Navigation
Use this procedure to load balance Horizon View Connection Servers, Horizon View Security Servers, and/or VMware Access Points.
- Overview
- Monitors
- Servers
- Services
- Load Balancing Virtual Servers
- Persistency Group
- Horizon View Configuration
Overview
A typical Horizon View Installation will have at least six connection servers:
- Two Internal View Connection Servers – these need to be load balanced on an internal VIP
- Two DMZ View Security Servers – these need to be load balanced on a DMZ VIP
- The DMZ View Security Servers are paired with two additional internal View Connection Servers. There is no need to load balance the internal Paired Connection Servers. However, we do need to monitor them.
If you are using Access Points instead of Security Servers then you’ll have the following machines. Server pairing is not necessary.
- Two Internal View Connection Servers – these need to be load balanced on an internal VIP
- Two DMZ VMware Access Point appliances – these need to be load balanced on a DMZ VIP
This topic is focused on traditional View Security Servers but could be easily adapted for Access Point appliances. The difference is that with Access Points there are no paired servers and thus there’s no need to monitor the paired servers. The VIP ports are identical for both solutions.
Monitors
Users connect to Horizon View Connection Server, Horizon View Security Server, and Access Point appliances on four ports: TCP 443, TCP 8443, TCP 4172, and UDP 4172. Users will initially connect to port 443 and then be redirected to one of the other ports on the same server initially used for the 443 connection. If one of the ports is down, the entire server should be removed from load balancing. To facilitate this, create a monitor for each of the ports (except UDP 4172).
- On the left, expand Traffic Management, expand Load Balancing, and click Monitors.
- On the right, click Add.
- Name it View-PCOIP or similar.
- Change the Type drop-down to TCP.
- In the Destination Port field, enter 4172.
- Scroll down and click Create.
- On the right, click Add.
- Name it View-Blast or similar.
- Change the Type drop-down to TCP.
- In the Destination Port field, enter 8443.
- Scroll down and click Create.
- On the right, click Add.

- Name it View-SSL or similar.
- Change the Type drop-down to HTTP-ECV.
- In the Destination Port field, enter 443.
- Scroll down and check the box next to Secure.
- On the Special Parameters tab, in the Send String section, enter GET /broker/xml/
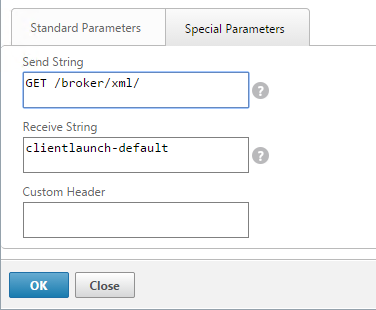
- In the Receive String section, enter clientlaunch-default.
- Scroll down and click Create.
- View Security Servers are paired with View Connection Servers. If the paired View Connection Server is down, then we should probably stop sending users to the corresponding View Security Server. Let’s create a monitor that has a specific IP address in it. Right-click the existing View-SSL or View-SSLAdv monitor and click Add.
- Note: this step does not apply to Access Points. Normally a monitor does not have any Destination IP defined, which means it uses the IP address of the service that it is bound to. However, we intend to bind this monitor to the View Security Server but we need it to monitor the paired View Connection Server, which is a different IP address. Type in the IP address of the paired View Connection Server. Then rename the monitor so it includes the View Connection Server name.
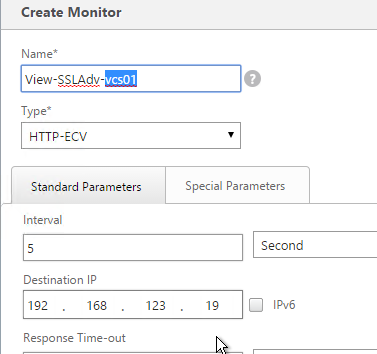
- Note: this step does not apply to Access Points. Since we are embedding an IP address into the monitor, you have to create a separate monitor for each paired View Connection Server IP.
Servers
Create Server Objects for the DMZ Security Servers and the internal non-paired Connection Servers. Do not create Server Objects for the Paired Connection Servers.
- On the left, expand Traffic Management, expand Load Balancing, and click Servers.
- On the right, click Add.
- Enter a descriptive server name, usually it matches the actual server name.
- Enter the IP address of the View Connection Server or View Security Server.
- Enter comments to describe the server. Click Create.
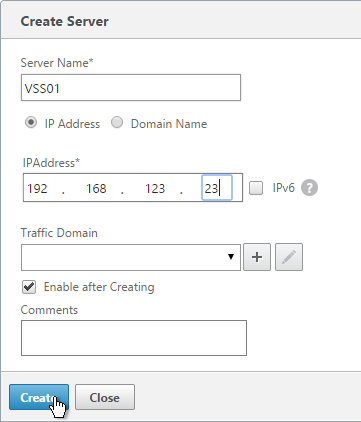
- Continue adding View Connection Servers or View Security Servers.
