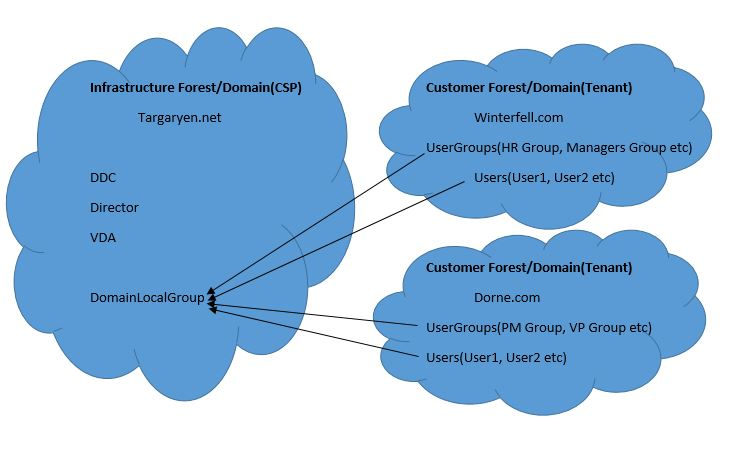
Navigation
💡 = Recently Updated
Change Log
Hardware
Hypervisor Host Hardware
- Citrix Blog Post Citrix Scalability — The Rule of 5 and 10: Simply take the number of physical cores in a hypervisor host, multiply it by 5 or 10, and the result will be your Single Server Scalability. Use 5 if you’re looking for the number of XenDesktop VMs you can host on a box, and use 10 if you’re looking for the number of XenApp user sessions you can host on a box.
Virtual Machine Hardware
- Operating system version support: VDA 7.16 supports Windows 10 (1607 and newer), Windows Server 2012 R2 (RDSH only), and Windows Server 2016 (RDSH or Server VDI).
- For older operating systems (e.g Windows 7 or Windows Server 2008 R2), install VDA 7.15 with the latest Cumulative Update. VDA 7.15 will work with newer Delivery Controllers (e.g. Delivery Controller 7.16).
- CTX224843 Windows 10 compatibility with Citrix XenDesktop
- Citrix provides partial support for Semi-Annual Channel Targeted (aka Current Branch) versions of Windows 10
- Citrix provides full support for Semi-Annual Channel Broad (aka Current Branch for Business) versions of Windows 10, starting with the VDA version released after a Windows 10 version is designated as Broad (typically 4 months and 4 patches after initial release).
- Windows 10 1709 Targeted: Citrix has a live article about this: CTX229052. The Microsoft patches required for 1709 will come out in 2 dates:
- Nov 14th (Patch Tuesday KB4051314) will allow you to upgrade from 1703 and older with a VDA already installed, to 1709.
- ’11D’ patch (last week of November via Microsoft Update Catalogue) will allow you to do a fresh new VDA install on top of 1709.
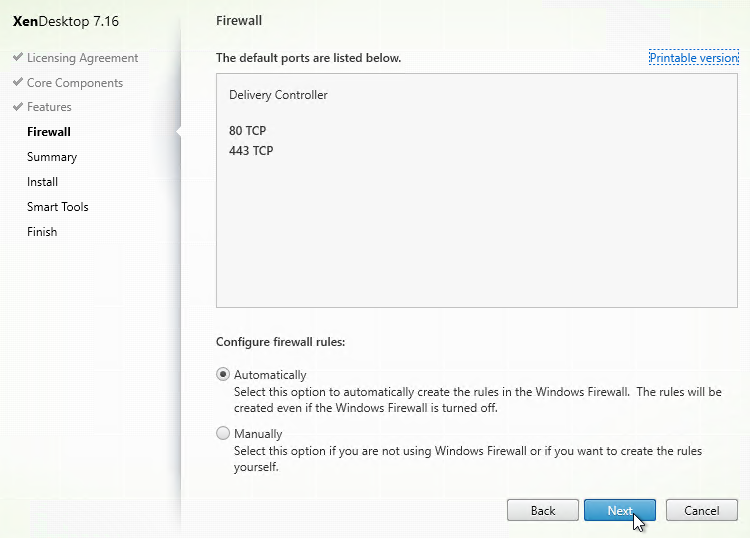
- Firewall – VDA 7.16 enables the UDP-based EDT protocol by default. Make sure the UDP ports are open for ICA/HDX:
- UDP 1494
- UDP 2598
- UDP 443 – from Internet to NetScaler Gateway.
- UDP 443 can also be used by internal ICA connections if VDA SSL is configured.
- For EDT through NetScaler Gateway, make sure your NetScaler firmware is up to date, preferably 11.1 build 56 or newer.
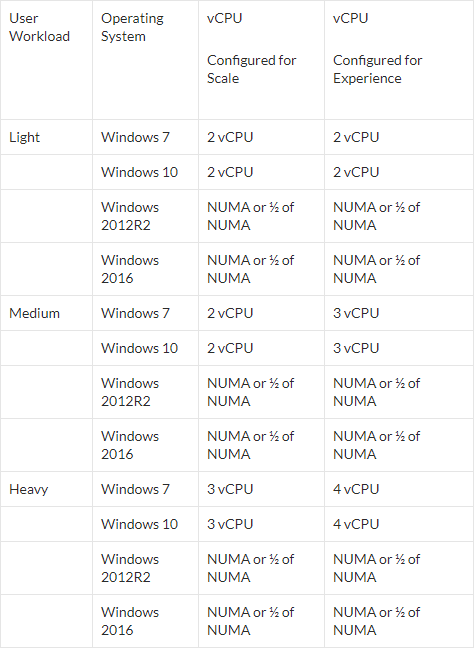
- VDA virtual machine sizing:
- For Windows 10 virtual desktops, give the virtual machine: 2+ vCPU and 2+ GB of RAM
- For Windows 2012 R2 RDSH, give the virtual machine 8 vCPU, and 24-48 GB of RAM
- See Daniel Feller Sizing Windows 2016, Windows 2012 And Windows 10 Virtual Machines
- If using RAM caching (MCSIO or PvS), add more RAM for the cache
- Remove the floppy drive
- Remove any serial or LPT ports
- If vSphere:
- To reduce disk space, reserve memory. Memory reservations reduce or eliminate the virtual machine .vswp file.
- The NIC should be VMXNET3.
- If this VDA will boot from Provisioning Services:
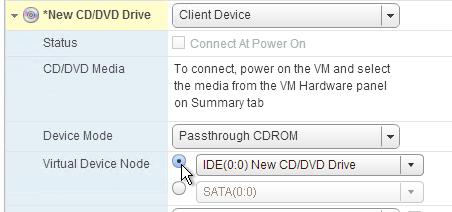
- For vSphere, the NIC must be VMXNET3.
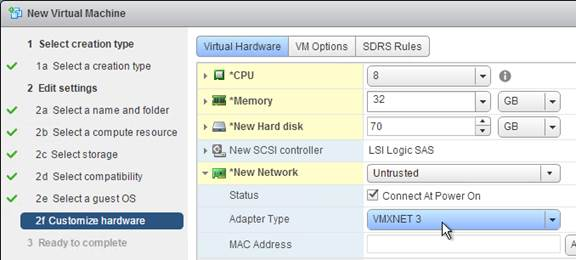
- For vSphere, configure the CD-ROM to boot from IDE instead of SATA. SATA comes with VM hardware version 10. SATA won’t work with PvS.
- Install the latest version of hypervisor drivers (e.g. VMware Tools).
- The vSphere Activity Monitoring Feature with NSX Guest Introspection feature uses a TDI driver (vnetflt.sys), which might cause a “Connection Interrupted” message when users log off of Citrix. See CTX221206 “Connection Interrupted” error message displayed while logging off ICA session.
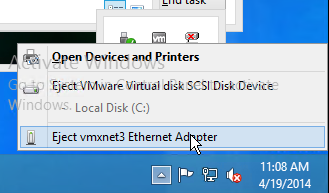
If vSphere, disable NIC Hotplug
- Users could use the systray icon to Eject the Ethernet Controller. Obviously this is bad.
- To disable this functionality, power off the virtual machine.
- Once powered off, right-click the virtual machine, and click Edit Settings.
- On the VM Options tab, expand Advanced, and then click Edit Configuration.
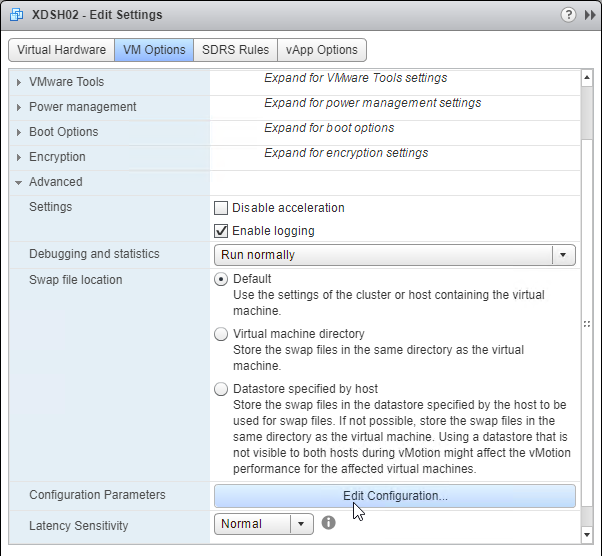
- On the bottom left, enter devices.hotplug. On the right, enter false. Then click Add.
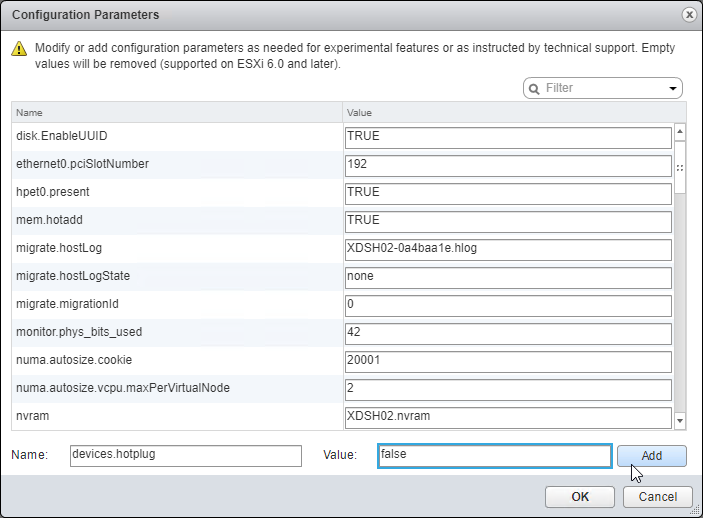
- Then click OK a couple times to close the windows.
- The VM can then be powered on.
Windows Preparation
- Computer Group Policy – Make sure the Master VM is in the same OU as the Linked Clones so the Master VM will get the computer-level GPO settings in its registry. Run gpupdate on the master after moving the VM to the correct OU. When Clones are created from the Master, the computer-level GPO settings will already be applied, thus eliminating a timing issue.
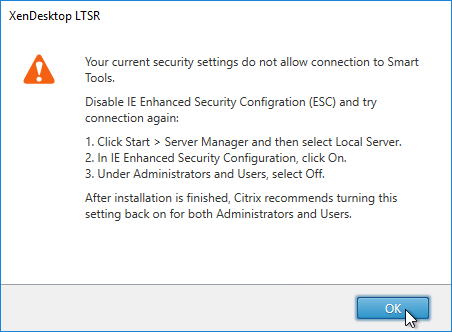
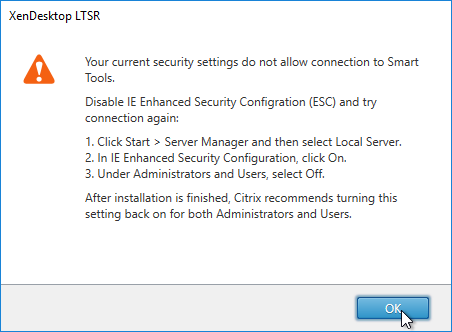
- If Server OS, disable IE Enhanced Security Configuration in Server Manager > Local Server.
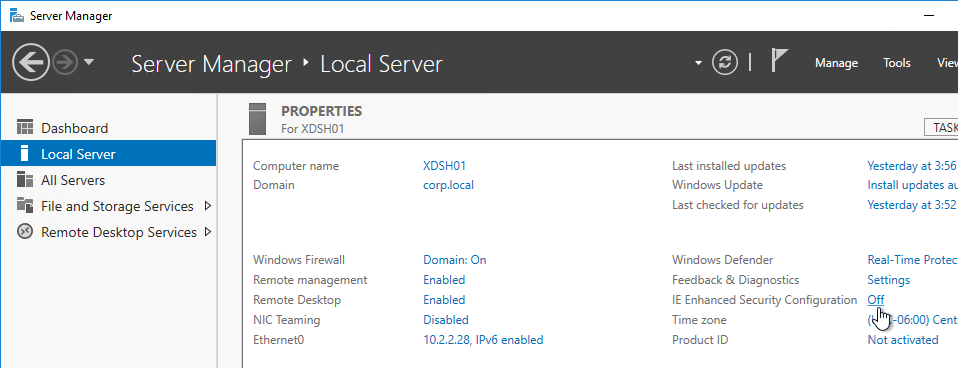
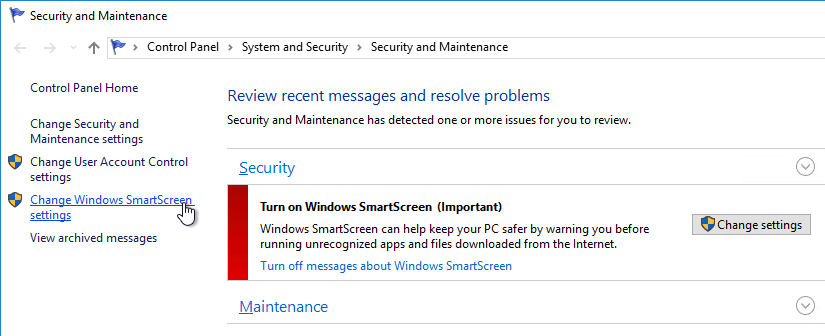
- Optionally, go to Action Center (Windows 2012 R2) or Control Panel > Security and Maintenance (Windows 10/2016) to disable User Account Control, and enable SmartScreen.
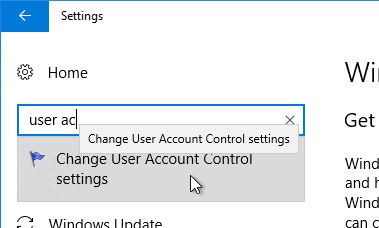
- In Windows 10 1703 and newer, search the Settings app for Change User Account Control settings.
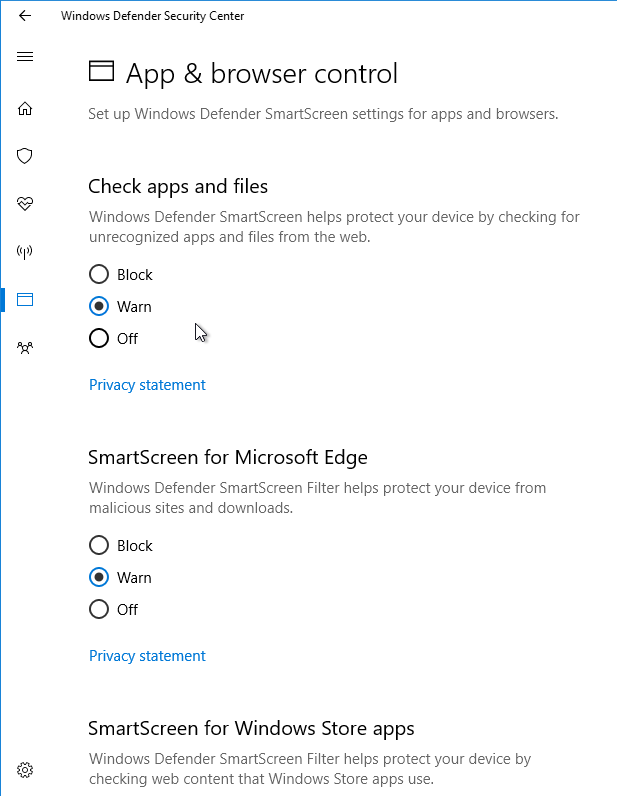
- SmartScreen is configured in Windows Defender Security Center > App & browser control.
- Run Windows Update. Do not skip this step. Many VDA installation problems are fixed by simply updating Windows.
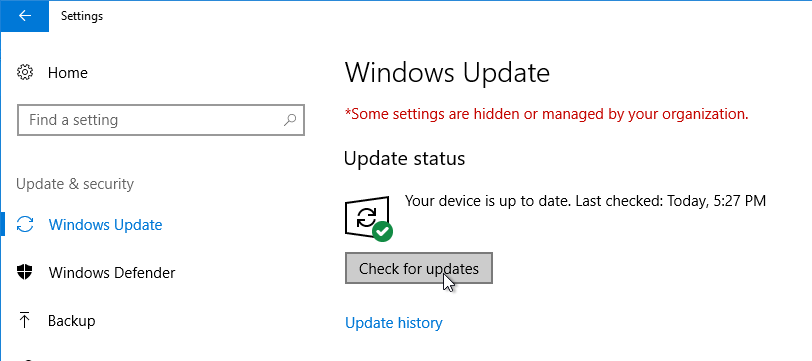
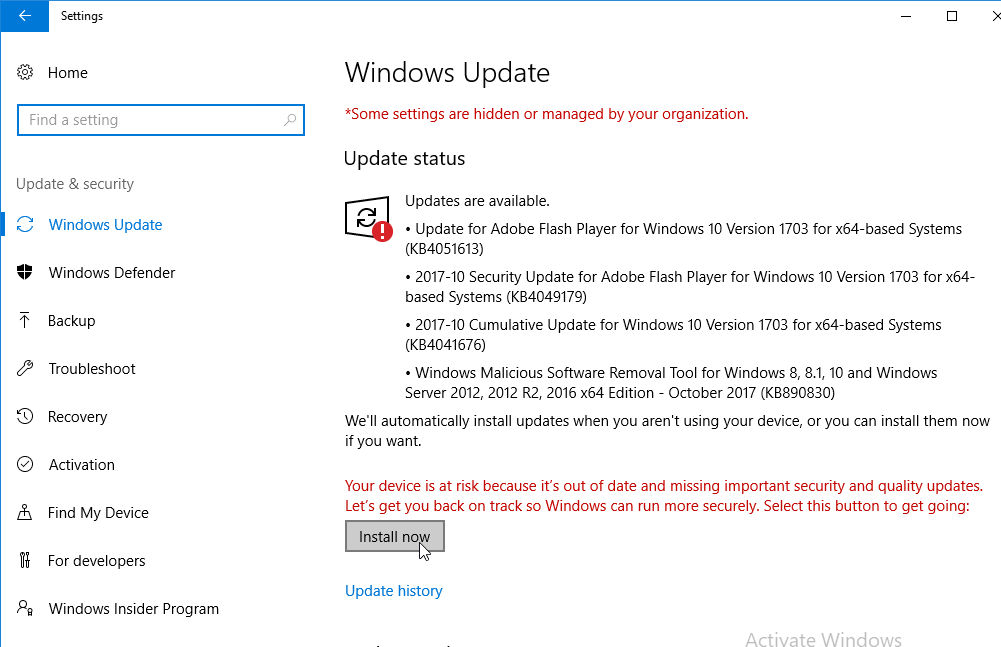
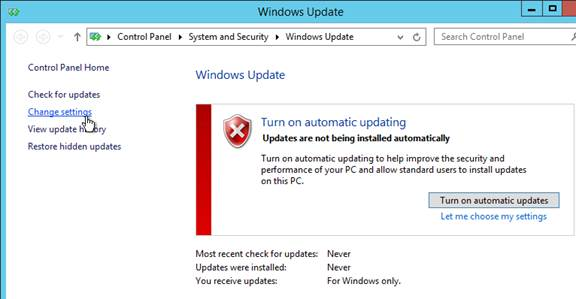
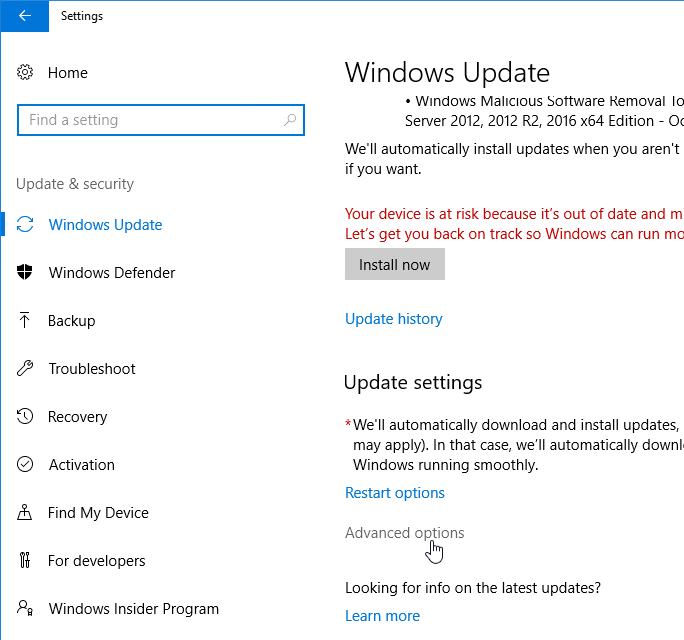
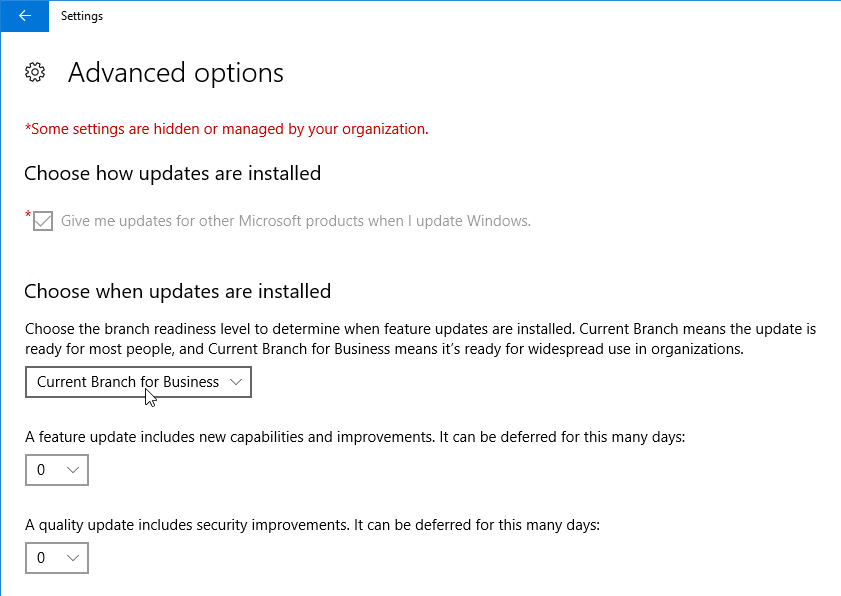
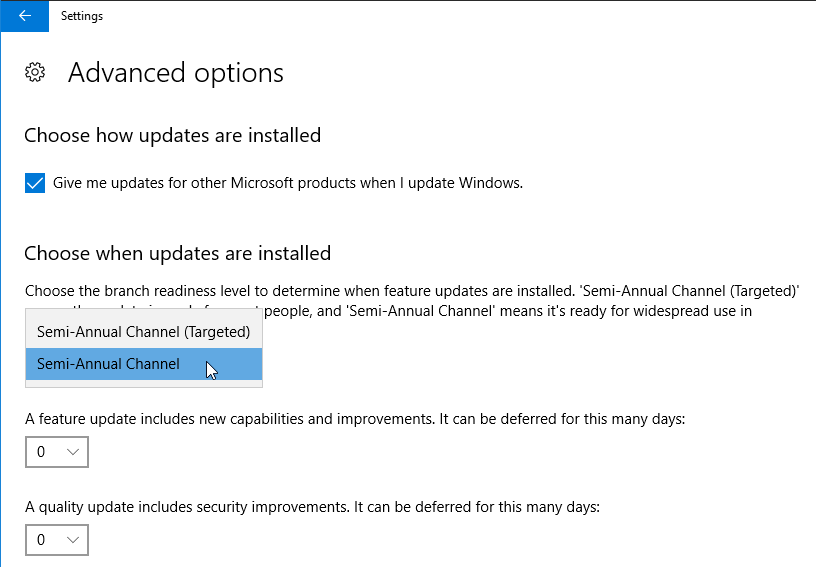
- Defer Feature Updates – For Windows 10, since Citrix VDA does not immediately support new Windows 10 versions, configure Windows Update to defer feature updates.
