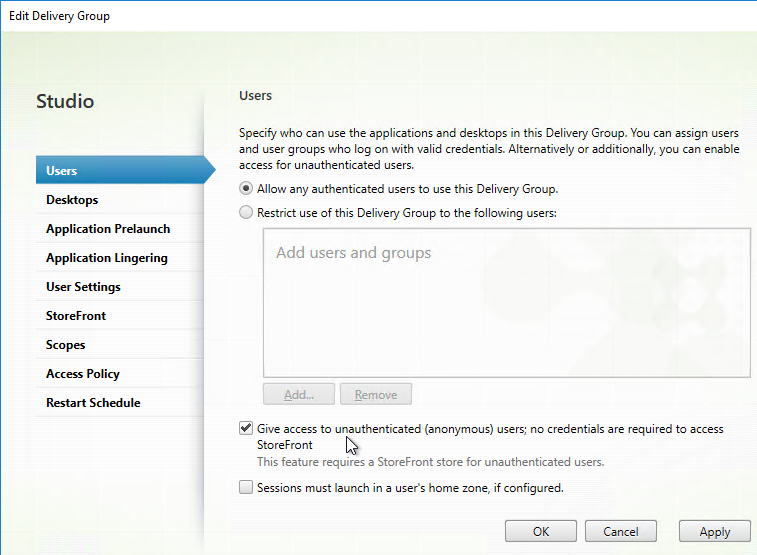
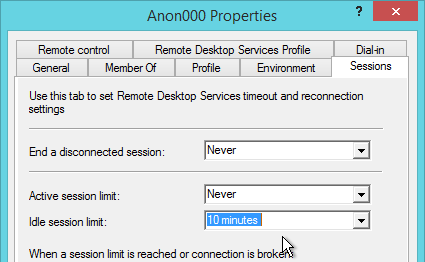
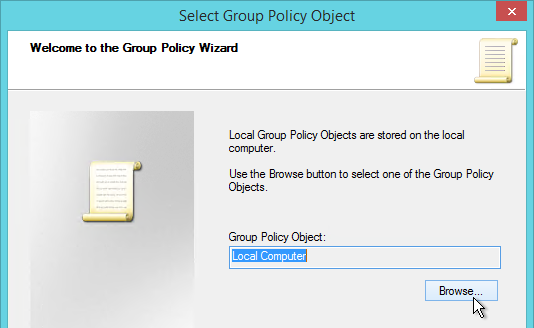
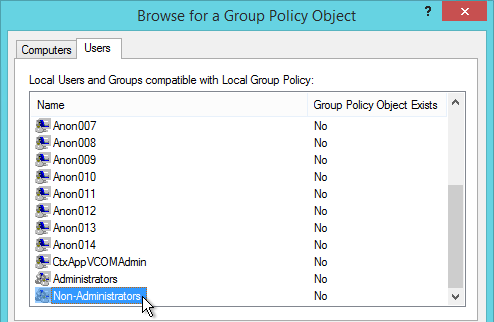
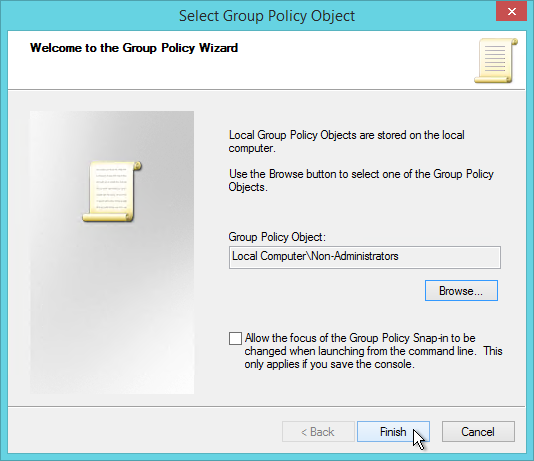
Anonymous Users are managed differently than regular Domain Users. See VDA Anon instructions for adding anon accounts, configuring session timeouts, and configuring local group policy.
Anonymous published apps should show up for all authenticated users. However, you can also create a StoreFront store that does not require any authentication.