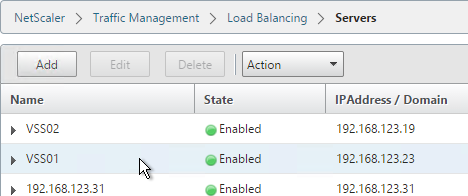
Services
If deploying View Security Servers, create Services Objects for the DMZ Security Servers and the internal non-paired Connection Servers. Do not create Services Objects for the Paired Connection Servers.
If deploying Access Points, create Services Objects for the DMZ Access Point appliances and the internal Connection Servers
Each connection server and security server needs separate Service objects. Each Security Server listens on multiple port numbers and thus there will be multiple Services Objects for each Security Server.
For Internal Connection Servers (not the paired servers), load balancing monitoring is very simple:
- Create services for SSL 443
- To verify server availability, monitor port TCP 443 on the same server.
- If tunneling is disabled then internal users connect directly to View Agents and UDP/TCP 4172 and TCP 8443 are not used on Internal Connection Servers. There’s no need to create services and monitors for these ports.
Security Servers and Access Points are more complex:
- The PCoIP Secure Gateway and HTML Blast Secure Gateway are typically enabled on Security Servers and Access Points but they are not typically enabled on internal Connection Servers.
- All traffic initially connects on TCP 443. For Security Servers and Access Points, the clients then connect to UDP 4172 or TCP 8443 on the same Security Server. If UDP 4172 or TCP 8443 are down, then you probably want to make sure TCP 443 is also brought down.
- Each Security Server is paired with an internal Connection Server. If the internal Connection Server is down then the Security Server should be taken down. This does not apply to Access Points.
- To accommodate these failure scenarios, bind multiple monitors to the View Security Server or Access Point load balancing Services. If any of the monitors fails then NetScaler will no longer forward traffic to 443 on that particular server.
If you have two View Security Servers or Access Points named VSS01 and VSS02, the configuration is summarized as follows (scroll down for detailed configuration):
- Service = VSS01, Protocol = SSL_BRIDGE, Port = 443
- Monitors = PCoIP (TCP 4172), SSL (443), and Blast (8443)
- Monitor = SSL (443) on paired View Connection Server VCS01. This monitor is not needed on Access Points.
- Service = VSS02, Protocol = SSL_BRIDGE, Port = 443
- Monitors = PCoIP (TCP 4172), SSL (443), and Blast (8443)
- Monitor = SSL (443) on paired View Connection Server VCS02. This monitor is not needed on Access Points.
- Service = VSS01, Protocol = TCP, Port = 4172
- Monitor = PCoIP (TCP 4172)
- Service = VSS02, Protocol = TCP, Port = 4172
- Monitor = PCoIP (TCP 4172)
- Service = VSS01, Protocol = UDP, Port = 4172
- Monitor = PCoIP (TCP 4172)
- Service = VSS02, Protocol = UDP, Port = 4172
- Monitor = PCoIP (TCP 4172)
- Service = VSS01, Protocol = SSL_BRIDGE, Port = 8443
- Monitor = Blast (8443)
- Service = VSS02, Protocol = SSL_BRIDGE, Port = 8443
- Monitor = Blast (8443)
If you are not using HTML Blast then you can skip 8443. If you are not using PCoIP Secure Gateway, then you can skip the 4172 ports.
- On the left, expand Traffic Management, expand Load Balancing, and click Services.
- On the right, click Add.
- Give the Service a descriptive name (e.g. svc-VSS01-SSL).
- Change the selection to Existing Server and select the View Security Server or internal (non-paired) View Connection Server you created earlier.
- Change the Protocol to SSL_BRIDGE and click OK.
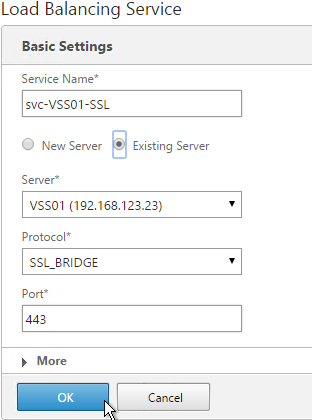
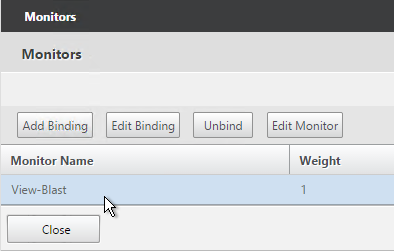
- On the left, in the Monitors section, click where it says 1 Service to Load Balancing Monitor Binding.
- Click Add Binding.
- Click the arrow next to Click to select.