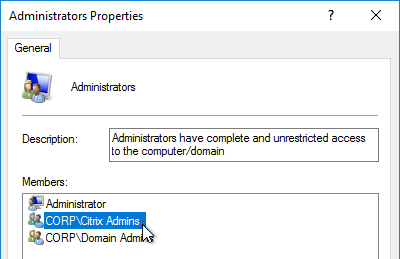
- Add your Citrix Administrators group to the local Administrators group on the VDA. Computer Management.
- The Remote Desktop Services “Prompt for Password” policy prevents Single Sign-on to the Virtual Delivery Agent. Check registry key
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\Terminal Services. If fPromptForPassword = 1 then you need to fix group policy. The following GPO setting will prevent Single Sign-on from working.
Computer Configuration | Policies | Administrative Templates | Windows Components | Remote Desktop Services | Remote Desktop Session Host | Security | Always prompt for password upon connection
Or set the registry value HKEY_LOCAL_MACHINE\SOFTWARE\Citrix\PorticaAutoLogon (DWORD) = 0x10.
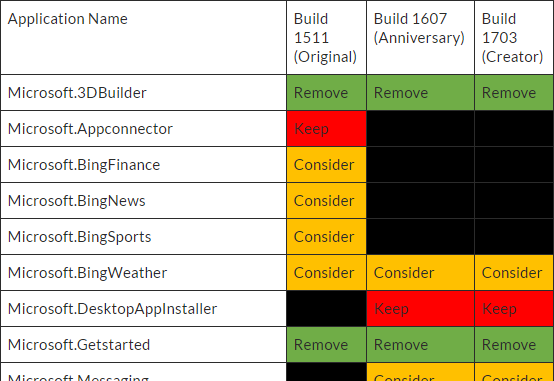
- To remove the built-in apps in Windows 10, see Robin Hobo How to remove built-in apps in Windows 10 Enterprise.
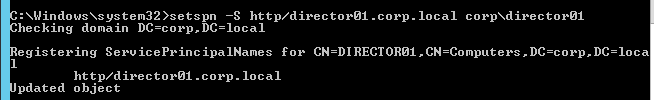
- For Remote Assistance in Citrix Director, configure the GPO setting Computer Configuration | Policies | Administrative Templates | System | Remote Assistance | Offer Remote Assistance. See Jason Samuel – How to setup Citrix Director Shadowing with Remote Assistance using Group Policy for more details.
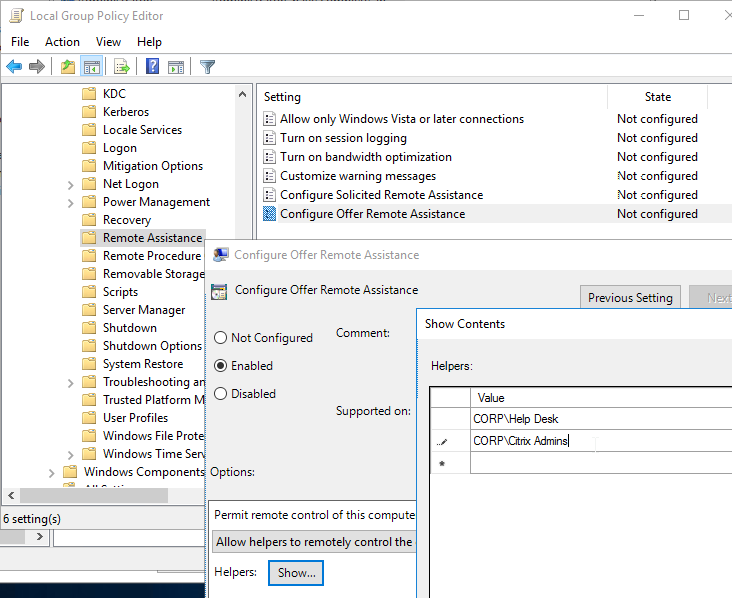
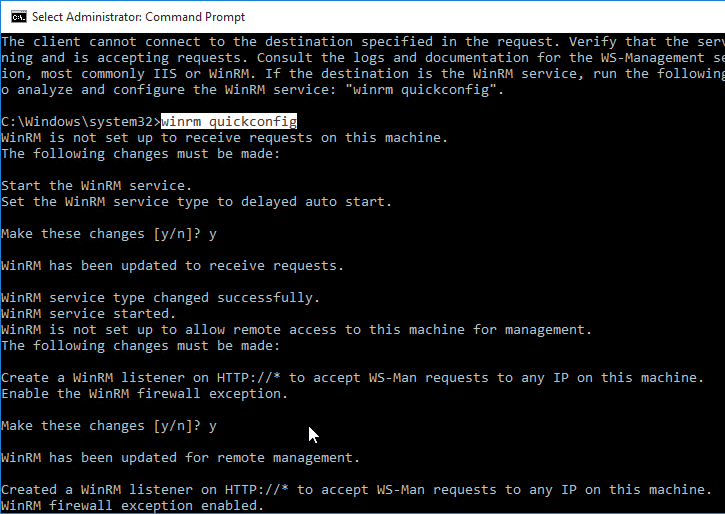
- If you intend to use Citrix’s SCOM Management Packs for XenApp/XenDesktop, make sure WinRM is enabled on the VDA by running winrm quickconfig. Or you can enable WinRM using Group Policy.
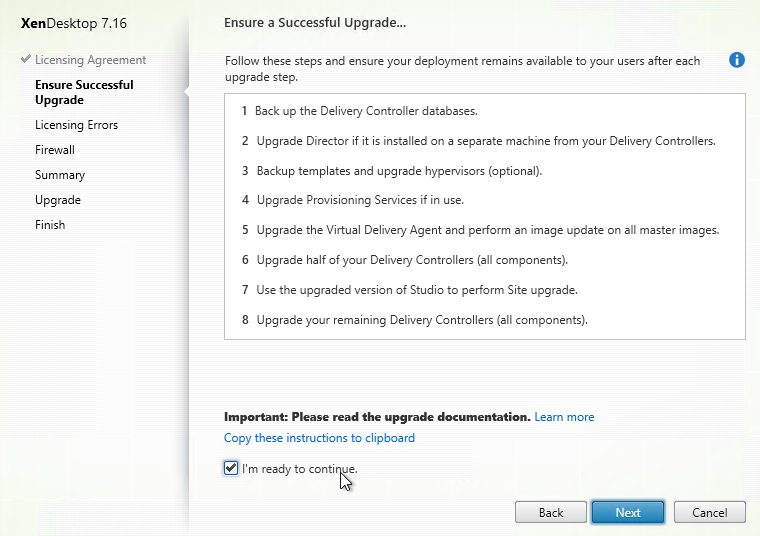
Install Virtual Delivery Agent 7.16
- For virtual desktops, make sure you are logged into the console. The VDA won’t install if you are connected using RDP.
- Make sure .NET Framework 4.5.2 or newer is installed.
CLI Install:
Command Line Install Options are detailed at Install using the command line at Citrix Docs.
The Citrix Telemetry Service seems to cause problems. You can use the Command Line Installer to exclude Telemetry Service as detailed at VDA upgrade cmdlet at Citrix Discussions.
XenDesktopVDASetup.exe /quiet /noreboot /masterimage /Enable_HDX_PORTS /enable_framehawk_port /Enable_REAL_TIME_TRANSPORT /optimize /controllers "xdc01.corp.local xdc02.corp.local" /Exclude "Citrix Telemetry Service"
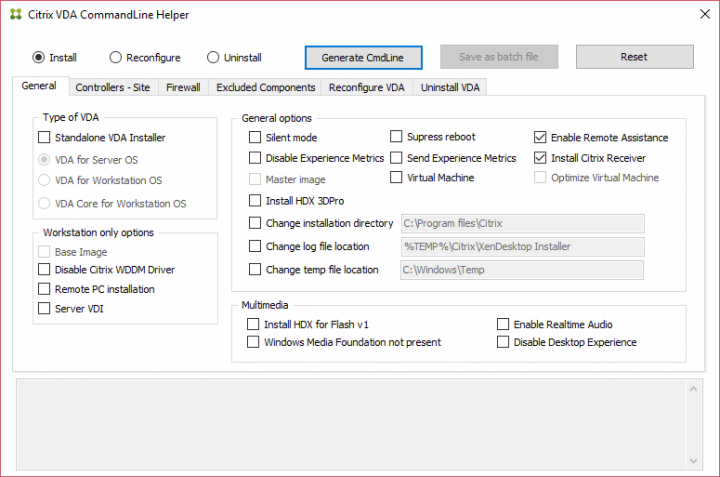
Citrix Blog Post Citrix VDA Commandline Helper Tool: a GUI to configure the VDA installation options.
GUI Install:
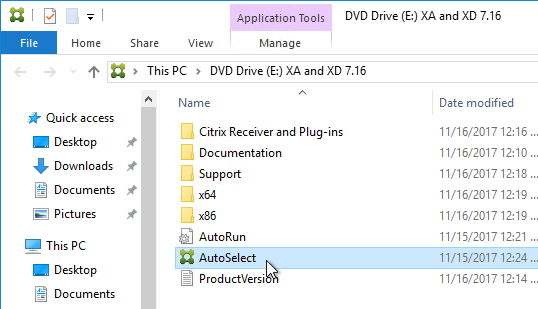
- Mount the downloaded XenDesktop 7.16 ISO, and and run AutoSelect.exe.
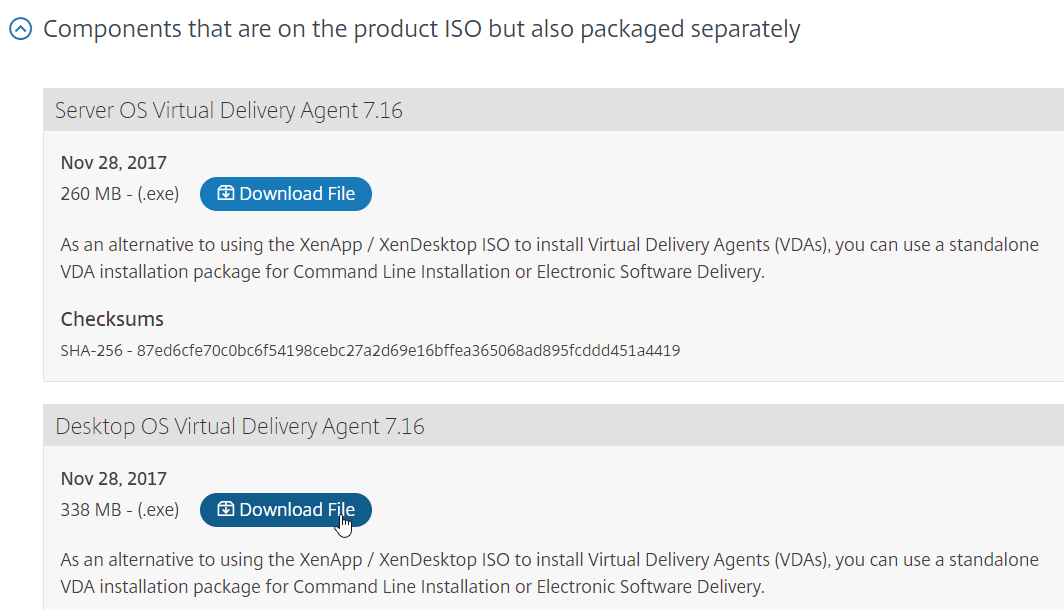
- Alternatively, you can download the standalone VDA package and run that instead. Go the main XenDesktop 7.16 download page. Expand the section labelled Components that are on the product ISO but also packaged separately. There is a VDA installer called Desktop OS Core Services that is designed for Remote PC deployments.
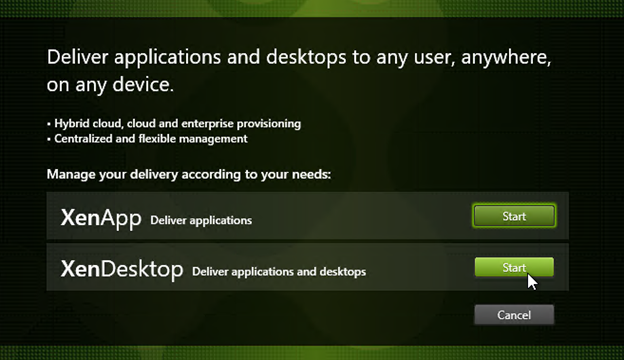
- Click Start next to either XenApp or XenDesktop. The only difference is the product name displayed in the installation wizard.
- On the top right, click Virtual Delivery Agent for Windows Desktop OS, or Windows Server OS, depending on which type of VDA you are building.
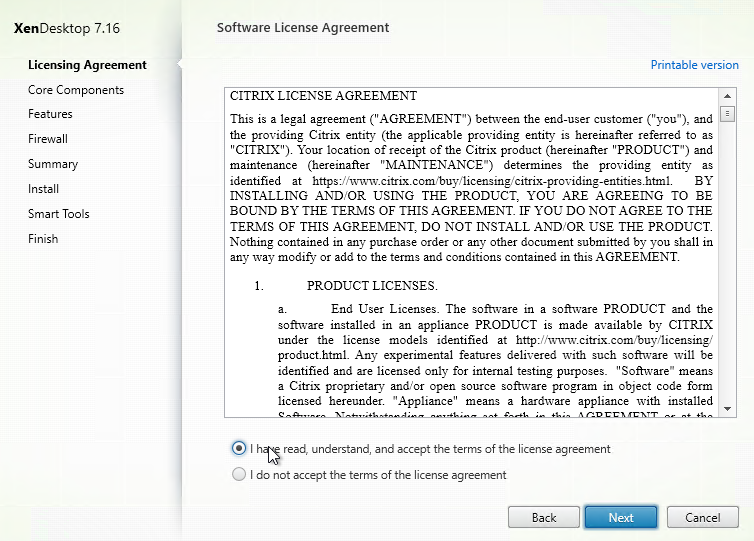
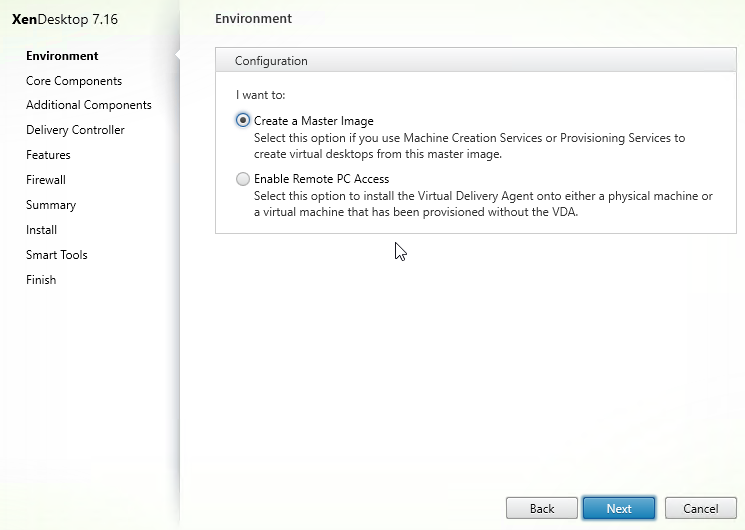
- In the Environment page, select Create a Master Image, and click Next.
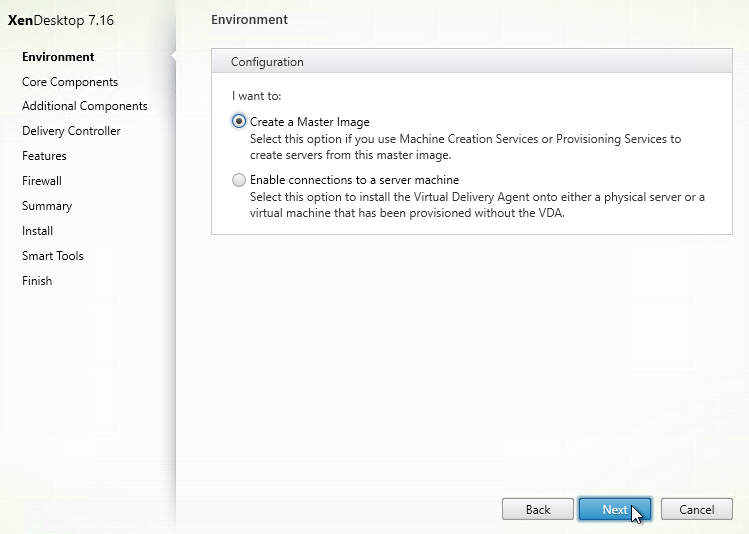
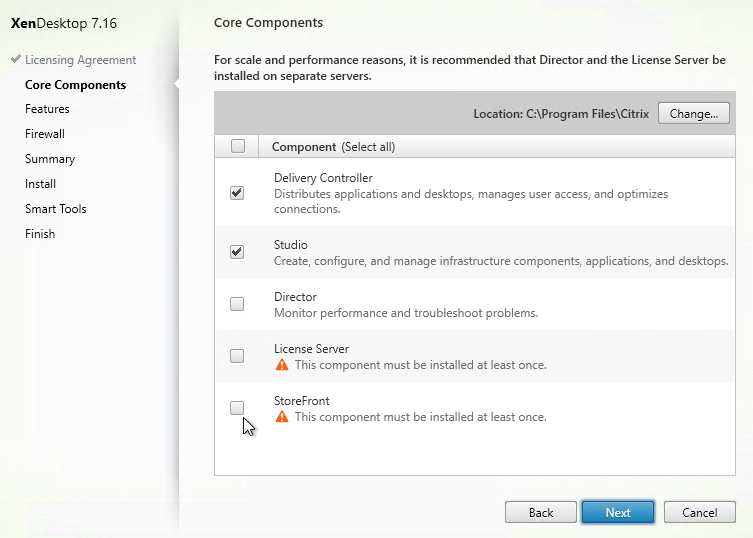
- In the Core Components page, if you don’t need Citrix Receiver installed on your VDA, then uncheck the box. Receiver is usually only needed for double-hop connections (connect to first VDA, and then from there, connect to second VDA). Click Next.
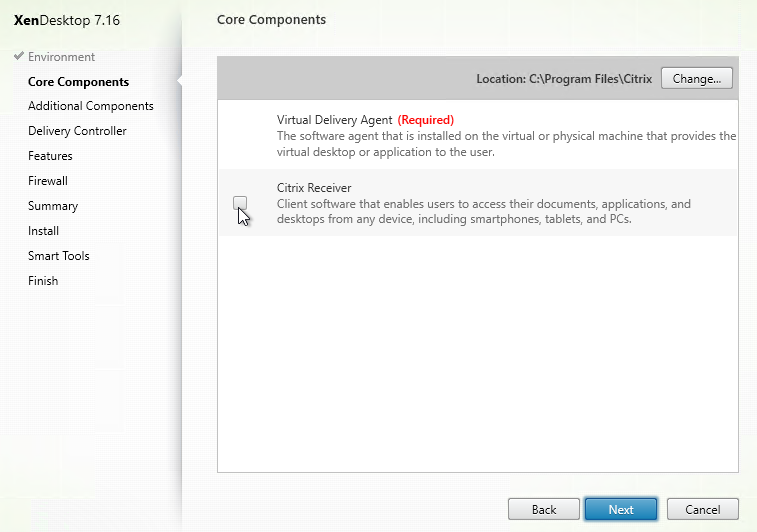
- In the Additional Components page, uncheck Citrix AppDisk/Personal vDisk. This feature has been deprecated and is being replaced by Citrix App Layering (Unidesk). Click Next.