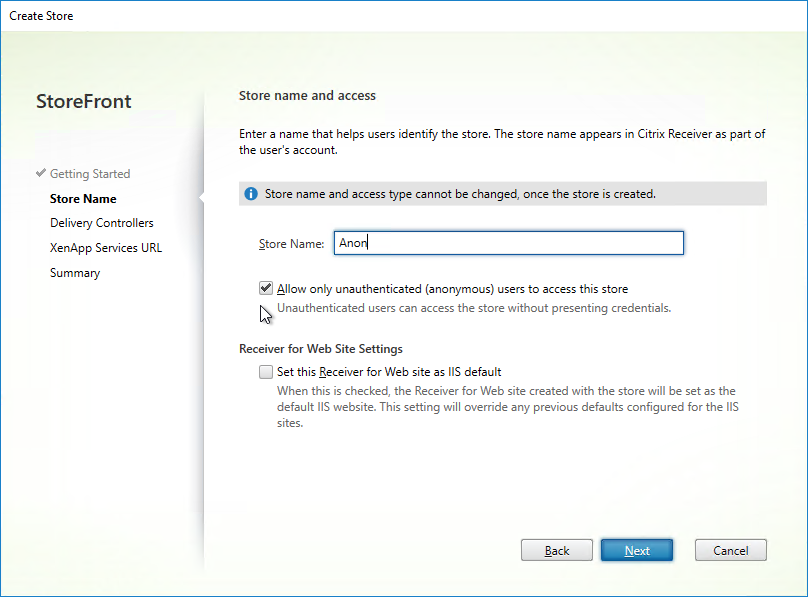
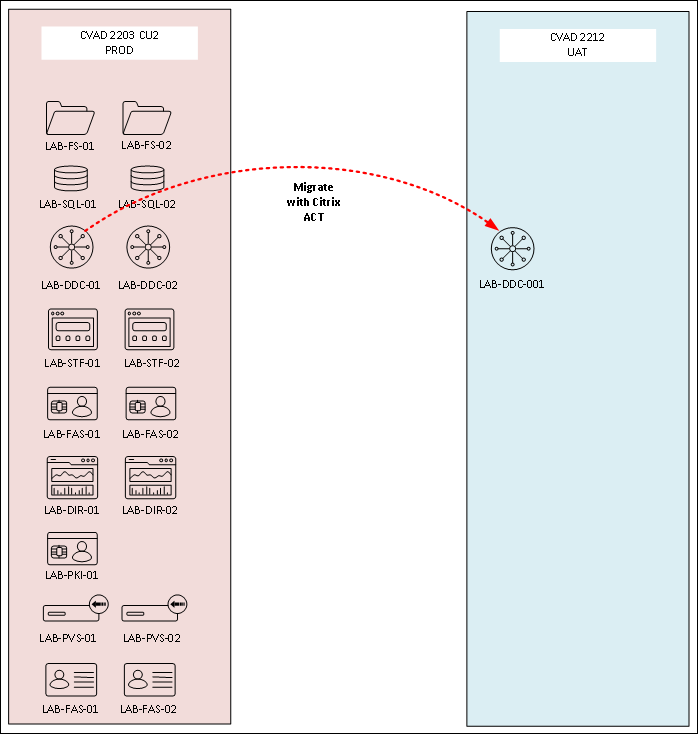
Export/Import Published Applications
If your destination CVAD farm is version 2212 or newer with Web Studio, then you can use Citrix’s Automated Configuration Tool to export and import the configuration. See Citrix Docs PoC Guide: Automated Configuration Tool – On-Premises to On-Premises Migration
Links:
- Citrix CTX582697 Export apps setting and import by using PowerShell
- Kaspars Vilde at XenDesktop/XenApp 7.X Applications – Exporting / Importing at Citrix Discussions has PowerShell scripts to export and import published applications.
- CTP James Kindon Citrix Migration Scripts.
- Steven Lemonier Export and Import On-Prem Citrix Site configuration – scripts to export/import MCS Catalogs, Delivery Groups, and Published Apps.
- CTA Ryan Butler’s XDReplicate at github can export (Export-XDApps) and import (Import-XDApps) published applications.
- Kasper Johansen Citrix Published Apps Migration Script
- Dominik Britz Export And Import Citrix XenDesktop Published Apps – two PowerShell scripts, one to export all published apps to json files and one to import apps with the information of the exported json files. Get the scripts from the Blog Post.






 `
`