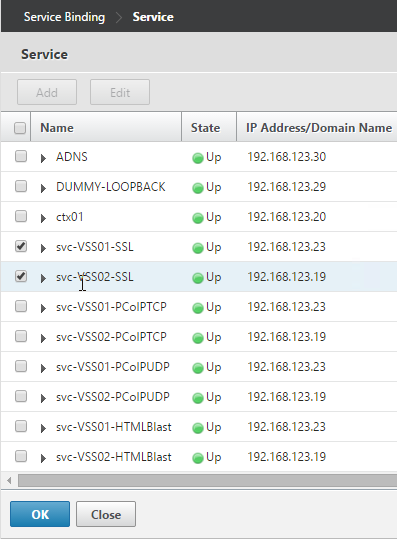
- Select the View-SSL monitor and click OK.
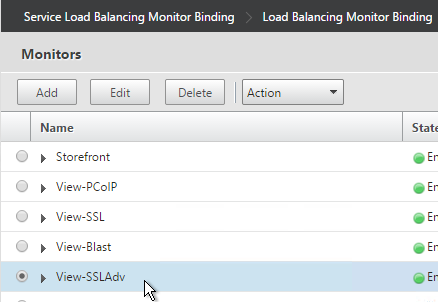
- Then click Bind.
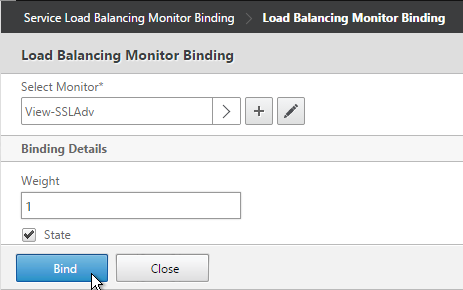
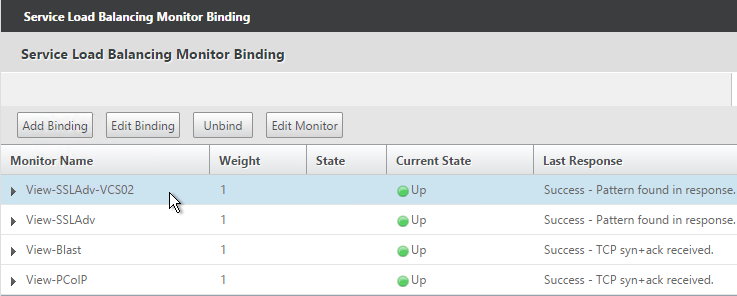
- If this is a View Security Server, add monitors for PCoIP and HTML Blast. If any of those services fails, then 443 needs to be marked DOWN.
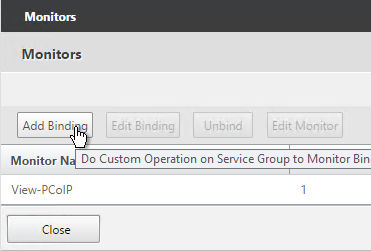
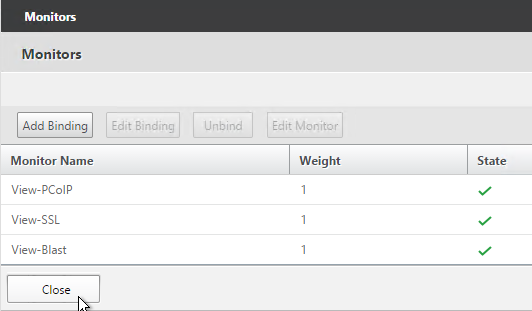
- If this is a View Security Server, also add a monitor that has the IP address of the paired View Connection Server. If the paired View Connection Server is down, then stop sending connections to this View Security Server.
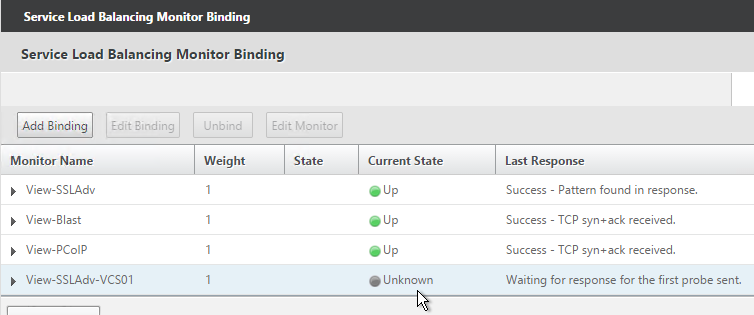
- The Last Response should indicate Success. If you bound multiple monitors to the Service, then the member will only be UP if all monitors succeed. There’s a refresh button on the top-right. Click Close when done.