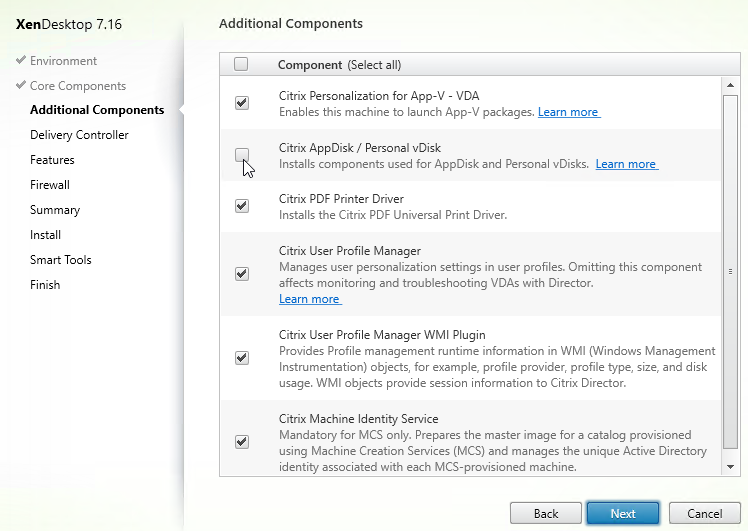
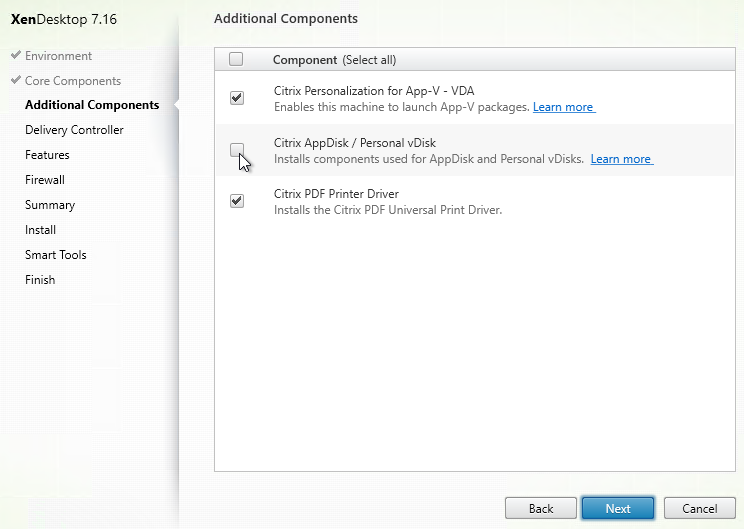
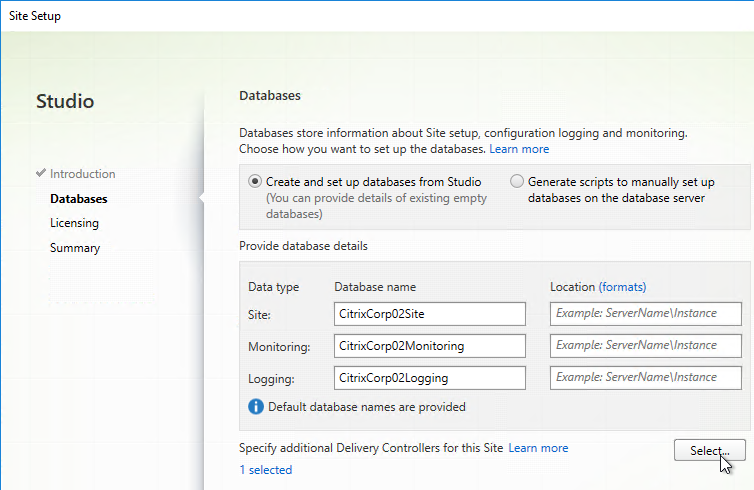
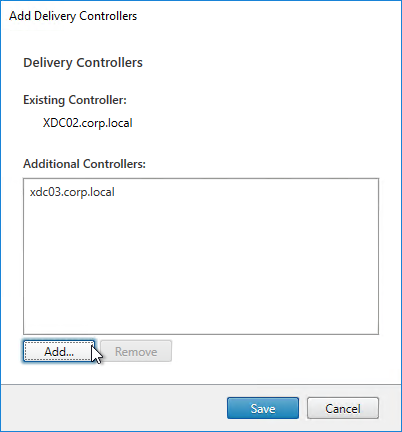
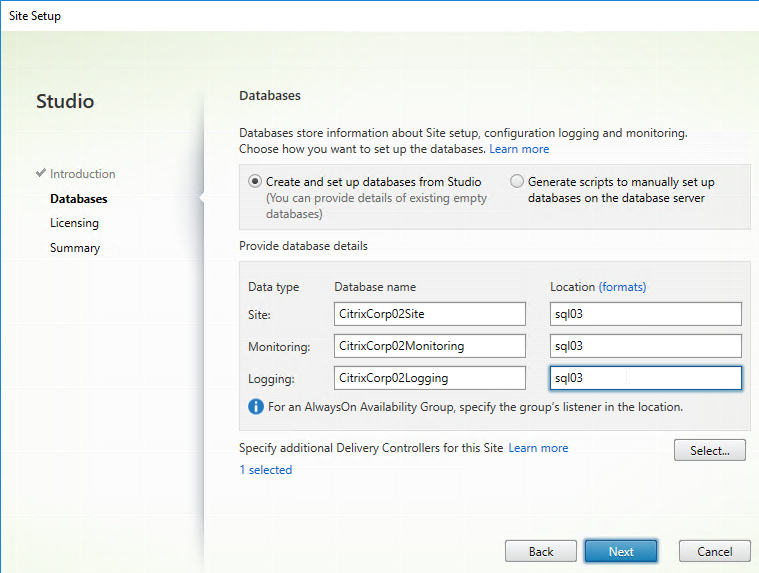
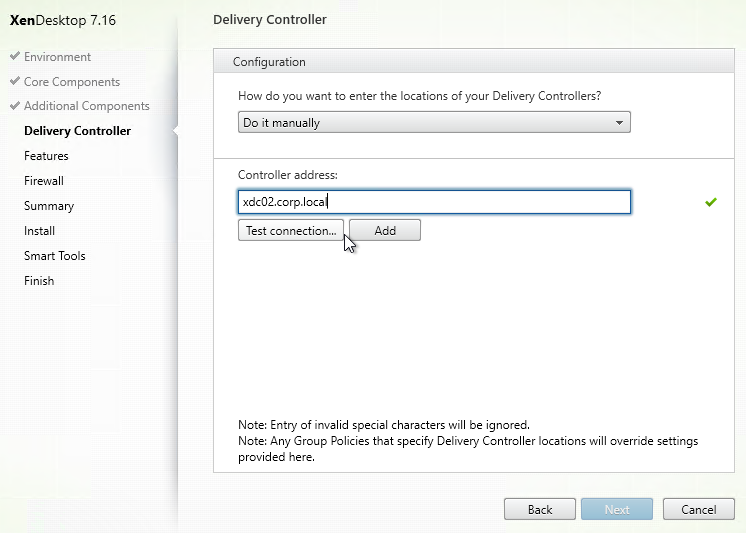
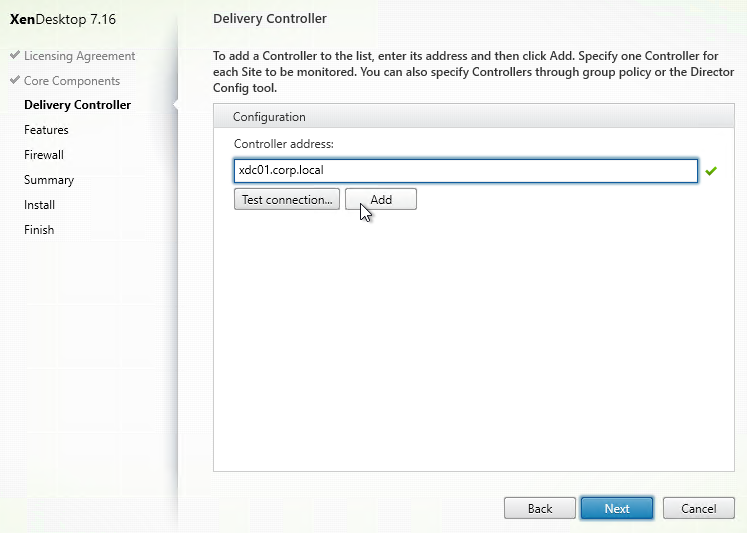
- In the Delivery Controller page, select Do it manually. Enter the FQDN of each Controller. Click Test connection. And then make sure you click Add. Click Next when done.
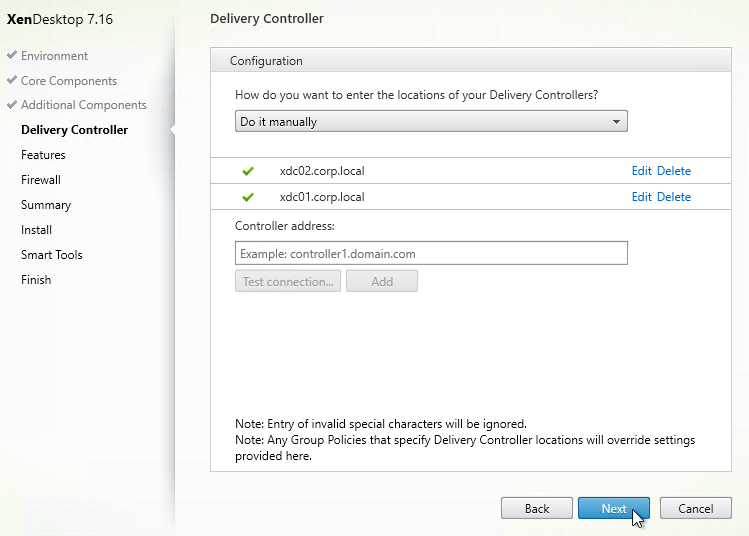
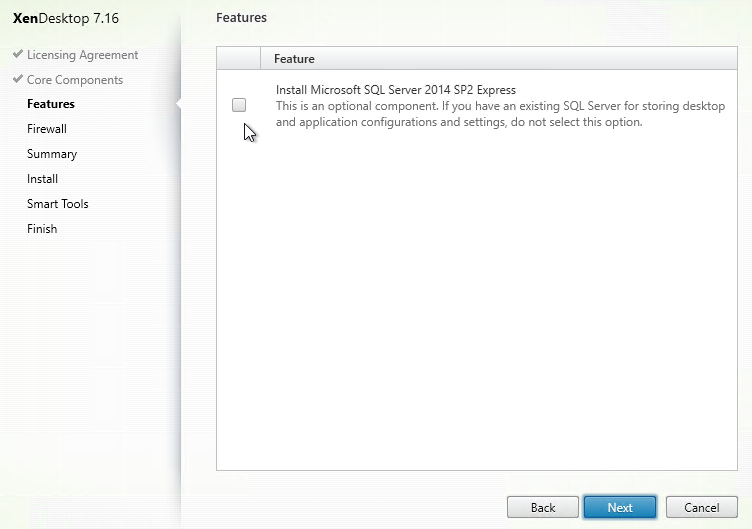
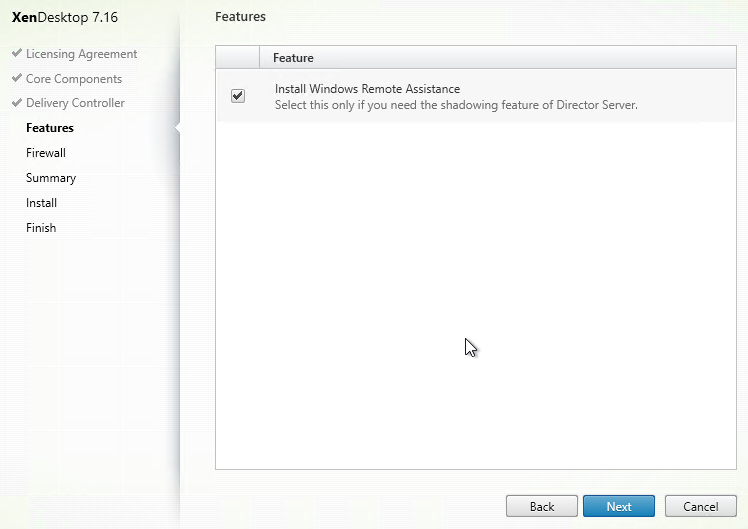
- In the Features page, check boxes. Only the top box is checked by default. If you want to use the other features, check the boxes. If this is a virtual desktop, you can leave Personal vDisk unchecked now and enable it later. Then click Next.
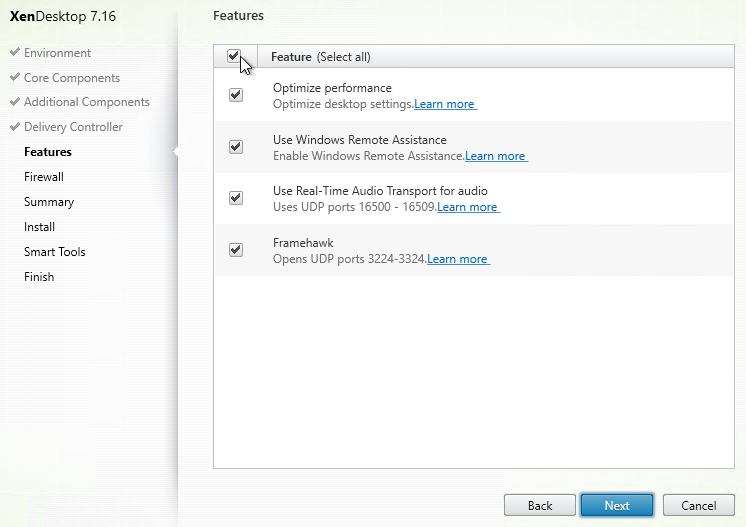
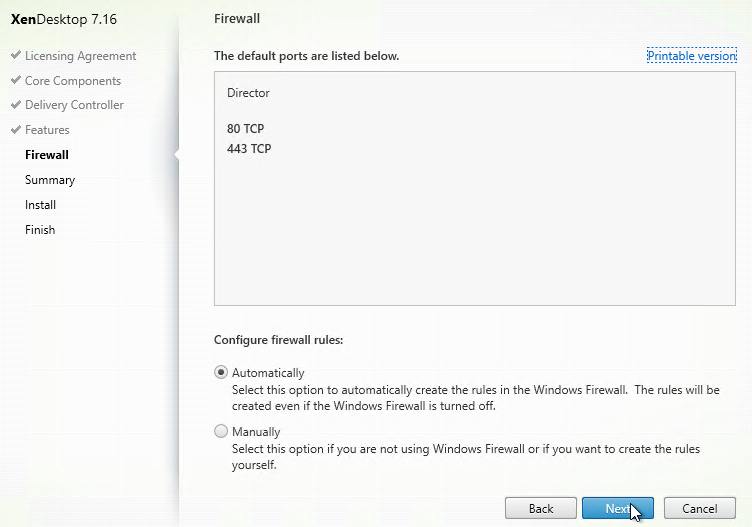
- In the Firewall page, click Next.
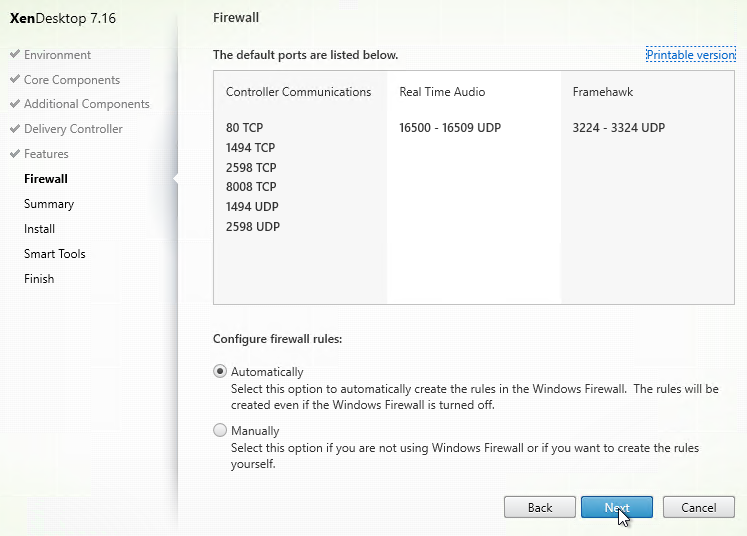
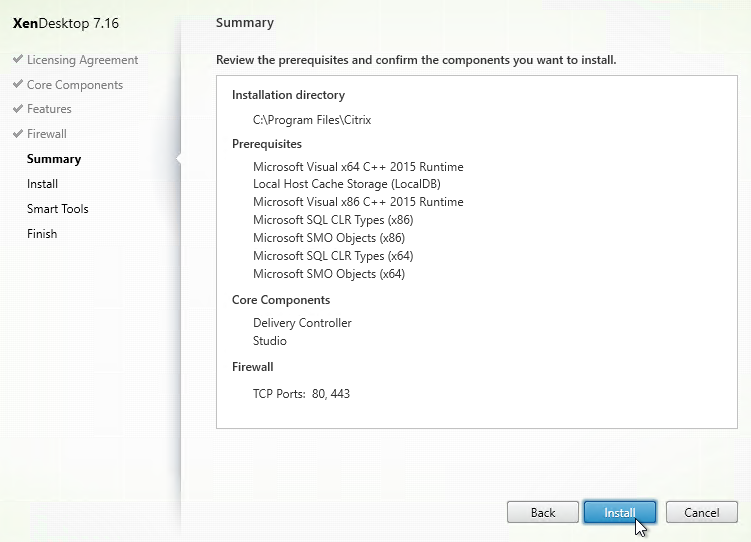
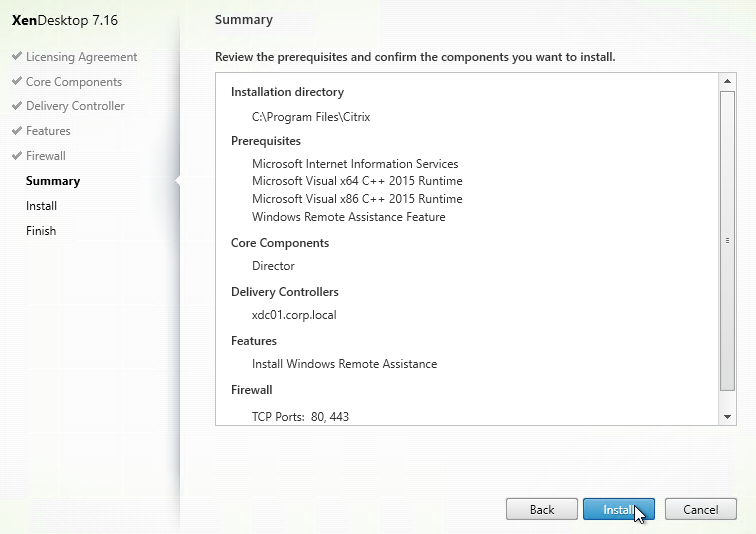
- In the Summary page, click Install.
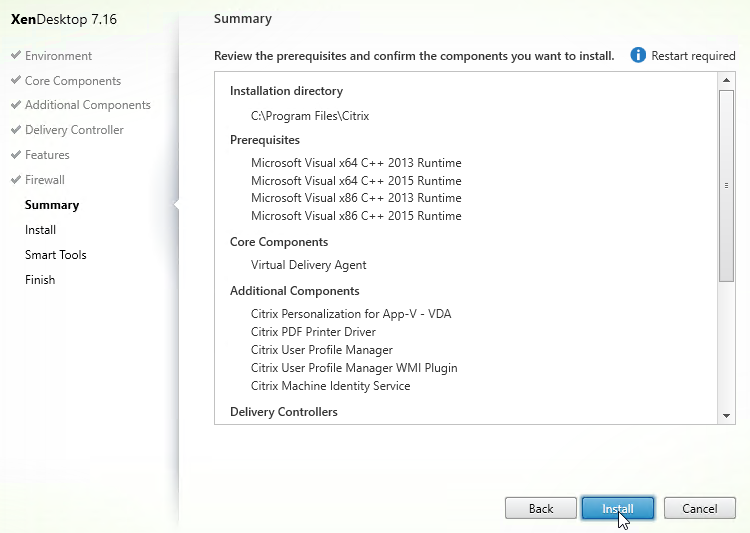
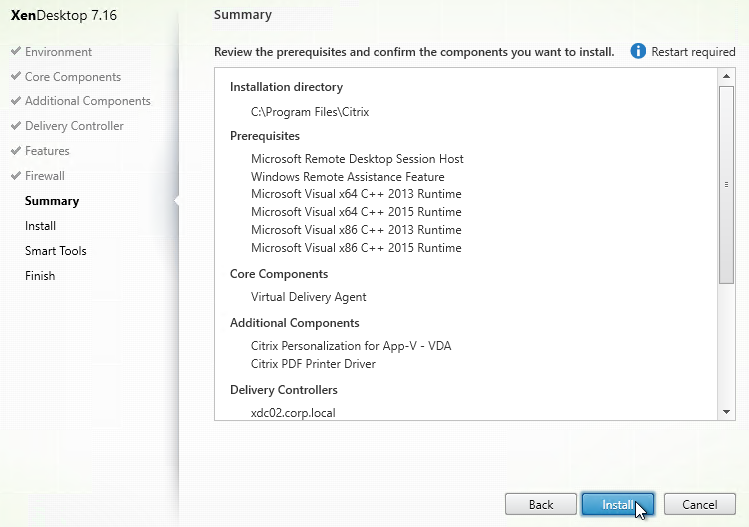
- If RDSH, click Close when you are prompted to restart.
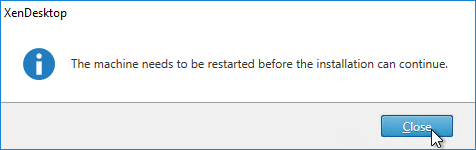
- After the machine reboots twice, login and installation should continue.
- If you see a Locate ‘XenDesktop’ installation media window, click Cancel.
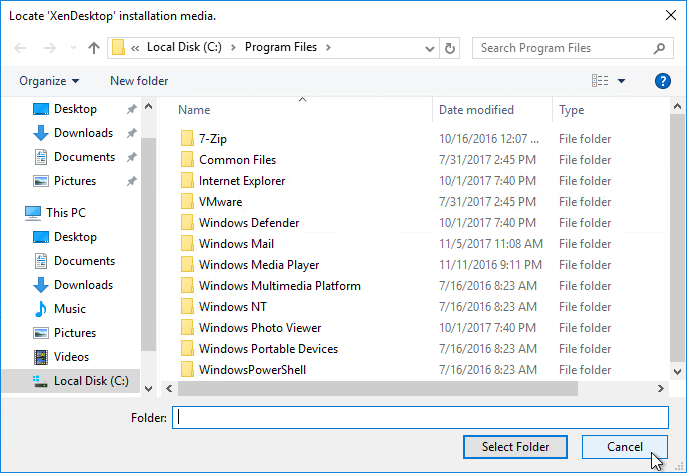
- Mount the XenApp_and_XenDesktop_7_16.iso.
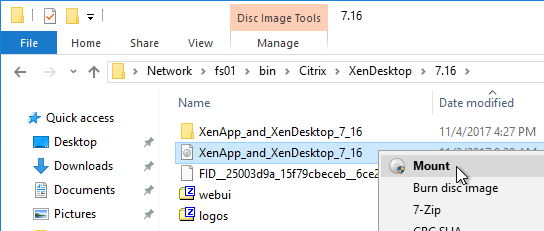
- Run AutoSelect.exe.
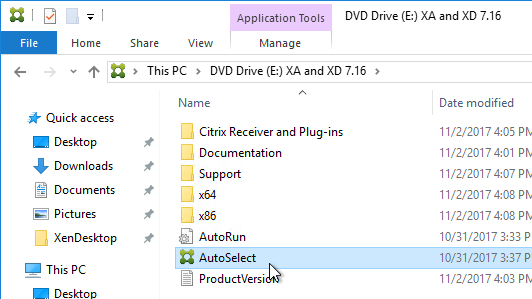
- Click the Virtual Desktop Agent box to resume installation.
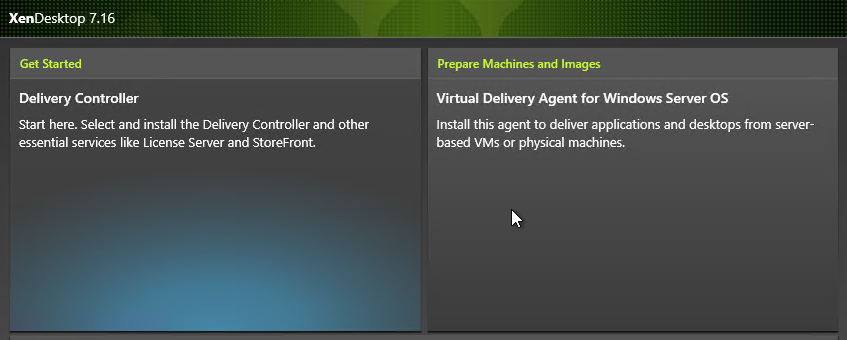
- Installation will continue automatically.
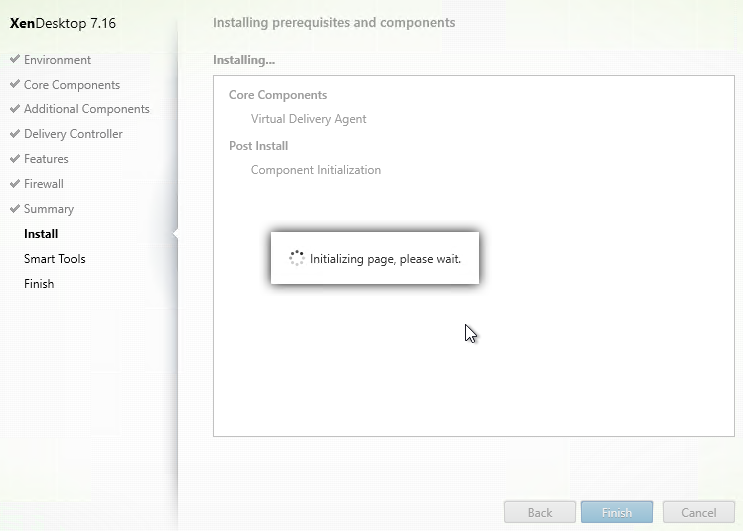
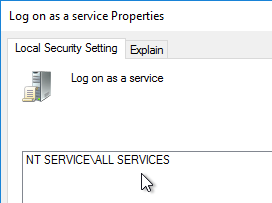
- Note: NT SERVICE\CitrixTelemetryService needs permission to login as a service.
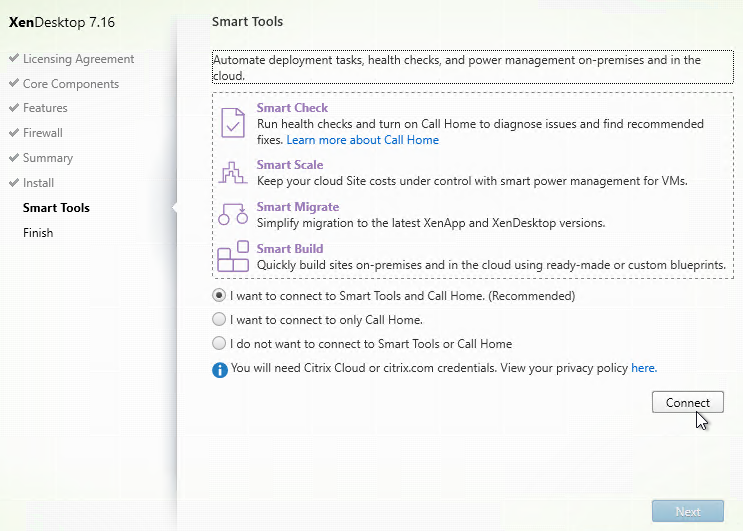
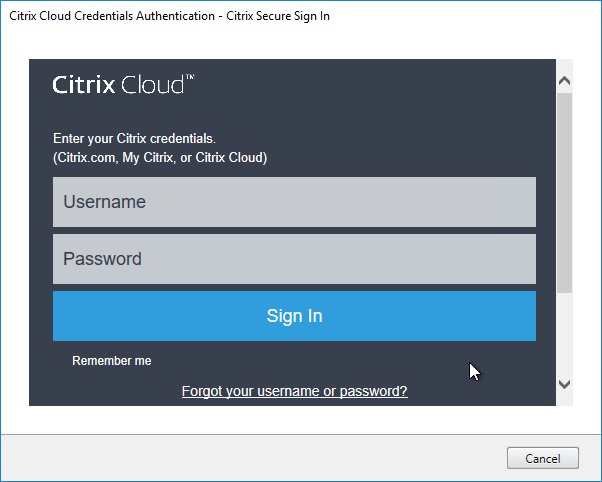
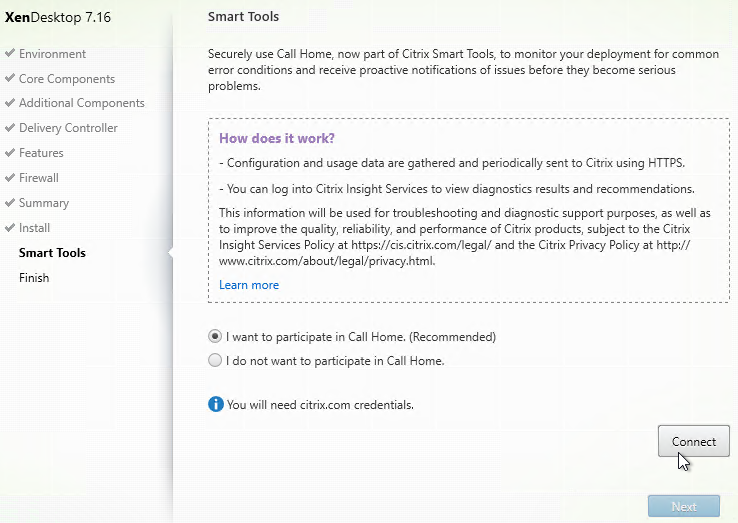
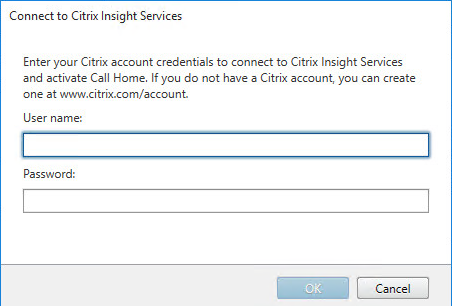
- In the Smart Tools page, click Connect, enter your MyCitrix.com credentials, and then click Next.
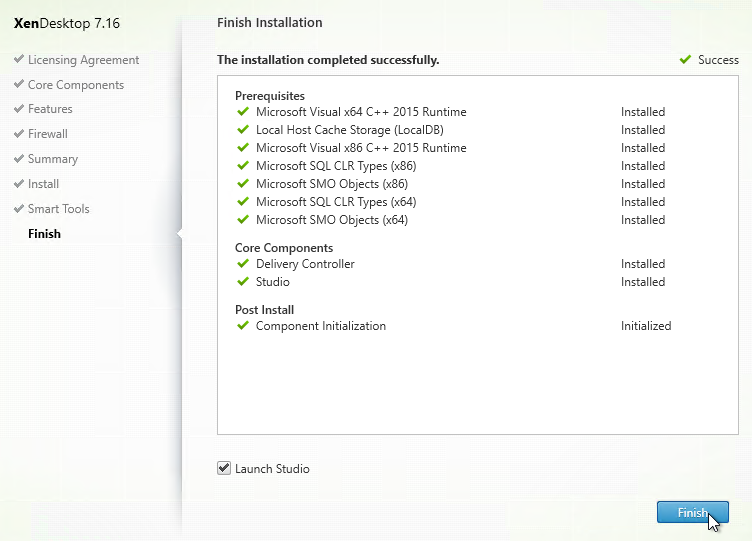
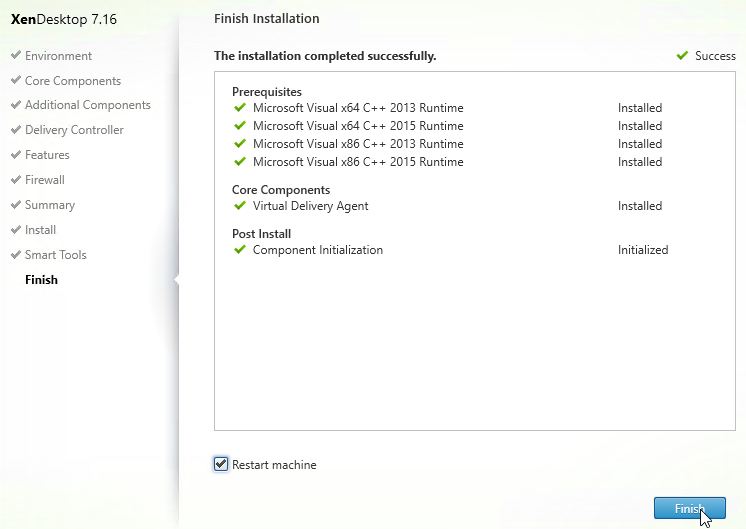
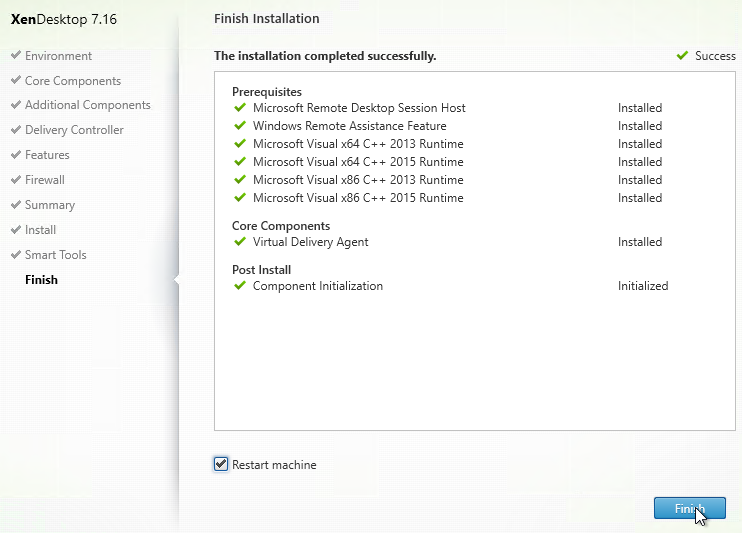
- In the Finish page, click Finish to restart the machine again.
- According to CTX225819 When Launching an Application Published from Windows Server 2016, a Black Screen Appears for Several Seconds Before Application is Visible, HKLM\SOFTWARE\Citrix\Citrix Virtual Desktop Agent\DisableLogonUISuppression (DWORD) should be set to 0.
RDSH – VDA 7.16 Hotfix 1
- For RDSH (multi-user Sever OS) VDAs, download VDA 7.16 Hotfix 1 from CTX231127.
- Run the downloaded ServerVDACoreX64_7_16_001.msp.
- In the Welcome to the Citrix HDX TS (retail) Setup Wizard page, click Next.
- In the Ready to update page, click Update.
- In the Completed the Citrix HDX TS (retail) Setup Wizard page, click Finish.
- Click Yes to restart your computer.
- Programs and Features > Installed Updates shows the installed hotfix.
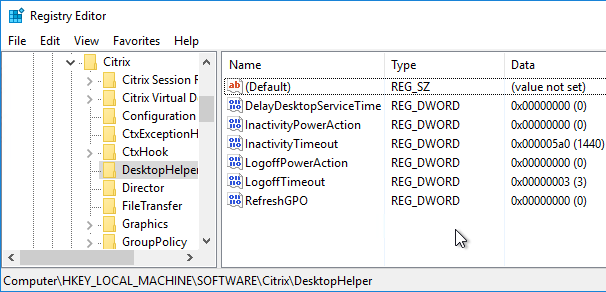
Citrix Desktop Helper Service
Citrix Blog Post Augment Your XenDesktop Deployment with the Desktop Helper Service: this installable service adds the following functionality to your VDAs:
- The “Shutdown Inactive Desktops” feature allows Citrix administrators to enable a timer that shuts down a virtual desktop after it has been registered for a configured amount of minutes without a user connection.
- Delaying the Citrix Desktop Service start by a configurable amount of time allows the desktop to finish performing on-boot tasks before a user is brokered to it.
- The “Force Group Policy Update” feature give administrators the ability to force a group policy update after a configured amount of time.
If these features are desirable, download the tool from the blog post and install it.
Configurable Registry keys are located at HKEY_LOCAL_MACHINE\SOFTWARE\Citrix\DesktopHelper. Each value is detailed in the accompanying Word document.
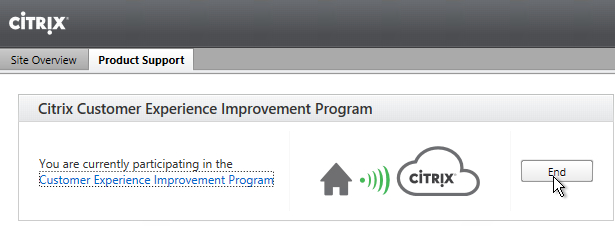
Customer Experience Improvement Program (CEIP)
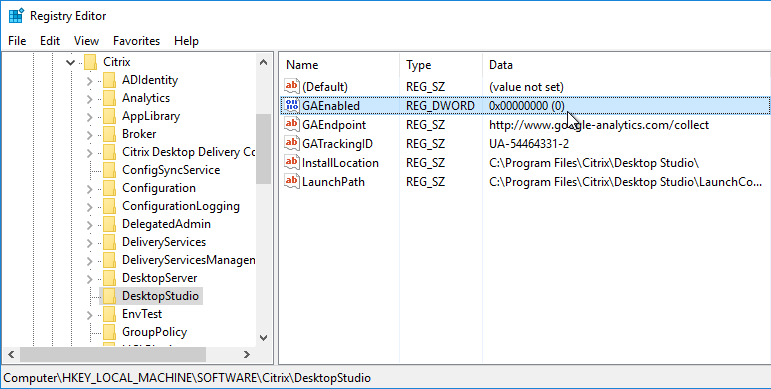
Customer Experience Improvement Program (CEIP) is enabled by default. To disable it, create the registry value HKEY_LOCAL_MACHINE\SOFTWARE\Citrix\Telemetry\CEIP\Enabled (DWORD), and set it to 0 (zero). Also see CEIP at Citrix Insight Services at Citrix Docs.
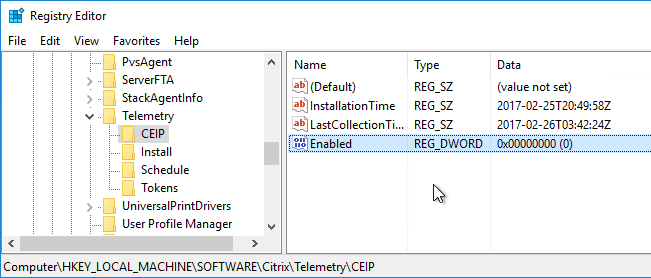
See https://www.carlstalhood.com/delivery-controller-7-16-and-licensing/#ceip for additional places where CEIP is enabled.
Connection Quality Indicator
The Connection Quality Indicator tells the user the quality of the connection. For example:
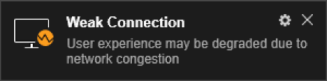
Position of the indicator is configurable by the user. Thresholds are configurable through group policy.
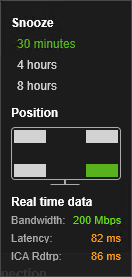
Download it from CTX220774 Connection Quality Indicator and install it. The article is very detailed.
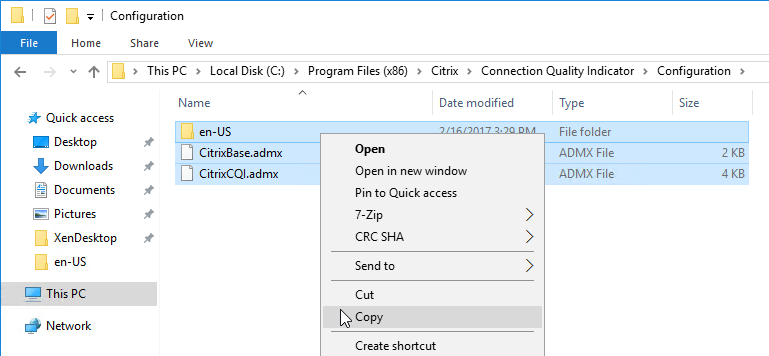
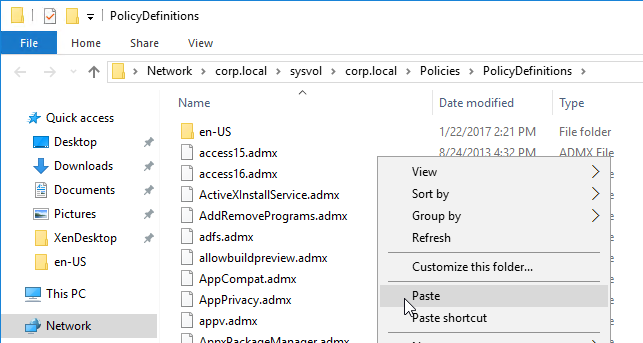
Group Policy templates are located at C:\Program Files (x86)\Citrix\Connection Quality Indicator\Configuration. Copy the files and folder to <Sysvol>\Policies\PolicyDefinitions, or C:\Windows\PolicyDefinitions.
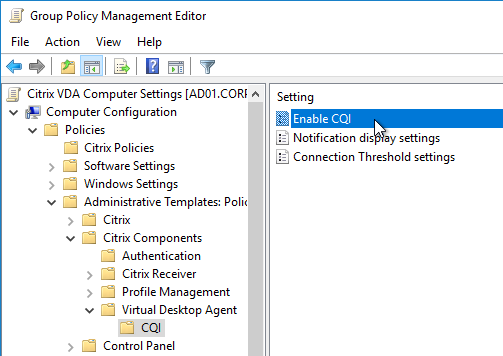
Find the settings under Computer Config | Policies | Administrative Templates | Citrix Components | Virtual Desktop Agent | CQI
Version 1.2 adds the GPO settings to the user half of a GPO.
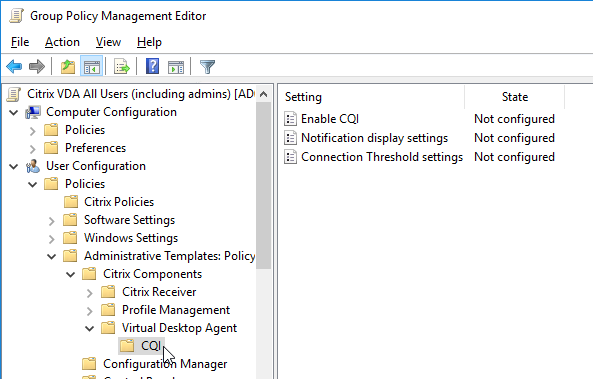
Notification display settings lets you customize the user notifications, or disable them.
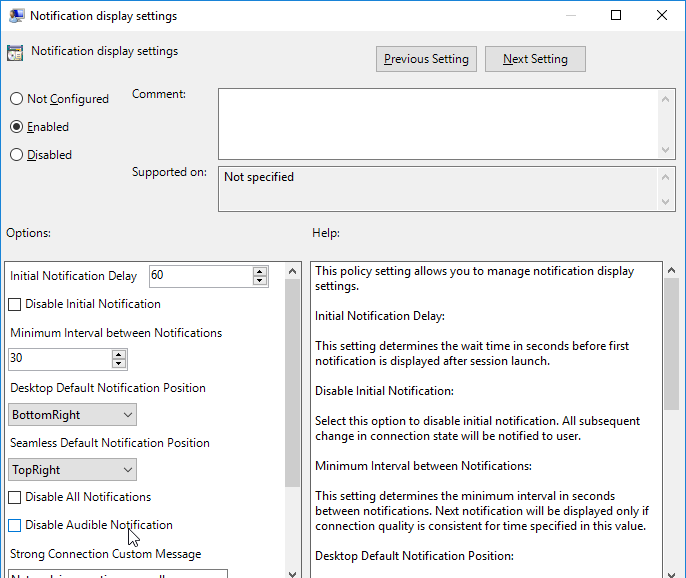
Connection Threshold Settings lets you set the notification thresholds.
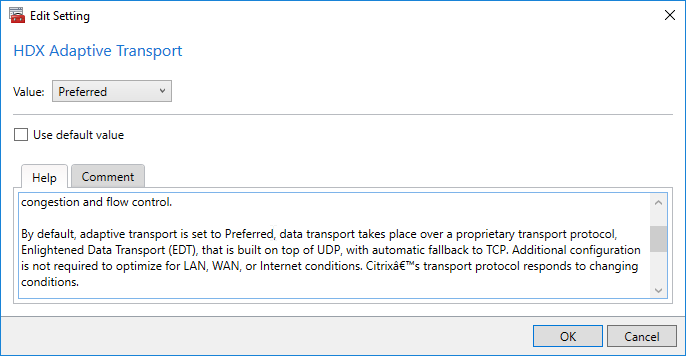
Adaptive Transport
XenApp/XenDesktop 7.16 includes Adaptive Transport, which uses EDT protocol, which uses UDP Ports 1494/2598 for HDX connections to the VDA. The UDP ports should already be open in the Windows Firewall.
For EDT through NetScaler Gateway, make sure your NetScaler firmware is up to date, preferably 11.1 build 56 or newer.
In 7.16, Adaptive Transport is defaults to Preferred, which means it’s enabled by default. It can be configured in the Citrix Policy setting HDX Adaptive Transport.