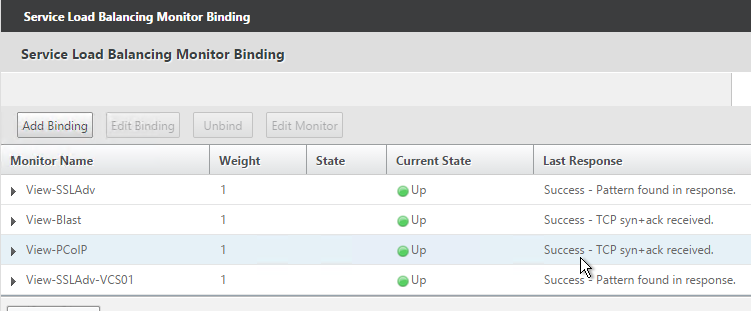
- Then click Done.

- Right-click the first service and click Add.
- Change the name to match the second View Server.
- Use the Server drop-down to select to the second View Server.
- The remaining configuration is identical to the first server. Click OK.
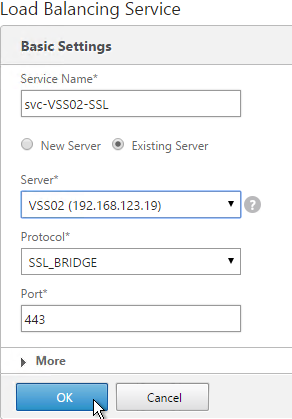
- You will need to configure the monitors again. They will be identical to the first server except for the monitoring of the paired View Connection Server. Click Done when done.
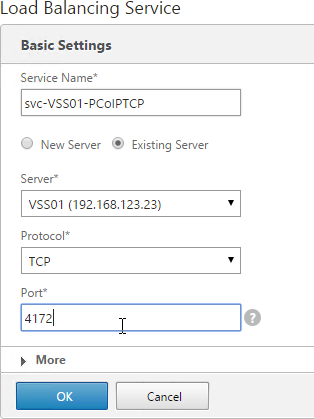
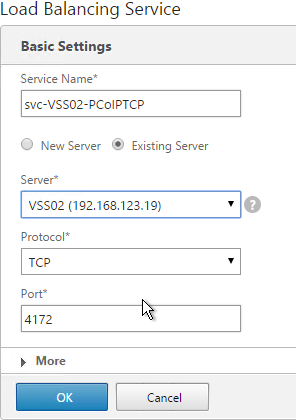
- Add another Service for PCoIP on TCP 4172.
- Name = svc-VSS01-PCoIPTCP or similar.
- Server = Existing Server, select the first View Server.
- Protocol = TCP
- Port = 4172.
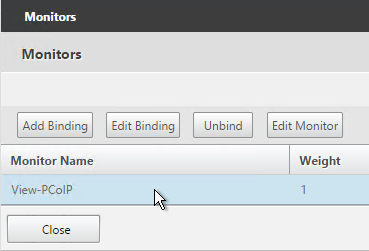
- Monitors = View-PCoIP. You can add the other monitors if desired.
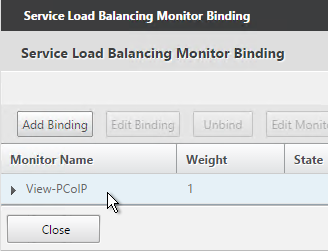
- Repeat for the 2nd View Security Server.
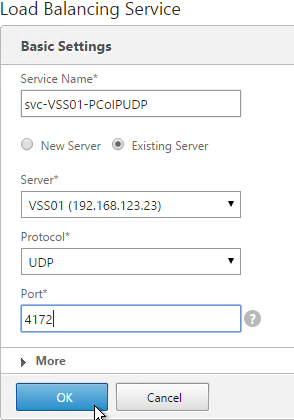
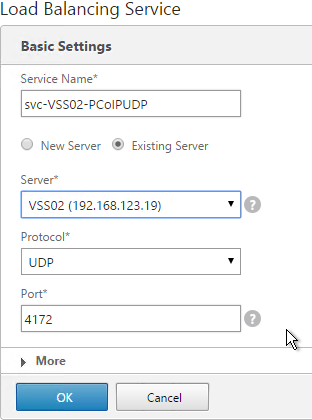
- Add another Service for PCoIP on UDP 4172.
- Name = svc-VSS01-PCoIPUDP or similar.
- Existing Server = first View Server
- Protocol = UDP
- Port = 4172.
- Monitors = View-PCoIP. You can add the other monitors if desired.
- Repeat for the 2nd View Server.
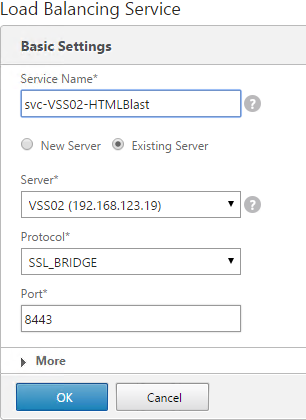
- Add another Service for HTML Blast on SSL_BRIDGE 8443.