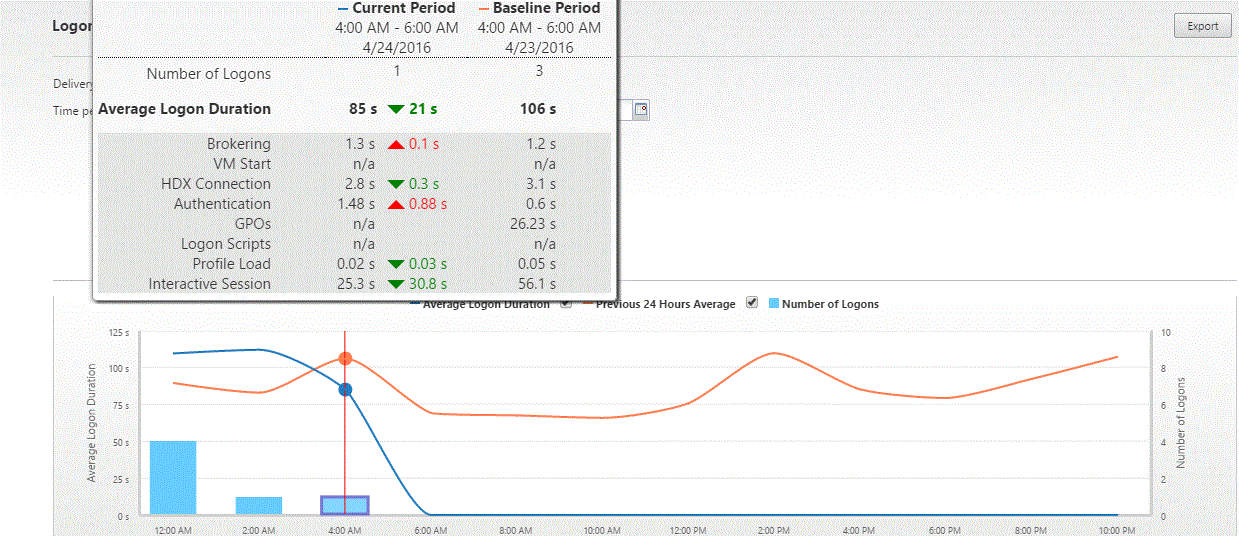
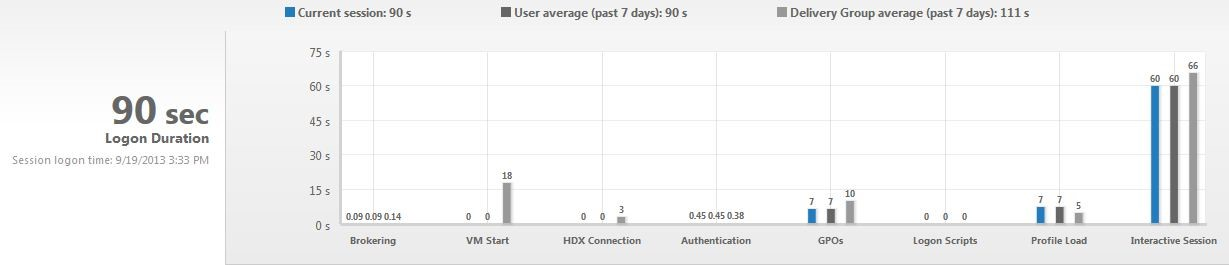
Slow Logons
Citrix Discussions Xenapp 7.9: Wait for local session manager: “I have a Xenapp 7.9 environment on Windows 2012 R2. When logging in through Citrix I got message “Wait for local session manager” for 20-30 seconds. When logging in to the server with RDS, I do not have to wait for this.”
“Add the following 2 registry keys to your 7.9 VDA server – then try connecting to it using ICA to see if the issue still occurs:
Add reg keys in “HKLM\SOFTWARE\Citrix\GroupPolicy”
Dword: “CacheGpoExpireInHours” – Value = 5-24 (# of Hours) ***start with value of 5***
Dword: “GpoCacheEnabled” – Value = 1
Restart the machine after adding these registry keys and attempt an ICA connection (at least twice) to see if that helps the Login delay.”
Mark DePalma at XenApp slow logon times, user get black screen for 20 seconds at Citrix Discussions says that pushing Tile Refresh to a background task speeds up logons.
- Regedit:
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Active Setup\Installed Components\DisableUPMResetCache]
@="DisableUPMResetCache"
"Version"="1,1,1,1"
"StubPath"="REG ADD HKCU\\Software\\Microsoft\\Windows\\CurrentVersion\\ImmersiveShell\\StateStore /v ResetCache /t REG_DWORD /d 0 /f"
"Locale"="*"
- UPM Exclusions:
Directory - '!ctx_localappdata!\Microsoft\Windows\Caches'
Registry - 'SOFTWARE\Microsoft\Active Setup\Installed Components\DisableUPMResetCache'
Marvin Neys at XenApp slow logon times, user get black screen for 20 seconds at Citrix Discussions says that deleting HKCU\Software\Microsoft\Windows\CurrentVersion\UFH\SHC at logoff reduces logon times from 40 seconds to 6 seconds.
Remove-Item HKCU:\Software\Microsoft\Windows\CurrentVersion\UFH\SHC
For additional logon delay troubleshooting, see Alexander Ollischer XenApp/XenDesktop – “Please Wait For Local Session Manager” message when logging into RDS. He found some Windows Updates that caused a logon delay.
XenApp recalculates WMI filters on every reconnect. CTX212610 Session Reconnect 30 sec Delay – DisableGPCalculation – WMI Filters indicates that recalculation can be disabled by setting HKEY_LOCAL_MACHINE\SOFTWARE\Citrix\Reconnect\DisableGPCalculation (DWORD) to 1.
CTX212439 Desktop Session Stuck in Pre-Logon State with Message “Please wait for the Local Session Manager”:
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa\Kerberos\Parameters\MaxTokenSize (DWORD) = 48000
- Delete HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\RCM\GracePeriod\L$RTMTIMEBOMB
Controller Registration Port
Some environments will not accept the default port 80 for Virtual Delivery Agent registration, even though registration is authenticated and encrypted on port 80. To change the port, do the following on the Virtual Delivery Agent:
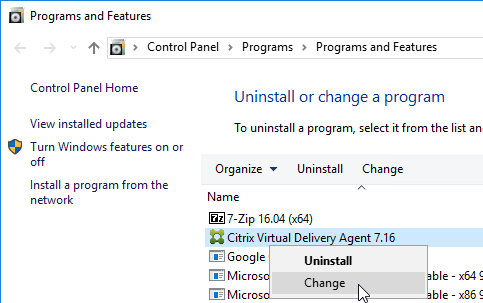
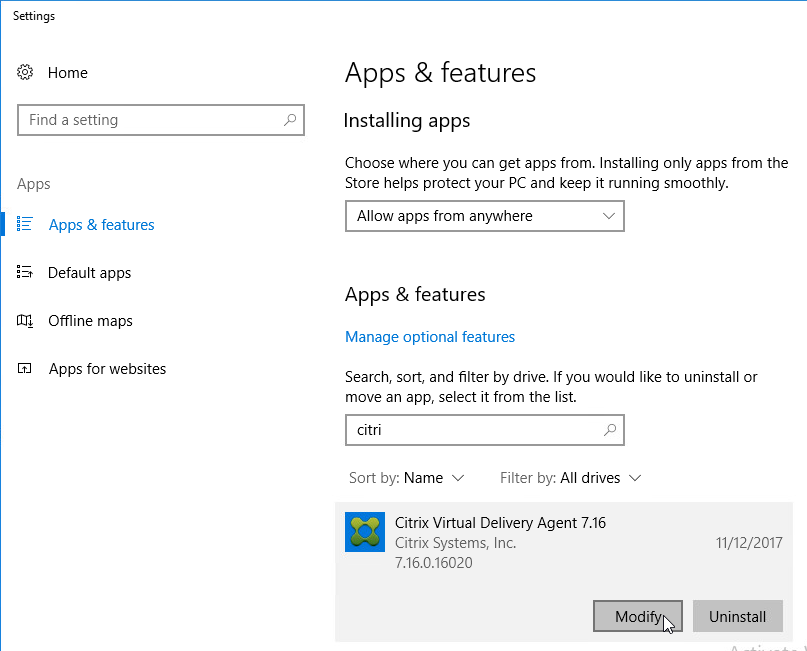
- Open Programs and Features. If Windows 10 1703 or newer, open Apps and Features.
- Find Citrix Virtual Delivery Agent, and click Change or Modify (Windows 10 1703 and newer).
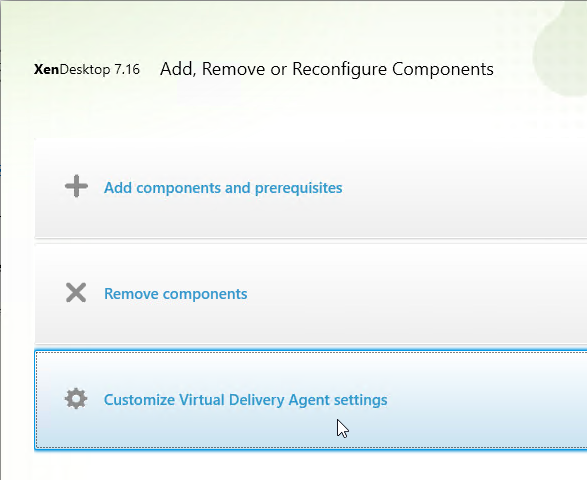
- Click Customize Virtual Delivery Agent Settings.
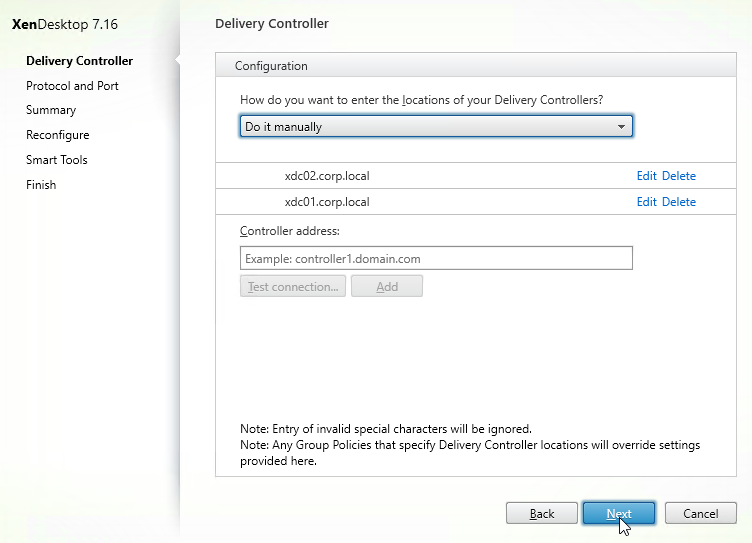
- Edit the Delivery Controllers, and click Next.
- On the Protocol and Port page, change the port number, and click Next.
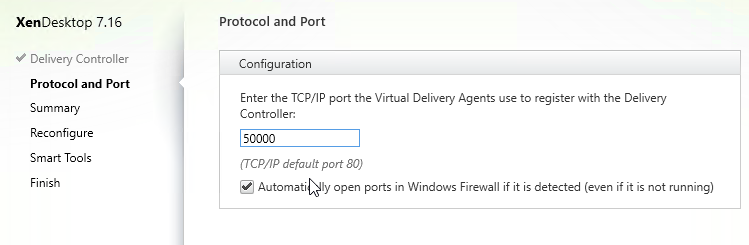
- In the Summary page, click Reconfigure.
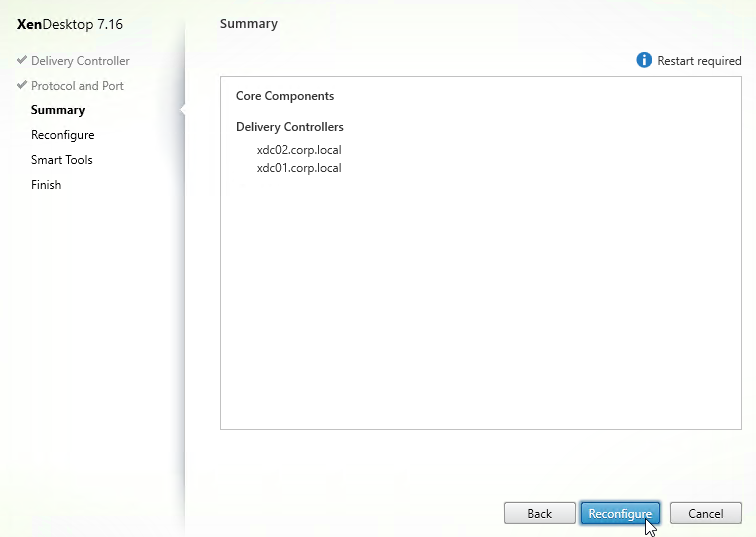
- If you see a Smart Tools page, make a selection for Call Home, and click Next.
- In the Finish Reconfiguration page, click Finish.
- Restart the VDA machine.
- You must also change the VDA registration port on the Delivery Controllers by running
BrokerService.exe /VDAPort.
- For Local Host Cache, on the Delivery Controller, run
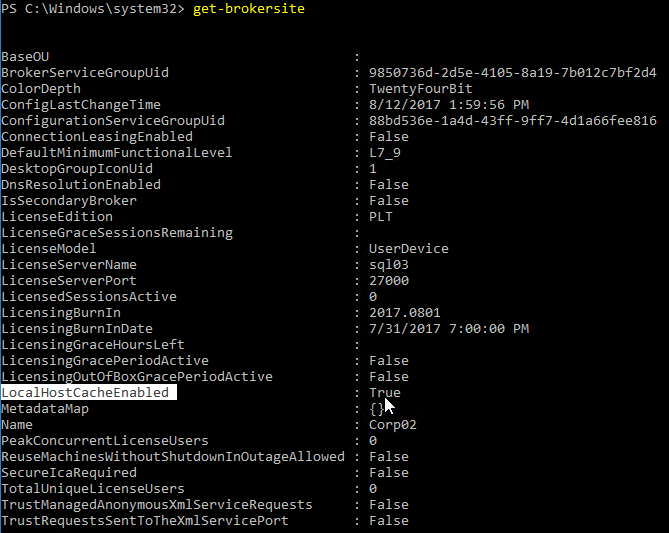
C:\Program Files\Citrix\Broker\Service\HighAvailabilityService.exe –VdaPort <CORRECT PORT #>. Source = CTX229493 VDAs Do Not Register in LHC Mode When Registration Port is Not Set To Default.
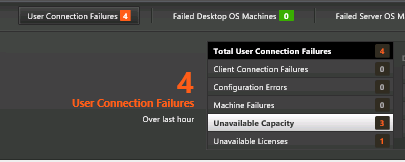
Verify that VDA registered with a Controller
- If you restart the Virtual Delivery Agent machine, or restart the Citrix Desktop Service…
- In Windows Logs > Application log, you should see an event 1012 from Citrix Desktop Service saying that it successfully registered with a controller.
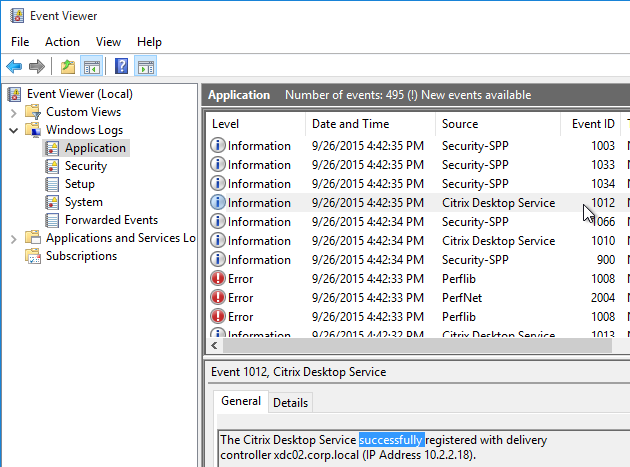
- If you don’t see successful registration, then you’ll need to fix the ListOfDDCs registry key.
- See VDA registration with Controllers at Citrix Docs.
- See The Most Common VDA Registration Issues & Troubleshooting Steps at Citrix Blogs.
- You can also run Citrix’s Health Assistant on the VDA.
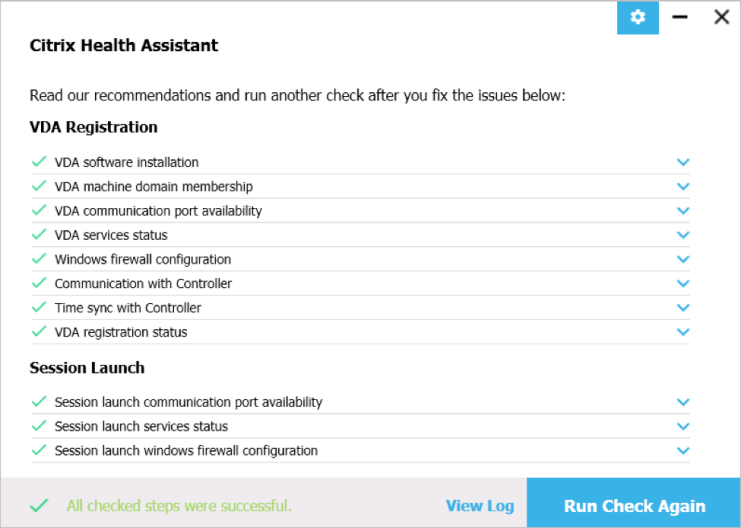
- See CTX220772 Technical Primer: VDA Registration for a very detailed explanation of the VDA Registration process.
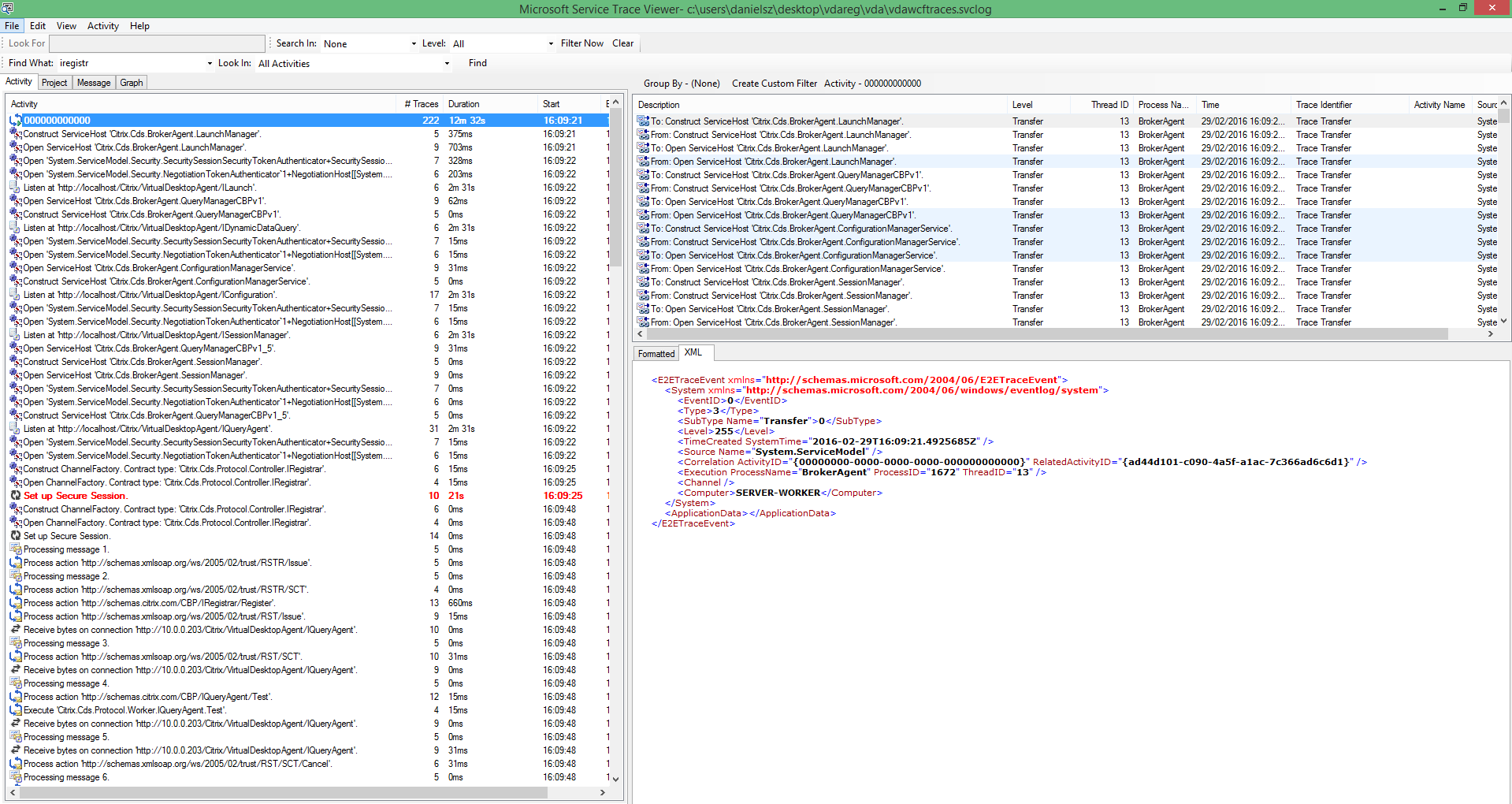
Citrix PDF Printer for Receiver for HTML5/Chrome
- VDA 7.16 installs the PDF Printer automatically so there’s no need for a separate installation.
- To enable the PDF printer for HTML5 connections, configure the Citrix Policy setting called Auto-create PDF Universal Printer in the user half of a Citrix Policy GPO.
Citrix File Access 2.0.3 for Receiver for Chrome
- If you support Receiver for Chrome (Chromebook) and want published applicatons to open files on Google Drive, install Citrix File Access on the VDAs. Get it from the Receiver for Chrome download page, in the Additional Components section.
- Go to the extracted Citrix_File_Access_2.0.3, and run FileAccess.msi.
- In the Please read the File Access License Agreement page, check the box next to I accept the terms, and click Install.
- In the Completed the File Access Setup Wizard page, click Finish.
- File Access is listed in Programs and Features (or Apps & Features) as version 2.0.3.33.
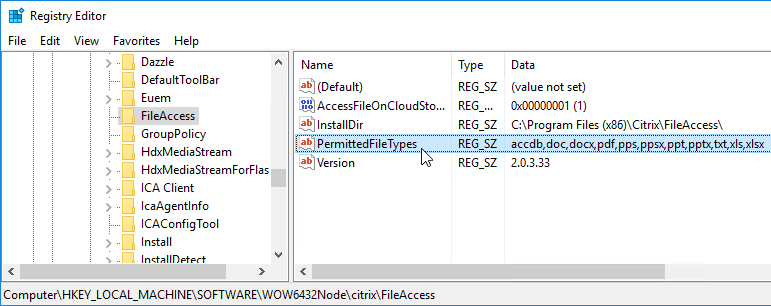
- File Access has a default list of supported file extensions. The list can be expanded by editing the registry on the VDA. See CTX219983 Receiver for Chrome Error: Invalid command line arguments: Unable to open the file as it has an unsupported extension.
- To open a file from Google Drive, right-click and and open the file using Citrix Receiver.
Framehawk Configuration
To enable Framehawk, see https://www.carlstalhood.com/citrix-policy-settings/#framehawkconfig
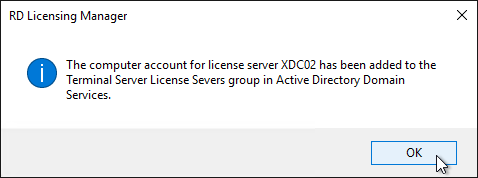
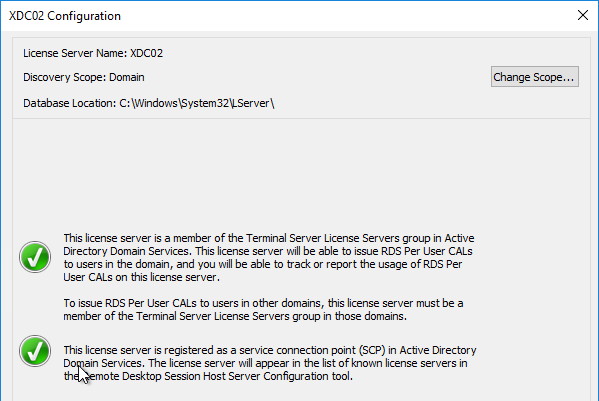
Remote Desktop Licensing Configuration
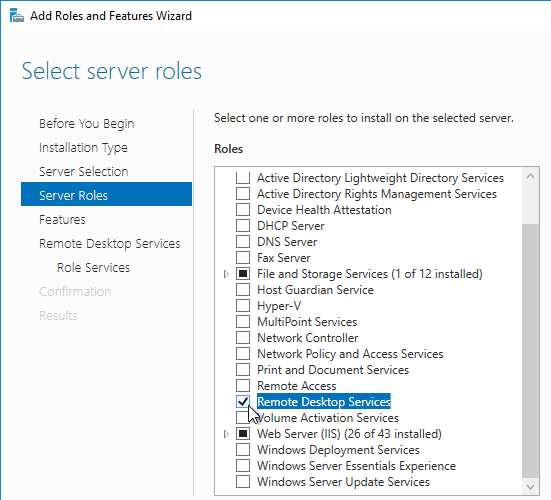
On 2012 R2 and newer RDSH, the only way to configure Remote Desktop Licensing is using group policy (local or domain). This procedure is not needed on virtual desktops.
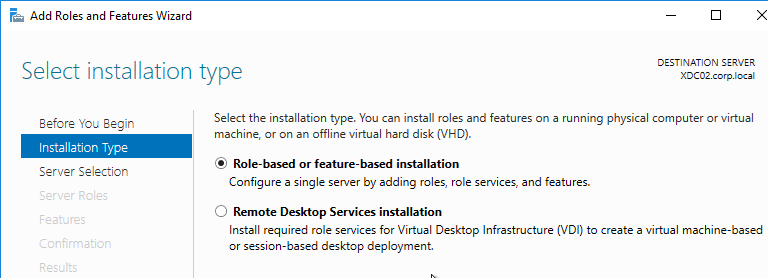
- For local group policy, run gpedit.msc. Alternatively, you can configure this in a domain GPO.
- Go to Computer Configuration > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host > Licensing.
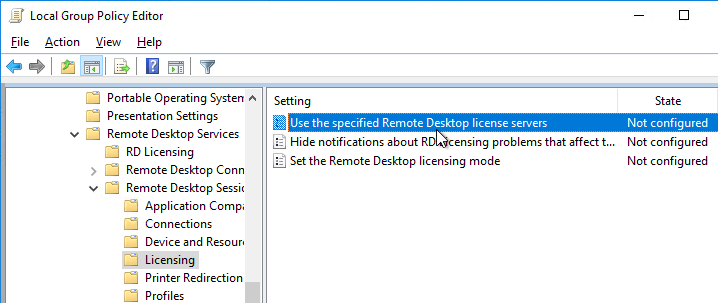
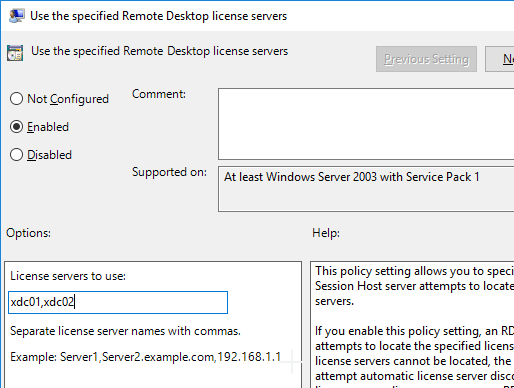
- Double-click Use the specified Remote Desktop license servers. Change it to Enabled, and enter the names of the RDS Licensing Servers (typically installed on XenDesktop Delivery Controllers). Click OK.
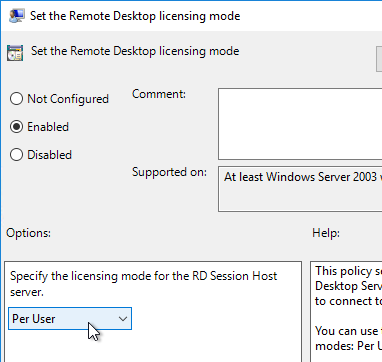
- Double-click Set the Remote Desktop licensing mode. Change it to Enabled and select Per User. Click OK.
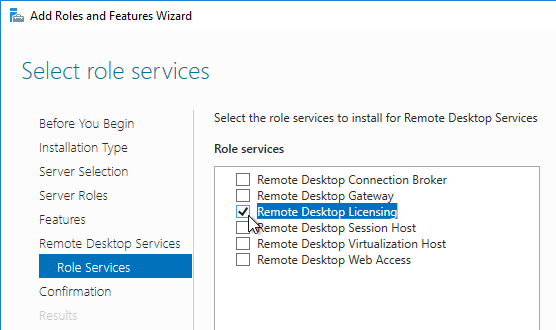
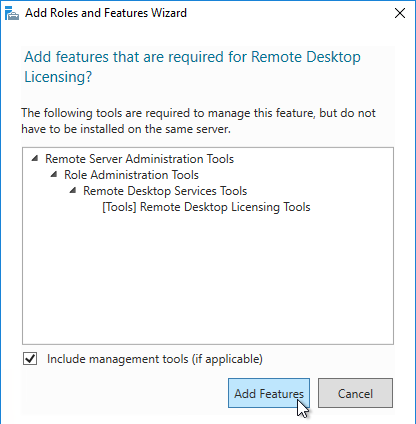
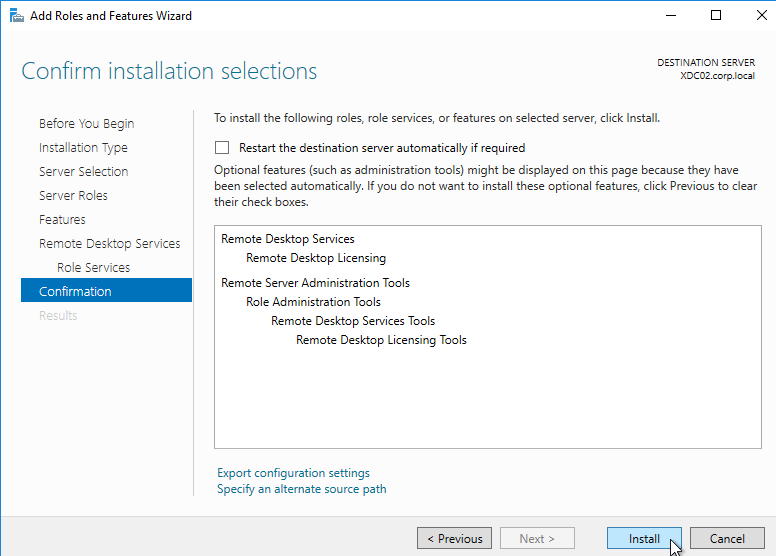
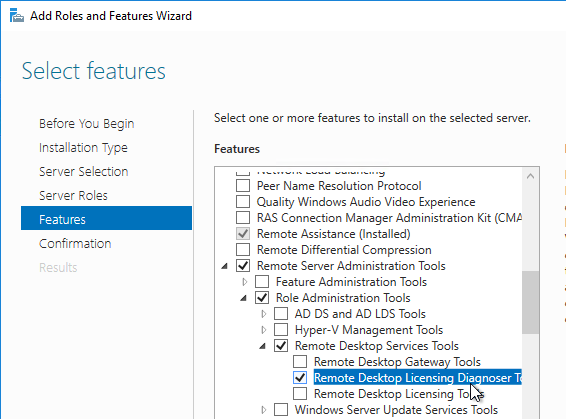
- Optionally, you can install the Remote Desktop Licensing Diagnoser Tool. In the Server Manager > Add Roles and Features Wizard, on the Features page, expand Remote Server Administration Tools, expand Role Administration Tools, expand Remote Desktop Services Tools, and select Remote Desktop Licensing Diagnoser Tool. Then Finish the wizard.
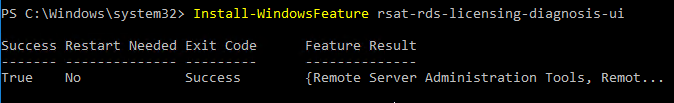
- If it won’t install from Server Manager, you can install it from PowerShell by running
Install-WindowsFeature rsat-rds-licensing-diagnosis-ui.
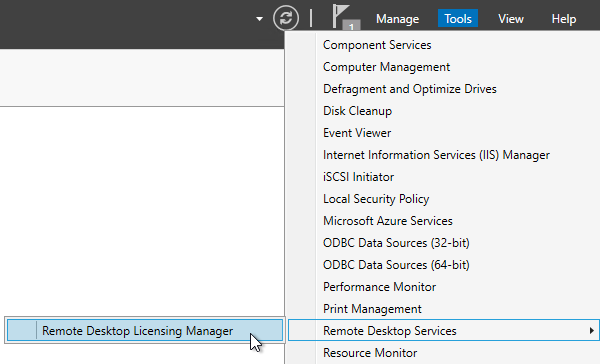
- In Server Manager, open the Tools menu, expand Remote Desktop Services (or Terminal Services), and click Remote Desktop Licensing Diagnoser.
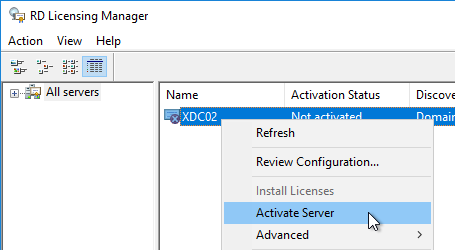
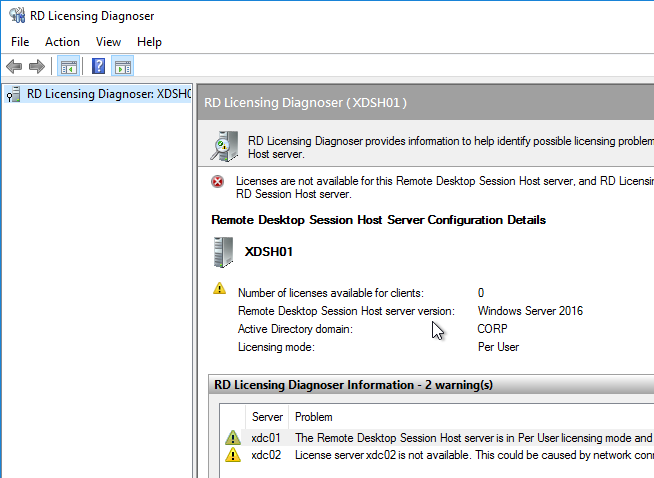
- The Diagnoser should find the license server, and indicate the licensing mode. If you’re configured for Per User licenses, then it’s OK if there are no licenses installed on the Remote Desktop License Server.
Several people in Citrix Discussions reported the following issue: If you see a message about RD Licensing Grace Period has expired even though RD Licensing is properly configured, see Eric Verdumen No remote Desktop Licence Server availible on RD Session Host server 2012. The solution was to delete the REG_BINARY in HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\RCM\GracePeriod only leaving the default. You must take ownership and give admin users full control to be able to delete this value.
C: Drive Permissions
This section is more important for shared VDAs like RDSH (Windows Server 2012 R2, and Windows Server 2016).
The default permissions allow users to store files on the C: drive in places other than their profile.
- Open the Properties dialog box for C:.
- On the Security tab, click Advanced.
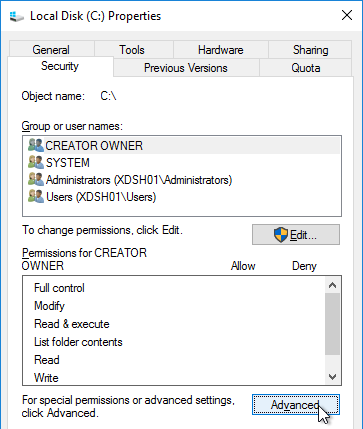
- If UAC is enabled, click Change permissions.
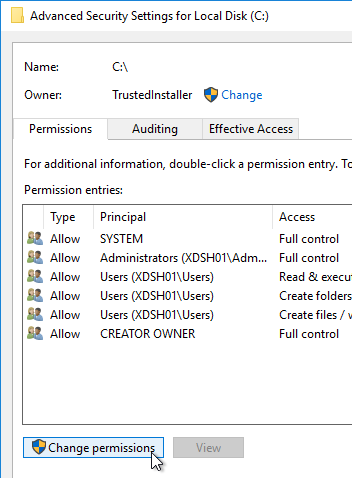
- Highlight the line containing Users and Create Folders, and click Remove.
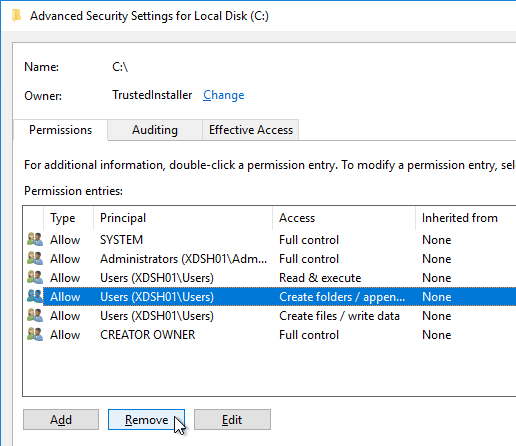
- Highlight the line containing Users and Create files (or Special), and click Remove. Click OK.
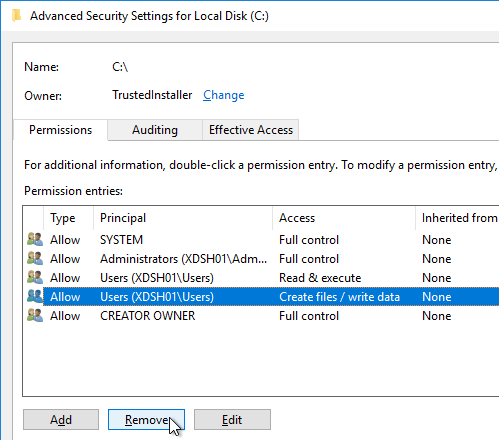
- Click Yes to confirm the permissions change.
- If you see any of these Error Applying Security windows, click Continue. This window should appear multiple times.
- Click OK to close the C: drive properties.
Pagefile
If this image will be converted to a Provisioning Services vDisk, then you must ensure the pagefile is smaller than the cache disk. For example, if you allocate 20 GB of RAM to your Remote Desktop Session Host, and if the cache disk is only 15 GB, then Windows will have a default pagefile size of 20 GB, and Provisioning Services will be unable to move it to the cache disk. This causes Provisioning Services to cache to server instead of caching to your local cache disk (or RAM).
- Open System. In 2012 R2 and newer, you can right-click the Start button, and click System. Note: in Windows 10 1703 and newer, this method no longer opens the correct tool.
- Another option is to open File Explorer, right-click This PC, and click Properties. This works in Windows 10 1703.
- Click Advanced system settings.
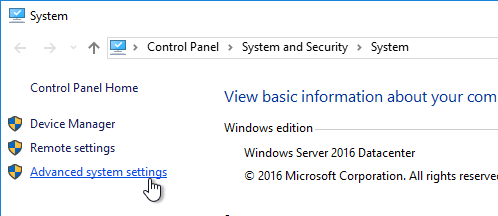
- On the Advanced tab, click the top Settings button.
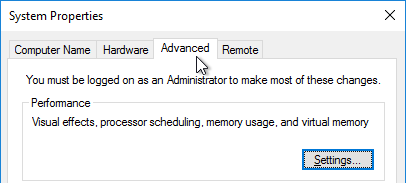
- On the Advanced tab, click Change.
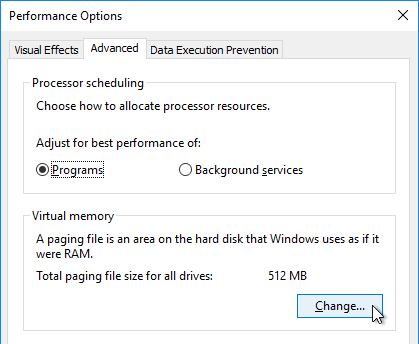
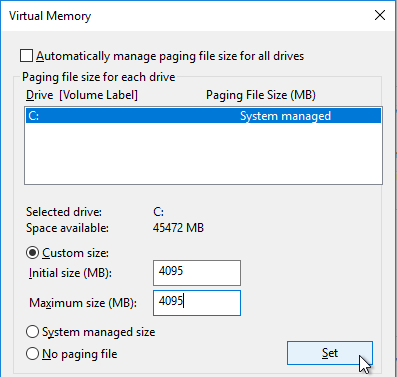
- Uncheck the box next to Automatically manage paging file size for all drives. Then either turn off the pagefile, or set the pagefile to be smaller than the cache disk. Don’t leave it set to System managed size. Click OK several times.
Direct Access Users
When Citrix Virtual Delivery Agent is installed on a machine, non-administrators can no longer RDP to the machine. A new local group called Direct Access Users is created on each Virtual Delivery Agent. Add your non-administrator RDP users to this local group so they can RDP directly to the machine.
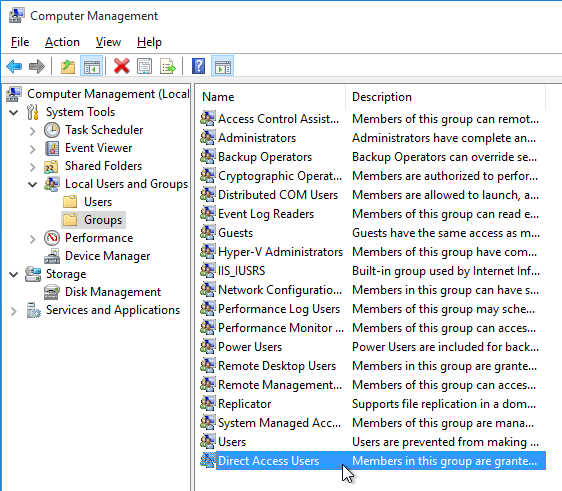
From CTX228128 What is the HKLM\Software\Citrix\PortICA\DirectAccessUsers registry function: The HKLM\Software\Citrix\PortICA\DirectAccessUsers registry key determines which Local group the VDA references to determine if a user should be allowed Unbrokered RDP access. Members of the Local Administrators group will always be granted access. If the Registry Key does not exist, or gets deleted, VDA will always allow the Unbrokered RDP Connection. The Registry key and local group are created as part of the VDA installation process.
Windows Profiles v3/v4/v5/v6
Roaming Profiles are compatible only between the following client and server operating system pairs. The profile version is also listed.
- v6 = Windows 10 (1607 and 1703) and Windows Server 2016
- v5 = Windows 10 (1511 and older)
- v4 = Windows 8.1 and Windows Server 2012 R2
- v3 = Windows 8 and Windows Server 2012
- v2 = Windows 7 and Windows Server 2008 R2
- v2 = Windows Vista and Windows Server 2008
For Windows 2012 R2, install Microsoft hotfix 2890783, and set the UseProfilePathExtensionVersion registry value to 1.
CTX230343 Reset Profile Options Is Greyed Out In Citrix Director states that the UseProfilePathExtensionVersion registry value is required on Windows 2012 R2 to enable Director users to reset profiles.
Registry
Black Screen when launch Published Apps on Windows Server 2016
From CTX225819 When Launching an Application Published from Windows Server 2016, a Black Screen Appears for Several Seconds Before Application is Visible: Citrix and Microsoft have worked together together to deliver code fixes for both Windows Server 2016 and XenApp. Microsoft is targeting their KB4034661 patch for the third week of August 2017. This fix requires a registry edit to enable.
- Key =
HKLM\SOFTWARE\Citrix\Citrix Virtual Desktop Agent
- Value =
DisableLogonUISuppression (DWORD) = 0
Published Explorer
From Citrix CTX128009 Explorer.exe Fails to Launch: When publishing the seamless explorer.exe application, the session initially begins to connect as expected. After the loading, the dialog box disappears, and the Explorer application fails to appear. On the VDA, use the following registry change to set the length of time a client session waits before disconnecting the session:
- Key =
HKLM\SYSTEM\CurrentControlSet\Control\Citrix\wfshell\TWI
- Value =
LogoffCheckerStartupDelayInSeconds (DWORD) = 10 (Hexadecimal)
Screen Saver
From Citrix CTX205214 Screensaver Not Working in XenDesktop: By default, Screen Saver doesn’t work on Desktop OS. To enable it, on the VDA, configure the following registry value:
- Key =
HKEY_LOCAL_MACHINE\SOFTWARE\Citrix\Graphics
- Value =
SetDisplayRequiredMode (DWORD) = 0
Logon Disclaimer Window Size
From XenApp 7.8 – Session Launch Security/Warning Login Banner at Citrix Discussions: If your logon disclaimer window has scroll bars, set the following registry values:
- Key =
HKEY_LOCAL_MACHINE\Software\Wow6432node\Citrix\CtxHook\AppInit_DLLS\Multiple Monitor Hook
- Value =
LogonUIWidth (DWORD) = 300
- Value =
LogonUIHeight (DWORD) = 200
Login Timeout
From Citrix CTX203760 VDI Session Launches Then Disappears: XenDesktop, by default, only allows 180 seconds to complete a logon operation. The timeout can be increased by setting the following:
- Key =
HKLM\SOFTWARE\Citrix\PortICA
- Value =
AutoLogonTimeout ( DWORD) = decimal 240 or higher (up to 3599).
Also see Citrix Discussions Machines in “Registered” State, but VM closes after “Welcome” screen.
From Citrix CTX138404 Application Connection Starts but Disappears after Timeout: after loading the application, the dialog box disappears and the application fails to appear.
- Key =
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Citrix\wfshell\TWI
- Value =
ApplicationLaunchWaitTimeoutMS (DWORD) = decimal 60000
HDX Flash
From Citrix Knowledgebase article CTX139939 – Microsoft Internet Explorer 11 – Citrix Known Issues: The registry key value IEBrowserMaximumMajorVersion is queried by the HDX Flash service to check for maximum Internet Explorer version that HDX Flash supports. For Flash Redirection to work with Internet Explorer 11 set the registry key value IEBrowserMaximumMajorVersion to 11 on the machine where HDX flash service is running. In case of XenDesktop it would be the machine where VDA is installed.
- Key =
HKLM\SOFTWARE\Wow6432Node\Citrix\HdxMediaStreamForFlash\Server\PseudoServer
- Value =
IEBrowserMaximumMajorVersion (DWORD) = 11 (Decimal)
From Citrix Discussions: Add the DWORD FlashPlayerVersionComparisonMask=0 on the VDA under HKLM\Software\Wow6432Node\Citrix\HdxMediaStreamForFlash\Server\PseudoServer. This disables the Flash major version checking between the VDA and Client Device.