- Name = svc-VSS01-HTMLBlast or similar.
- Existing Server = the first View Server
- Protocol =
- Port = 8443.
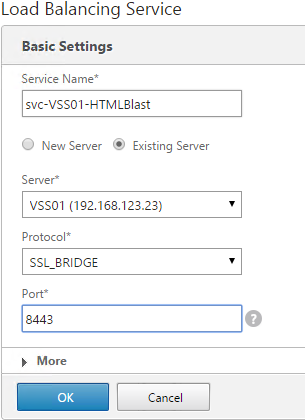
- Monitors = View-Blast. You can add the other monitors if desired.
- Repeat for the 2nd View Server.
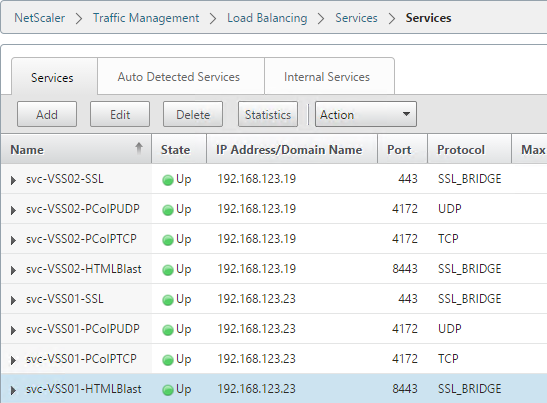
- The eight services should look something like this:
- Repeat these instructions to add the internal (non-paired) View Connection Servers except that you only need to add services for SSL_BRIDGE 443 and only need monitoring for 443.
Load Balancing Virtual Servers
Create separate load balancers for internal and DMZ.
- Internal load balances the two non-paired Internal View Connections Servers.
- DMZ load balances the two View Security Servers or Access Point appliances.
The paired View Connection Servers do not need to be load balanced.
For the internal View Connection Servers you only need a load balancer for SSL_BRIDGE 443. If tunneling is disabled then you don’t need load balancers for the other ports (UDP/TCP 4172 and SSL_BRIDGE 8443).
However, tunneling is enabled on the View Security Servers and Access Point appliances so you will need separate load balancers for each port number. Here is a summary of the Virtual Servers:
- Virtual Server on SSL_BRIDGE 443 – bind both View SSL Services.
- Virtual Server on UDP 4172 – bind both View PCoIPUDP Services.
- Virtual Server on TCP 4172 – bind both View PCoIPTCP Services.
- Virtual Server on SSL_BRIDGE 8443 – bind both View Blast Services.
Do the following to create the Virtual Servers:
- On the left, under Traffic Management > Load Balancing, click Virtual Servers.
- On the right click Add.
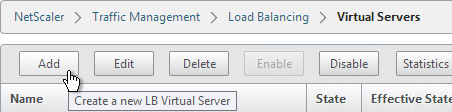
- Name it View-SSL-LB or similar.
- Change the Protocol to SSL_BRIDGE.
- Specify a new internal VIP. This one VIP will be used for all of the Virtual Servers.
- Enter 443 as the Port.
- Click OK.
- On the left, in the Services and Service Groups section, click where it says No Load Balancing Virtual Server Service Binding.
- Click the arrow next to Click to select.
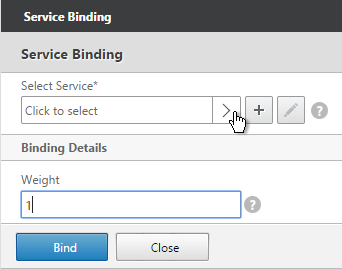
- Select the two View-SSL Services and click OK.
- Click Bind.
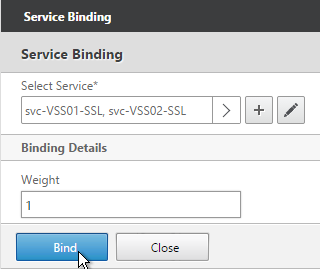
- Click OK.
- Then click Done. Persistency will be configured later.

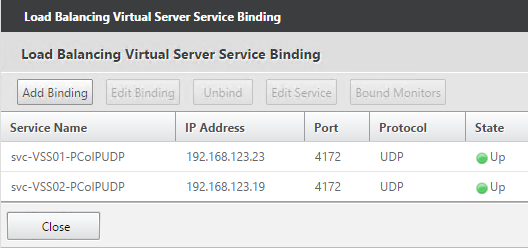
- If this is a View Security Server or Access Point or if tunneling is enabled then create another Load Balancing Virtual Server for PCoIP UDP 4172:
- Same VIP as the 443 Load Balancer.
- Protocol = UDP, Port = 4172
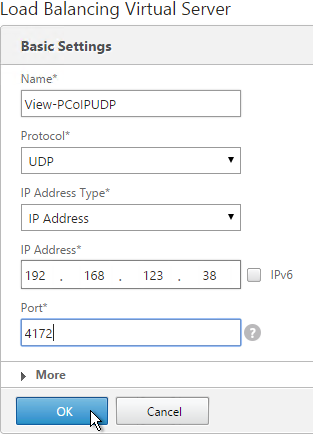
- Services = the PCoIP UDP Services.
- If this is a View Security Server or Access Point or if tunneling is enabled then create another Load Balancing Virtual Server for PCoIP TCP 4172:
- Same VIP as the 443 Load Balancer.
- Protocol = TCP, Port = 4172
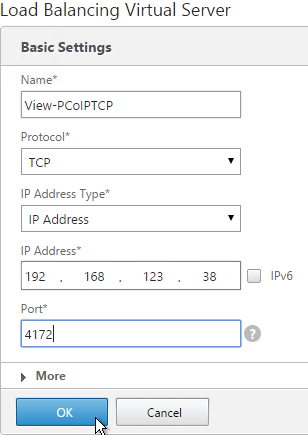
- Services = the PCoIP TCP Services.
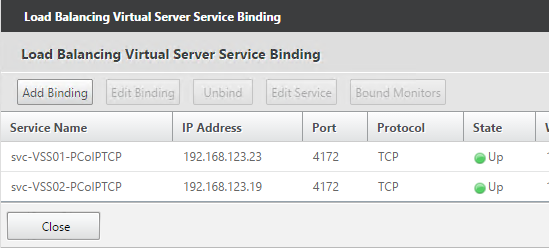
- If this is a View Security Server or Access Point or if tunneling is enabled then create another Load Balancing Virtual Server for HTML Blast SSL_BRIDGE 8443:
- Same VIP as the 443 Load Balancer.
- Protocol = SSL_BRIDGE, Port = 8443
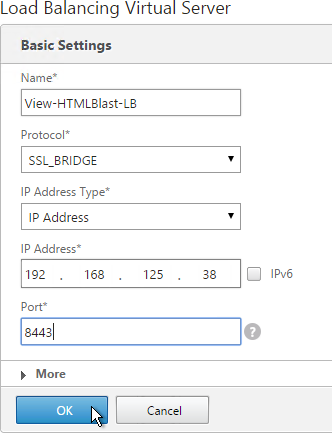
- Services = the HTML Blast SSL_BRIDGE Services.
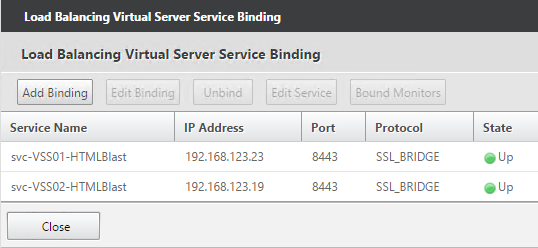
- This gives you four Virtual Servers on the same VIP but different protocols and port numbers.
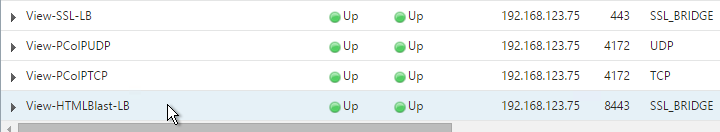
Persistency Group
For Security Servers and Access Point appliances, users will first connect to SSL_BRIDGE 443 and be load balanced. Subsequent connections to the other port numbers must go to the same load balanced server. Create a Persistency Group to facilitate this.
If tunneling is disabled on the internal View Connection Servers then you probably only have one load balancer for those servers and thus you could configure persistence directly on that one load balancer instead of creating a Persistency Group. However, since the View Security Servers have multiple load balancers then you need to bind them together in a Persistency Group.
- On the left, under Traffic Management, expand Load Balancing and click Persistency Groups.
- On the right, click Add.
- Give the Persistency Group a name (e.g. View).
- Change the Persistence to SOURCEIP.
- Enter a timeout that is equal to or greater than the timeout in View Administrator, which defaults to 10 hours (600 minutes).
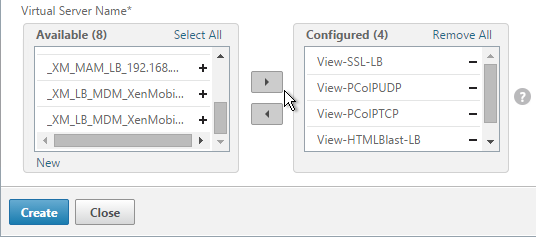
- In the Virtual Server Name section, click Add.