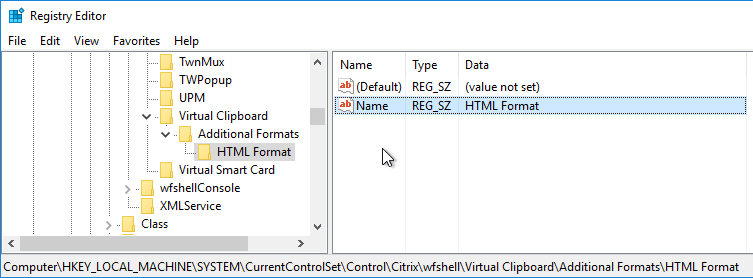
Receiver for HTML5/Chrome Enhanced Clipboard
From About Citrix Receiver for Chrome 1.9 at Citrix Docs: To enable enhanced clipboard support, create a REG_SZ registry value HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Citrix\wfshell\Virtual Clipboard\Additional Formats\HTML Format\Name=”HTML Format”. Create any missing registry keys. This applies to both virtual desktops and Remote Desktop Session Hosts.
Receiver for HTML5/Chrome Upload Folder
The Receiver for HTML5 (or Chrome) lets upload files.
By default, the user is prompted to select a upload location. If you use the Upload feature multiple times, the last selected folder is not remembered.
Citrix CTX217351 How to Customize File Upload and Download Using Receiver for HTML5 and Receiver for Chrome. You can specify a default uploads location by editing HKLM\Software\Citrix\FileTransfer\UploadFolderLocation on the VDA. Environment variables are supported. When this value is configured, users are no longer prompted to select an upload location. The change takes effect at next logon.
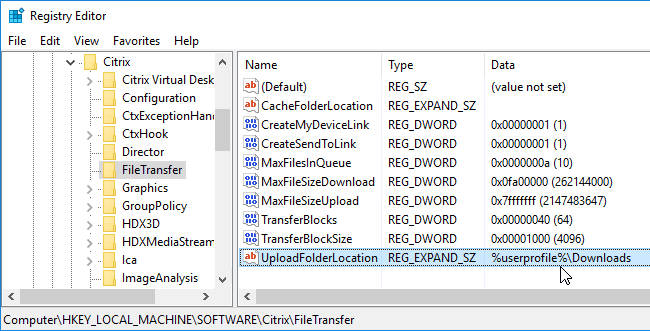
Note: HTML5/Chrome Receiver also adds a Save to My Device location to facilitate downloads.
4K Monitors
From Citrix Knowledgebase article CTX218217 Unable to span across multiple monitors after upgrade to 7.11 VDA, Black/Blank screen appears on the monitors while connecting to ICA session: .
- For VDA 7.11 and newer, calculate the video memory that is required for monitors using the following formula:
SumOfAllMons (Width * Height) * 4 / 0.3, where width and height are resolution of the monitor. Note: There is no hard and fast rule that will work for all cases.
Example: Consider the resolution of monitor 1 is 1920*1200 and monitor 2 is 1366*768. Then SumOfAllMons will be (1920*1200 + 1366*768)
- CTX115637 Citrix Session Graphics Memory Reference describes how multi-monitor resolution is determined.
- Open the registry (regedit) and navigate to: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\vbdenum
- Increase the value of “MaxVideoMemoryBytes” REG_DWORD value to the above calculated memory.
- Reboot the VDA.
Citrix Policies also control graphics performance.
COM Port Threads
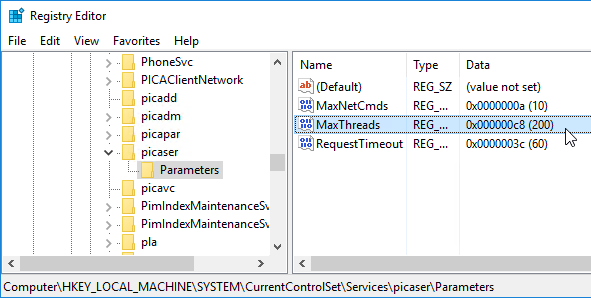
CTX212090 COM Port Intermittently Inaccessible During ICA Sessions: increase the default value of “MaxThreads” under the registry key HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\picaser\Parameters from 20 to a value greater than the number of COM port connections you want to support. For example, if a XenApp server supports 100 sessions and each session opens two COM ports, the value of “MaxThreads” should be greater than 200.
Legacy Client Drive Mapping
Citrix CTX127968 How to Enable Legacy Client Drive Mapping Format on XenApp: Citrix Client Drive Mapping no longer uses drive letters and instead they appear as local disks. This is similar to RDP drive mapping.
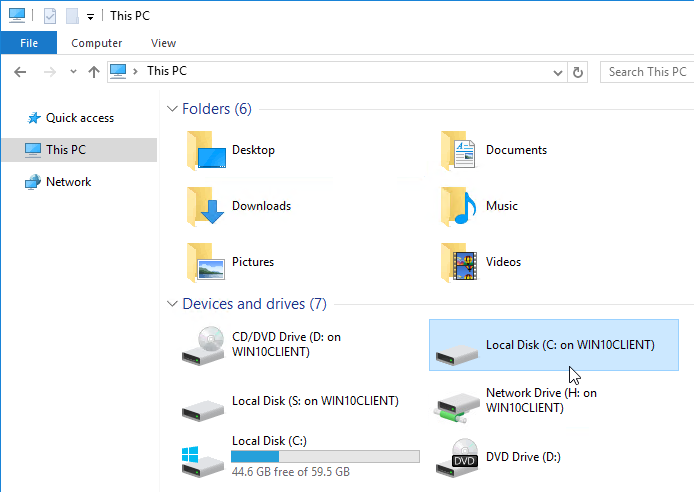
The old drive letter method can be enabled by setting the registry value:
- Key =
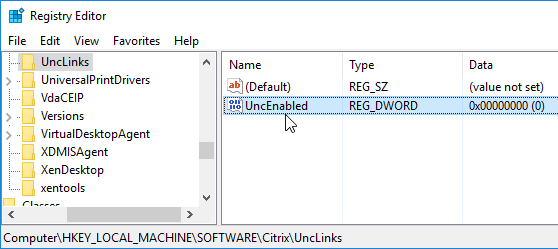
HKEY_LOCAL_MACHINE\SOFTWARE\Citrix\UncLinks (create the key)
- Value =
UNCEnabled (DWORD) = 0
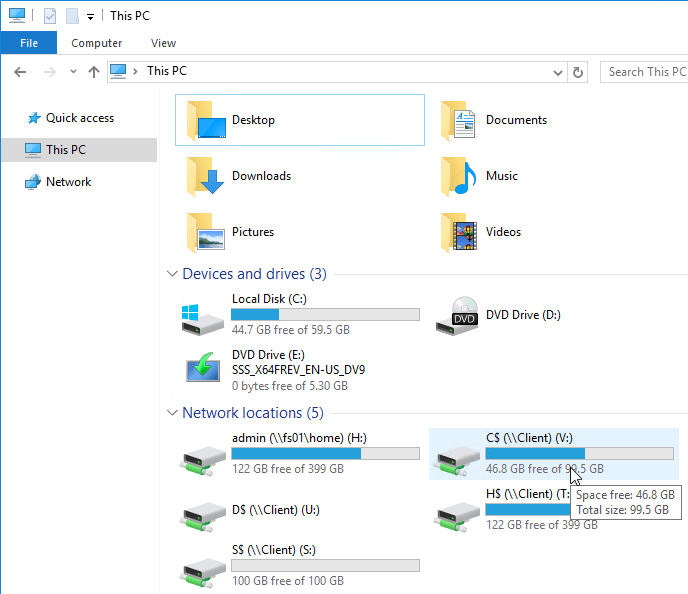
When you reconnect, the client drives will be mapped as drive letters (starts with V: and goes backwards).
Print Driver for Non-Windows Clients
From CTX139020 Configuring Virtual Machines for Mac Client Printer Mapping with Windows 8.x. By default, Non-Windows clients cannot map printers due to a missing print driver on the VDA machine.
- Requirements:
- Internet Access
- Windows Update service enabled
- Click Start, and run Devices and Printers.
- In Windows 10 1703, open Printers & scanners, then scroll down, and click Devices and printers.
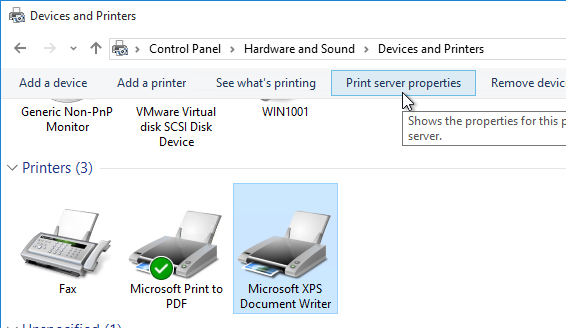
- In the Printers section, highlight a local printer (e.g. Microsoft XPS Document Writer). Then in the toolbar, click Print server properties.
- Switch to the Drivers tab. Click Change Driver Settings.
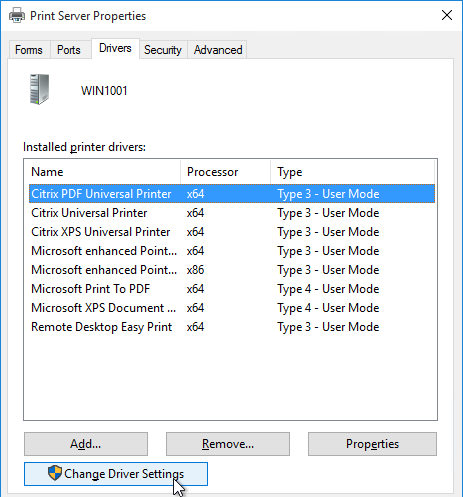
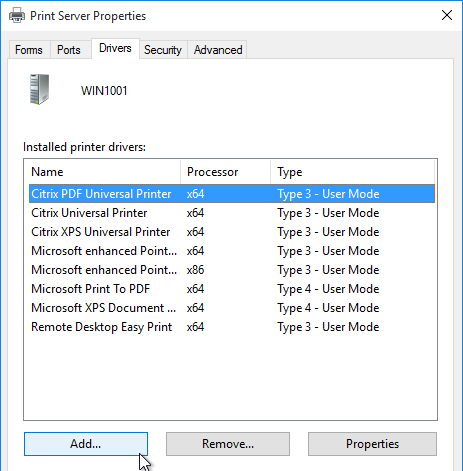
- Then click Add.
- In the Welcome to the Add Printer Driver Wizard page, click Next.
- In the Processor Selection page, click Next.
- In the Printer Driver Selection page, click Windows Update. The driver we need won’t be in the list until you click this button. Internet access is required.
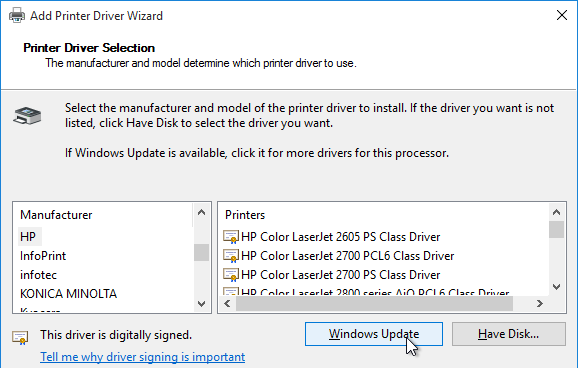
- Once Windows Update is complete, highlight HP on the left, and then select HP Color LaserJet 2800 Series PS (Microsoft) on the right. Click Next.
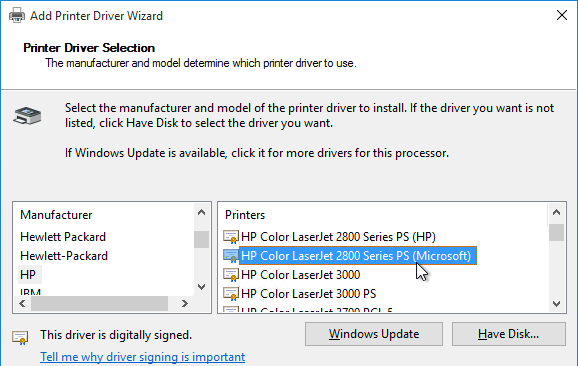
- In the Completing the Add Printer Driver Wizard page, click Finish.
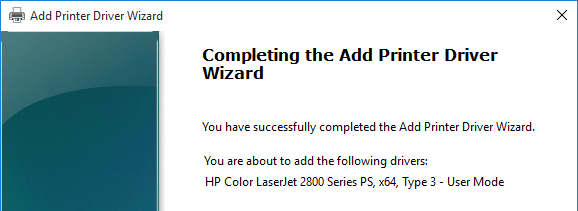
- Repeat these instructions to install the following additional drivers:
- HP LaserJet Series II
- HP Color LaserJet 4500 PCL 5
SSL for VDA
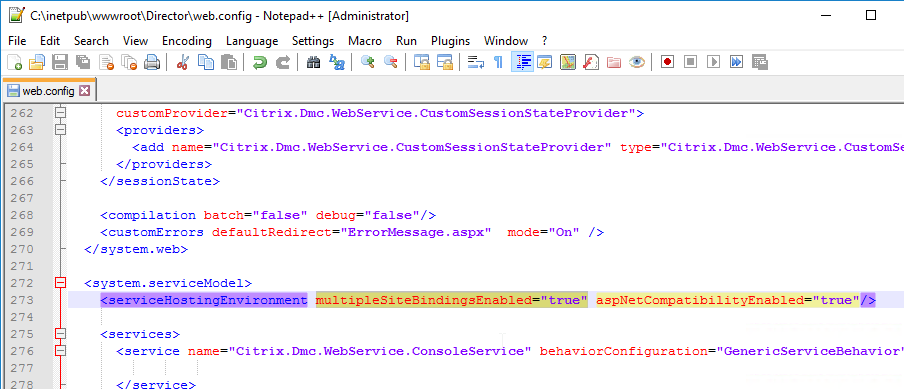
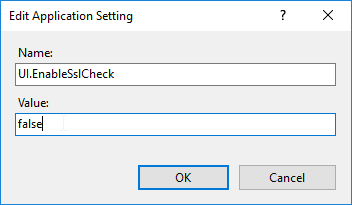
If you intend to use HTML5 Receiver internally, install certificates on the VDAs so the WebSockets (and ICA) connection will be encrypted. Internal HTML5 Receivers will not accept clear text WebSockets. External users don’t have this problem since they are SSL-proxied through NetScaler Gateway.
Notes:
- Each Virtual Delivery Agent needs a machine certificate that matches the machine name. This is feasible for a small number of persistent VDAs. For non-persistent VDAs, you’ll need some automatic means for creating machine certificates every time they reboot.
- As detailed in the following procedure, use PowerShell on the Controller to enable SSL for the Delivery Group. This forces SSL for every VDA in the Delivery Group, which means every VDA in the Delivery Group must have SSL certificates installed.
The following instructions for manually enabling SSL on VDA can be found at Configure TLS on a VDA using the PowerShell script at Citrix Docs.
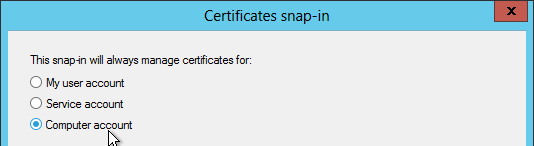
- On the VDA machine, run certlm.msc.
- Right-click Personal, expand All Tasks, and click Request New Certificate to request a certificate from your internal Certificate Authority. You can use either the Computer template or the Web Server template.
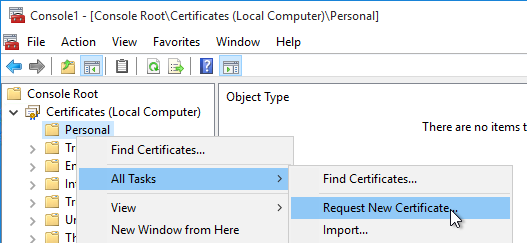
- You can also use group policy to enable Certificate Auto-Enrollment for the VDA computers.
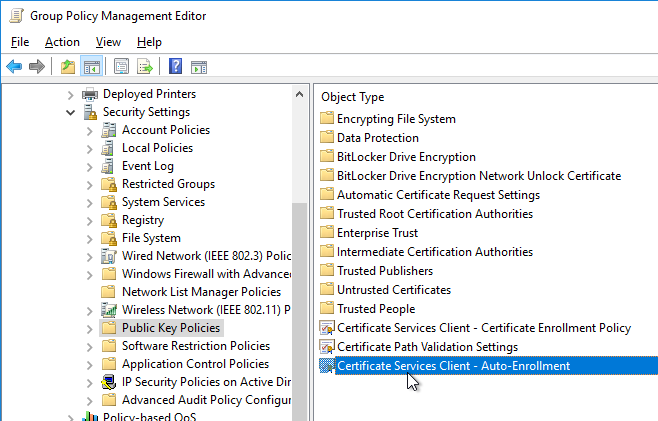
- Browse to the XenApp/XenDesktop 7.16 ISO. In the Support\Tools\SslSupport folder, shift+right-click the Enable-VdaSSL.ps1 script, and click Copy as path.
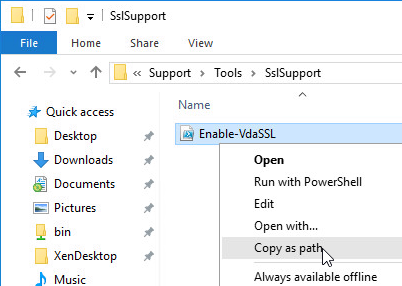
- Run PowerShell as administrator (elevated).
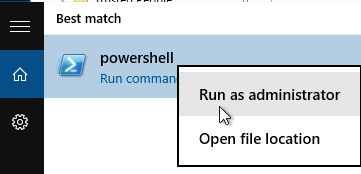
- Run the command Set-ExecutionPolicy unrestricted. Enter Y to approve.
- In the PowerShell prompt, type in an ampersand (&), and a space.
- Right-click the PowerShell prompt to paste in the path copied earlier.
- At the end of the path, type in
-Enable
- If there’s only one certificate on this machine, press Enter.
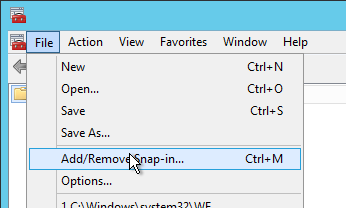
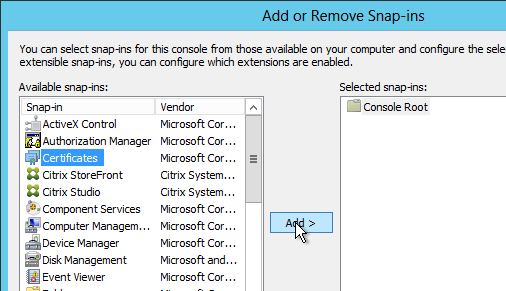
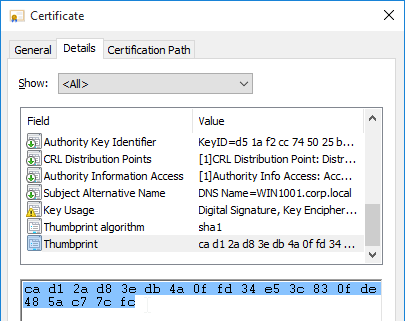
- If there are multiple certificates, then you’ll need to specify the thumbprint of the certificate you want to use. Open the Certificates snap-in, open the properties of the machine certificate you want to use, and copy the Thumbprint from the Details tab.
In the PowerShell prompt, at the end of the command, enter ‑CertificateThumbPrint, add a space, and type quotes (").
Right-click the PowerShell prompt to paste the thumbprint.
Type quotes (
") at the end of the thumbprint. Then remove all spaces from the thumbprint. The thumbprint needs to be wrapped in quotes.
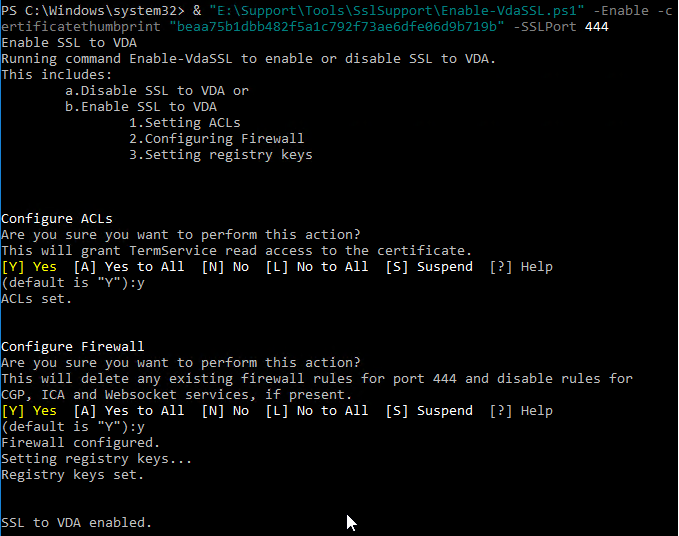
- There are additional switches to specify minimum SSL Version and Cipher Suites. Also see Citrix CTX226049 Disabling Triple DES on the VDA breaks the VDA SSL connection.

- Press <Enter> to run the Enable-VdaSSL.ps1 script.
- Press <Y> twice to configure the ACLs and Firewall.
- You might have to reboot before the settings take effect.
- Login to a Controller, and run PowerShell as Administrator (elevated).
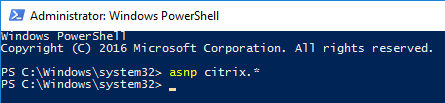
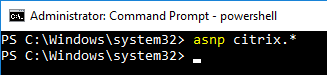
- Run the command
asnp Citrix.*
- Enter the command:
Get-BrokerAccessPolicyRule -DesktopGroupName '<delivery-group-name>' | Set-BrokerAccessPolicyRule ‑HdxSslEnabled $true
where <delivery-group-name> is the name of the Delivery Group containing the VDAs.
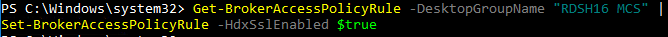
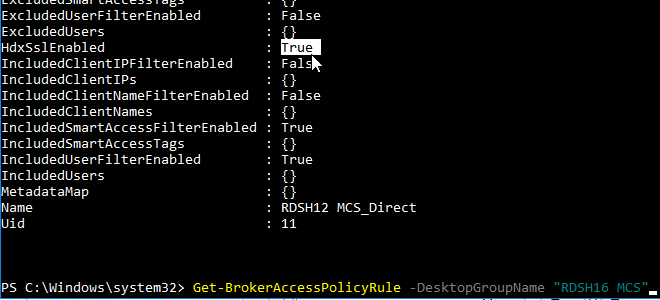
- You can run
Get-BrokerAccessPolicyRule -DesktopGroupName '<delivery-group-name>' to verify that HDX SSL is enabled.