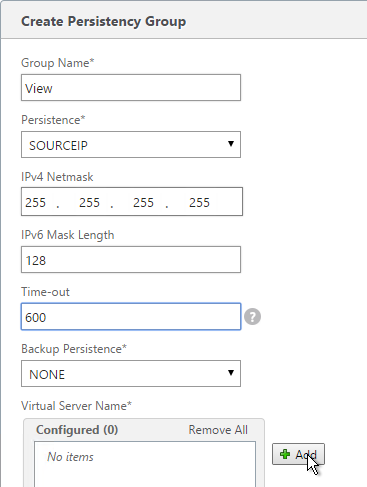
- Move all four View Security Server / Access Point Load Balancing Virtual Servers to the right. Click Create.
Horizon View Configuration
- On the View Security Servers (or View Connection Servers), request a certificate that matches the FQDN that resolves to the Load Balancing VIP.
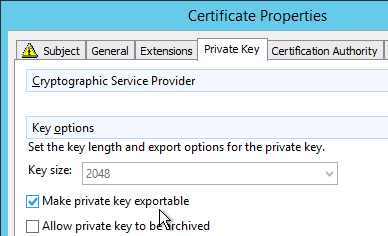
- Make sure the private key is exportable.
- Set the Friendly Name to vdm and restart the View Security Server services.
- In View Administrator, go to View Configuration > Servers.
- On the right, switch to the Security Servers tab.
- Highlight a server and click Edit.
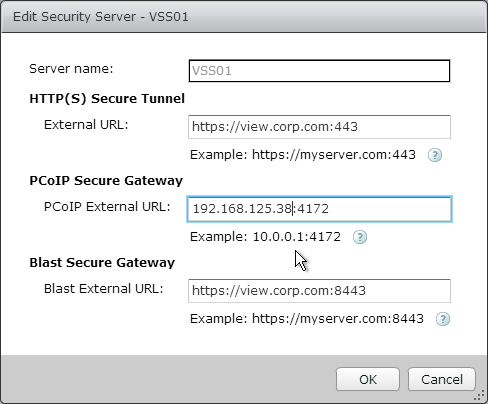
- Change the URLs to the FQDN that resolves to the load balancing VIP.
- Change the PCoIP URL to the VIP. For View Security Servers, this is typically a public IP that is NAT’d to the DMZ Load Balancing VIP.
Hi Carl,
I have a question that App Volumes compatible with Citrix PVS?. It is working fine with MCS but not with PVS. Could you please let me know there are any tweaks. Thanks in Advance!!
Hello Carl,
Thank you so much for this blog, this really helped us to over come the issue while putting the VDI to external users using NetScaler
Great article Carl… as always your articles are of great help. I had been struggling with the Horizon View configuration in my NetScaler load balancer. Following the steps outlined in this article made things work smoothly in one go…
Thank you so much!!!
Hi, Carl
Great article – it’s a good thing we have folks like you filling the HUGE gaps in vendor documentation. I am currently implementing this design and I have one question. While I understand the recommendation to use services instead of service groups in order to explicitly monitor the paired connection servers, is there any reason not to use security groups for the other vServers (PCoIP TCP, PCoIP UDP, and Blast)?
It seems that the SSL vServer would effectively act as the “traffic cop” and refuse initial connections to a SS if its paired CS is down and then the persistency group would take care of the rest, making sure none of the other vServers associated with that SS receive traffic. This logic is hinted at by the fact that you are not monitoring the paired CS on the PCoIP or Blast vServers.
Thanks!
Check out my NetScaler 11 article where I changed it to Service Groups. I haven’t back ported the changes to my 10.5 article yet. https://www.carlstalhood.com/horizon-view-load-balancing-netscaler-11/
Carl, rather than creating an individual service for each connection/security server, is it feasible to create just a single “service group” and the individual servers as service group members?
The problem is the monitors. For Security Servers, you probably want the Security Server to go down if the paired Connection Server is down. The monitor has a specific IP address in it and binding it to a service group would take down every server, not just the paired Security Server.
Access Point doesn’t have this problem.
Didn’t even think of the monitors. So with that in mind, service groups shouldn’t be an issue for Internal only Connection Servers (not paired w/ Security Servers), correct?
I can’t think of any reason why it wouldn’t work internally.
Is there a reason you are using SSL_Bridge for all the connections instead of SSL offloading? This is great documentation. I wasn’t able to find a deployment guide from Citrix, but this does a great job of fully describing the full process. Also have you ever configured load balancing between data centers using GSLB for VMware view specifically? We are currently using GSLB for our web farm between data centers (these do not require persistence) and would love you load balance View between our data centers. The data centers are connected via OTV so the back end view servers will be the same either data center you connect to. Any help would be appreciated. Thanks!
I suspect that if you don’t need smart cards then SSL Termination would probably work. But this is only for the 443 connection, which is quite minimal, since most of the traffic is PCoIP. However, I’m not sure if termination works with Blast Extreme. BTW, I revamped my NetScaler 11 version of the instructions – https://www.carlstalhood.com/horizon-view-load-balancing-netscaler-11/
Are you having difficulty configuring GSLB? If active/active, then you would need source IP persistence since there are multiple port numbers that aren’t HTTP-based. You only need GSLB configuration for SSL 443. But you might want to add monitors to the GSLB services so it monitors all of the ports.
Thank you for your response. I will review the updated documentation. As far as the GSLB implementation of View. I was more wondering if this is something that you have done before, and your thoughts on how well it works or does not work for the VMware view product. This is something we are in the process of evaluating.
I have not done GSLB with Horizon yet. Horizon Cloud Pod Architecture recommends GSLB for the main DNS name. With CPA, the PCoIP or Blast connection goes through whichever Connection Server handled the original authentication request.
For PCoIP, View Client connects to the IP address configured in the PCoIP Gateway. No GSLB involved.
For Blast, View Client or browser connects to the Blast Gateway FQDN, which needs to resolve to the same IP (and server) that handled the 443 connection. Once the connection is established, I don’t think it needs to keep resolving the DNS name.
Carl I have a case in a costumer that secure tunnel and pcoip secure gateway are checked and https external url point to own connection server, but haven’t security server paired and firewall rules not allow client direct connect to view desktops. in load balance only https service is configured. This customer are experiencing black screen between 30 sec – 2 min in session. When I disabled secure channel the problem is solved but I think that isn’t the difinitive action, an another issue is the self signed certificate is used. In this scenario to re-enable secure tunnel the URL for https have to be the VIP FQDN for the load balance? PCOIP remain checked and blast secure too. Thanks!!!
Secure Tunnel should be pointing to the load balancer.
What version of Horizon? 6.2.1 and newer disable TLS 1.0, which breaks older clients.
Hi Carl,
So I set this up just like you said and everything worked beautifully, up until a few days ago when my client decided to upgrade their Horizon View Environment to 6.2. Now View-SSL monitor is generating: “Failure – Time out during SSL handshake stage”. I checked the certificates and everything looks good, same certificates as 6.1. Has anything changed in Horizon View 6.2 regarding ssl?? All I saw in the release notes was that they disabled sslv3 but I should not be concerned about that since I am using SSL_BRIDGE. I am pulling my hair out trying to figure out why this is all of a sudden showing a down state. To make sure the monitor is working properly, the customer has a 5.3 environment, I added that to the Netscalers and the response was successful. Your feedback would greatly be appreciated..
Thank You
What version of NetScaler? Newer builds have TLS 1.2 for services and monitors.
I’m currently in the process of setting up a Horizon View 6 environment. How would I need to configure the External URL, PCOIP External URL and Blast Secure Gateway on the connection server? Would I use the load balanced VIP (i.e. vdi.mycompany.net) or would I use the FQDN of the connection server? From reading above with the security servers I would use the VIP for the URL.
Thank you
Internally you don’t normally enable the Gateways and thus don’t need to specify the URLs. Paired Connection Servers don’t matter either. It’s only the Security Servers that need accurate URLs.
With the addition of the Access Points are the two additional paired Connection servers still required?
No they are not. That’s a good point. I should update this for Access Point.
As always great documentation. I did not realize how involved it was to load balance View Security Servers. I do have a question, I will be using 2 Netscaler VPX’s for my implementation for HA. I want to make sure I truly understand this. If we are just load Balancing the Security Servers, the Netscalers will need Load Balancing DMZ VIP address and the public Address will be nat’ed to that VIP. So if they chose to also have internal connection servers load balanced, would I need to create 2 more Netscaler VPX and place them in the internal network? Then obtain an internal LB VIP address? Thanks again!!
My recommndation is to never connect a single NetScaler to multiple security zones unless you use traffic domains, partitioning, or multiple intances on an SDX. In a single traffic domain there is a single routing table and thus inbound DMZ traffic could route to the internal interface and bypass the firewall. If you’re OK with that then you can certainly use one appliance for both DMZ and internal. Many companies do that because they weren’t aware of the risks before purchasing NetScalers. Try to implement separate internal appliances if you can.
Thanks for the quick response! This is what I thought but wanted to verify it. Thank you again!
Sorry one last question, what is the reasoning behind not being able to load balance the 2 connection servers that are being paired with the security servers for internal users instead of building another 2 connection servers for internal users. Just trying to get a complete understanding, I am used to how XD7.6 is but this is a little different.
You should have two separate servers for internal connections.
SSL Tunnel is configured on the paired connection server. If you disable it for internal users and if you have paired security Servers then the external connections won’t be proxied through the security server. If you want tunnel for external and no tunnel for internal then you need separate connection servers for both. That’s six servers total: 2 security, 2 connection for external paired with the security, and 2 connection for internal.