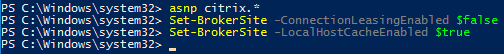
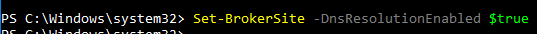
- Also run the following command to enable DNS resolution.
Set-BrokerSite –DnsResolutionEnabled $true
- Since VDA 7.16 defaults to enabling the UDP-based EDT protocol, open port UDP 443 to the VDAs.
You should now be able to connect to the VDA using the HTML5 Receiver from internal machines.
The Citrix blog post How To Secure ICA Connections in XenApp and XenDesktop 7.6 using SSL has a method for automatically provisioning certificates for pooled virtual desktops by enabling certificate auto-enrollment and setting up a task that runs after the certificate has been enrolled.
Anonymous Accounts
If you intend to publish apps anonymously then follow this section.
- Anonymous accounts are created locally on the VDAs. When XenDesktop creates Anon accounts, it gives them an idle time as specified at HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Citrix\AnonymousUserIdleTime. The default is 10 minutes. Adjust as desired.
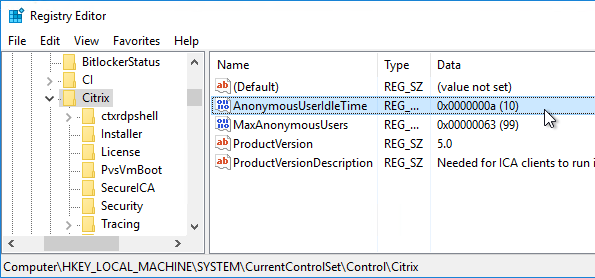
- Pre-create the Anon accounts on the VDA by running
"C:\Program Files\Citrix\ICAConfigTool\CreateAnonymousUsersApp.exe". If you don’t run this tool, then anonymous users can’t login.
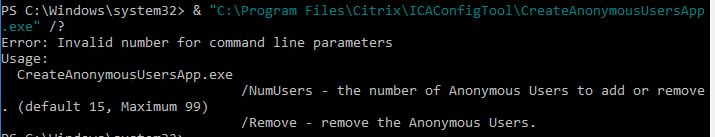
- You can see the local Anon accounts by opening Computer Management, expanding System Tools, expanding Local Users and Groups and clicking Users.
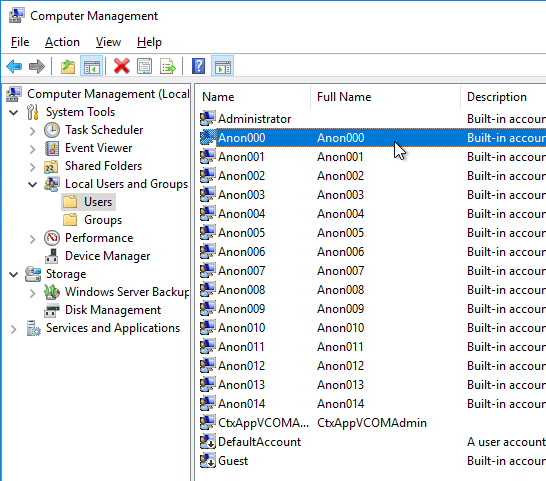
- If you want profiles for anonymous users to delete at logoff, then you’ll need to add the local Anon users to the local Guests group.
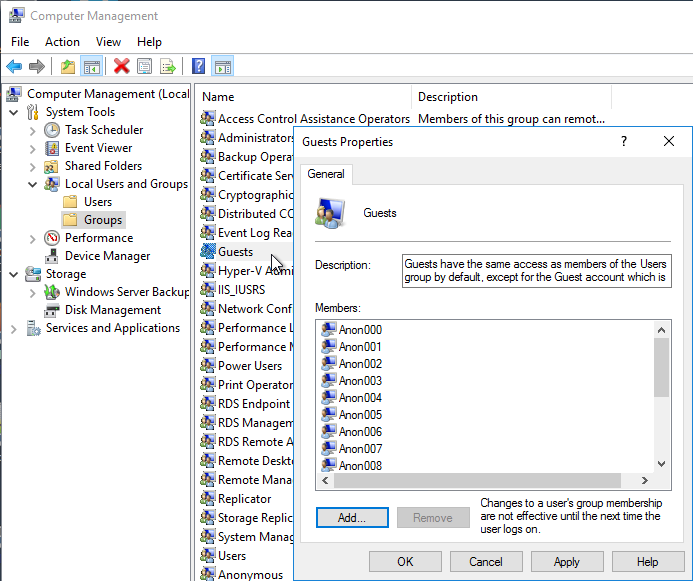
- If you open one of the accounts, on the Sessions tab, notice that idle timeout defaults to 10 minutes. Feel free to change it.
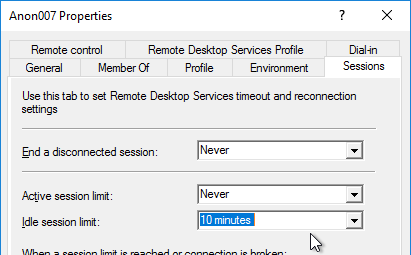
Group Policy for Anonymous Users
Since Anonymous users are local accounts on each Virtual Delivery Agent, domain-based GPOs will not apply. To work around this limitation, you’ll need to edit the local group policy on each Virtual Delivery Agent.
- On the Virtual Delivery Agent, run mmc.exe.
- Open the File menu, and click Add/Remove Snap-in.
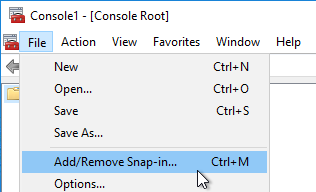
- Highlight Group Policy Object Editor, and click Add to move it to the right.
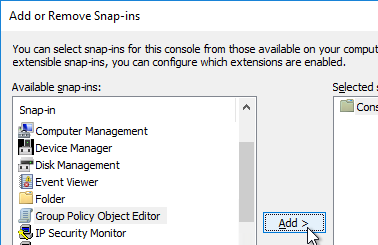
- In the Welcome to the Group Policy Wizard page, click Browse.
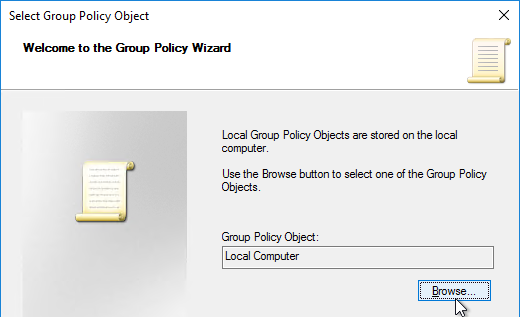
- On the Users tab, select Non-Administrators.
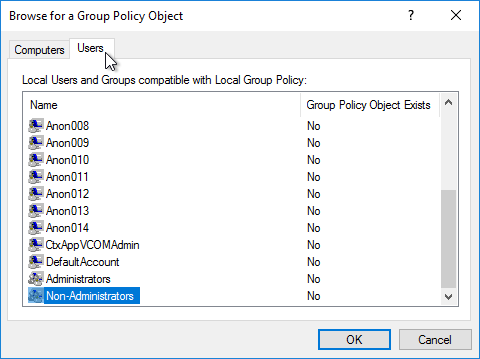
- Click Finish.
- Now you can configure group policy to lockdown sessions for anonymous users. Since this is a local group policy, you’ll need to repeat the group policy configuration on every Virtual Delivery Agent image. Also, Group Policy Preferences is not available in local group policy.
Antivirus
Install antivirus using your normal procedure. Instructions vary for each Antivirus product.
Microsoft’s virus scanning recommendations (e.g. exclude group policy files) – http://support.microsoft.com/kb/822158.
Citrix’s Recommended Antivirus Exclusions
Citrix Blog Post Citrix Recommended Antivirus Exclusions: the goal here is to provide you with a consolidated list of recommended antivirus exclusions for your Citrix virtualization environment focused on the key processes, folders, and files that we have seen cause issues in the field:
- Set real-time scanning to scan local drives only and not network drives
- Disable scan on boot
- Remove any unnecessary antivirus related entries from the Run key
- Exclude the pagefile(s) from being scanned
- Exclude Windows event logs from being scanned
- Exclude IIS log files from being scanned
See the Blog Post for exclusions for each Citrix component/product including: StoreFront, VDA, Controller, and Provisioning Services. The Blog Post also has links to additional KB articles on antivirus.
Symantec
Symantec links:
Trend Micro
Trend Micro Slow login on Citrix environment after installing OfficeScan (OSCE): The following registries can be used to troubleshoot the issue. These registries will allow a delay on the startup procedure of OSCE until the system has launched successfully. This avoids deadlock situations during login.
Citrix CTX136680 – Slow Server Performance After Trend Micro Installation. Citrix session hosts experience slow response and performance more noticeable while users try to log in to the servers. At some point the performance of the servers is affected, resulting in issues with users logging on and requiring the server to be restarted. This issue is more noticeable on mid to large session host infrastructures.
Trend Micro has provided a registry fix for this type of issue. Create the following registry on all the affected servers. Add new DWORD Value as:
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\TmFilterParameters] “DisableCtProcCheck”=dword:00000001
Trend Micro Links:
Sophos
Best Practice for running Sophos on virtual systems: we’ve amassed the following practical information about how you can optimize our software to work with this technology.
Sophos Anti-Virus for Windows XP+: Installation and configuration considerations for Sophos Anti-Virus on a Remote Desktop Services server: It maybe desirable to disable the Sophos AutoUpdate shield icon
Sophos Anti-Virus for Windows 2000+: incorporating current versions in a disk image, including for use with cloned virtual machines: This procedure will make sure that the produced target/cloned computers:
- Get their distinct identity with Enterprise Console, under which they can be subsequently managed.
- Have the desired version of Sophos Anti-Virus already installed and configured on the created image.
Windows Defender Antivirus
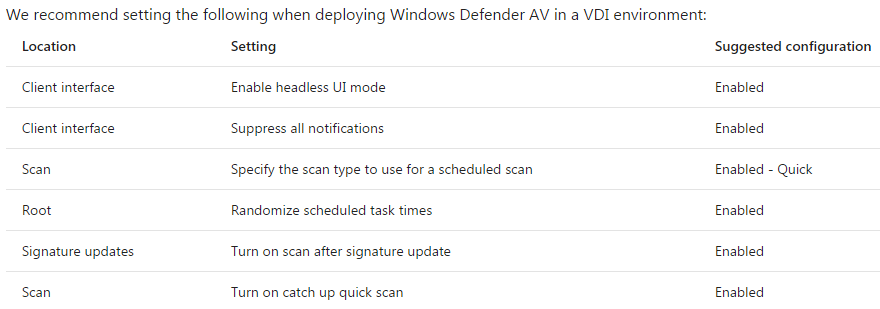
Deployment guide for Windows Defender Antivirus in a virtual desktop infrastructure (VDI) environment
Optimize Performance
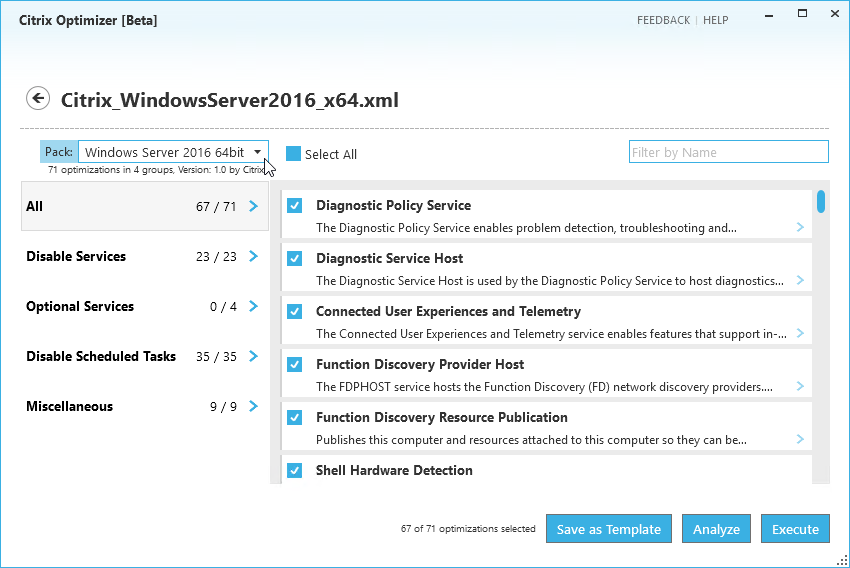
VDA Optimizer
Installation of the VDA might have already done this, but there’s no harm in doing it again. This tool is only available if you installed VDA in Master Image mode.
- On the master VDA, go to C:\Program Files\Citrix\PvsVm\TargetOSOptimizer, and run TargetOSOptimizer.exe.
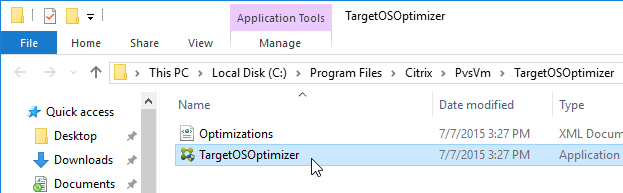
- Then click OK. Notice that it disables Windows Update.
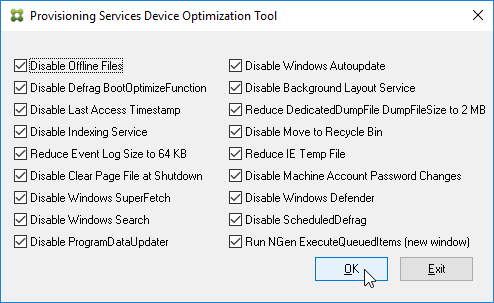
- See CTX125874 How to Optimize XenDesktop Machines for the list of registry values changed by the TargetOSOptimizer tool. You can use Group Policy Preferences to set these values.
Windows 10 / Windows 2012 R2 / Windows 2016 and newer
Optimization Notes:
Seal and Shut Down
If this VDA will be a master image in a Machine Creation Services or Provisioning Services catalog, after the master is fully prepared (including applications), do the following:
- Go to the properties of the C: drive, and run Disk Cleanup.
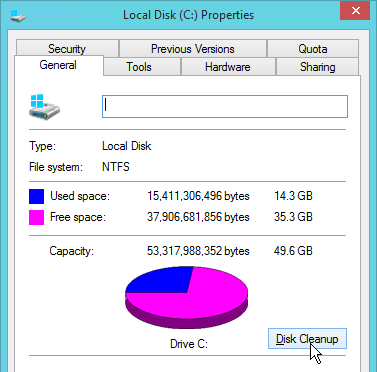
- If Disk Cleanup is missing, you can run cleanmgr.exe instead.
- Windows 10 1703 and newer has a new method for cleaning up temporary files.
- Right-click the Start button, and click System.
- Click Storage on the left, and click This PC (C:) on the right.
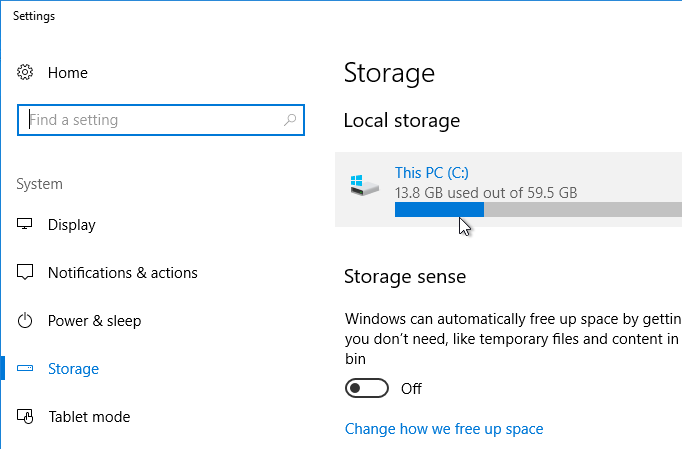
- Click Temporary Files.
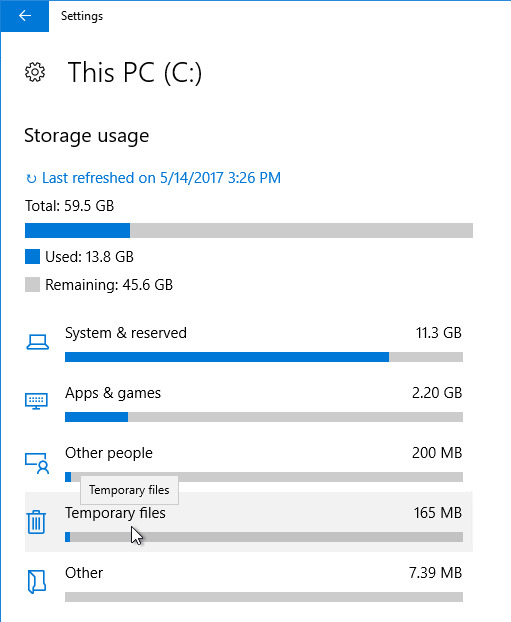
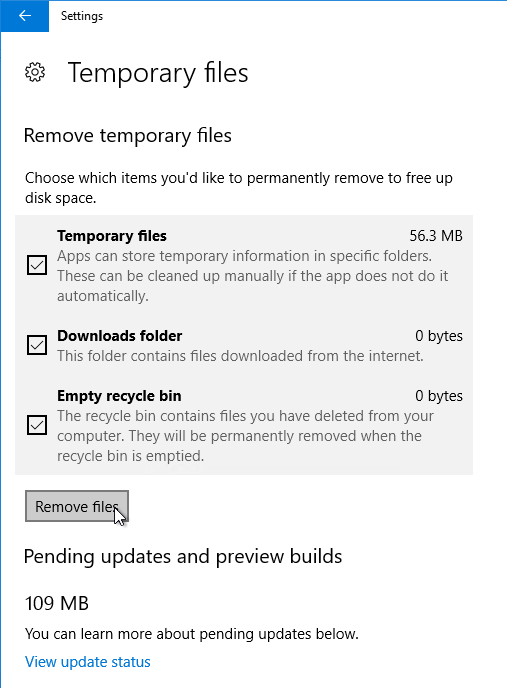
- Check boxes, and click Remove files.
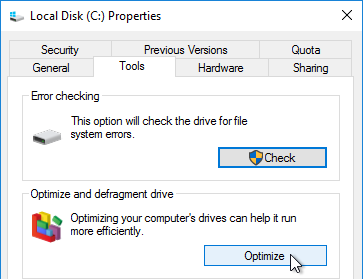
- On the Tools tab, click Optimize to defrag the drive.
 `
`
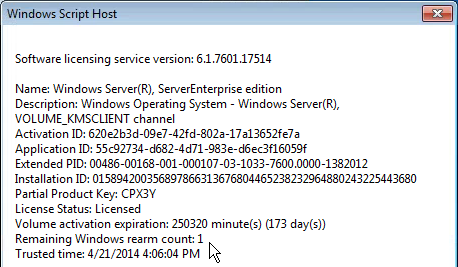
- Run slmgr.vbs /dlv and make sure it is licensed with KMS and has at least one rearm remaining. It is not necessary to manually rearm licensing since MCS will do it automatically.
- Run Delprof2 to clean up local profiles. Get it from http://helgeklein.com/download/.
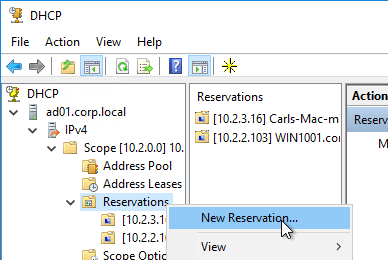
- Machine Creation Services and Provisioning Services require DHCP.

- Session hosts (RDSH) commonly have DHCP reservations.
- Base Image Script Framework (BIS-F) automates many sealing tasks. The script is configurable using Group Policy.
- Shut down the master image. You can now use Studio (Machine Creation Services) or Provisioning Services to create a catalog of linked clones.
Troubleshooting – Graphics
For Citrix Policies that control graphics codecs, see https://www.carlstalhood.com/citrix-policy-settings/#graphics
Citrix Blog post – Optimising the performance of HDX 3D Pro – Lessons from the field
From Citrix Knowledgebase article CTX218217 Unable to span across multiple monitors after upgrade to 7.11 VDA, Black/Blank screen appears on the monitors while connecting to ICA session:
- For VDA 7.11 and newer, calculate the video memory that is required for monitors using the following formula :
SumOfAllMons (Width * Height) * 4 / 0.3, where width and height are resolution of the monitor. Note: There is no hard and fast rule that will work for all cases.
Example: Consider the resolution of monitor 1 is 1920*1200 and monitor 2 is 1366*768. Then SumOfAllMons will be (1920*1200 + 1366*768)
- CTX115637 Citrix Session Graphics Memory Reference describes how multi-monitor resolution is determined.
- Open the registry (regedit) and navigate to:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\vbdenum
- Increase the value of “MaxVideoMemoryBytes” REG_DWORD value to the above calculated memory.
- Reboot the VDA
From Citrix Discussions: To exclude applications from Citrix 3D rendering, create a REG_DWORD registry value “app.exe” with value 0 or a registry value “*” with value 0.
- Both x86 and x64:
- reg add hklm\software\citrix\vd3d\compatibility /v * /t REG_DWORD /f /d 0
Wildcards are not supported. The asterisk * here has a special meaning “all apps” but is not a traditional wildcard. To blacklist multiple apps e.g. both appa.exe and appb.exe must be done by creating a registry value for each app individually.
This is most problematic in Remote PC since most physical PCs have GPUs. I recently had to blacklist Internet Explorer to prevent lockup issues when switching back to physical.
Uninstall VDA
Uninstall the VDA from Programs and Features.
Then see CTX209255 VDA Cleanup Utility.
To run the VDA Cleanup Tool silently:
- Execute VDACleanupUtility.exe /silent /noreboot to suppress reboot.
- Once the VDACleanupUtility has finished executing, setup Auto logon for the current user.
- Reboot.
- After reboot, tool will launch automatically to continue Cleanup.
Another option is to delete CitrixVdaCleanup value under HKLM\Software\Microsoft\Windows\CurrentVersion\RunOnce. Then after reboot, run VDACleanupUtility.exe /silent /reboot to indicate that it’s running after the reboot.
Related Pages














































































































































































 `
`